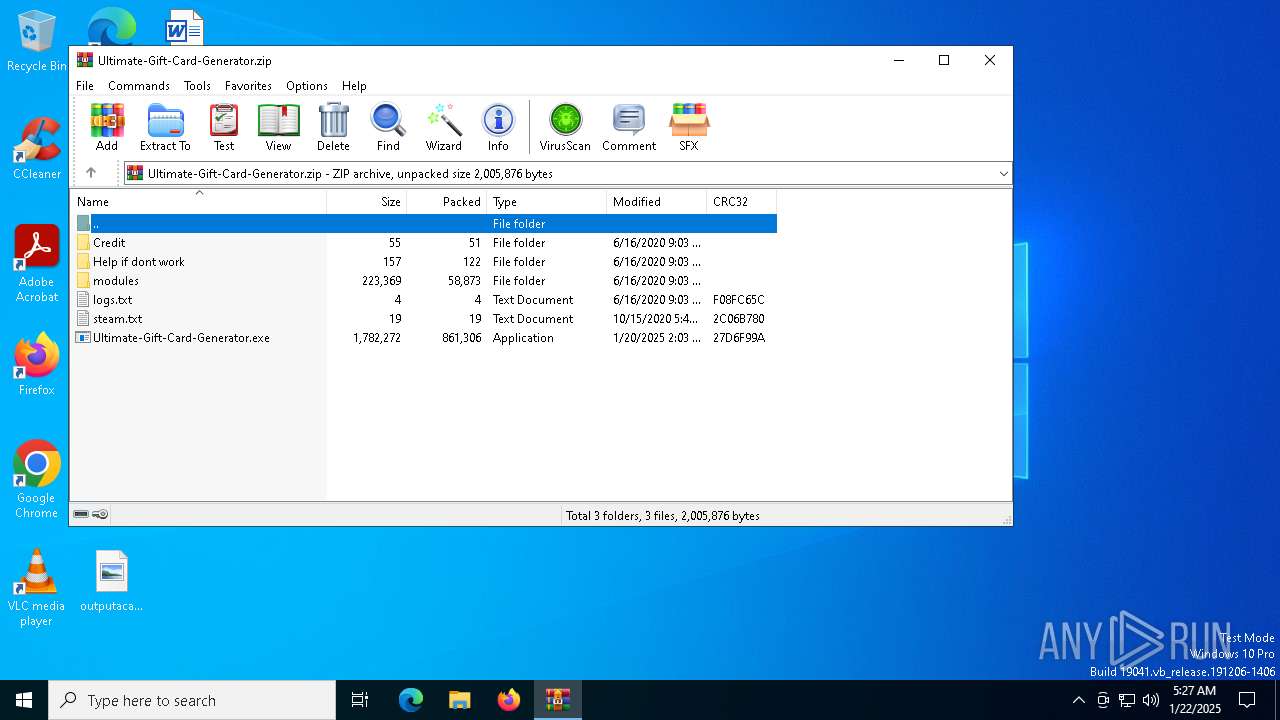
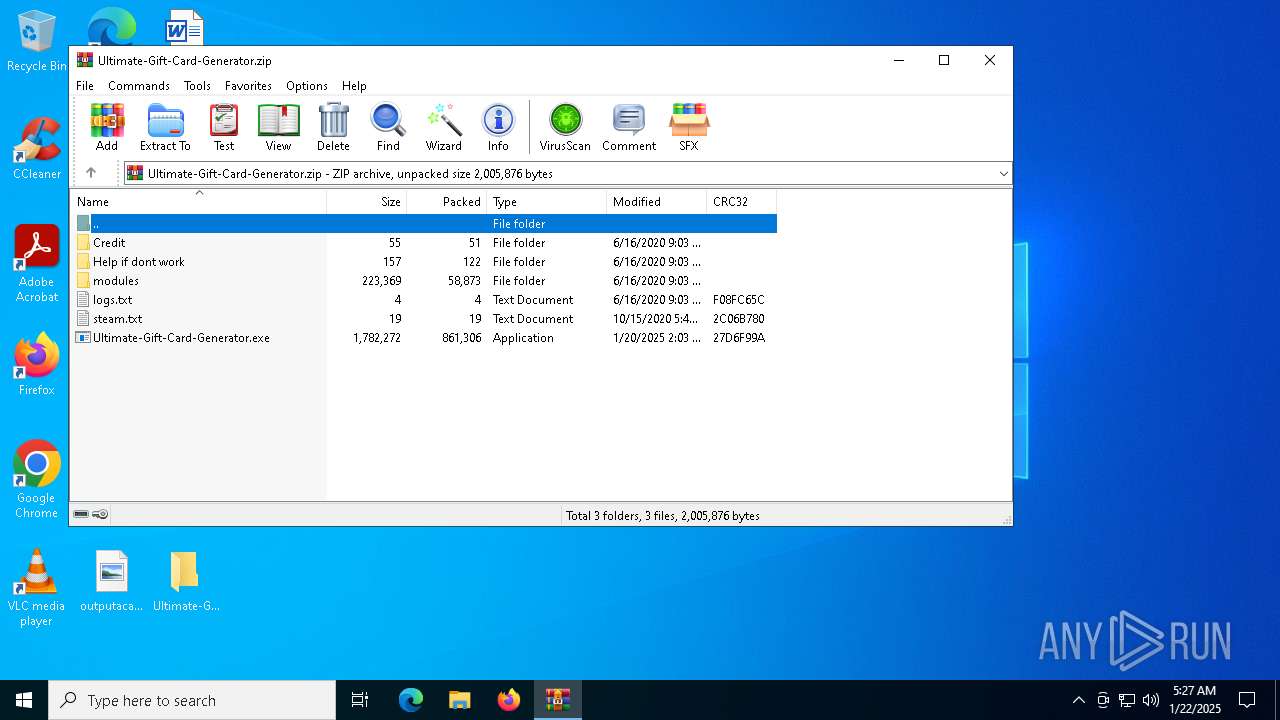
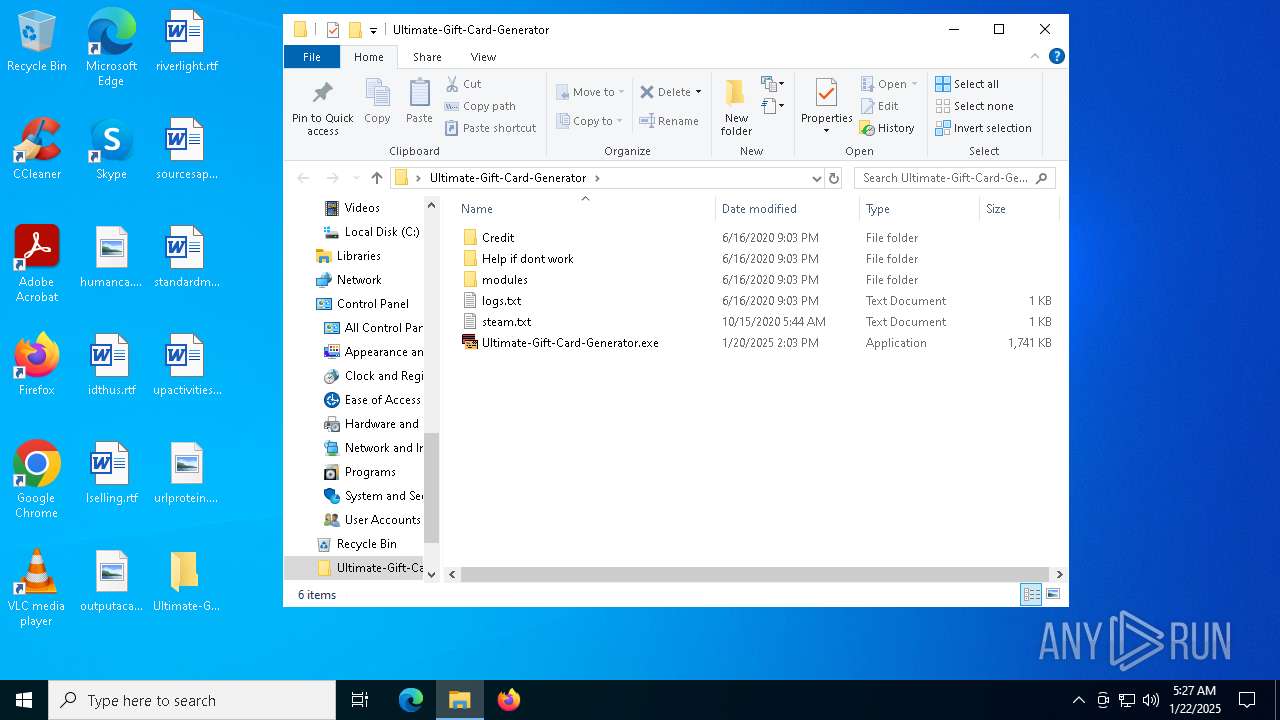
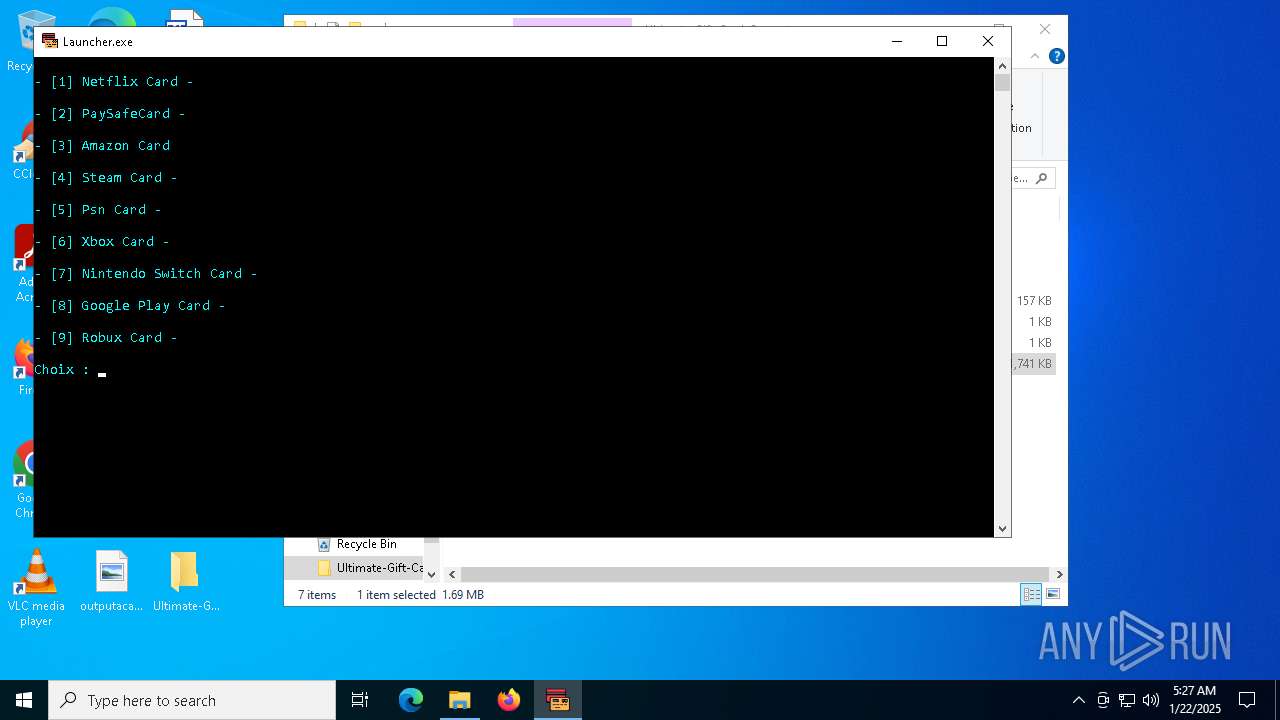
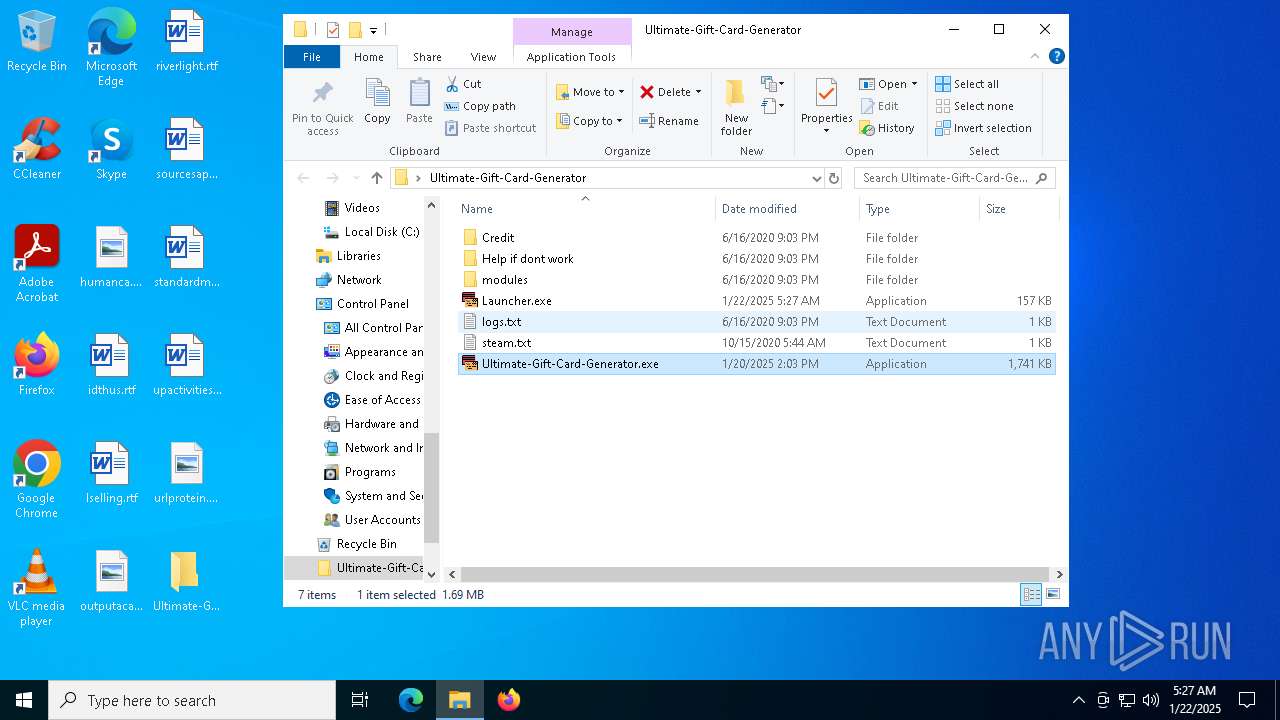
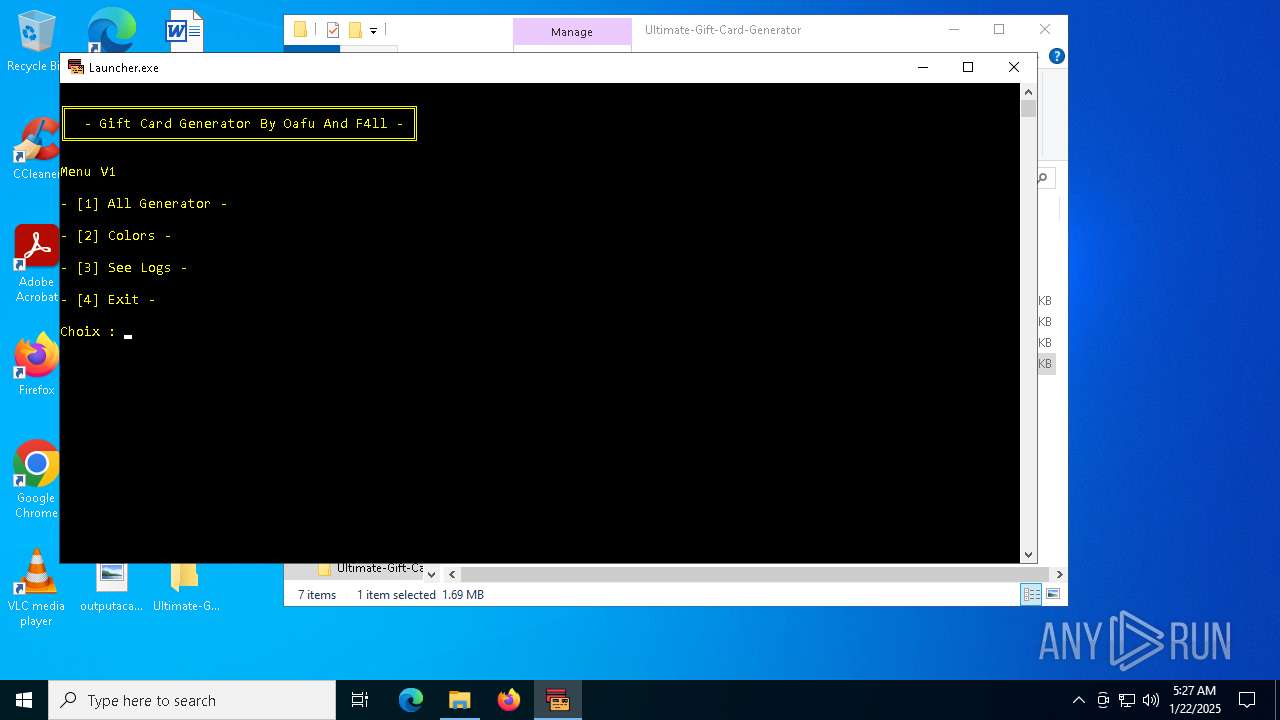
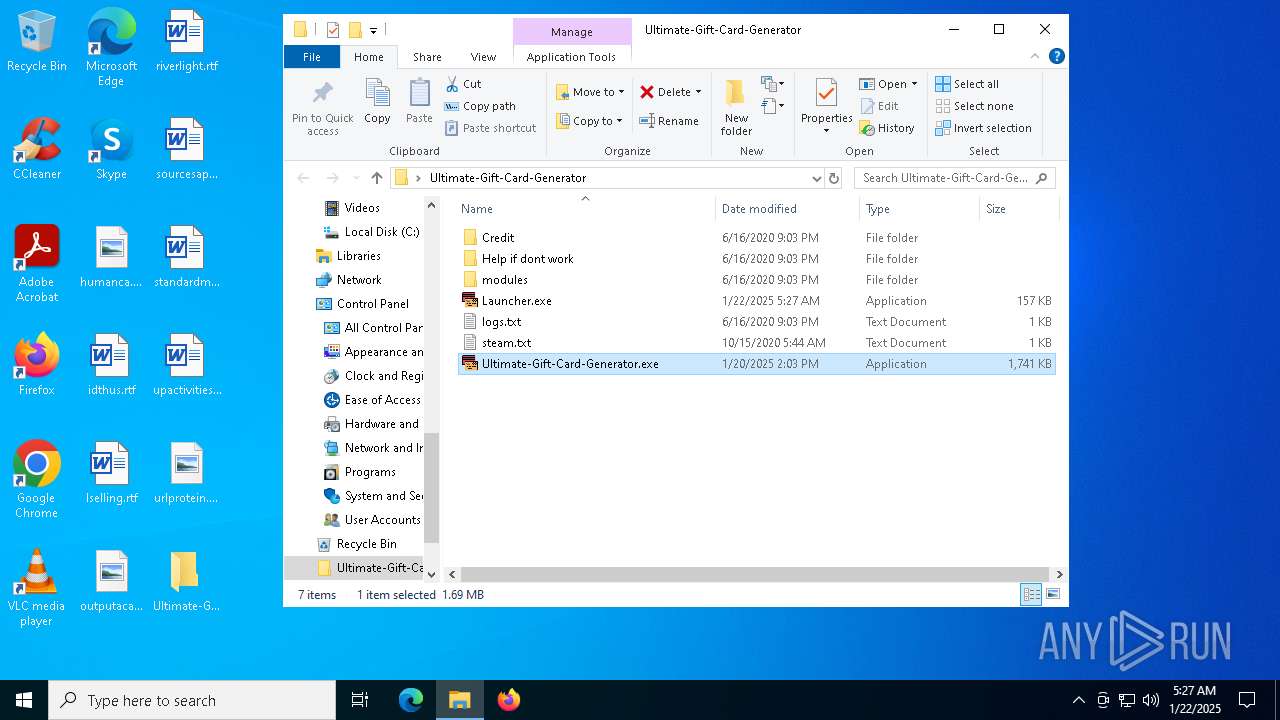
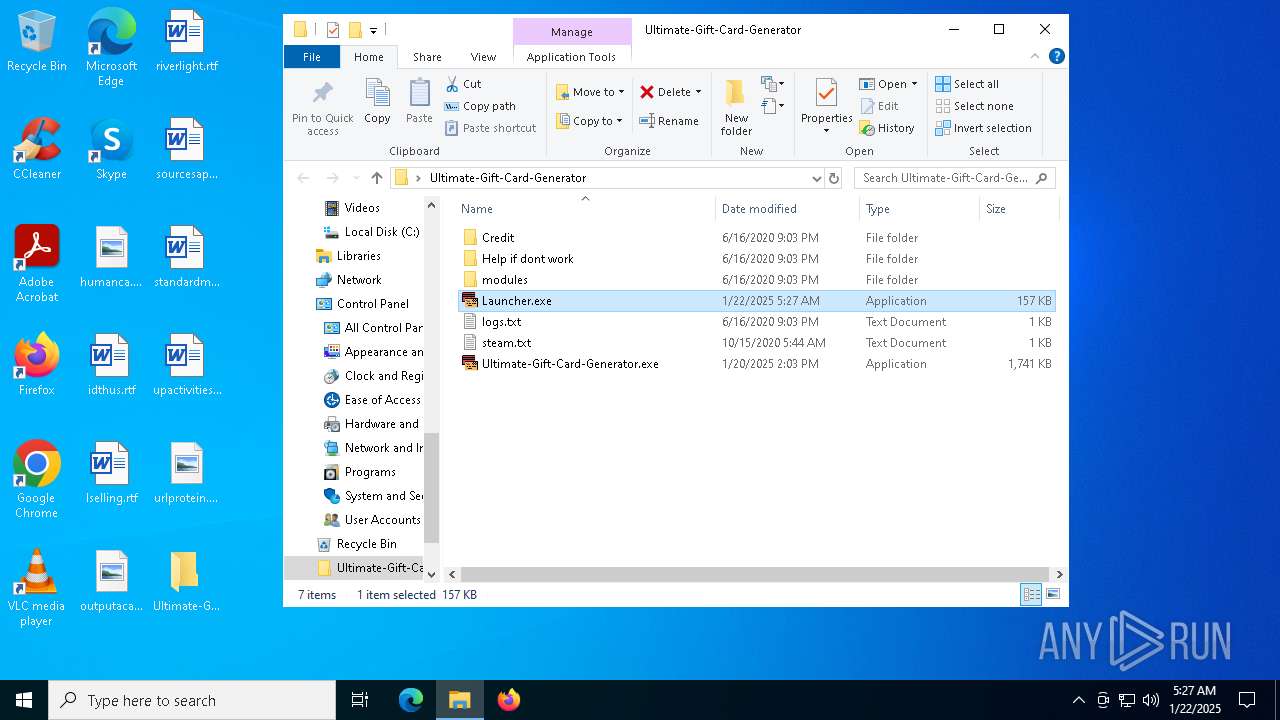
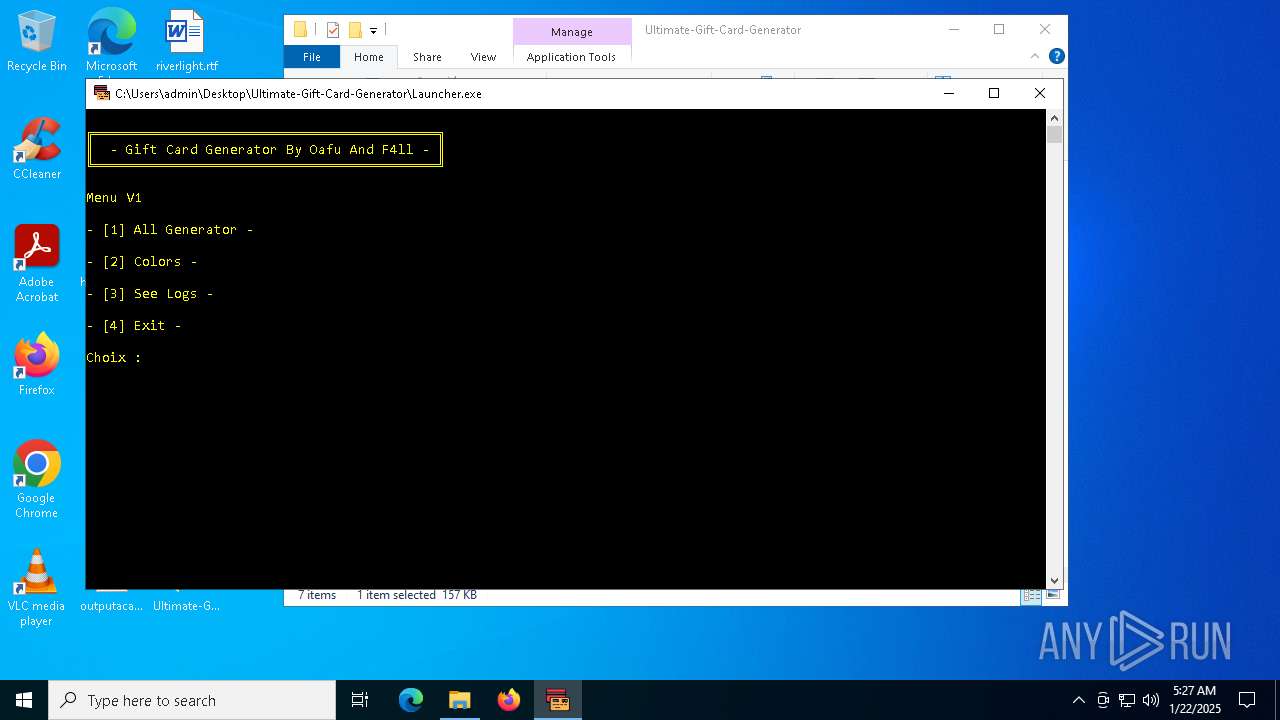
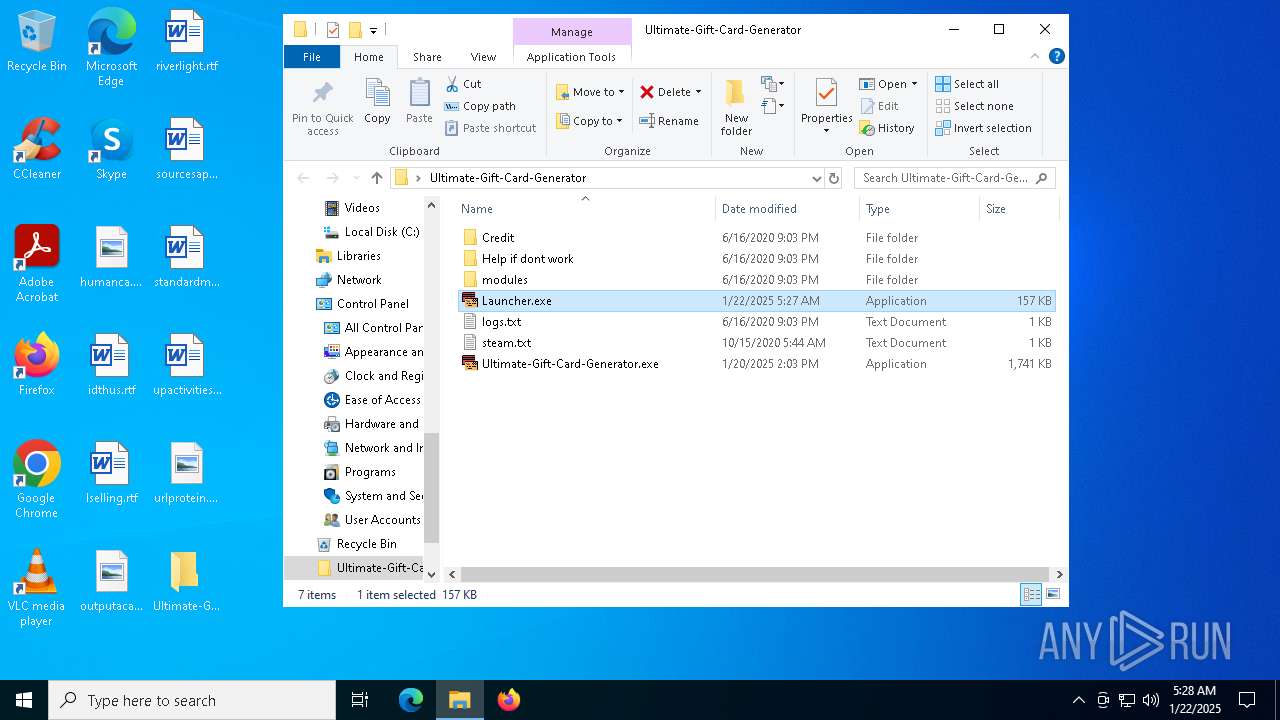
| File name: | Ultimate-Gift-Card-Generator.zip |
| Full analysis: | https://app.any.run/tasks/c19f92d2-773f-4f99-bfb5-77120bf3a95a |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | January 22, 2025, 05:27:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | F71BF5125AF5B17C87BE1EB9D9A0F7ED |
| SHA1: | 426BB95F80735307E0088C9565B05E445A050D65 |
| SHA256: | 2BF2BF1D02A6A19B5DB98C807ADCAC6B8F70B70F1984EC59EAC24A284CD5CAE4 |
| SSDEEP: | 49152:pk5tEHC2oXI5y8559w6Kv4cK0cEzwVoDjRhLC8yQ3FBNjYAzT0KVQRTymuMQyC08:7HHWIzM6KvZFcOwVoD9XVPlT1gym3gcC |
MALICIOUS
Changes the autorun value in the registry
- syxstccx.exe (PID: 6244)
- sysxapcpteam.exe (PID: 6252)
- explorer.exe (PID: 4488)
Runs injected code in another process
- sysxapcpteam.exe (PID: 6252)
Application was injected by another process
- explorer.exe (PID: 4488)
Actions looks like stealing of personal data
- sysxchceck.exe (PID: 6264)
- sysxchceck.exe (PID: 2800)
- sysxchceck.exe (PID: 6232)
SUSPICIOUS
Executable content was dropped or overwritten
- Ultimate-Gift-Card-Generator.exe (PID: 6164)
- sysxapcpteam.exe (PID: 6252)
- syxstccx.exe (PID: 6244)
The process creates files with name similar to system file names
- syxstccx.exe (PID: 6244)
Starts CMD.EXE for commands execution
- Launcher.exe (PID: 2940)
- Launcher.exe (PID: 6448)
- Launcher.exe (PID: 7116)
- Launcher.exe (PID: 4536)
Connects to the server without a host name
- sysxchceck.exe (PID: 6264)
- explorer.exe (PID: 4488)
- sysxchceck.exe (PID: 2800)
- sysxchceck.exe (PID: 6232)
Executing commands from a ".bat" file
- Launcher.exe (PID: 2940)
- Launcher.exe (PID: 6448)
- Launcher.exe (PID: 7116)
- Launcher.exe (PID: 4536)
Reads security settings of Internet Explorer
- sysxchceck.exe (PID: 6264)
- sysxchceck.exe (PID: 2800)
- sysxchceck.exe (PID: 6232)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6496)
Creates files or folders in the user directory
- explorer.exe (PID: 4488)
- Ultimate-Gift-Card-Generator.exe (PID: 6164)
- sysxapcpteam.exe (PID: 6252)
- sysxchceck.exe (PID: 6264)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6496)
The process uses the downloaded file
- WinRAR.exe (PID: 6496)
- explorer.exe (PID: 4488)
Manual execution by a user
- Ultimate-Gift-Card-Generator.exe (PID: 6164)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4488)
- notepad.exe (PID: 6668)
Checks supported languages
- Ultimate-Gift-Card-Generator.exe (PID: 6164)
- sysxapcpteam.exe (PID: 6252)
- sysxchceck.exe (PID: 6264)
- syxstccx.exe (PID: 6244)
- syxstccx.exe (PID: 6788)
- Ultimate-Gift-Card-Generator.exe (PID: 4044)
- sysxapcpteam.exe (PID: 3172)
- Launcher.exe (PID: 2940)
- sysxchceck.exe (PID: 2800)
- Launcher.exe (PID: 6448)
- syxstccx.exe (PID: 6644)
- sysxapcpteam.exe (PID: 6260)
- Launcher.exe (PID: 7116)
- Launcher.exe (PID: 4536)
- Ultimate-Gift-Card-Generator.exe (PID: 2084)
- sysxchceck.exe (PID: 6232)
Reads the machine GUID from the registry
- sysxapcpteam.exe (PID: 6252)
- sysxapcpteam.exe (PID: 3172)
- sysxapcpteam.exe (PID: 6260)
Creates files in the program directory
- sysxchceck.exe (PID: 6264)
- syxstccx.exe (PID: 6244)
- sysxchceck.exe (PID: 2800)
- sysxchceck.exe (PID: 6232)
Create files in a temporary directory
- Launcher.exe (PID: 2940)
- sysxchceck.exe (PID: 6264)
- Launcher.exe (PID: 6448)
- sysxchceck.exe (PID: 2800)
- Launcher.exe (PID: 4536)
- Launcher.exe (PID: 7116)
- sysxchceck.exe (PID: 6232)
Reads the computer name
- sysxchceck.exe (PID: 6264)
- sysxchceck.exe (PID: 2800)
- sysxchceck.exe (PID: 6232)
Checks proxy server information
- sysxchceck.exe (PID: 6264)
- explorer.exe (PID: 4488)
- sysxchceck.exe (PID: 2800)
- sysxchceck.exe (PID: 6232)
Reads Microsoft Office registry keys
- explorer.exe (PID: 4488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:06:16 14:03:04 |
| ZipCRC: | 0xf08fc65c |
| ZipCompressedSize: | 4 |
| ZipUncompressedSize: | 4 |
| ZipFileName: | logs.txt |
Total processes
154
Monitored processes
28
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | "C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\Ultimate-Gift-Card-Generator.exe" | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\Ultimate-Gift-Card-Generator.exe | — | explorer.exe | |||||||||||
User: admin Company: CryptoX Integrity Level: MEDIUM Description: CryptoX Exit code: 0 Version: 1.2.1.1 Modules
| |||||||||||||||
| 2324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2800 | "C:\Users\admin\AppData\Roaming\sysxchceck.exe" | C:\Users\admin\AppData\Roaming\sysxchceck.exe | Ultimate-Gift-Card-Generator.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2940 | "Launcher.exe" | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\Launcher.exe | — | Ultimate-Gift-Card-Generator.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3172 | "C:\Users\admin\AppData\Roaming\sysxapcpteam.exe" | C:\Users\admin\AppData\Roaming\sysxapcpteam.exe | — | Ultimate-Gift-Card-Generator.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4044 | "C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\Ultimate-Gift-Card-Generator.exe" | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\Ultimate-Gift-Card-Generator.exe | — | explorer.exe | |||||||||||
User: admin Company: CryptoX Integrity Level: MEDIUM Description: CryptoX Exit code: 0 Version: 1.2.1.1 Modules
| |||||||||||||||
| 4488 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4536 | "C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\Launcher.exe" | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\Launcher.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5156 | "C:\WINDOWS\sysnative\cmd" /c "C:\Users\admin\AppData\Local\Temp\9771.tmp\9772.tmp\9782.bat C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\Launcher.exe" | C:\Windows\System32\cmd.exe | — | Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 875
Read events
21 743
Write events
108
Delete events
24
Modification events
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ultimate-Gift-Card-Generator.zip | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000602A4 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A48A294F7A40804AB924005FF030B61F | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010012000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C0000000F00000000000000680075006D0061006E00630061002E0070006E0067003E002000200000000E000000000000006900640074006800750073002E007200740066003E0020002000000010000000000000006C00730065006C006C0069006E0067002E007200740066003E0020002000000016000000000000006F0075007400700075007400610063006100640065006D00690063002E0070006E0067003E002000200000001200000000000000720069007600650072006C0069006700680074002E007200740066003E00200020000000150000000000000073006F00750072006300650073006100700070006500610072002E007200740066003E0020002000000017000000000000007300740061006E0064006100720064006D0061006E0061006700650072002E007200740066003E0020002000000014000000000000007500700061006300740069007600690074006900650073002E007200740066003E002000200000001200000000000000750072006C00700072006F007400650069006E002E0070006E0067003E00200020000000200000000000000055006C00740069006D006100740065002D0047006900660074002D0043006100720064002D00470065006E0065007200610074006F0072003E005C0020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001200000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000000400000A0401100 | |||
Executable files
7
Suspicious files
12
Text files
51
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6496 | WinRAR.exe | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\logs.txt | text | |
MD5:2165E4FA5BDDB65A31F6A0C495C2FA37 | SHA256:98F38F12DB221A8CF8CA7AADFDCD759B01D52EB4EBB3EEDBB2D97E92805C6960 | |||
| 6496 | WinRAR.exe | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\Credit\V0.2 RELASE DATE.txt | text | |
MD5:FC1E071526A96EF9C46D97AED035BB52 | SHA256:D88740878AEA8B07CE376FB2BF5EA6BDD33B9FD24497F57A54293DB309437905 | |||
| 6496 | WinRAR.exe | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\Ultimate-Gift-Card-Generator.exe | executable | |
MD5:4F43922D15DFEADA357E79ECC70F9B6F | SHA256:49791F07D26FBB35D82CE073EFE2694792BD922EA30B38D4EA49F6ACFD628080 | |||
| 6496 | WinRAR.exe | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\modules\paysafecard.js | text | |
MD5:19B9229560B48FA8159453AE7E8A1D79 | SHA256:1DEB7C9D73C1324D8F96B87F1FCADF4CE02066B6F53E4D4BF007A29A3E993F54 | |||
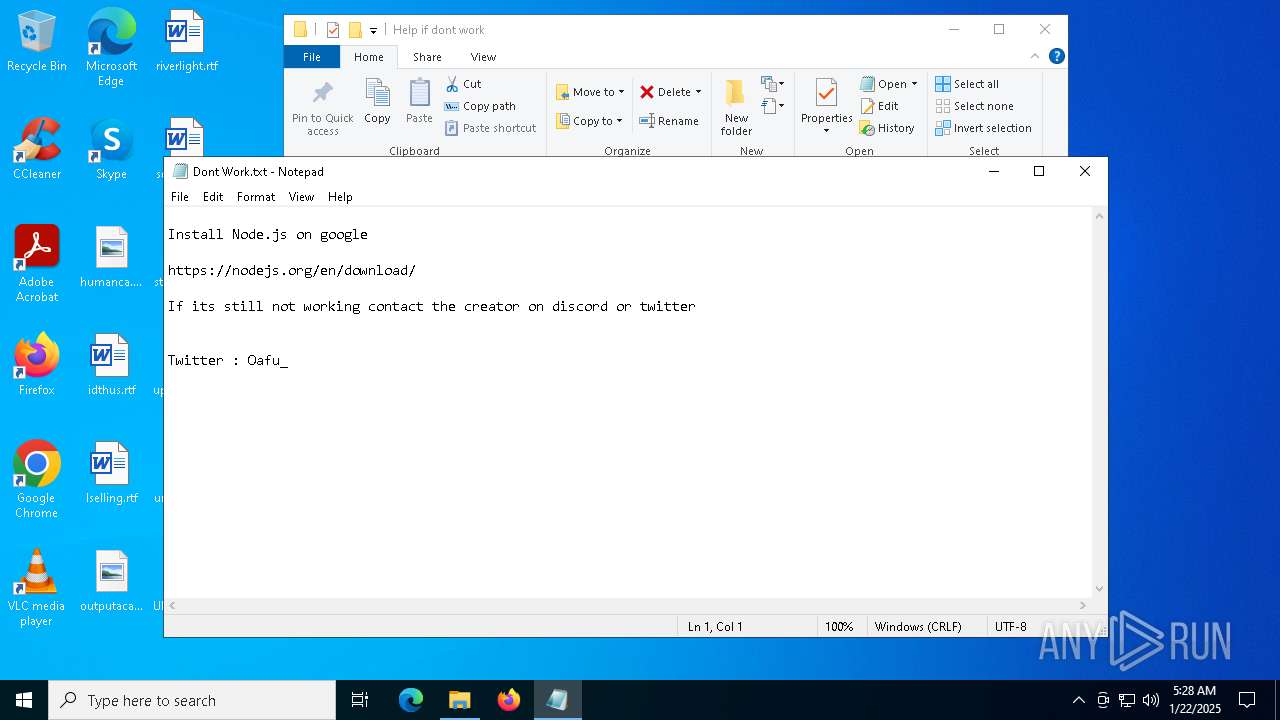
| 6496 | WinRAR.exe | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\Help if dont work\Dont Work.txt | text | |
MD5:18F815ED9A9C15DBAA0F0463DE09EE8E | SHA256:6878D0F6139EC9B76E6BF7946C2CE4CE16CB2735173980B96D40FA0FEDE1DFBA | |||
| 6496 | WinRAR.exe | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\modules\psn.js | text | |
MD5:FE852FF4BBABD8B8A87BAC85FB28BCC0 | SHA256:8D3FA2BEAFA01AD3B04D5989C0A11E56FCAF579F6F52E801DBC975C11DA35A00 | |||
| 6496 | WinRAR.exe | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\modules\amazon.js | text | |
MD5:64A0E4A16F121DA0D48B0EC39083B288 | SHA256:6FB04512ED1FBCC878821B6C19F79F1402D0464F7E198038B1F9F7696C08FD6A | |||
| 6496 | WinRAR.exe | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\modules\robux.js | text | |
MD5:1ADD4055338820FBE3632360D0D9EF95 | SHA256:E119CD4B9C668D358790626EB4A53ADFF16046089E96F898AE2683A158E8BFD2 | |||
| 6496 | WinRAR.exe | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\Credit\Contact.txt | text | |
MD5:0B0646CC33F7D1337A465B3356CA710F | SHA256:8EF18D81E431E2141FADAB3EFB738484A2FBC20C36FCA20F2FA94F55BCB910D3 | |||
| 6496 | WinRAR.exe | C:\Users\admin\Desktop\Ultimate-Gift-Card-Generator\modules\netflix.js | text | |
MD5:D3FBB5DE38879414191626AC513ABEE6 | SHA256:5F062BF0C5750E0CE31BA41AEDA9A9913ACF82EC9DFBBD91868E28CEE7387D8F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
35
DNS requests
15
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2800 | sysxchceck.exe | POST | 200 | 185.81.68.147:80 | http://185.81.68.147/svcstealer/get.php | unknown | — | — | malicious |
4488 | explorer.exe | POST | 200 | 185.81.68.147:80 | http://185.81.68.147/VzCAHn.php?2F33566DA0B91573532102 | unknown | — | — | malicious |
2800 | sysxchceck.exe | POST | 200 | 185.81.68.147:80 | http://185.81.68.147/svcstealer/get.php | unknown | — | — | malicious |
2800 | sysxchceck.exe | POST | 200 | 185.81.68.147:80 | http://185.81.68.147/svcstealer/get.php | unknown | — | — | malicious |
4488 | explorer.exe | POST | 200 | 185.81.68.147:80 | http://185.81.68.147/VzCAHn.php?2F33566DA0B91573532102 | unknown | — | — | malicious |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6264 | sysxchceck.exe | POST | 200 | 185.81.68.147:80 | http://185.81.68.147/svcstealer/get.php | unknown | — | — | malicious |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6264 | sysxchceck.exe | POST | 200 | 185.81.68.147:80 | http://185.81.68.147/svcstealer/get.php | unknown | — | — | malicious |
6264 | sysxchceck.exe | POST | 200 | 185.81.68.147:80 | http://185.81.68.147/svcstealer/get.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.155:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
6264 | sysxchceck.exe | 185.81.68.147:80 | — | Chang Way Technologies Co. Limited | RU | malicious |
6380 | backgroundTaskHost.exe | 20.74.47.205:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6264 | sysxchceck.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 32 |
4488 | explorer.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
4488 | explorer.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 32 |
4488 | explorer.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
4488 | explorer.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
4488 | explorer.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
4488 | explorer.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 32 |