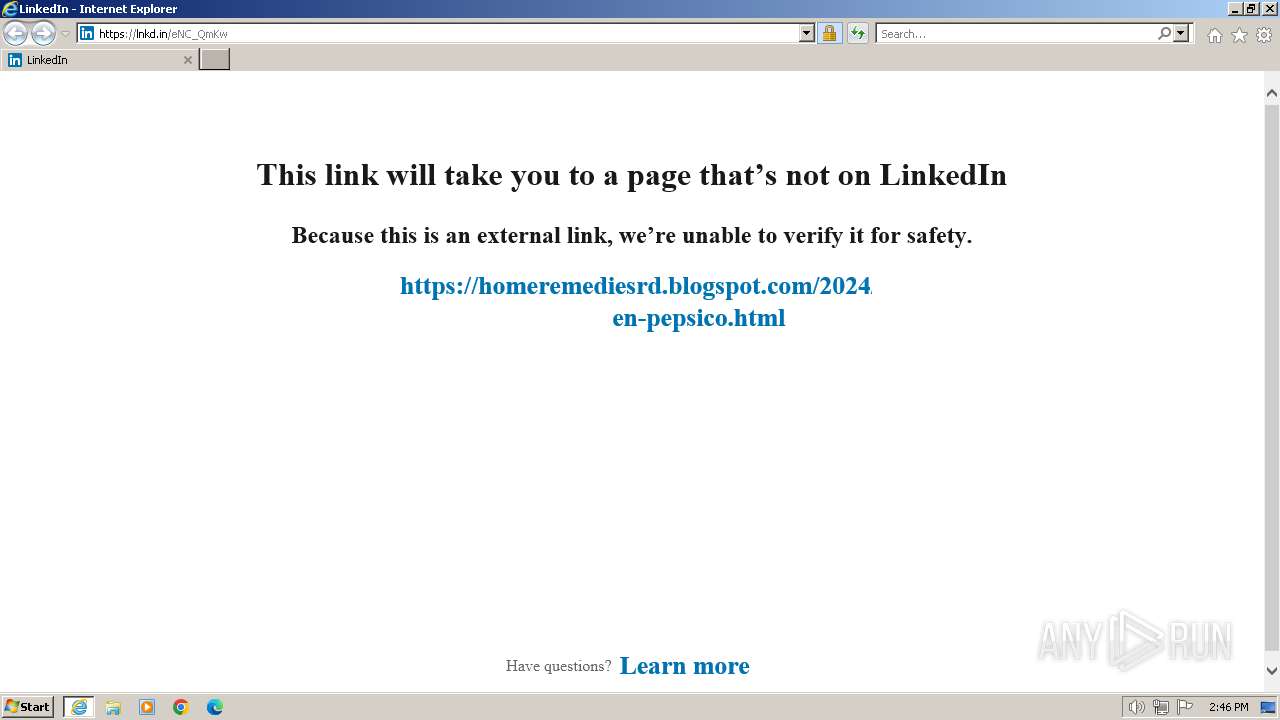
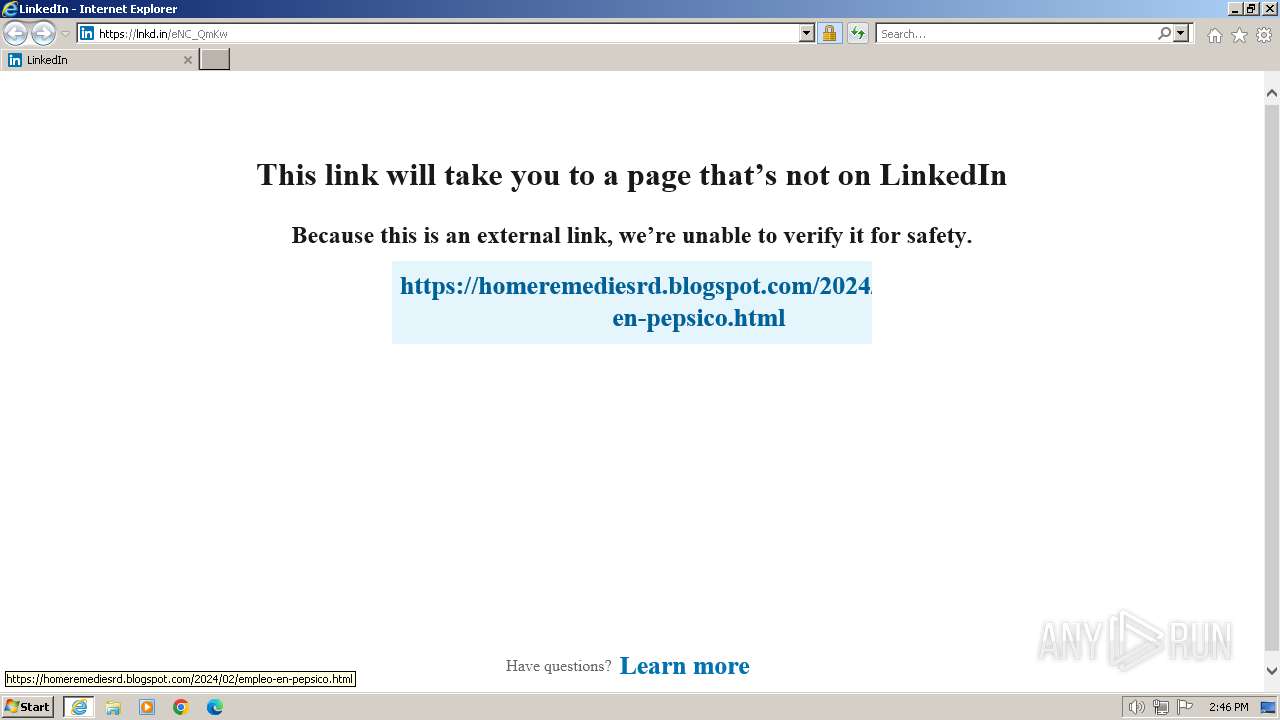
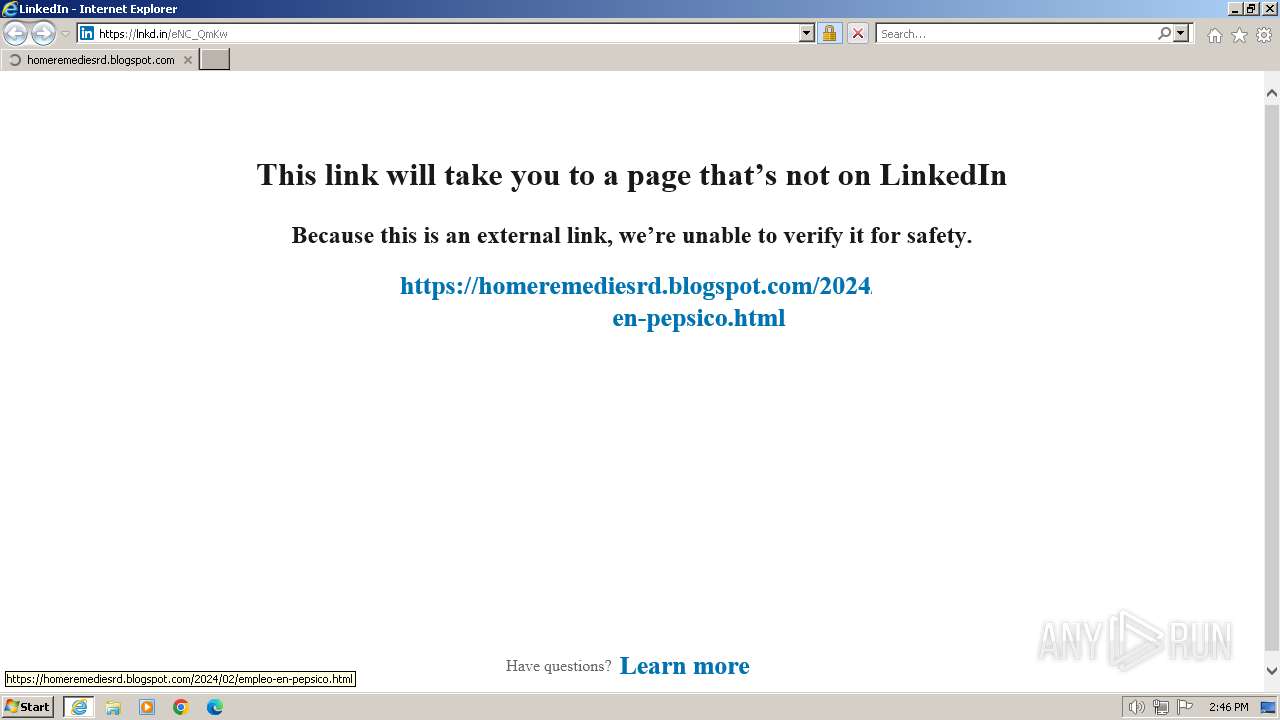
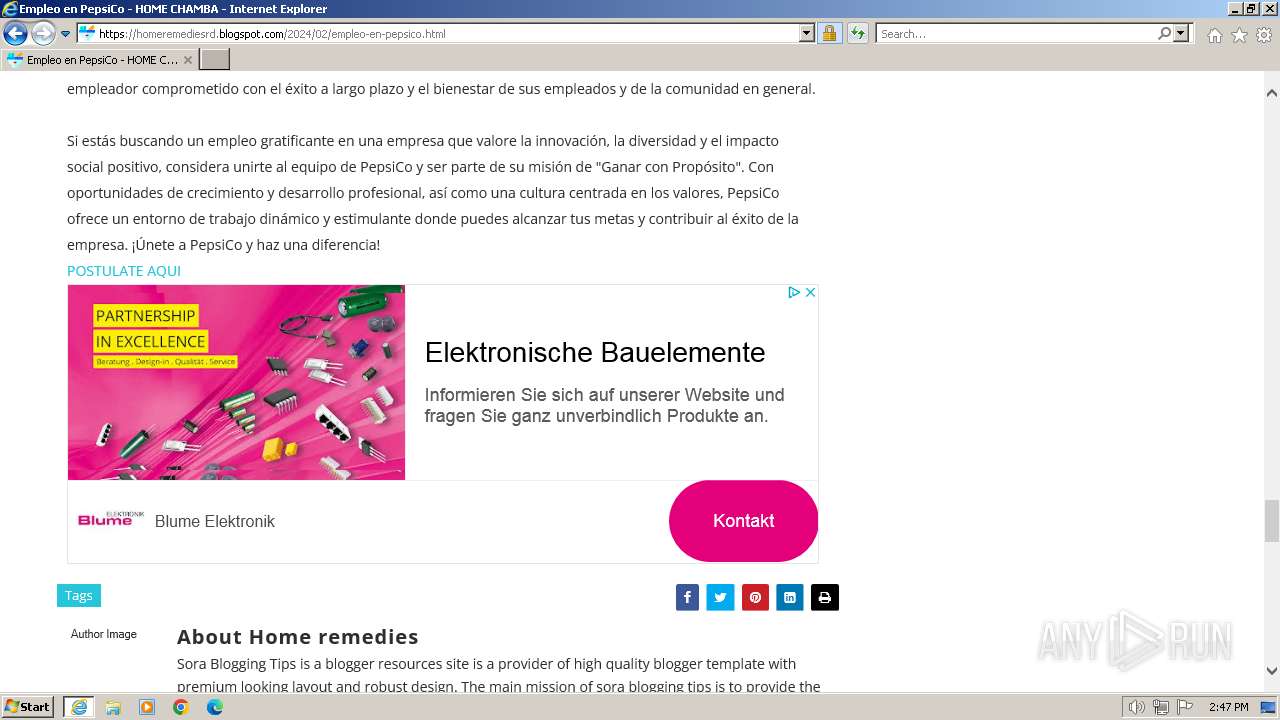
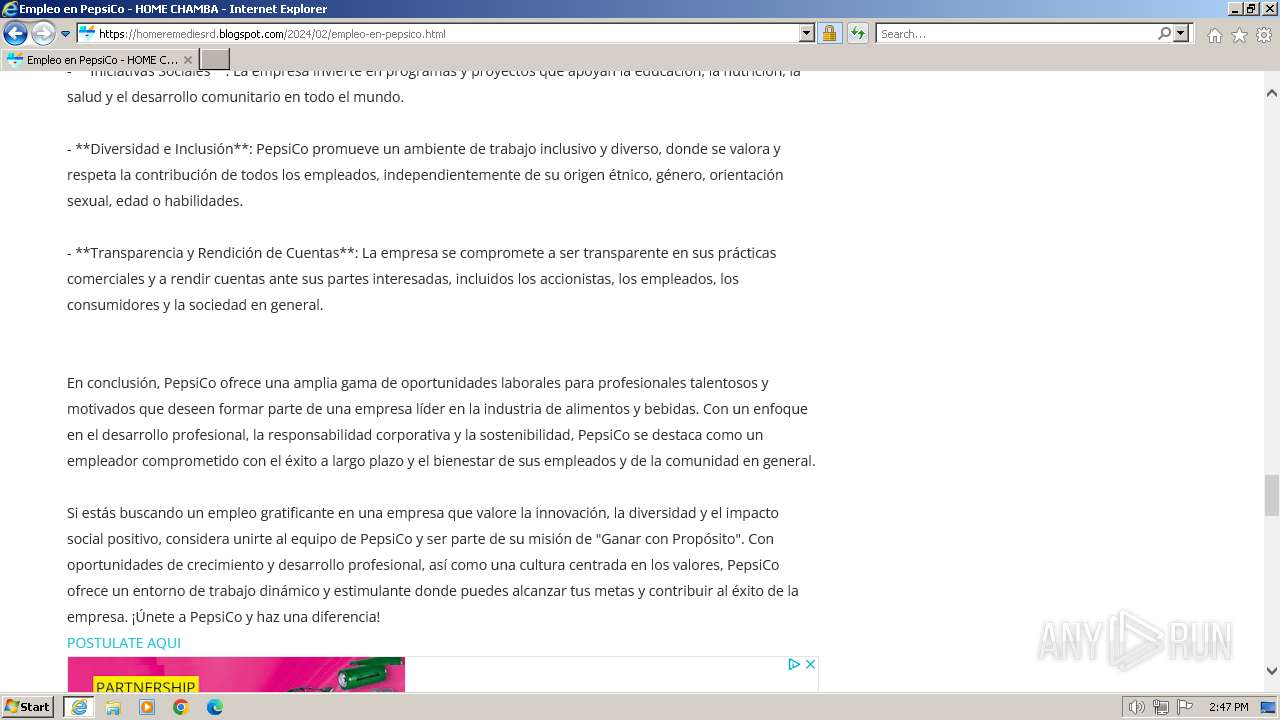
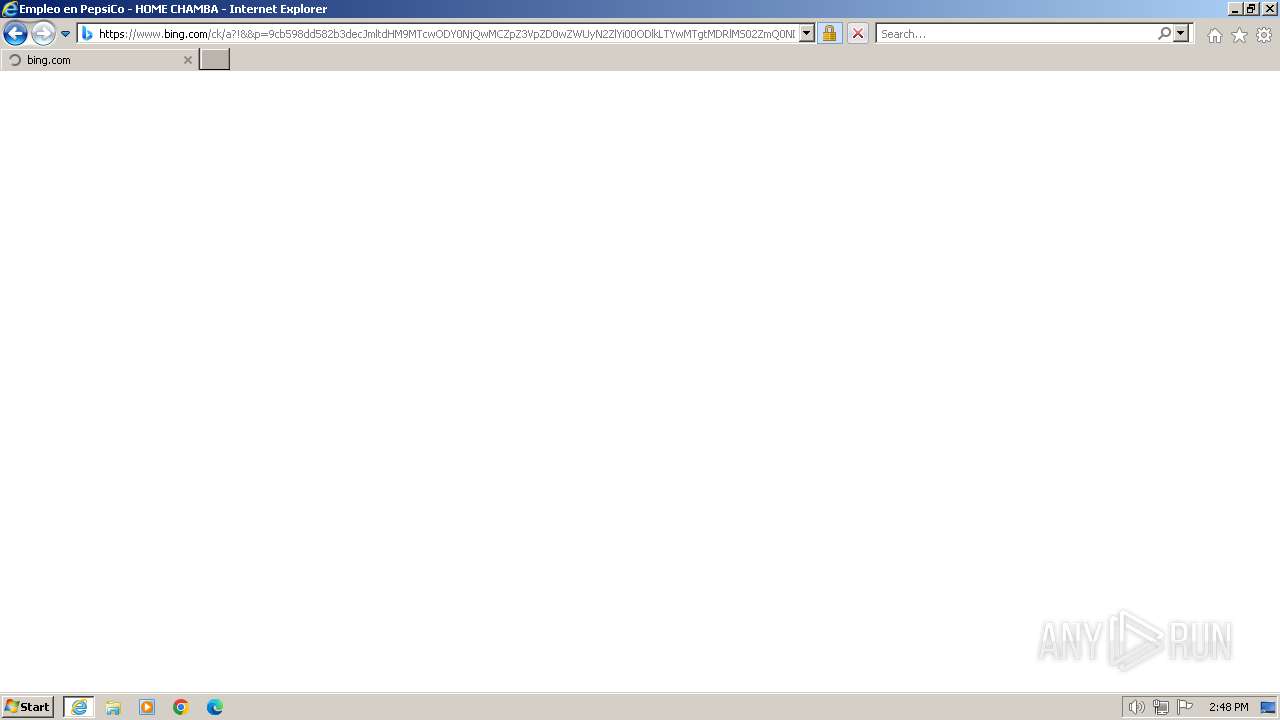
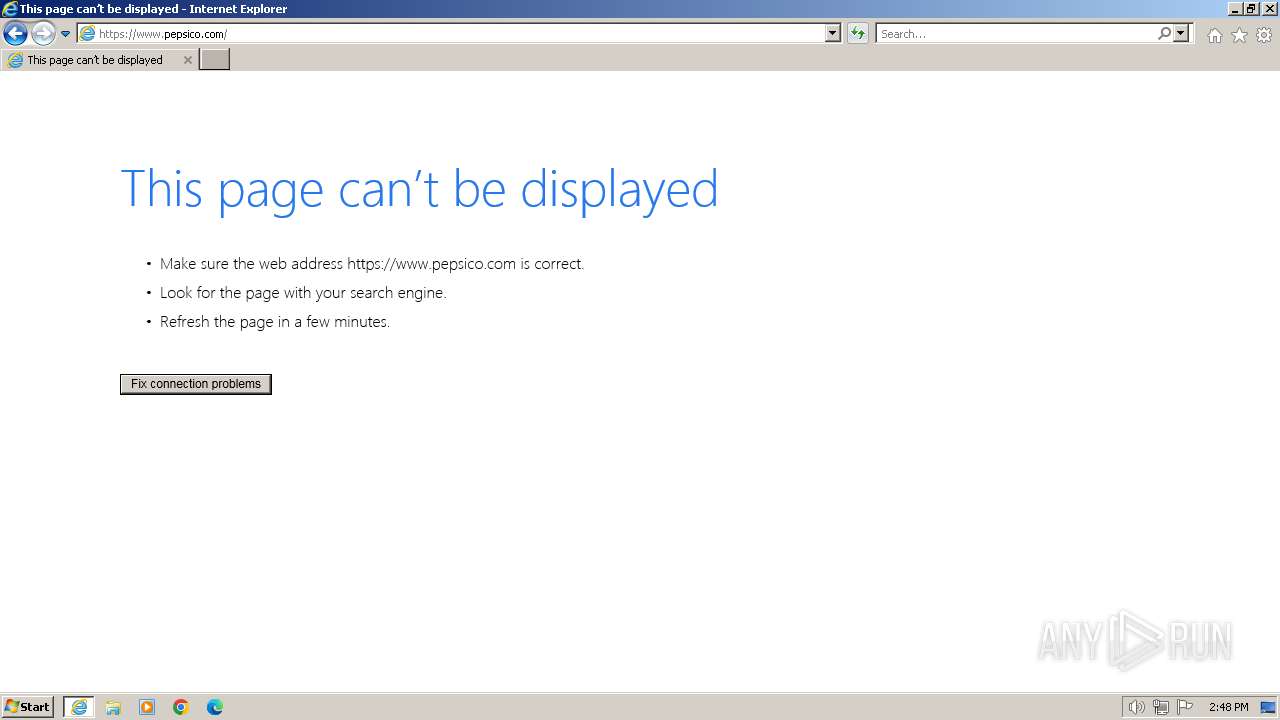
| URL: | https://lnkd.in/eNC_QmKw |
| Full analysis: | https://app.any.run/tasks/07b9171b-01ad-40c0-9163-35c94bef87d2 |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2024, 14:46:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 9F7B38C8103525905EB6D5A2D7C5ED10 |
| SHA1: | 49596913112314195A232DAF3B9A5CC8AE5254F2 |
| SHA256: | 2C72D27ACD75614AA45DBAD88379D7AB711CDED6487613BFE144F5C2AA524F57 |
| SSDEEP: | 3:N8LEM+AyrS:2wmyrS |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- msdt.exe (PID: 2592)
Reads settings of System Certificates
- msdt.exe (PID: 2592)
Uses ROUTE.EXE to obtain the routing table information
- sdiagnhost.exe (PID: 880)
Process uses IPCONFIG to discover network configuration
- sdiagnhost.exe (PID: 880)
Reads the Internet Settings
- sdiagnhost.exe (PID: 880)
INFO
Application launched itself
- iexplore.exe (PID: 3700)
Drops the executable file immediately after the start
- msdt.exe (PID: 2592)
Reads the software policy settings
- msdt.exe (PID: 2592)
Reads security settings of Internet Explorer
- sdiagnhost.exe (PID: 880)
- msdt.exe (PID: 2592)
Create files in a temporary directory
- sdiagnhost.exe (PID: 880)
- makecab.exe (PID: 1232)
- msdt.exe (PID: 2592)
Creates files or folders in the user directory
- msdt.exe (PID: 2592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 880 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | "C:\Windows\system32\makecab.exe" /f NetworkConfiguration.ddf | C:\Windows\System32\makecab.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Cabinet Maker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1728 | "C:\Windows\system32\ROUTE.EXE" print | C:\Windows\System32\ROUTE.EXE | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Route Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2044 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3700 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2592 | -modal 1114548 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDF66DF.tmp -ep NetworkDiagnosticsWeb | C:\Windows\System32\msdt.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2632 | "C:\Windows\system32\ipconfig.exe" /all | C:\Windows\System32\ipconfig.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3700 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://lnkd.in/eNC_QmKw" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
36 234
Read events
36 038
Write events
157
Delete events
39
Modification events
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 418334416 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31090279 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 718490666 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31090279 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
2
Suspicious files
70
Text files
181
Unknown types
41
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\4o8gxtliocwvtgr7owxqs64b5[1].css | text | |
MD5:4EEF9E114DCD0D5E1F48FAF349B3AF51 | SHA256:FF520887F7EE0DA1E2A5FA1717A7AA1831748B822B36B16085A43DDDB4FA1B68 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\eNC_QmKw[1].htm | html | |
MD5:82B1201BABFF257C9706A3078A340AF7 | SHA256:22CEE76B3BBCB86235479BD355BB3F867D65EEFCFF584B24A093C4652C89C6EE | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\al2o9zrvru7aqj8e1x2rzsrca[1].ico | image | |
MD5:B2CCD167C908A44E1DD69DF79382286A | SHA256:19B079C09197FBA68D021FA3BA394EC91703909FFD237EFA3EB9A2BCA13148EC | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:DB82E2C0495E31DB3B3408E27FD40B77 | SHA256:3B6BDAA2C9A126E1B422CC13C4D611262268B091C3BD1E3801BAC976057368A2 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\619jehjlz8c2hgfzs38iftu9q[1].js | text | |
MD5:65F0D3D85F45FB68463D1DD44100757E | SHA256:7F0A6F8C17F6A37286F762EFD17C400A9606274B6A49CF126E6846509C92243F | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\4u3n21bmitzyljlm274yvwzfu[1].svg | image | |
MD5:51B0316726004828C259B06D2E75C26A | SHA256:6CC064CB7FBED0B47B20729EFA6DD968529995C7E2B2CB3E79F52DB512FF75E4 | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:C9E698F4208D83CB2FCF21C47316BBDD | SHA256:5B1CBD5CBDE0DCE1AE75216A75EE6ED44E4954787E7AEF8CF3E9DD1FB9664DAE | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
126
DNS requests
36
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2044 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c70275e956f241e7 | unknown | — | — | unknown |
2044 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3700 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a973ebecfe8ccbeb | unknown | — | — | unknown |
3700 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4dd617501e33218a | unknown | — | — | unknown |
2044 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?927e0d673a39dd41 | unknown | — | — | unknown |
3700 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
2044 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
2044 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCRs%2Fkp3S0EjBKeXx2SMJsz | unknown | binary | 472 b | unknown |
2044 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC5pxuh%2BtX0xxBQ9RoUHy9Y | unknown | binary | 472 b | unknown |
2044 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCBMXTZnnaYAQkPx5X6giGI | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2044 | iexplore.exe | 13.107.42.14:443 | lnkd.in | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2044 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2044 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2044 | iexplore.exe | 152.199.21.118:443 | static.licdn.com | EDGECAST | US | unknown |
3700 | iexplore.exe | 152.199.21.118:443 | static.licdn.com | EDGECAST | US | unknown |
3700 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3700 | iexplore.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
lnkd.in |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
static.licdn.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
homeremediesrd.blogspot.com |
| unknown |
ocsp.pki.goog |
| whitelisted |
www.blogger.com |
| shared |
fonts.googleapis.com |
| whitelisted |