| File name: | TunnlTo_1.0.7_x64_en-US.msi |
| Full analysis: | https://app.any.run/tasks/c58cf2fe-d12f-49a9-b20d-a271ebe079a9 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | June 09, 2025, 00:04:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: TunnlTo, Author: tunnl, Keywords: Installer, Comments: This installer database contains the logic and data required to install TunnlTo., Template: x64;0, Revision Number: {61FF8CDE-2F35-44D5-A379-E4CE8CE75A15}, Create Time/Date: Mon May 20 02:16:42 2024, Last Saved Time/Date: Mon May 20 02:16:42 2024, Number of Pages: 450, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | ABA32A1DCD826CFFEF0DD1832F0FC882 |
| SHA1: | DF44CD8BAF537D3543BE0D5AE2B773866DE502D8 |
| SHA256: | 2C4177EE75B4297E31EA834C1BD140FA7422C8F2049347141C2B83E8C255C48C |
| SSDEEP: | 98304:k2Lax6gp2bSMoRfkcYJ3faC2z5lRAEkRS1jx4ZvHBGu0gGw+XtY782Un6yXoDhxx:gz |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 3760)
GENERIC has been found (auto)
- msiexec.exe (PID: 1052)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 6456)
Downloads file from URI via Powershell
- powershell.exe (PID: 3760)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 1052)
- TunnlTo.exe (PID: 5164)
Starts process via Powershell
- powershell.exe (PID: 3760)
- powershell.exe (PID: 7600)
Executable content was dropped or overwritten
- powershell.exe (PID: 3760)
- MicrosoftEdgeUpdate.exe (PID: 2908)
- MicrosoftEdgeWebview2Setup.exe (PID: 7424)
- MicrosoftEdge_X64_137.0.3296.68.exe (PID: 7784)
- setup.exe (PID: 5640)
Manipulates environment variables
- powershell.exe (PID: 3760)
Process drops legitimate windows executable
- powershell.exe (PID: 3760)
- MicrosoftEdgeWebview2Setup.exe (PID: 7424)
- MicrosoftEdgeUpdate.exe (PID: 2908)
- MicrosoftEdge_X64_137.0.3296.68.exe (PID: 7784)
- msiexec.exe (PID: 1052)
- setup.exe (PID: 5640)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 7424)
- MicrosoftEdgeUpdate.exe (PID: 2908)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 2908)
Application launched itself
- setup.exe (PID: 5640)
- MicrosoftEdgeUpdate.exe (PID: 4408)
- msedgewebview2.exe (PID: 7652)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 1052)
Found IP address in command line
- powershell.exe (PID: 7600)
INFO
The sample compiled with english language support
- msiexec.exe (PID: 6072)
- msiexec.exe (PID: 1052)
- powershell.exe (PID: 3760)
- MicrosoftEdgeWebview2Setup.exe (PID: 7424)
- MicrosoftEdgeUpdate.exe (PID: 2908)
- MicrosoftEdge_X64_137.0.3296.68.exe (PID: 7784)
- setup.exe (PID: 5640)
Creates files or folders in the user directory
- msiexec.exe (PID: 6072)
Reads the software policy settings
- msiexec.exe (PID: 6072)
Checks proxy server information
- msiexec.exe (PID: 6072)
Checks supported languages
- msiexec.exe (PID: 1052)
- msiexec.exe (PID: 4404)
Manages system restore points
- SrTasks.exe (PID: 8152)
- SrTasks.exe (PID: 7496)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6072)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6072)
- msiexec.exe (PID: 1052)
Reads the computer name
- msiexec.exe (PID: 1052)
- msiexec.exe (PID: 4404)
The executable file from the user directory is run by the Powershell process
- MicrosoftEdgeWebview2Setup.exe (PID: 7424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | TunnlTo |
| Author: | tunnl |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install TunnlTo. |
| Template: | x64;0 |
| RevisionNumber: | {61FF8CDE-2F35-44D5-A379-E4CE8CE75A15} |
| CreateDate: | 2024:05:20 02:16:42 |
| ModifyDate: | 2024:05:20 02:16:42 |
| Pages: | 450 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
170
Monitored processes
34
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | "C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\137.0.3296.68\msedgewebview2.exe" --type=renderer --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\com.tunnl.to\EBWebView" --webview-exe-name=TunnlTo.exe --webview-exe-version=1.0.7 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=2 --force-high-res-timeticks=disabled --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --js-flags="--expose-gc --ms-user-locale=" --always-read-main-dll --field-trial-handle=1892,i,3580028067147407614,13080966583481013789,262144 --enable-features=ForceSWDCompWhenDCompFallbackRequired,msAggressiveCacheTrimming,msCustomDataPartition,msWebView2NoTabForScreenShare,msWindowsTaskManager --disable-features=BackForwardCache,BackgroundTabLoadingFromPerformanceManager,CloseOmniboxPopupOnInactiveAreaClick,CollectAVProductsInfo,CollectCodeIntegrityInfo,EnableHangWatcher,FilterAdsOnAbusiveSites,GetWifiProtocol,LoginDetection,MediaFoundationCameraUsageMonitoring,PreconnectToSearch,SafetyHub,SegmentationPlatform,SpareRendererForSitePerProcess,Ukm,WebPayments,msAITrackerClassification,msAbydosForWindowlessWV2,msAffirmVirtualCard,msAllowChromeWebstore,msAllowMSAPrtSSOForNonMSAProfile,msApplicationGuard,msAskBeforeClosingMultipleTabs,msAutoToggleAADPrtSSOForNonAADProfile,msAutofillEdgeCoupons,msAutofillEdgeCouponsAutoApply,msAutofillEdgeServiceRequest,msAutomaticTabFreeze,msBrowserSettingsSupported,msCoarseGeolocationService,msDataProtection,msDesktopMode,msDesktopRewards,msDisableVariationsSeedFetchThrottling,msEEProactiveHistory,msETFOffstoreExtensionFileDataCollection,msETFPasswordTheftDNRActionSignals,msEdgeAdPlatformUI,msEdgeAddWebCapturetoCollections,msEdgeAutofillAdvancedSuggestionsBasic,msEdgeAutofillOneClickAutocomplete,msEdgeAutofillShowDeployedPassword,msEdgeAutofillSs,msEdgeBrowserEssentialsShowUpdateSection,msEdgeCloudConfigService,msEdgeCloudConfigServiceV2,msEdgeCohorts,msEdgeCollectionsPrismExperiment1,msEdgeCollectionsPrismOverallMigration,msEdgeComposeNext,msEdgeEnableNurturingFramework,msEdgeEnclavePrefsBasic,msEdgeEnclavePrefsNotification,msEdgeFaviconService,msEdgeHJTelemetry,msEdgeHubAppSkype,msEdgeImageEditorUI,msEdgeLinkDoctor,msEdgeMouseGestureDefaultEnabled,msEdgeMouseGestureSupported,msEdgeNewDeviceFre,msEdgeOnRampFRE,msEdgeOnRampImport,msEdgePDFCMHighlightUX,msEdgePasswordIris,msEdgePasswordIrisSaveBubble,msEdgeProngPersonalization,msEdgeReadingView,msEdgeRose,msEdgeSendTabToSelf,msEdgeSettingsImport,msEdgeSettingsImportV2,msEdgeShoppingPersistentStorage,msEdgeShoppingUI,msEdgeSmartFind,msEdgeSuperDragDefaultEnabled,msEdgeSuperDragDropSupported,msEdgeTipping,msEdgeTranslate,msEdgeUseCaptivePortalService,msEdgeWebContentFilteringFeedback,msEdgeWorkSearchBanner,msEnableCustomJobMemoryLimitsOnXbox,msEnableMIPForPDF,msEnablePdfUpsell,msEnableThirdPartyScanning,msEnableWebSignInCta,msEnableWebToBrowserSignIn,msEndpointDlp,msEntityExtraction,msExtensionTelemetryFramework,msExternalTaskManager,msFileSystemAccessDirectoryIterationBlocklistCheck,msForceBrowserSignIn,msForeignSessionsPage,msGeolocationAccessService,msGeolocationOSLocationPermissionFallback,msGeolocationSQMService,msGeolocationService,msGrowthInfraLaunchSourceLogging,msGuidedSwitchAllowed,msHubPinPersist,msImplicitSignin,msIrm,msIrmv2,msKlarnaVirtualCard,msLoadStatistics,msLogIsEdgePinnedToTaskbarOnLaunch,msMIPCrossTenantPdfViewSupport,msMdatpWebSiteDlp,msNotificationPermissionForPWA,msOnHoverSearchInSidebar,msOpenOfficeDocumentsInWebViewer,msPasswordBreachDetection,msPdfAnnotationsVisibility,msPdfDataRecovery,msPdfDigitalSignatureRead,msPdfFreeText,msPdfFreeTextForCJK,msPdfHighlightMode,msPdfInking,msPdfKeyphraseSupport,msPdfOOUI,msPdfPopupMarkerRenderer,msPdfShare,msPdfSharedLibrary,msPdfTextNote,msPdfTextNoteMoreMenu,msPdfThumbnailCache,msPdfUnderside,msPdfViewRestore,msPersonalizationUMA,msPriceComparison,msPromptDefaultHandlerForPDF,msReactiveSearch,msReadAloud,msReadAloudPdf,msRedirectToShoreline,msRevokeExtensions,msSaasDlp,msShoppingTrigger,msShorelineSearch,msShorelineSearchFindOnPageWebUI,msShowOfflineGameEntrance,msShowReadAloudIconInAddressBar,msShowUXForAADPrtSSOForNonAADProfile,msSmartScreenProtection,msSuspendMessageForNewSessionWhenHavingPendingNavigation,msSyncEdgeCollections,msTabResourceStats,msTokenizationAutofillInlineEnabled,msTouchMode,msTriggeringSignalGenerator,msUserUnderstanding,msVideoSuperResolutionUI,msWalletBuyNow,msWalletCheckout,msWalletDiagnosticDataLogger,msWalletHubEntry,msWalletHubIntlP3,msWalletPartialCard,msWalletPasswordCategorization,msWalletPasswordCategorizationPlatformExpansion,msWalletTokenizationCardMetadata,msWalletTokenizedAutofill,msWebAssist,msWebAssistHistorySearchService,msWebOOUI,msWindowsUserActivities,msZipPayVirtualCard --variations-seed-version --mojo-platform-channel-handle=3484 /prefetch:1 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\137.0.3296.68\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge WebView2 Version: 137.0.3296.68 Modules
| |||||||||||||||
| 1052 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2408 | "C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\137.0.3296.68\msedgewebview2.