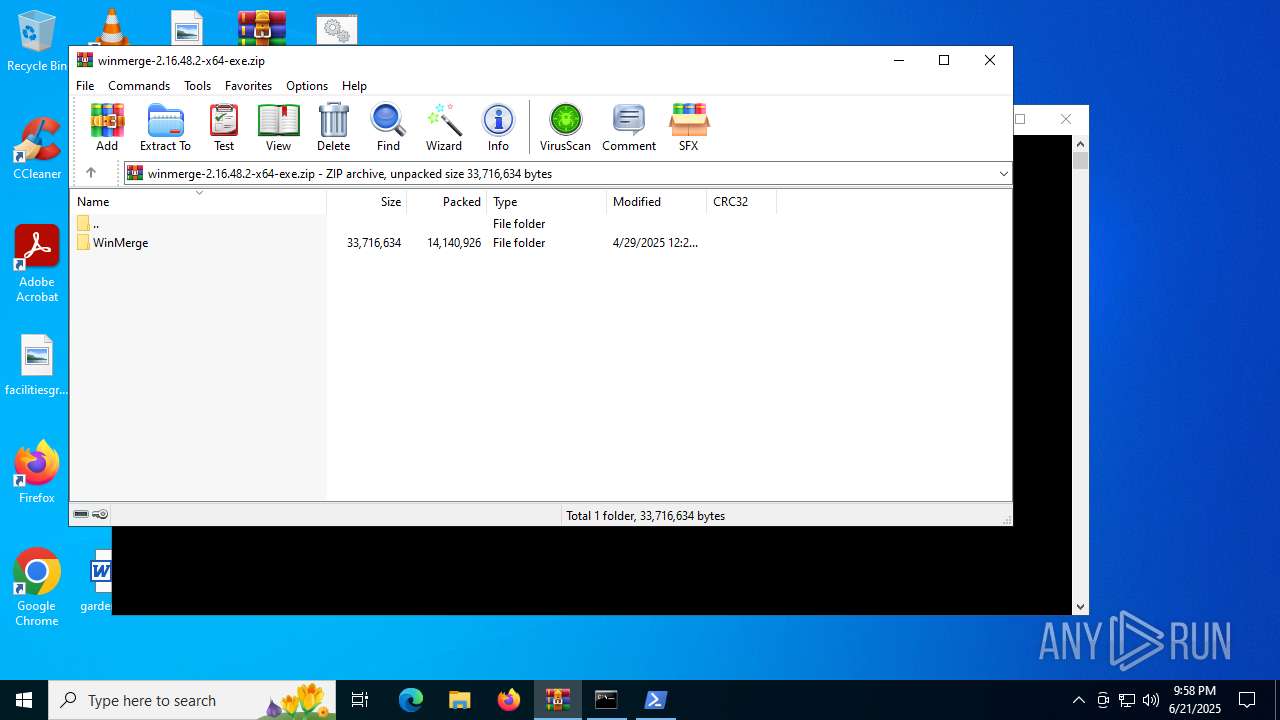
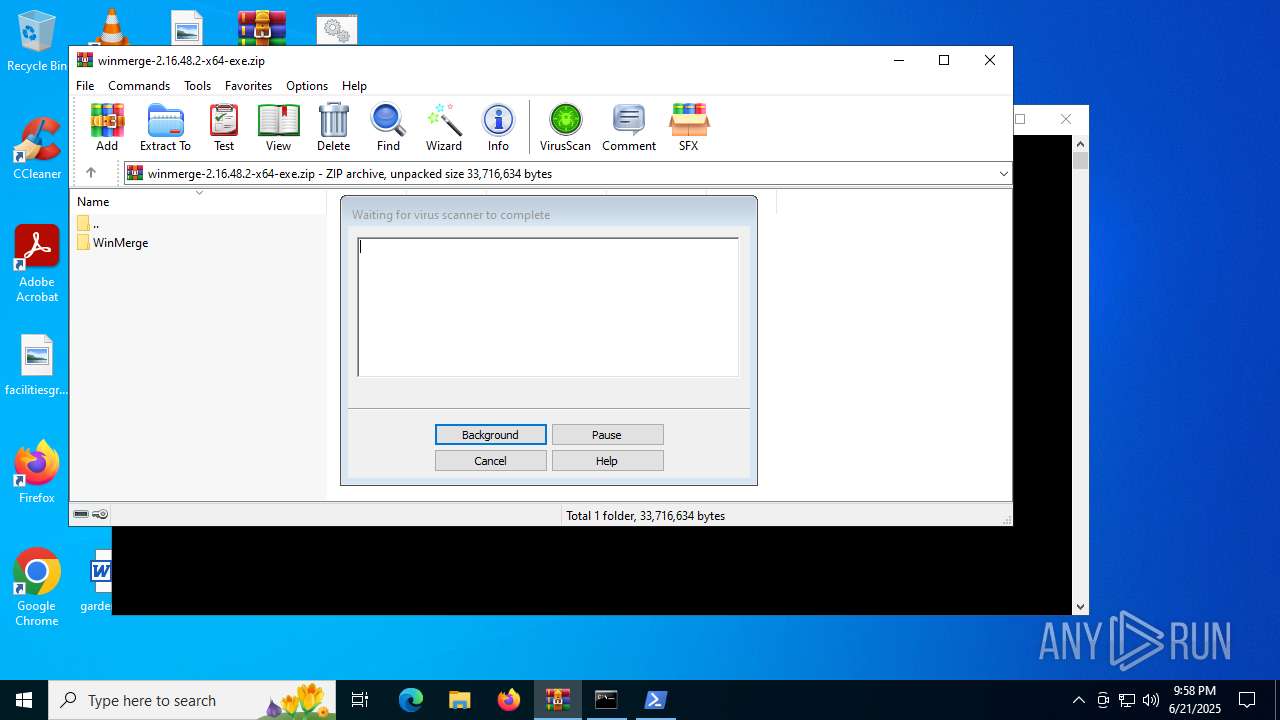
| File name: | winmerge-2.16.48.2-x64-exe.zip |
| Full analysis: | https://app.any.run/tasks/b8ef4bd4-6dff-4b20-8eb9-045ad5bfe2e4 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 21:57:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
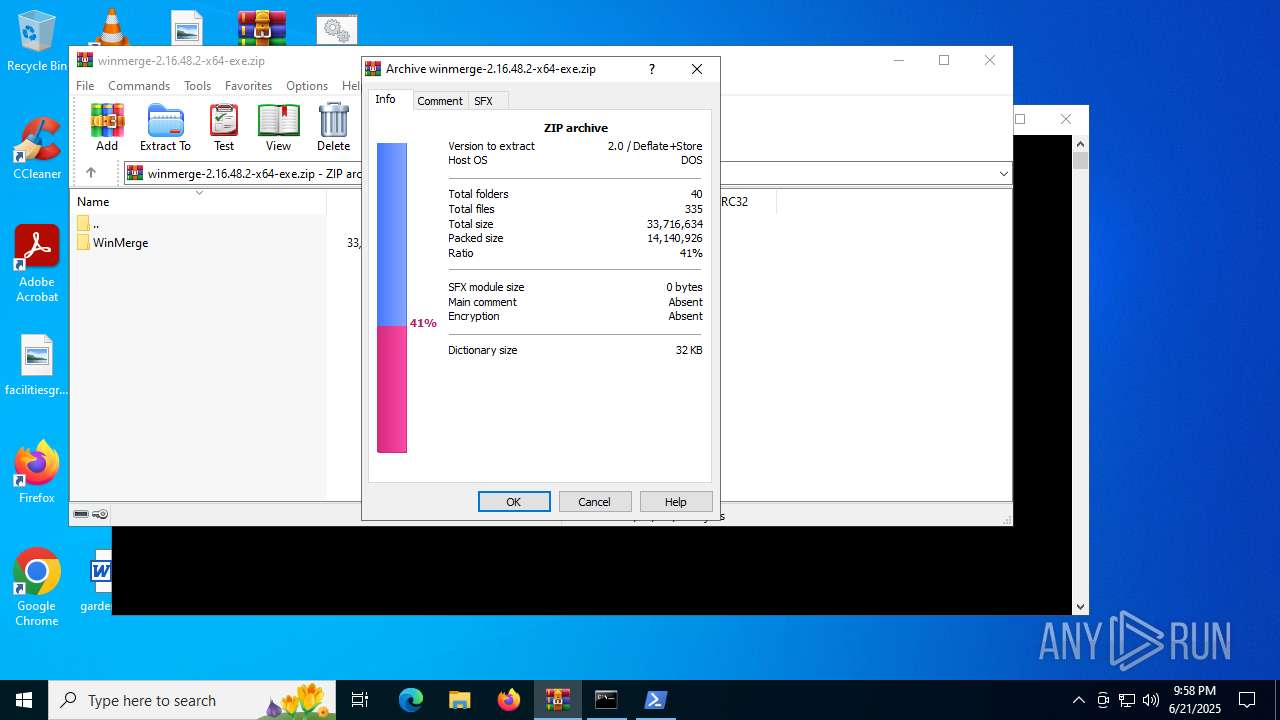
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 851424C20BC61BECD875BF8610FDDBB4 |
| SHA1: | 3B3ED6C901B9103E4B9FFBAD86A712885C333EA8 |
| SHA256: | 2C4AFEFFC66794EB482DDFD8DF9604F304B7402CE5E5570B724B4445FF56C68B |
| SSDEEP: | 98304:EJk2fN0Gt1WZFxb8IFOyWTTkU69Sco+ORo5CPt4hWkAt2wB97KOxi+t4MJS1c8hz:cW8k4E96B8G+h+JBdSprdUnPfApwTvoN |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2520)
SUSPICIOUS
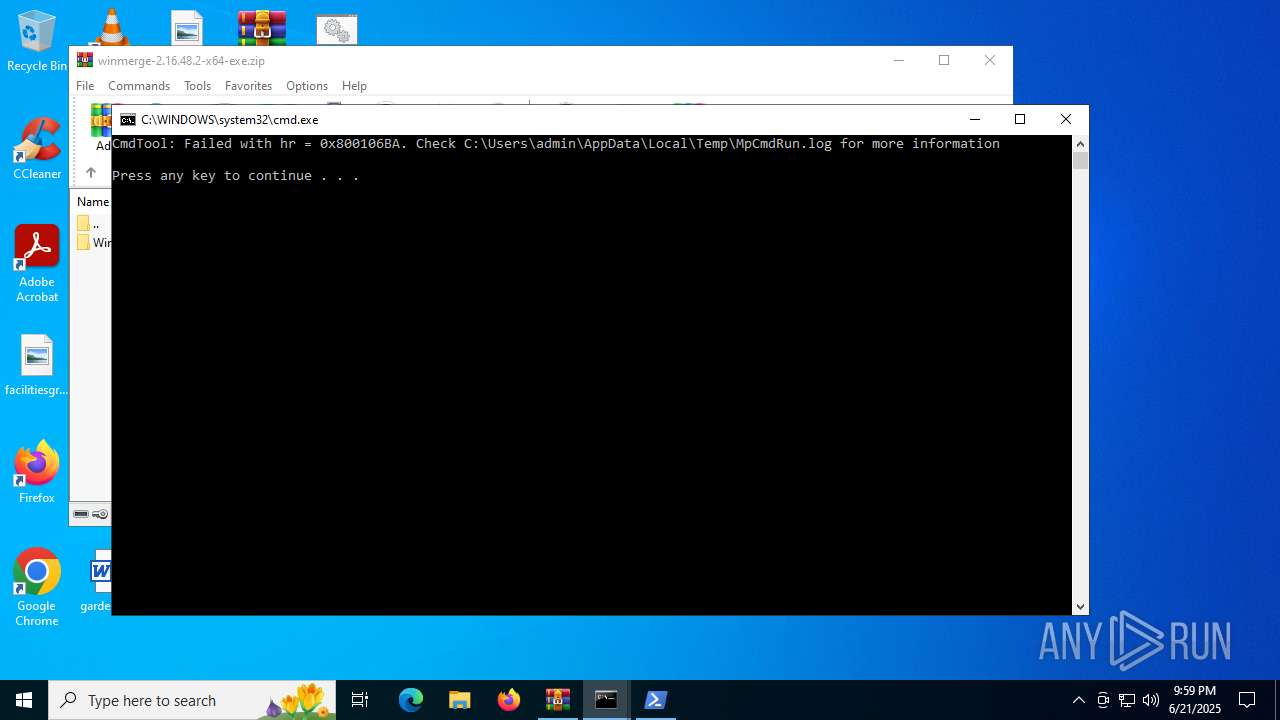
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6516)
- cmd.exe (PID: 1028)
- WinRAR.exe (PID: 2520)
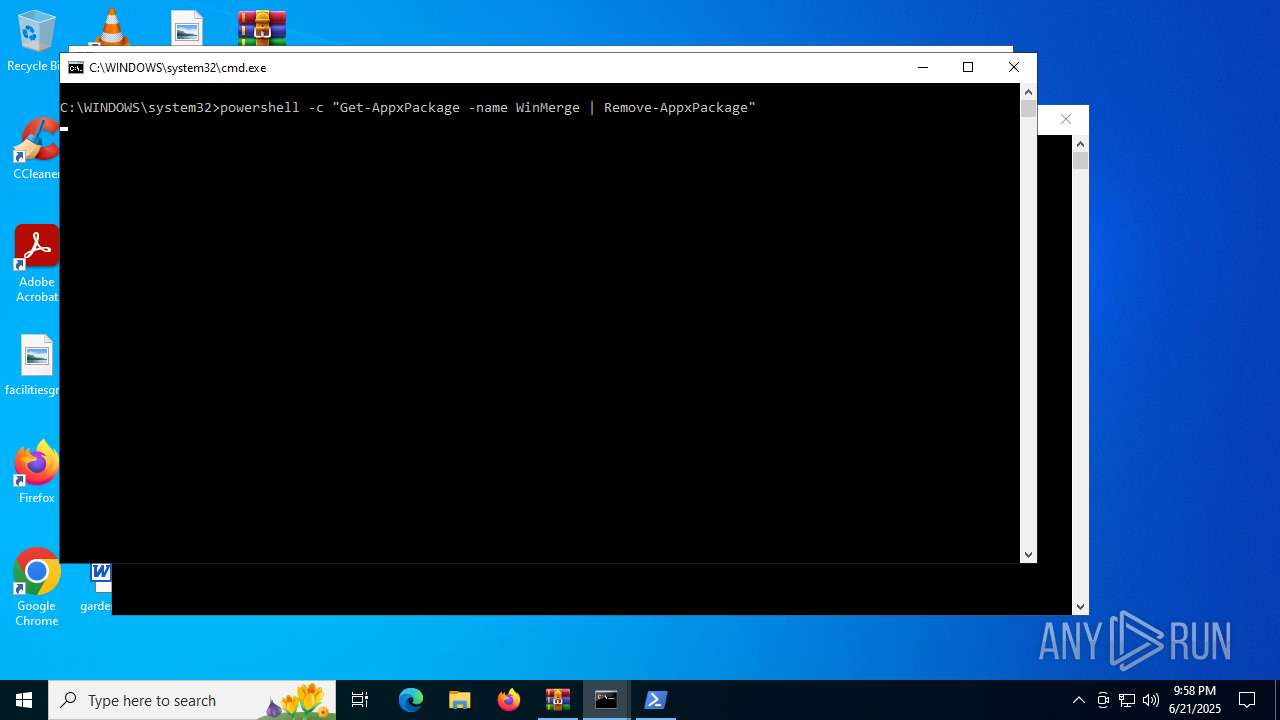
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6936)
- cmd.exe (PID: 5904)
Application launched itself
- cmd.exe (PID: 6516)
- cmd.exe (PID: 1028)
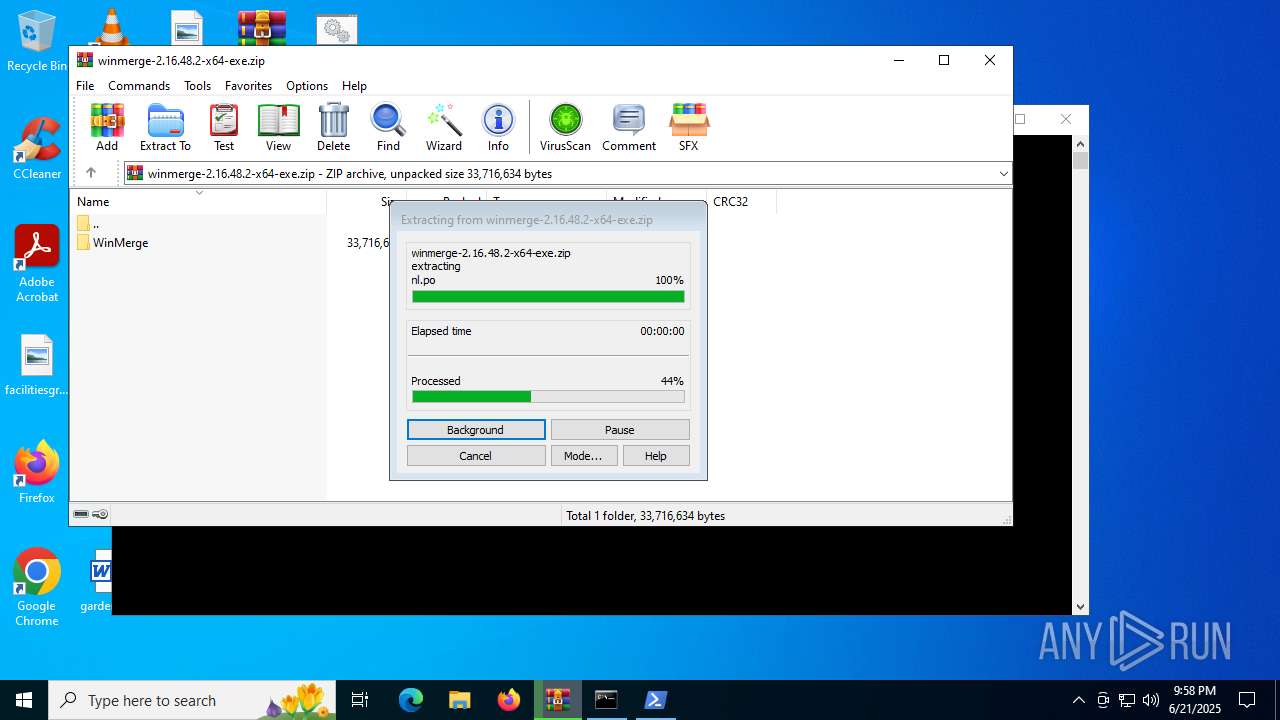
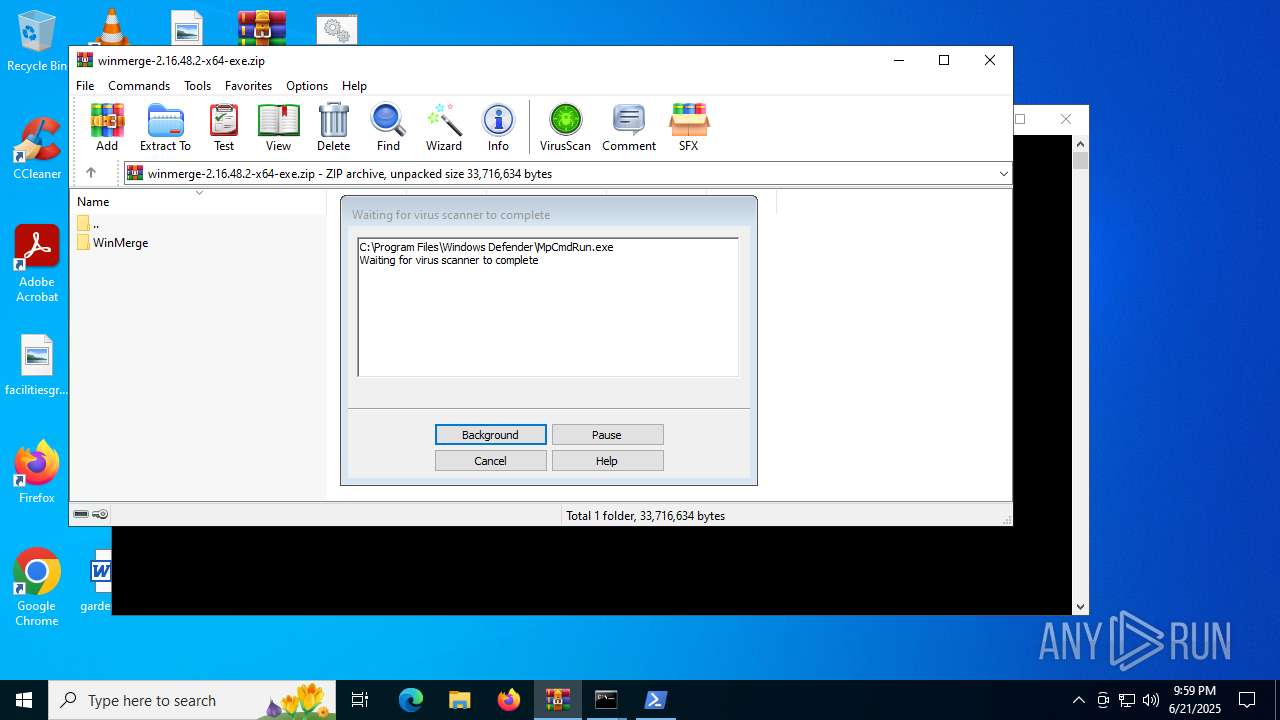
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 2520)
Process drops legitimate windows executable
- WinRAR.exe (PID: 2520)
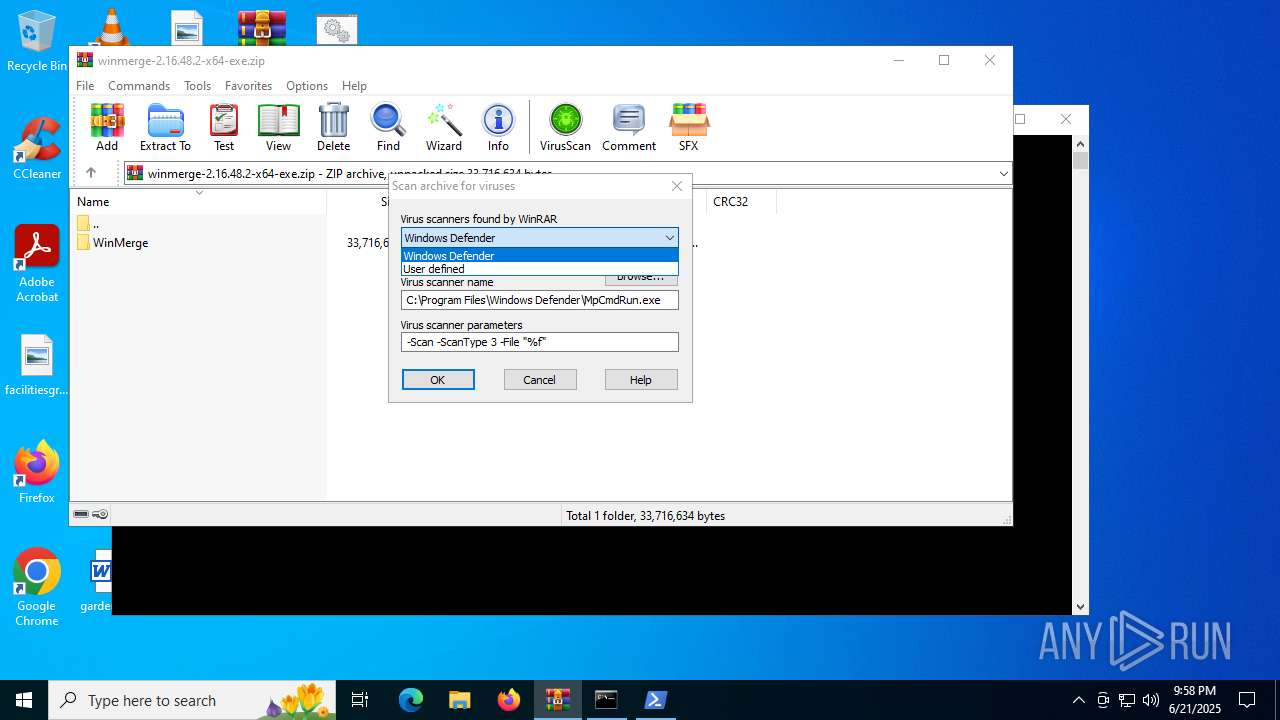
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2520)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 2520)
INFO
Manual execution by a user
- cmd.exe (PID: 5904)
- cmd.exe (PID: 6516)
- cmd.exe (PID: 1644)
- cmd.exe (PID: 6936)
- cmd.exe (PID: 1712)
- cmd.exe (PID: 1028)
The sample compiled with english language support
