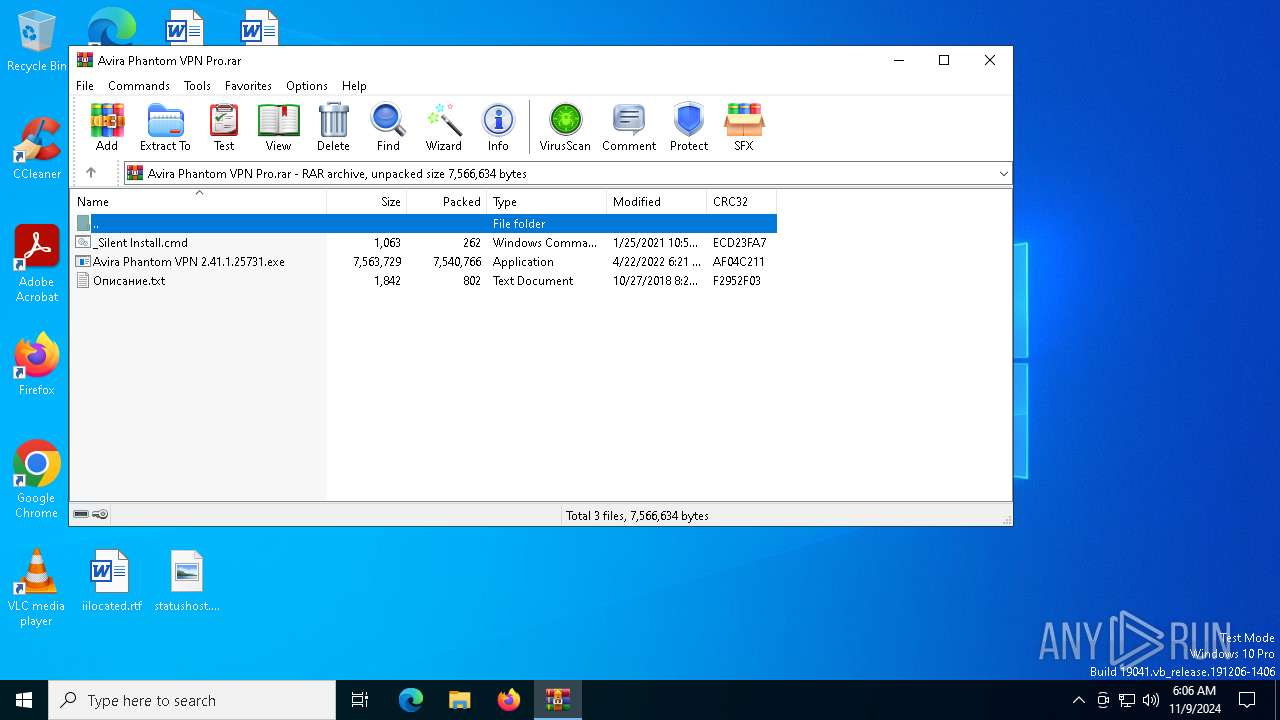
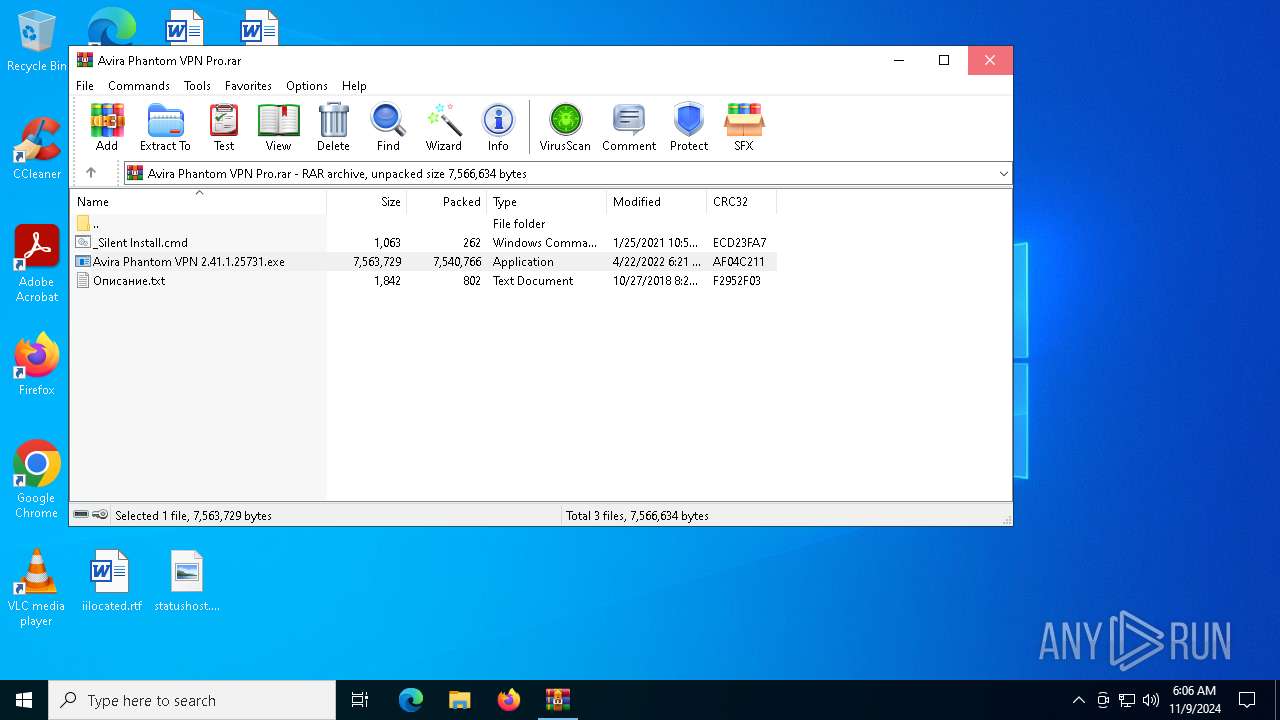
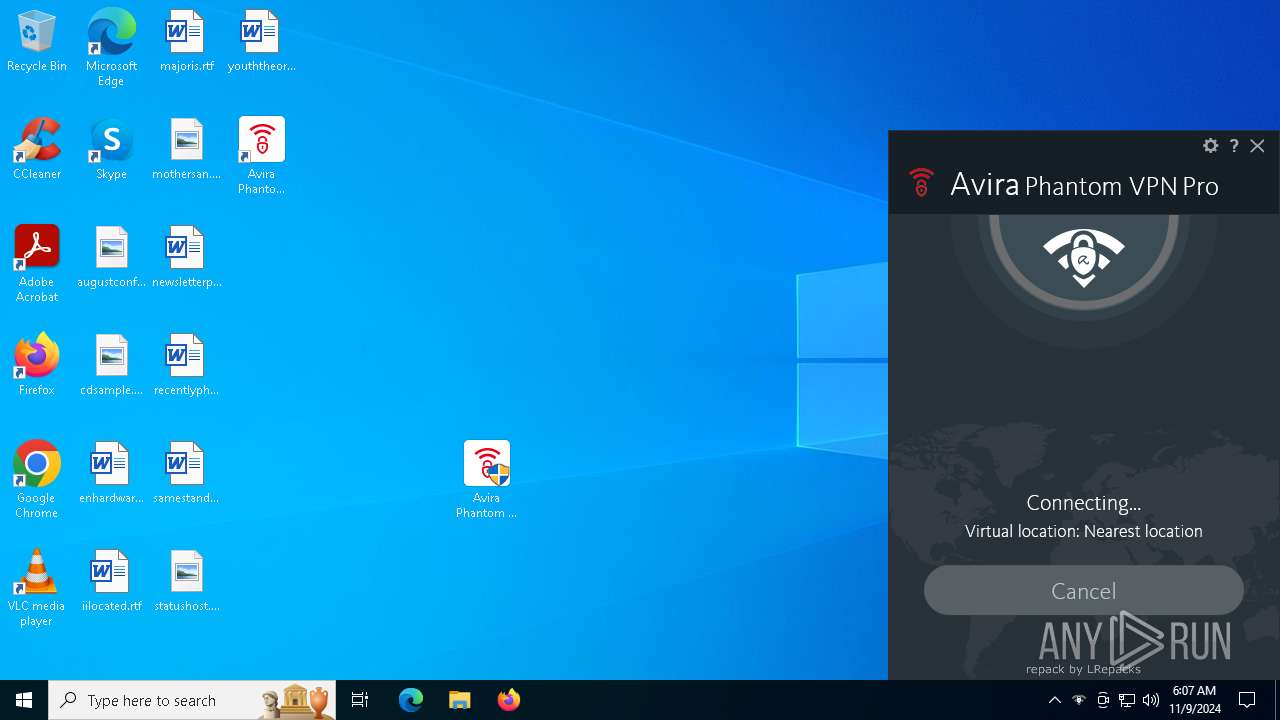
| File name: | Avira Phantom VPN Pro.rar |
| Full analysis: | https://app.any.run/tasks/904ed4eb-332f-4972-add5-c0c496ebcd59 |
| Verdict: | Malicious activity |
| Analysis date: | November 09, 2024, 06:05:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | B0C48A33DCE600717ED1EC4031DF7405 |
| SHA1: | 269814721C66EFF7924A836A3350D242A85F300E |
| SHA256: | 2C09FBBD325F85A96785DD124FDF52F501DCEC60E9BE886D451144F1E64912D1 |
| SSDEEP: | 98304:qvC8PjU+b0mn2Ct1y9mmxv/g8S8dQz7LirN4PtRWaual5lplOjOyOTwBpSaMfgLx:+NI1Lbu3iUsLw/2ClEIU |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 3972)
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
Generic archive extractor
- WinRAR.exe (PID: 6768)
Actions looks like stealing of personal data
- Avira.VpnService.exe (PID: 7124)
SUSPICIOUS
Executable content was dropped or overwritten
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
- Avira Phantom VPN 2.41.1.25731.exe (PID: 7084)
- drvinst.exe (PID: 6148)
- drvinst.exe (PID: 5168)
Process drops legitimate windows executable
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
Drops a system driver (possible attempt to evade defenses)
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
- drvinst.exe (PID: 6148)
- drvinst.exe (PID: 5168)
Reads the Windows owner or organization settings
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
- Avira.VpnService.exe (PID: 7124)
Creates or modifies Windows services
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
Reads security settings of Internet Explorer
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
- Avira.VpnService.exe (PID: 7124)
- Avira.WebAppHost.exe (PID: 2784)
- Avira.WebAppHost.exe (PID: 7044)
Executes as Windows Service
- Avira.VpnService.exe (PID: 7124)
The process verifies whether the antivirus software is installed
- Avira.VpnService.exe (PID: 7124)
- Avira.WebAppHost.exe (PID: 2784)
- Avira.NetworkBlocker.exe (PID: 6204)
- Avira.WebAppHost.exe (PID: 7044)
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
Uses NETSH.EXE to add a firewall rule or allowed programs
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
Searches for installed software
- Avira.VpnService.exe (PID: 7124)
Adds/modifies Windows certificates
- Avira.VpnService.exe (PID: 7124)
Checks Windows Trust Settings
- Avira.VpnService.exe (PID: 7124)
Reads Microsoft Outlook installation path
- Avira.WebAppHost.exe (PID: 7044)
Reads Internet Explorer settings
- Avira.WebAppHost.exe (PID: 7044)
Application launched itself
- phantomvpn.exe (PID: 1748)
Suspicious use of NETSH.EXE
- phantomvpn.exe (PID: 1748)
Process uses IPCONFIG to clear DNS cache
- phantomvpn.exe (PID: 7628)
Process uses IPCONFIG to get network configuration information
- phantomvpn.exe (PID: 7628)
INFO
Manual execution by a user
- Avira Phantom VPN 2.41.1.25731.exe (PID: 6172)
- Avira Phantom VPN 2.41.1.25731.exe (PID: 7084)
- Avira.WebAppHost.exe (PID: 2784)
- msedge.exe (PID: 6980)
- Avira.WebAppHost.exe (PID: 7044)
The process uses the downloaded file
- WinRAR.exe (PID: 6768)
- Avira.VpnService.exe (PID: 7124)
- Avira.WebAppHost.exe (PID: 2784)
- Avira.WebAppHost.exe (PID: 7044)
Create files in a temporary directory
- Avira Phantom VPN 2.41.1.25731.exe (PID: 7084)
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
Checks supported languages
- Avira Phantom VPN 2.41.1.25731.exe (PID: 7084)
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
- Avira.WebAppHost.exe (PID: 2784)
- Avira.VpnService.exe (PID: 7124)
- Avira.NetworkBlocker.exe (PID: 6204)
- identity_helper.exe (PID: 6540)
- Avira.WebAppHost.exe (PID: 7044)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6768)
Reads the computer name
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
- Avira.VpnService.exe (PID: 7124)
- Avira.WebAppHost.exe (PID: 2784)
- Avira.NetworkBlocker.exe (PID: 6204)
- identity_helper.exe (PID: 6540)
- Avira.WebAppHost.exe (PID: 7044)
Creates files in the program directory
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
- Avira.VpnService.exe (PID: 7124)
Creates a software uninstall entry
- Avira Phantom VPN 2.41.1.25731.tmp (PID: 7108)
Reads the machine GUID from the registry
- Avira.VpnService.exe (PID: 7124)
- Avira.WebAppHost.exe (PID: 2784)
- Avira.WebAppHost.exe (PID: 7044)
Reads Environment values
- Avira.VpnService.exe (PID: 7124)
- identity_helper.exe (PID: 6540)
- Avira.WebAppHost.exe (PID: 7044)
Reads the software policy settings
- Avira.VpnService.exe (PID: 7124)
- Avira.WebAppHost.exe (PID: 7044)
Disables trace logs
- Avira.VpnService.exe (PID: 7124)
- Avira.WebAppHost.exe (PID: 7044)
Reads CPU info
- Avira.VpnService.exe (PID: 7124)
Application launched itself
- msedge.exe (PID: 2980)
- msedge.exe (PID: 4836)
- msedge.exe (PID: 6980)
Checks proxy server information
- Avira.WebAppHost.exe (PID: 7044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 262 |
| UncompressedSize: | 1063 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | _Silent Install.cmd |
Total processes
221
Monitored processes
93
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 696 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tapinstall.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 700 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2488 --field-trial-handle=2332,i,8830556443333580239,9762656200538059449,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 916 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5524 --field-trial-handle=2436,i,5594742974506802319,2539149667949605456,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1008 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3736 --field-trial-handle=2436,i,5594742974506802319,2539149667949605456,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tapinstall.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1248 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5768 --field-trial-handle=2436,i,5594742974506802319,2539149667949605456,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1332 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5112 --field-trial-handle=2332,i,8830556443333580239,9762656200538059449,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1528 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5080 --field-trial-handle=2436,i,5594742974506802319,2539149667949605456,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1748 | "C:\Program Files (x86)\Avira\VPN\OpenVpn\phantomvpn.exe" --auth-nocache --reneg-sec 0 --mute-replay-warnings --management-hold --block-outside-dns --management-query-passwords --service AviraVPNOpenVpnQuitEvent --redirect-gateway def1 --register-dns --resolv-retry 15 --connect-retry-max 3 --tls-exit --remap-usr1 SIGTERM --remote de.phantom.avira-vpn.com 443 tcp --hand-window 60 --config VpnClient.ovpn --management 127.0.0.1 23000 --tun-ipv6 --dev-node "Local Area Connection" | C:\Program Files (x86)\Avira\VPN\OpenVpn\phantomvpn.exe | — | Avira.VpnService.exe | |||||||||||
User: SYSTEM Company: The OpenVPN Project Integrity Level: SYSTEM Description: OpenVPN Daemon Version: 2.4.9.0 | |||||||||||||||
Total events
16 329
Read events
16 233
Write events
94
Delete events
2
Modification events
| (PID) Process: | (6768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Avira Phantom VPN Pro.rar | |||
| (PID) Process: | (6768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
150
Suspicious files
342
Text files
782
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7108 | Avira Phantom VPN 2.41.1.25731.tmp | C:\Users\admin\AppData\Local\Temp\is-6Q5O1.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:0EE914C6F0BB93996C75941E1AD629C6 | SHA256:4DC09BAC0613590F1FAC8771D18AF5BE25A1E1CB8FDBF4031AA364F3057E74A2 | |||
| 7108 | Avira Phantom VPN 2.41.1.25731.tmp | C:\Program Files (x86)\Avira\VPN\unins000.exe | executable | |
MD5:918DE89F7BE9C39F437AD6C0951460CD | SHA256:001CA545FF3419F0520E54107A3862AA54E23B540921DA01E2BE10F47F785095 | |||
| 7108 | Avira Phantom VPN 2.41.1.25731.tmp | C:\Users\admin\AppData\Local\Temp\is-6Q5O1.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 7108 | Avira Phantom VPN 2.41.1.25731.tmp | C:\Program Files (x86)\Avira\VPN\is-ITDKP.tmp | executable | |
MD5:918DE89F7BE9C39F437AD6C0951460CD | SHA256:001CA545FF3419F0520E54107A3862AA54E23B540921DA01E2BE10F47F785095 | |||
| 7084 | Avira Phantom VPN 2.41.1.25731.exe | C:\Users\admin\AppData\Local\Temp\is-TEH5K.tmp\Avira Phantom VPN 2.41.1.25731.tmp | executable | |
MD5:02C5691AF81933CE36735946E3ED1EA4 | SHA256:E1F5E87796C015E567153DB6B994A35A34B0819B1093D1EA12064EE35102C42D | |||
