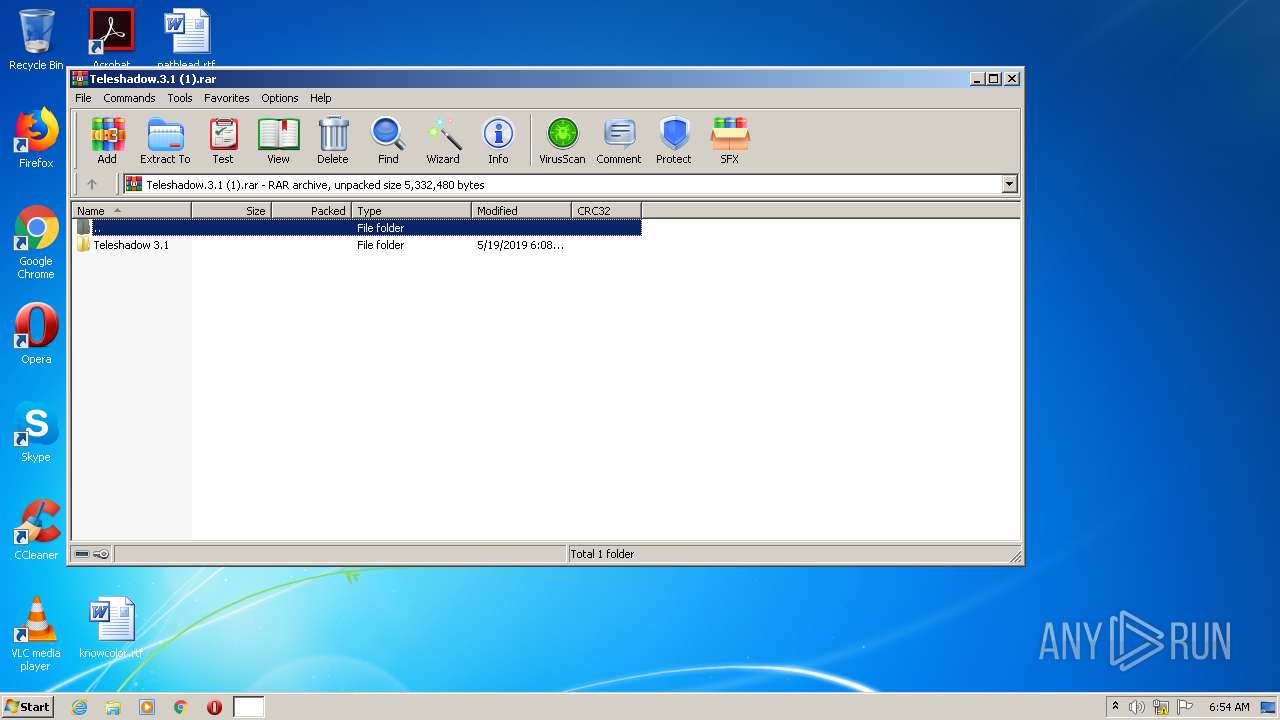
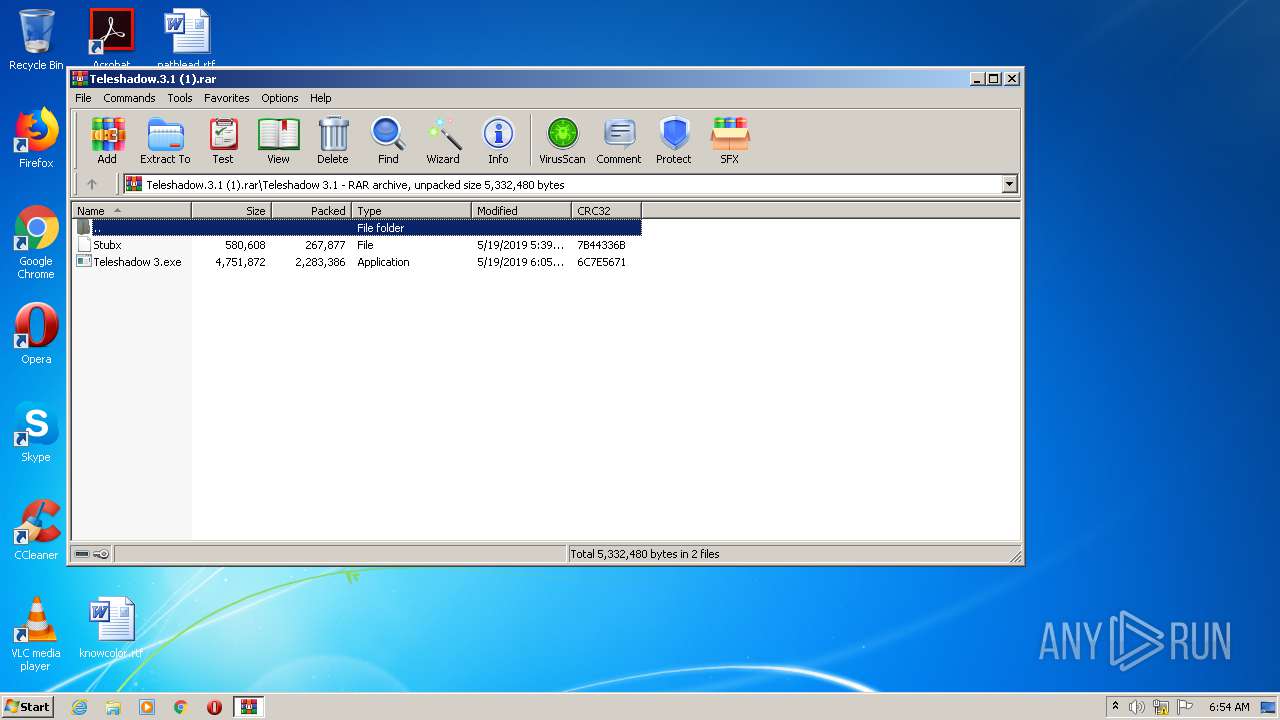
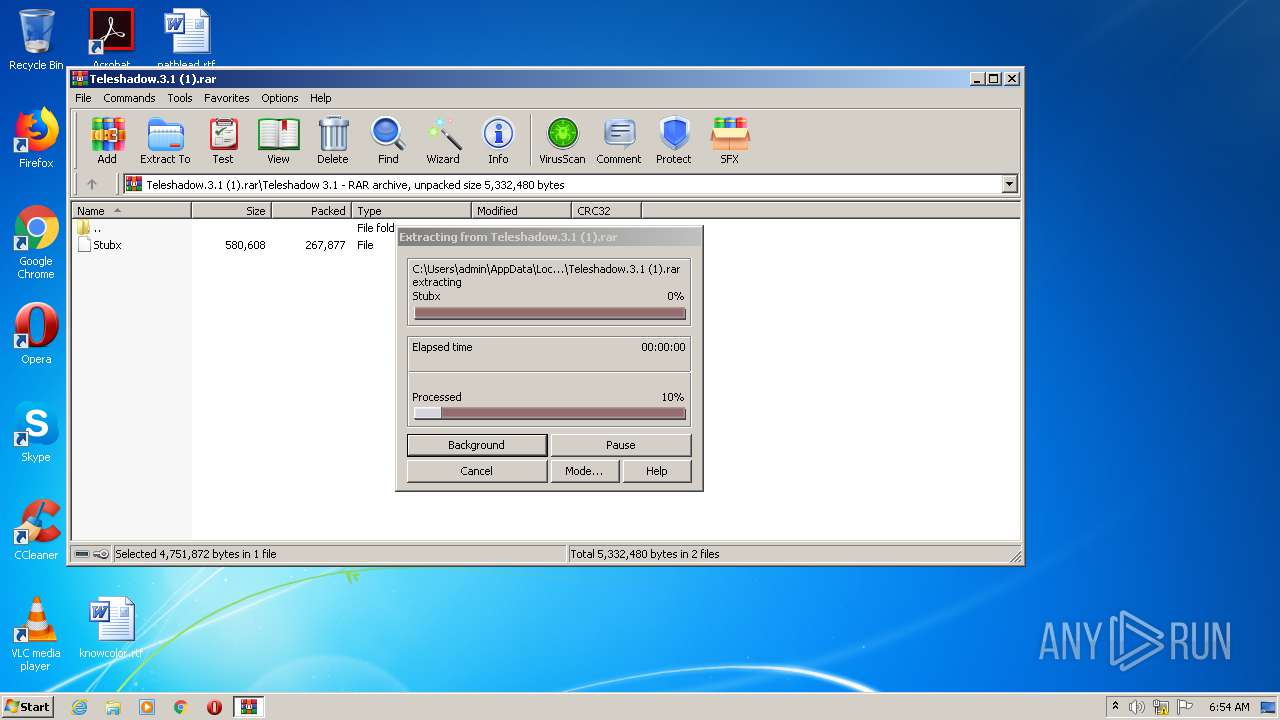
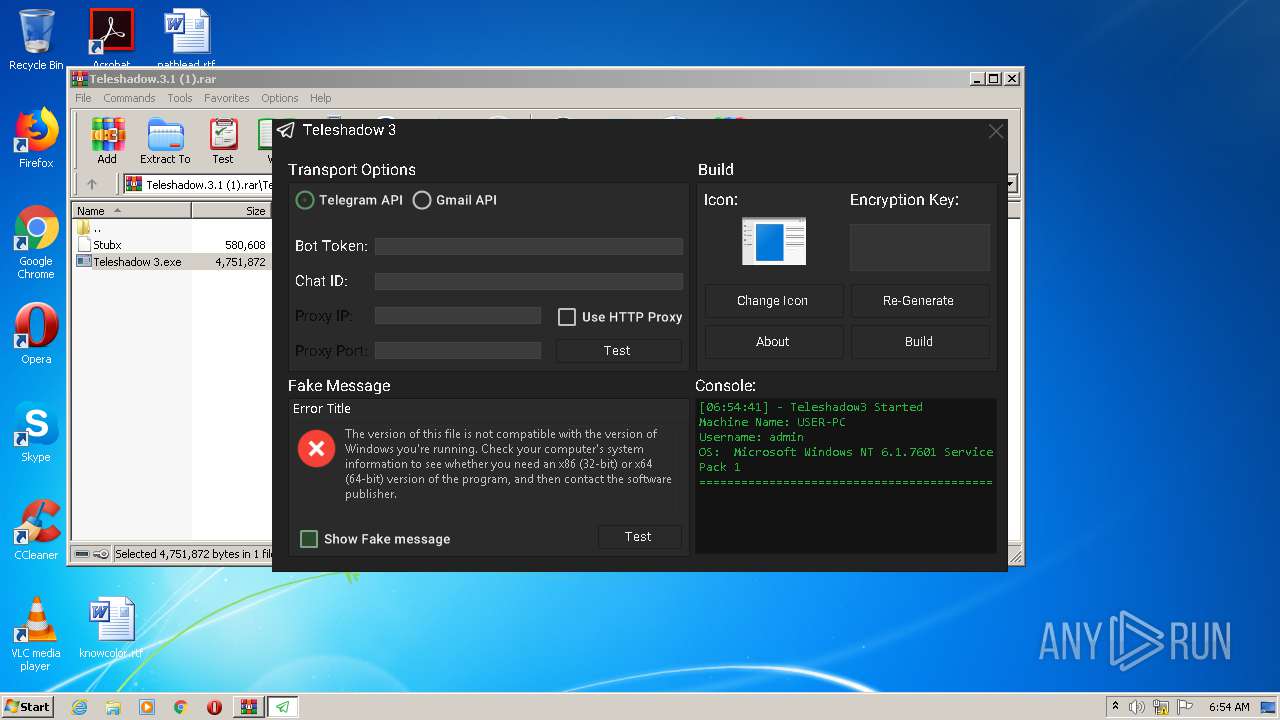
| File name: | Teleshadow.3.1 (1).rar |
| Full analysis: | https://app.any.run/tasks/a425e172-26e2-41da-83d5-5ce92711f94f |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2021, 05:54:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C29B1A951EAE54D36D0A110217713348 |
| SHA1: | 73E12A7E320148E2E999C2D0A9495B9216FCA70C |
| SHA256: | 2C8CD3B41F34B23CC0DD45550542F05082A1EC401962C76386EEE6C2D1AE09A6 |
| SSDEEP: | 49152:554qbBjTh4gjlFviB4YINXiua9zEjoOcQ8+6K7Dvp+rebhJMK4MRUPk:5+qdSgjrviBkNXieEv+NvU2h3/Uc |
MALICIOUS
Drops executable file immediately after starts
- Teleshadow 3.exe (PID: 2336)
Application was dropped or rewritten from another process
- Teleshadow 3.exe (PID: 2336)
SUSPICIOUS
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 1544)
Drops a file with too old compile date
- WinRAR.exe (PID: 1544)
- Teleshadow 3.exe (PID: 2336)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1544)
- Teleshadow 3.exe (PID: 2336)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
33
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1544 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Teleshadow.3.1 (1).rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2336 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1544.40907\Teleshadow 3.1\Teleshadow 3.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1544.40907\Teleshadow 3.1\Teleshadow 3.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Teleshadow Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
913
Read events
889
Write events
24
Delete events
0
Modification events
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Teleshadow.3.1 (1).rar | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
10
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1544.40907\Teleshadow 3.1\Teleshadow 3.exe | executable | |
MD5:ED813189205C0D0E961D3EB7AE208DDE | SHA256:C9B7567230206F52F560D5CCF21C9B2022AE65D0411B30B8E4374E64B34E7BD2 | |||
| 2336 | Teleshadow 3.exe | C:\Users\admin\AppData\Local\Temp\evb442C.tmp | executable | |
MD5:B32993F21039491DD17CECDB5B06A2EC | SHA256:9D68A1C0F0E7125C8836042E40DA2C53D3302D21A86574045BE0225D09C27514 | |||
| 2336 | Teleshadow 3.exe | C:\Users\admin\AppData\Local\Temp\evb448D.tmp | executable | |
MD5:216FB1D780870623861B94E67A210F88 | SHA256:E61530CC222745087C9996633763FD65EB053C1CCFB42F1DC6AF7D0B0DA83F06 | |||
| 2336 | Teleshadow 3.exe | C:\Users\admin\AppData\Local\Temp\evb442D.tmp | executable | |
MD5:B32993F21039491DD17CECDB5B06A2EC | SHA256:9D68A1C0F0E7125C8836042E40DA2C53D3302D21A86574045BE0225D09C27514 | |||
| 2336 | Teleshadow 3.exe | C:\Users\admin\AppData\Local\Temp\evb449E.tmp | executable | |
MD5:BB56410706CA93F476FD45AE6ECCB2EC | SHA256:C6F73F24CA154F807A397FD951C5F4661757E4994B8F65DFBA0C3DAE85C4B87D | |||
| 2336 | Teleshadow 3.exe | C:\Users\admin\AppData\Local\Temp\evb447C.tmp | executable | |
