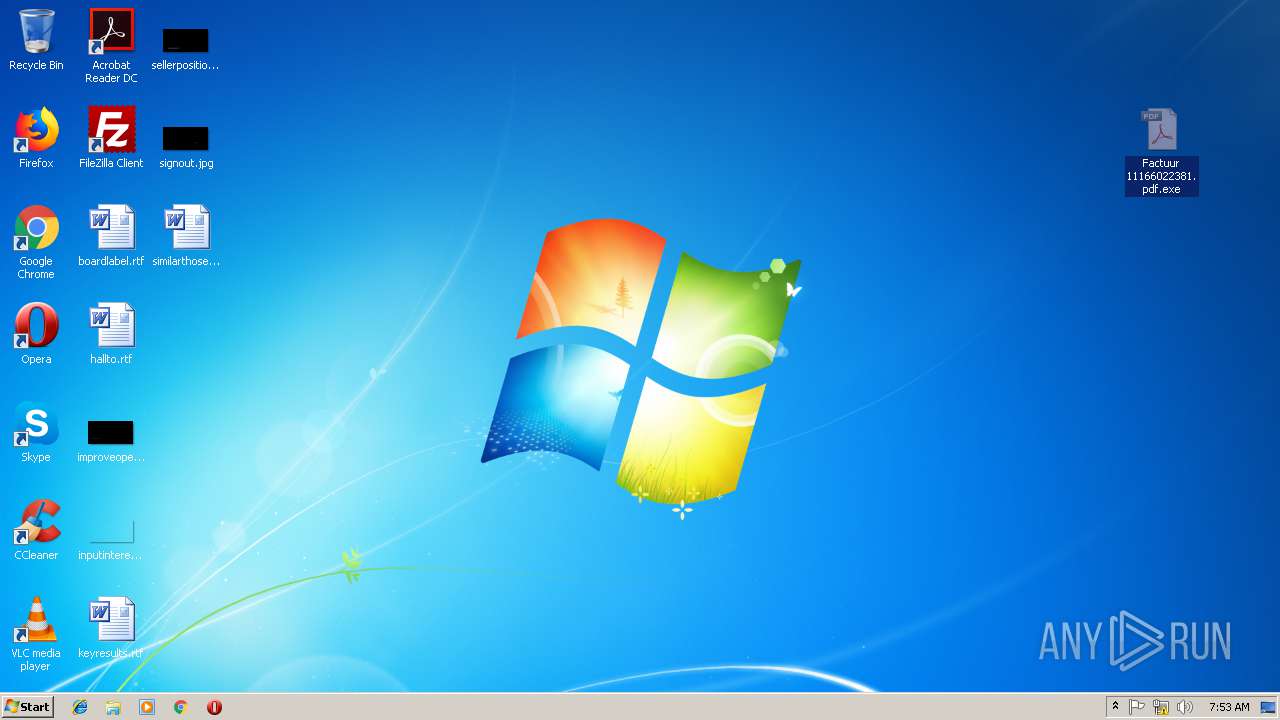
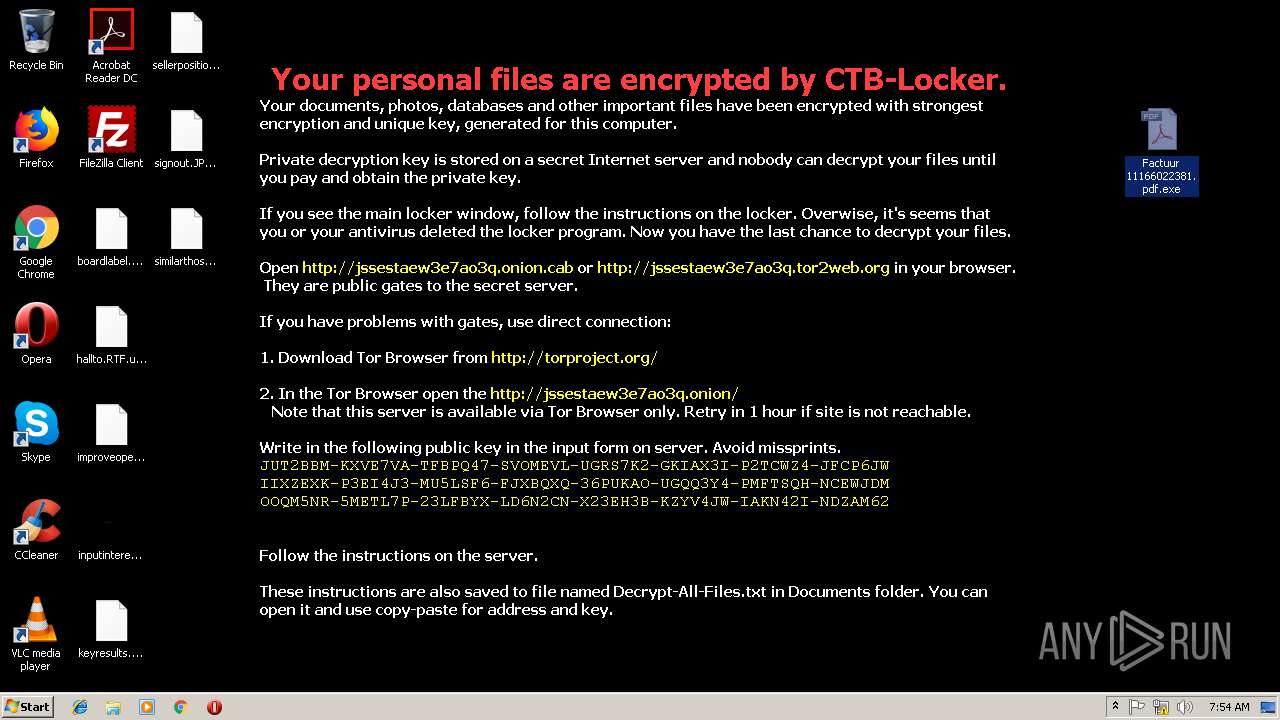
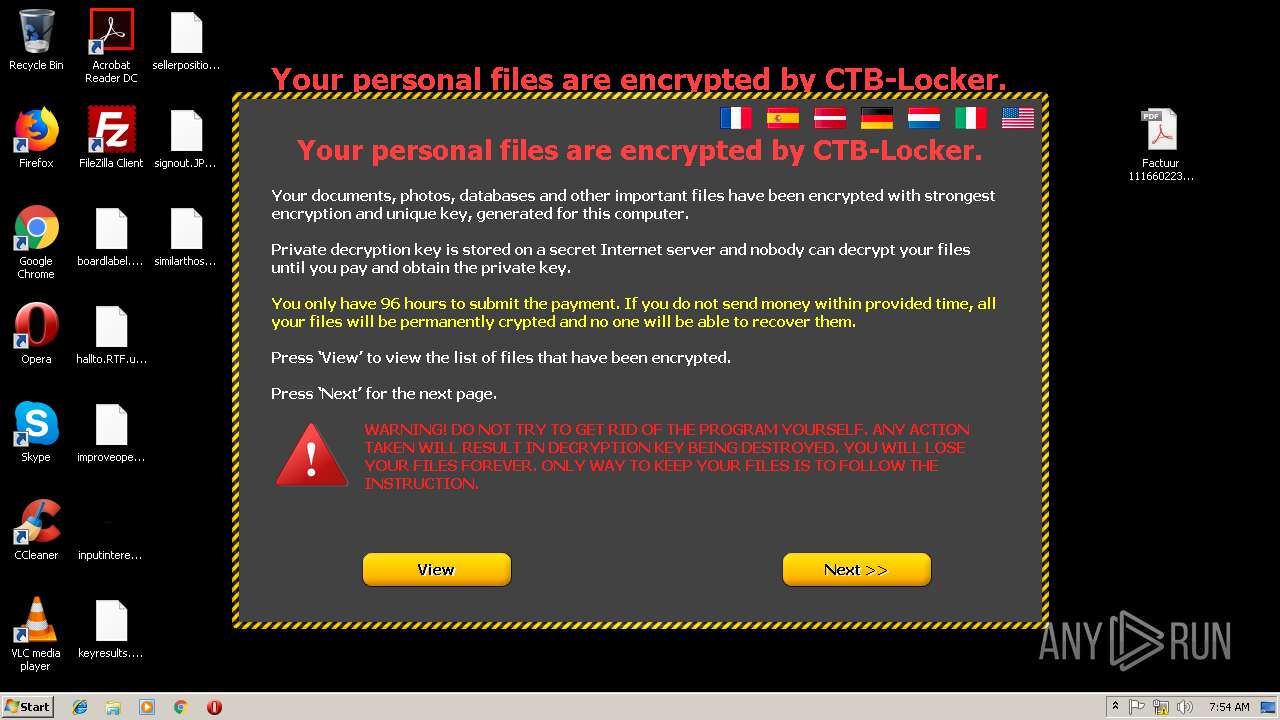
| File name: | Factuur 11166022381.pdf.7z |
| Full analysis: | https://app.any.run/tasks/53434097-1433-4396-b3b9-f68586358eed |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2018, 07:53:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
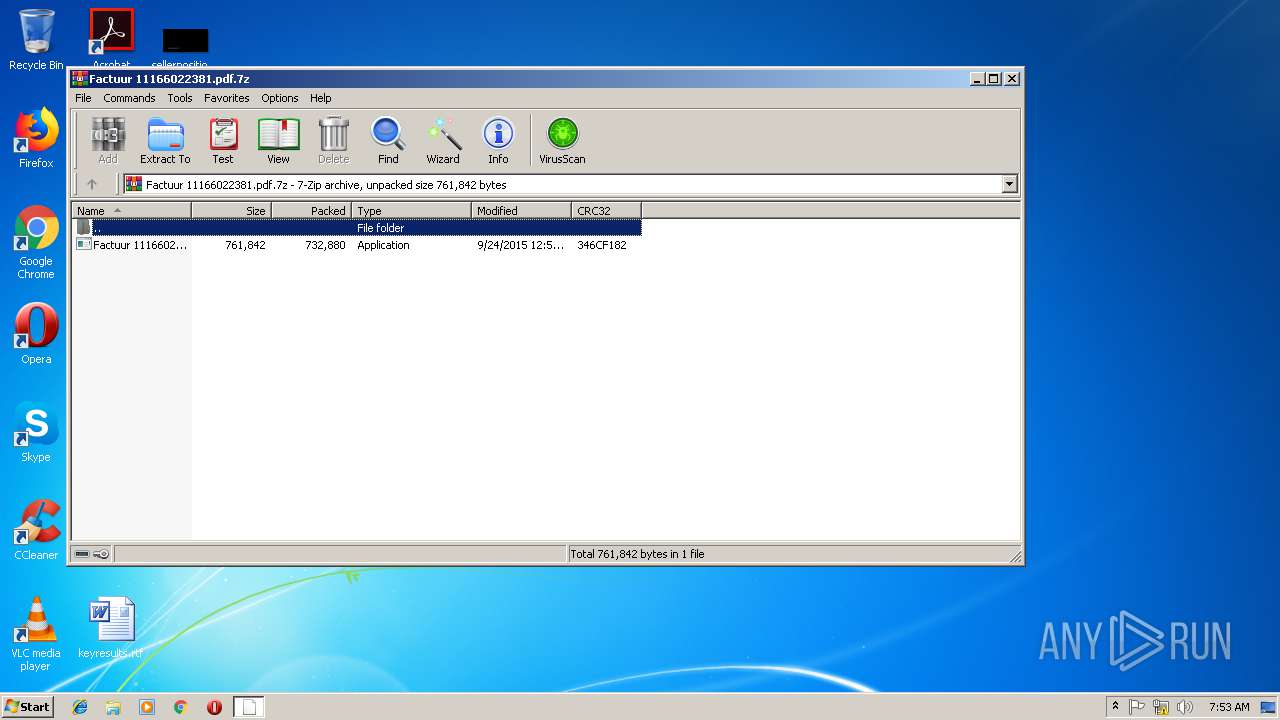
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 122C74AC209D70F30472E5A047DE3A49 |
| SHA1: | 91CEF35DE43A7A9948A4A5263A26B8ECDA66F669 |
| SHA256: | 2C10F6A01D5A5378B58761B84FC0A2E68D100448510AC739F94E71D2DBCD0D22 |
| SSDEEP: | 12288:VJxP0/YkUrErD+Ai4fPa27OkCaJUCEkhMNNwngw3CEgxh7TzZZY:VTkYkUu+QPa1kbJUCFaNNugwlq7nZZY |
MALICIOUS
Application was dropped or rewritten from another process
- ourkble.exe (PID: 3280)
- Factuur 11166022381.pdf.exe (PID: 3672)
- Factuur 11166022381.pdf.exe (PID: 3260)
- ourkble.exe (PID: 1128)
Loads dropped or rewritten executable
- Factuur 11166022381.pdf.exe (PID: 3672)
- ourkble.exe (PID: 3280)
Runs injected code in another process
- ourkble.exe (PID: 1128)
Loads the Task Scheduler COM API
- Factuur 11166022381.pdf.exe (PID: 3260)
Application was injected by another process
- explorer.exe (PID: 1728)
SUSPICIOUS
Application launched itself
- Factuur 11166022381.pdf.exe (PID: 3672)
- ourkble.exe (PID: 3280)
Executable content was dropped or overwritten
- Factuur 11166022381.pdf.exe (PID: 3672)
- Factuur 11166022381.pdf.exe (PID: 3260)
- ourkble.exe (PID: 3280)
Creates files in the program directory
- ourkble.exe (PID: 1128)
- explorer.exe (PID: 1728)
Reads Internet Cache Settings
- ourkble.exe (PID: 1128)
Changes the desktop background image
- explorer.exe (PID: 1728)
Reads internet explorer settings
- ourkble.exe (PID: 1128)
INFO
Dropped object may contain URL to Tor Browser
- explorer.exe (PID: 1728)
Dropped object may contain TOR URL's
- explorer.exe (PID: 1728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
38
Monitored processes
6
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1128 | "C:\Users\admin\AppData\Local\Temp\ourkble.exe" | C:\Users\admin\AppData\Local\Temp\ourkble.exe | — | ourkble.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1728 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3132 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Factuur 11166022381.pdf.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
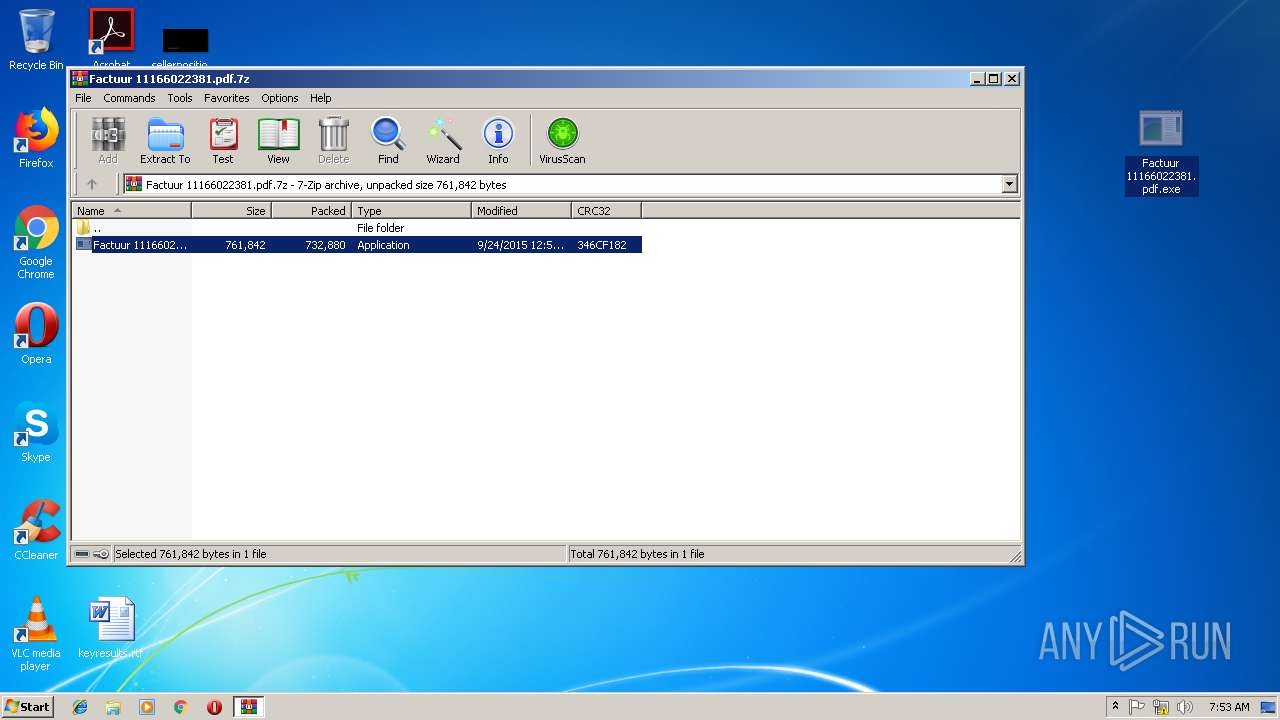
| 3260 | "C:\Users\admin\Desktop\Factuur 11166022381.pdf.exe" | C:\Users\admin\Desktop\Factuur 11166022381.pdf.exe | Factuur 11166022381.pdf.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3280 | C:\Users\admin\AppData\Local\Temp\ourkble.exe | C:\Users\admin\AppData\Local\Temp\ourkble.exe | taskeng.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 3672 | "C:\Users\admin\Desktop\Factuur 11166022381.pdf.exe" | C:\Users\admin\Desktop\Factuur 11166022381.pdf.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
Total events
2 377
Read events
2 335
Write events
40
Delete events
2
Modification events
| (PID) Process: | (3132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3132) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Factuur 11166022381.pdf.7z | |||
| (PID) Process: | (3132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3132) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1728) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (1728) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
6
Suspicious files
129
Text files
5
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3132 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3132.40612\Factuur 11166022381.pdf.exe | — | |
MD5:— | SHA256:— | |||
| 3672 | Factuur 11166022381.pdf.exe | C:\Users\admin\AppData\Local\Temp\nsrD3E0.tmp | — | |
MD5:— | SHA256:— | |||
| 3280 | ourkble.exe | C:\Users\admin\AppData\Local\Temp\nsb12FC.tmp | — | |
MD5:— | SHA256:— | |||
| 1728 | explorer.exe | C:\Users\admin\AppData\Local\Temp\leafshoa.tmp | — | |
MD5:— | SHA256:— | |||
| 1728 | explorer.exe | C:\Users\admin\AppData\Local\Temp\lgdlohoa.tmp | — | |
MD5:— | SHA256:— | |||
| 1728 | explorer.exe | C:\Users\admin\AppData\Local\Temp\laukohoa.tmp | — | |
MD5:— | SHA256:— | |||
| 1728 | explorer.exe | C:\Users\admin\AppData\Local\Temp\leablhoa.tmp | — | |
MD5:— | SHA256:— | |||
| 1728 | explorer.exe | C:\Users\admin\AppData\Local\Temp\lewiwioa.tmp | — | |
MD5:— | SHA256:— | |||
| 1728 | explorer.exe | C:\Users\admin\AppData\Local\Temp\lmejwioa.tmp | — | |
MD5:— | SHA256:— | |||
| 1728 | explorer.exe | C:\Users\admin\AppData\Local\Temp\lmydrhoa.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report