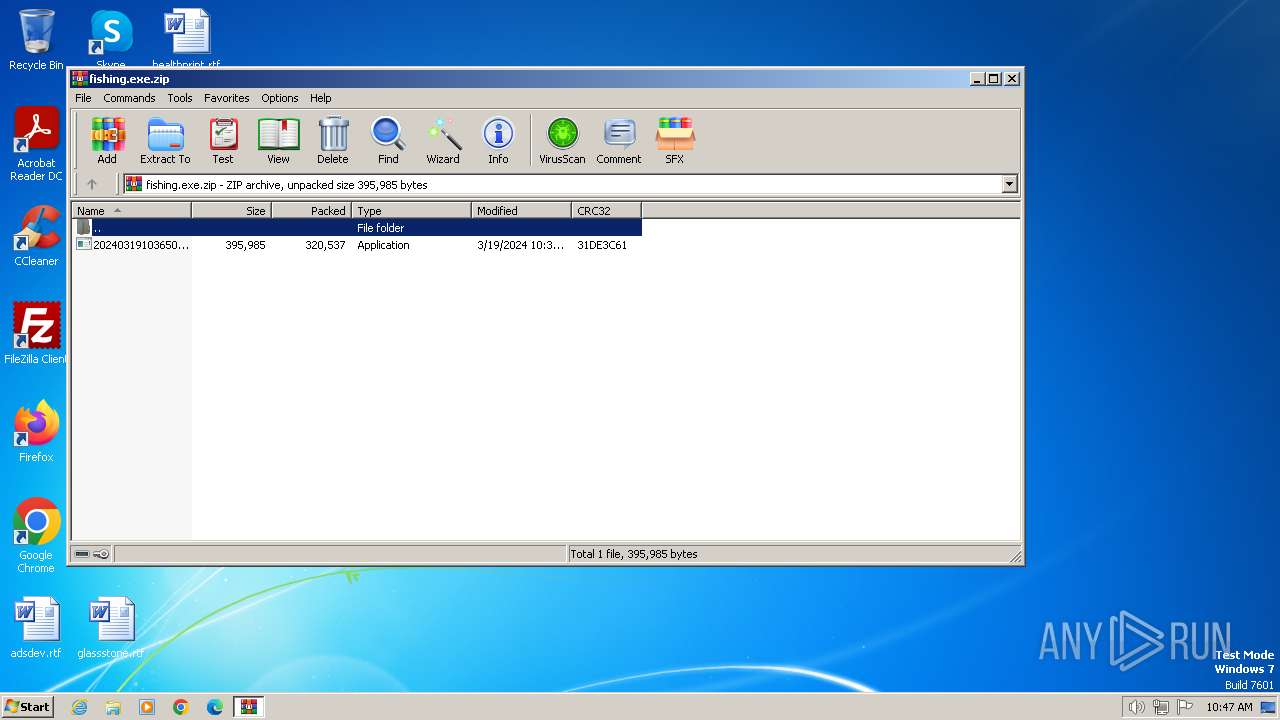
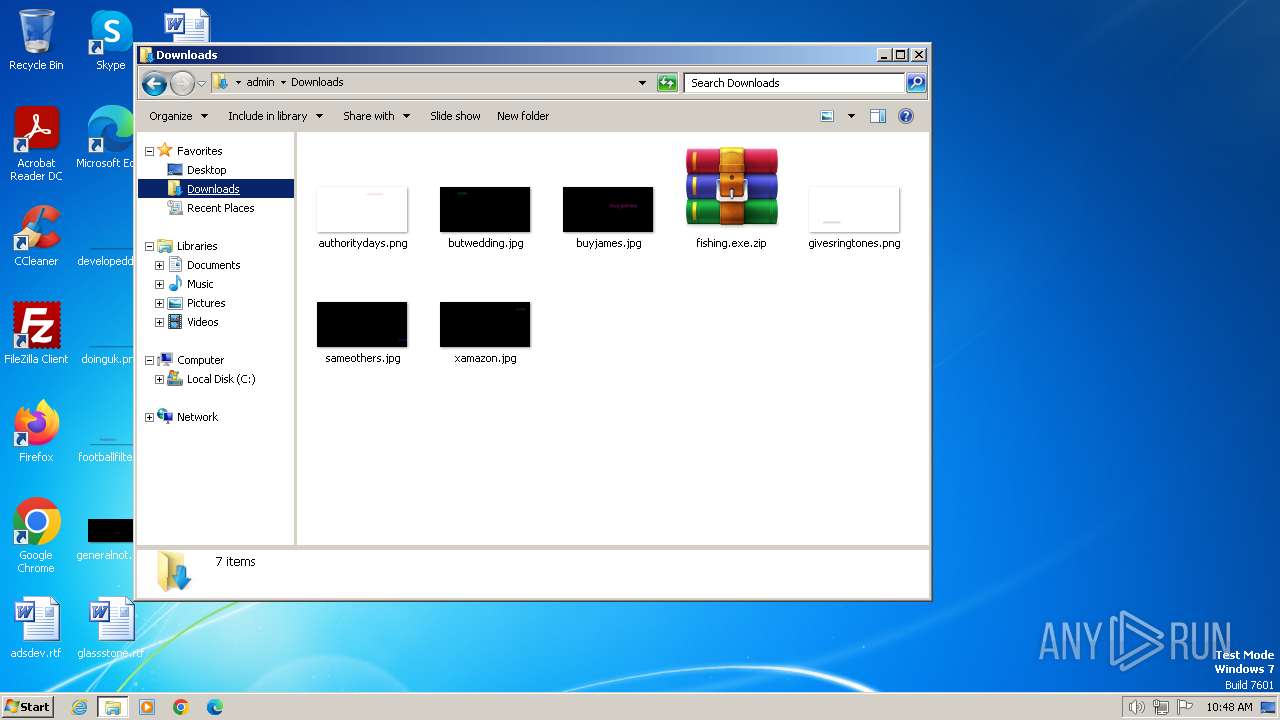
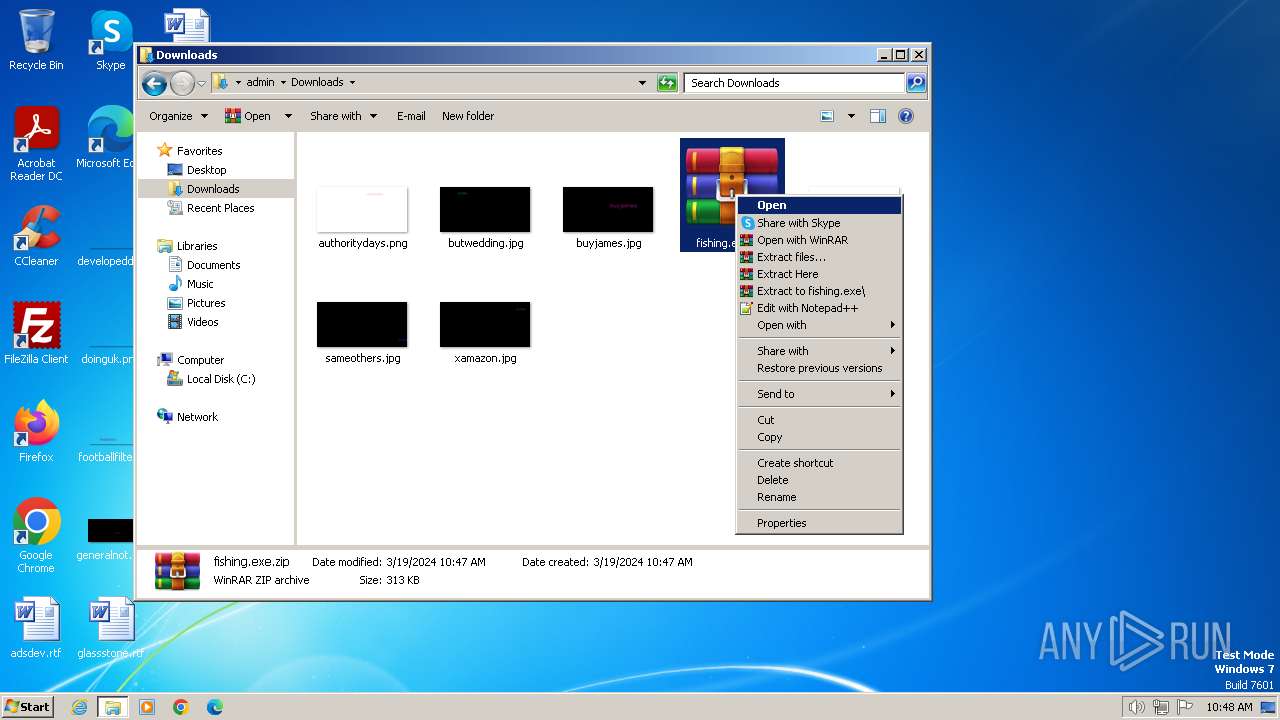
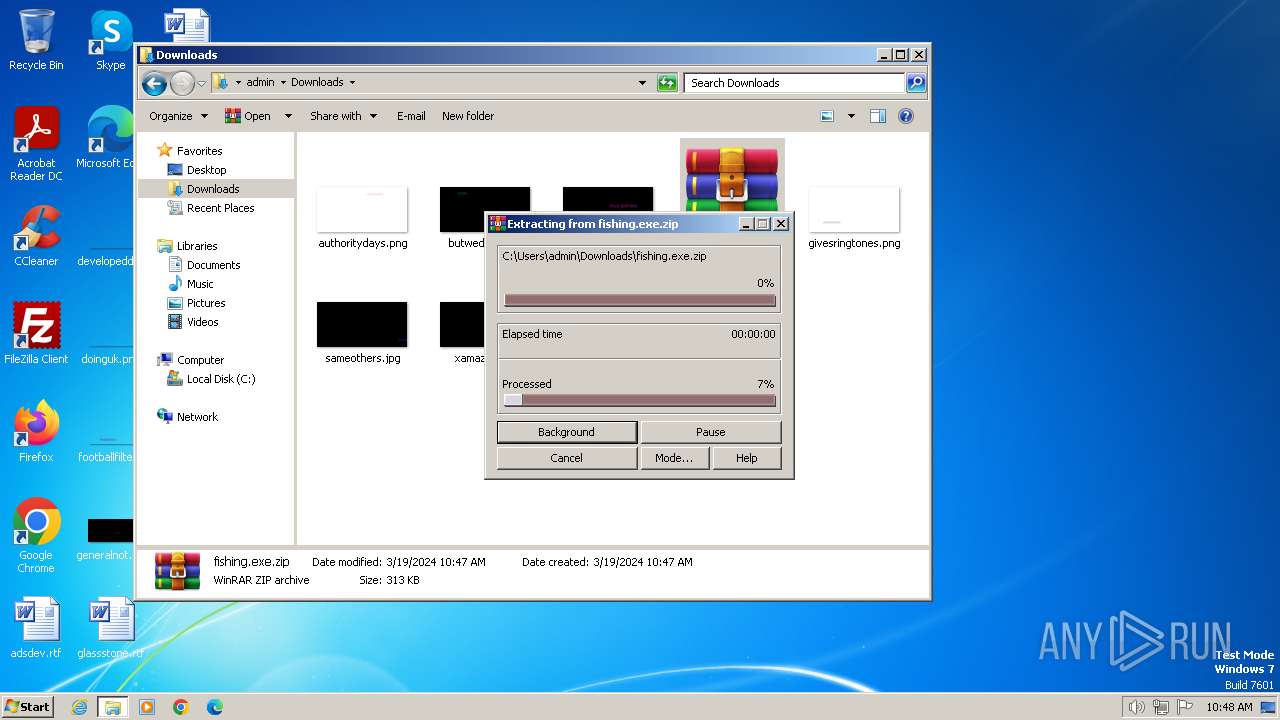
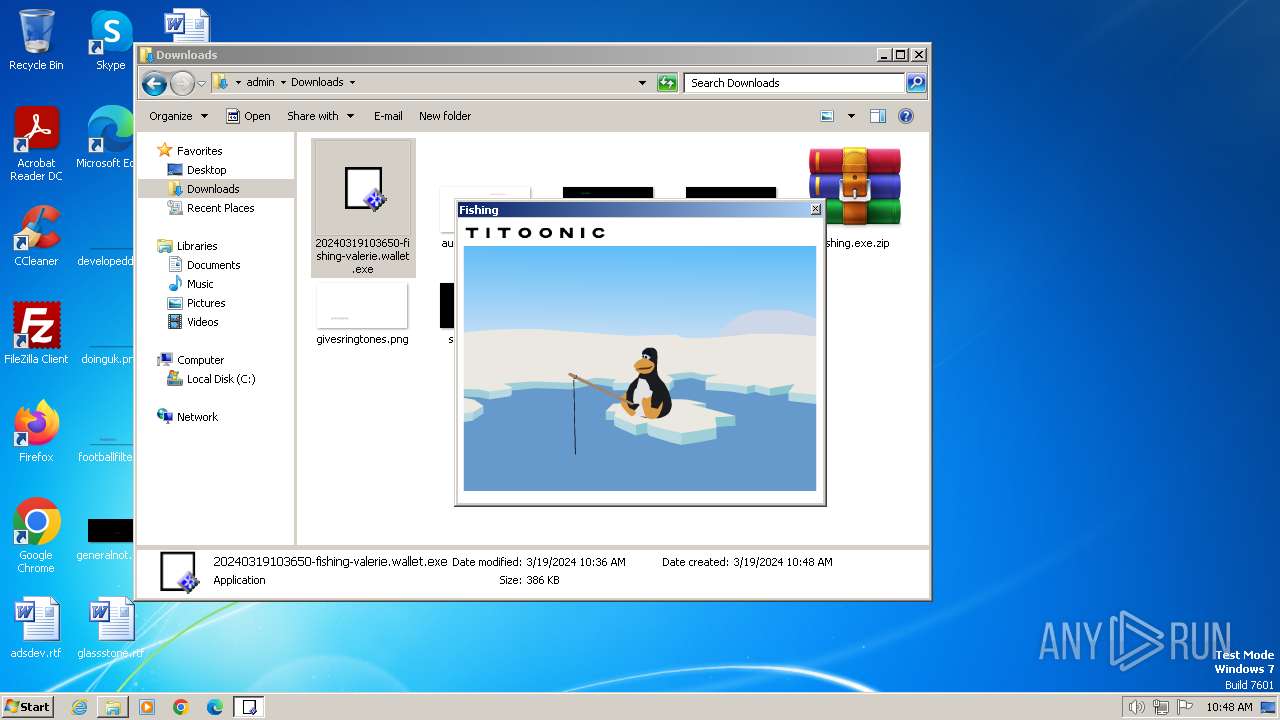
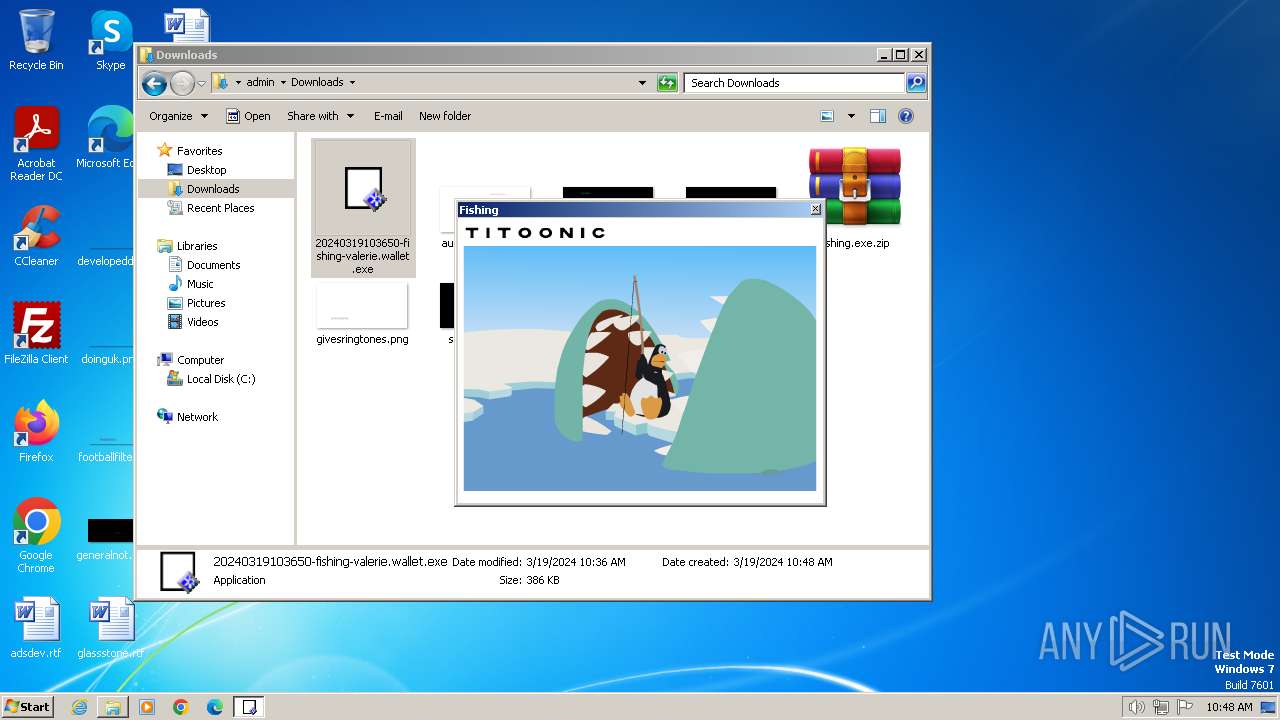
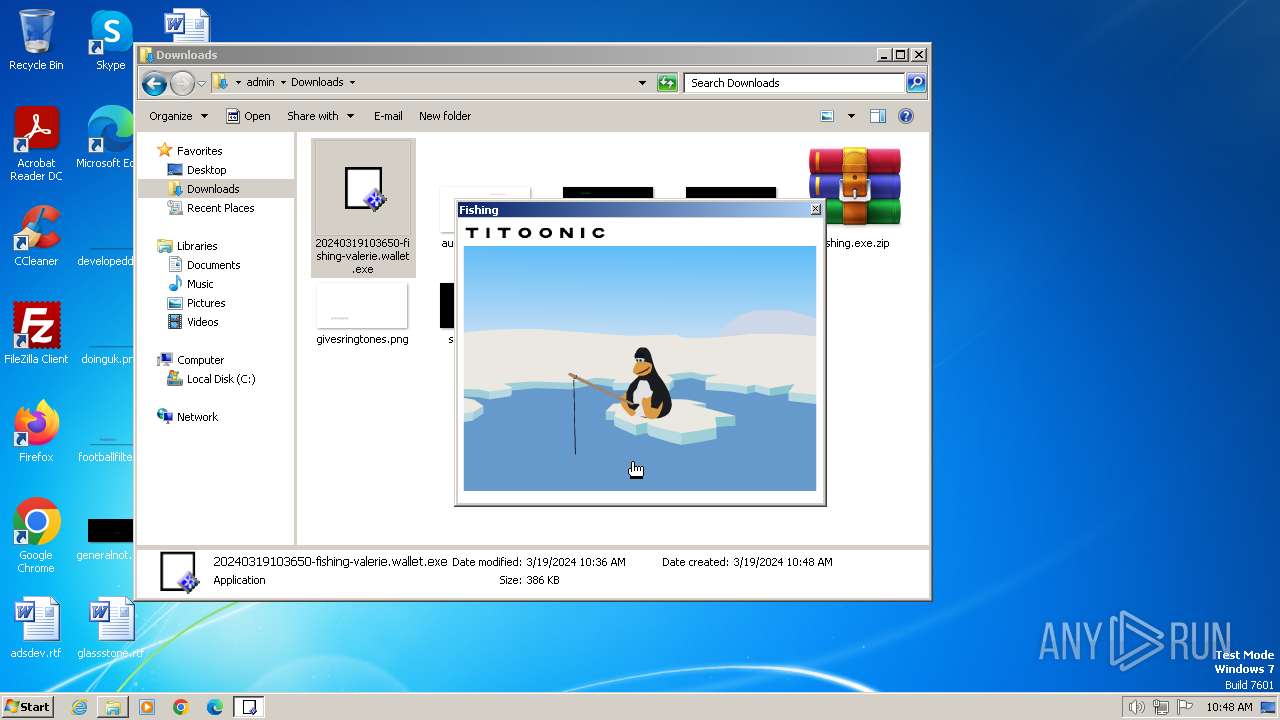
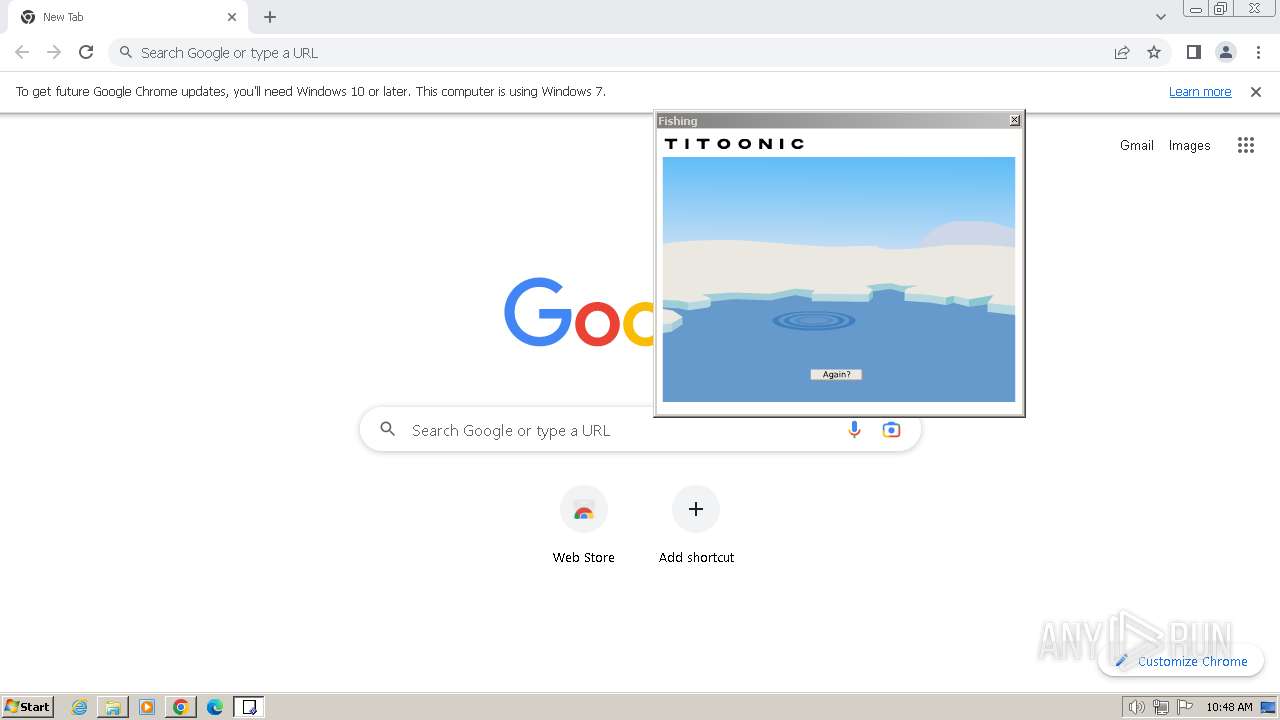
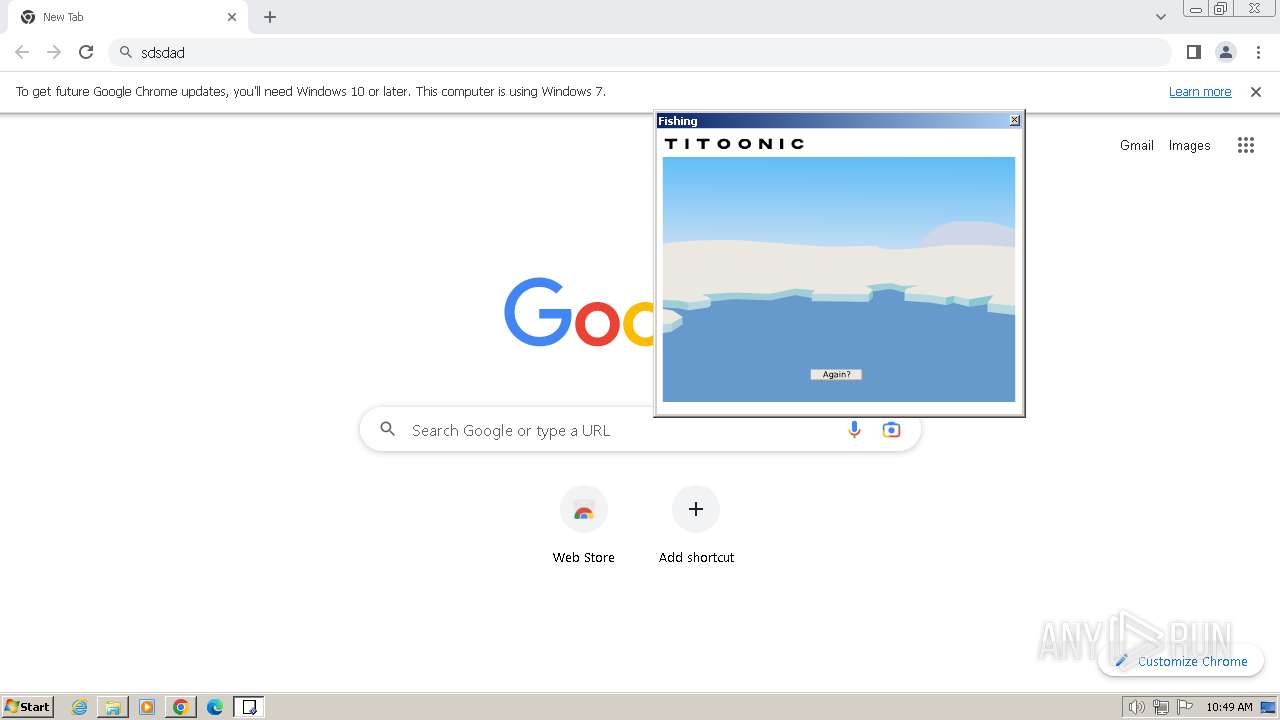
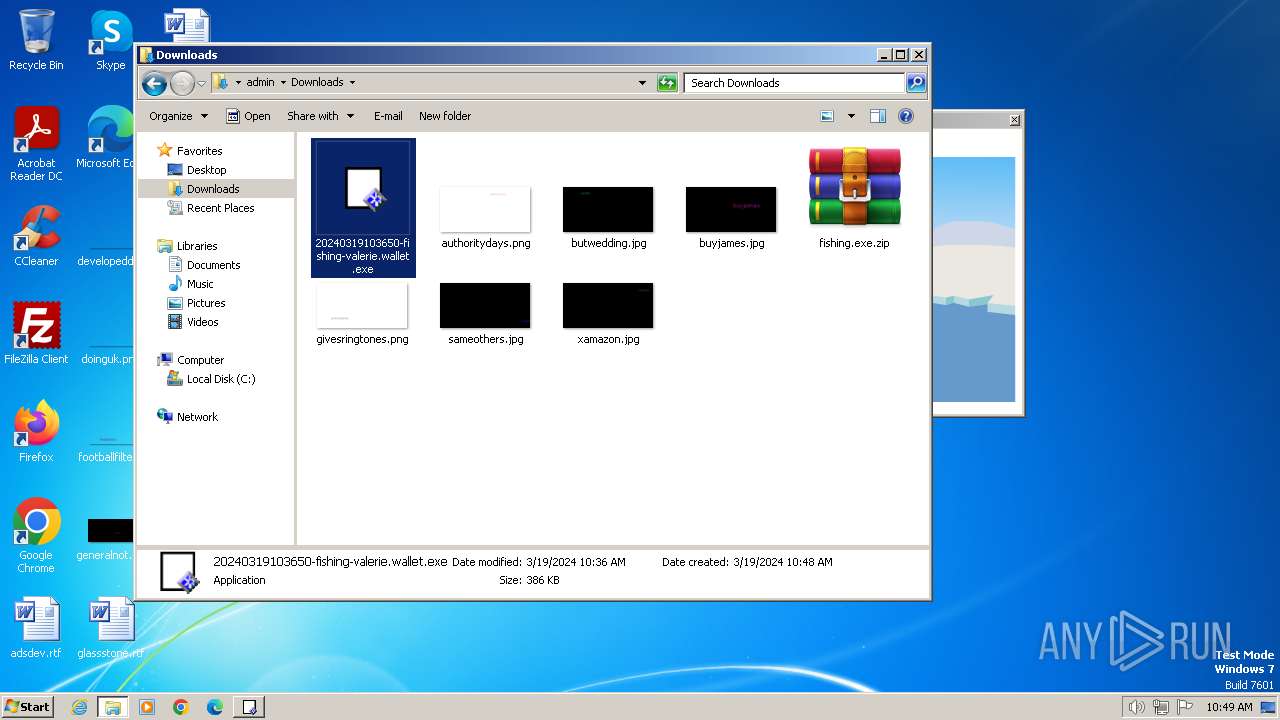
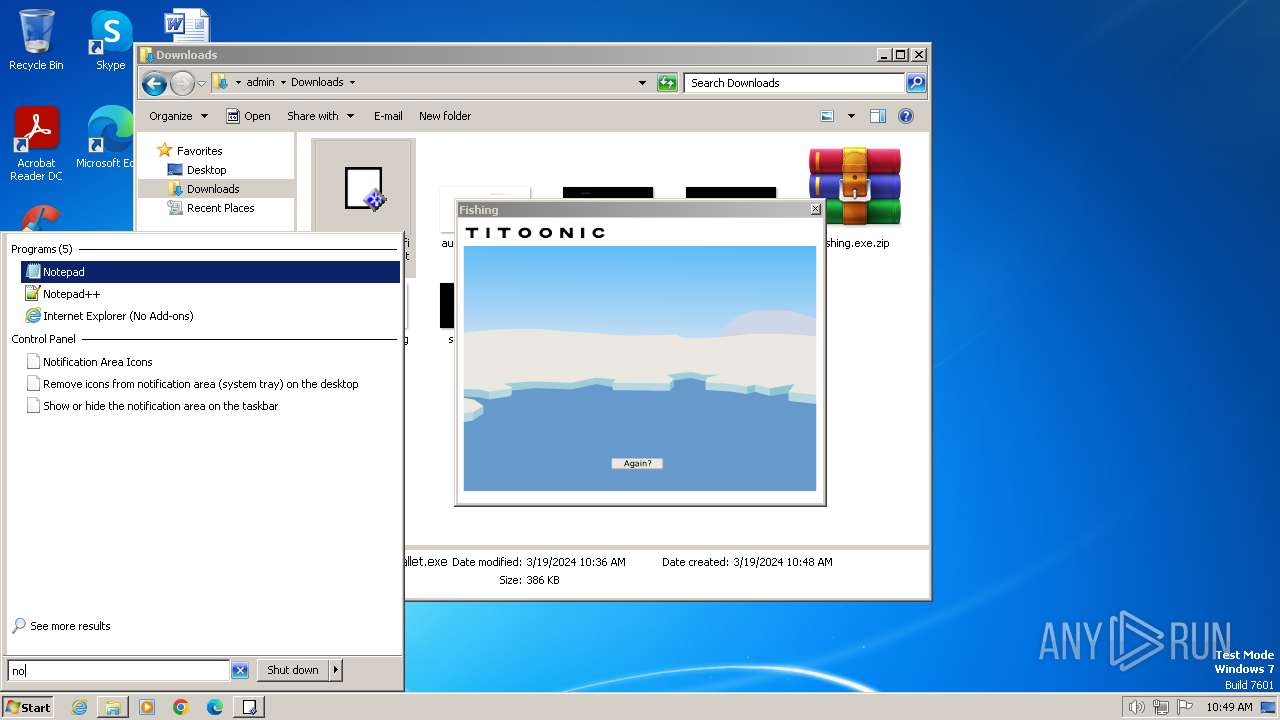
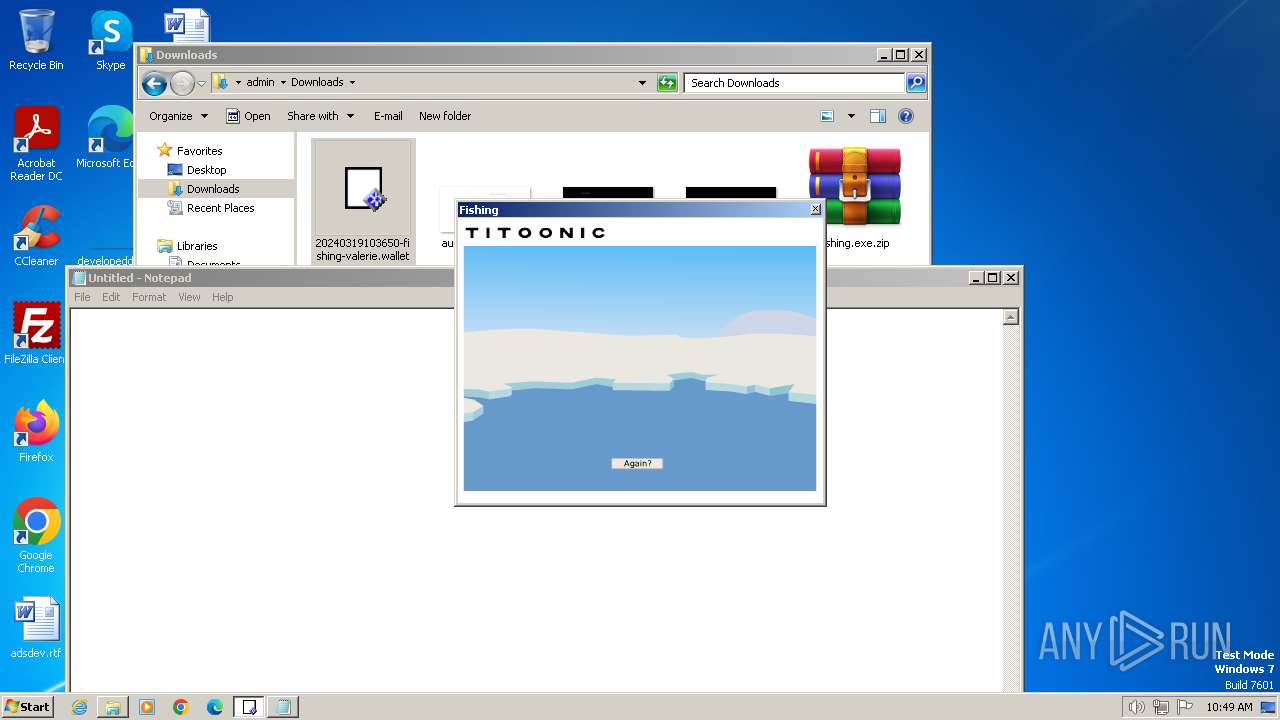
| File name: | fishing.exe.zip |
| Full analysis: | https://app.any.run/tasks/a0054ad9-dc10-4423-a5e6-e1bdaf649ab3 |
| Verdict: | Malicious activity |
| Analysis date: | March 19, 2024, 10:47:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | FBCD60DF9D460CCEB029F78DC32D065A |
| SHA1: | 90FA08A46A655F5D3CC701CAA341766D873AC5E9 |
| SHA256: | 2C93478BC6D7C93979D82018044FEC6A3257AE6F4BA188A6F694632E45D042F3 |
| SSDEEP: | 12288:xdpLAoLI8w28IcMnic+wAApQG0I5hGMWtsddk+:xdpLAoLrw28v+ic+wAApQG0I5hXWCvk+ |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3956)
- 20240319103650-fishing-valerie.wallet.exe (PID: 2644)
- 20240319103650-fishing-valerie.wallet.exe (PID: 3600)
SUSPICIOUS
Executable content was dropped or overwritten
- 20240319103650-fishing-valerie.wallet.exe (PID: 2644)
- 20240319103650-fishing-valerie.wallet.exe (PID: 3600)
INFO
Manual execution by a user
- explorer.exe (PID: 2572)
- WinRAR.exe (PID: 2168)
- 20240319103650-fishing-valerie.wallet.exe (PID: 2644)
- notepad.exe (PID: 2948)
- 20240319103650-fishing-valerie.wallet.exe (PID: 3600)
- chrome.exe (PID: 2432)
- wmpnscfg.exe (PID: 3244)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2168)
Create files in a temporary directory
- 20240319103650-fishing-valerie.wallet.exe (PID: 2644)
- 20240319103650-fishing-valerie.wallet.exe (PID: 3600)
Checks supported languages
- bigfish-standalone.exe (PID: 2596)
- 20240319103650-fishing-valerie.wallet.exe (PID: 2644)
- wmpnscfg.exe (PID: 3244)
- bigfish-standalone.exe (PID: 3596)
- 20240319103650-fishing-valerie.wallet.exe (PID: 3600)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2168)
Application launched itself
- chrome.exe (PID: 2432)
Reads the computer name
- wmpnscfg.exe (PID: 3244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:03:19 10:36:50 |
| ZipCRC: | 0x31de3c61 |
| ZipCompressedSize: | 320537 |
| ZipUncompressedSize: | 395985 |
| ZipFileName: | 20240319103650-fishing-valerie.wallet.exe |
Total processes
61
Monitored processes
24
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=828 --field-trial-handle=1160,i,17676470092400255178,16356123539949226720,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3616 --field-trial-handle=1160,i,17676470092400255178,16356123539949226720,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1628 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3380 --field-trial-handle=1160,i,17676470092400255178,16356123539949226720,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1584 --field-trial-handle=1160,i,17676470092400255178,16356123539949226720,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2168 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\fishing.exe.zip" C:\Users\admin\Downloads\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2432 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1224 --field-trial-handle=1160,i,17676470092400255178,16356123539949226720,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6a7f8b38,0x6a7f8b48,0x6a7f8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2572 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2596 | "C:\Users\admin\AppData\Local\Temp\414735~1\bigfish-standalone.exe" | C:\Users\admin\AppData\Local\Temp\41473590 98214276 64920491\bigfish-standalone.exe | — | 20240319103650-fishing-valerie.wallet.exe | |||||||||||
User: admin Company: Macromedia, Inc. Integrity Level: MEDIUM Description: Flash Player 4.0 r7 Exit code: 0 Version: 4,0,7,0 Modules
| |||||||||||||||
Total events
6 669
Read events
6 603
Write events
65
Delete events
1
Modification events
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\fishing.exe.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
5
Suspicious files
33
Text files
46
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2432 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1908df.TMP | — | |
MD5:— | SHA256:— | |||
| 2432 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2432 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 2432 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 2432 