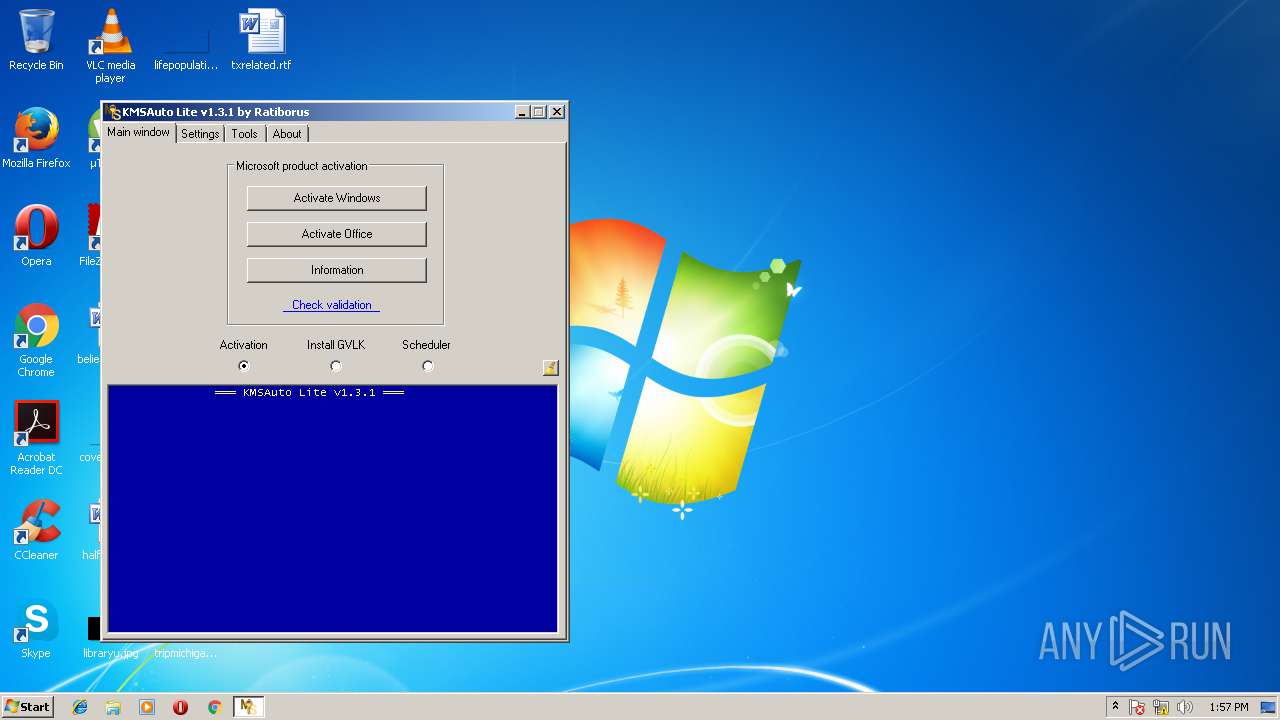
| File name: | KMSAuto.exe |
| Full analysis: | https://app.any.run/tasks/89f81dfc-4d2b-459f-9936-4eb7bfdc5d3d |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2018, 12:57:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6BF0A53E1823B2CEDD3E0F30A277DEC1 |
| SHA1: | AA0E65BE68CD3B7369E5171570A25DA6C92A3AA8 |
| SHA256: | 2BECBF916BCA5665AAC64D699063D5D56043675A495F686B1146D9382F17BB1E |
| SSDEEP: | 196608:/cywwyw7iywndywwywHywWywbywmIiyw7LzX:/Bwtw7fwgwtwSwLwewhw7LzX |
MALICIOUS
Application was dropped or rewritten from another process
- wzt.dat (PID: 3528)
Changes settings of System certificates
- certmgr.exe (PID: 3384)
- certmgr.exe (PID: 2284)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 3696)
- cmd.exe (PID: 2744)
Starts CMD.EXE for commands execution
- KMSAuto.exe (PID: 3888)
Creates files in the Windows directory
- wzt.dat (PID: 3528)
- KMSAuto.exe (PID: 3888)
- bin.dat (PID: 1236)
Removes files from Windows directory
- KMSAuto.exe (PID: 3888)
INFO
Loads rich edit control libraries
- KMSAuto.exe (PID: 3888)
Dropped object may contain URL's
- bin.dat (PID: 1236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:12:06 13:21:28+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 475136 |
| InitializedDataSize: | 6075392 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.1.0 |
| ProductVersionNumber: | 1.3.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 06-Dec-2016 12:21:28 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 06-Dec-2016 12:21:28 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.code | 0x00001000 | 0x0001BEAF | 0x0001C000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.94063 |
.text | 0x0001D000 | 0x00057FD1 | 0x00058000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.5646 |
.rdata | 0x00075000 | 0x000092B8 | 0x00009400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.61891 |
.data | 0x0007F000 | 0x005B6DE8 | 0x005B5200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.52472 |
.rsrc | 0x00636000 | 0x0000B164 | 0x0000B200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.46398 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.8674 | 874 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.29604 | 2216 | UNKNOWN | English - United States | RT_ICON |
3 | 4.35071 | 1736 | UNKNOWN | English - United States | RT_ICON |
4 | 3.03007 | 1384 | UNKNOWN | English - United States | RT_ICON |
5 | 3.79019 | 16936 | UNKNOWN | English - United States | RT_ICON |
6 | 4.1678 | 9640 | UNKNOWN | English - United States | RT_ICON |
7 | 4.32586 | 4264 | UNKNOWN | English - United States | RT_ICON |
8 | 4.672 | 2440 | UNKNOWN | English - United States | RT_ICON |
9 | 5.05539 | 1128 | UNKNOWN | English - United States | RT_ICON |
Imports
ADVAPI32.DLL |
COMCTL32.DLL |
GDI32.DLL |
ICMP.DLL |
IMAGEHLP.DLL |
IPHLPAPI.DLL |
KERNEL32.dll |
MSI.DLL |
MSVCRT.dll |
NETAPI32.DLL |
Total processes
49
Monitored processes
11
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1236 | bin.dat -y -pkmsauto | C:\Windows\Temp\KMSAuto\bin.dat | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2284 | certmgr.exe -add wzteam.cer -n wzteam -s -r localMachine ROOT | C:\Windows\Temp\KMSAuto\wzt\certmgr.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2744 | "C:\Windows\System32\cmd.exe" /c wzt.dat -y -pkmsauto | C:\Windows\System32\cmd.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2884 | "C:\Windows\System32\cmd.exe" /c certmgr.exe -add wzteam.cer -n wzteam -s -r localMachine TRUSTEDPUBLISHER | C:\Windows\System32\cmd.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2980 | "C:\Users\admin\AppData\Local\Temp\KMSAuto.exe" | C:\Users\admin\AppData\Local\Temp\KMSAuto.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3004 | "C:\Windows\System32\cmd.exe" /c copy C:\Windows\system32\Tasks\KMSAuto "C:\Users\admin\AppData\Local\Temp\KMSAuto.tmp" /Y | C:\Windows\System32\cmd.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3384 | certmgr.exe -add wzteam.cer -n wzteam -s -r localMachine TRUSTEDPUBLISHER | C:\Windows\Temp\KMSAuto\wzt\certmgr.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3528 | wzt.dat -y -pkmsauto | C:\Windows\Temp\KMSAuto\wzt.dat | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3696 | "C:\Windows\System32\cmd.exe" /c bin.dat -y -pkmsauto | C:\Windows\System32\cmd.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3828 | "C:\Windows\System32\cmd.exe" /c certmgr.exe -add wzteam.cer -n wzteam -s -r localMachine ROOT | C:\Windows\System32\cmd.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
32
Read events
30
Write events
2
Delete events
0
Modification events
| (PID) Process: | (2284) certmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\648384A4DEE53D4C1C87E10D67CC99307CCC9C98 |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000648384A4DEE53D4C1C87E10D67CC99307CCC9C982000000001000000FE010000308201FA30820167A00302010202108AC1A3101349C28A4D33947CFCD07662300906052B0E03021D05003011310F300D06035504031306575A5465616D301E170D3136313130323138343730365A170D3339313233313233353935395A3011310F300D06035504031306575A5465616D30819F300D06092A864886F70D010101050003818D0030818902818100AD2F8AA939C3EB40D1D6DE0509B9F4E7EBF8475B98C49E9FB4AD556D408E9B84E80D014078D65BE351E8A5D84CE2E92E84504F82E09DFA6C8310B58955527CEC2843039328B51891F2A09F70FD7E1348668A0AF780F741A30254397E9135220D442704C2395810A0A65B6B4EC54558E26C468C6087FD3BB1A1DE8414ADE68AAF0203010001A35B305930130603551D25040C300A06082B0601050507030330420603551D01043B30398010106AC14D8CB580F787E68A2938AB9BF3A1133011310F300D06035504031306575A5465616D82108AC1A3101349C28A4D33947CFCD07662300906052B0E03021D050003818100601D9E4107BECC4352D02281EC0764B2865E4ED60EE58228B7375D707730DEDE148E9ED41CE051C44D4E15D041CF8C601A054CA14B4A484F7DBAAB409E1D75CEBE6F8FA171E97E16EAE94B6757DA5C61B0B6F85CE2FEA31F50D664CC5BC1A40476A44EDDD5390357BC0D44C37B4969B5E4E923FEE772AFD4643B21BA918D40A8 | |||
| (PID) Process: | (3384) certmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\TrustedPublisher\Certificates\648384A4DEE53D4C1C87E10D67CC99307CCC9C98 |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000648384A4DEE53D4C1C87E10D67CC99307CCC9C982000000001000000FE010000308201FA30820167A00302010202108AC1A3101349C28A4D33947CFCD07662300906052B0E03021D05003011310F300D06035504031306575A5465616D301E170D3136313130323138343730365A170D3339313233313233353935395A3011310F300D06035504031306575A5465616D30819F300D06092A864886F70D010101050003818D0030818902818100AD2F8AA939C3EB40D1D6DE0509B9F4E7EBF8475B98C49E9FB4AD556D408E9B84E80D014078D65BE351E8A5D84CE2E92E84504F82E09DFA6C8310B58955527CEC2843039328B51891F2A09F70FD7E1348668A0AF780F741A30254397E9135220D442704C2395810A0A65B6B4EC54558E26C468C6087FD3BB1A1DE8414ADE68AAF0203010001A35B305930130603551D25040C300A06082B0601050507030330420603551D01043B30398010106AC14D8CB580F787E68A2938AB9BF3A1133011310F300D06035504031306575A5465616D82108AC1A3101349C28A4D33947CFCD07662300906052B0E03021D050003818100601D9E4107BECC4352D02281EC0764B2865E4ED60EE58228B7375D707730DEDE148E9ED41CE051C44D4E15D041CF8C601A054CA14B4A484F7DBAAB409E1D75CEBE6F8FA171E97E16EAE94B6757DA5C61B0B6F85CE2FEA31F50D664CC5BC1A40476A44EDDD5390357BC0D44C37B4969B5E4E923FEE772AFD4643B21BA918D40A8 | |||
Executable files
2
Suspicious files
0
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3888 | KMSAuto.exe | C:\Windows\Temp\KMSAuto\bin.dat | — | |
MD5:— | SHA256:— | |||
| 3528 | wzt.dat | C:\Windows\Temp\KMSAuto\wzt\certmgr.exe | — | |
MD5:— | SHA256:— | |||
| 3888 | KMSAuto.exe | C:\Windows\Temp\KMSAuto\bin\KMSactivator.vbs | text | |
MD5:EECEB60C87B8C588E78E16C1FE492F23 | SHA256:2A0E02EDDAB71AF1A718875E6FBDAA3E9B51007D37DFB863260212A6272B9AAF | |||
| 1236 | bin.dat | C:\Windows\Temp\KMSAuto\bin\KMSSS.exe | executable | |
MD5:ADD80E5D9FAD482705C3807BACFE1993 | SHA256:BB3830B14DF80838FB201C611ABF0C1F3714C6B8B103ED084EAFC170036631BE | |||
| 3888 | KMSAuto.exe | C:\Windows\Temp\KMSAuto\wzt.dat | executable | |
MD5:822DA2319294F2B768BFE9ED4EEBAC15 | SHA256:17B74D4EA905FAC0BA6857F78F47EE1E940675AF1BC27DED69FE2941318106EF | |||
| 3528 | wzt.dat | C:\Windows\Temp\KMSAuto\wzt\wzteam.cer | der | |
MD5:76B56D90E6F1DA030A8B85E64579F25A | SHA256:FD2D7DF0220DD65EE23D0090299DFCC356F6F8F7167BAE9ADF7D08CEFAF39D02 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
teredo.ipv6.microsoft.com |
| whitelisted |