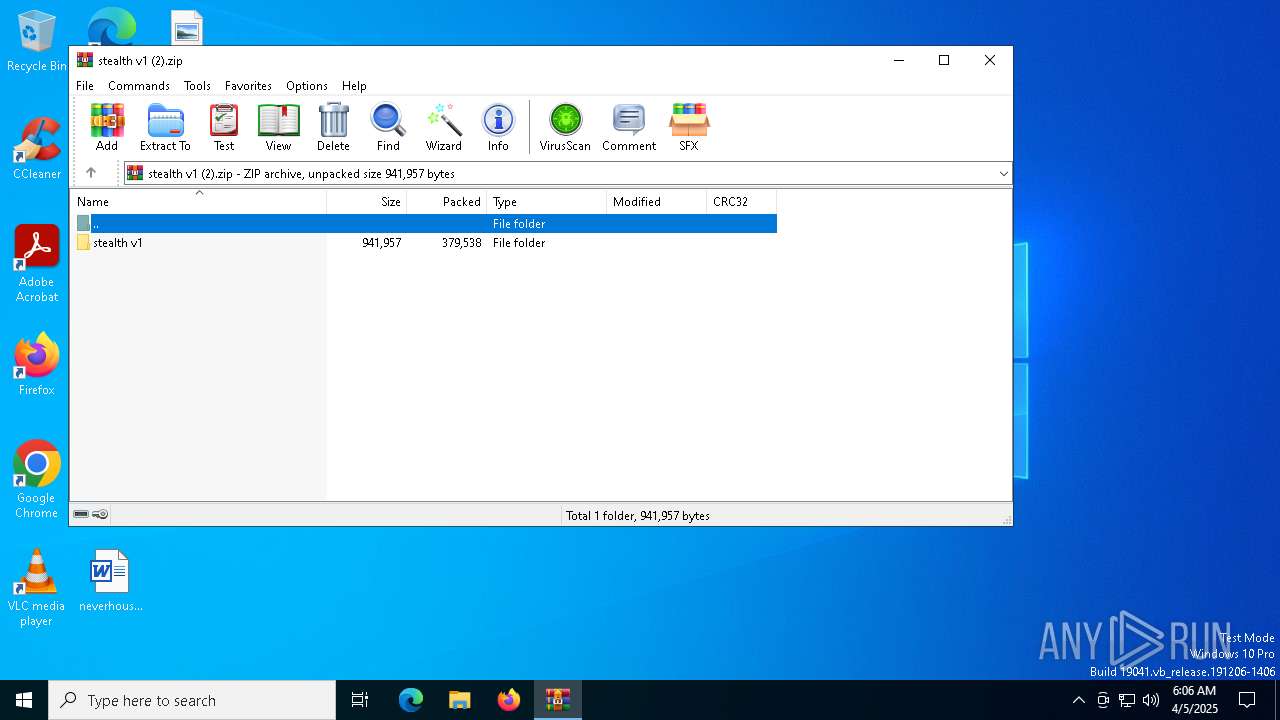
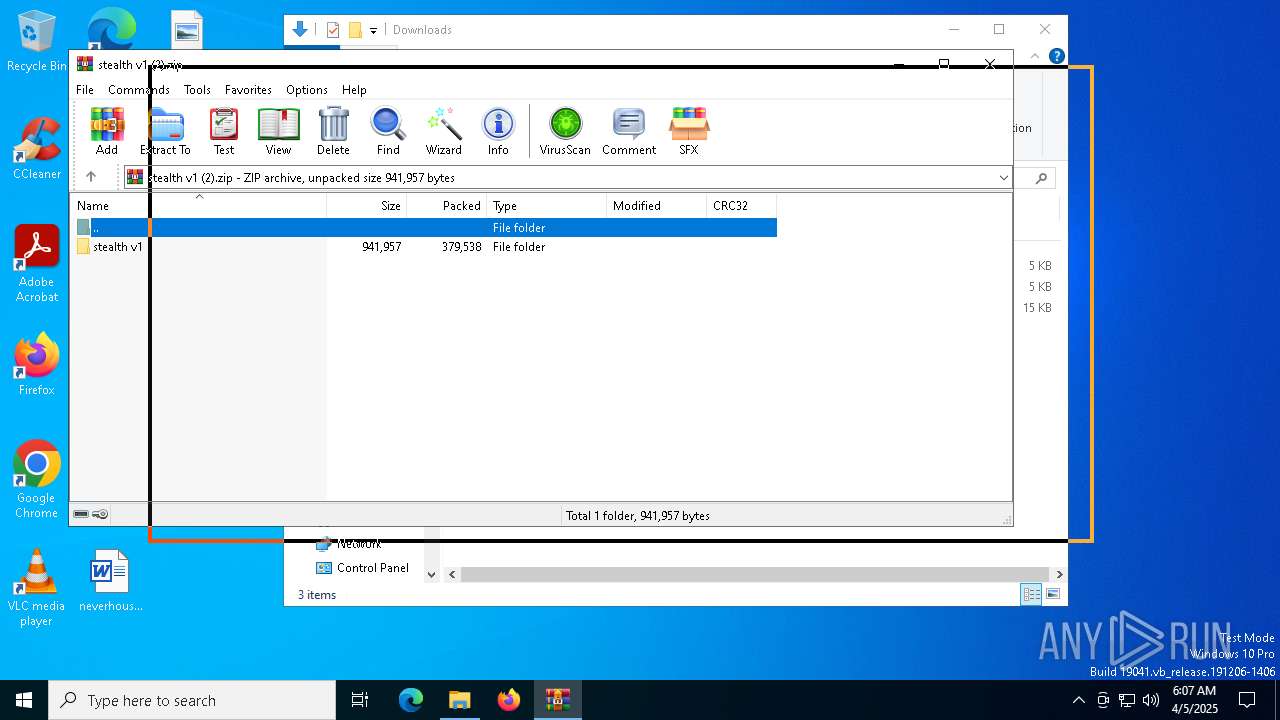
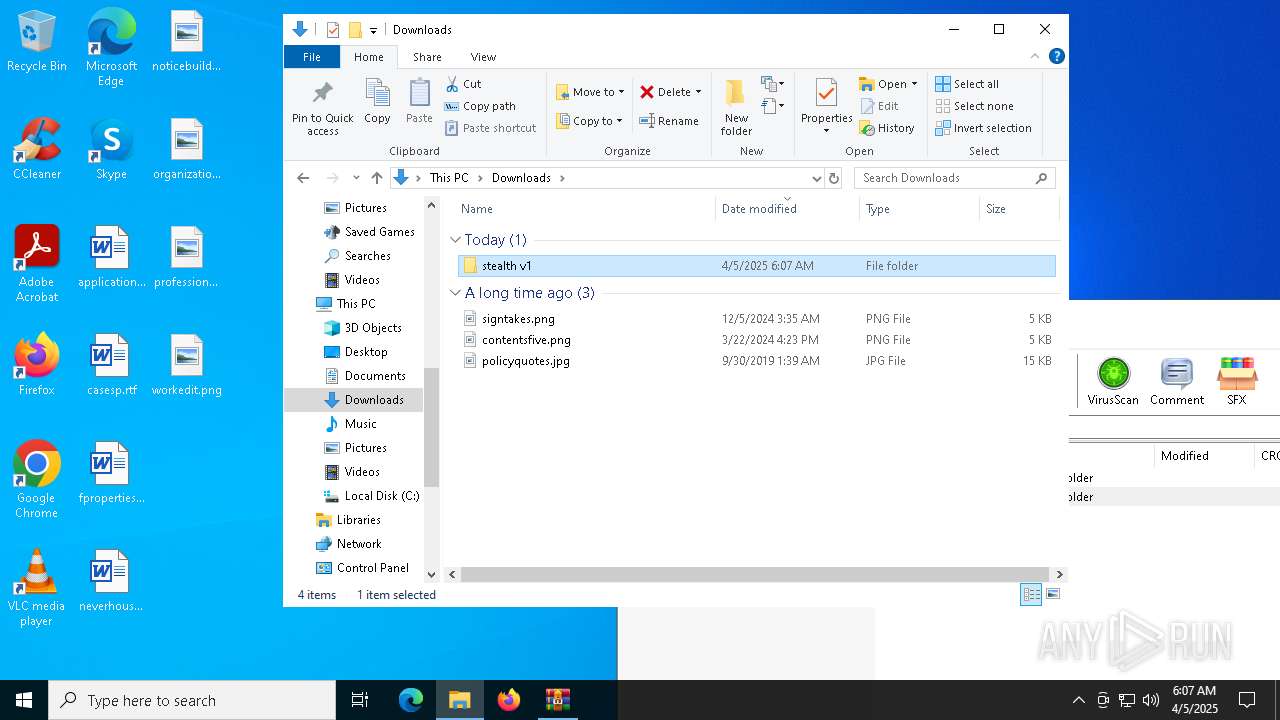
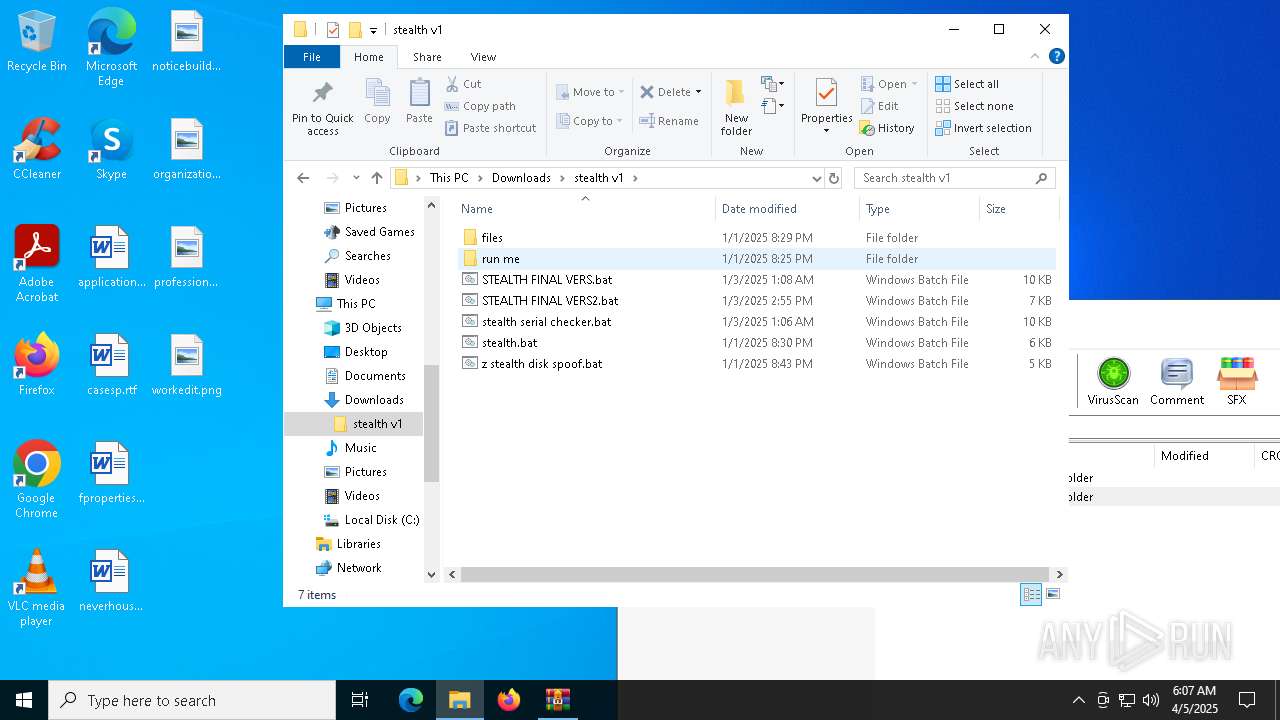
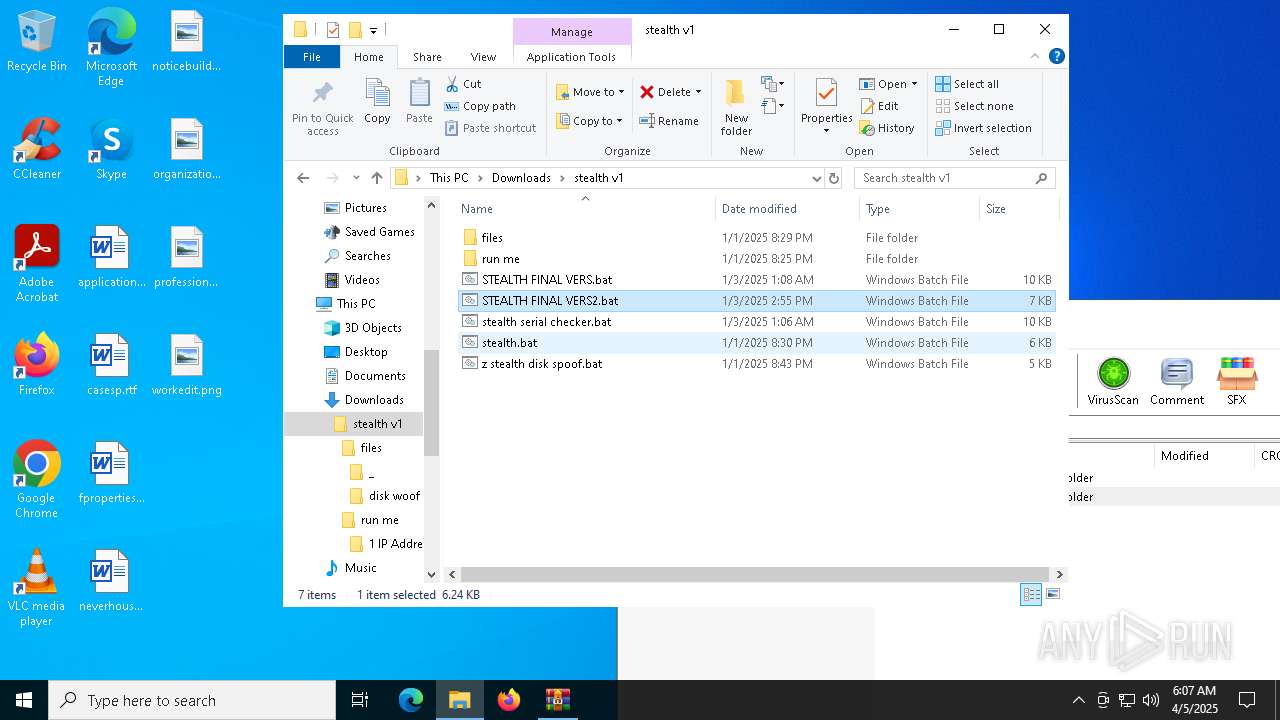
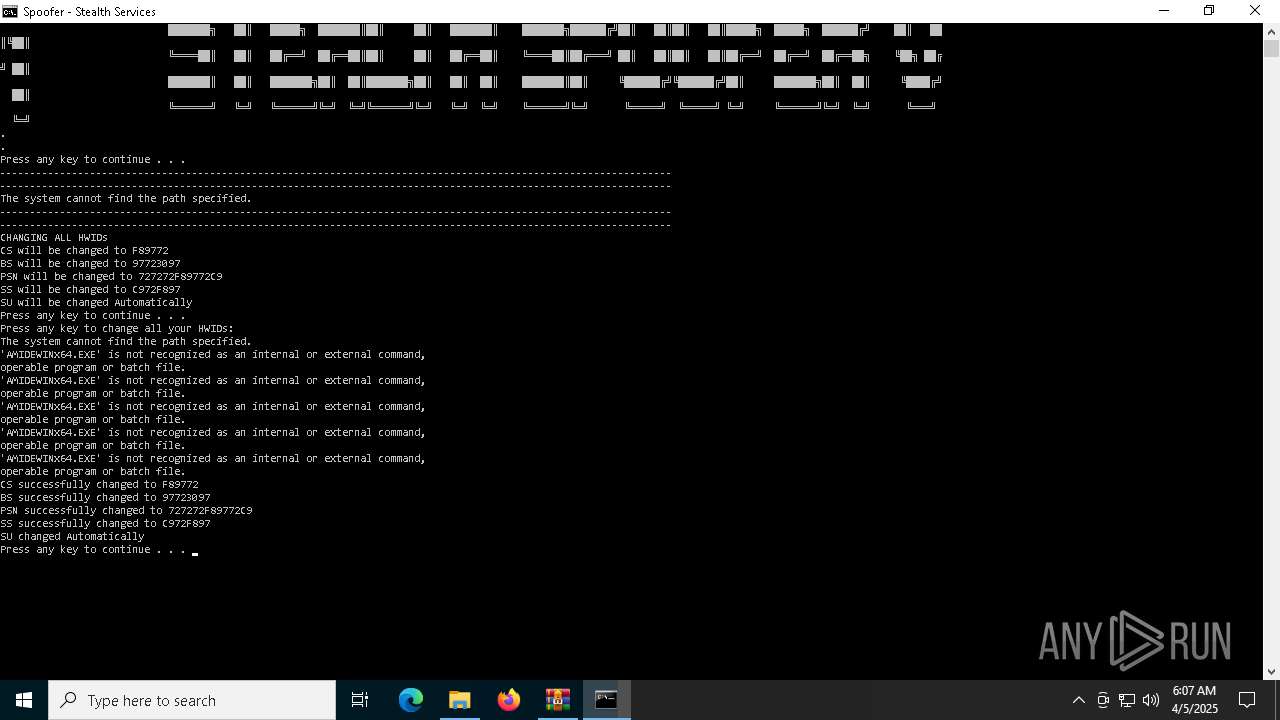
| File name: | stealth v1 (2).zip |
| Full analysis: | https://app.any.run/tasks/b44a0fa9-c941-414a-a1fb-b525f61f8e8e |
| Verdict: | Malicious activity |
| Analysis date: | April 05, 2025, 06:06:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 7E61119C1713A459042893F0F13C574B |
| SHA1: | 0B6B8DEDAFDD9C080A4DE3D9BE41EB81692EAA61 |
| SHA256: | 2CAA3668B51EBAD7FF037EB2C8DEEBE1B89E2DD486DC8D87037864EDBA264B96 |
| SSDEEP: | 12288:XOTCKkZi3TRBpE5vIbEcUDO0DNxNhGJbiHYfcs1HDyHtBkc:+OKkZi3TRBpE5AbEcUi0DNxPoO4fcs1k |
MALICIOUS
Vulnerable driver has been detected
- WinRAR.exe (PID: 3020)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 3020)
Application launched itself
- cmd.exe (PID: 4812)
Starts application with an unusual extension
- cmd.exe (PID: 4812)
- cmd.exe (PID: 6540)
- cmd.exe (PID: 5392)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4812)
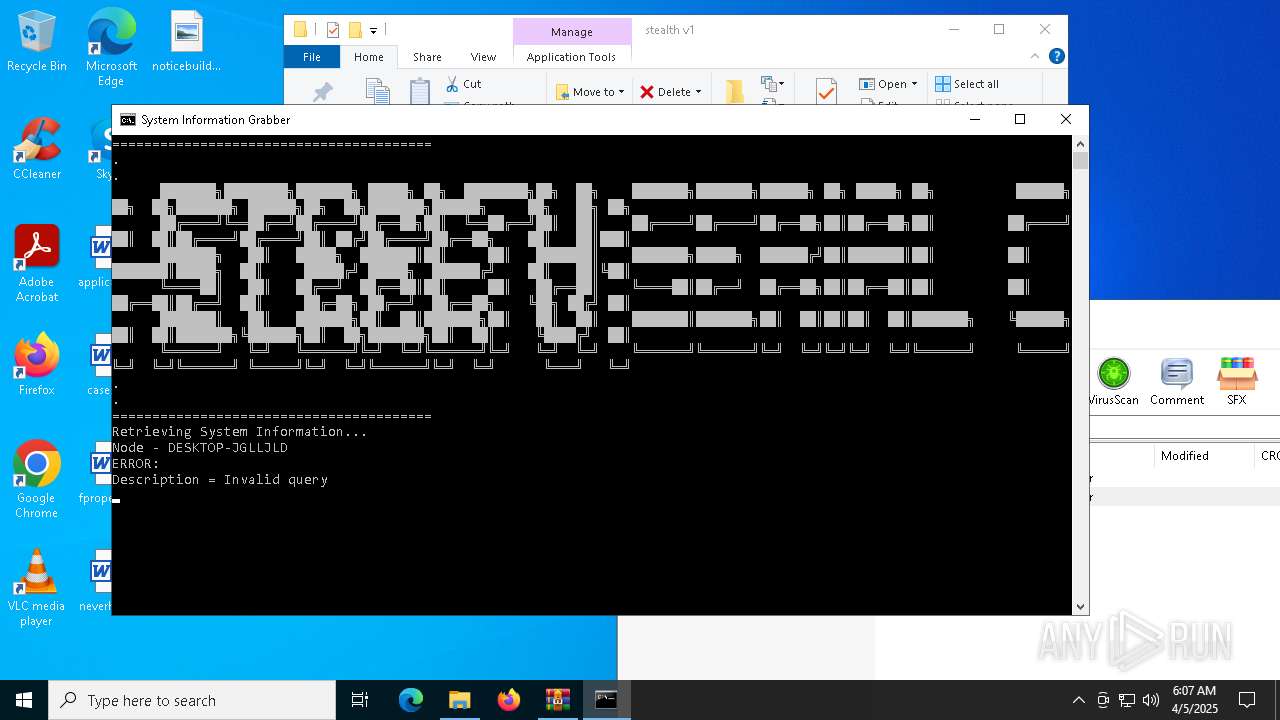
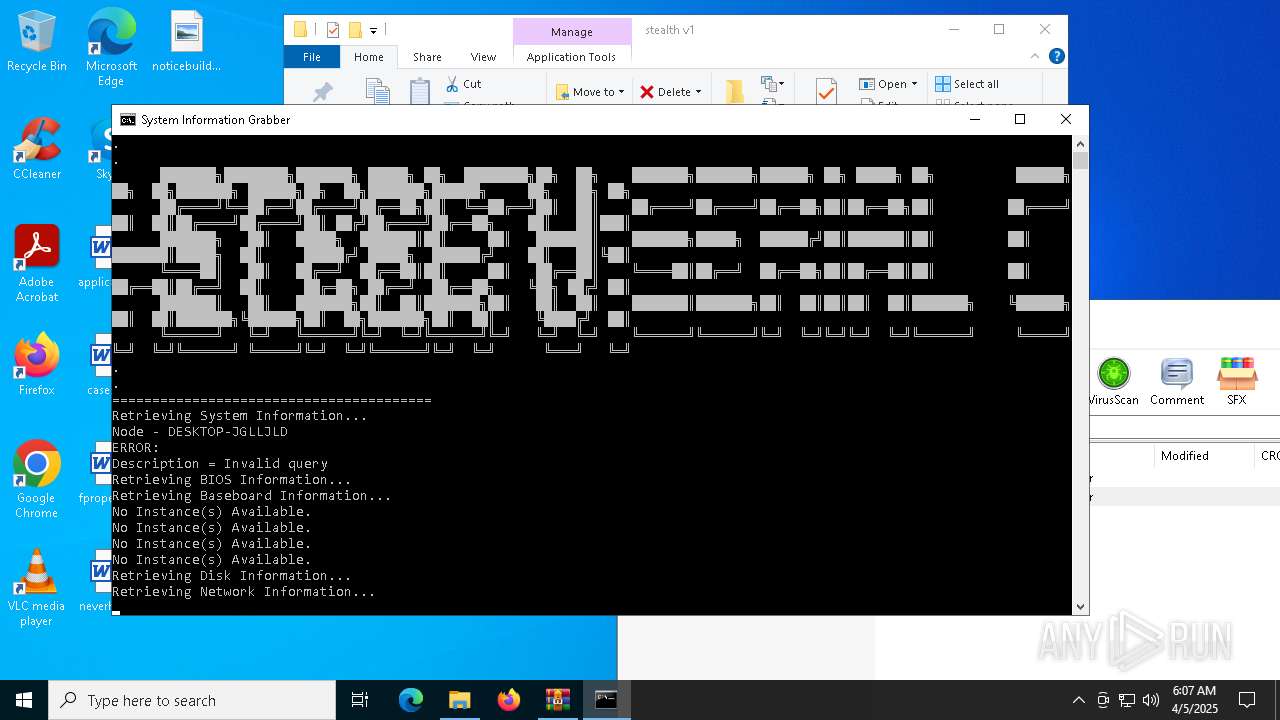
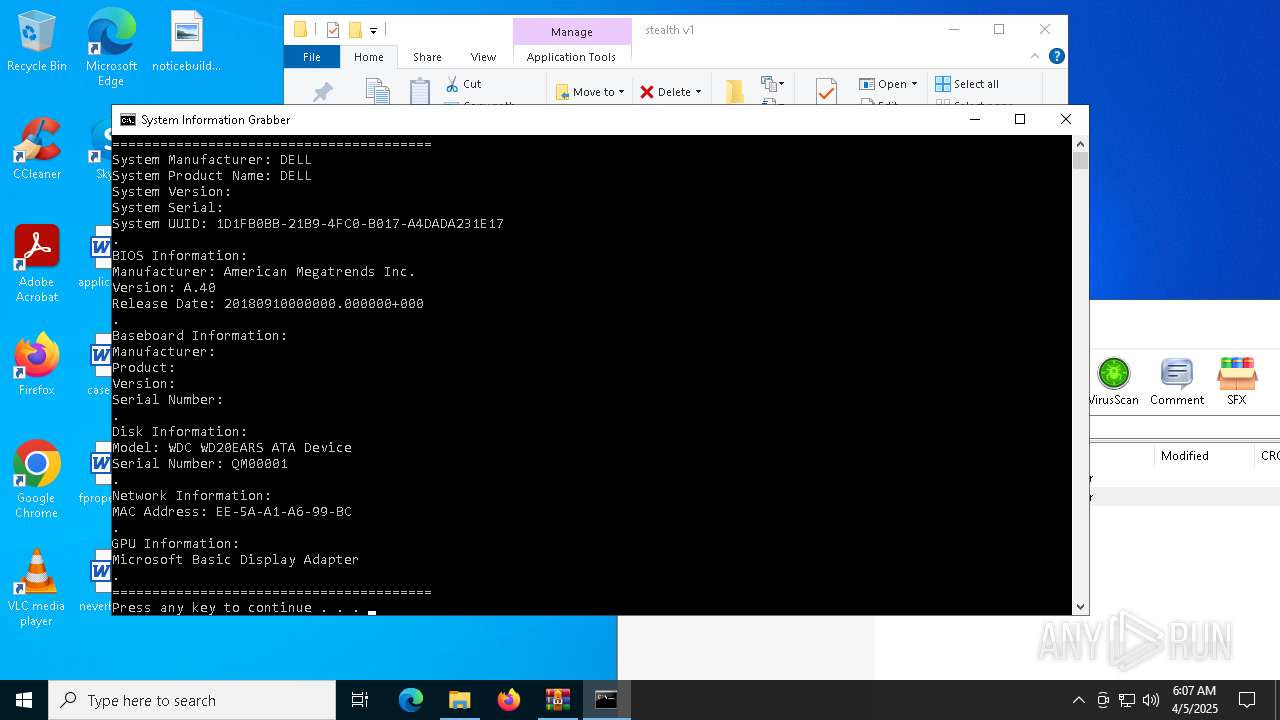
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6244)
- cmd.exe (PID: 6080)
- cmd.exe (PID: 664)
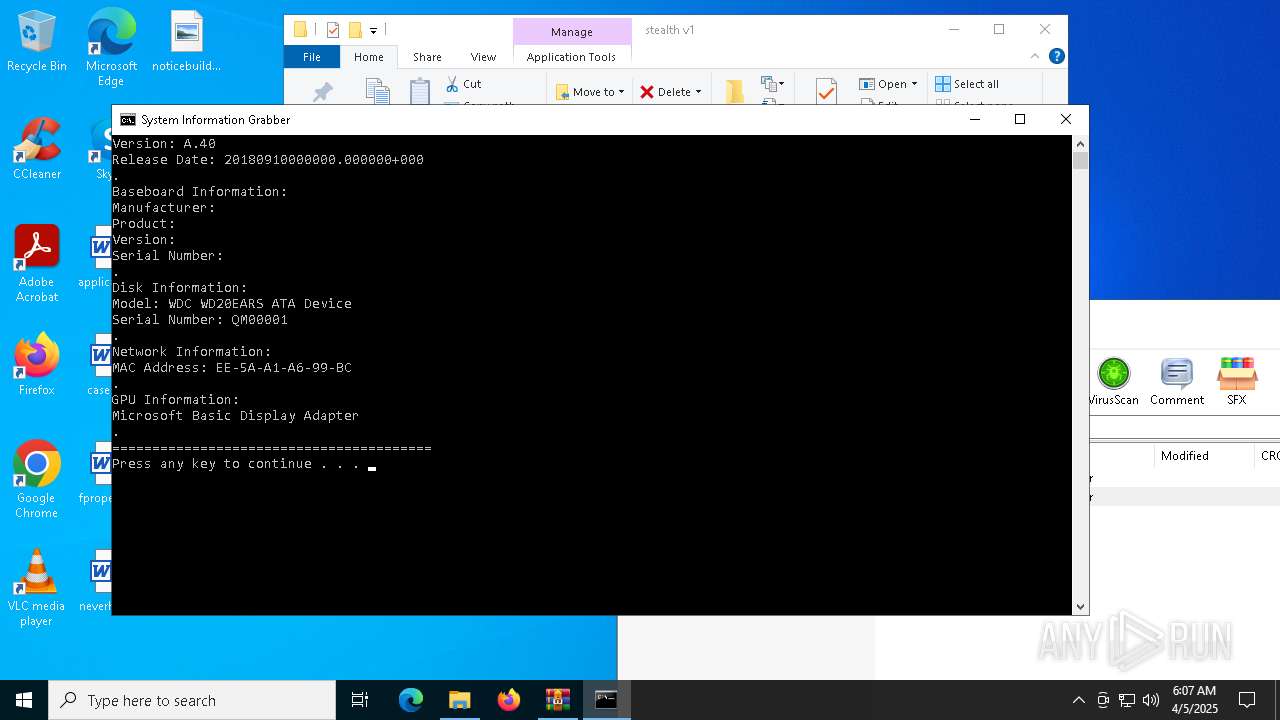
Uses WMIC.EXE to obtain BIOS management information
- cmd.exe (PID: 4756)
- cmd.exe (PID: 6828)
- cmd.exe (PID: 3268)
- cmd.exe (PID: 1512)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6740)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 5156)
- cmd.exe (PID: 2288)
- cmd.exe (PID: 5800)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 4188)
- cmd.exe (PID: 668)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 6736)
INFO
Manual execution by a user
- cmd.exe (PID: 4812)
- cmd.exe (PID: 6540)
- cmd.exe (PID: 5392)
- AMIDEWINx64.EXE (PID: 5936)
- AMIDEWINx64.EXE (PID: 5400)
The sample compiled with english language support
- WinRAR.exe (PID: 3020)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3020)
Changes the display of characters in the console
- cmd.exe (PID: 4812)
- cmd.exe (PID: 6540)
- cmd.exe (PID: 5392)
Checks supported languages
- chcp.com (PID: 4068)
- chcp.com (PID: 5136)
- chcp.com (PID: 864)
- AMIDEWINx64.EXE (PID: 5400)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1012)
- WMIC.exe (PID: 1240)
- WMIC.exe (PID: 616)
- WMIC.exe (PID: 2644)
- WMIC.exe (PID: 5212)
- WMIC.exe (PID: 6540)
- WMIC.exe (PID: 5136)
- WMIC.exe (PID: 1312)
- WMIC.exe (PID: 5116)
- WMIC.exe (PID: 5936)
- WMIC.exe (PID: 5588)
- WMIC.exe (PID: 1012)
- WMIC.exe (PID: 4944)
- WMIC.exe (PID: 3884)
- WMIC.exe (PID: 1240)
Reads the software policy settings
- slui.exe (PID: 2852)
Reads the computer name
- AMIDEWINx64.EXE (PID: 5400)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:01 20:29:28 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | stealth v1/files/ |
Total processes
178
Monitored processes
50
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | wmic computersystem get version /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749911 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | getmac /fo csv /nh | C:\Windows\System32\getmac.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Displays NIC MAC information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | C:\WINDOWS\system32\cmd.exe /c wmic computersystem get version /value | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2147749911 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | C:\WINDOWS\system32\cmd.exe /c wmic diskdrive get serialnumber /value | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | wmic computersystem get manufacturer /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | wmic diskdrive get model /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | wmic computersystem get model /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | wmic diskdrive get serialnumber /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 257
Read events
5 249
Write events
8
Delete events
0
Modification events
| (PID) Process: | (3020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\stealth v1 (2).zip | |||
| (PID) Process: | (3020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
2
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
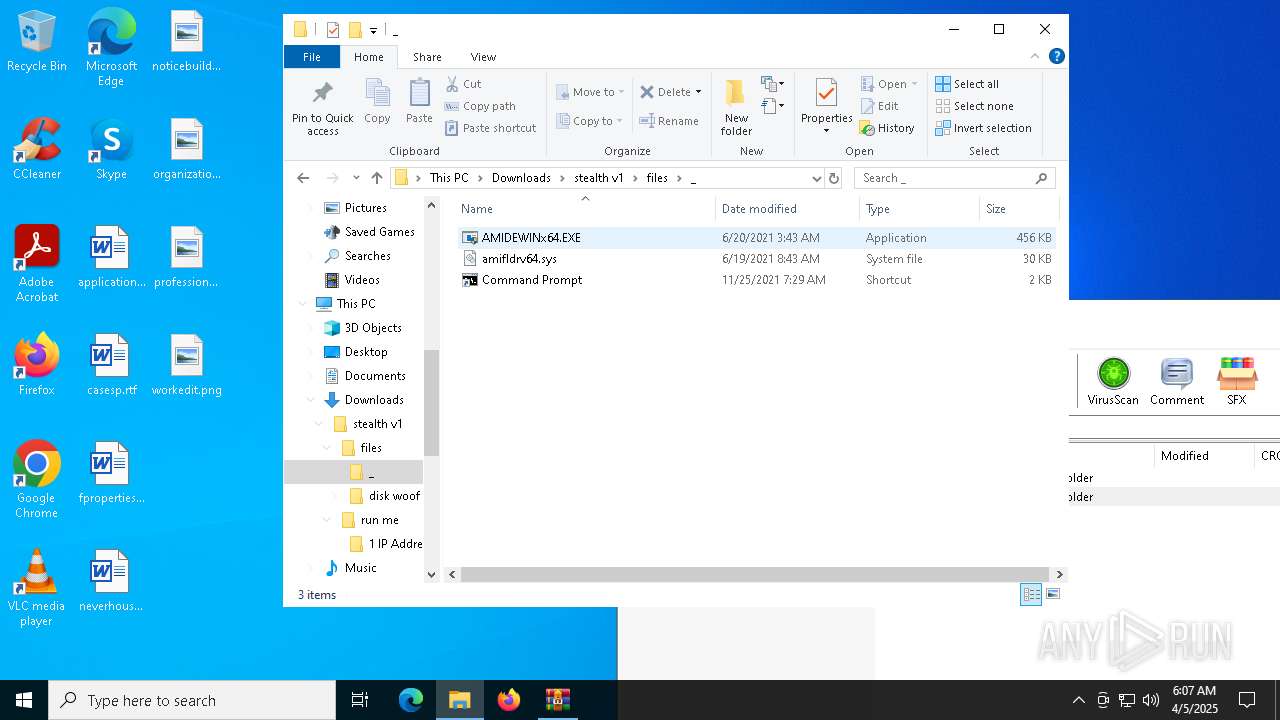
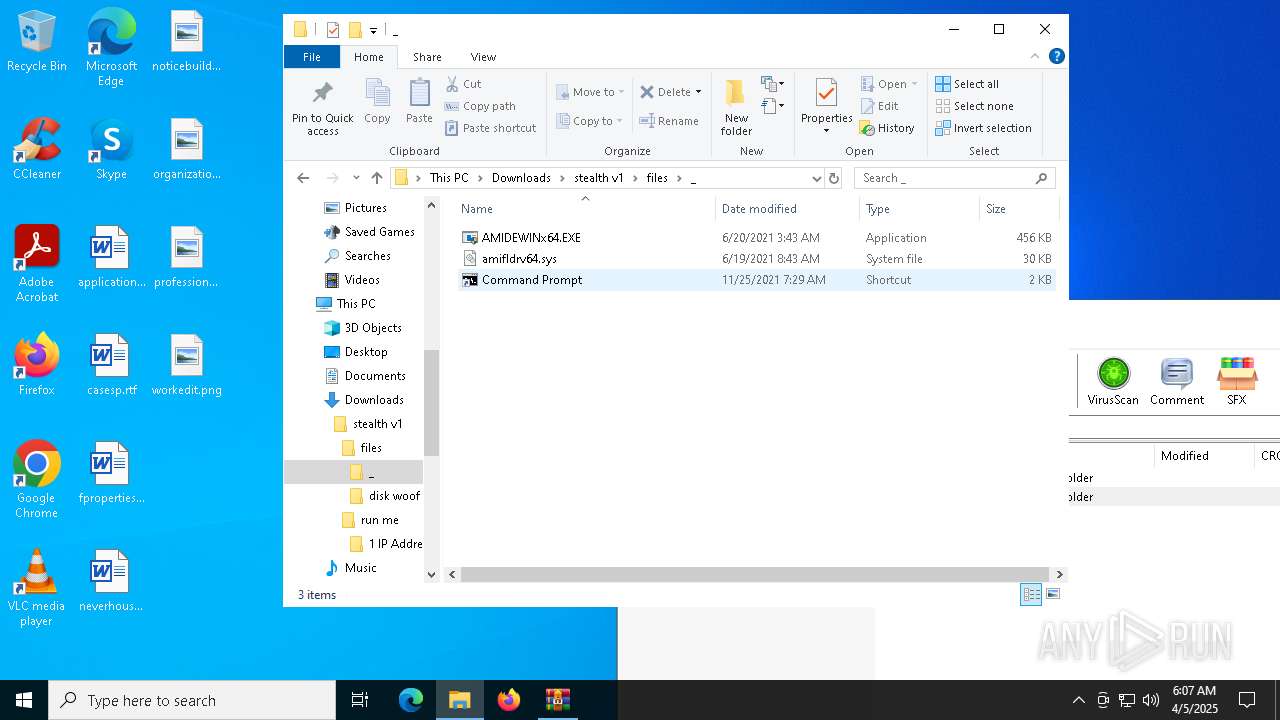
| 3020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3020.4024\stealth v1\files\_\amifldrv64.sys | executable | |
MD5:F22740BA54A400FD2BE7690BB204AA08 | SHA256:65C26276CADDA7A36F8977D1D01120EDB5C3418BE2317D501761092D5F9916C9 | |||
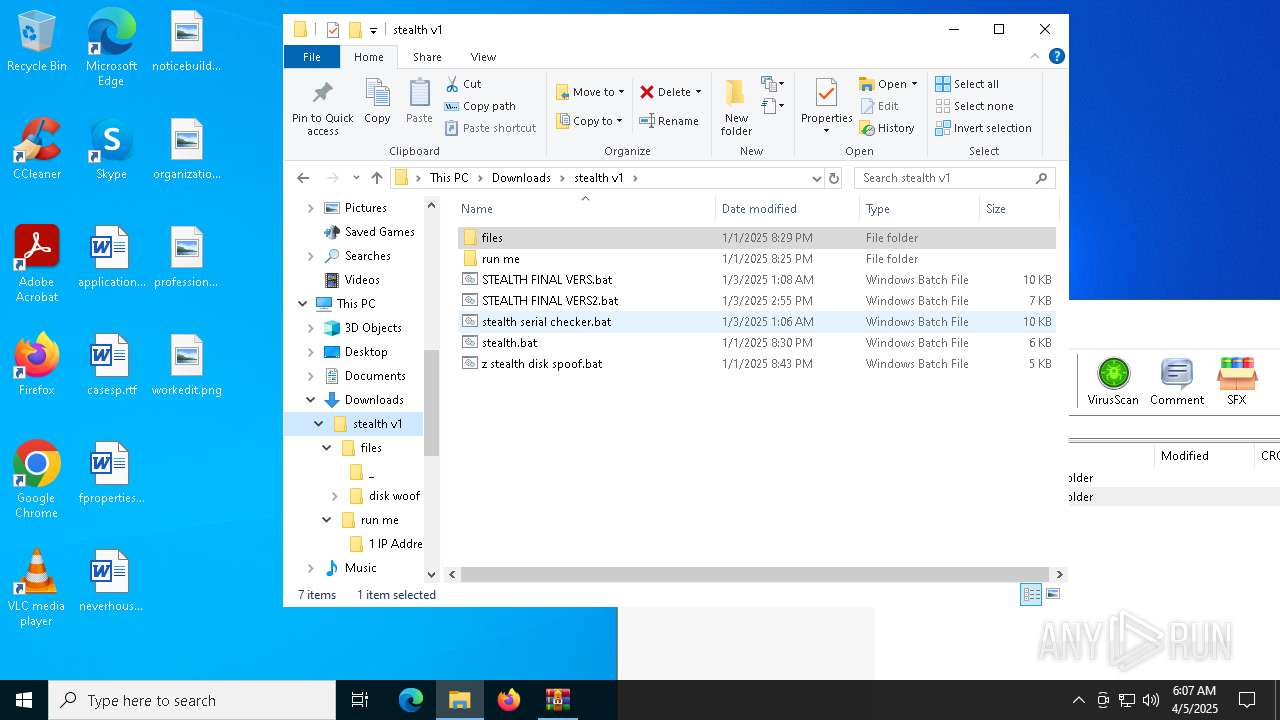
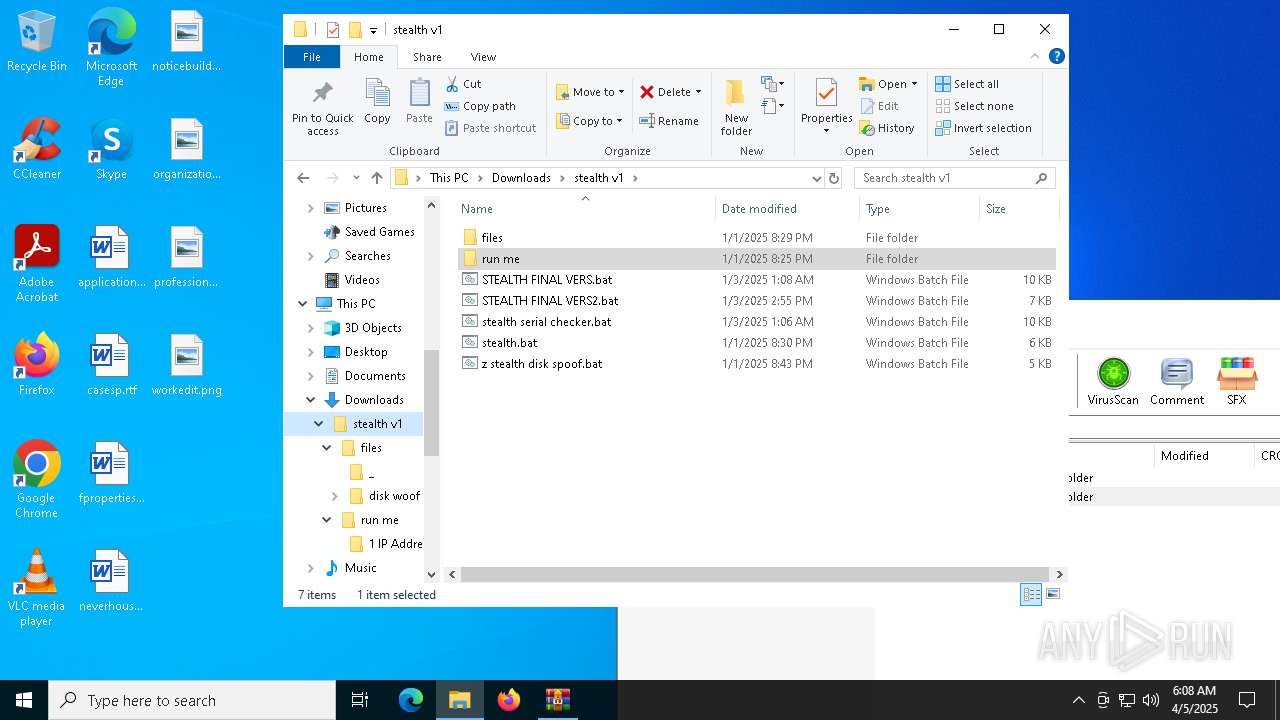
| 3020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3020.4024\stealth v1\stealth serial checker.bat | text | |
MD5:26CF27E74C3F144513F0EA50D8F2BE23 | SHA256:FD7D0F9714033A3F15BA5DE410B45881A3F7B78DF3A643D9F10E90CECE8B2918 | |||
| 3020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3020.4024\stealth v1\stealth.bat | text | |
MD5:07062B73AC1F411B8BC342E6A9CC6A97 | SHA256:715FD6F7BB5E762E5BC5F341A0C04870C5CA4D30A7F6201508733032F4B64411 | |||
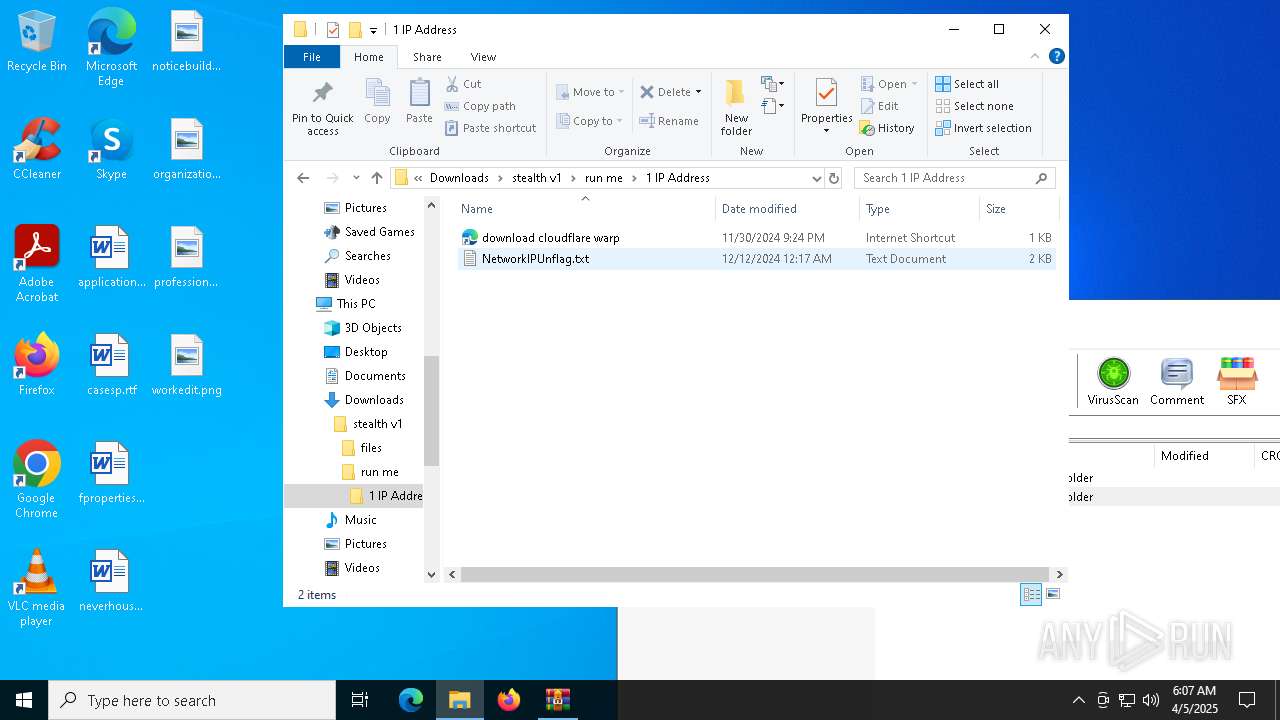
| 3020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3020.4024\stealth v1\run me\1 IP Address\NetworkIPUnflag.txt | text | |
MD5:146E88D84805B0A40D4937C950865B82 | SHA256:326B9DE70704A46E36991F11D47B226357F311E6F5CE6D835D7B104E64FC8834 | |||
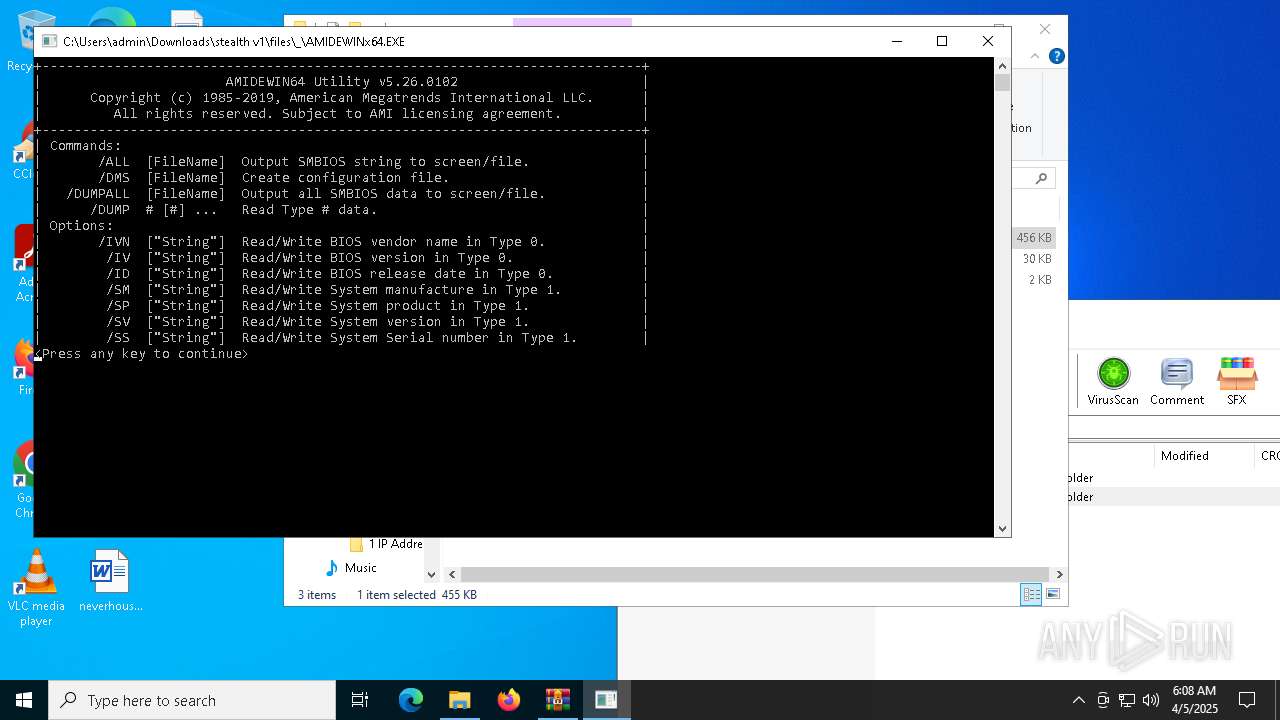
| 3020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3020.4024\stealth v1\files\_\AMIDEWINx64.EXE | executable | |
MD5:9ADFCDAC59DB3286690C7EEDE8DA2528 | SHA256:13037EEDD91F9313EC0D807947DB65C639642E5AE6497E87D12FA6D19951F78E | |||
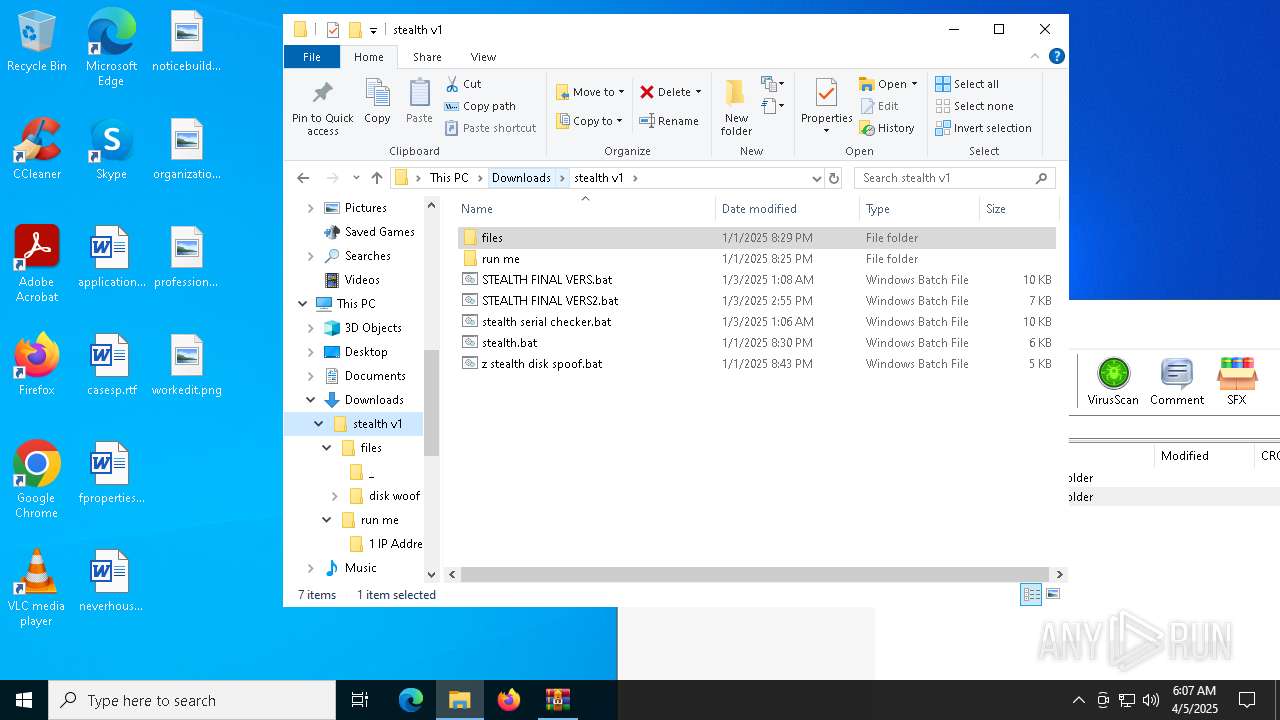
| 3020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3020.4024\stealth v1\STEALTH FINAL VERS.bat | text | |
MD5:125B672B6A66922583B2D9A4B849BD11 | SHA256:A7AA662203318AE2FEB6C22B71B210D192463AB1E77B96832A1AF00448130598 | |||
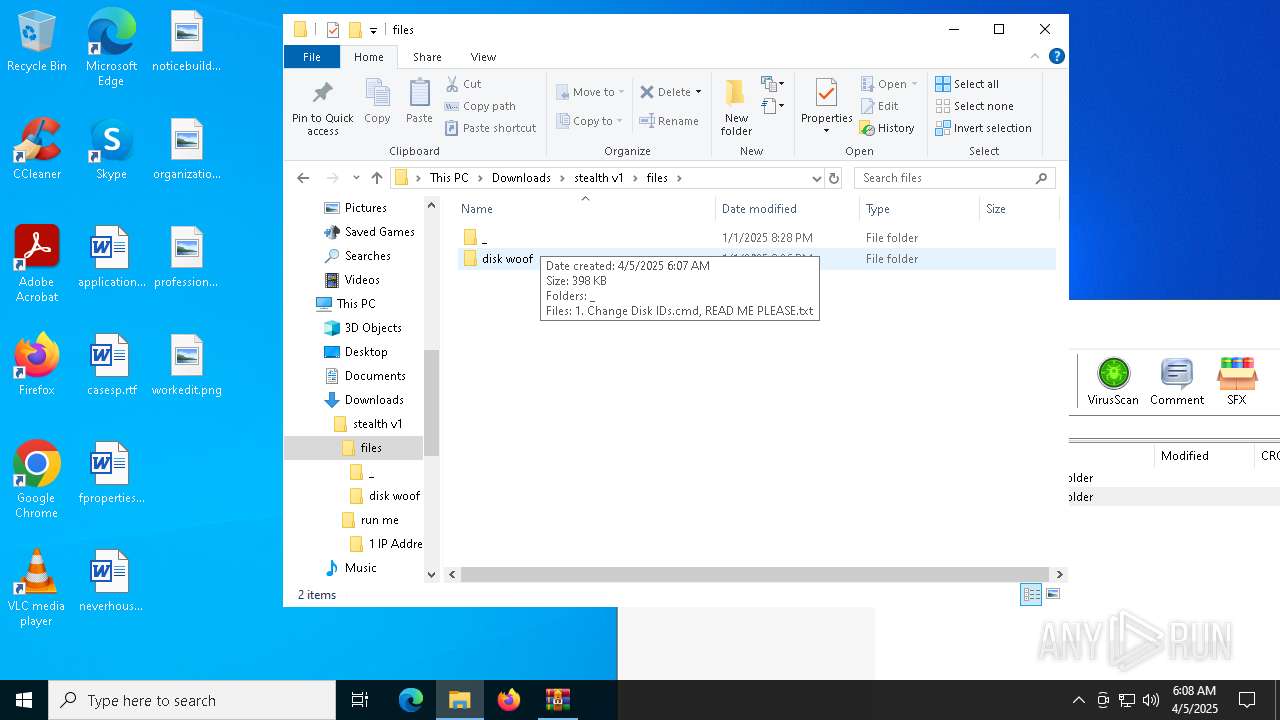
| 3020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3020.4024\stealth v1\files\disk woof\READ ME PLEASE.txt | text | |
MD5:50BC60383C45B15BB32F3168DCE065F9 | SHA256:240B617B3AC0232FDCECE77E79A9FD9D02BA0DECB252BBE5710B3634B4B87985 | |||
| 3020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3020.4024\stealth v1\files\disk woof\_\Volumeid64.exe | executable | |
MD5:81A45F1A91448313B76D2E6D5308AA7A | SHA256:FB0D02EA26BB1E5DF5A07147931CAF1AE3D7D1D9B4D83F168B678E7F3A1C0ECD | |||
| 3020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3020.4024\stealth v1\run me\1 IP Address\download cloudflare warp.url | binary | |
MD5:3C069BECC717182A41C7100FCD32880A | SHA256:C2CF07D60800952E204CF265E63DC74C05F530CADDAC9693FF0D24E520D95431 | |||
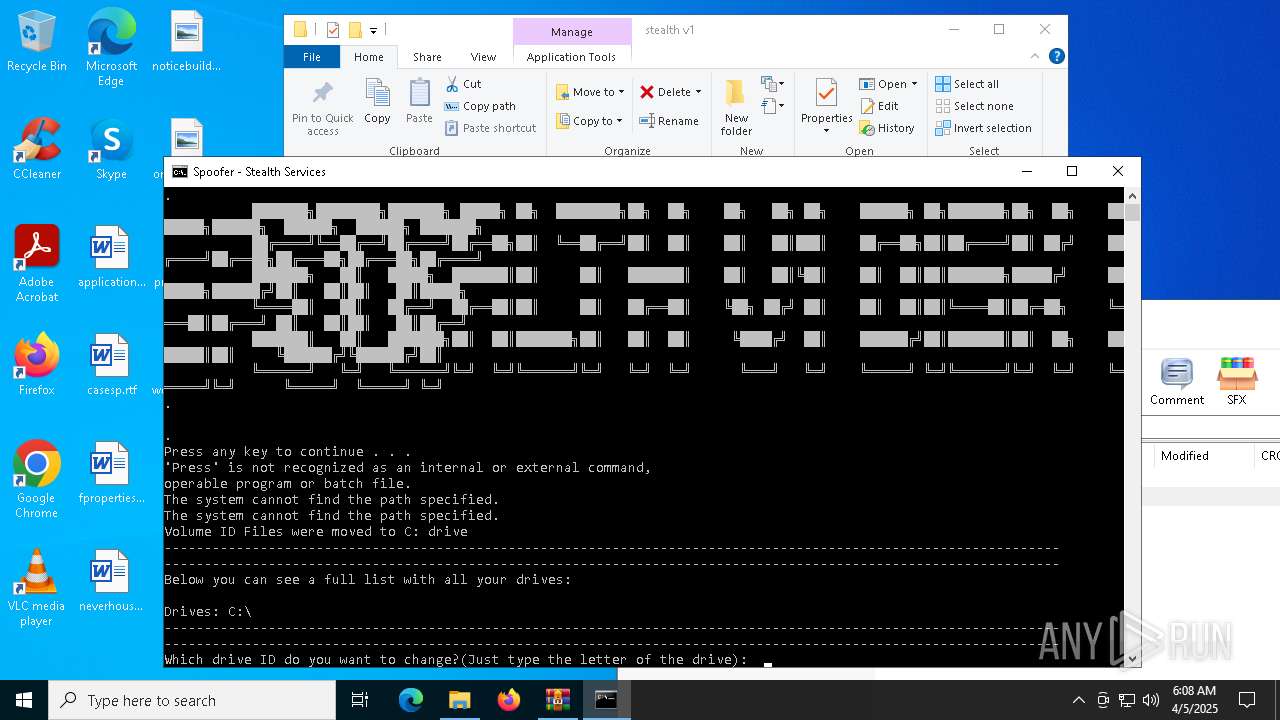
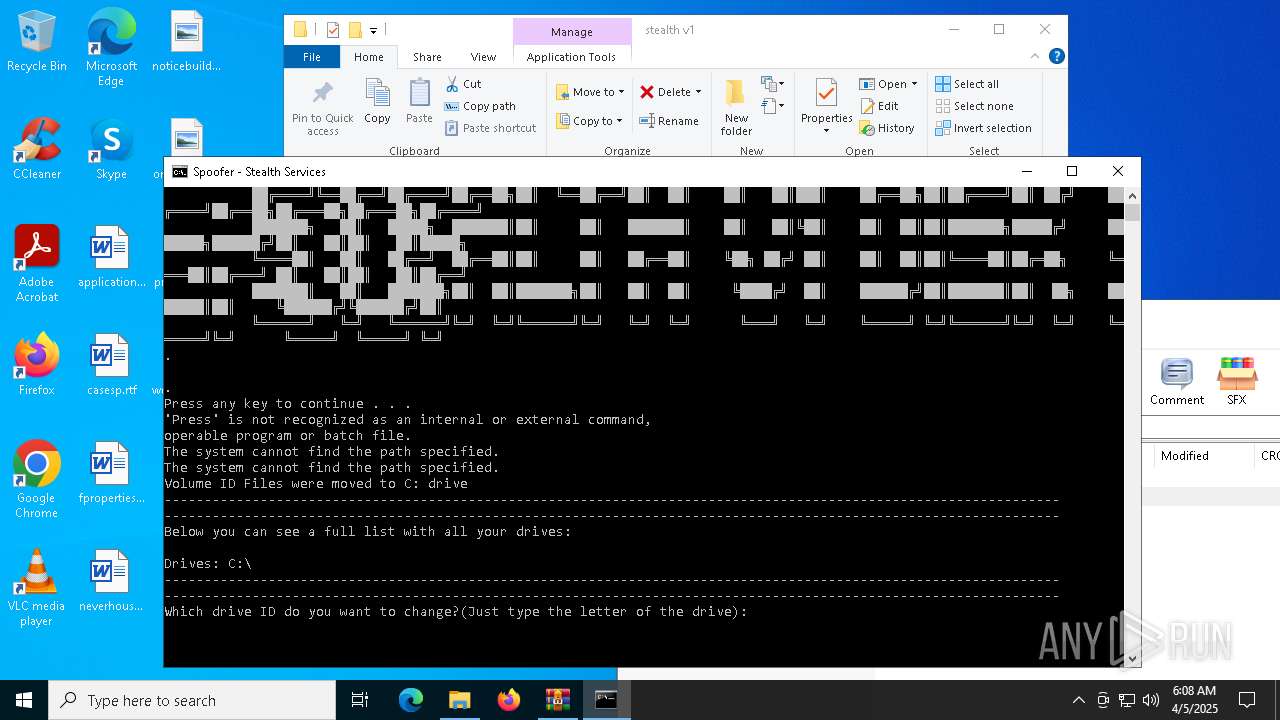
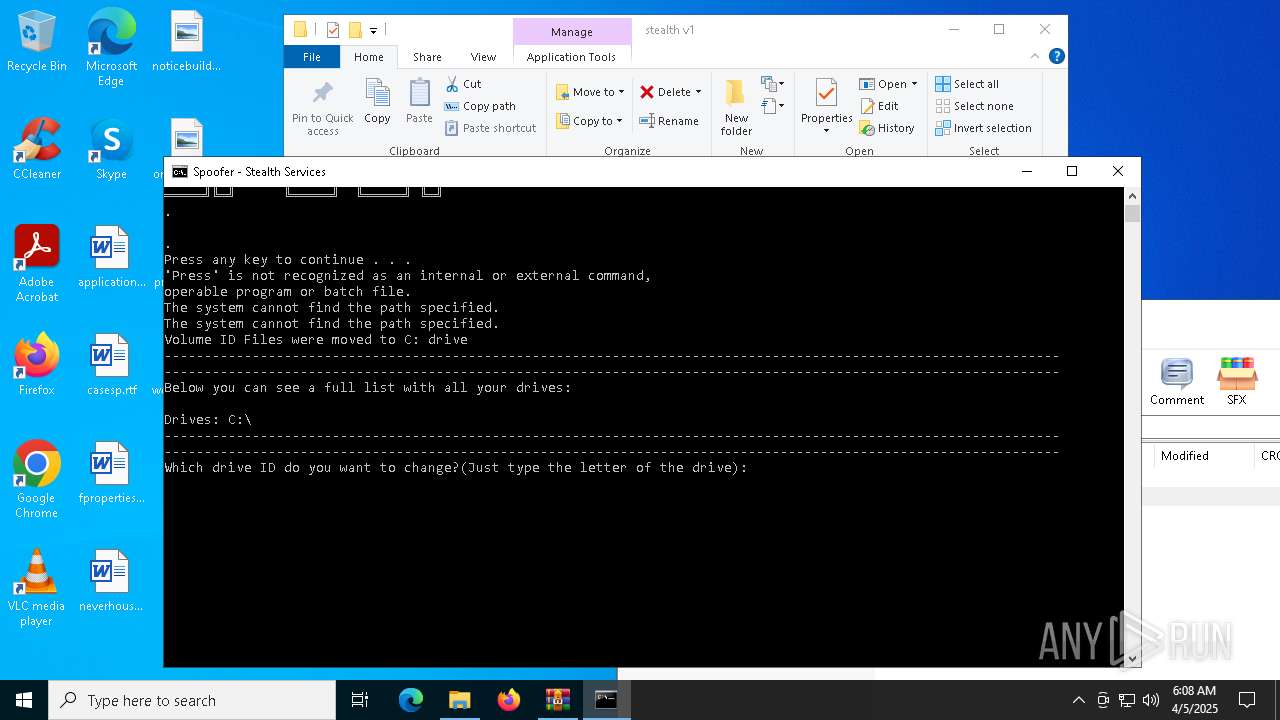
| 3020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3020.4024\stealth v1\z stealth disk spoof.bat | text | |
MD5:618DC1A55301793F4AFDA3A105E1CEF8 | SHA256:FE1CE35E34ACCBBDADBB90984CBF2E9AADB0F116E35A810EFFD6CDD27141C9ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
780 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
780 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.172.255.218:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
780 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |