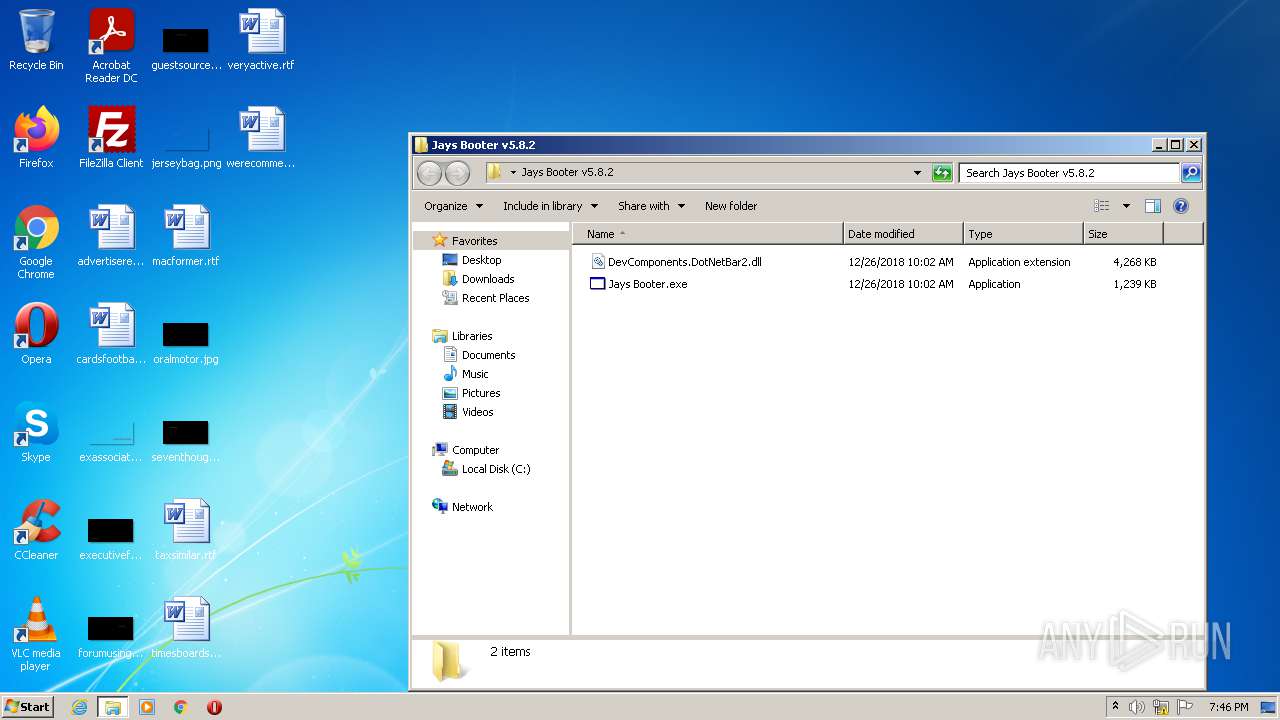
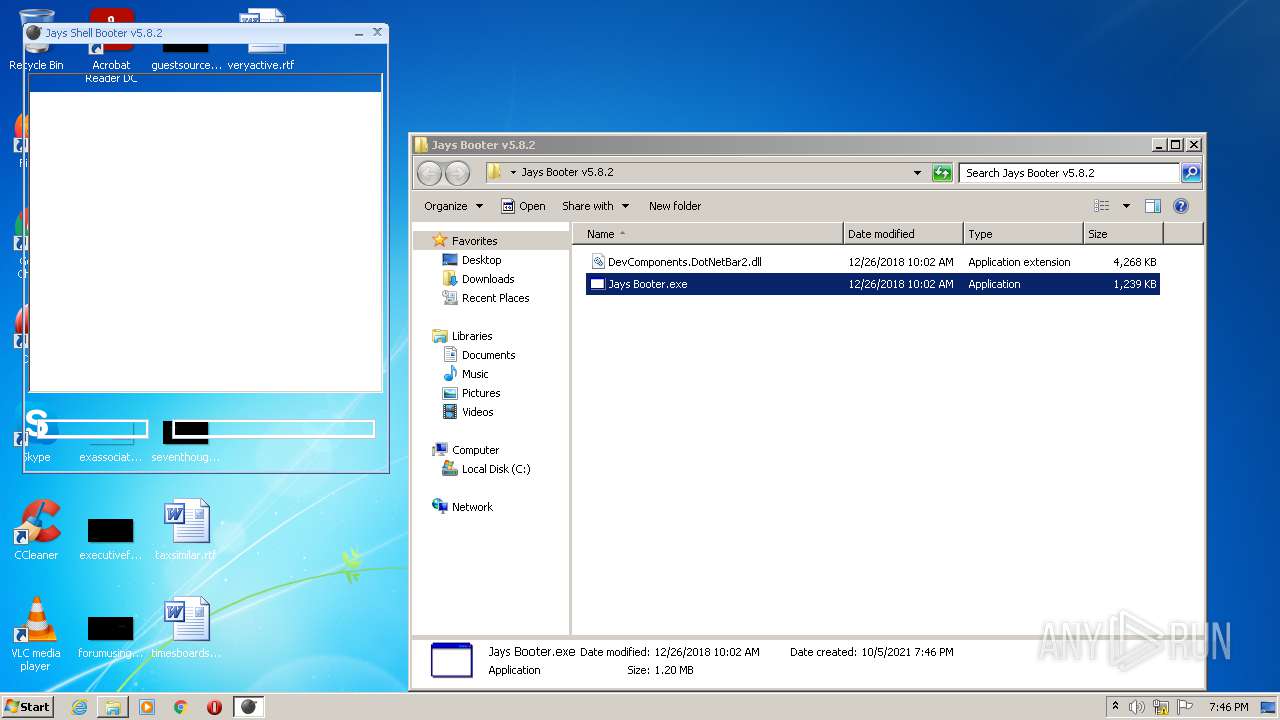
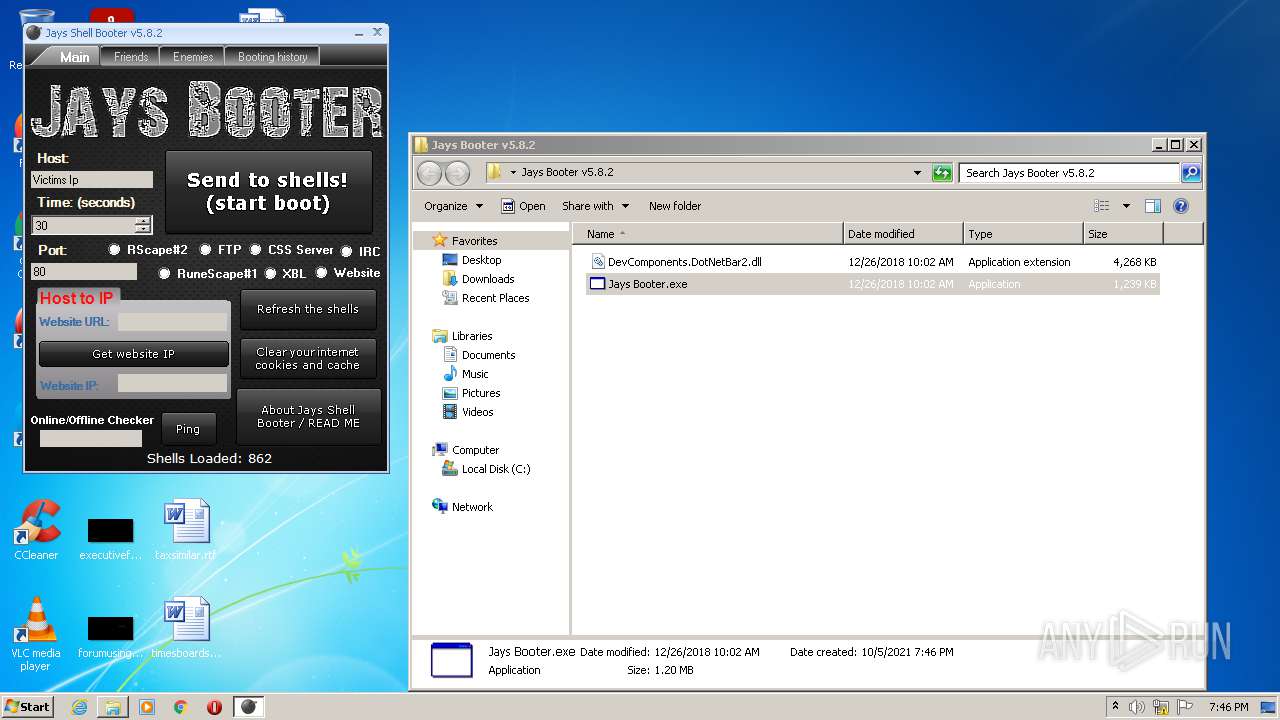
| File name: | Jays Booter v5.8.2.zip |
| Full analysis: | https://app.any.run/tasks/2420da7f-ce34-4d3e-9684-fc158f4cb620 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2021, 18:45:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | CAFC8887EFFF9A9E0A2AF4BCF076A0A9 |
| SHA1: | EEB07885B07013AAA81E745EBCE2C10EDE29E8E7 |
| SHA256: | 2C411E470FC32F5206167332F2426DECF7D07D706EEA531D4283467853758E25 |
| SSDEEP: | 49152:oGyIonyvvaVxyovn8jYSXIXLqtgpNr5D9Ga9ewyKS7+1JeuE+w+vIsQCGeVL6sl2:NnvaSInkYSXIXLEgf9D9Ga9ewyKy+vD0 |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3568)
- Jays Booter.exe (PID: 524)
Application was dropped or rewritten from another process
- Jays Booter.exe (PID: 524)
SUSPICIOUS
Drops a file with too old compile date
- WinRAR.exe (PID: 3320)
Reads the computer name
- WinRAR.exe (PID: 3320)
- Jays Booter.exe (PID: 524)
Checks supported languages
- WinRAR.exe (PID: 3320)
- Jays Booter.exe (PID: 524)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3320)
Reads Microsoft Outlook installation path