- WinRAR.exe (PID: 2520)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2520)
Checks supported languages
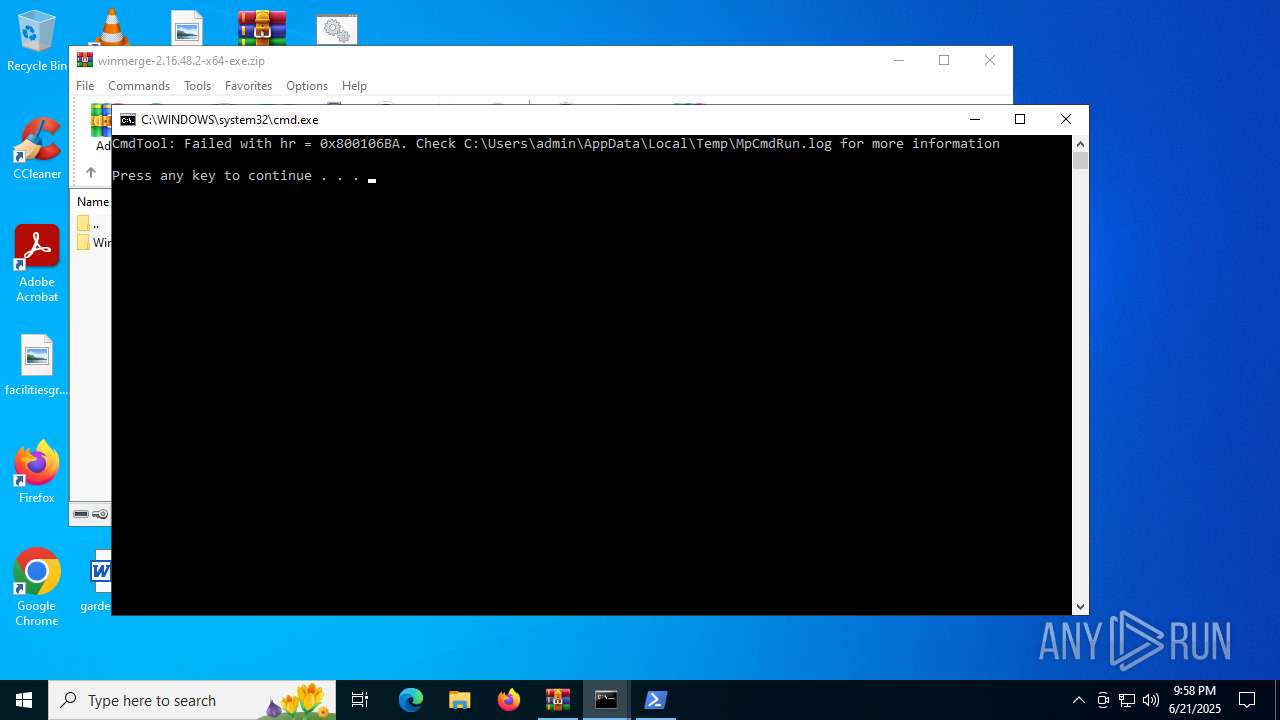
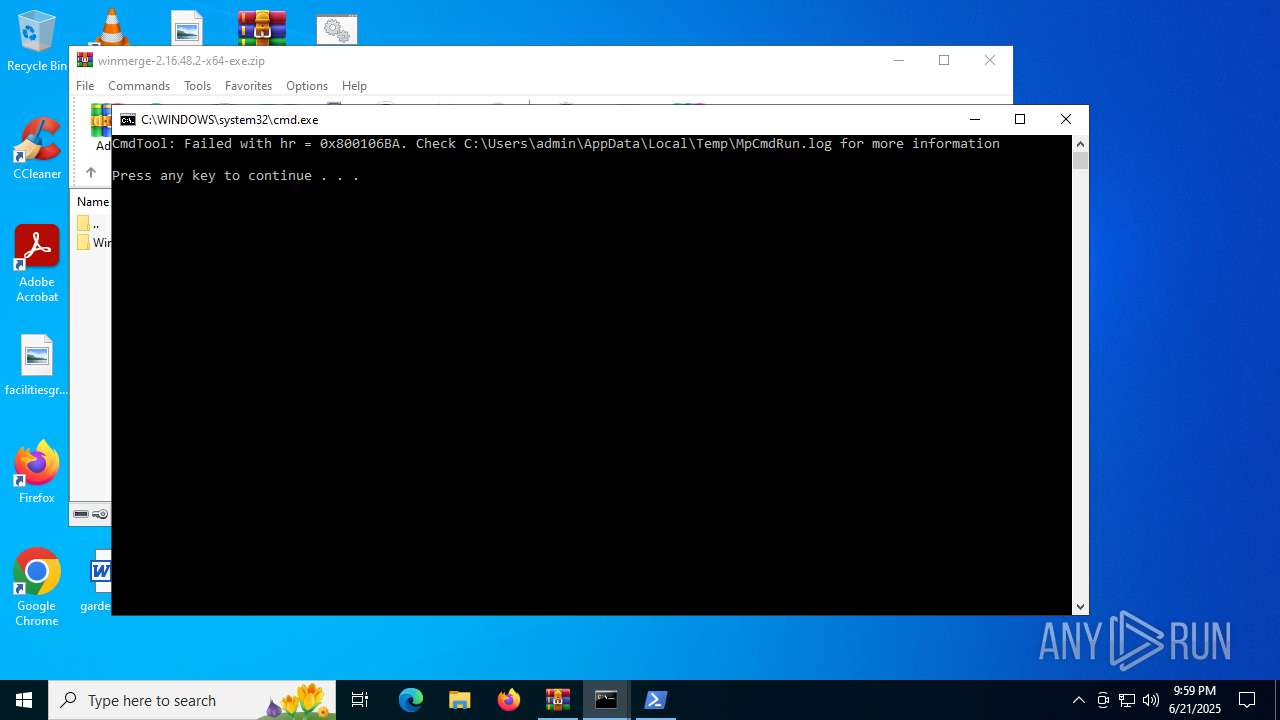
- MpCmdRun.exe (PID: 3608)
Reads the computer name
- MpCmdRun.exe (PID: 3608)
Checks proxy server information
- slui.exe (PID: 5628)
Reads the software policy settings
- slui.exe (PID: 5628)
Create files in a temporary directory
- MpCmdRun.exe (PID: 3608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:04:29 21:24:58 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | WinMerge/ |
Total processes
151
Monitored processes
25
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1028 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\md2html.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 255 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
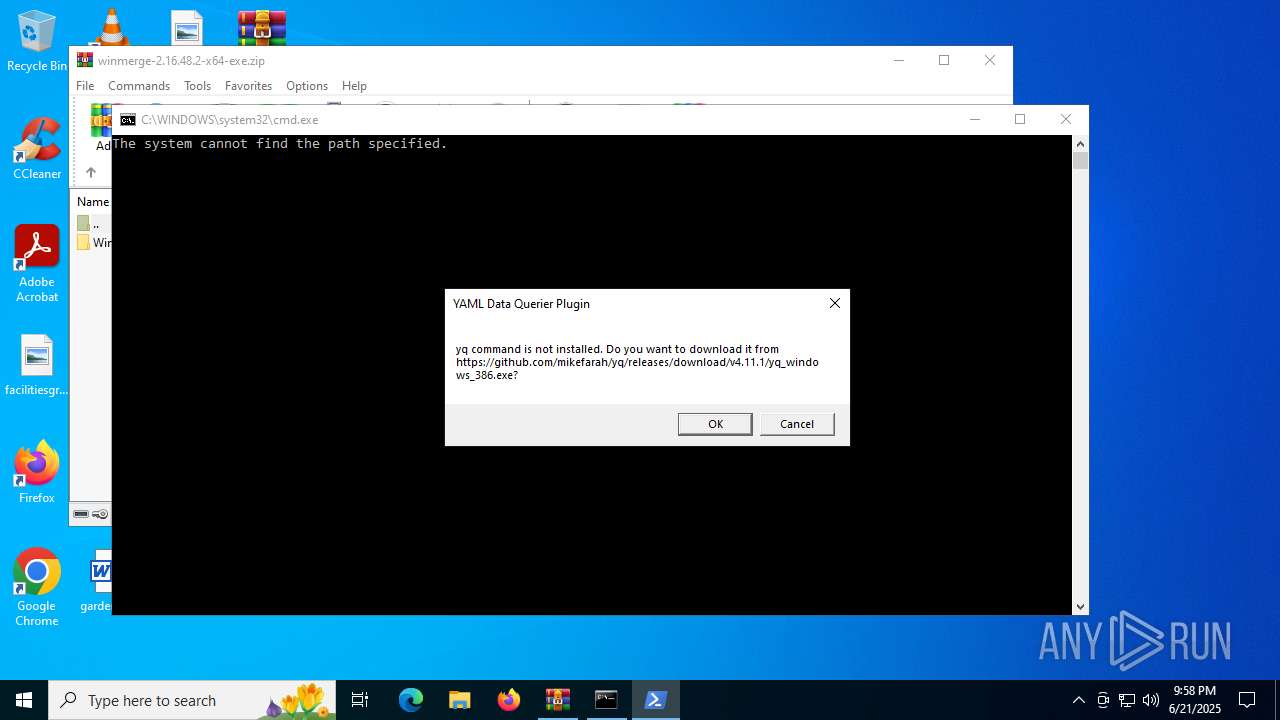
| 1036 | powershell "if ((New-Object -com WScript.Shell).Popup('yq command is not installed. Do you want to download it from https://github.com/mikefarah/yq/releases/download/v4.11.1/yq_windows_386.exe?',0,'YAML Data Querier Plugin',1) -ne 1) { throw }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1644 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\dumpbin.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\UnRegister.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1984 | C:\WINDOWS\system32\cmd.exe /S /D /c" type " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2032 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | powershell -c "Get-AppxPackage -name WinMerge | Remove-AppxPackage" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2276 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2520 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\winmerge-2.16.48.2-x64-exe.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
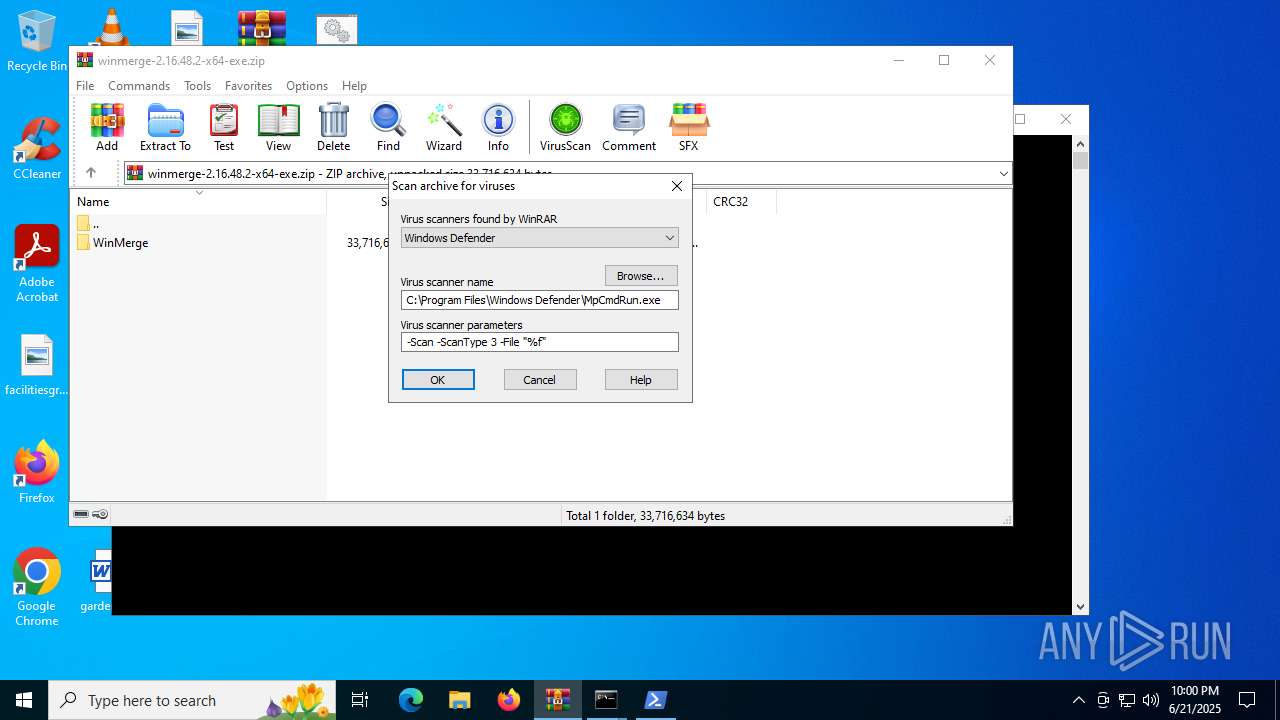
| 3608 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR2520.43349" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 024
Read events
14 013
Write events
11
Delete events
0
Modification events
| (PID) Process: | (2520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\winmerge-2.16.48.2-x64-exe.zip | |||
| (PID) Process: | (2520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (2520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
36
Suspicious files
19
Text files
467
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1036 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3huay1zq.3ih.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2520.43349\winmerge-2.16.48.2-x64-exe.zip\WinMerge\ColorSchemes\Default.ini | text | |
MD5:6BA54ED6FF85024E20F9973C1B93E45C | SHA256:53138F2E8BF7CB28184FA8B6172A66DA7AAAC55CF03D54F0B3A6C5104B60710E | |||
| 2192 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:7531396BEFA2B12EFB9ACFBB5D999C42 | SHA256:8B2AC523794F6209B52E36C21845018927A09CB59844807D0F81161B0EEC7A3B | |||
| 2192 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hs3dtvzf.31c.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1036 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_z51syyze.xc3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2192 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hj04wsbi.fji.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2520.43349\winmerge-2.16.48.2-x64-exe.zip\WinMerge\Commands\Apache-Tika\LICENSE-2.0.txt | text | |
MD5:D273D63619C9AEAF15CDAF76422C4F87 | SHA256:3DDF9BE5C28FE27DAD143A5DC76EEA25222AD1DD68934A047064E56ED2FA40C5 | |||
| 2520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2520.43349\winmerge-2.16.48.2-x64-exe.zip\WinMerge\Commands\Apache-Tika\URL.txt | text | |
MD5:A2A893448BC7D356D94EE8EBFFD2AFC8 | SHA256:A14D3585747B992192E431D02DCC25F92F2C4390FB90F1CFBE2BB1476FC62494 | |||
| 2520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2520.43349\winmerge-2.16.48.2-x64-exe.zip\WinMerge\ColorSchemes\Midnight.ini | text | |
MD5:4B6739531F19CBB4D5E10A0E9B4346F6 | SHA256:78A81B286A10F50234BE3897627EB64E66380155BAFBFD5E949DB6D5BFA7A731 | |||
| 2520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2520.43349\winmerge-2.16.48.2-x64-exe.zip\WinMerge\Commands\Apache-Tika\tika.bat | text | |
MD5:30958BAB65CCA300670D7393AC4BE51E | SHA256:DC0C9640C894027E4E291B721479561AA9B038A03528BE00854914D50EA362A4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
48
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.11:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.11:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.24.77.11:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.64:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 200 | 40.126.32.68:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 40.126.32.136:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 184.24.77.11:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.24.77.11:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.24.77.11:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |