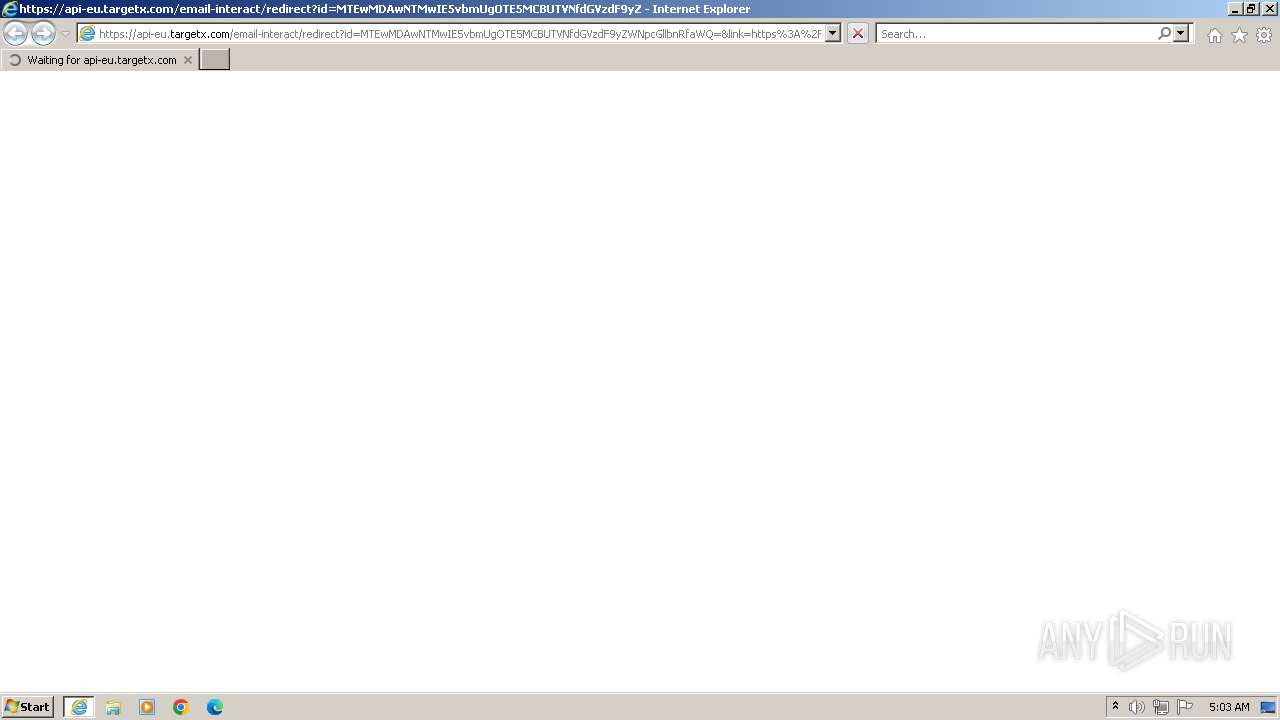
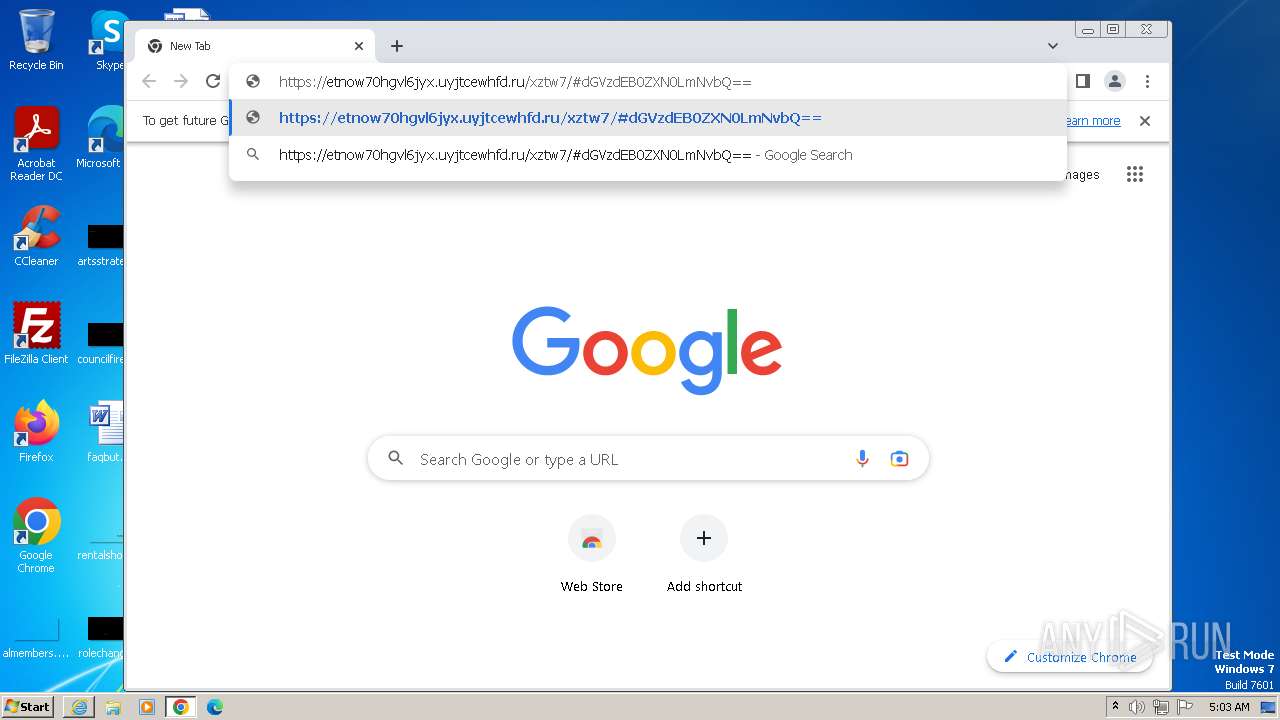
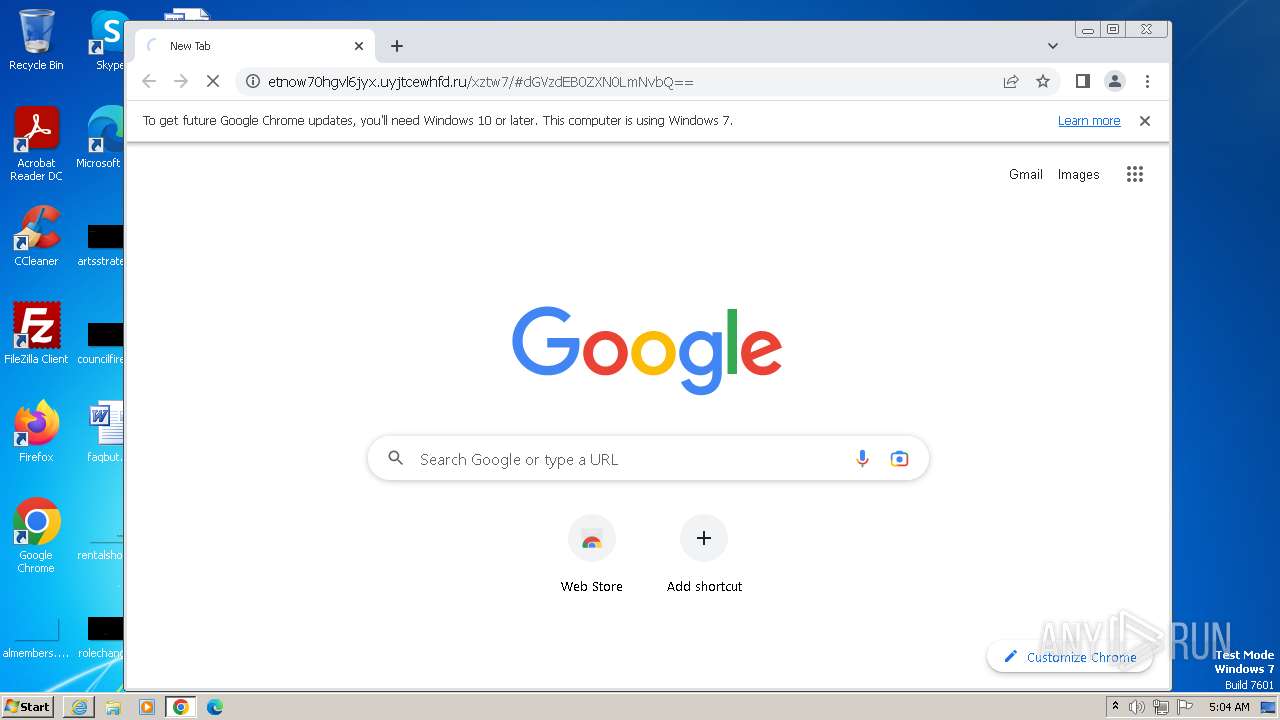
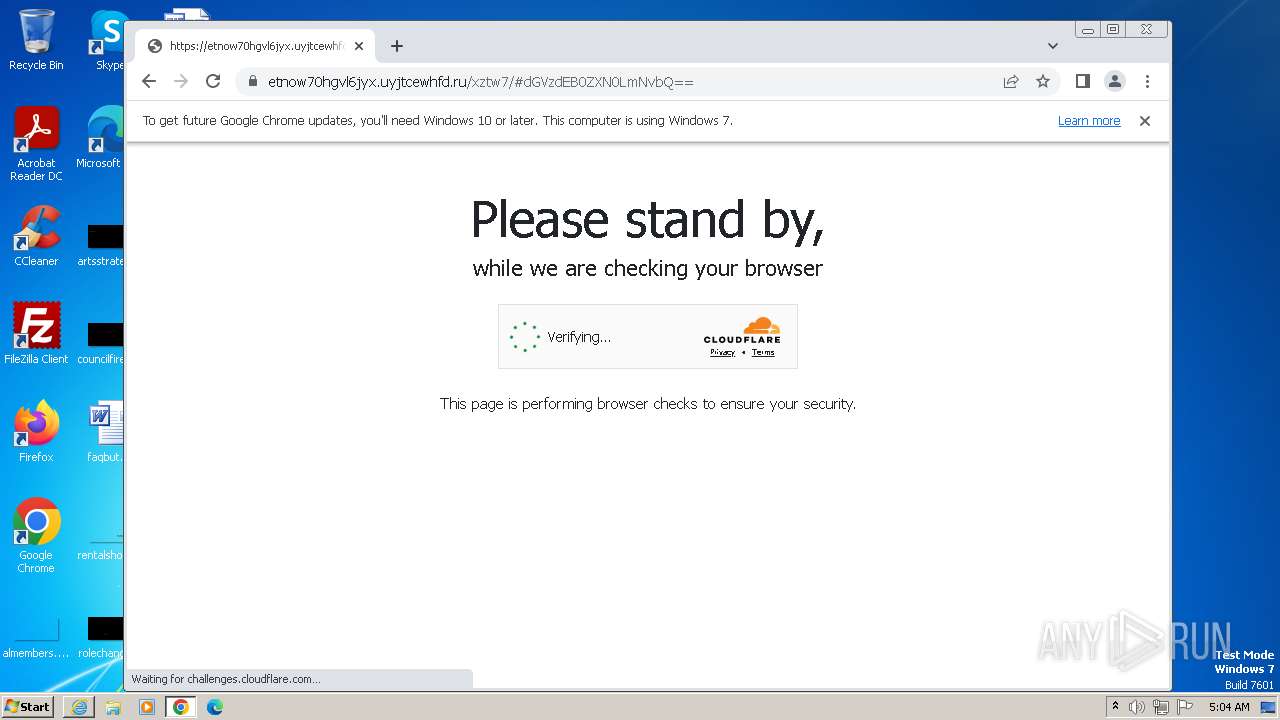
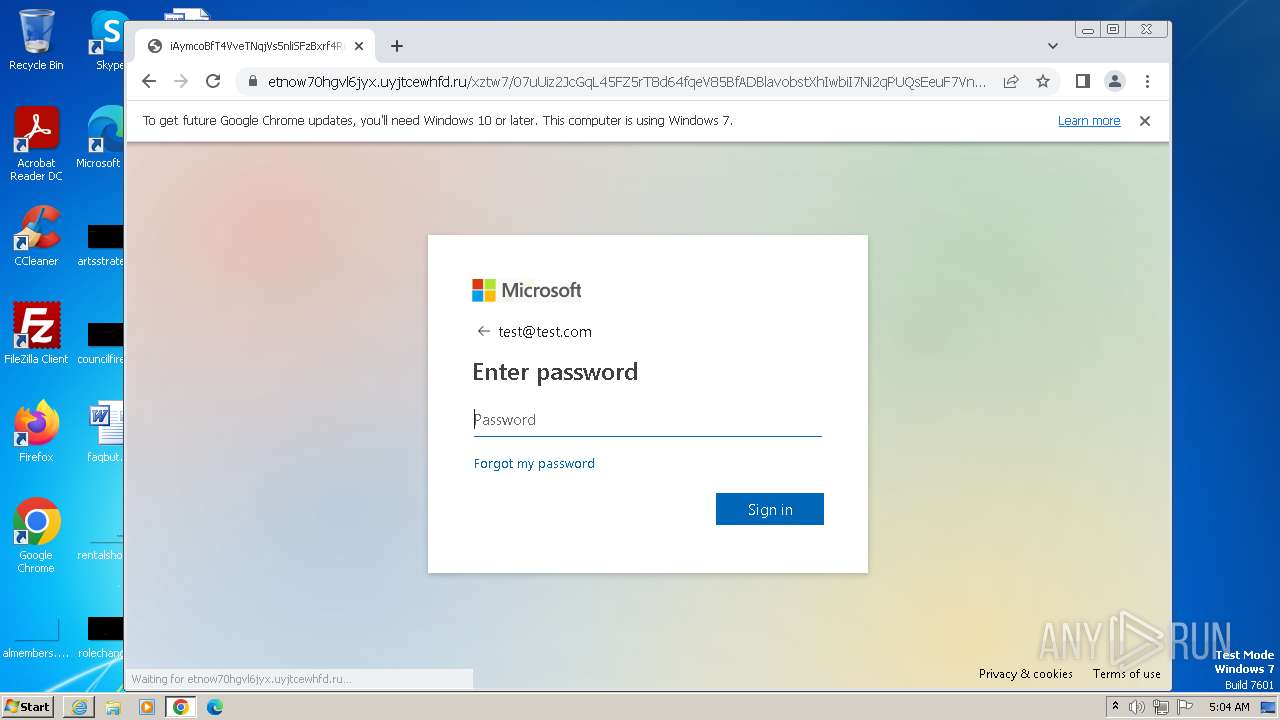
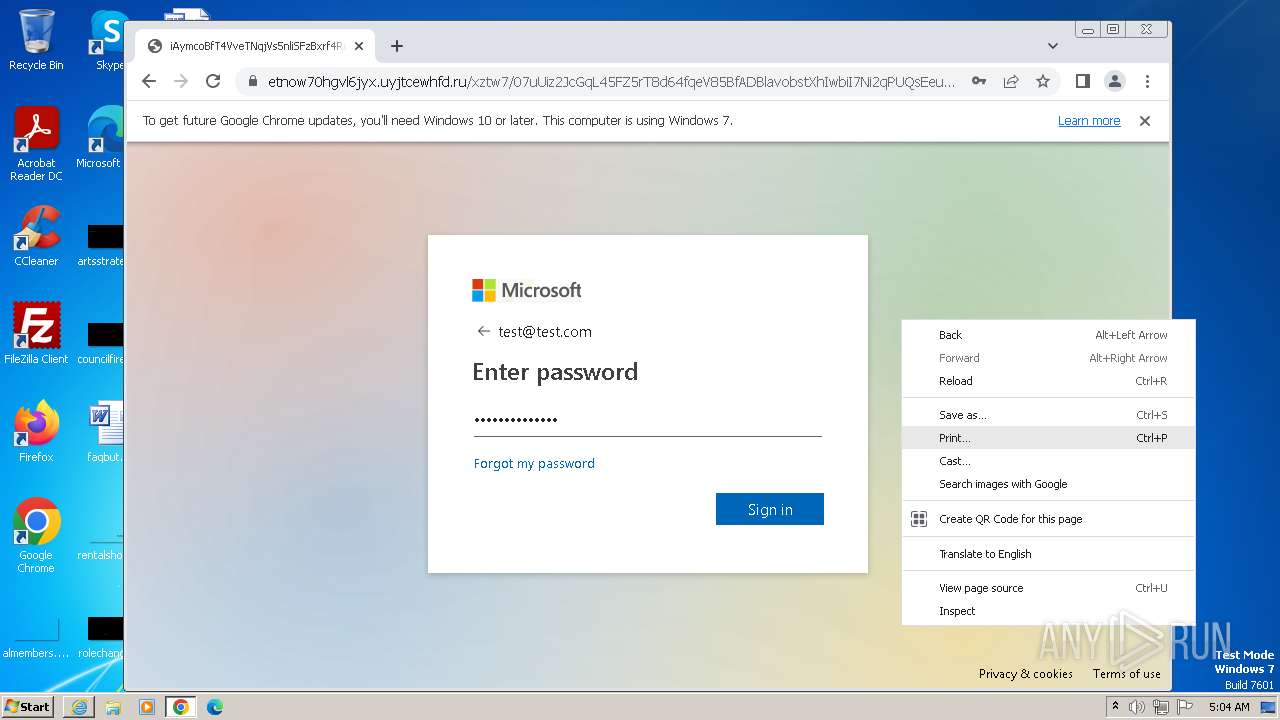
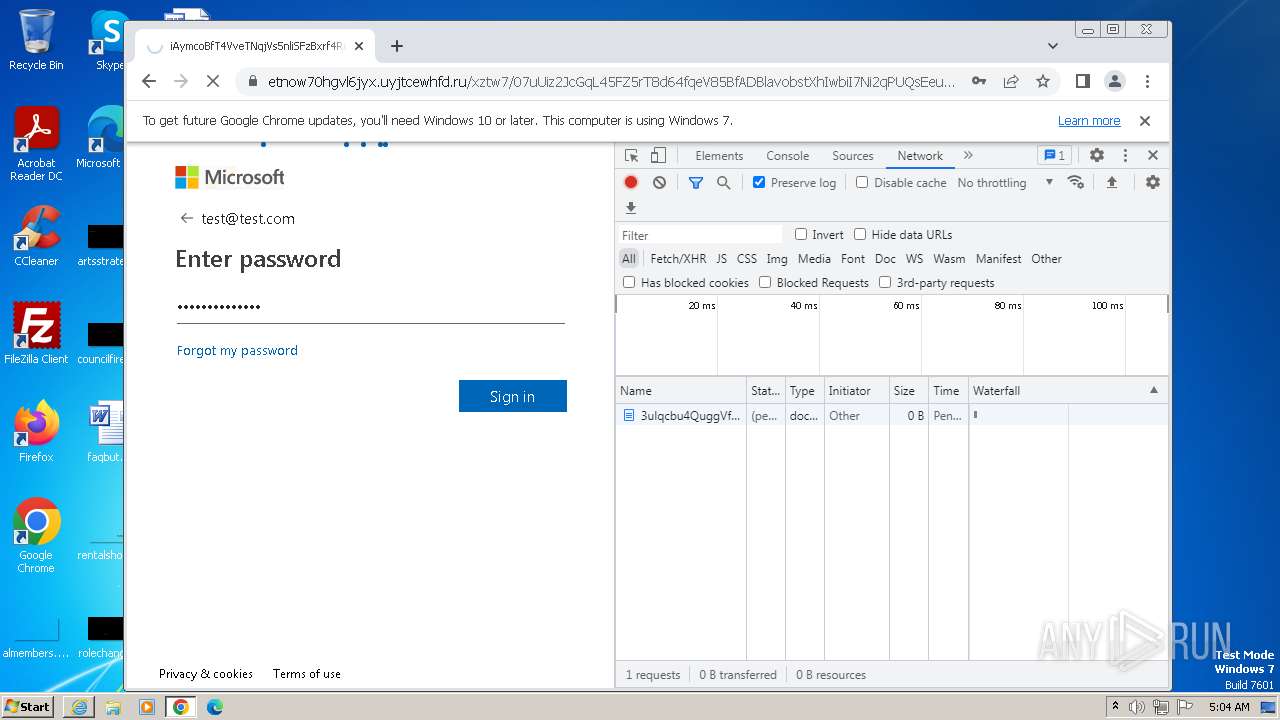
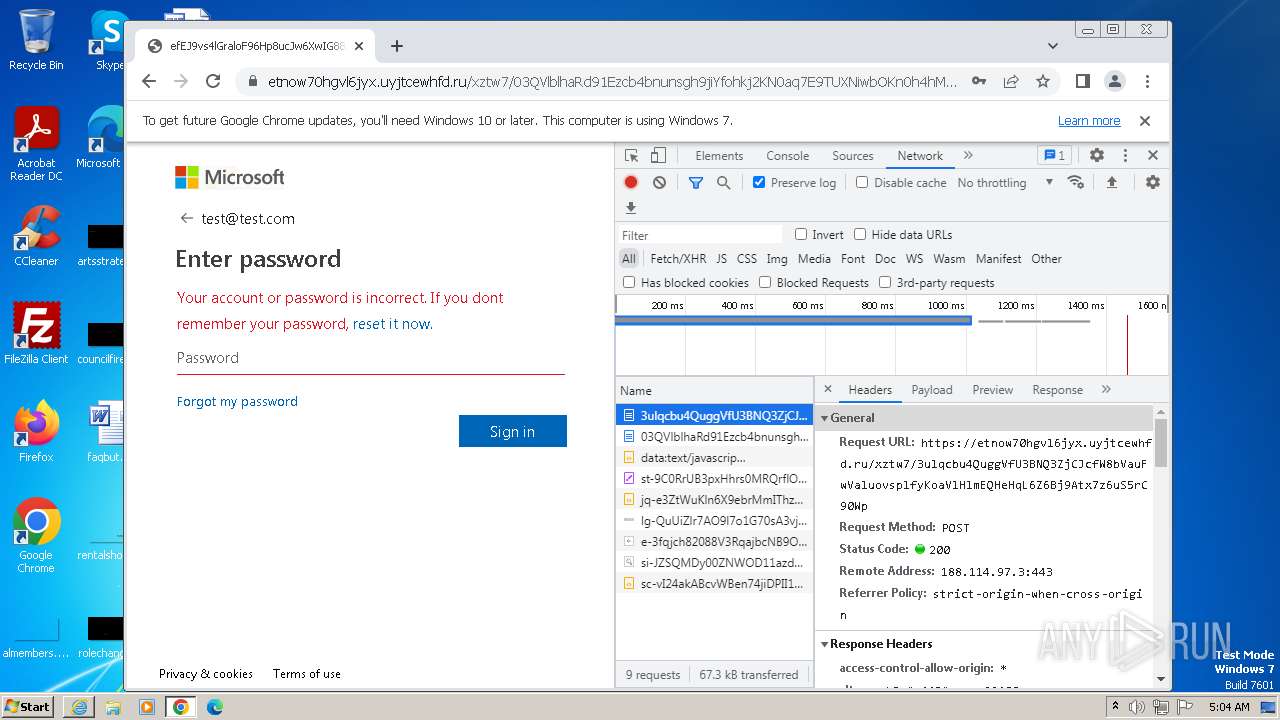
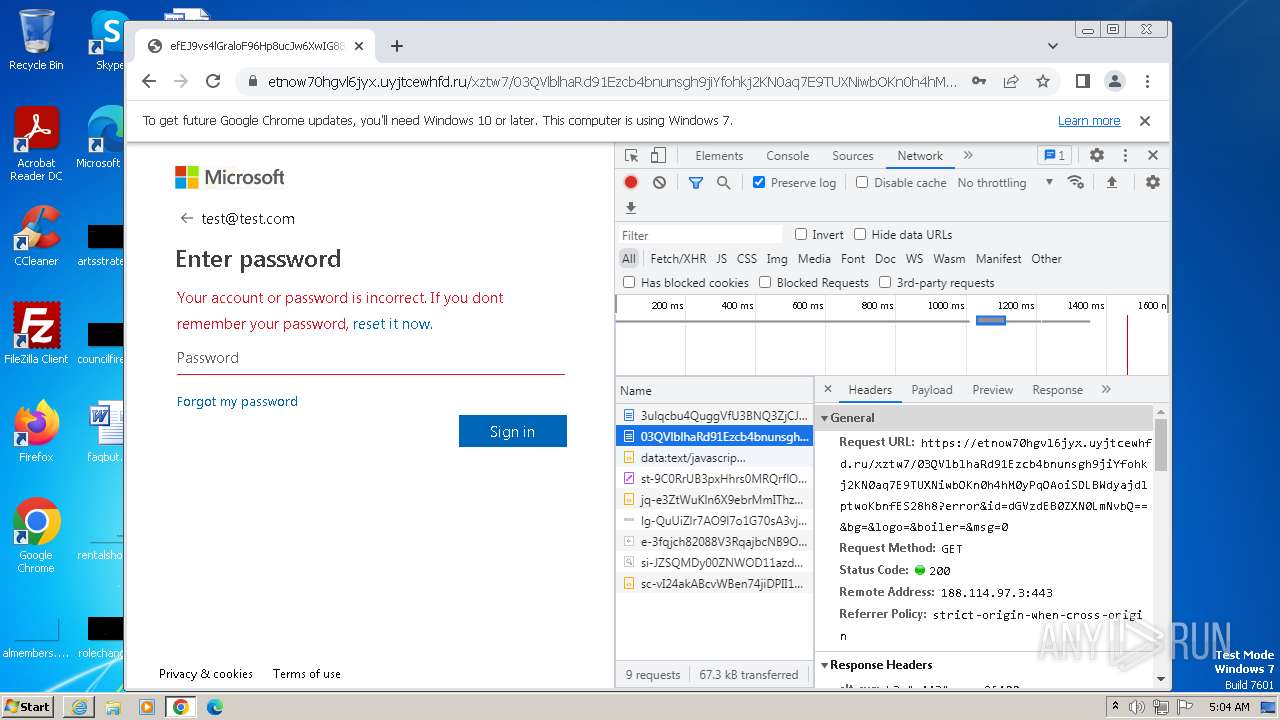
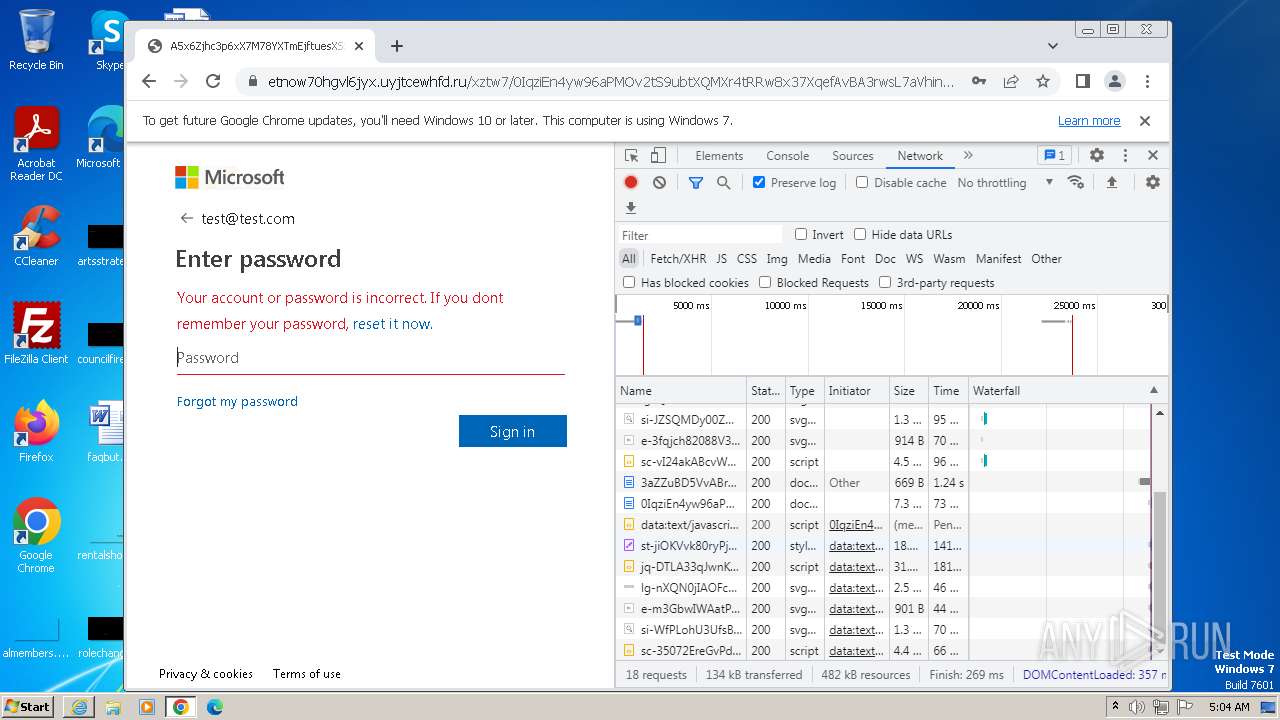
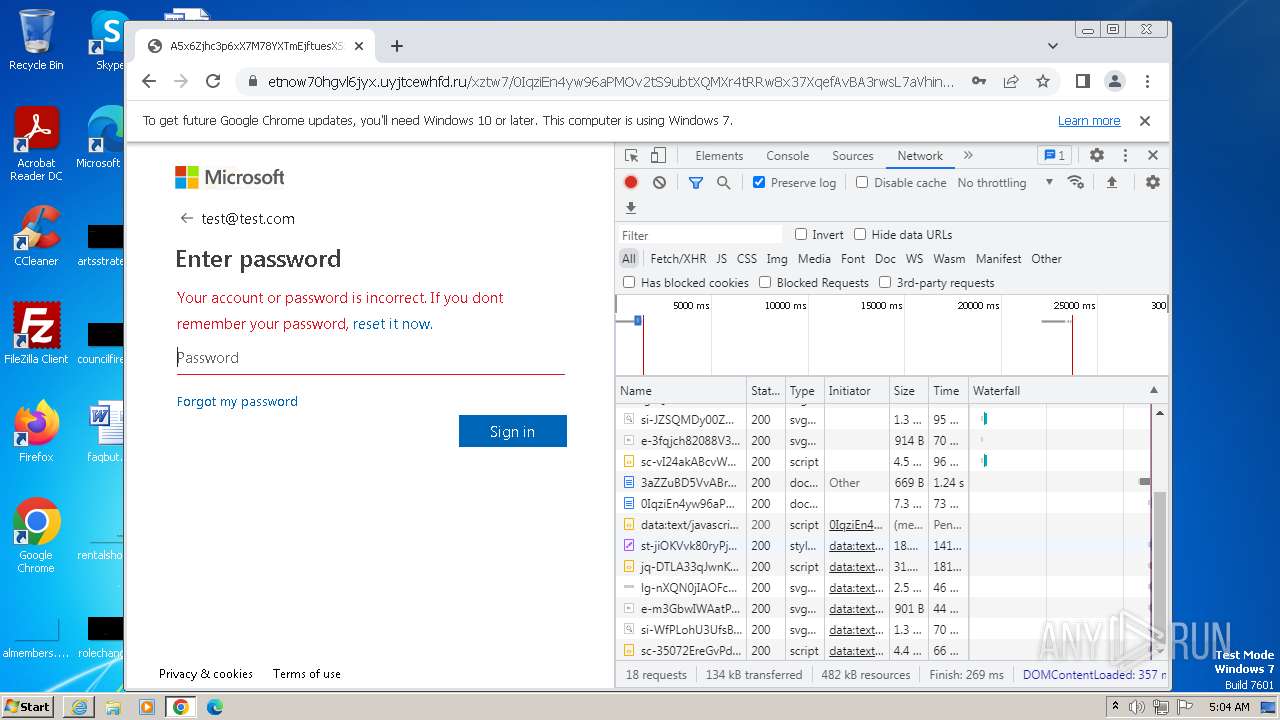
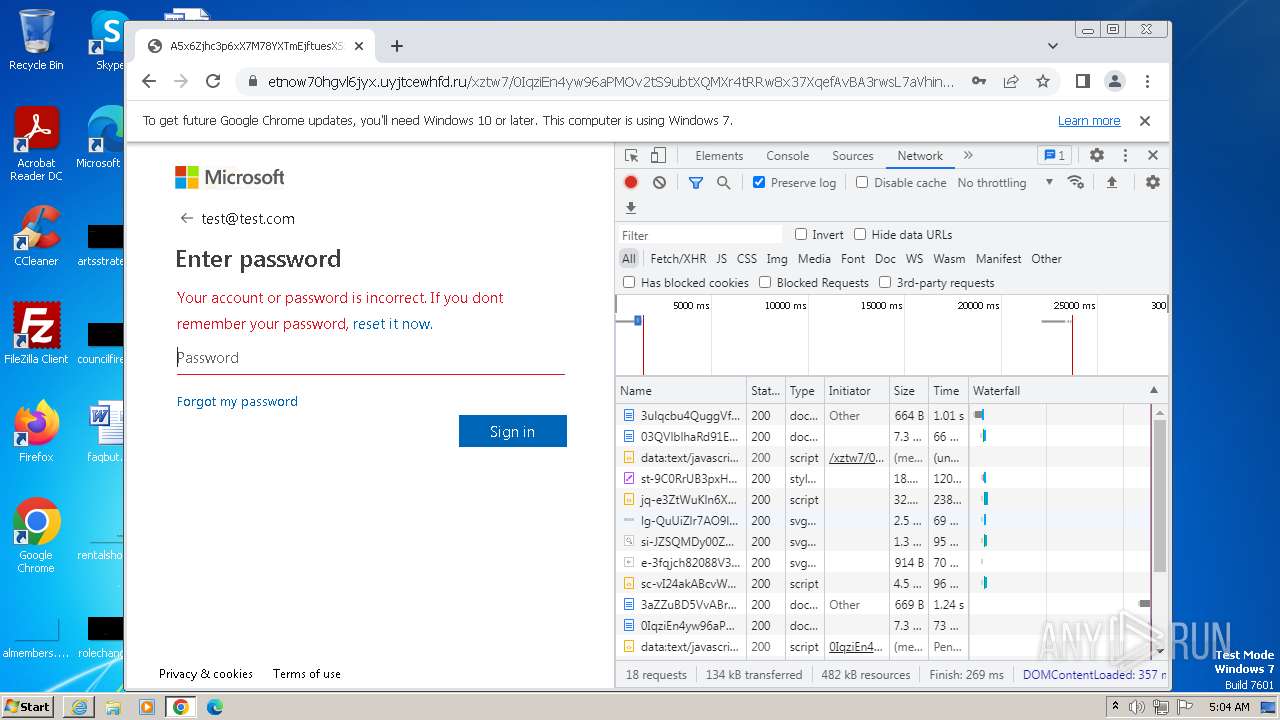
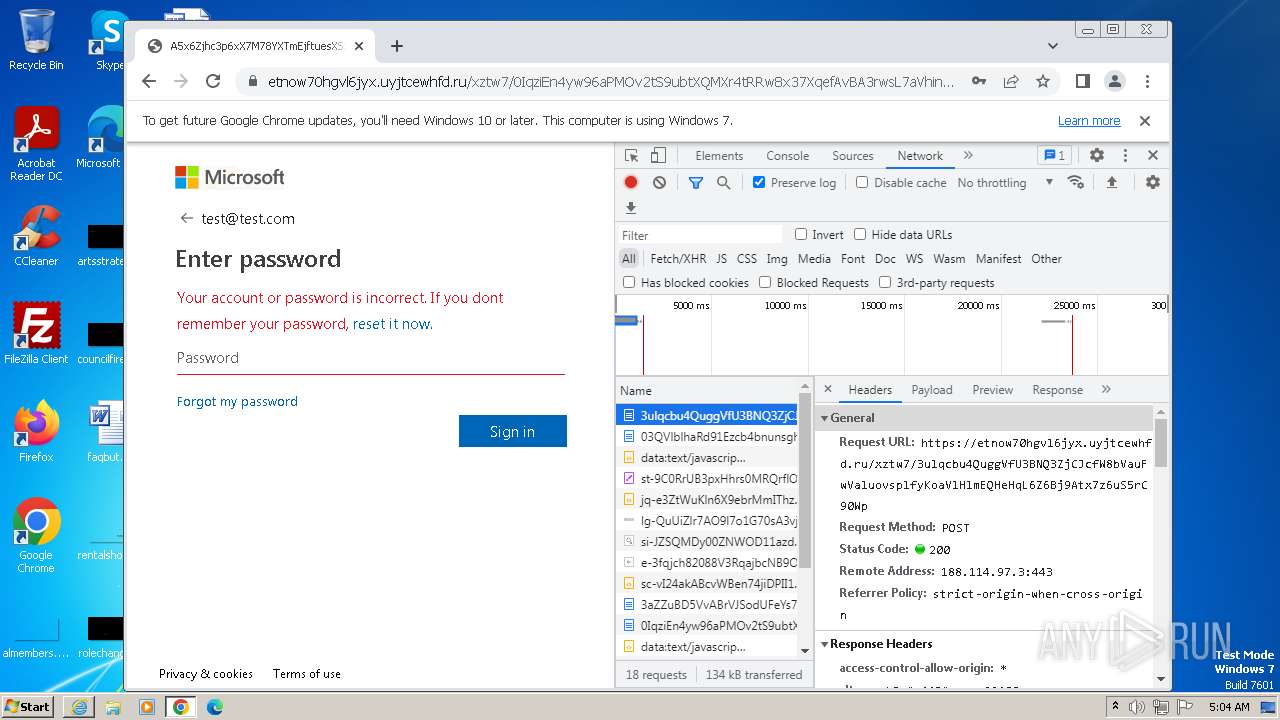
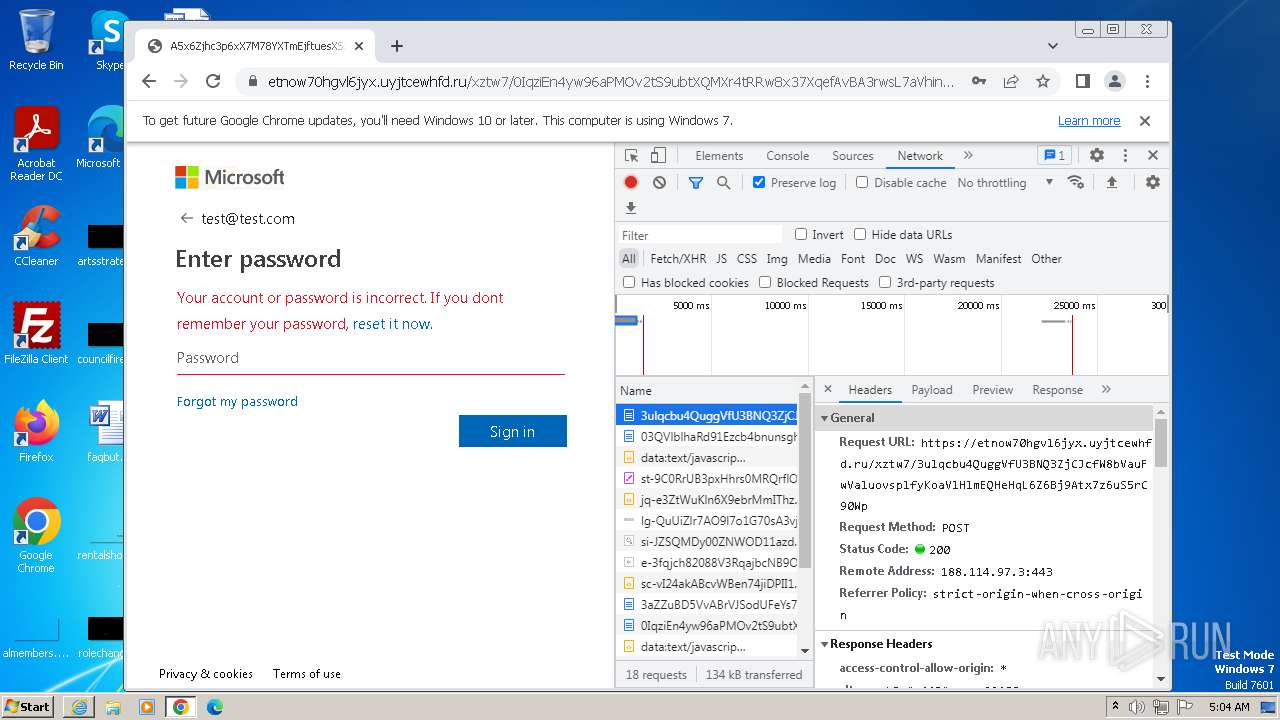
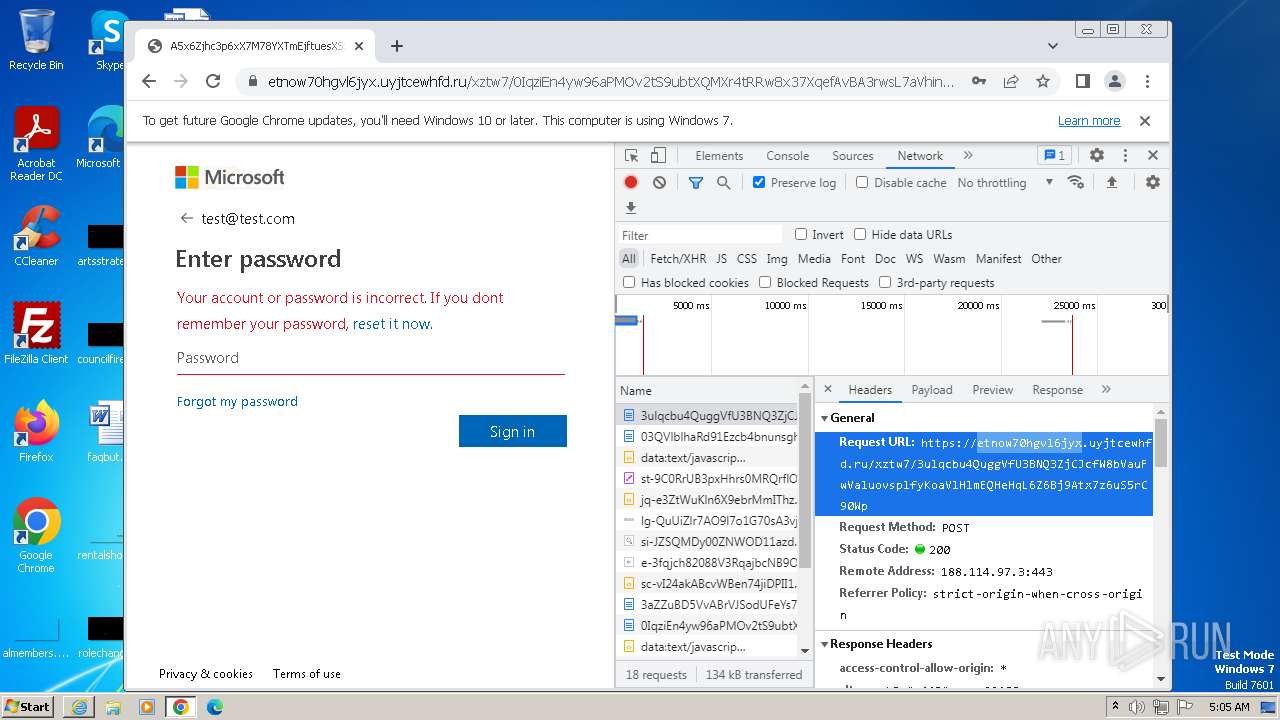
| URL: | https://api-eu.targetx.com/email-interact/redirect?id=MTEwMDAwNTMwIE5vbmUgOTE5MCBUTVNfdGVzdF9yZWNpcGllbnRfaWQ=&link=https%3A%2F%2Fetnow70hgvl6jyx.uyjtcewhfd.ru%2Fxztw7%2F#dGVzdEB0ZXN0LmNvbQ== |
| Full analysis: | https://app.any.run/tasks/c874b98b-6f33-4ae3-81a9-3d2bdaf5d7af |
| Verdict: | Malicious activity |
| Analysis date: | October 31, 2023, 05:03:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| SHA1: | 45C019C6FFFB8B1D56C6B04EABD32F825B9F6CB7 |
| SHA256: | 2CBFA8BCFD9DDE7B4B91A7C8FAA695F676CCD1652C8B83FBB642234DDDCE9D04 |
| SSDEEP: | 3:N8DIBRESARdyX6IMQ3WnYUSrxU26lEY2OGr3cWYNRR8AWCXjZadUeNdLX967jGkY:2JzRg6I13WYG2tGGr32N33z+UeLX96ny |
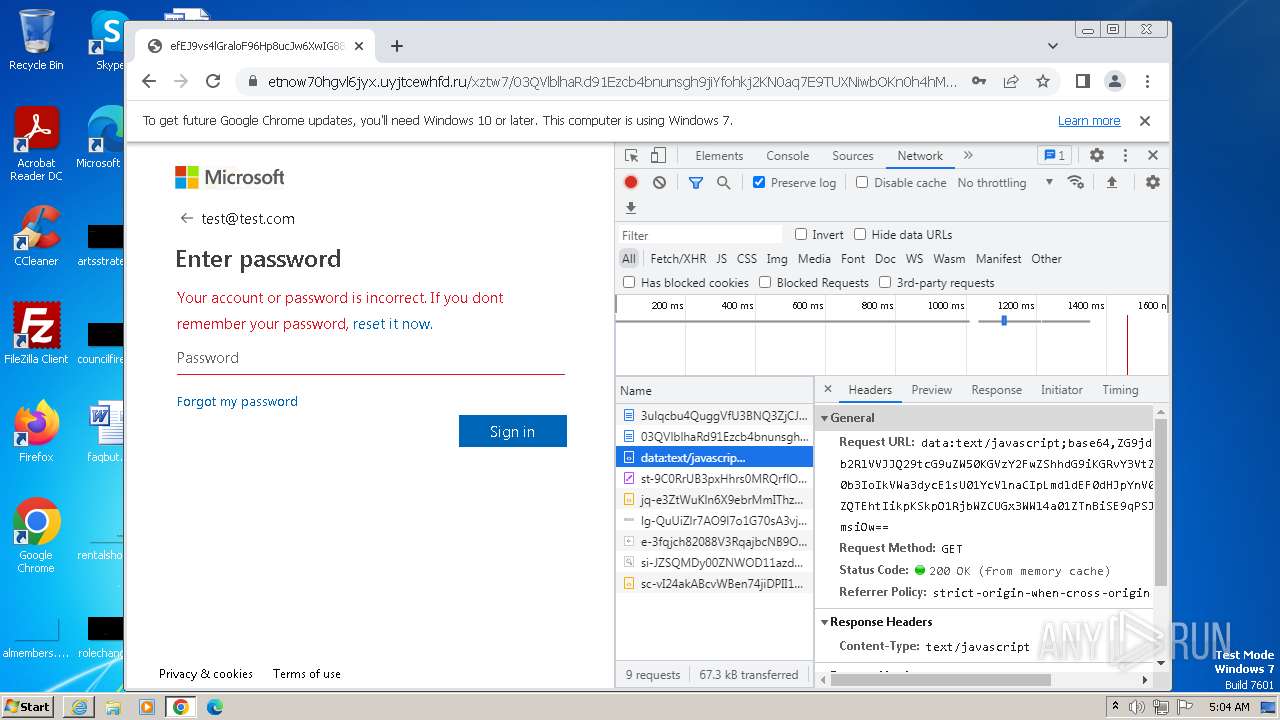
MALICIOUS
PHISHING has been detected (SURICATA)
- chrome.exe (PID: 3756)
- iexplore.exe (PID: 4068)
SUSPICIOUS
No suspicious indicators.INFO
The process uses the downloaded file
- chrome.exe (PID: 1884)
- chrome.exe (PID: 3728)
- chrome.exe (PID: 3648)
Application launched itself
- chrome.exe (PID: 4048)
- iexplore.exe (PID: 2096)
Manual execution by a user
- chrome.exe (PID: 4048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
68
Monitored processes
31
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 460 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1128 --field-trial-handle=1140,i,5900591026300778825,12340102335382775830,131072 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3332 --field-trial-handle=1140,i,5900591026300778825,12340102335382775830,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 632 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=948 --field-trial-handle=1140,i,5900591026300778825,12340102335382775830,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=24 --mojo-platform-channel-handle=4192 --field-trial-handle=1140,i,5900591026300778825,12340102335382775830,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2080 --field-trial-handle=1140,i,5900591026300778825,12340102335382775830,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1484 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=16 --mojo-platform-channel-handle=2340 --field-trial-handle=1140,i,5900591026300778825,12340102335382775830,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1012 --field-trial-handle=1140,i,5900591026300778825,12340102335382775830,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1884 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3112 --field-trial-handle=1140,i,5900591026300778825,12340102335382775830,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://api-eu.targetx.com/email-interact/redirect?id=MTEwMDAwNTMwIE5vbmUgOTE5MCBUTVNfdGVzdF9yZWNpcGllbnRfaWQ=&link=https%3A%2F%2Fetnow70hgvl6jyx.uyjtcewhfd.ru%2Fxztw7%2F#dGVzdEB0ZXN0LmNvbQ==" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1552 --field-trial-handle=1140,i,5900591026300778825,12340102335382775830,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
23 387
Read events
23 221
Write events
161
Delete events
5
Modification events
| (PID) Process: | (2096) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2096) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2096) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2096) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2096) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2096) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2096) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2096) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2096) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2096) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
1
Suspicious files
135
Text files
47
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_056B48C93C4964C2E64C0A8958238656 | binary | |
MD5:44F421BBED1B9B44F674B8015F7AA036 | SHA256:0C5E85BA012C191F05EF0C17B754001A229866005BC9D0077E765FBB2E574998 | |||
| 4068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 4068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:22E6817B73AACE162B2C27DC93AA9673 | SHA256:26745B7B231035CDD99A27E7C9BC7FBE4714F816DE1AB4BED47B747214E538C3 | |||
| 4068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F53EB4E574DE32C870452087D92DBEBB_C75344DC27B732D751A8F7CD87A4C9BA | binary | |
MD5:04D5C21488742CE417FC281AD519BB22 | SHA256:48042ACCFF2BDBA1898578CE05D9BE2BEF7952CE8E8615ABB279081938A05F3A | |||
| 4068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:00A3CCE7AC29337CF45DA36470FB4D37 | SHA256:0D250A736CB3F45AFA8284E0887278D07C5BB2348788AE0AD0A02A348EFAC5E4 | |||
| 4068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_056B48C93C4964C2E64C0A8958238656 | der | |
MD5:0D95215397DFEEB35E975011E1B3E8EA | SHA256:DE4CB600D205C4E3E5289230226361A35BED25B032AC818EDD71AE7FFF332675 | |||
| 4068 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabB94B.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 4068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 4068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F53EB4E574DE32C870452087D92DBEBB_C75344DC27B732D751A8F7CD87A4C9BA | binary | |
MD5:DF0CAF34A447400CA8EDDC2814AD4D85 | SHA256:50C57EC6F87CAA1902A34E898CCA2E2B33720CC1CA920FB06716A7CDC540BD67 | |||
| 4068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:A3E8D3CCAAC19250655FEC85763FB6E1 | SHA256:0273E40270AFDA7DECC5BBC1A1ECF51953262CD0FDD12AEF140E3FE98A1863BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
60
DNS requests
52
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
4068 | iexplore.exe | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
4068 | iexplore.exe | GET | 200 | 8.253.204.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7147a541e8aecbd1 | unknown | compressed | 4.66 Kb | unknown |
4068 | iexplore.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | binary | 1.51 Kb | unknown |
2096 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 6.14 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 10.2 Kb | unknown |
4068 | iexplore.exe | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m02.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRmbQtwnInkvkvr7BNFR%2BS2lTYPjAQUwDFSzVpQw4J8dHHOy%2Bmc%2BXrrguICEAHnPSv99GjdKpTqE3Tuw84%3D | unknown | binary | 471 b | unknown |
4068 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
2096 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4068 | iexplore.exe | 8.253.204.120:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4068 | iexplore.exe | 108.138.2.10:80 | o.ss2.us | AMAZON-02 | US | unknown |
4068 | iexplore.exe | 18.66.142.79:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | unknown |
4068 | iexplore.exe | 18.245.65.219:80 | ocsp.r2m02.amazontrust.com | — | US | unknown |
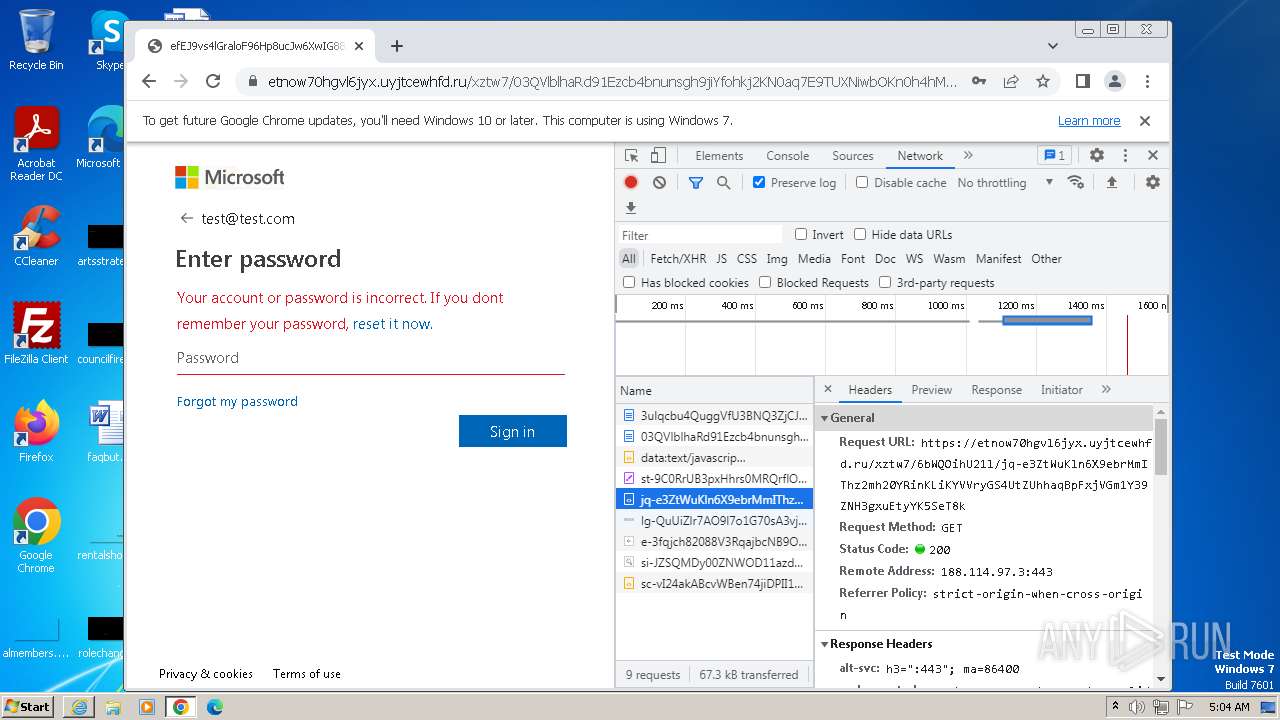
4068 | iexplore.exe | 188.114.97.3:443 | etnow70hgvl6jyx.uyjtcewhfd.ru | CLOUDFLARENET | NL | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4068 | iexplore.exe | 23.212.210.158:80 | x1.c.lencr.org | AKAMAI-AS | AU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m02.amazontrust.com |
| whitelisted |
etnow70hgvl6jyx.uyjtcewhfd.ru |
| unknown |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4068 | iexplore.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] A phishing domain chain was detected (DadSec) |
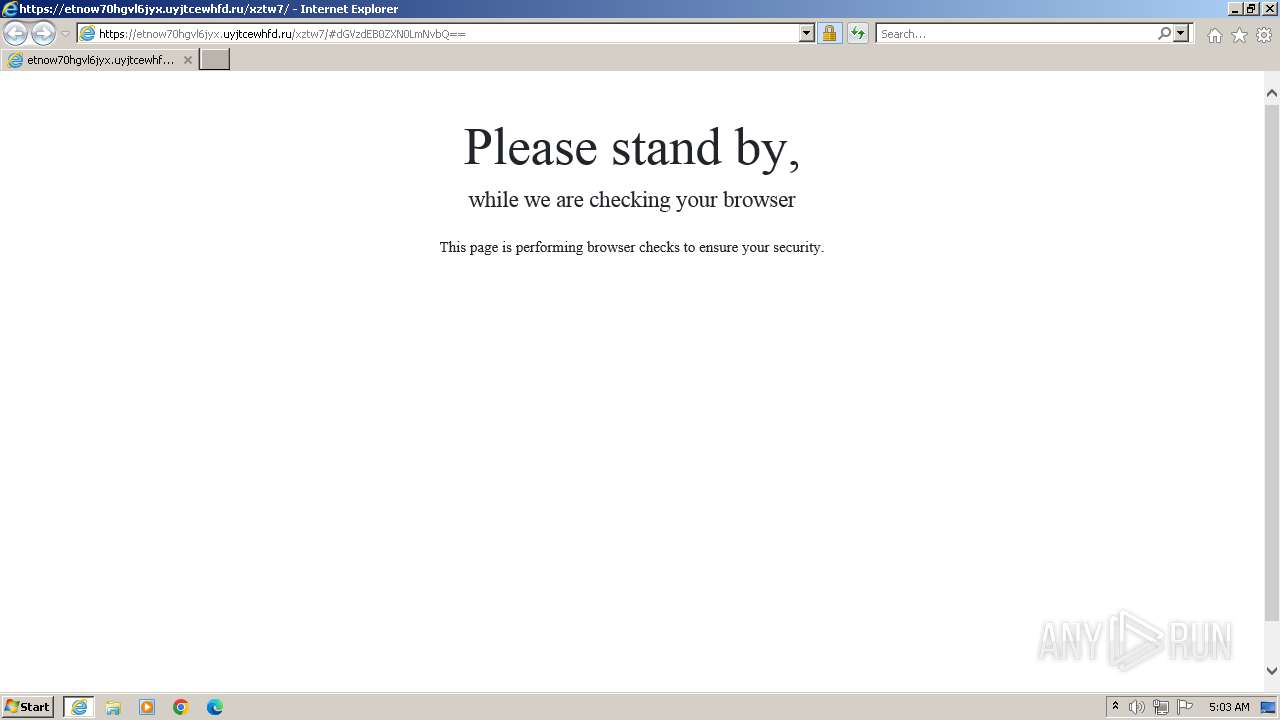
4068 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
4068 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
3756 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] A phishing domain chain was detected (DadSec) |
3756 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
3756 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
3756 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |