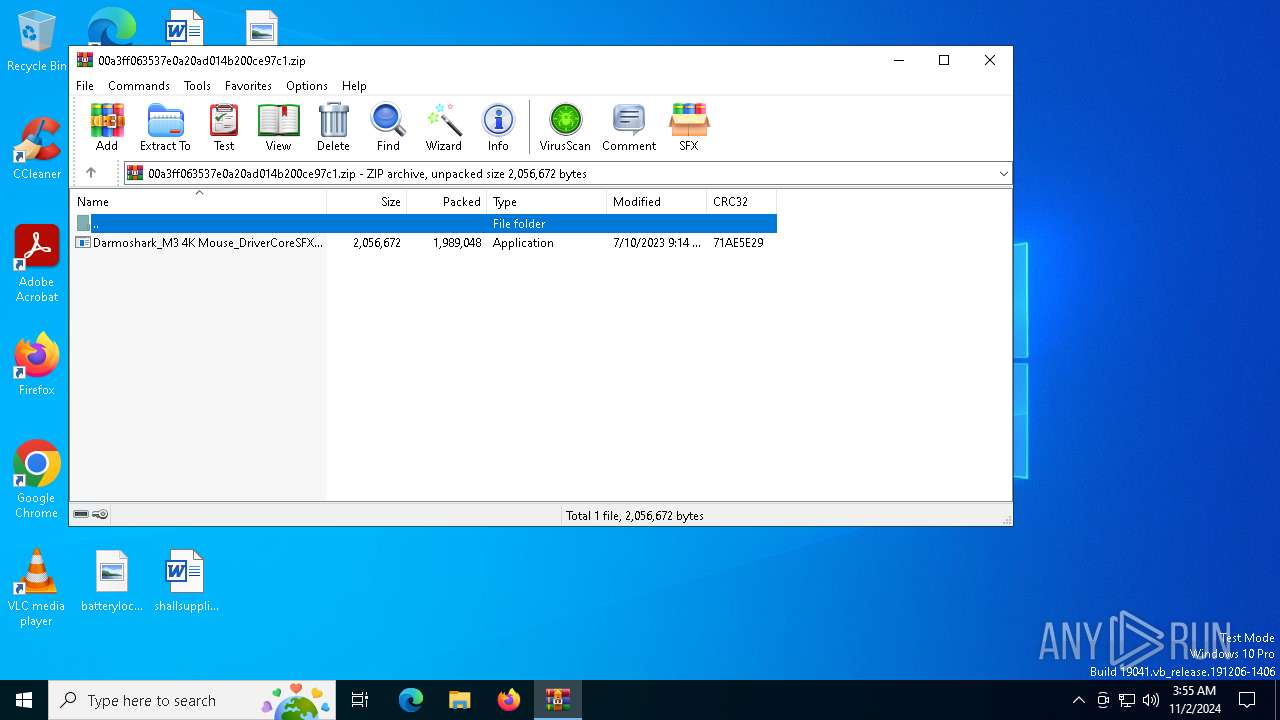
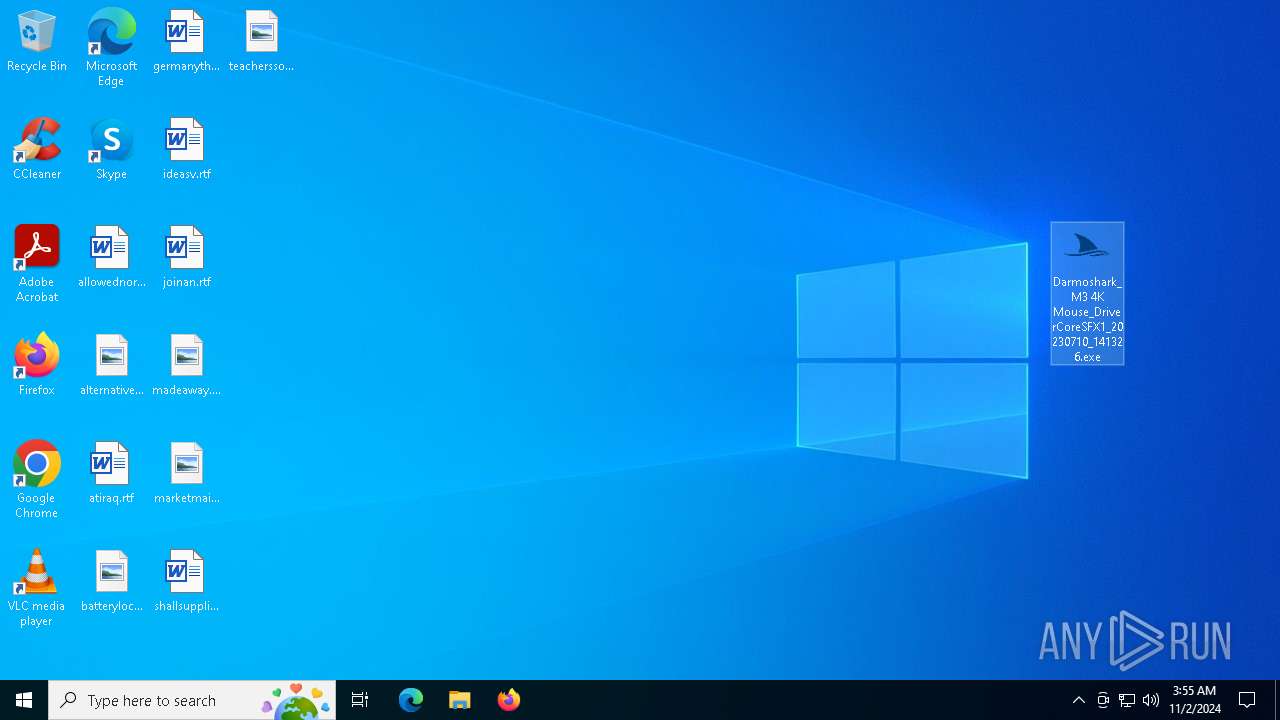
| File name: | 00a3ff063537e0a20ad014b200ce97c1.zip |
| Full analysis: | https://app.any.run/tasks/4487fc6d-5132-45e5-b2ba-4795d5fb7ae4 |
| Verdict: | Malicious activity |
| Analysis date: | November 02, 2024, 03:55:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C536D36773773242141FF38AB049E3B2 |
| SHA1: | 5A9997F5A86523A8441830720EAF50EDFB07FB9F |
| SHA256: | 2C597E3D6F692E9CAD4632F1685E3FF6F5A1AA23E7CBA64F7296F6AD273A9E32 |
| SSDEEP: | 98304:skzzs0LwDsbdBRaKxZkRA3szBDecUsSPdjS/wnCtPYeJ/kQP7QJu79Gd4jyXe/S2:bL1M |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6160)
SUSPICIOUS
Reads security settings of Internet Explorer
- DriverCore.exe (PID: 512)
- DriverCore.exe (PID: 4088)
- DriverCore.exe (PID: 5652)
- Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe (PID: 6668)
Checks Windows Trust Settings
- DriverCore.exe (PID: 512)
- DriverCore.exe (PID: 4088)
- DriverCore.exe (PID: 5652)
Executable content was dropped or overwritten
- Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe (PID: 6668)
INFO
Checks supported languages
- Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe (PID: 6668)
- DriverCore.exe (PID: 512)
- DriverCore.exe (PID: 4088)
- DriverCore.exe (PID: 5652)
The process uses the downloaded file
- WinRAR.exe (PID: 6160)
- DriverCore.exe (PID: 512)
- WinRAR.exe (PID: 6124)
- DriverCore.exe (PID: 4088)
- DriverCore.exe (PID: 5652)
- Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe (PID: 6668)
Reads the machine GUID from the registry
- DriverCore.exe (PID: 512)
- DriverCore.exe (PID: 4088)
- DriverCore.exe (PID: 5652)
Reads the software policy settings
- DriverCore.exe (PID: 512)
- DriverCore.exe (PID: 4088)
- DriverCore.exe (PID: 5652)
- slui.exe (PID: 3620)
Checks proxy server information
- DriverCore.exe (PID: 512)
Reads the computer name
- DriverCore.exe (PID: 512)
- DriverCore.exe (PID: 4088)
- DriverCore.exe (PID: 5652)
- Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe (PID: 6668)
Creates files or folders in the user directory
- DriverCore.exe (PID: 512)
- DriverCore.exe (PID: 4088)
Manual execution by a user
- Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe (PID: 6668)
- WinRAR.exe (PID: 6124)
- DriverCore.exe (PID: 4088)
- notepad.exe (PID: 6276)
- DriverCore.exe (PID: 5652)
- notepad.exe (PID: 6372)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6160)
- WinRAR.exe (PID: 6124)
.NET Reactor protector has been detected
- DriverCore.exe (PID: 512)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6276)
- notepad.exe (PID: 6372)
Create files in a temporary directory
- Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe (PID: 6668)
Process checks computer location settings
- Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe (PID: 6668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:07:10 17:14:32 |
| ZipCRC: | 0x71ae5e29 |
| ZipCompressedSize: | 1989048 |
| ZipUncompressedSize: | 2056672 |
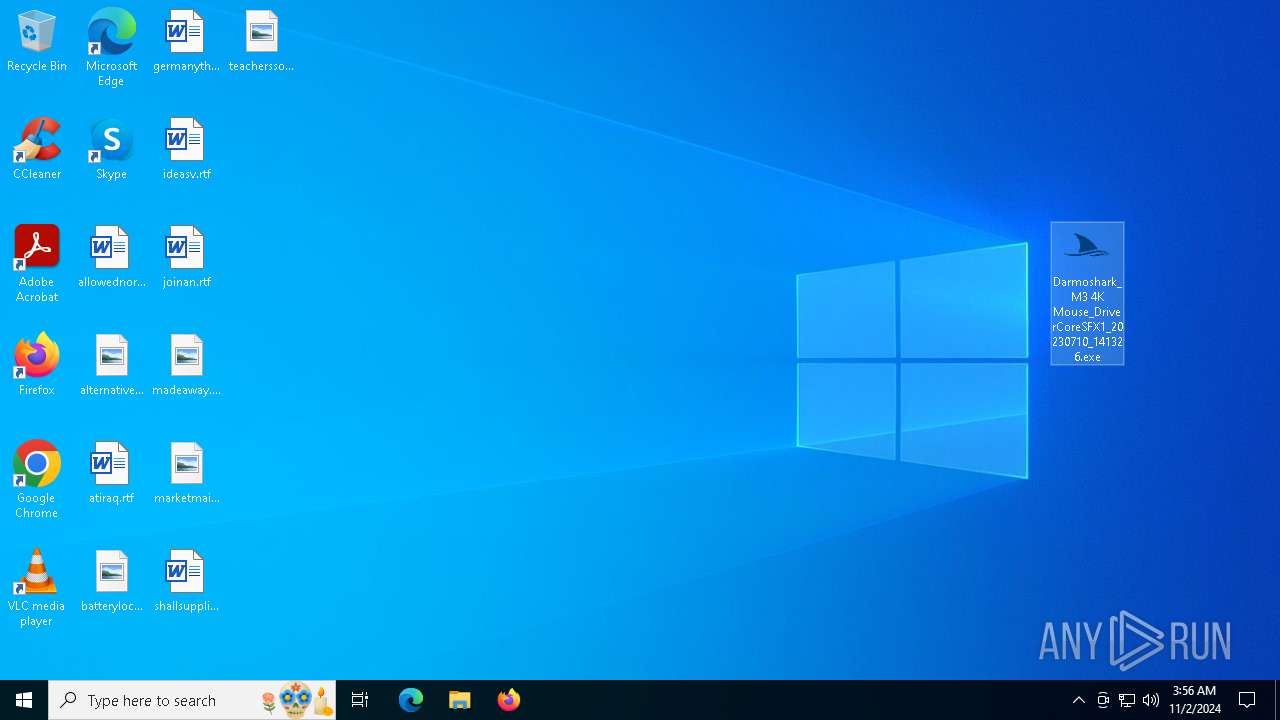
| ZipFileName: | Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe |
Total processes
145
Monitored processes
12
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
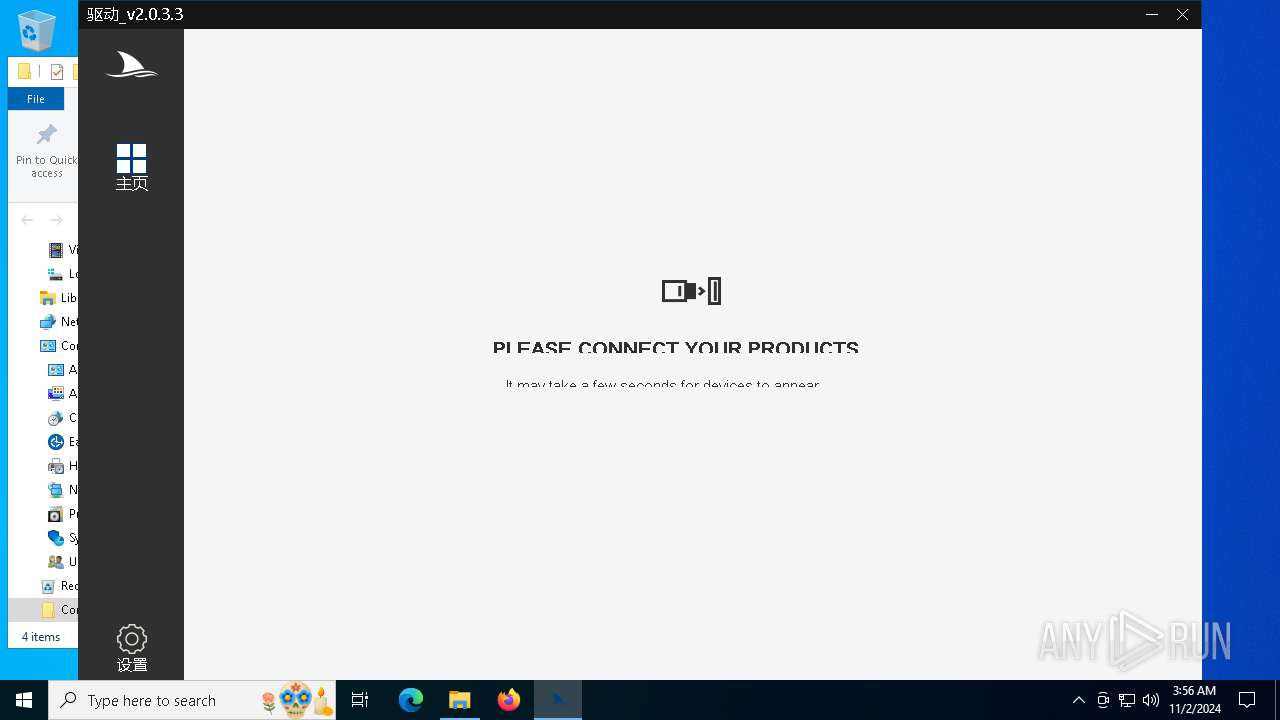
| 512 | "C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\DriverCore.exe" | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\DriverCore.exe | Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: DriverCore Exit code: 0 Version: 2.0.3.3 Modules
| |||||||||||||||
| 1112 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4072 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4088 | "C:\Users\admin\Desktop\DriverCore.exe" | C:\Users\admin\Desktop\DriverCore.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: DriverCore Exit code: 0 Version: 2.0.3.3 Modules
| |||||||||||||||
| 5652 | "C:\Users\admin\Desktop\DriverCore.exe" | C:\Users\admin\Desktop\DriverCore.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: DriverCore Exit code: 0 Version: 2.0.3.3 Modules
| |||||||||||||||
| 6124 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6160 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\00a3ff063537e0a20ad014b200ce97c1.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6276 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Config\Language.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6372 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Config\Darmoshark\Language.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 131
Read events
14 098
Write events
33
Delete events
0
Modification events
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\00a3ff063537e0a20ad014b200ce97c1.zip | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
3
Suspicious files
6
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6668 | Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Config\Darmoshark\CompanyName.png | image | |
MD5:9C43DB4D4C24519AC1F3E4A4318DD195 | SHA256:6B5DAD5FBBA0B267DCAD88FA15FB4B2490C633B276245ED8D83BC34DB2D4C6F0 | |||
| 6668 | Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Config\Darmoshark\Device.png | image | |
MD5:827D2E9569246E9FA3FE5110A932926B | SHA256:03C2F5F05149865D4F3C2A25395C65B85CB36A6D5AB3808FB08BBA7DC5B27AA8 | |||
| 6160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6160.6618\Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe | executable | |
MD5:B39CFBA9EC6E827EBAA23A0279A3D93F | SHA256:8434FC20A3C51D36B88EEC7299D13E00255DD8A2BCF93B71955CED03ABB01E02 | |||
| 6668 | Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Config\Darmoshark\PairMouse.png | image | |
MD5:0B27AC2F806BCEDEBE09F2F8B03113BC | SHA256:41FC9D117185BAE3BA0FA3BBA47806599D8A03C762CA9DC1D6422E8CE45DF0E8 | |||
| 6668 | Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Config\Darmoshark\Home.png | image | |
MD5:A12809FB34938368EA352BD2EA25E881 | SHA256:8FA9BB1185BE393E0755D580DFC4FE72FC716E2D9A5BA1BCC86FA85F88A20A56 | |||
| 6668 | Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Config\新文字文件.txt | text | |
MD5:9A674C366B091626A8AB9E3705668481 | SHA256:1C1EA6DDE4FB9FA17DAAAE71373DC4415E1578A78E1BB447B792A03816FD5BC7 | |||
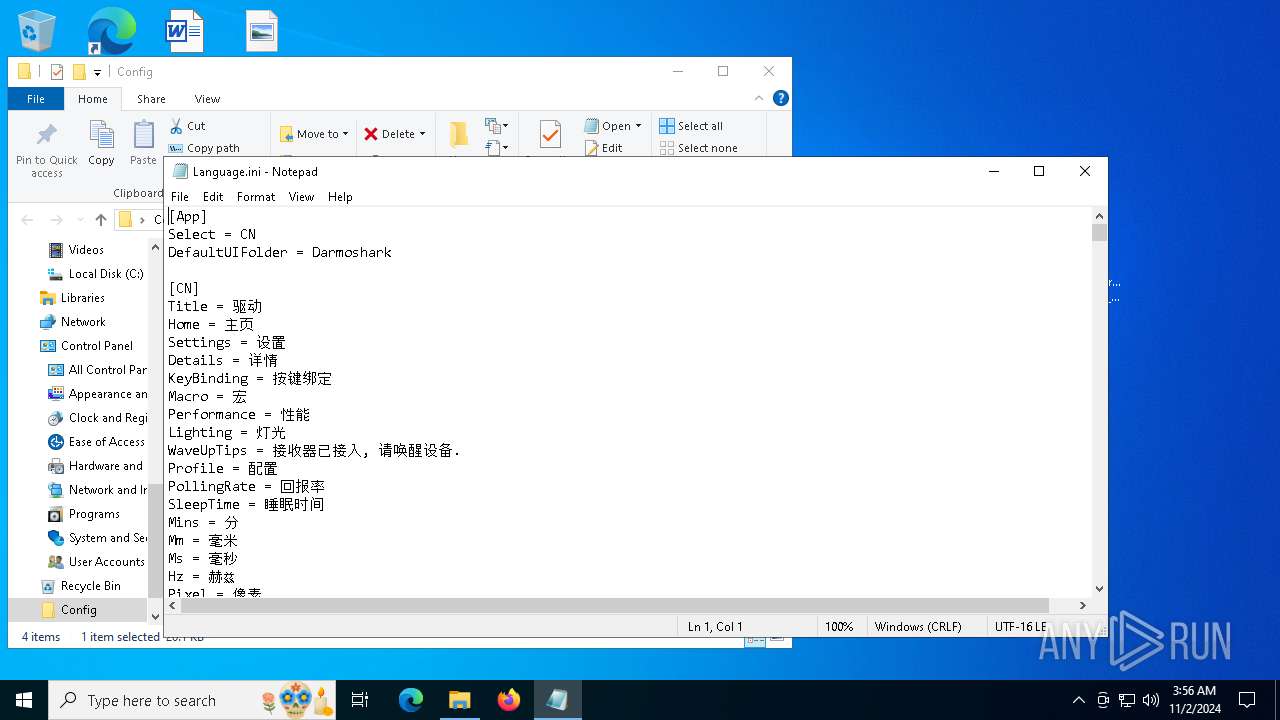
| 6668 | Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Config\Darmoshark\Language.ini | text | |
MD5:E2B73DB414364F9F1D20858A34FA45EA | SHA256:8EC03698C4691079C0DC1E3C2CFA2E32474F65428CC63453AF74CDFD0E9DF1A8 | |||
| 6668 | Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Config\Darmoshark\SettingsSelect.png | image | |
MD5:4BED0813879631F9EE2C30FE4F0A4CC0 | SHA256:51284F237BC25A73D1F23185ABC0A85B0F98ABE2C2E724146CEE158A3822024B | |||
| 6668 | Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Config\Darmoshark\Device_Key.png | image | |
MD5:96D39EB82E705D1C77D2D1AB0220FC55 | SHA256:51DFC6FCA0B12BD0A84C98328D25FC677865E6A4D367B1EBD7406255844AE7AD | |||
| 6668 | Darmoshark_M3 4K Mouse_DriverCoreSFX1_20230710_141326.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Config\Darmoshark\LogoMain.ico | image | |
MD5:EB0722BA5F4E9C2081AD7521D31AA774 | SHA256:E00455A806A74C7CF0EA0CA5C5C33151EB3BA847558FD53AAFCF74BF7466778C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
39
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
512 | DriverCore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
5652 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
512 | DriverCore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDF0RJpUmRfSXRvUW%2BQ%3D%3D | unknown | — | — | whitelisted |
3764 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
624 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5652 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1752 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4360 | SearchApp.exe | 2.16.110.121:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
512 | DriverCore.exe | 104.18.21.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |