| URL: | zaibcrack.com |
| Full analysis: | https://app.any.run/tasks/f1efb3b4-2c44-45a3-a6c5-435975901be5 |
| Verdict: | Malicious activity |
| Analysis date: | January 06, 2024, 12:29:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 4073AB2A951D96C7169AC185FB8B5CB4 |
| SHA1: | 24D4B3814FB28CA88626777B1EE434ED12A9C8B3 |
| SHA256: | 2C0F927AABCFC91A422FF9C536774C328A3DBAB88F9367E982EA3FF38D8F39A2 |
| SSDEEP: | 3:MXEMTn:Qn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 2044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2044 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1740 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2044 CREDAT:2888979 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2044 | "C:\Program Files\Internet Explorer\iexplore.exe" "zaibcrack.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
18 438
Read events
18 357
Write events
79
Delete events
2
Modification events
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
43
Text files
58
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:EF2C9D9E5E27052CE3E0A1552423A1CD | SHA256:EDAFC61F668DEB8634F309AAACE118E57824DDD0594F58898CDD9B4237CD3099 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:5B31882CAD88A1EC64186B9FDBFCA9AB | SHA256:1C4DC99DA44CF7672EEBF4C65FB4837CEDB80B0A6A379B5DE6D58C0D0F33F1FF | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:8A91A9A0004E4A4E18969EA6FE95BBE9 | SHA256:396E62742CA5CD37EAE3CA1089A0070485D6E464C1BCD7E47C0ABFB6808F0AE8 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:BF3E2DBFF715E6EAD50E708669FB2490 | SHA256:3A2586735A95E8D78D7AE1D736894D6C778D1DD617850E89DDFC003027AF751F | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\7YE99JQ2.htm | html | |
MD5:A7855F73C54AA674F668DFDB924C6A6A | SHA256:B5240DAF5B758510BF1EF85E37D597A83F64C48CB4F21A22728DDD6BEA6B1006 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\L29VSDD5 | text | |
MD5:FDA44910DEB1A460BE4AC5D56D61D837 | SHA256:933B971C6388D594A23FA1559825DB5BEC8ADE2DB1240AA8FC9D0C684949E8C9 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\e-202401[1].js | text | |
MD5:2567B82FC5B4900C78BE291E6A957E99 | SHA256:CA7752FB33CF3A98C0F29BC4EEC563112025DA4109A0DCC69DABF5F861751258 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab22E.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
64
DNS requests
33
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
864 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | binary | 1.42 Kb | unknown |
864 | iexplore.exe | GET | 200 | 2.19.126.137:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1a2f195c97973615 | unknown | compressed | 65.2 Kb | unknown |
864 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | binary | 980 b | unknown |
864 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQClj3zJOwEs2AlR6v%2BfUXog | unknown | binary | 472 b | unknown |