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:E53573A93829681410D5E7DBB1B61C78 | SHA256:A82D28F2C1E22A2AE0ABC5F5AF0CC8EE7AD913BAB3A0BF84CE6D8D23F67E06A3 | |||
| 2432 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF1908df.TMP | text | |
MD5:05CF4C3C5148DA6355D3561A9EAA5E8A | SHA256:8D720243F6876898E4F197C8867C4CEE69F1C7335C55B8A29C120B1028D93E41 | |||
| 2432 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\fcdc6e78-b91c-4d26-85ce-39afd4e31dd9.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 2432 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF190b12.TMP | — | |
MD5:— | SHA256:— | |||
| 2432 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2432 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old~RF190a37.TMP | text | |
MD5:B36B68CE4A71A5BFAF89A4D1CC07893F | SHA256:6422CC04455EF100D67FD9F299AACFEF3BA4F77D0FA1D2440D89E7D1CF65EBBC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
23
DNS requests
16
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2780 | chrome.exe | 142.250.185.100:443 | www.google.com | GOOGLE | US | whitelisted |
2432 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
2780 | chrome.exe | 74.125.206.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
2780 | chrome.exe | 142.250.181.227:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2780 | chrome.exe | 172.217.18.3:443 | www.gstatic.com | GOOGLE | US | whitelisted |
2780 | chrome.exe | 172.217.16.142:443 | apis.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
www.googleapis.com |
| whitelisted |