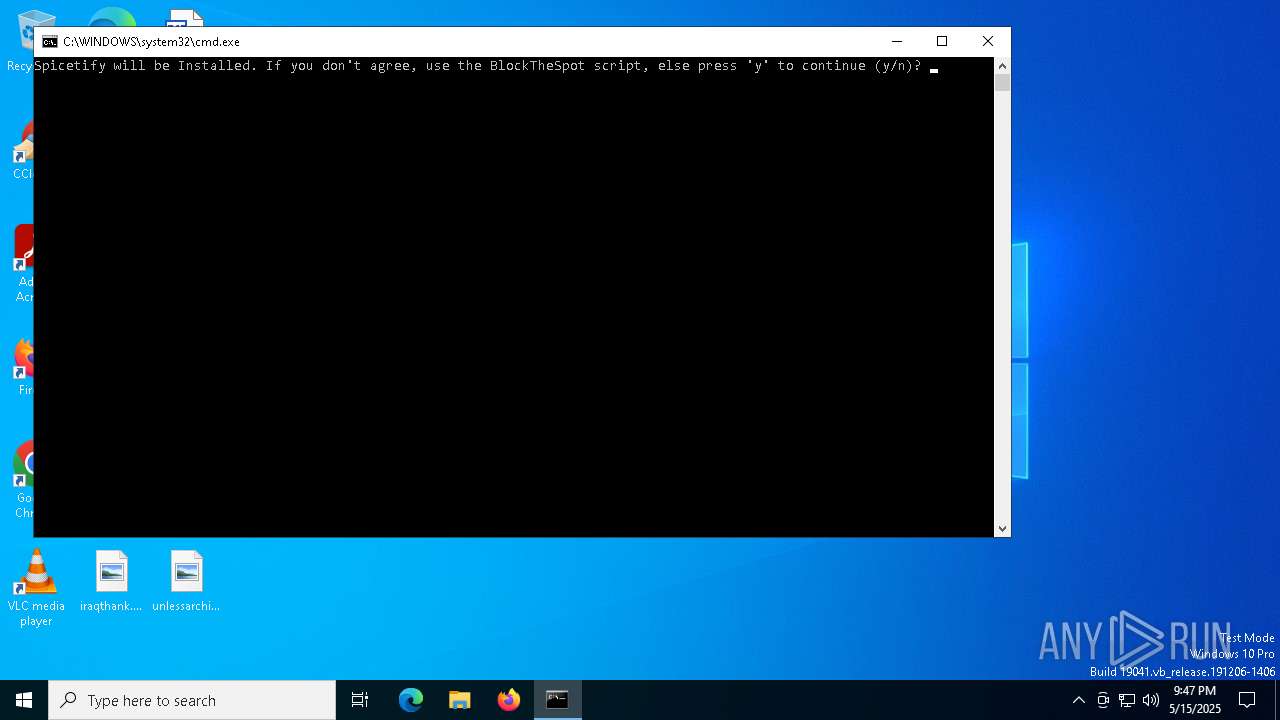
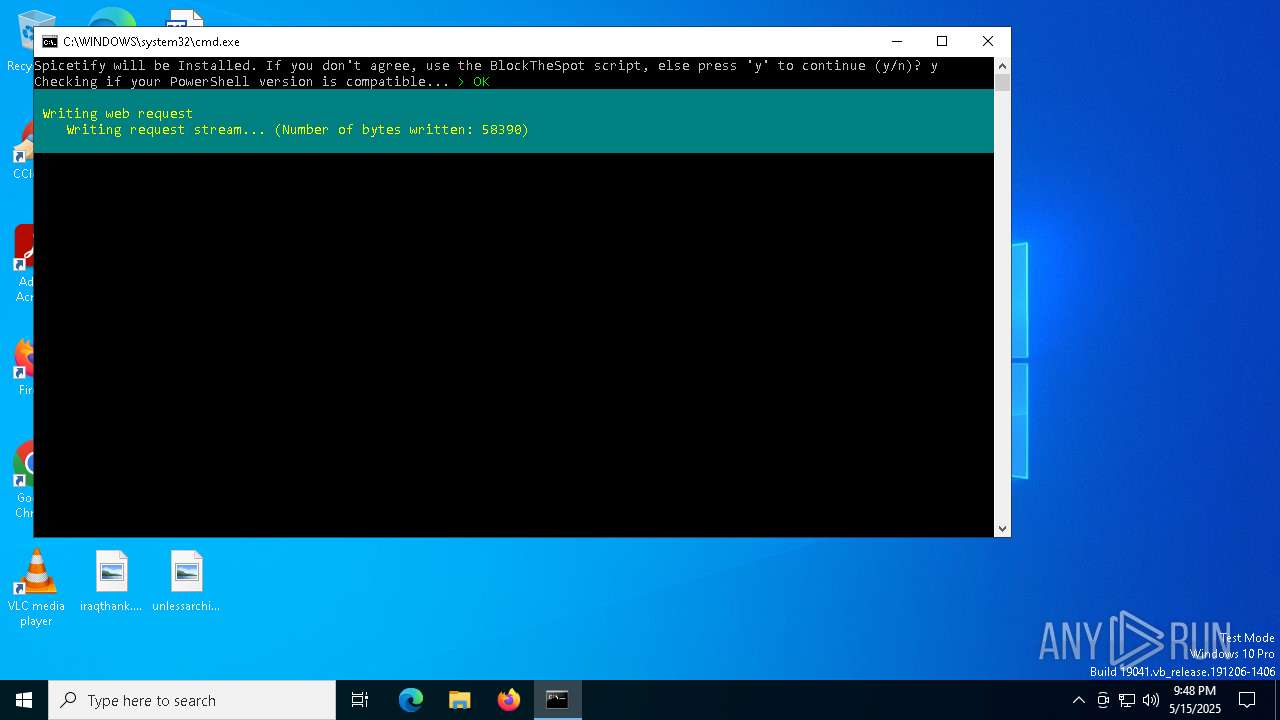
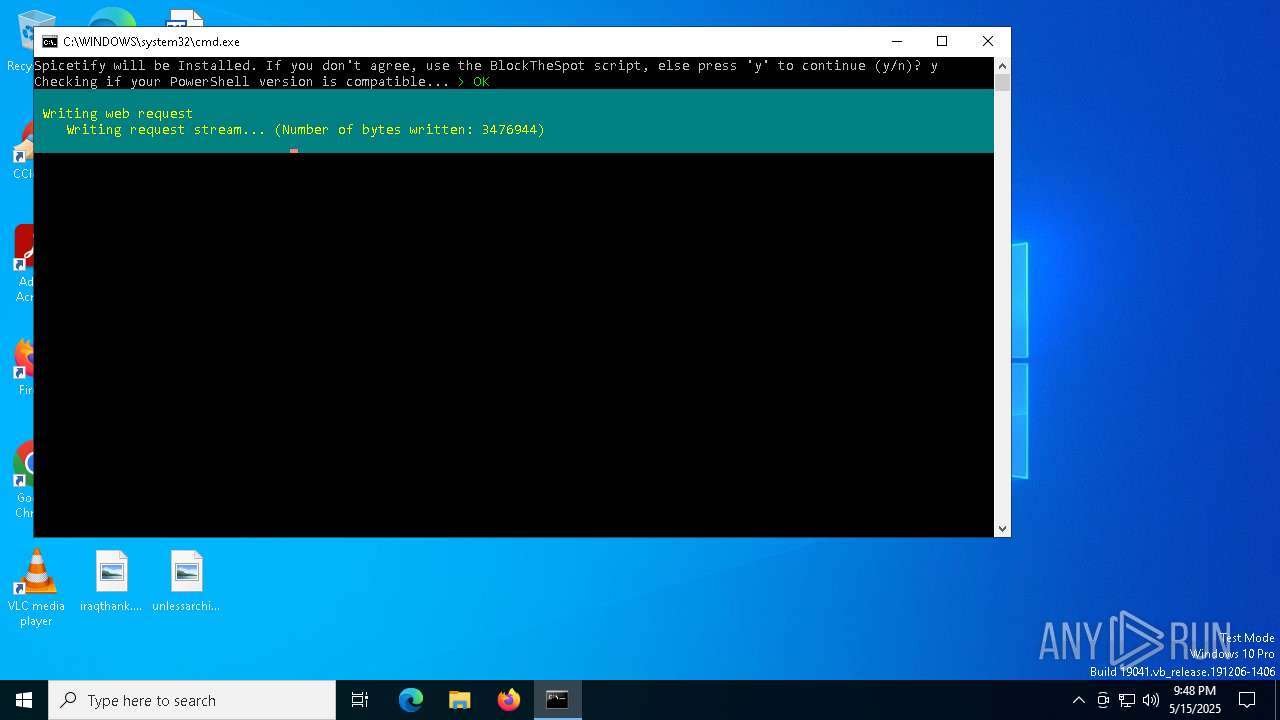
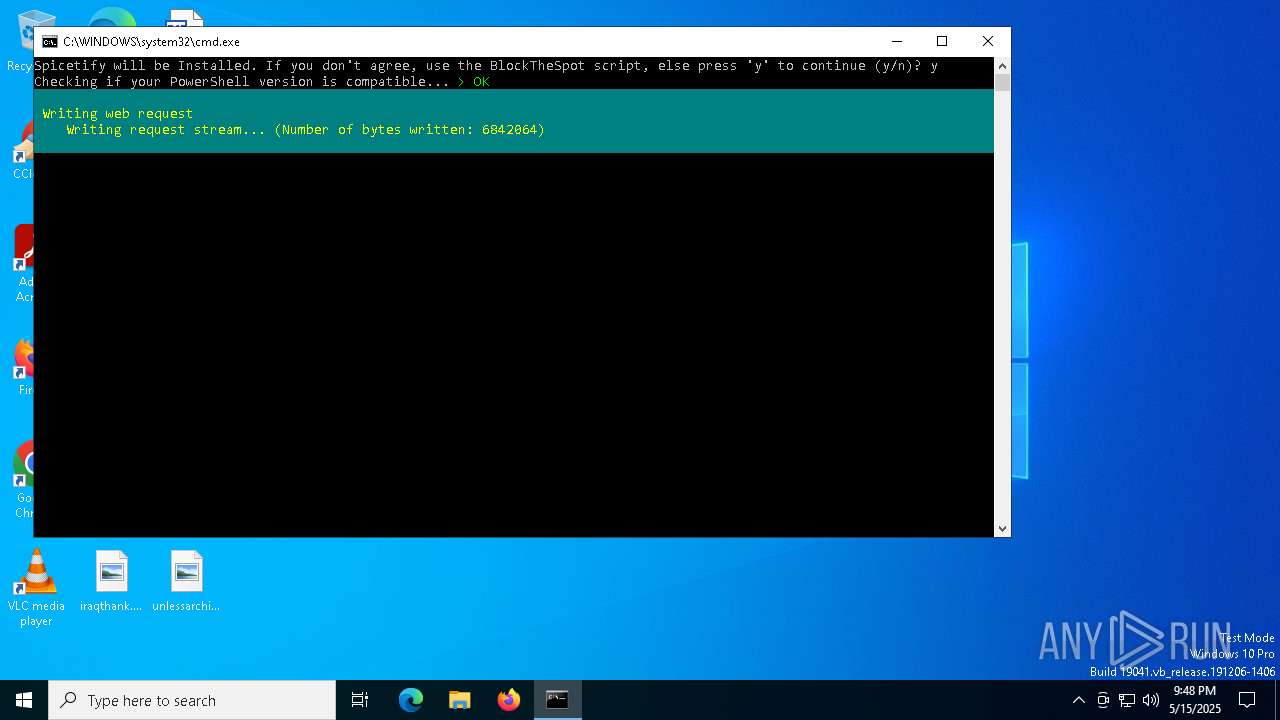
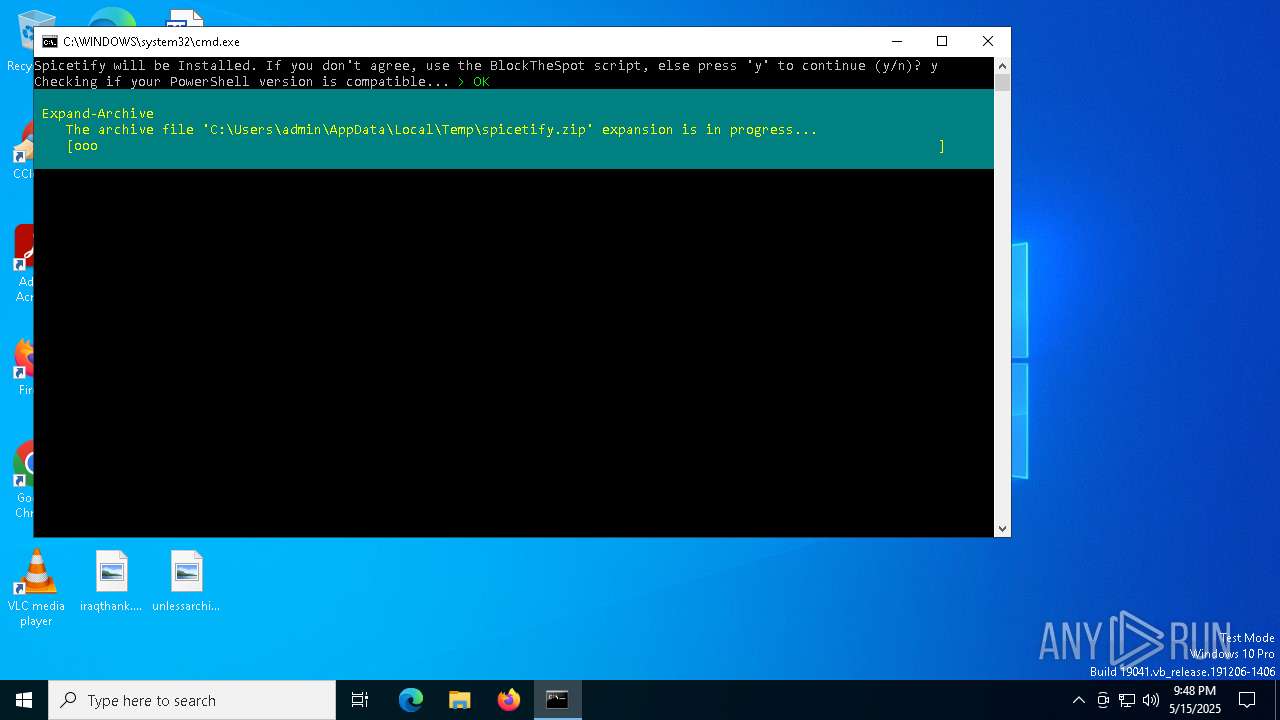
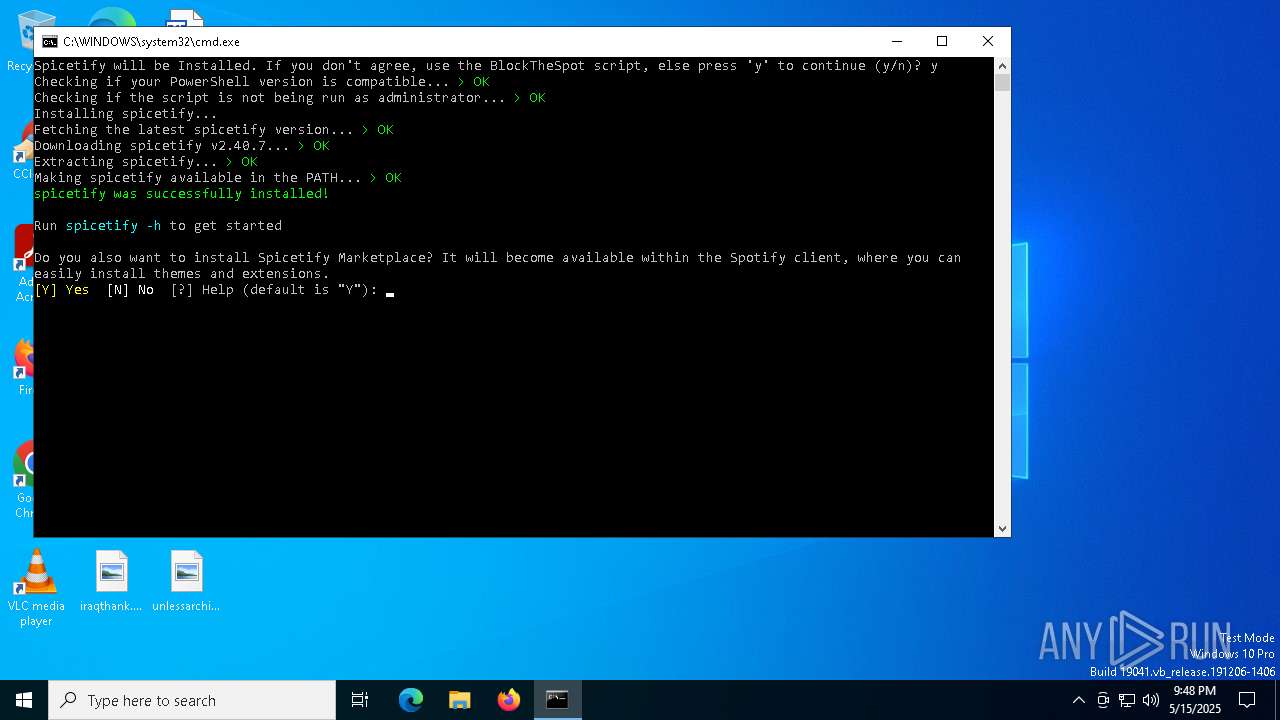
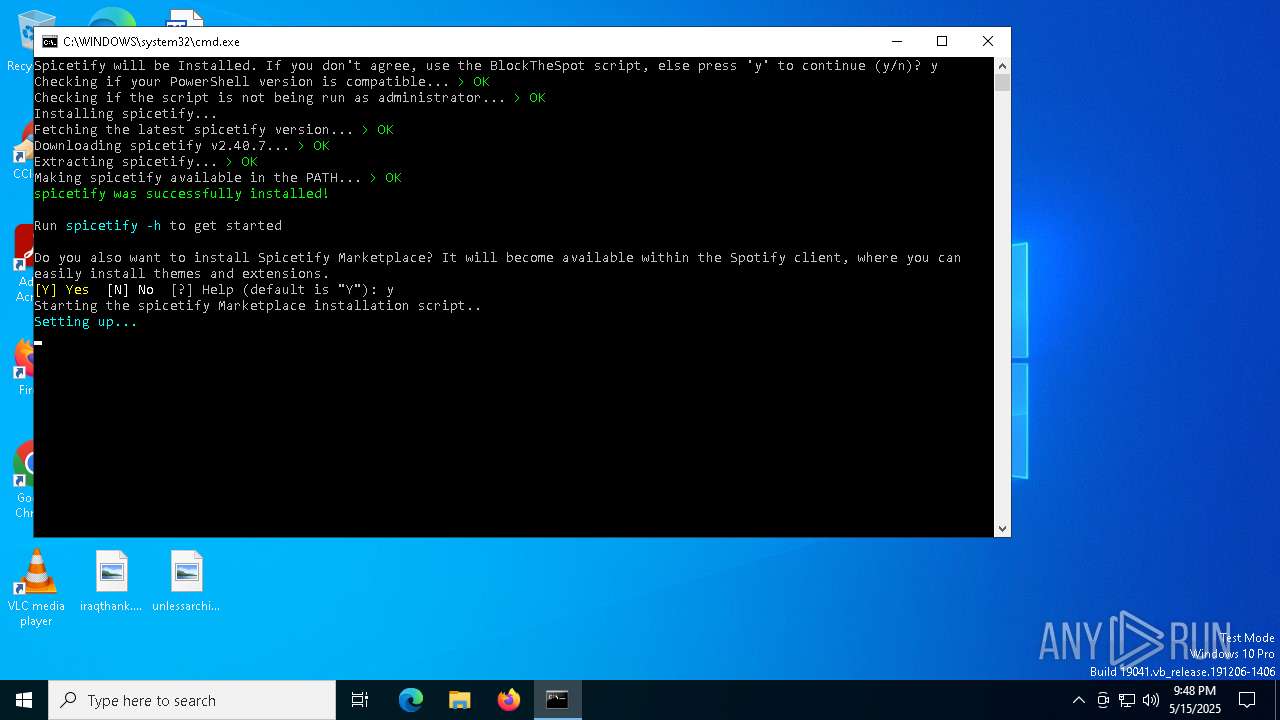
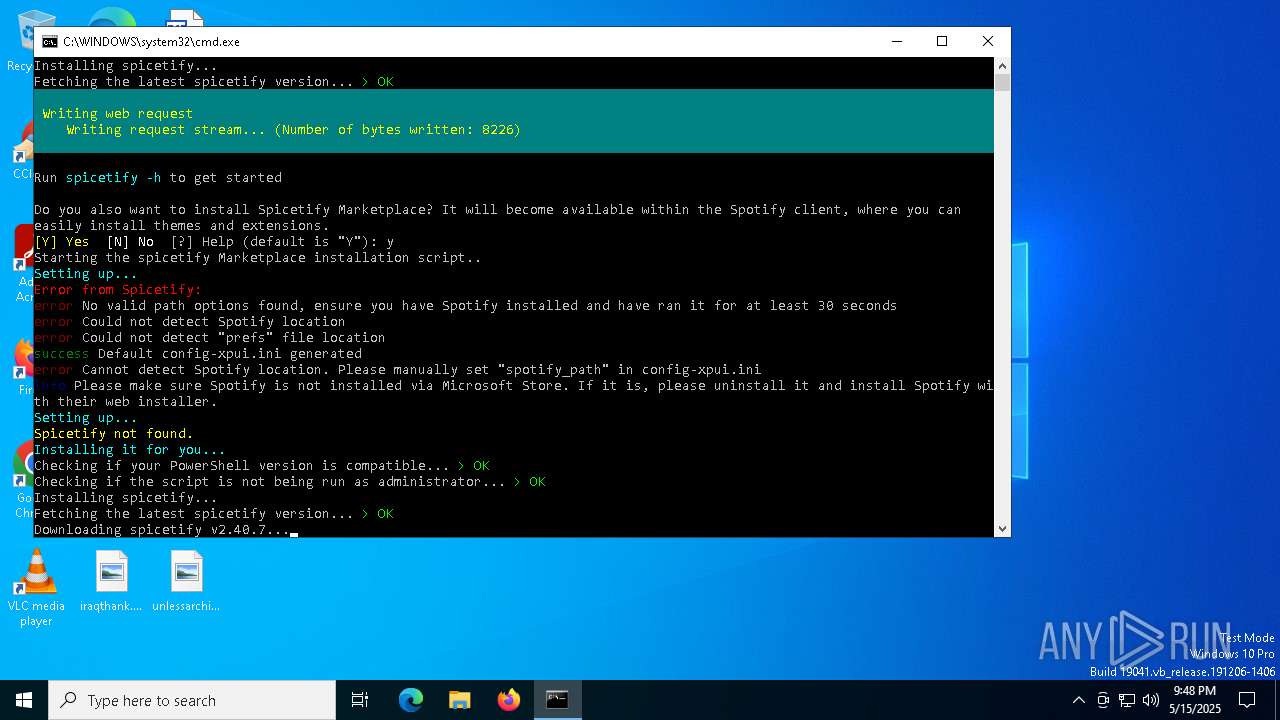
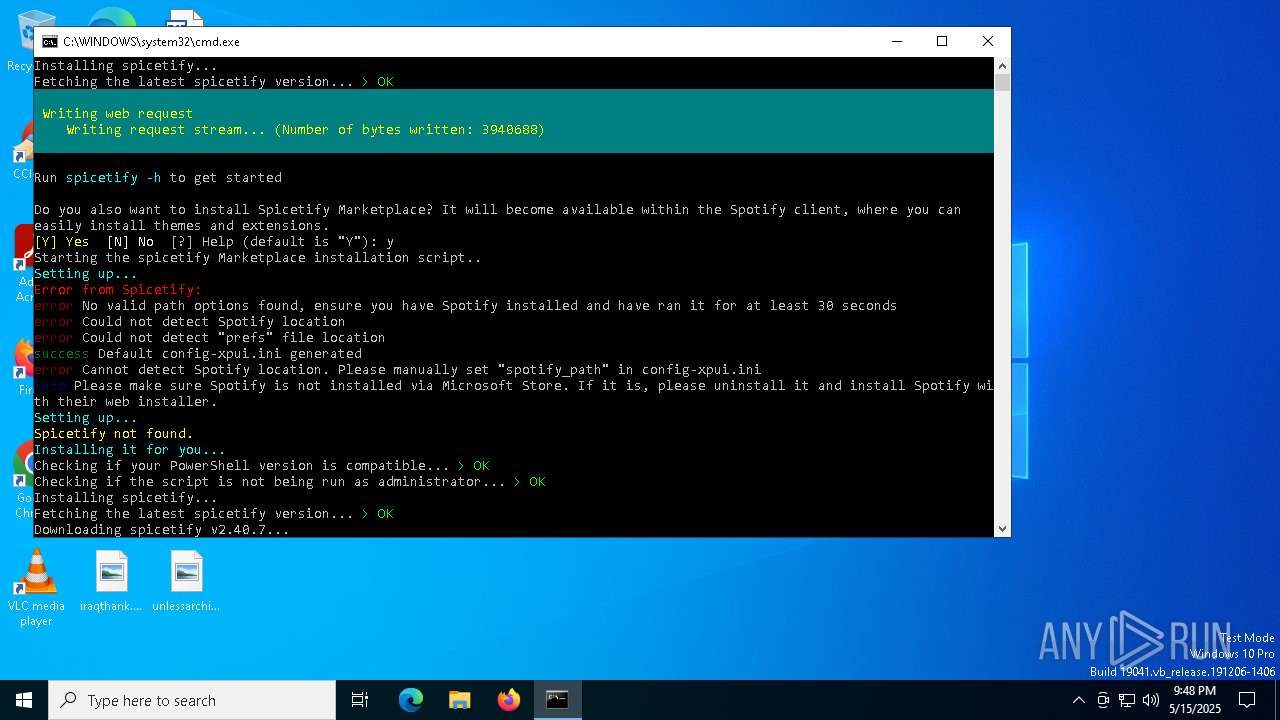
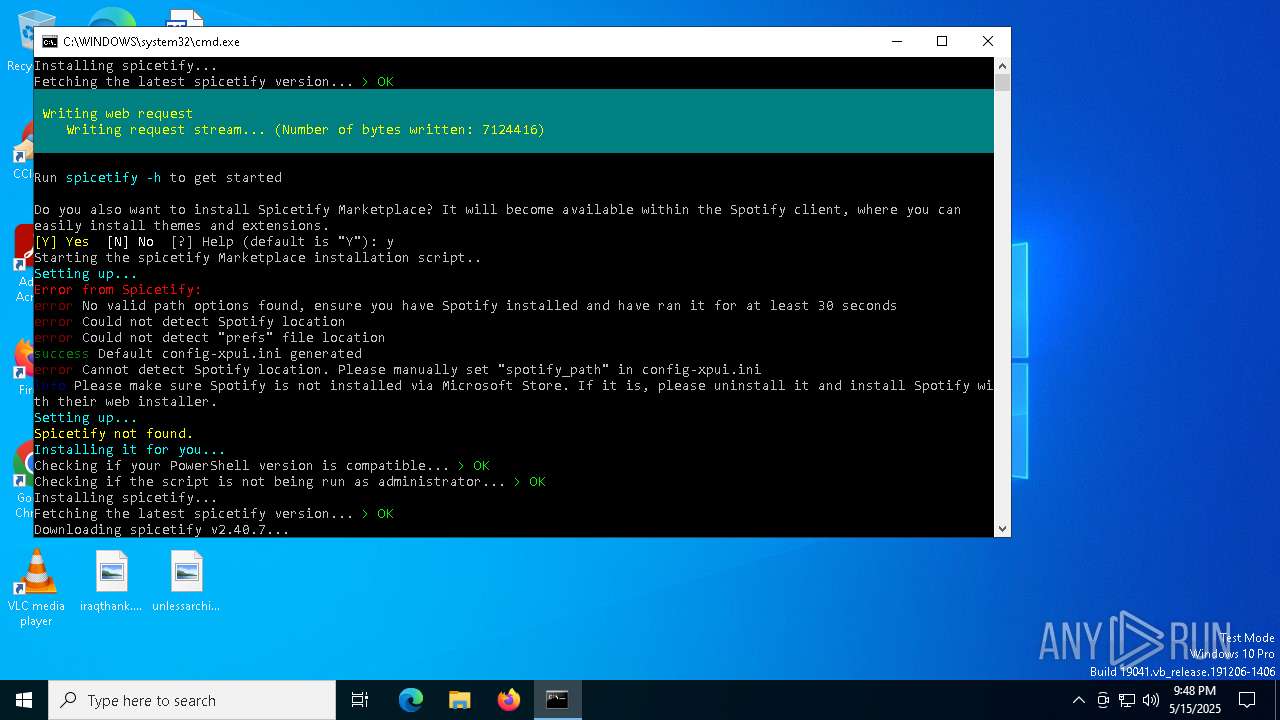
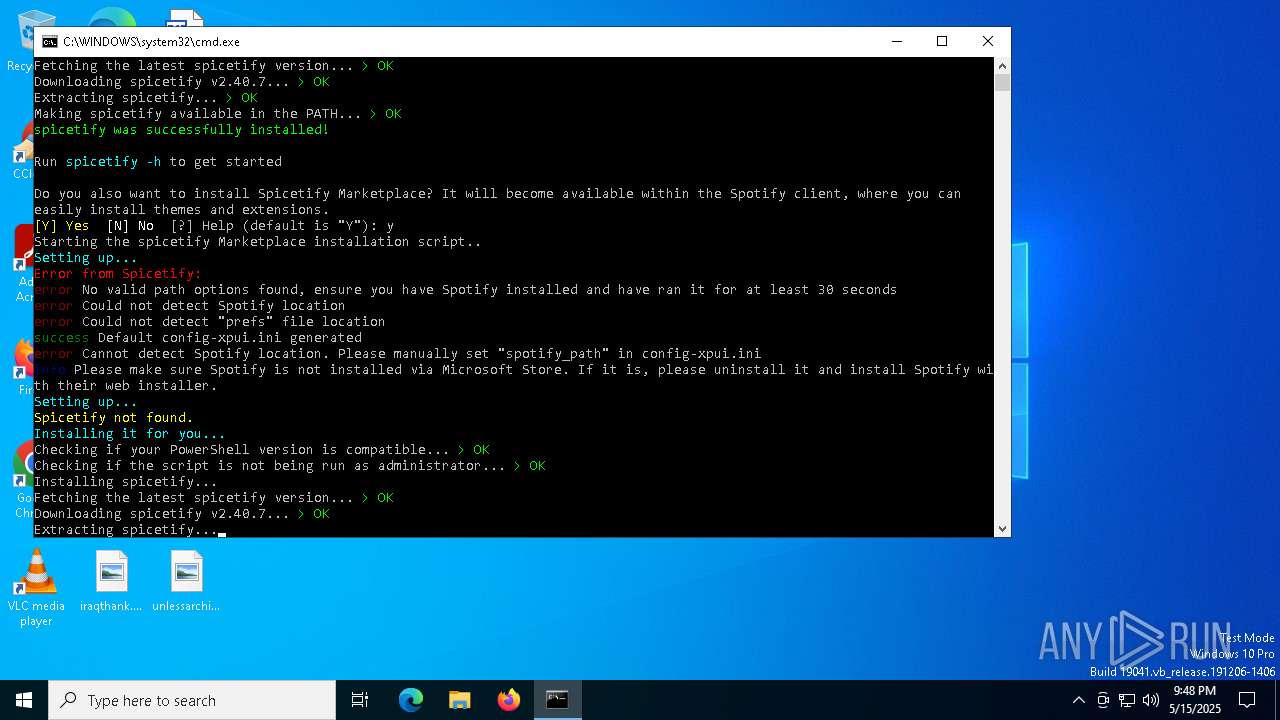
| File name: | BlockTheSpot + Spicetify.bat |
| Full analysis: | https://app.any.run/tasks/80e7b8e0-e9b1-482a-99ee-8b78a54b0c93 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 21:47:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text |
| MD5: | 163D734662B67321FDDC9487398C93C5 |
| SHA1: | E440ACE29746D6A0E03383E2A2C281EF2C5DA879 |
| SHA256: | 2C51881DAAC7D5991FA0EDBD19595161D2E132DB9BE56B3C97E5C3C05CA28D4B |
| SSDEEP: | 12:lFHCxg9E6AYRA8L68p8QxdMGeGb8QxdMGkQsib892im6KbGuz0MGqS0qRN9p2W:+MvAYRDxzMGeQMGk/vHuYMGVdpf |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5216)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 5216)
Downloads file from URI via Powershell
- powershell.exe (PID: 6656)
- powershell.exe (PID: 3008)
The process executes Powershell scripts
- cmd.exe (PID: 5216)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 6656)
- powershell.exe (PID: 3008)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6656)
- powershell.exe (PID: 3008)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6656)
- powershell.exe (PID: 3008)
Executable content was dropped or overwritten
- powershell.exe (PID: 6656)
- powershell.exe (PID: 3008)
INFO
Disables trace logs
- powershell.exe (PID: 6656)
- powershell.exe (PID: 3008)
Checks proxy server information
- powershell.exe (PID: 6656)
- powershell.exe (PID: 3008)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6656)
- powershell.exe (PID: 3008)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6656)
- powershell.exe (PID: 3008)
The executable file from the user directory is run by the Powershell process
- spicetify.exe (PID: 1096)
Checks supported languages
- spicetify.exe (PID: 1096)
Creates files or folders in the user directory
- spicetify.exe (PID: 1096)
Drops encrypted JS script (Microsoft Script Encoder)
- spicetify.exe (PID: 1096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
134
Monitored processes
7
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1096 | "C:\Users\admin\AppData\Local\spicetify\spicetify.exe" path userdata | C:\Users\admin\AppData\Local\spicetify\spicetify.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1452 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3008 | powershell -Command "& {iwr -useb https://raw.githubusercontent.com/spicetify/spicetify-marketplace/main/resources/install.ps1 | iex}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5216 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\BlockTheSpot + Spicetify.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5508 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6476 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6656 | powershell -Command "& {iwr -useb https://raw.githubusercontent.com/spicetify/spicetify-cli/master/install.ps1 | iex}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 791
Read events
14 789
Write events
2
Delete events
0
Modification events
| (PID) Process: | (6656) powershell.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | PATH |
Value: C:\Users\admin\AppData\Local\Microsoft\WindowsApps;;C:\Users\admin\AppData\Local\spicetify | |||
| (PID) Process: | (3008) powershell.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | PATH |
Value: C:\Users\admin\AppData\Local\Microsoft\WindowsApps;;C:\Users\admin\AppData\Local\spicetify | |||
Executable files
3
Suspicious files
46
Text files
72
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6656 | powershell.exe | C:\Users\admin\AppData\Local\spicetify\CustomApps\lyrics-plus\README.md | text | |
MD5:790D3B6330796628F50D5F958CBBEB6B | SHA256:117135D3941898EAE2B07DB20F736E9E33EFCFCA4B88BBFBE538E9349A55CB31 | |||
| 6656 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_25dzvxrt.wiv.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6656 | powershell.exe | C:\Users\admin\AppData\Local\spicetify\CustomApps\lyrics-plus\Pages.js | binary | |
MD5:172DADB78CFD1615E891353994ED9589 | SHA256:CAE91DE0286CEAC14D5691A6A650D2AEFD7437A5FB275729B17FC3E7E3433A83 | |||
| 6656 | powershell.exe | C:\Users\admin\AppData\Local\spicetify\CustomApps\lyrics-plus\PlaybarButton.js | binary | |
MD5:1242A489D729283BD99C6C86DD4176FA | SHA256:406503572D7F6B22F19EBF2FC3431E776481FB18A74EB861A80AD7FE64BC0DF8 | |||
| 6656 | powershell.exe | C:\Users\admin\AppData\Local\spicetify\CustomApps\lyrics-plus\OptionsMenu.js | text | |
MD5:2518ABD5C46C897004D1C0BA12439E3B | SHA256:A400BE927EA3044E95E430D80267C9836A306CD8B9E08E541F726D7A6B76E5BF | |||
| 6656 | powershell.exe | C:\Users\admin\AppData\Local\Temp\spicetify.zip | compressed | |
MD5:A0F1E456E92FFAA1CF4D1A97CACC3A57 | SHA256:57699A39AF6D7C4326A2A1C30BE84C7E11142013CD9689870EE84C8854FC74EC | |||
| 6656 | powershell.exe | C:\Users\admin\AppData\Local\spicetify\CustomApps\lyrics-plus\ProviderLRCLIB.js | text | |
MD5:780D2755EF8C2BE3A108B0CE99E54C72 | SHA256:FB1992A45CB0640A34A409DA175DAF3ADE008FE9FC91460EC4A96D777D3CCB47 | |||
| 6656 | powershell.exe | C:\Users\admin\AppData\Local\spicetify\CustomApps\lyrics-plus\ProviderGenius.js | binary | |
MD5:63E4B78751B237369698F40046CC5E64 | SHA256:215170647CAC2A02763CC7776C74F45F478EB7E666F0EF8F5EA4FFB41C321959 | |||
| 6656 | powershell.exe | C:\Users\admin\AppData\Local\spicetify\CustomApps\lyrics-plus\ProviderMusixmatch.js | text | |
MD5:BE555AEA1D6665E43B9FB46B29D00145 | SHA256:EA54604F9CC9CC0DE5FF179F6660A93661FCD19F0D009B52337E200F8AB6901C | |||
| 6656 | powershell.exe | C:\Users\admin\AppData\Local\spicetify\CustomApps\lyrics-plus\ProviderNetease.js | text | |
MD5:7E9B924A597D8E06AEADF38A771AF064 | SHA256:12E45D81999CEDFC063452ED6B929E1D0301726A5566936768377A10B718C5AE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
29
DNS requests
19
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.22:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.22:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6132 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6132 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.22:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.216.77.22:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
api.github.com |
| whitelisted |
github.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |