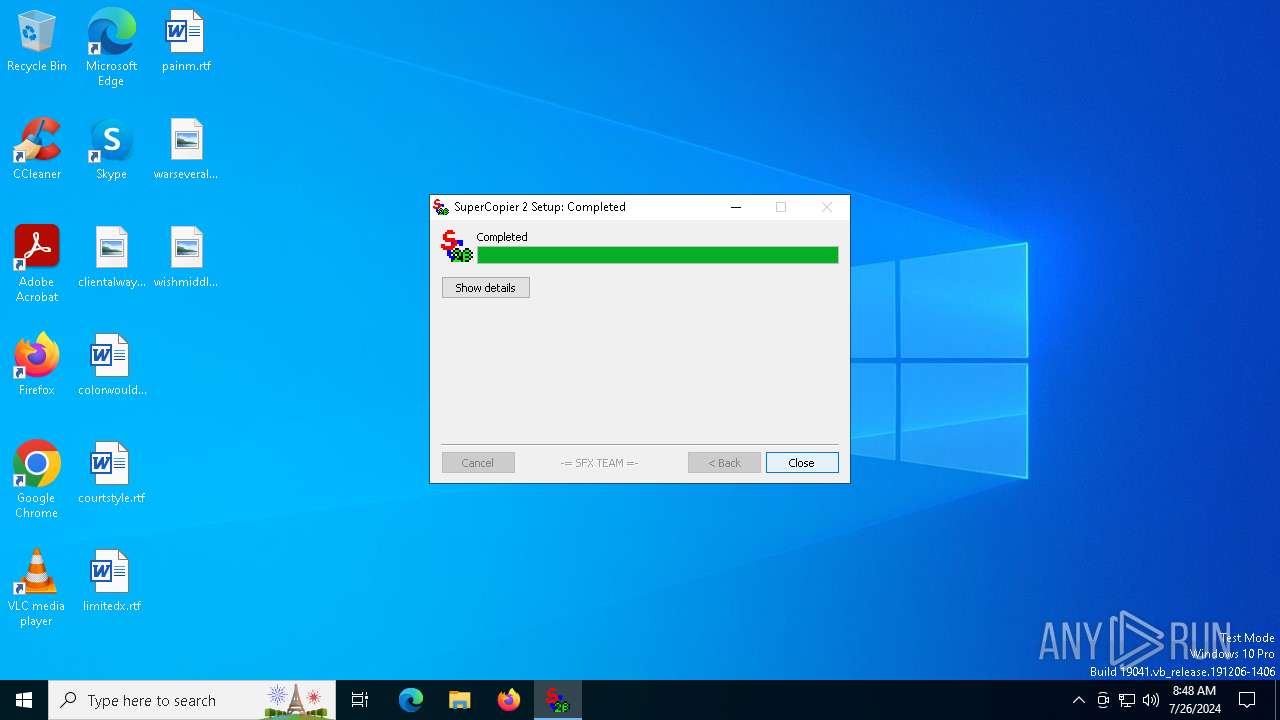
| File name: | SuperCopier22beta.exe |
| Full analysis: | https://app.any.run/tasks/70b5631e-1f2e-41f8-aad6-194cd030ff23 |
| Verdict: | Malicious activity |
| Analysis date: | July 26, 2024, 08:47:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | AB0787C780AAA099CE2046242EDB6CD2 |
| SHA1: | 6DC4DF23B891FA8558B0A56BC9F18A31C68A1324 |
| SHA256: | 2BBF0D4BC3848B1489FB2314E210F5E308113725D929E356BFB29E41774E2927 |
| SSDEEP: | 24576:yo4wiMk6cgd/MX9vQ7NAKAWipfv3glBY/a7YJZvcGcqO:yo4NMk6cgd/u9vQ7NAKAWipfv3glBY/G |
MALICIOUS
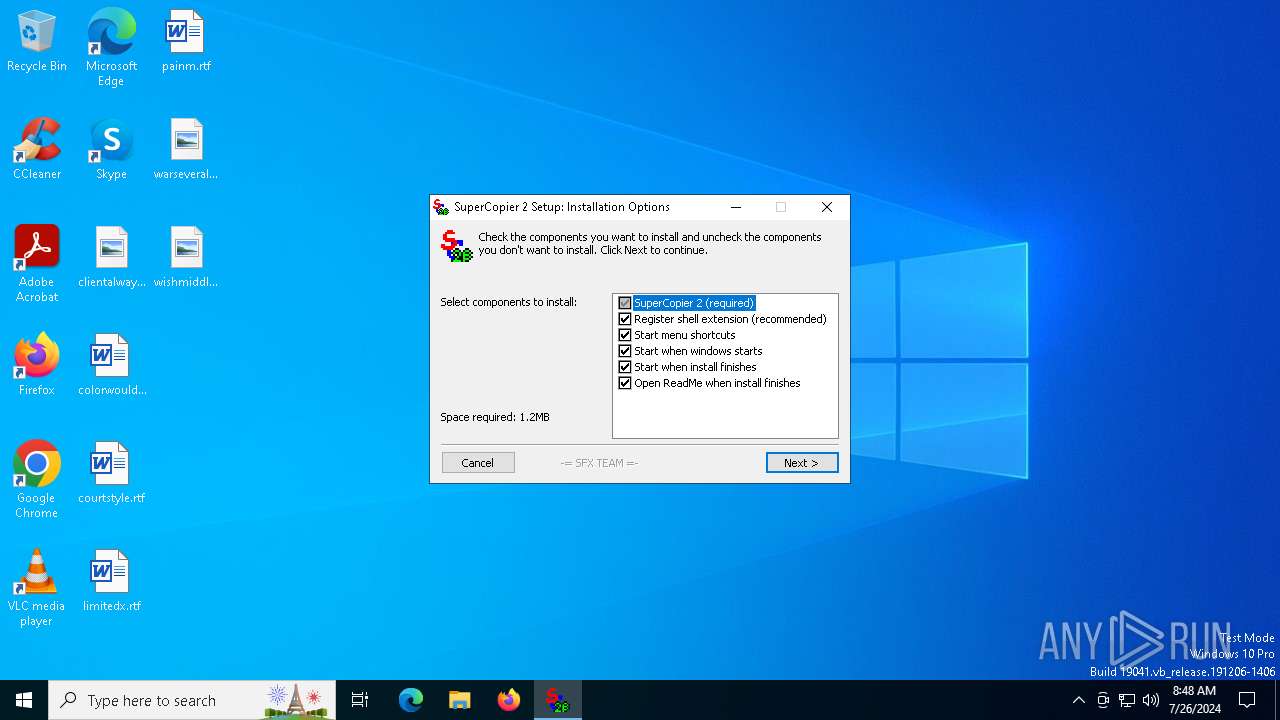
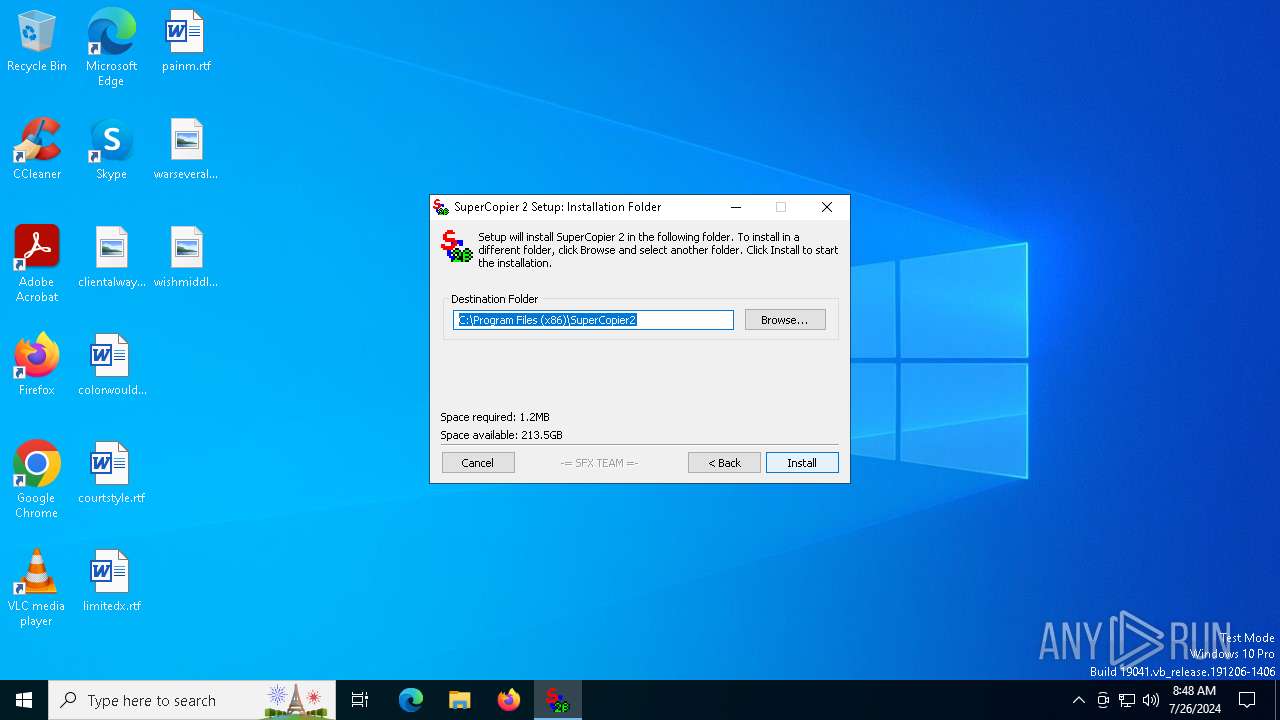
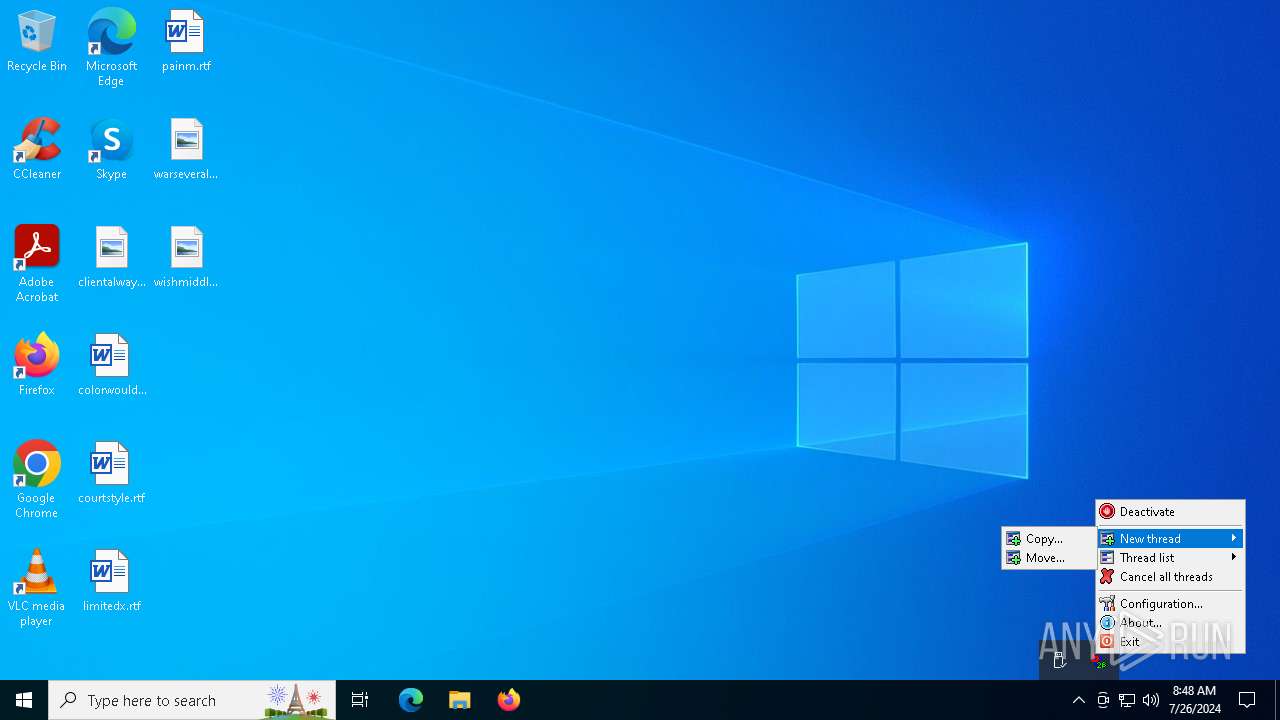
Drops the executable file immediately after the start
- SuperCopier22beta.exe (PID: 1180)
Registers / Runs the DLL via REGSVR32.EXE
- SuperCopier22beta.exe (PID: 1180)
Changes the autorun value in the registry
- SuperCopier22beta.exe (PID: 1180)
SUSPICIOUS
Executable content was dropped or overwritten
- SuperCopier22beta.exe (PID: 1180)
Malware-specific behavior (creating "System.dll" in Temp)
- SuperCopier22beta.exe (PID: 1180)
Creates/Modifies COM task schedule object
- SuperCopier22beta.exe (PID: 1180)
- regsvr32.exe (PID: 6440)
Creates a software uninstall entry
- SuperCopier22beta.exe (PID: 1180)
The process creates files with name similar to system file names
- SuperCopier22beta.exe (PID: 1180)
Reads security settings of Internet Explorer
- SuperCopier22beta.exe (PID: 1180)
Reads the date of Windows installation
- SuperCopier22beta.exe (PID: 1180)
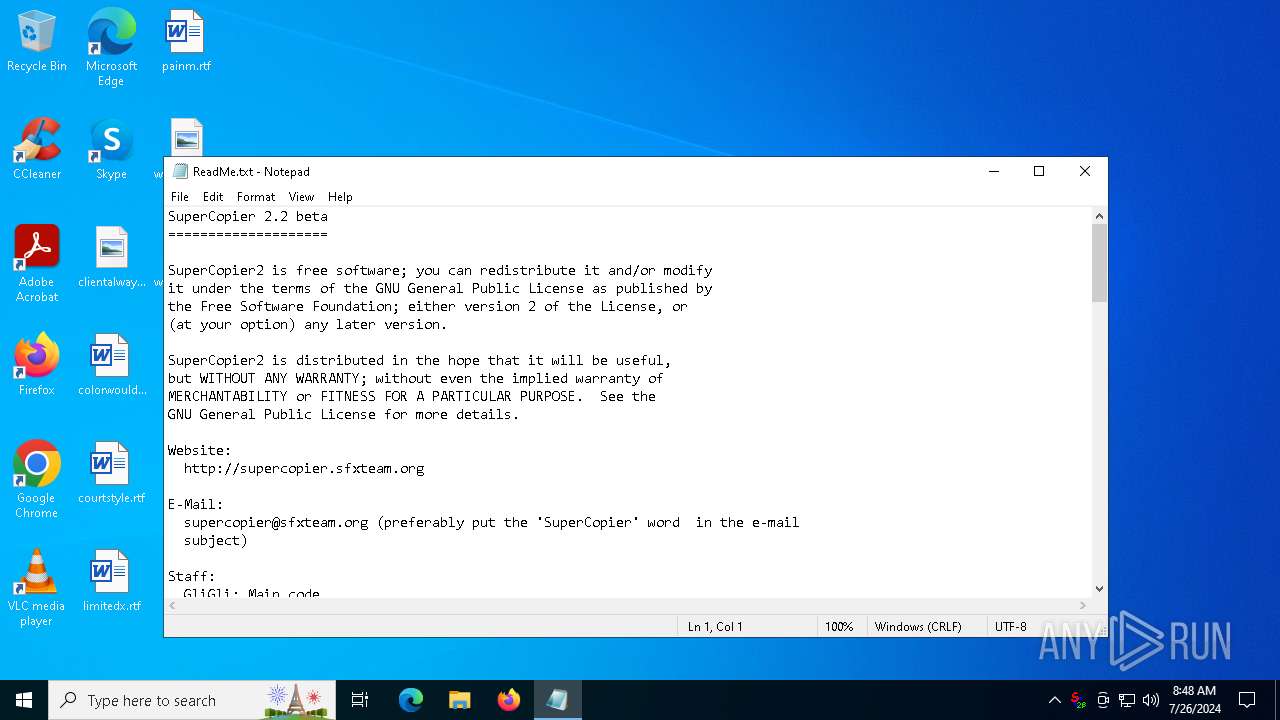
Start notepad (likely ransomware note)
- SuperCopier22beta.exe (PID: 1180)
There is functionality for taking screenshot (YARA)
- SuperCopier2.exe (PID: 2432)
INFO
Checks supported languages
- SuperCopier22beta.exe (PID: 1180)
- SuperCopier2.exe (PID: 2432)
Creates files in the program directory
- SuperCopier22beta.exe (PID: 1180)
Reads the computer name
- SuperCopier22beta.exe (PID: 1180)
- SuperCopier2.exe (PID: 2432)
Create files in a temporary directory
- SuperCopier22beta.exe (PID: 1180)
Creates files or folders in the user directory
- SuperCopier22beta.exe (PID: 1180)
Process checks computer location settings
- SuperCopier22beta.exe (PID: 1180)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (91.9) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.3) |
| .exe | | | Win64 Executable (generic) (3) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:02:21 19:46:34+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 119808 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x323c |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
148
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | "C:\Users\admin\AppData\Local\Temp\SuperCopier22beta.exe" | C:\Users\admin\AppData\Local\Temp\SuperCopier22beta.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1328 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Program Files (x86)\SuperCopier2\ReadMe.txt | C:\Windows\SysWOW64\notepad.exe | — | SuperCopier22beta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | "C:\Program Files (x86)\SuperCopier2\SuperCopier2.exe" | C:\Program Files (x86)\SuperCopier2\SuperCopier2.exe | SuperCopier22beta.exe | ||||||||||||
User: admin Company: SFX TEAM Integrity Level: HIGH Description: SuperCopier 2 (explorer file copy replacement) Version: 2.2.0.650 Modules
| |||||||||||||||
| 5196 | "C:\Users\admin\AppData\Local\Temp\SuperCopier22beta.exe" | C:\Users\admin\AppData\Local\Temp\SuperCopier22beta.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6440 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\SuperCopier2\SC2ShellExt64.dll" | C:\Windows\System32\regsvr32.exe | — | SuperCopier22beta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7108 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 699
Read events
8 635
Write events
61
Delete events
3
Modification events
| (PID) Process: | (1180) SuperCopier22beta.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\SuperCopier2 |
| Operation: | write | Name: | DisplayName |
Value: SuperCopier2 | |||
| (PID) Process: | (1180) SuperCopier22beta.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\SuperCopier2 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\SuperCopier2\SC2Uninst.exe" | |||
| (PID) Process: | (1180) SuperCopier22beta.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\SuperCopier2 |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (1180) SuperCopier22beta.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\SuperCopier2 |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (1180) SuperCopier22beta.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{68D44A27-FFB6-4B89-A3E5-7B0E50A7AB33}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (1180) SuperCopier22beta.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {68D44A27-FFB6-4B89-A3E5-7B0E50A7AB33} |
Value: SC2ShellExt | |||
| (PID) Process: | (6440) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{68FF37C4-51BC-4c2a-A992-7E39BC0E706F}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (6440) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {68FF37C4-51BC-4c2a-A992-7E39BC0E706F} |
Value: SC2ShellExt64 | |||
| (PID) Process: | (1180) SuperCopier22beta.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 12 | |||
| (PID) Process: | (1180) SuperCopier22beta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SuperCopier2.exe |
Value: C:\Program Files (x86)\SuperCopier2\SuperCopier2.exe | |||
Executable files
7
Suspicious files
1
Text files
4
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1180 | SuperCopier22beta.exe | C:\Program Files (x86)\SuperCopier2\ReadMe.txt | text | |
MD5:691157B7221D9492F716247425F918D7 | SHA256:52269B101F4C8CEAC9B0D51AF041CD99312773627B1BB8452F040AFFFEA97D5B | |||
| 1180 | SuperCopier22beta.exe | C:\Program Files (x86)\SuperCopier2\SC2Config.exe | executable | |
MD5:7ABED2B3EC1B782F13F908A48A3C3DFA | SHA256:5798A868CE9810598B96B9E26D2CEF4B0FF71C48DA74C427F828AE7B5989F715 | |||
| 1180 | SuperCopier22beta.exe | C:\Program Files (x86)\SuperCopier2\LisezMoi.txt | text | |
MD5:F17FD7456C5A78B684DA93D62B7D792D | SHA256:1D127B1D69F61FEFC16CF7516226BA7E878D970146BEE212E685FEAFD0F2664B | |||
| 1180 | SuperCopier22beta.exe | C:\Users\admin\AppData\Local\Temp\nscAF5.tmp | binary | |
MD5:F431FE3F05D01975F02918380BA5F7E3 | SHA256:932169F0BCF1E66ECFF71CB7EED1221E6ECCA25E4D3A0E6B432042EF85664D30 | |||
| 1180 | SuperCopier22beta.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\SuperCopier2\ReadMe.lnk | lnk | |
MD5:66155AB6AB3DB70721B744B80742E285 | SHA256:DF939BBEAD715F75694FD21558D45467D0E9C2E5F9EEEE3214696B12552FAF7F | |||
| 1180 | SuperCopier22beta.exe | C:\Program Files (x86)\SuperCopier2\SC2ShellExt64.dll | executable | |
MD5:44838089C7BC1FB1F9A3B8F5F645B0E0 | SHA256:2B8601DF6655F2DD0A4E4E0D51E7AE109D41912D2A6AC934EADC05B4DCA9D4CE | |||
| 1180 | SuperCopier22beta.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\SuperCopier2\SuperCopier2.lnk | lnk | |
MD5:56E7C7986E6E41292709F393CE813B6F | SHA256:8308EC55A32B8E46C81683A972538CB703673999BA2F85060C04B227ED9DC812 | |||
| 1180 | SuperCopier22beta.exe | C:\Users\admin\AppData\Local\Temp\nscAF6.tmp\System.dll | executable | |
MD5:C6F5B9596DB45CE43F14B64E0FBCF552 | SHA256:4B6DA3F2BDB6C452FB493B98F6B7AA1171787DBD3FA2DF2B3B22CCAEAC88FFA0 | |||
| 1180 | SuperCopier22beta.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\SuperCopier2\Menu access.lnk | lnk | |
MD5:457EEA0A4838AFC2CFA6E13D01CC3318 | SHA256:7948032565CA85BA9DDE215EDE56197BC1F498AC77060D80FDC9ADDC175C5678 | |||
| 2432 | SuperCopier2.exe | C:\Users\admin\Downloads\sciencevirtual.rtf | text | |
MD5:A000426FAAB4A2F7A1C59B759038115C | SHA256:072FE412EC131B7C936B6DE2DD5737FF07370E1CAC0EB0C7736F6C59DCDBE183 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
52
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5804 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5368 | SearchApp.exe | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5368 | SearchApp.exe | 184.86.251.15:443 | www.bing.com | Akamai International B.V. | DE | unknown |
484 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4340 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4248 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5368 | SearchApp.exe | 13.107.246.60:443 | fp-afd-nocache-ccp.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |