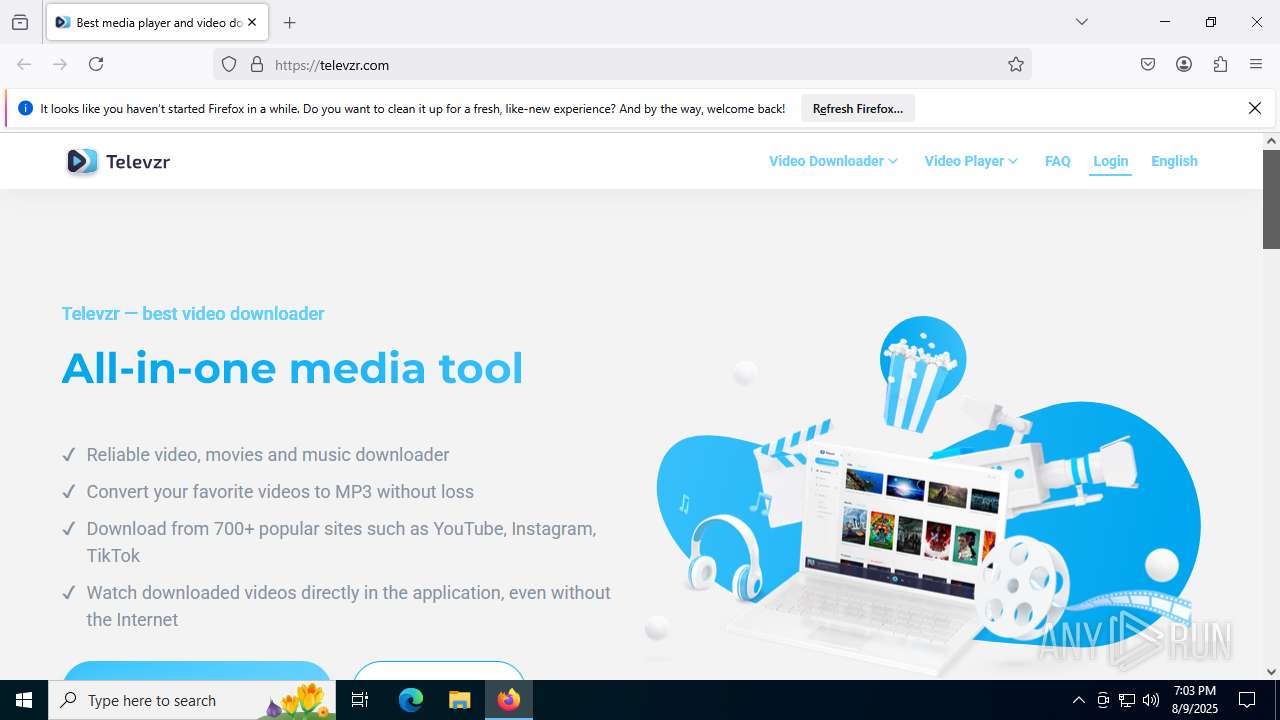
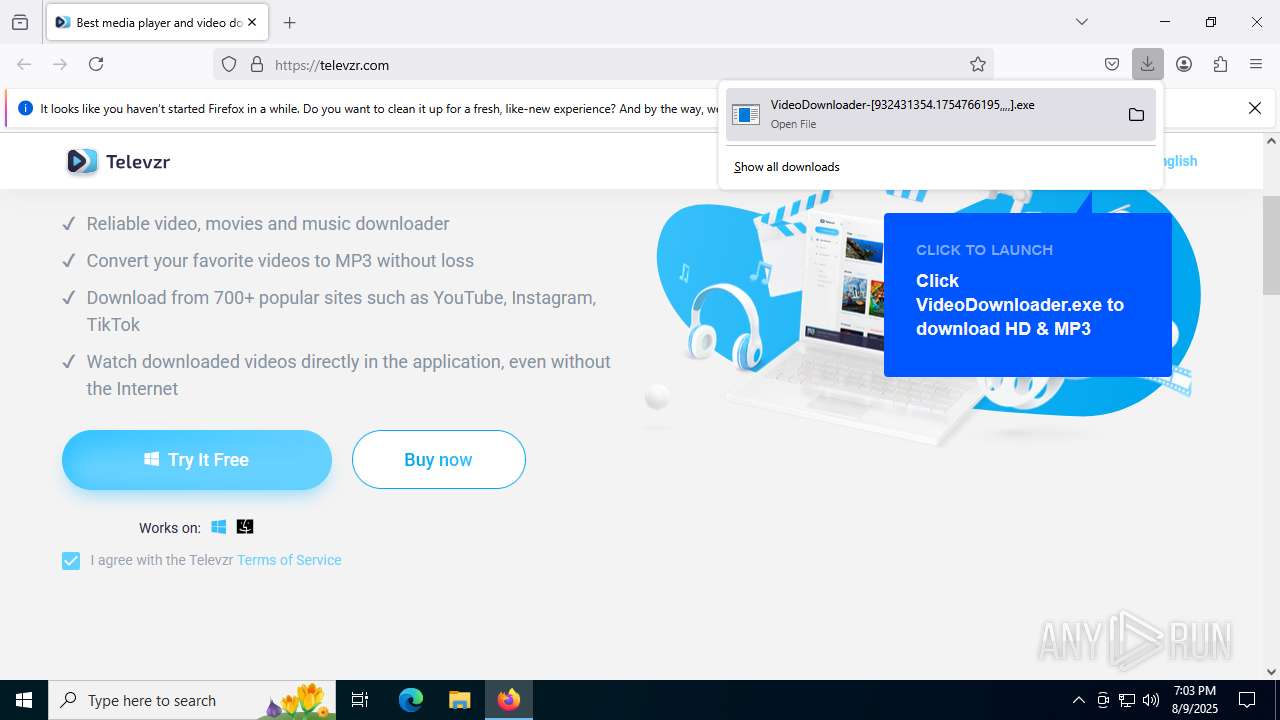
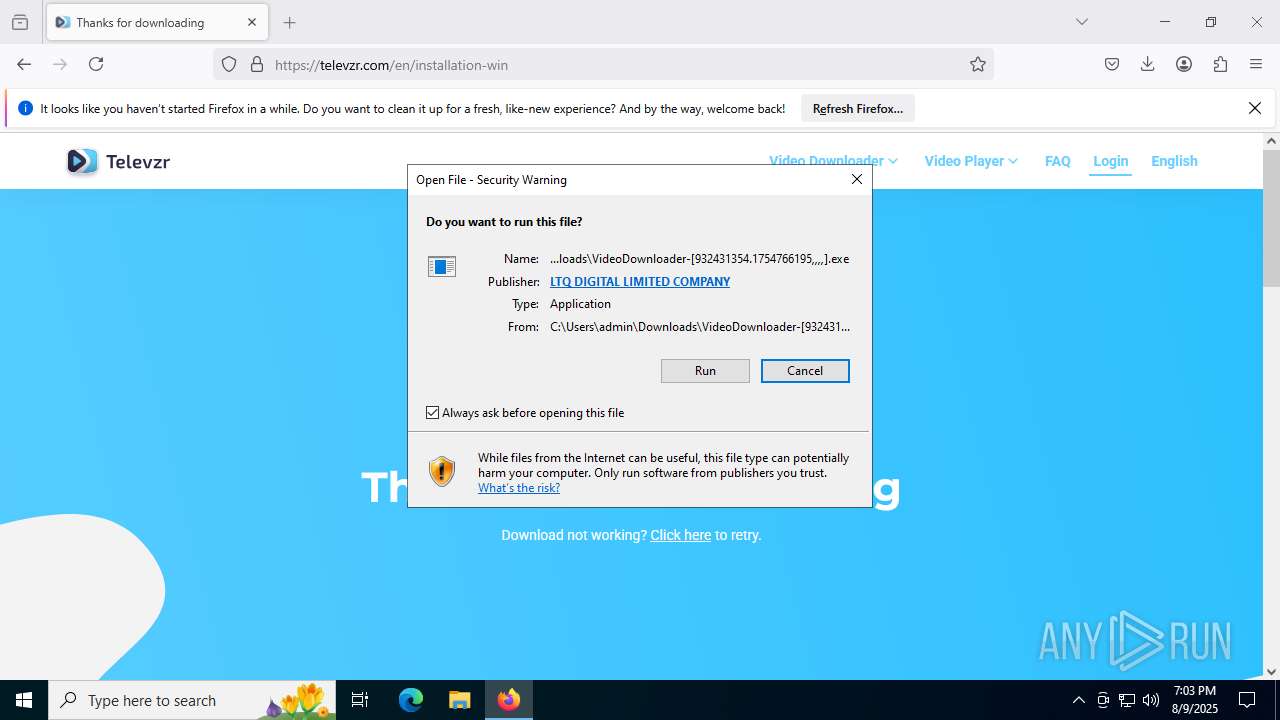
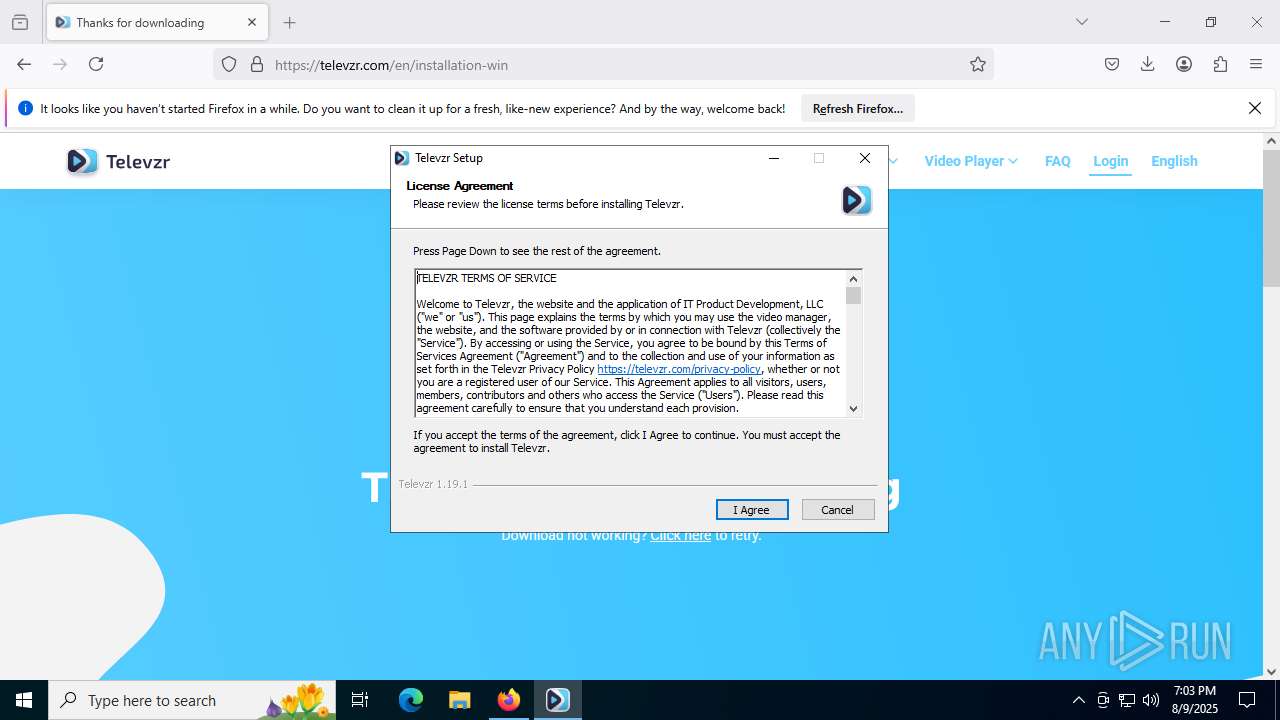
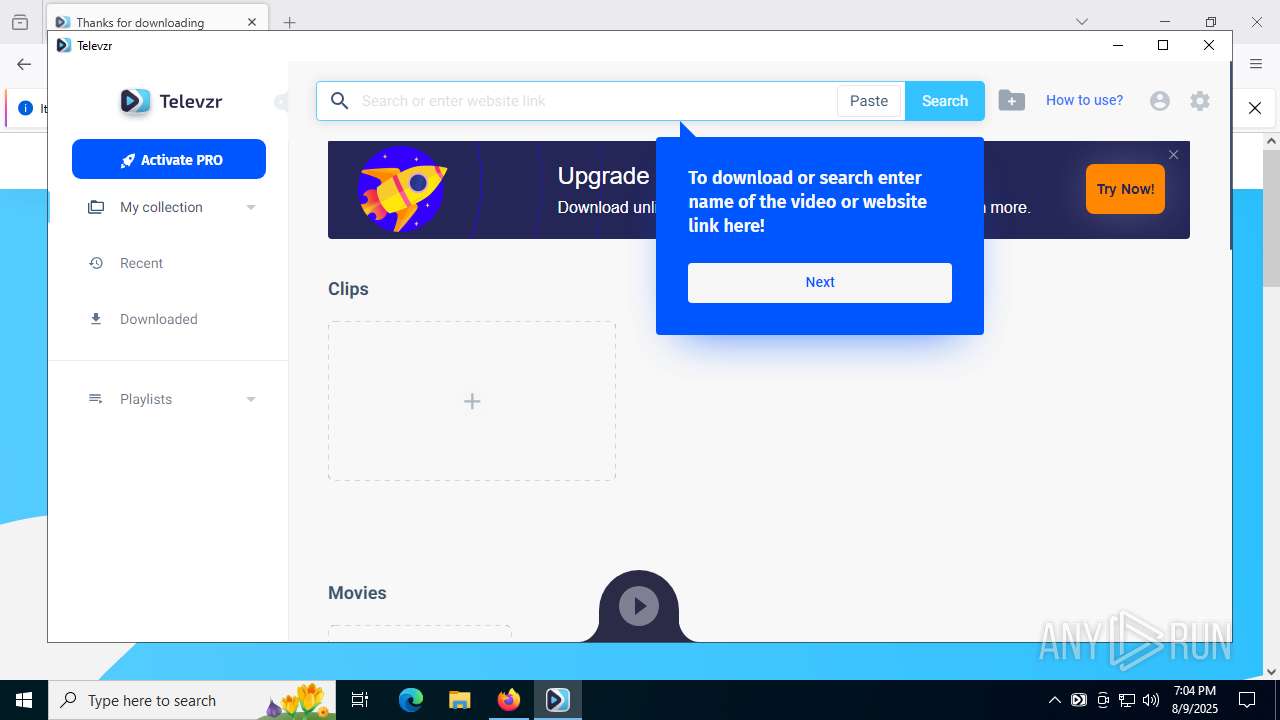
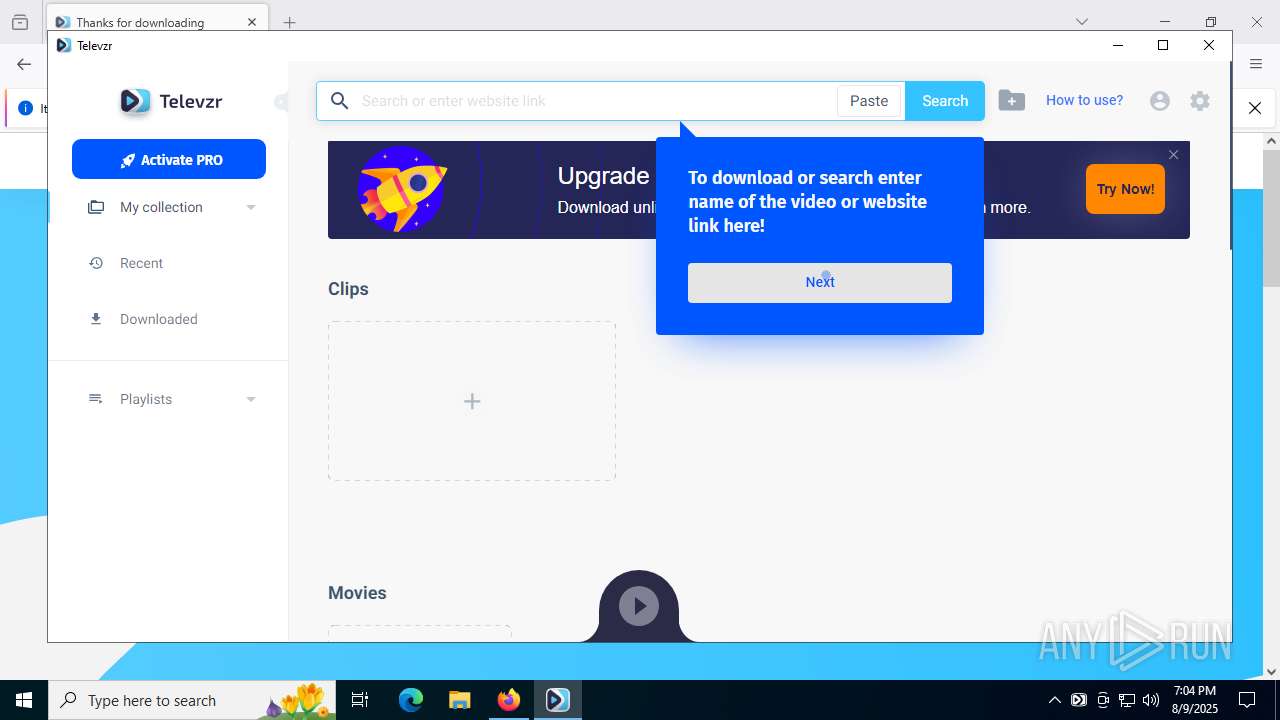
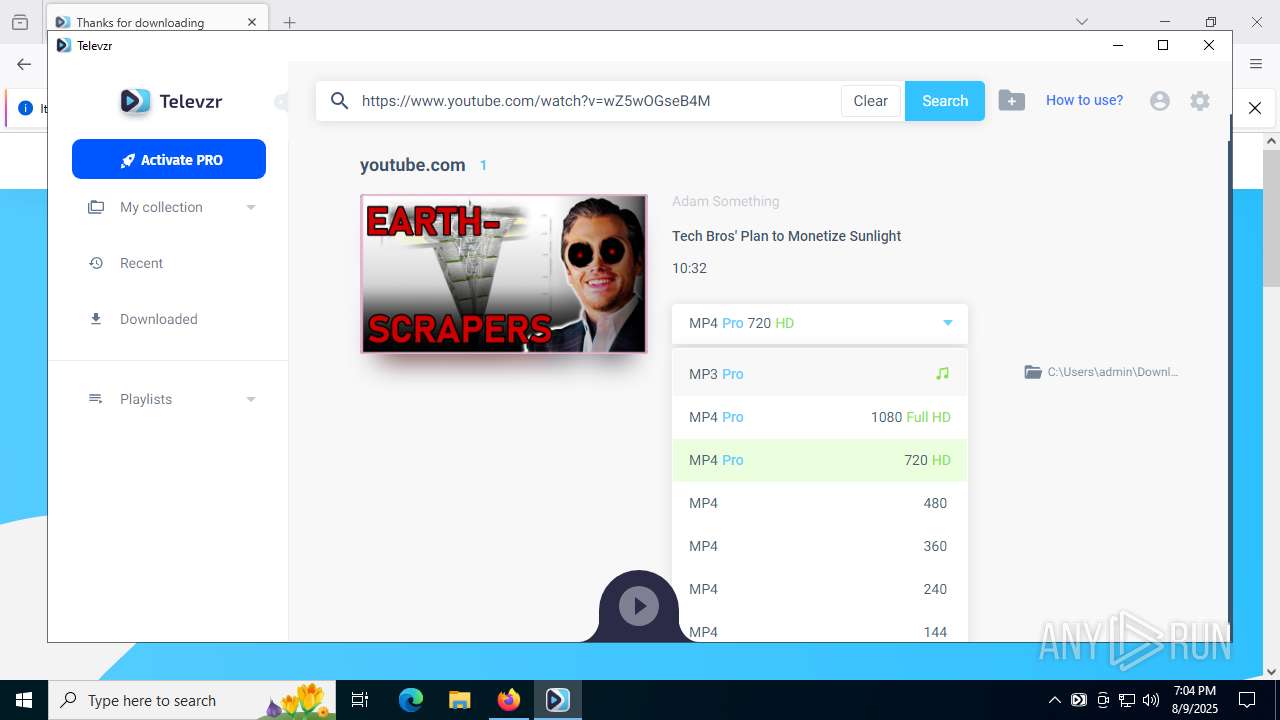
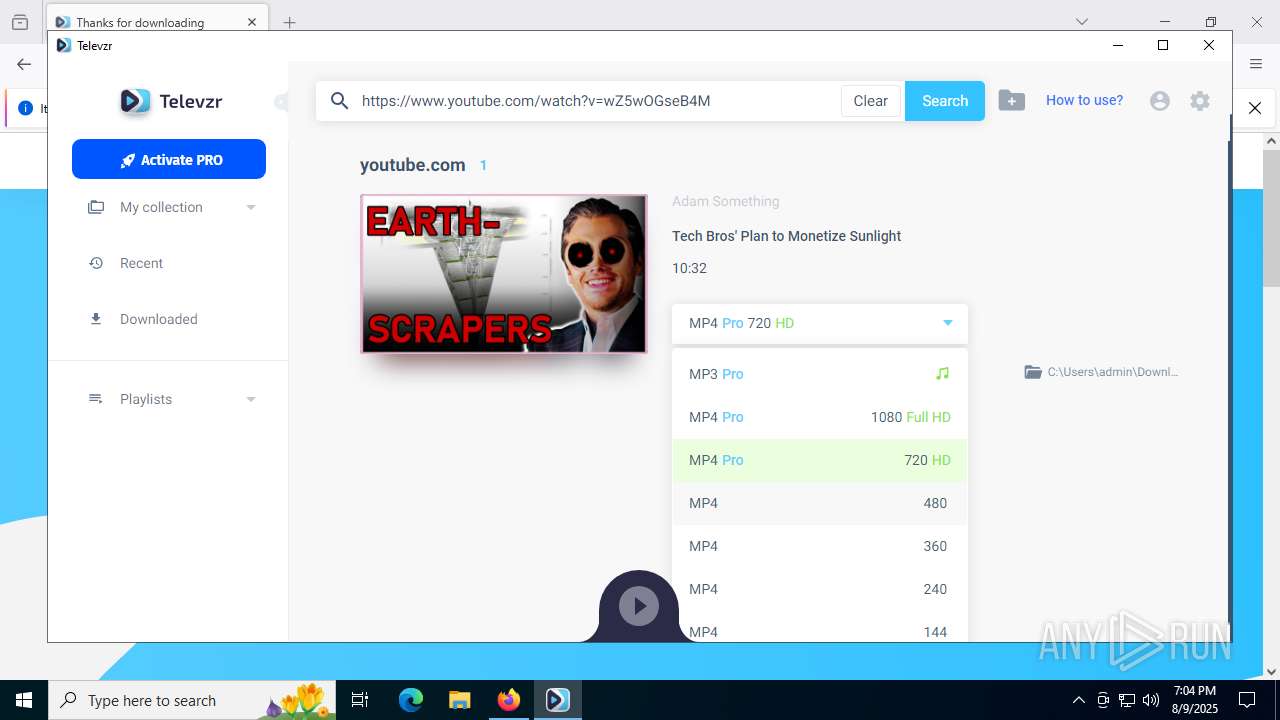
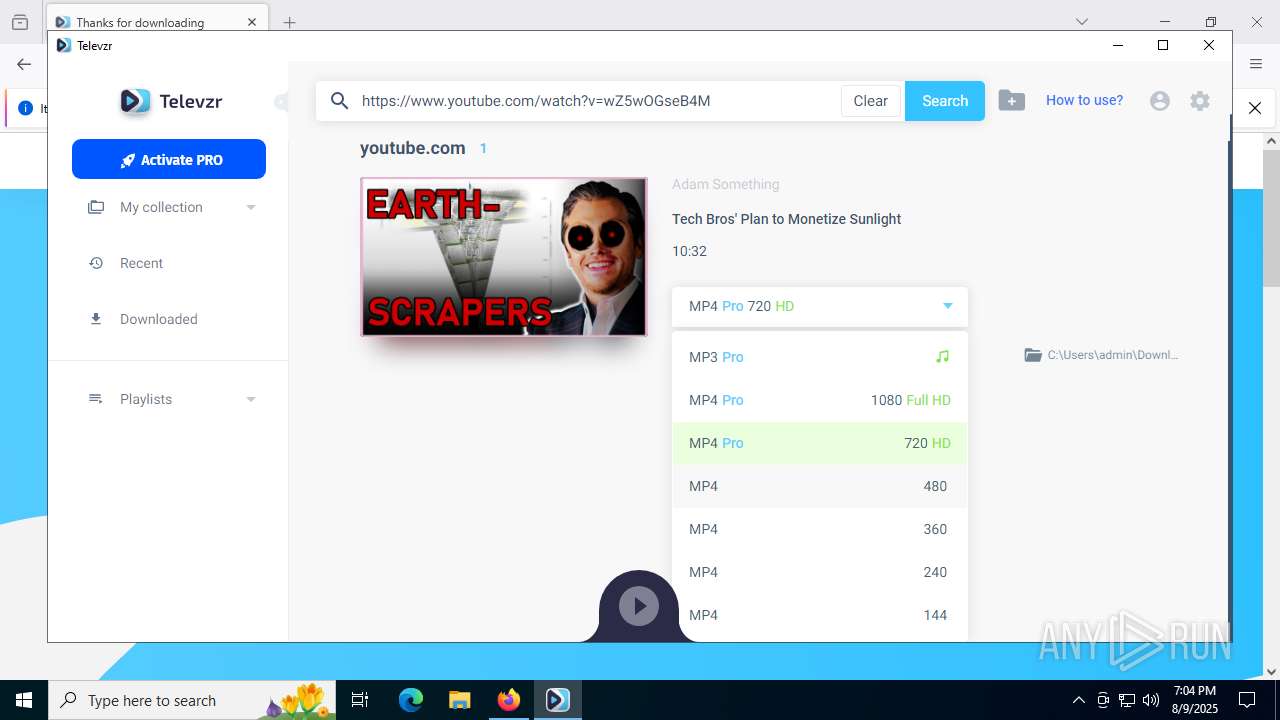
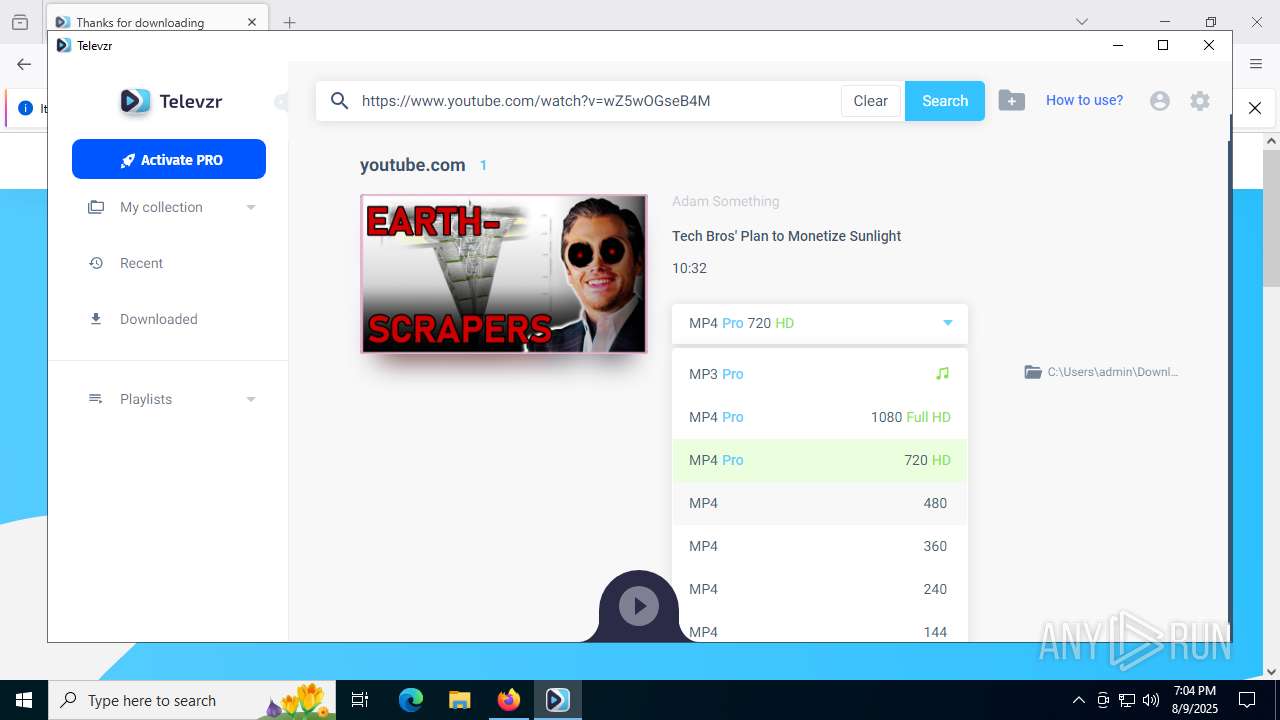
| URL: | https://televzr.com/ |
| Full analysis: | https://app.any.run/tasks/204458a0-5b9d-4097-a128-a33fd480ed5b |
| Verdict: | Malicious activity |
| Analysis date: | August 09, 2025, 19:03:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8CB1E108AF8651D7A4A64C49DB36B6C5 |
| SHA1: | 035ED7CF90FEB9F58436F577E6FC530F7C1F8EB2 |
| SHA256: | 2C3069363F03D67AC4FD92E544FF575C2BB6A1CF20C805AE35842DADDB09685D |
| SSDEEP: | 3:N8IObGGn:2Ikn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
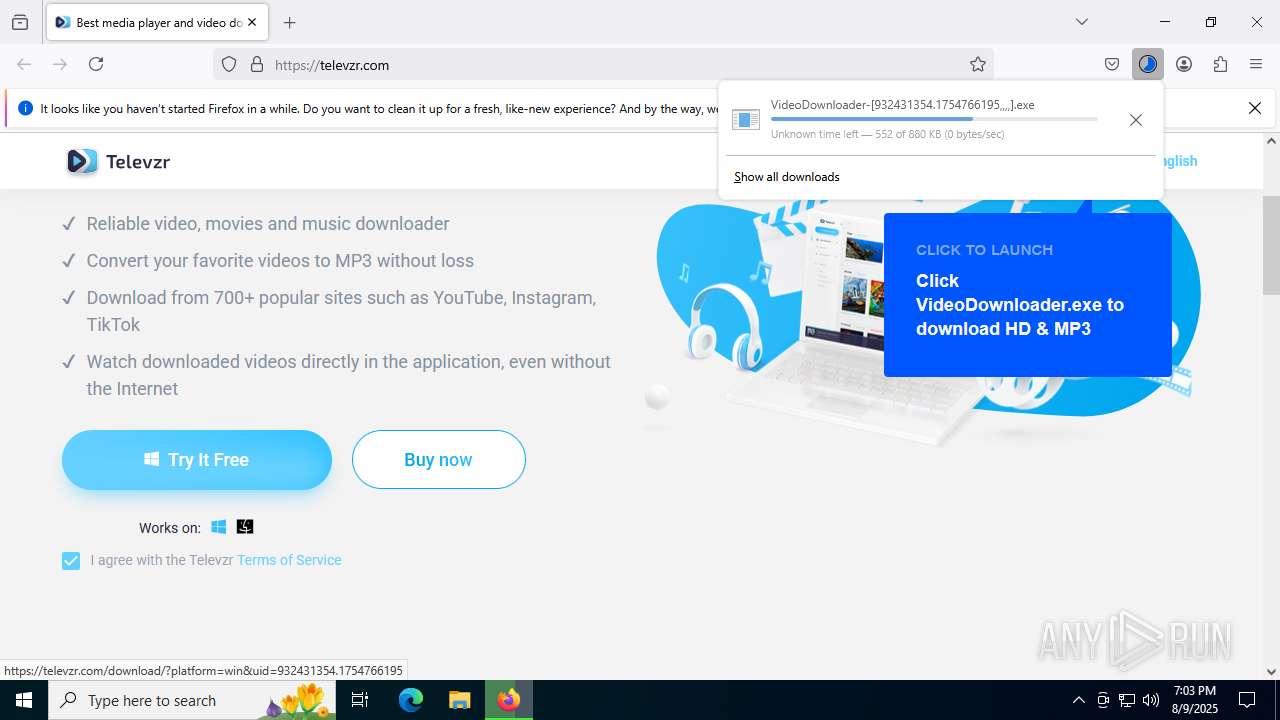
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
Executable content was dropped or overwritten
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- vcredist_x86.exe (PID: 1644)
- yt-dlp.exe (PID: 8556)
- yt-dlp.exe (PID: 8776)
- Televzr.exe (PID: 4168)
Starts CMD.EXE for commands execution
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- Televzr.exe (PID: 4168)
- yt-dlp.exe (PID: 8616)
- yt-dlp.exe (PID: 8832)
The process creates files with name similar to system file names
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
Starts application with an unusual extension
- cmd.exe (PID: 7576)
Get information on the list of running processes
- cmd.exe (PID: 1636)
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
Drops 7-zip archiver for unpacking
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
Creates a software uninstall entry
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
Process drops legitimate windows executable
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- vcredist_x86.exe (PID: 1644)
- msiexec.exe (PID: 8096)
- yt-dlp.exe (PID: 8556)
- yt-dlp.exe (PID: 8776)
Starts a Microsoft application from unusual location
- vcredist_x86.exe (PID: 1644)
- vcredist_x86.exe (PID: 2040)
Creates file in the systems drive root
- vcredist_x86.exe (PID: 1644)
- Televzr.exe (PID: 7368)
The process drops C-runtime libraries
- vcredist_x86.exe (PID: 1644)
- msiexec.exe (PID: 8096)
- yt-dlp.exe (PID: 8556)
- yt-dlp.exe (PID: 8776)
Reads security settings of Internet Explorer
- Setup.exe (PID: 4476)
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- Televzr.exe (PID: 8276)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 8096)
Application launched itself
- Televzr.exe (PID: 4168)
- yt-dlp.exe (PID: 8556)
- yt-dlp.exe (PID: 8776)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4380)
- cmd.exe (PID: 7608)
- cmd.exe (PID: 7812)
Process drops python dynamic module
- yt-dlp.exe (PID: 8556)
- yt-dlp.exe (PID: 8776)
Loads Python modules
- yt-dlp.exe (PID: 8616)
- yt-dlp.exe (PID: 8832)
INFO
Executable content was dropped or overwritten
- firefox.exe (PID: 1392)
- msiexec.exe (PID: 8096)
Reads Microsoft Office registry keys
- firefox.exe (PID: 1392)
Application launched itself
- firefox.exe (PID: 3844)
- firefox.exe (PID: 1392)
Checks supported languages
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- more.com (PID: 1496)
- vcredist_x86.exe (PID: 1644)
- Setup.exe (PID: 4476)
- msiexec.exe (PID: 8096)
- Televzr.exe (PID: 4168)
- Televzr.exe (PID: 1180)
- Televzr.exe (PID: 7604)
- Televzr.exe (PID: 7596)
- Televzr.exe (PID: 7368)
- yt-dlp.exe (PID: 8556)
- Televzr.exe (PID: 7272)
- yt-dlp.exe (PID: 8616)
- ffmpeg.exe (PID: 8712)
- yt-dlp.exe (PID: 8776)
- yt-dlp.exe (PID: 8832)
- ffmpeg.exe (PID: 8972)
- ffmpeg.exe (PID: 9000)
- ffprobe.exe (PID: 9096)
- Televzr.exe (PID: 8276)
The sample compiled with english language support
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- firefox.exe (PID: 1392)
- vcredist_x86.exe (PID: 1644)
- msiexec.exe (PID: 8096)
- yt-dlp.exe (PID: 8776)
- yt-dlp.exe (PID: 8556)
Create files in a temporary directory
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- Setup.exe (PID: 4476)
- Televzr.exe (PID: 4168)
- yt-dlp.exe (PID: 8556)
- yt-dlp.exe (PID: 8776)
Reads the software policy settings
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- Setup.exe (PID: 4476)
- msiexec.exe (PID: 8096)
- slui.exe (PID: 8332)
- Televzr.exe (PID: 8276)
Creates files or folders in the user directory
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- msiexec.exe (PID: 8096)
- Televzr.exe (PID: 4168)
- Televzr.exe (PID: 7604)
- yt-dlp.exe (PID: 8616)
- Televzr.exe (PID: 8276)
- Televzr.exe (PID: 7368)
Process checks computer location settings
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- Televzr.exe (PID: 4168)
- Televzr.exe (PID: 1180)
- Televzr.exe (PID: 7368)
Reads the machine GUID from the registry
- vcredist_x86.exe (PID: 1644)
- Setup.exe (PID: 4476)
- msiexec.exe (PID: 8096)
- Televzr.exe (PID: 4168)
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- yt-dlp.exe (PID: 8616)
- yt-dlp.exe (PID: 8832)
- Televzr.exe (PID: 8276)
Reads the computer name
- vcredist_x86.exe (PID: 1644)
- Setup.exe (PID: 4476)
- msiexec.exe (PID: 8096)
- Televzr.exe (PID: 4168)
- Televzr.exe (PID: 7596)
- Televzr.exe (PID: 7604)
- Televzr.exe (PID: 7272)
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- yt-dlp.exe (PID: 8556)
- yt-dlp.exe (PID: 8616)
- yt-dlp.exe (PID: 8776)
- Televzr.exe (PID: 8276)
- yt-dlp.exe (PID: 8832)
The sample compiled with chinese language support
- vcredist_x86.exe (PID: 1644)
- msiexec.exe (PID: 8096)
The sample compiled with Italian language support
- vcredist_x86.exe (PID: 1644)
- msiexec.exe (PID: 8096)
The sample compiled with french language support
- vcredist_x86.exe (PID: 1644)
- msiexec.exe (PID: 8096)
The sample compiled with german language support
- vcredist_x86.exe (PID: 1644)
- msiexec.exe (PID: 8096)
The sample compiled with russian language support
- vcredist_x86.exe (PID: 1644)
- msiexec.exe (PID: 8096)
The sample compiled with spanish language support
- vcredist_x86.exe (PID: 1644)
- msiexec.exe (PID: 8096)
The sample compiled with japanese language support
- vcredist_x86.exe (PID: 1644)
- msiexec.exe (PID: 8096)
The sample compiled with korean language support
- vcredist_x86.exe (PID: 1644)
- msiexec.exe (PID: 8096)
Reads CPU info
- Setup.exe (PID: 4476)
Creates a software uninstall entry
- msiexec.exe (PID: 8096)
Manual execution by a user
- Televzr.exe (PID: 4168)
Checks proxy server information
- Televzr.exe (PID: 4168)
- VideoDownloader-[932431354.1754766195,,,,].exe (PID: 7272)
- yt-dlp.exe (PID: 8616)
- yt-dlp.exe (PID: 8832)
- slui.exe (PID: 8332)
Checks operating system version
- yt-dlp.exe (PID: 8616)
- yt-dlp.exe (PID: 8832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
214
Monitored processes
68
Malicious processes
6
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1180 | "C:\Users\admin\AppData\Local\televzr\Televzr.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\Televzr Desktop" --standard-schemes=app --secure-schemes=app --cors-schemes=fs --fetch-schemes=app,fs --app-user-model-id=televzr.televzr_desktop --app-path="C:\Users\admin\AppData\Local\televzr\resources\app.asar" --no-sandbox --no-zygote --first-renderer-process --no-sandbox --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --mojo-platform-channel-handle=2528 --field-trial-handle=1784,i,13255110423695890236,4865621283600260083,262144 --enable-features=kWebSQLAccess --disable-features=HardwareMediaKeyHandling,SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version /prefetch:1 | C:\Users\admin\AppData\Local\televzr\Televzr.exe | — | Televzr.exe | |||||||||||
User: admin Company: LTQ DIGITAL LIMITED COMPANY Integrity Level: MEDIUM Description: Televzr Desktop Exit code: 0 Version: 1.19.1 Modules
| |||||||||||||||
| 1288 | C:\WINDOWS\system32\reg.exe ADD "HKCU\Software\Classes\televzr\shell\open\command" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://televzr.com/ | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 1496 | more | C:\Windows\SysWOW64\more.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1588 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 4112 -prefsLen 44877 -prefMapHandle 4116 -prefMapSize 272997 -jsInitHandle 4120 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 4128 -initialChannelId {44819715-ef05-40e5-8790-29f64c3894d5} -parentPid 1392 -crashReporter "\\.\pipe\gecko-crash-server-pipe.1392" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 5 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 1636 | "C:\WINDOWS\system32\cmd.exe" /c tasklist /FI "USERNAME eq %USERNAME%" /FI "IMAGENAME eq Televzr.exe" /FO csv | "C:\WINDOWS\system32\find.exe" "Televzr.exe" | C:\Windows\SysWOW64\cmd.exe | — | VideoDownloader-[932431354.1754766195,,,,].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1644 | "C:\Users\admin\AppData\Local\Temp\nsn1302.tmp\vcredist_x86.exe" /install /quiet /norestart | C:\Users\admin\AppData\Local\Temp\nsn1302.tmp\vcredist_x86.exe | VideoDownloader-[932431354.1754766195,,,,].exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2010 x86 Redistributable Setup Exit code: 0 Version: 10.0.40219.325 Modules
| |||||||||||||||
| 1652 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1800 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | "C:\Users\admin\AppData\Local\Temp\nsn1302.tmp\vcredist_x86.exe" /install /quiet /norestart | C:\Users\admin\AppData\Local\Temp\nsn1302.tmp\vcredist_x86.exe | — | VideoDownloader-[932431354.1754766195,,,,].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual C++ 2010 x86 Redistributable Setup Exit code: 3221226540 Version: 10.0.40219.325 Modules
| |||||||||||||||
Total events
36 762
Read events
36 129
Write events
591
Delete events
42
Modification events
| (PID) Process: | (1392) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (1392) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7272) VideoDownloader-[932431354.1754766195,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\c6ba130a-455e-5073-9dbd-f9d1f65c1562 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\televzr | |||
| (PID) Process: | (7272) VideoDownloader-[932431354.1754766195,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7272) VideoDownloader-[932431354.1754766195,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7272) VideoDownloader-[932431354.1754766195,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7272) VideoDownloader-[932431354.1754766195,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\c6ba130a-455e-5073-9dbd-f9d1f65c1562 |
| Operation: | write | Name: | KeepShortcuts |
Value: true | |||