| 6768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6768.18146\Avira Phantom VPN 2.41.1.25731.exe | executable | |
MD5:BF245B7DB7637E6B2991105F62CC76DE | SHA256:C414E764C53A81C6BEB2C393635044661DA238380492C182162B37F3E82A8C89 | |||
| 7108 | Avira Phantom VPN 2.41.1.25731.tmp | C:\Users\admin\AppData\Local\Temp\is-6Q5O1.tmp\MetroBlue.vsf | binary | |
MD5:295D085196B3DA13BFCD53373F82F8EE | SHA256:CBDC95EB9E7269E0C3E3BDDFD37B0918962795D80BDBA932E46EA16FF5E6CDBF | |||
| 7108 | Avira Phantom VPN 2.41.1.25731.tmp | C:\Users\admin\AppData\Local\Temp\is-6Q5O1.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
| 7108 | Avira Phantom VPN 2.41.1.25731.tmp | C:\Users\admin\AppData\Local\Temp\is-6Q5O1.tmp\VclStylesInno.dll | executable | |
MD5:B0CA93CEB050A2FEFF0B19E65072BBB5 | SHA256:0E93313F42084D804B9AC4BE53D844E549CFCAF19E6F276A3B0F82F01B9B2246 | |||
| 7108 | Avira Phantom VPN 2.41.1.25731.tmp | C:\Program Files (x86)\Avira\VPN\is-HI97E.tmp | executable | |
MD5:15251F271169251E9B962C57DD763D31 | SHA256:F3F28506D8419457640BB4E623DB9E78906051FA179180634D3DABDDB6D4F9DB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
104
DNS requests
142
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4004 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.193.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.16.193.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3728 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6956 | SIHClient.exe | GET | 200 | 2.16.193.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6956 | SIHClient.exe | GET | 200 | 2.16.193.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.21.20.154:80 | http://www.msftncsi.com/ncsi.txt | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.204.84:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
7040 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.216.77.25:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.216.77.25:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 2.16.193.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.193.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report