- Jays Booter.exe (PID: 524)
INFO
Manual execution by user
- Jays Booter.exe (PID: 524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Jays Booter v5.8.2/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2018:12:26 11:02:02 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
35
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 524 | "C:\Users\admin\Desktop\Jays Booter v5.8.2\Jays Booter.exe" | C:\Users\admin\Desktop\Jays Booter v5.8.2\Jays Booter.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Jays Booter Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3320 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Jays Booter v5.8.2.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3568 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
Total events
1 906
Read events
1 887
Write events
19
Delete events
0
Modification events
| (PID) Process: | (3320) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3320) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3320) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\171\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3320) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Jays Booter v5.8.2.zip | |||
| (PID) Process: | (3320) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3320) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3320) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3320) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3320) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3320) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
2
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3320.25242\Jays Booter v5.8.2\Jays Booter.exe | executable | |
MD5:7A31CFDB66D340937489B5769277D558 | SHA256:01F5C3893EDED5C0E3829C68379A97FB904BCFD7395181818DD285B3759F1B30 | |||
| 3320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3320.25242\Jays Booter v5.8.2\DevComponents.DotNetBar2.dll | executable | |
MD5:6C3CD66BBDCDFE43D106EECED2495914 | SHA256:81BFA5B4D8290E0C0DC0C7E81A24517F4BCA71DA7D42782CCD23ED99DE0F64AF | |||
| 524 | Jays Booter.exe | C:\Users\admin\AppData\Local\Temp\267D66C.tmp | image | |
MD5:E01D53EF1CB4D3C1755F896AC71E3B51 | SHA256:BC93C7FADE6617E17601130F8C4419210D79264FBFFB95D0E7B01F5B2FD7B493 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report