MD5:216FB1D780870623861B94E67A210F88 | SHA256:E61530CC222745087C9996633763FD65EB053C1CCFB42F1DC6AF7D0B0DA83F06 | |||
| 2336 | Teleshadow 3.exe | C:\Users\admin\AppData\Local\Temp\evb449D.tmp | executable | |
MD5:BB56410706CA93F476FD45AE6ECCB2EC | SHA256:C6F73F24CA154F807A397FD951C5F4661757E4994B8F65DFBA0C3DAE85C4B87D | |||
| 2336 | Teleshadow 3.exe | C:\Users\admin\AppData\Local\Temp\evb44AF.tmp | executable | |
MD5:B05EF07A65694848E41DE4F382BEEC80 | SHA256:4D4403B0AB603B94E25FF31575C0BCCB85835F1E7812518ACBAAF45531627B8B | |||
| 2336 | Teleshadow 3.exe | C:\Users\admin\AppData\Local\Temp\evb44BF.tmp | executable | |
MD5:B05EF07A65694848E41DE4F382BEEC80 | SHA256:4D4403B0AB603B94E25FF31575C0BCCB85835F1E7812518ACBAAF45531627B8B | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1544.40907\Teleshadow 3.1\Stubx | executable | |
MD5:F3091B9B1756B02DF619782F36C0C9AA | SHA256:DBED7C89CC3B7C81872A7375871454E2DDD8D80A98162ED854100620B8786EF4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.222:8675 | — | — | — | malicious |