| (PID) Process: | (7272) VideoDownloader-[932431354.1754766195,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\c6ba130a-455e-5073-9dbd-f9d1f65c1562 |
| Operation: | write | Name: | ShortcutName |
Value: Televzr | |||
| (PID) Process: | (7272) VideoDownloader-[932431354.1754766195,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\c6ba130a-455e-5073-9dbd-f9d1f65c1562 |
| Operation: | write | Name: | DisplayName |
Value: Televzr | |||
| (PID) Process: | (7272) VideoDownloader-[932431354.1754766195,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\c6ba130a-455e-5073-9dbd-f9d1f65c1562 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Users\admin\AppData\Local\televzr\Uninstall Televzr.exe" /currentuser | |||
Executable files
222
Suspicious files
577
Text files
227
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1392 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 1392 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 1392 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1392 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:3134ED3F12E4F4F8643DB90043B0FD7B | SHA256:26E4F122034D7A03F6DA0E707799B09CBEEBDAF8D7A3133A1F7BD894AC72EEA1 | |||
| 1392 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1392 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1392 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:6A30B2316F18C41DD8D09C68DF93FFD3 | SHA256:AC58BD63AEE5E1C2B9A359110E96C4823C4028E7EA36F5B3BEDE24D8D4B876A8 | |||
| 1392 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | binary | |
MD5:EFCC9E68E66381B0D3A720A07507C821 | SHA256:0B0AB1E02E6E3991414BA1817EF69A56090206F49E16266C9F6B4E6E3E3C4B8F | |||
| 1392 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:F34E18536FDA82D4A2AA3B4C9CDA02A9 | SHA256:6D2F837D96BA8023A4BB9019A2415CAAABE0758D61E20E37845840F53E4E687F | |||
| 1392 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
125
DNS requests
177
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1392 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
1392 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
1392 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
1392 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/s/wr3/k58 | unknown | — | — | whitelisted |
1392 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
1392 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
1392 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
1392 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
1392 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
1392 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5468 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1392 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1392 | firefox.exe | 104.21.25.13:443 | televzr.com | CLOUDFLARENET | — | whitelisted |
1392 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
1392 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
1392 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
content-signature-chains.prod.autograph.services.mozaws.net |
| whitelisted |
televzr.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
mc.prod.ads.prod.webservices.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Misc activity | ET INFO EXE - Served Attached HTTP |
— | — | Potentially Bad Traffic | ET INFO Possible Firefox Plugin install |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Misc activity | ET INFO EXE - Served Attached HTTP |
— | — | Misc activity | ET INFO Packed Executable Download |
Process | Message |
|---|---|
Setup.exe | The operation completed successfully.
|