| download: | release.exe |
| Full analysis: | https://app.any.run/tasks/05f4183a-faa7-41dc-9df0-d0cdcaf21f1c |
| Verdict: | Malicious activity |
| Analysis date: | September 21, 2021, 15:55:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5ACA117237E9C37136529D3778EC0C4D |
| SHA1: | CC9080C78B4AFCF728FEA50B4774E8977158B300 |
| SHA256: | 2BE86F526D00C0647DBE4C9C59A8F2FAA870D7FCAF575EC42F7D47F8C86DEFC0 |
| SSDEEP: | 49152:J84p+ldtH7riKKjJlrsJ3jD1jAwGe8mE6cO8GV4ijRE2HiBCbq7Nt8E4U:JzKh7KjJlINX1UwGeZcO5G2CBSUUE4U |
MALICIOUS
Drops executable file immediately after starts
- release.exe (PID: 3752)
Application was dropped or rewritten from another process
- Svc_host.exe (PID: 3200)
SUSPICIOUS
Checks supported languages
- release.exe (PID: 3752)
- Svc_host.exe (PID: 3200)
Drops a file with too old compile date
- release.exe (PID: 3752)
Executable content was dropped or overwritten
- release.exe (PID: 3752)
Drops a file that was compiled in debug mode
- release.exe (PID: 3752)
Reads the computer name
- release.exe (PID: 3752)
- Svc_host.exe (PID: 3200)
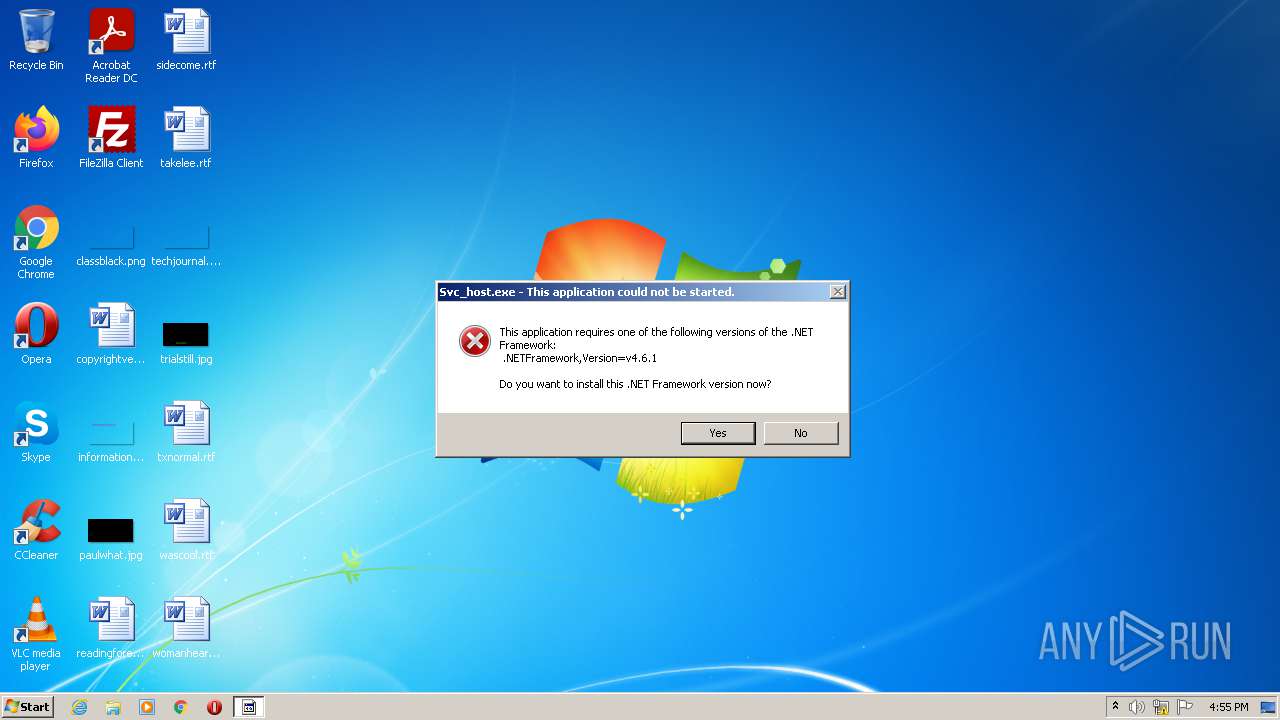
Starts Internet Explorer
- Svc_host.exe (PID: 3200)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3344)
INFO
Checks supported languages
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 3344)
Reads the computer name
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 3344)
Checks Windows Trust Settings
- iexplore.exe (PID: 3344)
- iexplore.exe (PID: 3104)
Changes internet zones settings
- iexplore.exe (PID: 3104)
Reads settings of System Certificates
- iexplore.exe (PID: 3344)
- iexplore.exe (PID: 3104)
Application launched itself
- iexplore.exe (PID: 3104)
Reads internet explorer settings
- iexplore.exe (PID: 3344)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3104)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3104)
Creates files in the user directory
- iexplore.exe (PID: 3344)
Changes settings of System certificates
- iexplore.exe (PID: 3104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x1eef0 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 114688 |
| CodeSize: | 201728 |
| LinkerVersion: | 14 |
| PEType: | PE32 |
| TimeStamp: | 2021:06:11 11:16:47+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-Jun-2021 09:16:47 |
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000110 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 11-Jun-2021 09:16:47 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000313BA | 0x00031400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.70981 |
.rdata | 0x00033000 | 0x0000A622 | 0x0000A800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.22268 |
.data | 0x0003E000 | 0x00023728 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.70882 |
.didat | 0x00062000 | 0x0000018C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.35543 |
.rsrc | 0x00063000 | 0x0000E038 | 0x0000E200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.80268 |
.reloc | 0x00072000 | 0x0000227C | 0x00002400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.56418 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.25329 | 1875 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
2 | 5.10026 | 2216 | Latin 1 / Western European | UNKNOWN | RT_ICON |
3 | 5.25868 | 3752 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 5.02609 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 5.18109 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
6 | 5.04307 | 9640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
7 | 3.66634 | 508 | Latin 1 / Western European | UNKNOWN | RT_STRING |
8 | 3.71728 | 582 | Latin 1 / Western European | UNKNOWN | RT_STRING |
9 | 3.73856 | 422 | Latin 1 / Western European | UNKNOWN | RT_STRING |
10 | 3.55807 | 220 | Latin 1 / Western European | UNKNOWN | RT_STRING |
Imports
KERNEL32.dll |
USER32.dll (delay-loaded) |
gdiplus.dll |
Total processes
38
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
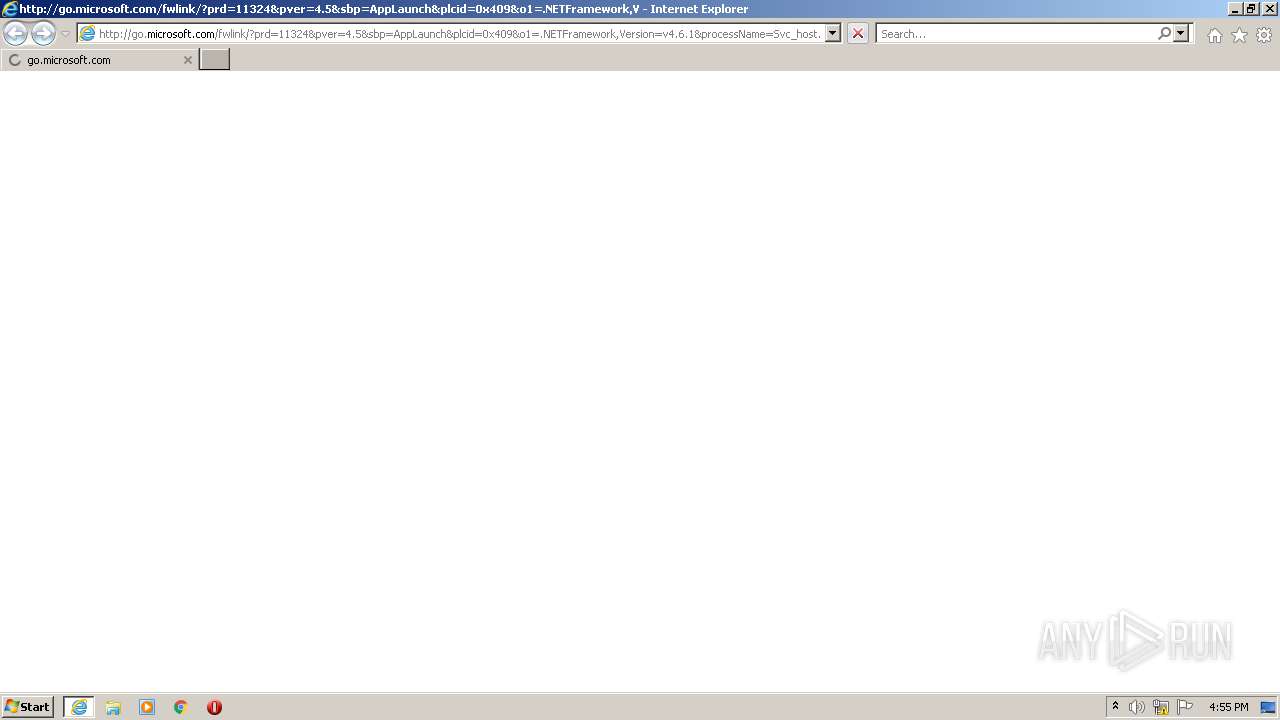
| 3104 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?prd=11324&pver=4.5&sbp=AppLaunch&plcid=0x409&o1=.NETFramework,Version=v4.6.1&processName=Svc_host.exe&platform=0000&osver=5&isServer=0&shimver=4.0.30319.34209 | C:\Program Files\Internet Explorer\iexplore.exe | Svc_host.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3200 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\Svc_host.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\Svc_host.exe | — | release.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Svc_host Exit code: 3221225547 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3344 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3104 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3752 | "C:\Users\admin\AppData\Local\Temp\release.exe" | C:\Users\admin\AppData\Local\Temp\release.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
12 467