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\com.tunnl.to\EBWebView" --webview-exe-name=TunnlTo.exe --webview-exe-version=1.0.7 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=2 --force-high-res-timeticks=disabled --always-read-main-dll --field-trial-handle=1892,i,3580028067147407614,13080966583481013789,262144 --enable-features=ForceSWDCompWhenDCompFallbackRequired,msAggressiveCacheTrimming,msCustomDataPartition,msWebView2NoTabForScreenShare,msWindowsTaskManager --disable-features=BackForwardCache,BackgroundTabLoadingFromPerformanceManager,CloseOmniboxPopupOnInactiveAreaClick,CollectAVProductsInfo,CollectCodeIntegrityInfo,EnableHangWatcher,FilterAdsOnAbusiveSites,GetWifiProtocol,LoginDetection,MediaFoundationCameraUsageMonitoring,PreconnectToSearch,SafetyHub,SegmentationPlatform,SpareRendererForSitePerProcess,Ukm,WebPayments,msAITrackerClassification,msAbydosForWindowlessWV2,msAffirmVirtualCard,msAllowChromeWebstore,msAllowMSAPrtSSOForNonMSAProfile,msApplicationGuard,msAskBeforeClosingMultipleTabs,msAutoToggleAADPrtSSOForNonAADProfile,msAutofillEdgeCoupons,msAutofillEdgeCouponsAutoApply,msAutofillEdgeServiceRequest,msAutomaticTabFreeze,msBrowserSettingsSupported,msCoarseGeolocationService,msDataProtection,msDesktopMode,msDesktopRewards,msDisableVariationsSeedFetchThrottling,msEEProactiveHistory,msETFOffstoreExtensionFileDataCollection,msETFPasswordTheftDNRActionSignals,msEdgeAdPlatformUI,msEdgeAddWebCapturetoCollections,msEdgeAutofillAdvancedSuggestionsBasic,msEdgeAutofillOneClickAutocomplete,msEdgeAutofillShowDeployedPassword,msEdgeAutofillSs,msEdgeBrowserEssentialsShowUpdateSection,msEdgeCloudConfigService,msEdgeCloudConfigServiceV2,msEdgeCohorts,msEdgeCollectionsPrismExperiment1,msEdgeCollectionsPrismOverallMigration,msEdgeComposeNext,msEdgeEnableNurturingFramework,msEdgeEnclavePrefsBasic,msEdgeEnclavePrefsNotification,msEdgeFaviconService,msEdgeHJTelemetry,msEdgeHubAppSkype,msEdgeImageEditorUI,msEdgeLinkDoctor,msEdgeMouseGestureDefaultEnabled,msEdgeMouseGestureSupported,msEdgeNewDeviceFre,msEdgeOnRampFRE,msEdgeOnRampImport,msEdgePDFCMHighlightUX,msEdgePasswordIris,msEdgePasswordIrisSaveBubble,msEdgeProngPersonalization,msEdgeReadingView,msEdgeRose,msEdgeSendTabToSelf,msEdgeSettingsImport,msEdgeSettingsImportV2,msEdgeShoppingPersistentStorage,msEdgeShoppingUI,msEdgeSmartFind,msEdgeSuperDragDefaultEnabled,msEdgeSuperDragDropSupported,msEdgeTipping,msEdgeTranslate,msEdgeUseCaptivePortalService,msEdgeWebContentFilteringFeedback,msEdgeWorkSearchBanner,msEnableCustomJobMemoryLimitsOnXbox,msEnableMIPForPDF,msEnablePdfUpsell,msEnableThirdPartyScanning,msEnableWebSignInCta,msEnableWebToBrowserSignIn,msEndpointDlp,msEntityExtraction,msExtensionTelemetryFramework,msExternalTaskManager,msFileSystemAccessDirectoryIterationBlocklistCheck,msForceBrowserSignIn,msForeignSessionsPage,msGeolocationAccessService,msGeolocationOSLocationPermissionFallback,msGeolocationSQMService,msGeolocationService,msGrowthInfraLaunchSourceLogging,msGuidedSwitchAllowed,msHubPinPersist,msImplicitSignin,msIrm,msIrmv2,msKlarnaVirtualCard,msLoadStatistics,msLogIsEdgePinnedToTaskbarOnLaunch,msMIPCrossTenantPdfViewSupport,msMdatpWebSiteDlp,msNotificationPermissionForPWA,msOnHoverSearchInSidebar,msOpenOfficeDocumentsInWebViewer,msPasswordBreachDetection,msPdfAnnotationsVisibility,msPdfDataRecovery,msPdfDigitalSignatureRead,msPdfFreeText,msPdfFreeTextForCJK,msPdfHighlightMode,msPdfInking,msPdfKeyphraseSupport,msPdfOOUI,msPdfPopupMarkerRenderer,msPdfShare,msPdfSharedLibrary,msPdfTextNote,msPdfTextNoteMoreMenu,msPdfThumbnailCache,msPdfUnderside,msPdfViewRestore,msPersonalizationUMA,msPriceComparison,msPromptDefaultHandlerForPDF,msReactiveSearch,msReadAloud,msReadAloudPdf,msRedirectToShoreline,msRevokeExtensions,msSaasDlp,msShoppingTrigger,msShorelineSearch,msShorelineSearchFindOnPageWebUI,msShowOfflineGameEntrance,msShowReadAloudIconInAddressBar,msShowUXForAADPrtSSOForNonAADProfile,msSmartScreenProtection,msSuspendMessageForNewSessionWhenHavingPendingNavigation,msSyncEdgeCollections,msTabResourceStats,msTokenizationAutofillInlineEnabled,msTouchMode,msTriggeringSignalGenerator,msUserUnderstanding,msVideoSuperResolutionUI,msWalletBuyNow,msWalletCheckout,msWalletDiagnosticDataLogger,msWalletHubEntry,msWalletHubIntlP3,msWalletPartialCard,msWalletPasswordCategorization,msWalletPasswordCategorizationPlatformExpansion,msWalletTokenizationCardMetadata,msWalletTokenizedAutofill,msWebAssist,msWebAssistHistorySearchService,msWebOOUI,msWindowsUserActivities,msZipPayVirtualCard --variations-seed-version --mojo-platform-channel-handle=2420 /prefetch:8 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\137.0.3296.68\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge WebView2 Version: 137.0.3296.68 Modules
| |||||||||||||||
| 2908 | C:\Users\admin\AppData\Local\Temp\EU6DC6.tmp\MicrosoftEdgeUpdate.exe /silent /install "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=prefers" | C:\Users\admin\AppData\Local\Temp\EU6DC6.tmp\MicrosoftEdgeUpdate.exe | MicrosoftEdgeWebview2Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.61 Modules
| |||||||||||||||
| 3396 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\137.0.3296.68\msedgewebview2.exe --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Local\com.tunnl.to\EBWebView /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Local\com.tunnl.to\EBWebView\Crashpad --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=137.0.7151.69 --annotation=exe=C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\137.0.3296.68\msedgewebview2.exe --annotation=plat=Win64 "--annotation=prod=Edge WebView2" --annotation=ver=137.0.3296.68 --initial-client-data=0x184,0x188,0x18c,0x160,0x194,0x7ffc8a44c148,0x7ffc8a44c154,0x7ffc8a44c160 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\137.0.3296.68\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge WebView2 Version: 137.0.3296.68 Modules
| |||||||||||||||
| 3760 | powershell.exe -NoProfile -windowstyle hidden try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 } catch {}; Invoke-WebRequest -Uri "https://go.microsoft.com/fwlink/p/?LinkId=2124703" -OutFile "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" ; Start-Process -FilePath "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" -ArgumentList ('/silent', '/install') -Wait | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4404 | C:\Windows\syswow64\MsiExec.exe -Embedding 2F58C85CD96D11C4377E49F8F0921BD7 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4408 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" -Embedding | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.61 Modules
| |||||||||||||||
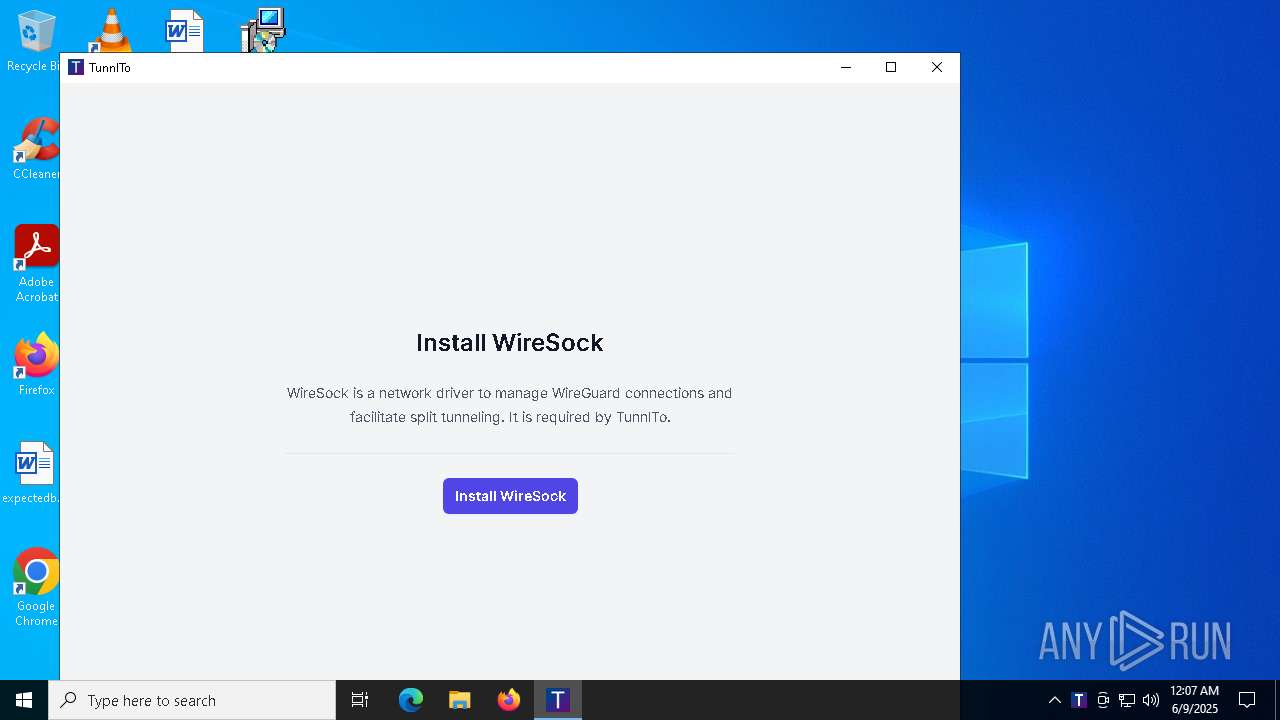
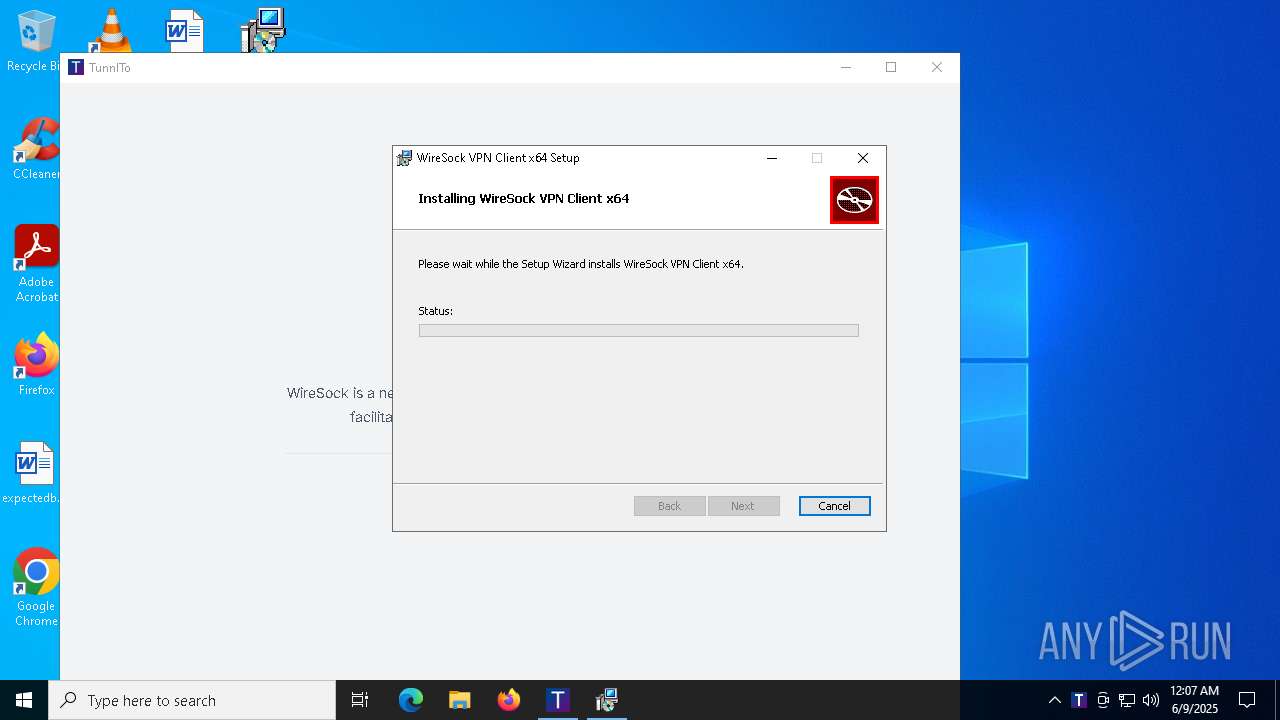
| 5164 | "C:\Program Files\TunnlTo\TunnlTo.exe" | C:\Program Files\TunnlTo\TunnlTo.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: TunnlTo Version: 1.0.7 Modules
| |||||||||||||||
| 5376 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /handoff "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=false" /installsource otherinstallcmd /sessionid "{839B5999-B05B-49F4-84B9-7FA6FD1428D9}" /silent | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.61 Modules
| |||||||||||||||
Total events
47 697
Read events
44 096
Write events
3 507
Delete events
94
Modification events
| (PID) Process: | (1052) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000613A8427D2D8DB011C040000200F0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1052) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000613A8427D2D8DB011C040000200F0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1052) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000004C9BA527D2D8DB011C040000200F0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1052) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000003D37A327D2D8DB011C040000200F0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1052) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000003D37A327D2D8DB011C040000200F0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1052) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000007D61AA27D2D8DB011C040000200F0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1052) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (1052) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000008AC7DE27D2D8DB011C040000440C0000E80300000100000000000000000000000D985B9CF79A334BB4B1082781ECD11B00000000000000000000000000000000 | |||
| (PID) Process: | (1052) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000CD64DC27D2D8DB011C040000200F0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6456) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000ED57E827D2D8DB013819000020050000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
217
Suspicious files
131
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1052 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1052 | msiexec.exe | C:\Windows\Installer\124f12.msi | — | |
MD5:— | SHA256:— | |||
| 6072 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0DA515F703BB9B49479E8697ADB0B955_4136D3715888E22D65EBE484B233D81B | binary | |
MD5:1784669F6A3E6D1690AFB7F789F58D2A | SHA256:4A1F0659BCA9C060040C47AB3D4285C11A6646E1060CF9B8D0F38148BCA67CE7 | |||
| 1052 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{9c5b980d-9af7-4b33-b4b1-082781ecd11b}_OnDiskSnapshotProp | binary | |
MD5:BFCE53DAD05C8F6249FE6D1F2C3C6371 | SHA256:AC7F10005F0275DC640C6E3FAAC3D49D3F9ADDFA49DB7C0699B78224FD697DF3 | |||
| 6072 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\357F04AD41BCF5FE18FCB69F60C6680F_CBBFF7A51C21E740C38443A74DDFD727 | binary | |
MD5:02FCD5195F8CF73C6336130DD76E6D72 | SHA256:1635B7FA9009430196D5E7F125419D3AB8D6ECCF4A2C1D1674FC47D1CEA2315C | |||
| 6072 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\357F04AD41BCF5FE18FCB69F60C6680F_CBBFF7A51C21E740C38443A74DDFD727 | binary | |
MD5:E4A0206BF1CBED9DBE822D53BB59E2D1 | SHA256:41978293536C54D3B24551FBFB1290B175603BAEB6703A8D9C084E956272DA4B | |||
| 1052 | msiexec.exe | C:\Windows\Installer\124f14.msi | — | |
MD5:— | SHA256:— | |||
| 6072 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:32FA32B77B415B8D28E4E4C5F8966864 | SHA256:21EA4037C6061CE23D0DD0CD4B2FA5A8BB6207C9FF934ECF5A3DC26E859E0AB4 | |||
| 1052 | msiexec.exe | C:\Windows\Temp\~DF960AA6345D765DAD.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 6072 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:5ED99060A9F4FA5B7B889C0DBBDB213A | SHA256:AA10E213BA43A5A0138D5AD7092D305F83607C8C593699C6956FD817D470AF97 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
54
DNS requests
28
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6072 | msiexec.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | unknown | — | — | whitelisted |
6072 | msiexec.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDDIt6H%2BXfAETa93iEg%3D%3D | unknown | — | — | whitelisted |
6072 | msiexec.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
6072 | msiexec.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGEJFcIpBz28BuO60qVQ%3D | unknown | — | — | whitelisted |
2516 | RUXIMICS.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2516 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 4.151.228.221:443 | https://msedge.api.cdp.microsoft.com/api/v1.1/internal/contents/Browser/namespaces/Default/names/msedgewebview-stable-win-x64/versions/137.0.3296.68/files?action=GenerateDownloadInfo&foregroundPriority=true | unknown | — | — | whitelisted |
— | — | GET | 301 | 184.30.21.171:443 | https://go.microsoft.com/fwlink/p/?LinkId=2124703 | unknown | — | — | unknown |
— | — | GET | 200 | 23.48.23.14:443 | https://msedge.sf.dl.delivery.mp.microsoft.com/filestreamingservice/files/815d89c2-508a-4010-89af-4a6770e178d9/MicrosoftEdgeWebview2Setup.exe | unknown | executable | 1.58 Mb | whitelisted |
— | — | POST | 200 | 4.151.228.221:443 | https://msedge.api.cdp.microsoft.com/api/v2/contents/Browser/namespaces/Default/names?action=batchupdates | unknown | text | 103 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2516 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6072 | msiexec.exe | 151.101.130.133:80 | ocsp.globalsign.com | FASTLY | US | whitelisted |
2516 | RUXIMICS.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2516 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
msedge.sf.dl.delivery.mp.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
msedge.api.cdp.microsoft.com |
| whitelisted |
msedge.f.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Misc activity | ET INFO Packed Executable Download |
— | — | Misc activity | ET INFO Request for EXE via Powershell |
2236 | svchost.exe | Misc activity | ET INFO Packed Executable Download |