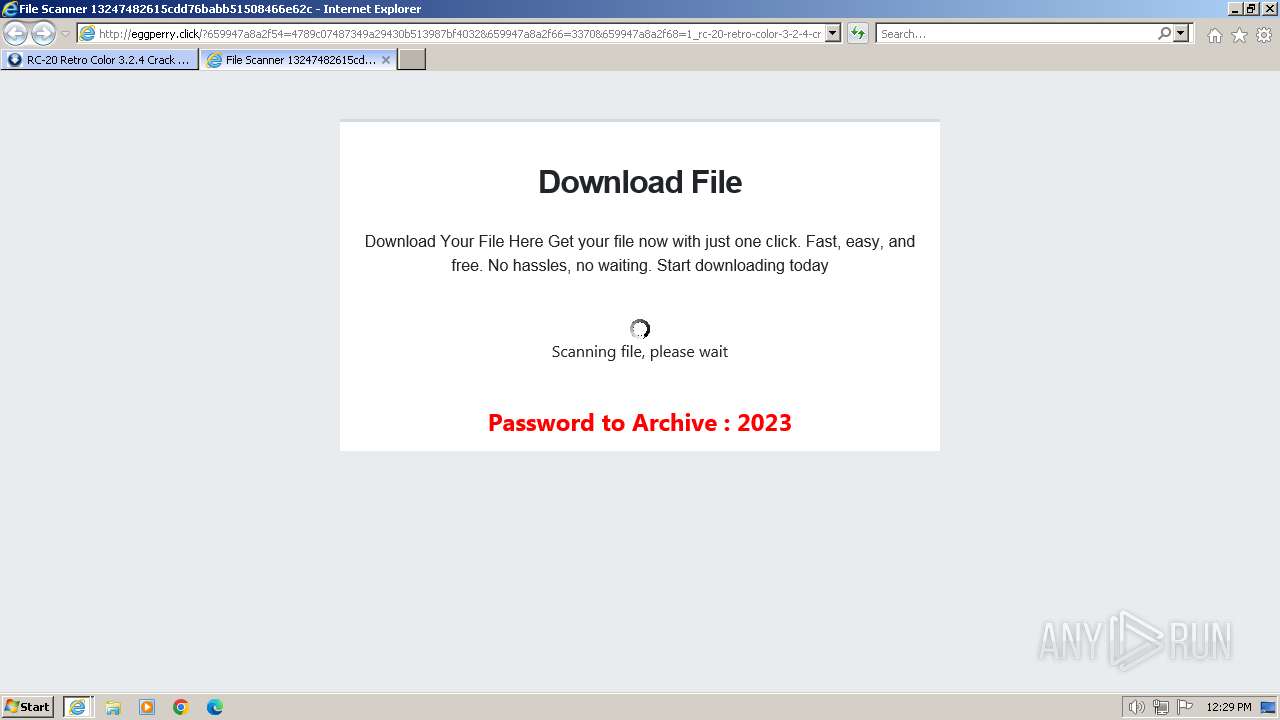
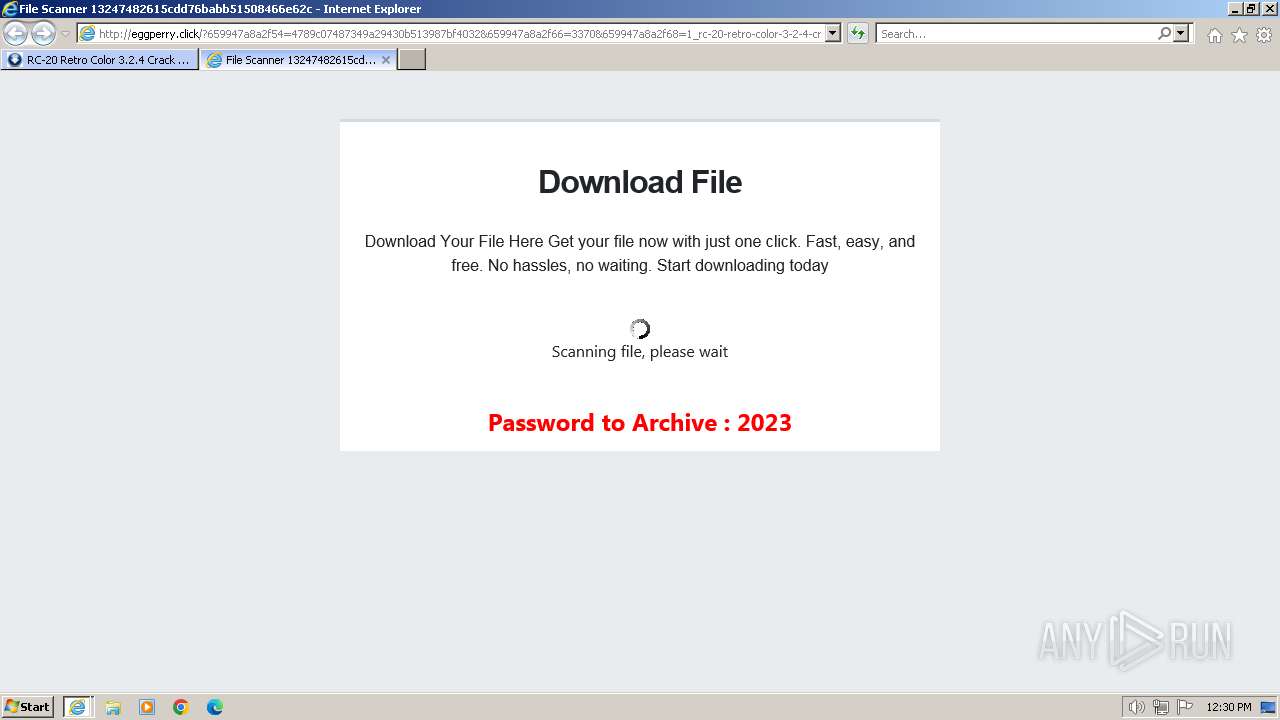
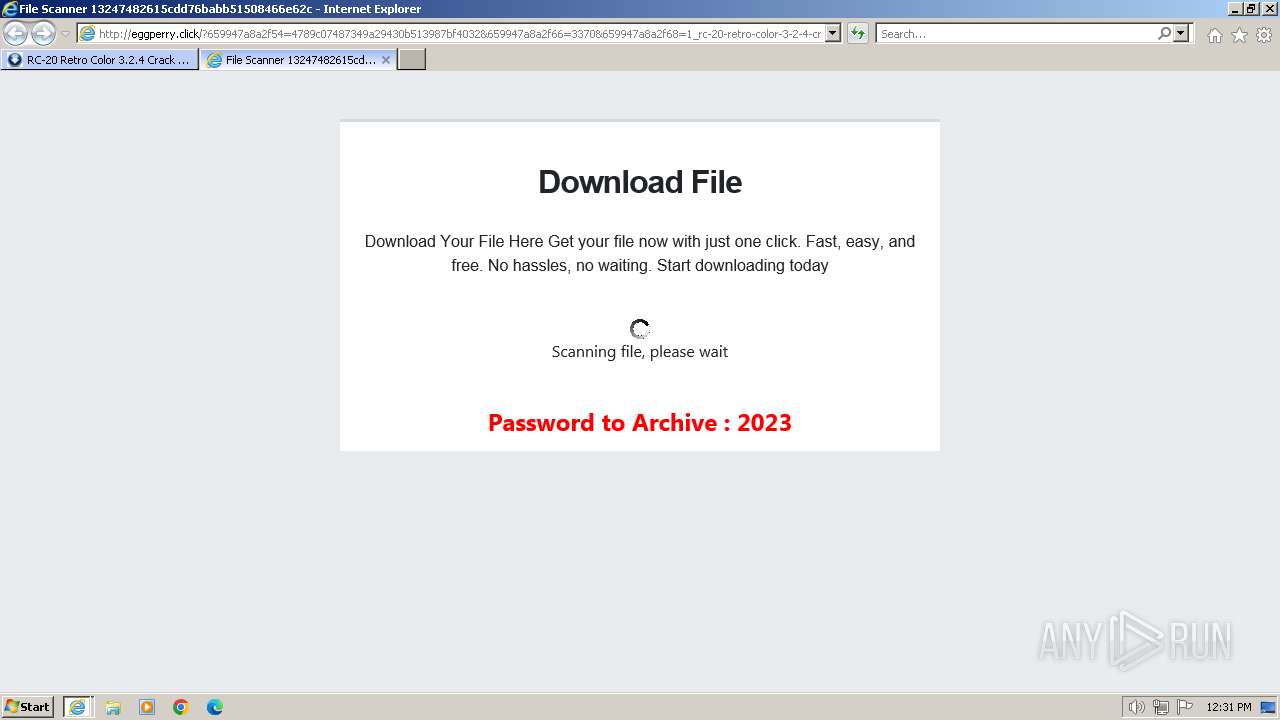
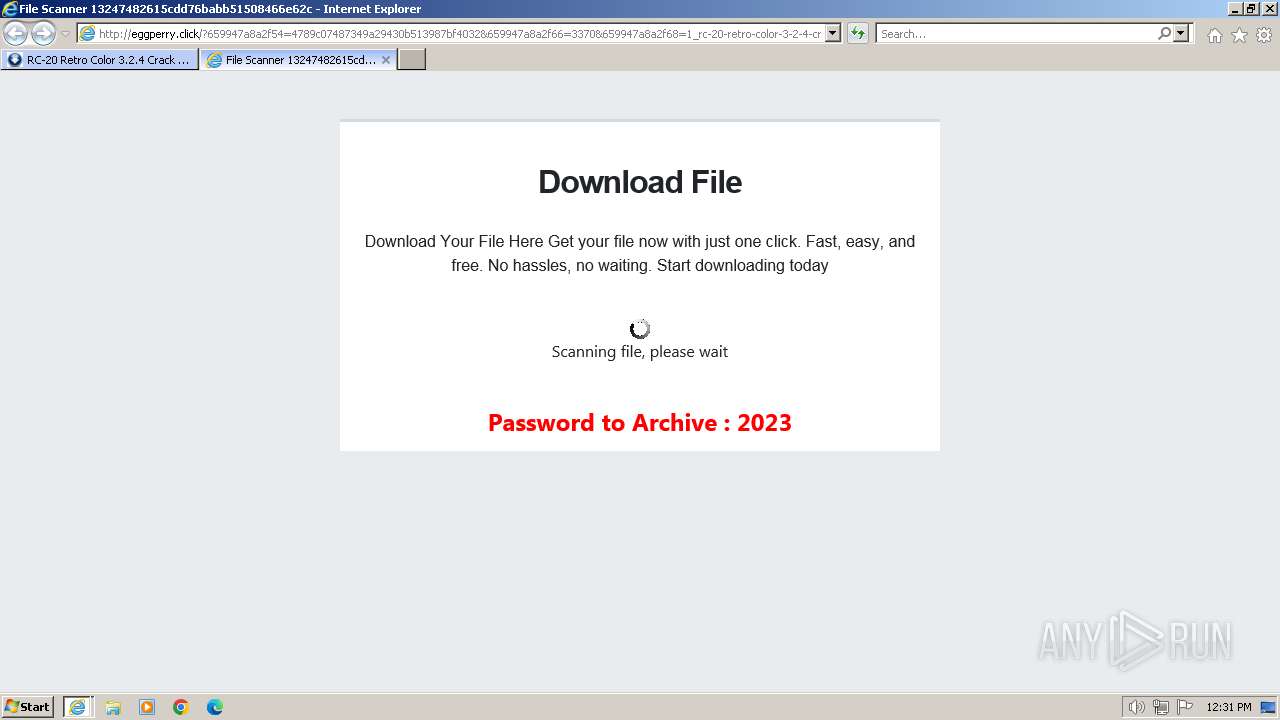
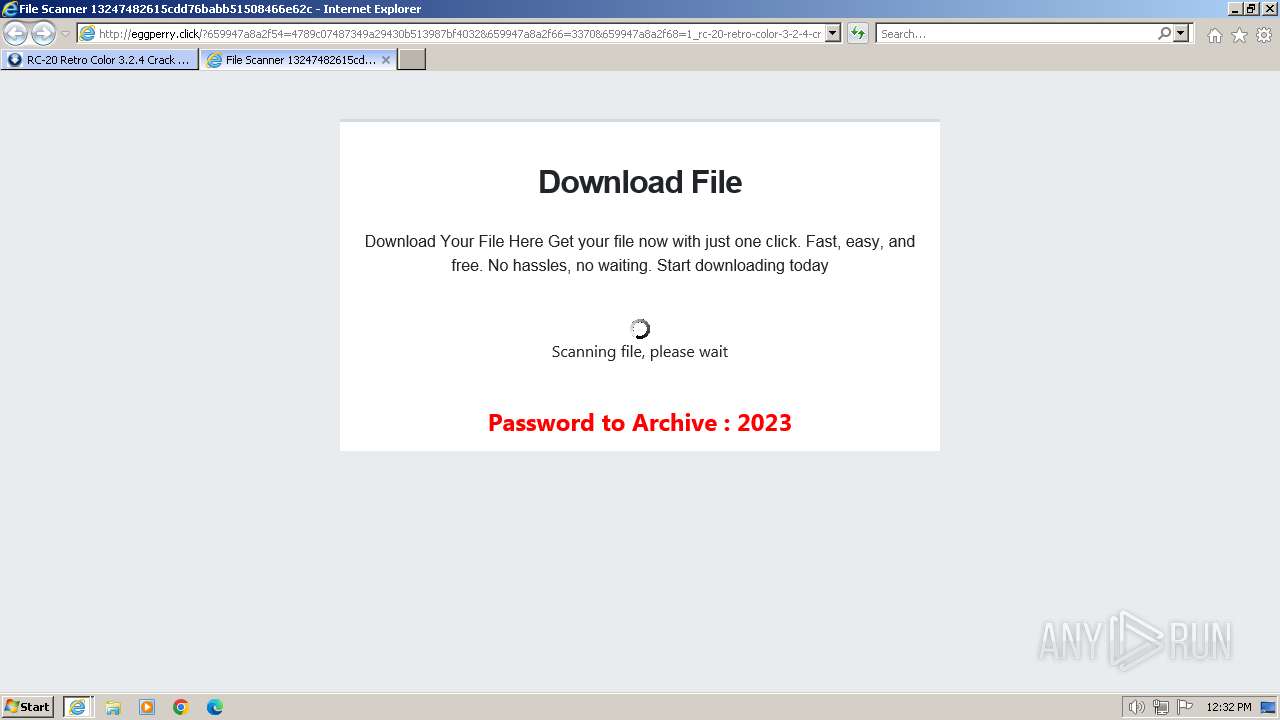
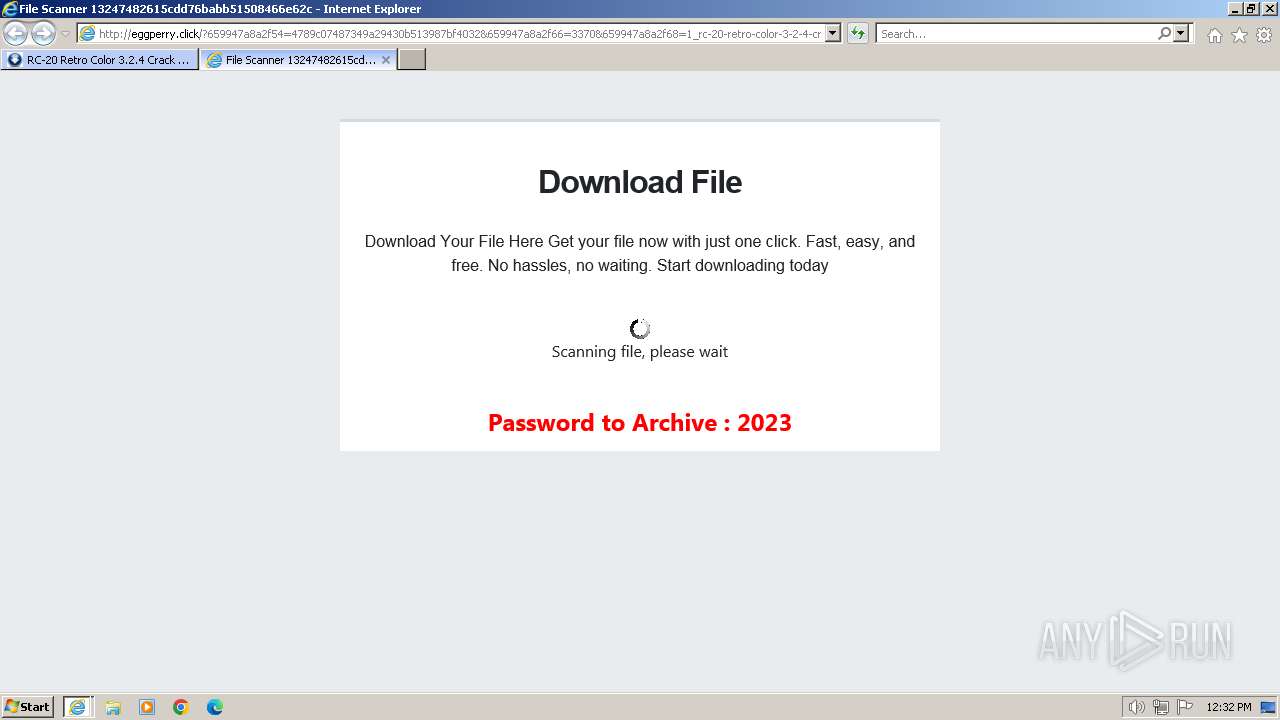
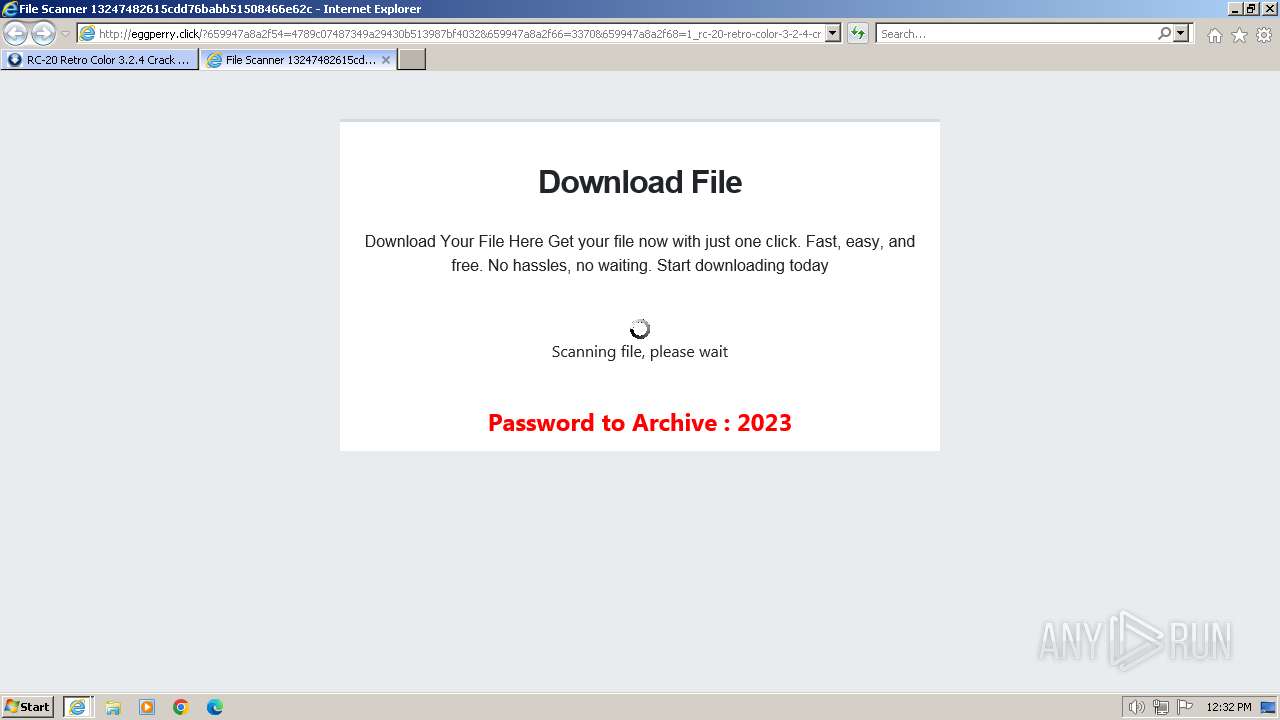
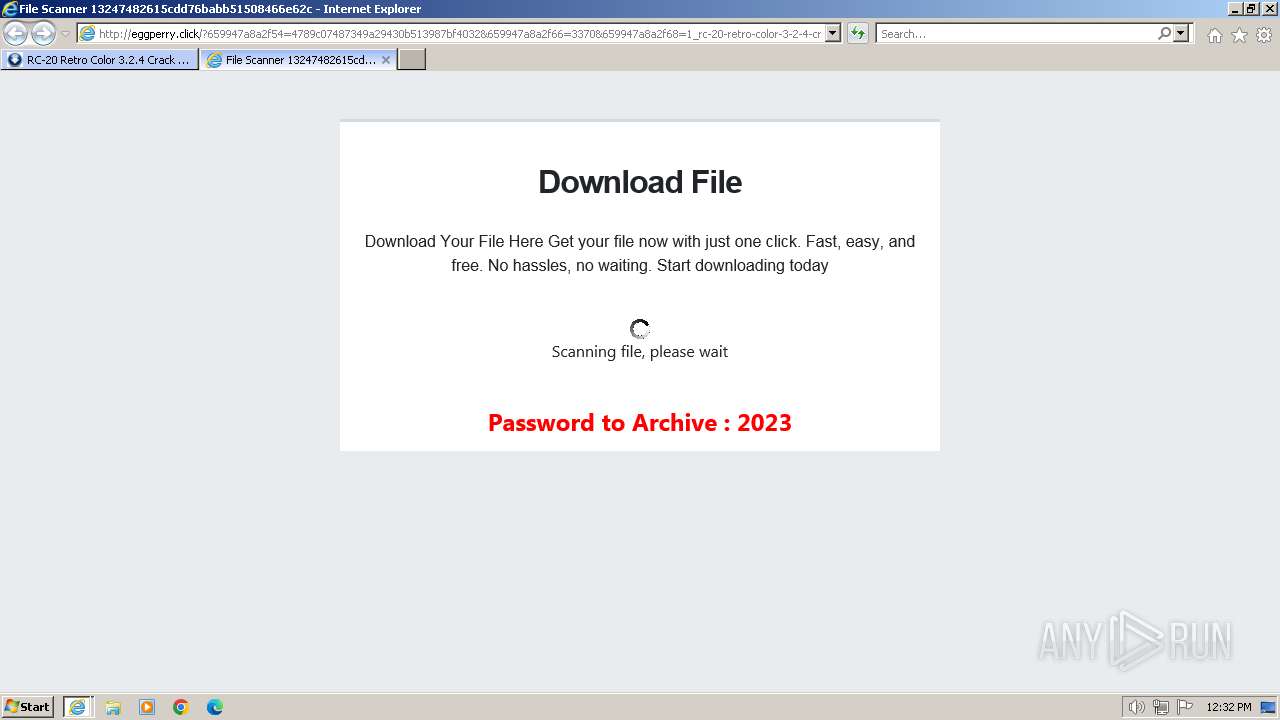
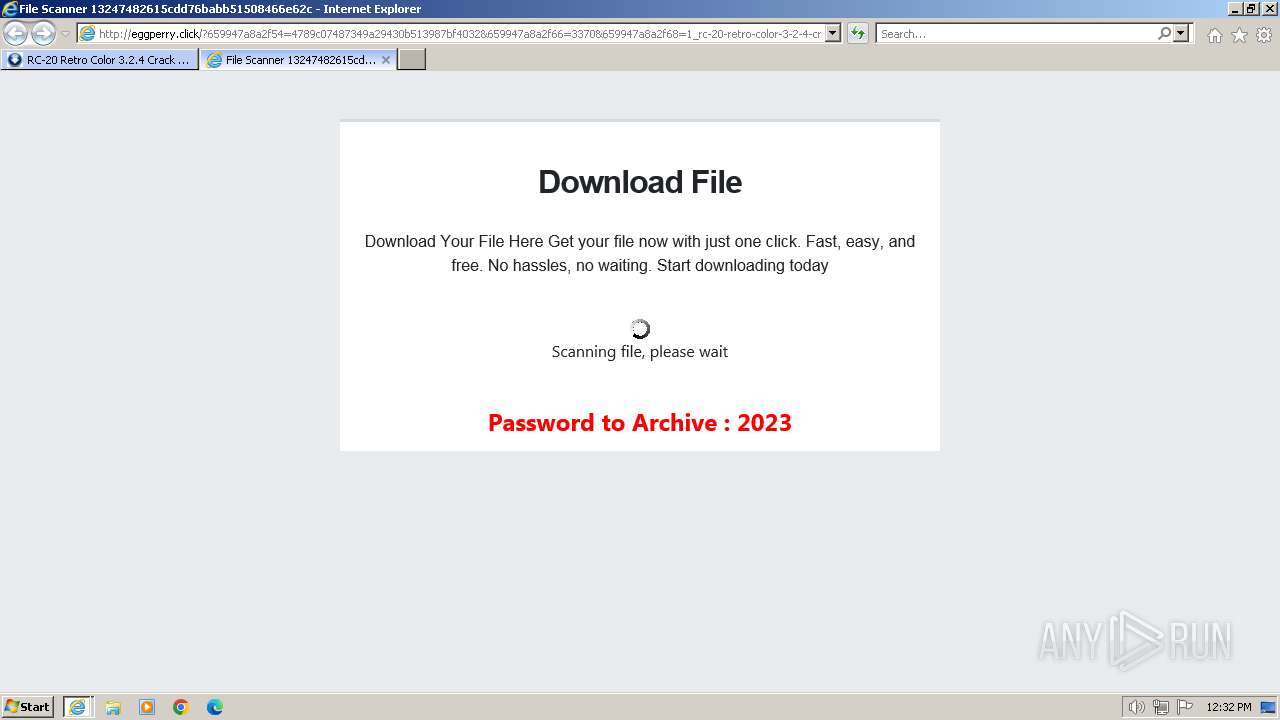
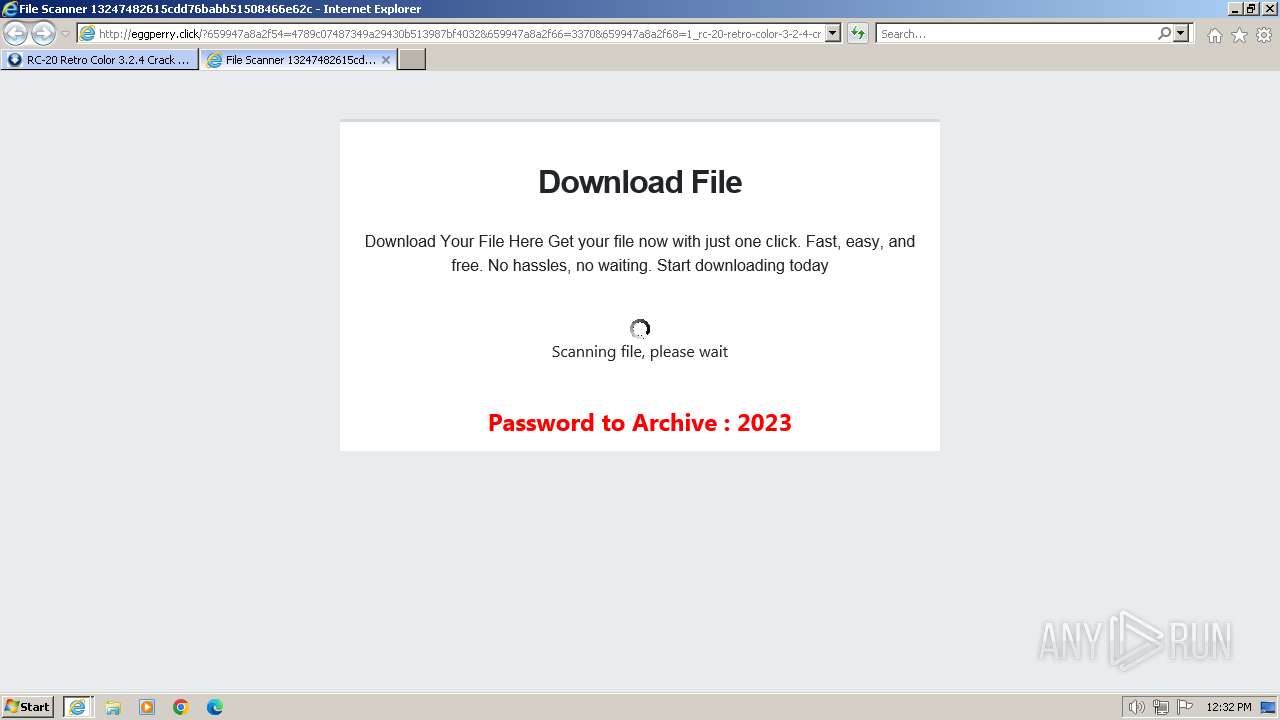
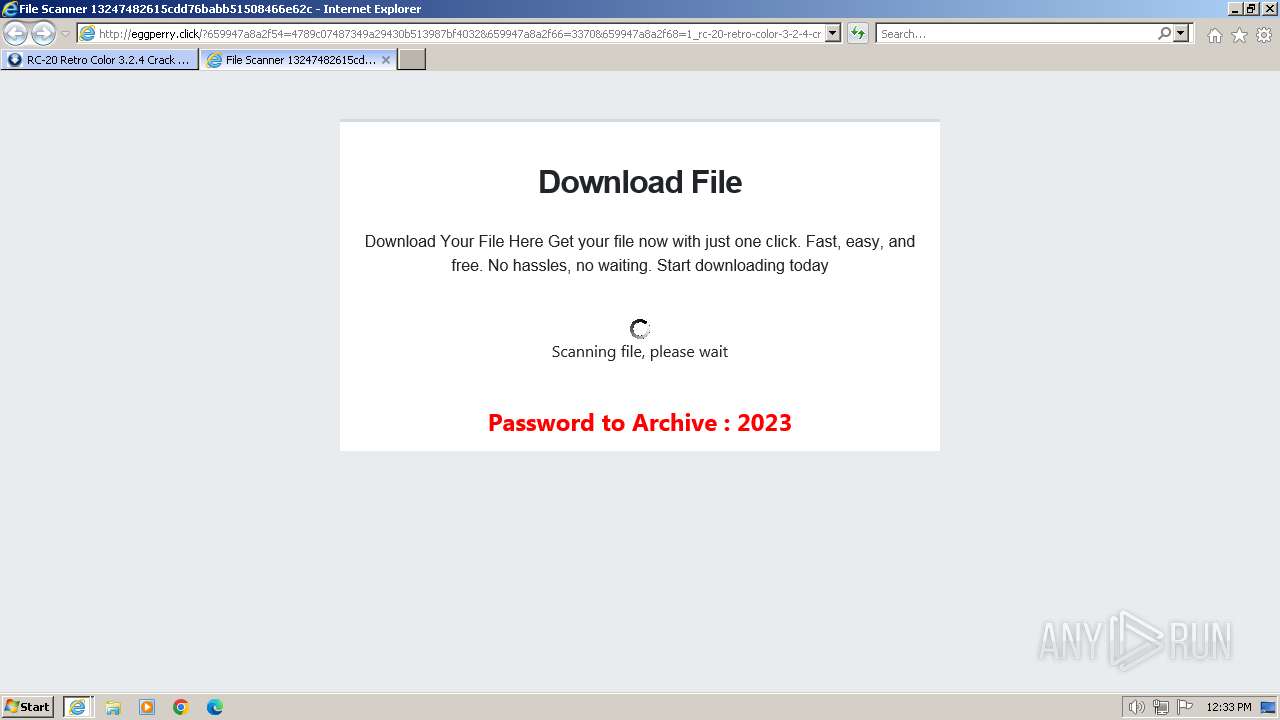
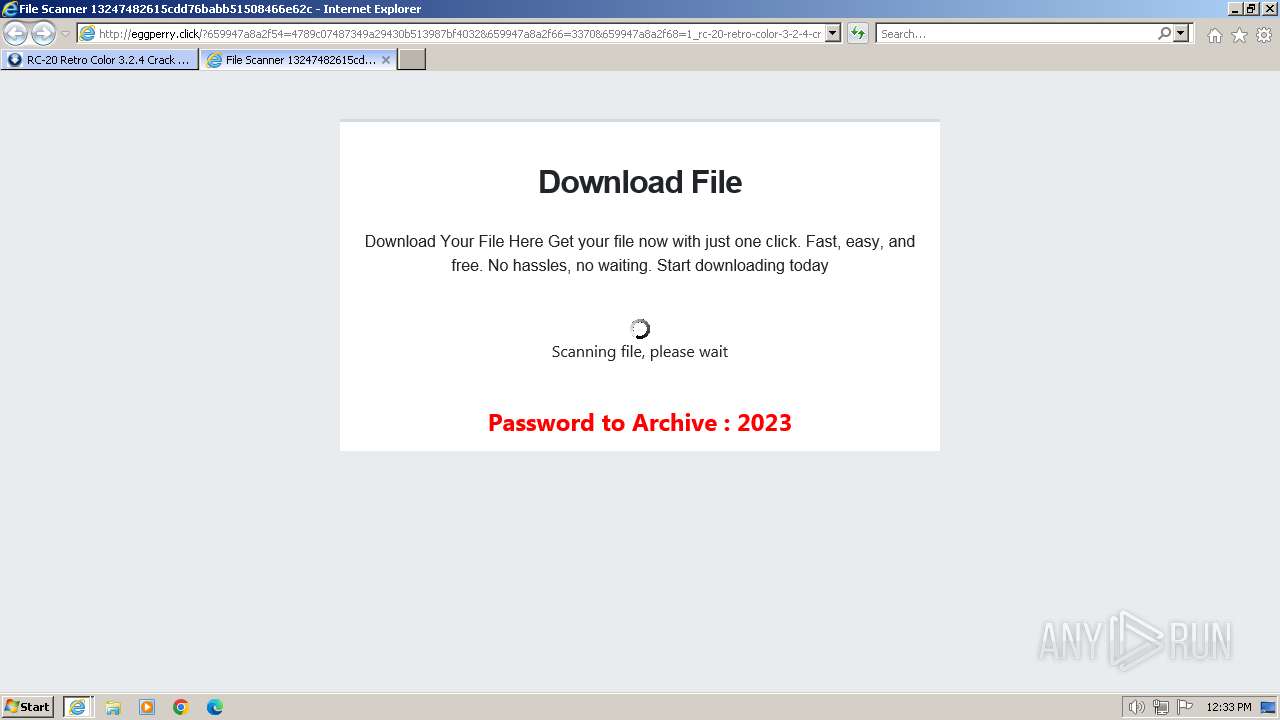
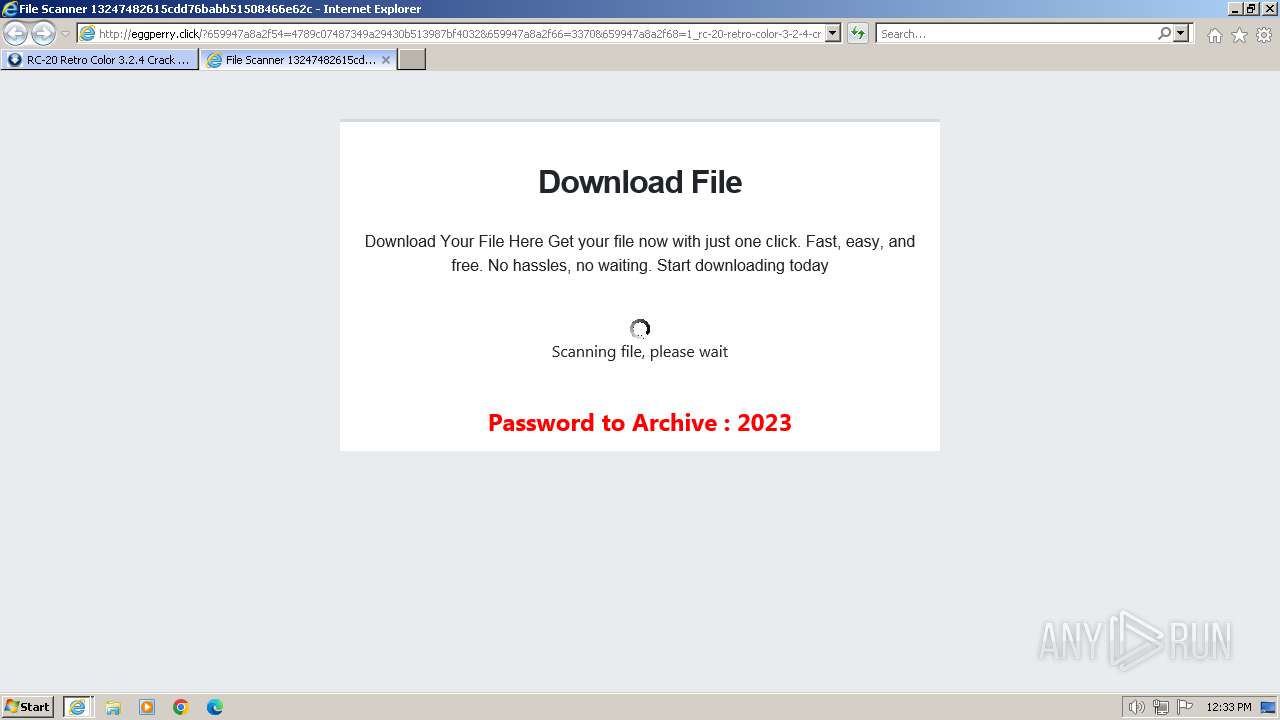
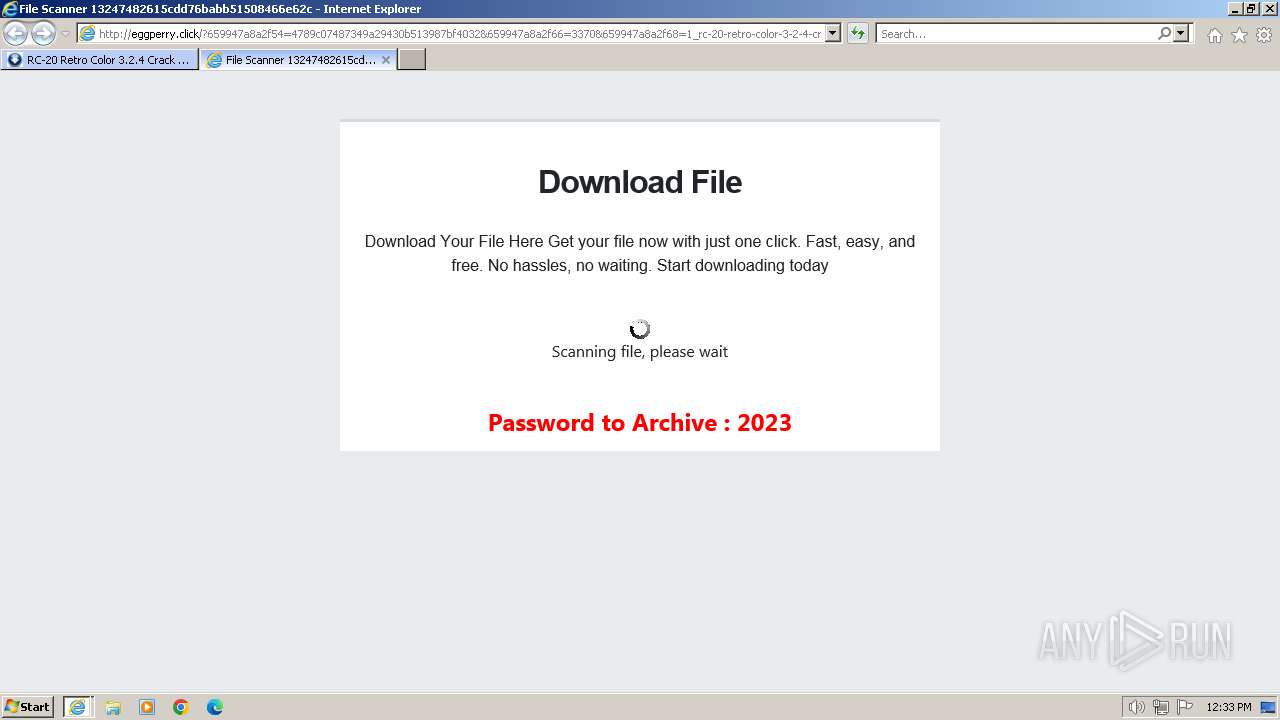
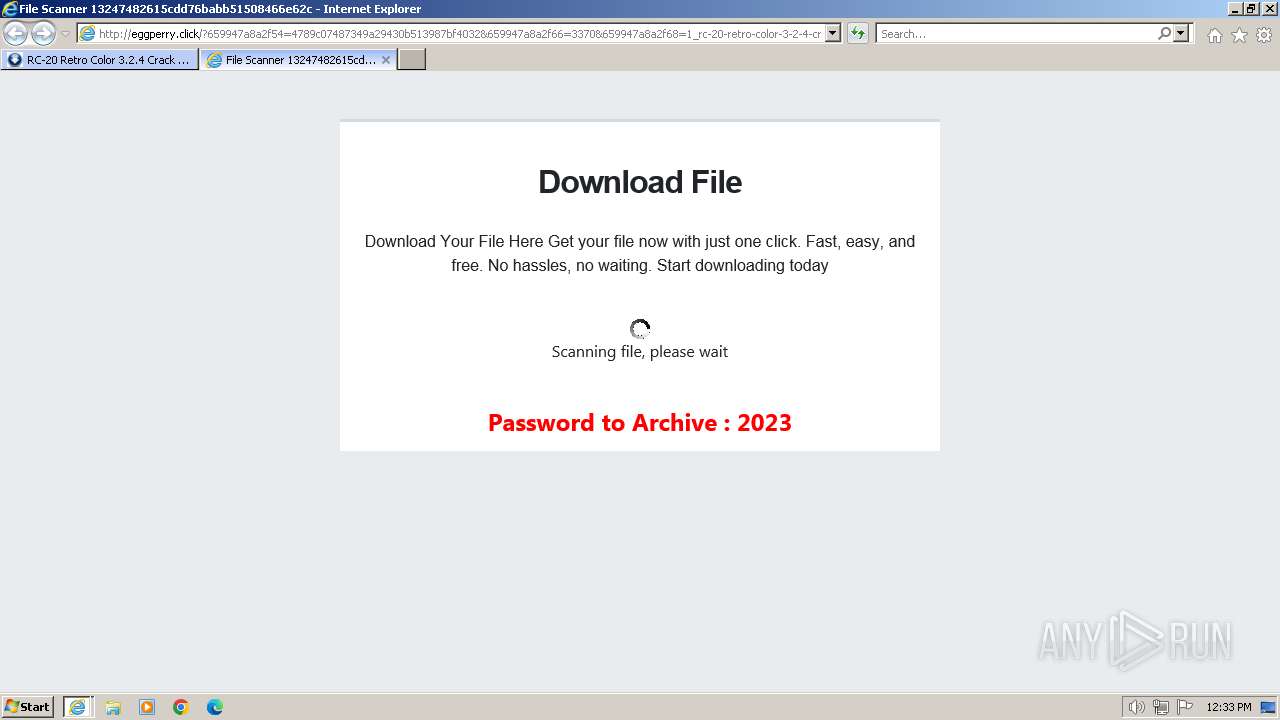
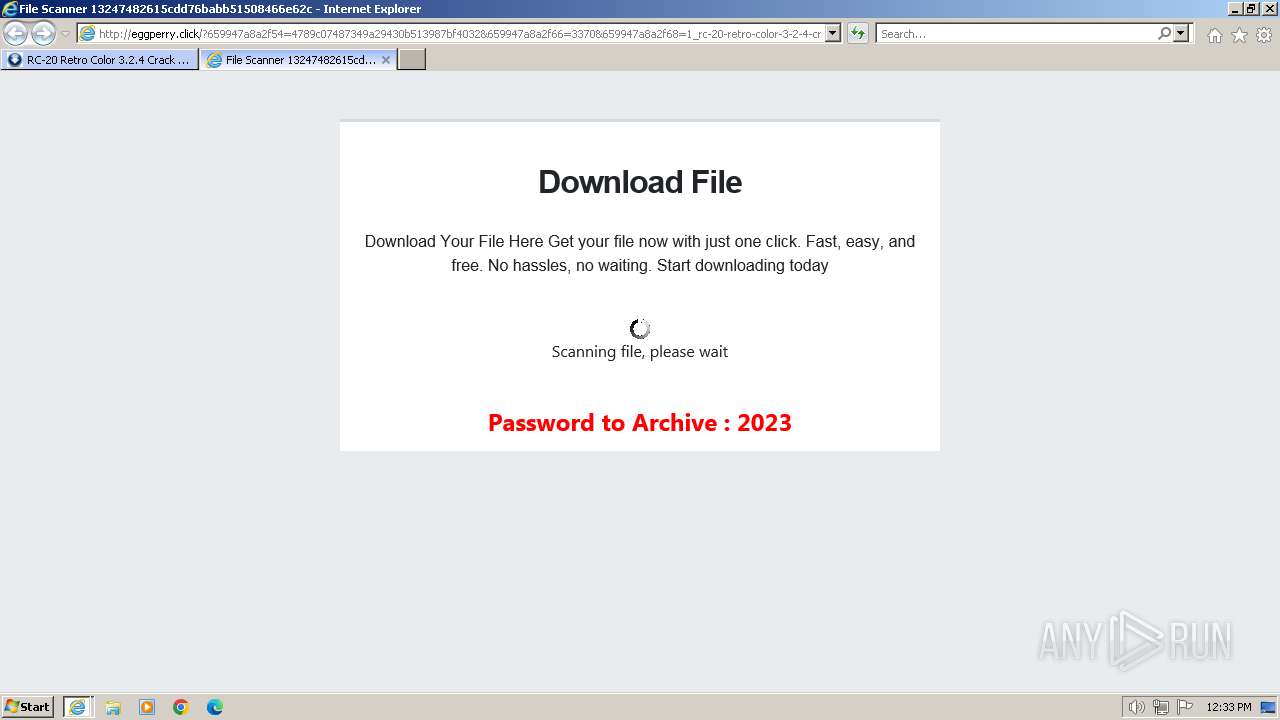
1740 | iexplore.exe | GET | 200 | 188.114.96.3:80 | http://eggperry.click/?659947a8a2f54=4789c07487349a29430b513987bf4032&659947a8a2f66=3370&659947a8a2f68=1_rc-20-retro-color-3-2-4-crack-license-key-free-download-2024&gkss=637525 | unknown | html | 1.75 Kb | unknown |
864 | iexplore.exe | GET | 200 | 23.192.153.142:80 | http://x2.c.lencr.org/ | unknown | binary | 300 b | unknown |
1740 | iexplore.exe | GET | 200 | 188.114.96.3:80 | http://eggperry.click/ldr.gif | unknown | image | 206 Kb | unknown |
2044 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?67308e0939100114 | unknown | — | — | unknown |
1740 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
864 | iexplore.exe | 188.114.96.3:80 | zaibcrack.com | CLOUDFLARENET | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
864 | iexplore.exe | 188.114.96.3:443 | zaibcrack.com | CLOUDFLARENET | NL | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
864 | iexplore.exe | 2.19.126.137:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
864 | iexplore.exe | 142.250.186.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
864 | iexplore.exe | 104.22.70.197:443 | static.addtoany.com | CLOUDFLARENET | — | unknown |
864 | iexplore.exe | 192.0.77.37:443 | c0.wp.com | AUTOMATTIC | US | unknown |
864 | iexplore.exe | 192.0.76.3:443 | stats.wp.com | AUTOMATTIC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
zaibcrack.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
static.addtoany.com |
| whitelisted |
c0.wp.com |
| whitelisted |
stats.wp.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (iplogger .com in DNS lookup) |
1740 | iexplore.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (iplogger .com in TLS SNI) |
1740 | iexplore.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (iplogger .com in TLS SNI) |
1740 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
1740 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
1740 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
1740 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
2 ETPRO signatures available at the full report