Read events
12 347
Write events
118
Delete events
2
Modification events
| (PID) Process: | (3752) release.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3752) release.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3752) release.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3752) release.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 708142928 | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30912257 | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30912257 | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
11
Suspicious files
12
Text files
36
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3752 | release.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Svc_host.exe | executable | |
MD5:— | SHA256:— | |||
| 3752 | release.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Buffers.xml | xml | |
MD5:1C55860DD93297A6EA2FAD2974834C3A | SHA256:2EC7FB12E11F9831E40524427F6D88A3C9FFDD56CCFA81D373467B75B479A578 | |||
| 3752 | release.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Data.SQLite.xml | xml | |
MD5:D111D791998481A37C62F2D465ECF970 | SHA256:B9C98B47E6BD8C4BF59B27E7DAC0C82D2DDDD3C93B794DE8538B4F23CD8E6464 | |||
| 3752 | release.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Newtonsoft.Json.xml | xml | |
MD5:AD1A946CDBE4FC83907CF558FB80A37F | SHA256:E3C9CB0CBF4B3BE20B6030F3A4872EDD81E042048D2D19732EAC3EEB9779DC0B | |||
| 3752 | release.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Numerics.Vectors.dll | executable | |
MD5:AAA2CBF14E06E9D3586D8A4ED455DB33 | SHA256:1D3EF8698281E7CF7371D1554AFEF5872B39F96C26DA772210A33DA041BA1183 | |||
| 3752 | release.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Numerics.Vectors.xml | xml | |
MD5:95DD29CA17B63843AD787D3BC9C8C933 | SHA256:AE2C3DE9AD57D7091D9F44DCDEE3F88ECCF2BA7CB43ADC9BB24769154A532DC7 | |||
| 3752 | release.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\BouncyCastle.Crypto.dll | executable | |
MD5:87A4ADE7FAEAF5021ADE5FCC797F4F70 | SHA256:07498B990AA84916EC6D84E24CDF99A0AC0E265FF3E53598A9B153285BD23594 | |||
| 3752 | release.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\x64\SQLite.Interop.dll | executable | |
MD5:7DE130CE491D63ECB3920687A84DF54A | SHA256:1D534617B38323027A64579A581258A55C3986F5B4B15297126C8A4CEF5AA105 | |||
| 3752 | release.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Buffers.dll | executable | |
MD5:ECDFE8EDE869D2CCC6BF99981EA96400 | SHA256:ACCCCFBE45D9F08FFEED9916E37B33E98C65BE012CFFF6E7FA7B67210CE1FEFB | |||
| 3752 | release.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Data.SQLite.dll | executable | |
MD5:83DFD2FE35EFB2154BCDD3B475F378F2 | SHA256:7A4DDE948B573B5A92CB1F63A2201006E61EA24107D9668A36EFA378E8D48F08 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
37
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3104 | iexplore.exe | GET | 304 | 8.248.131.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?db08cc433910c912 | US | — | — | whitelisted |
3344 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
3344 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
3104 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
3344 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3344 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA9bw6F2y3ieICDHiTyBZ7Q%3D | US | der | 1.47 Kb | whitelisted |
3344 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
3344 | iexplore.exe | GET | 200 | 216.58.212.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3344 | iexplore.exe | GET | 200 | 216.58.212.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
— | — | GET | 200 | 8.248.131.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9727023fcf0223e3 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3344 | iexplore.exe | 104.92.93.19:443 | go.microsoft.com | Akamai Technologies, Inc. | NL | unknown |
— | — | 8.248.131.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
3344 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
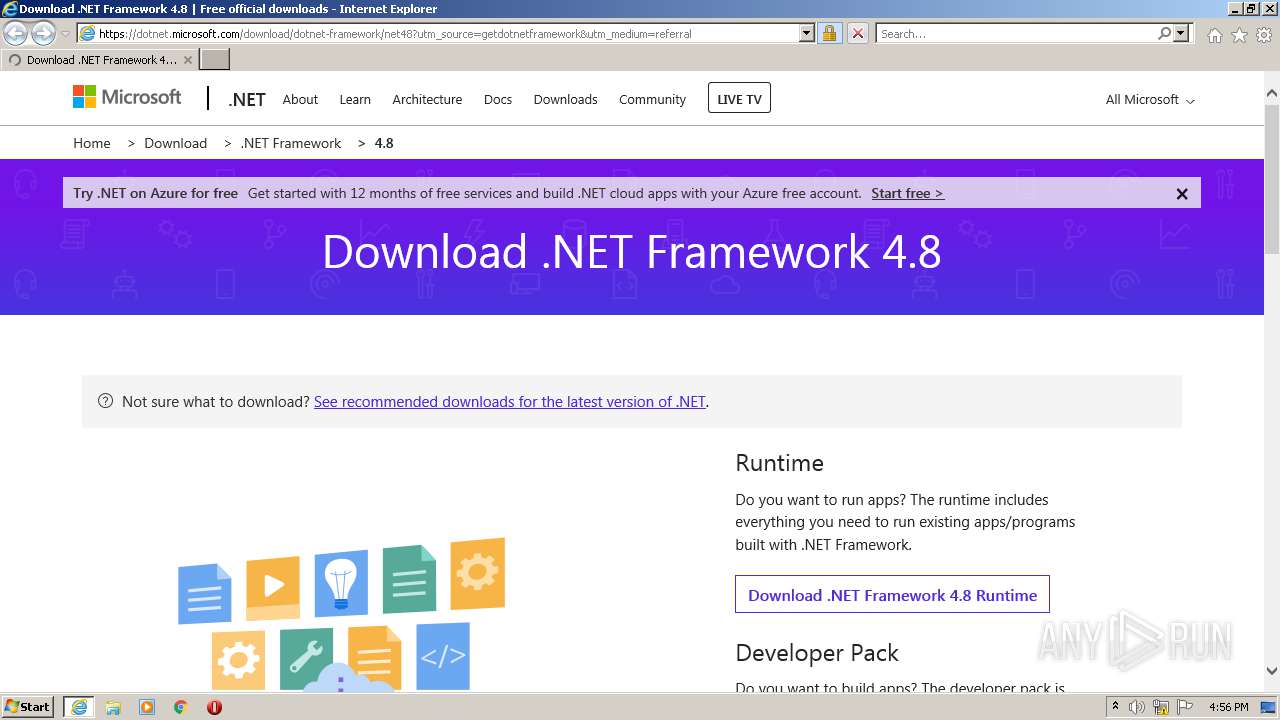
3344 | iexplore.exe | 13.107.246.45:443 | dotnet.microsoft.com | Microsoft Corporation | US | malicious |
3104 | iexplore.exe | 8.248.131.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
3344 | iexplore.exe | 172.217.20.14:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 13.107.246.45:443 | dotnet.microsoft.com | Microsoft Corporation | US | malicious |
3344 | iexplore.exe | 13.69.106.208:443 | dc.services.visualstudio.com | Microsoft Corporation | NL | unknown |
3344 | iexplore.exe | 92.123.195.43:443 | statics-marketingsites-wcus-ms-com.akamaized.net | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
dotnet.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
statics-marketingsites-wcus-ms-com.akamaized.net |
| whitelisted |
img-prod-cms-rt-microsoft-com.akamaized.net |
| whitelisted |
az416426.vo.msecnd.net |
| whitelisted |