| File name: | CLIENT.apk |
| Full analysis: | https://app.any.run/tasks/feb5f537-6e27-40c5-b26f-f313578738f7 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 14:20:37 |
| OS: | Android 14 |
| MIME: | application/vnd.android.package-archive |
| File info: | Android package (APK), with AndroidManifest.xml, with APK Signing Block |
| MD5: | E05F642A954E5FA5D06C56CF04C00B2D |
| SHA1: | 19D28D4F2677D6311CCC90C74806383931F2C0BC |
| SHA256: | 2BBE9CD94760FFE4F2AC5058343C25D7E9A24C5C678A1D3493999DE2A5EA18DC |
| SSDEEP: | 98304:WQuKsHcuv+DyijWvJUEbpLK4rj6m5iUYy1T2X/iWjUIvwcIvxaHYnCg3m1/xE3iU:XFBkZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Launches a new activity
- app_process64 (PID: 2255)
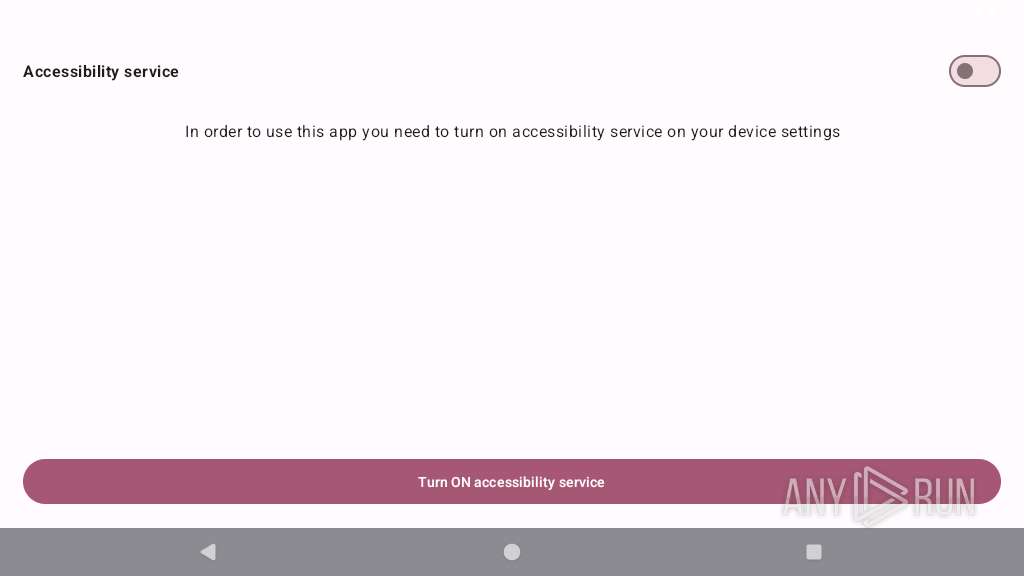
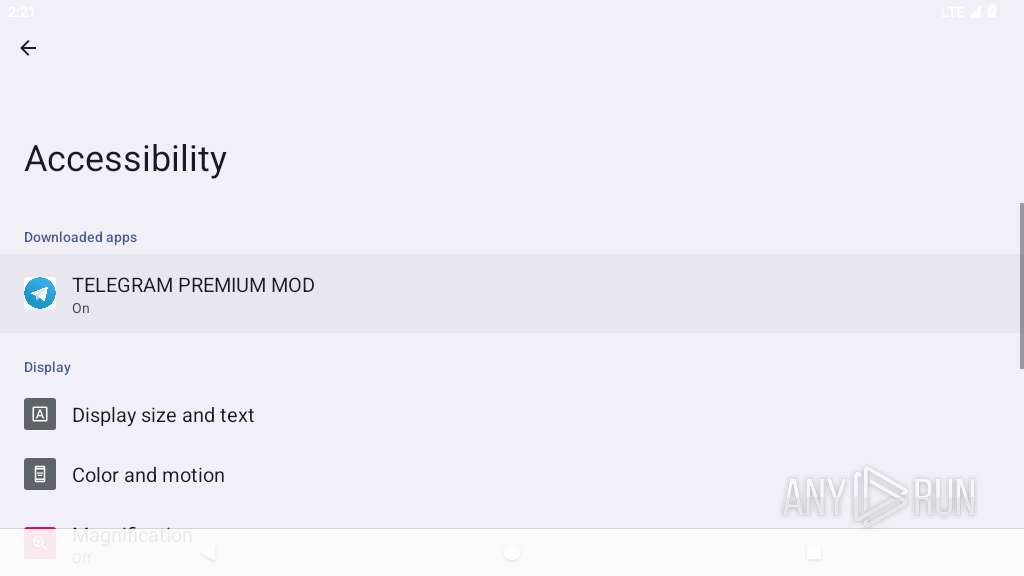
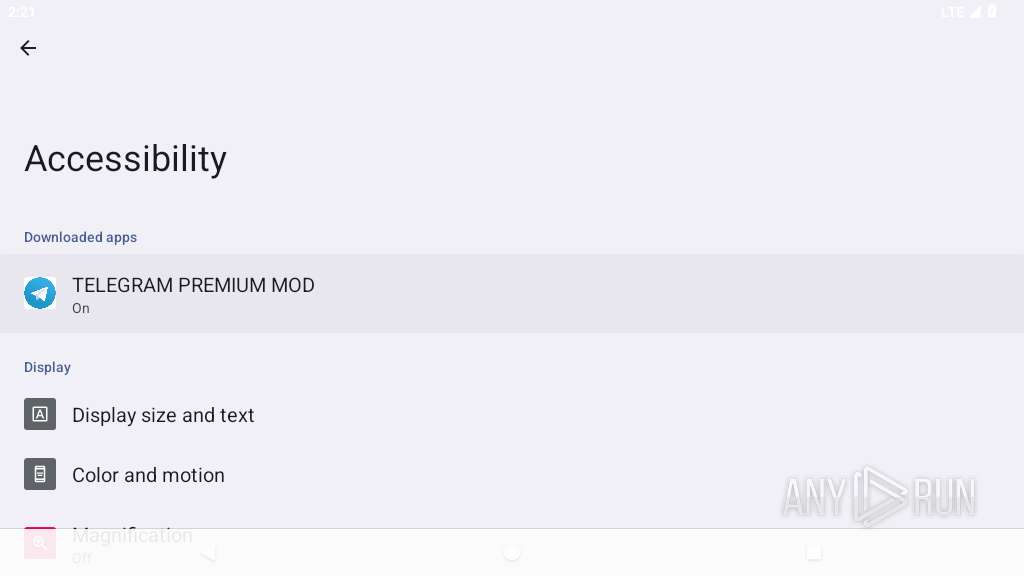
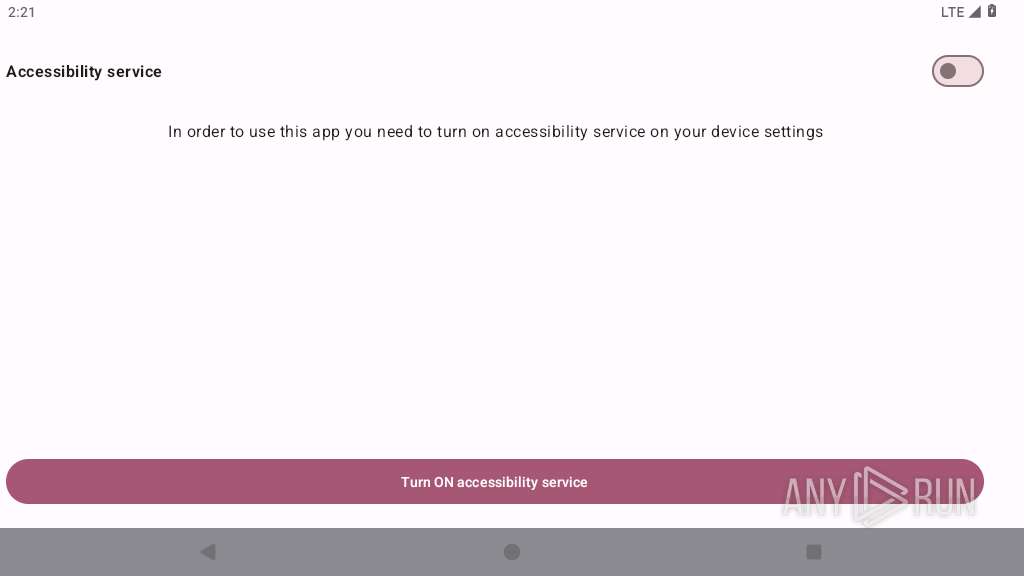
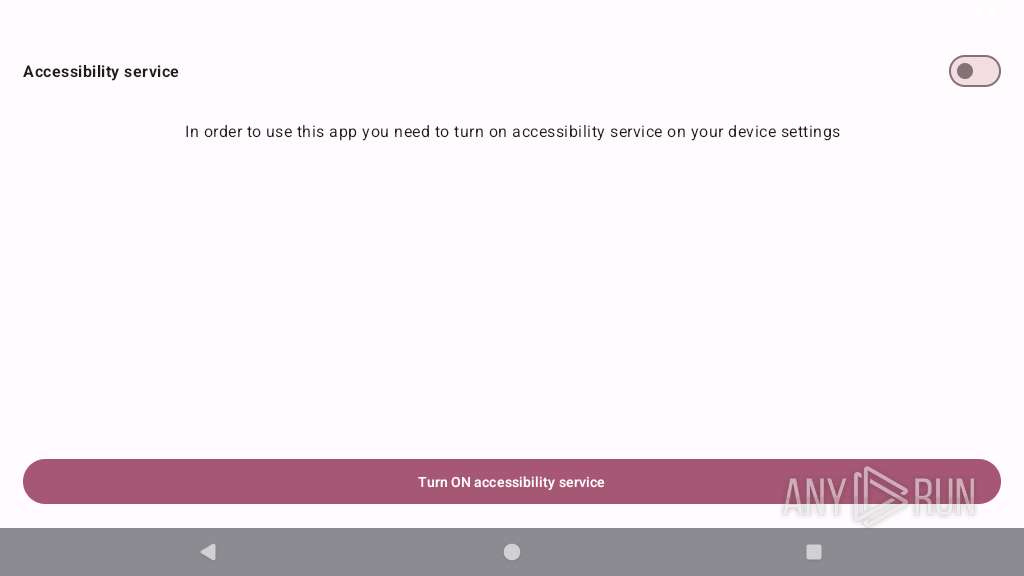
Requests access to accessibility settings
- app_process64 (PID: 2255)
Collects data about the device's environment (JVM version)
- app_process64 (PID: 2255)
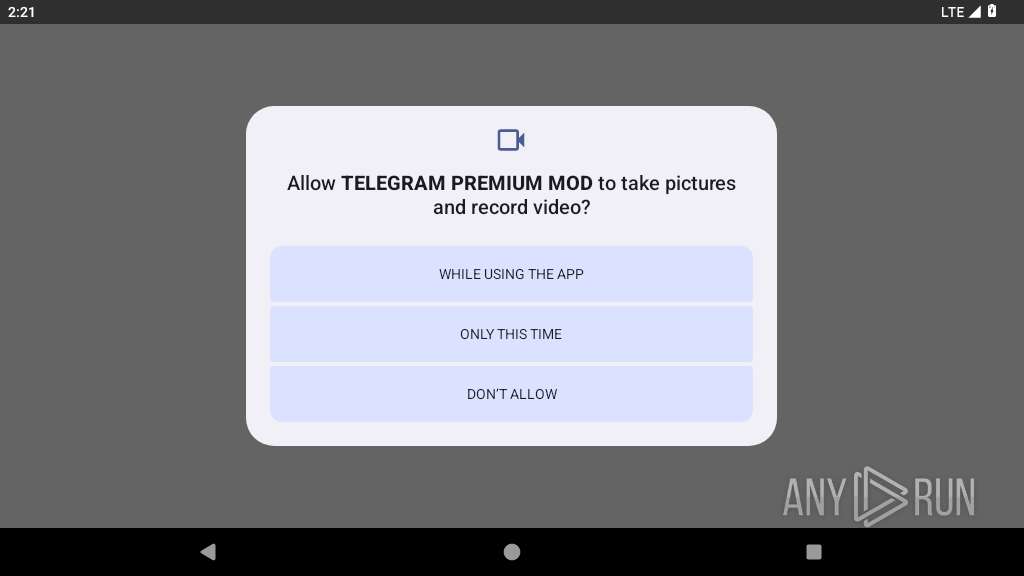
Accesses system-level resources
- app_process64 (PID: 2255)
INFO
Dynamically inspects or modifies classes, methods, and fields at runtime
- app_process64 (PID: 2255)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .apk | | | Android Package (73.9) |
|---|---|---|
| .jar | | | Java Archive (20.4) |
| .zip | | | ZIP compressed archive (5.6) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 05:30:00 |
| ZipCRC: | 0xef917095 |
| ZipCompressedSize: | 2359 |
| ZipUncompressedSize: | 9464 |
| ZipFileName: | AndroidManifest.xml |
Total processes
130
Monitored processes
5
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2255 | cybershieldx.rainbow | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2321 | com.android.systemui.accessibility.accessibilitymenu | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2407 | zygote | /system/bin/app_process32 | app_process32 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2418 | webview_zygote | /system/bin/app_process32 | — | app_process32 |
User: webview_zygote Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2457 | zygote | /system/bin/app_process32 | app_process32 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
83
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2255 | app_process64 | /data/data/cybershieldx.rainbow/cache/oat_primary/arm64/base.2255.tmp | binary | |
MD5:— | SHA256:— | |||
| 2255 | app_process64 | /data/data/cybershieldx.rainbow/files/profileInstalled | binary | |
MD5:— | SHA256:— | |||
| 2255 | app_process64 | /data/data/cybershieldx.rainbow/shared_prefs/WebViewChromiumPrefs.xml | xml | |
MD5:— | SHA256:— | |||
| 2255 | app_process64 | /data/data/cybershieldx.rainbow/app_webview/Default/Local Storage/leveldb/MANIFEST-000001 | binary | |
MD5:— | SHA256:— | |||
| 2255 | app_process64 | /data/data/cybershieldx.rainbow/cache/WebView/Default/HTTP Cache/Code Cache/webui_js/index | binary | |
MD5:— | SHA256:— | |||
| 2255 | app_process64 | /data/data/cybershieldx.rainbow/cache/WebView/Default/HTTP Cache/Code Cache/wasm/index | binary | |
MD5:— | SHA256:— | |||
| 2255 | app_process64 | /data/data/cybershieldx.rainbow/cache/WebView/Default/HTTP Cache/Code Cache/js/index | binary | |
MD5:— | SHA256:— | |||
| 2255 | app_process64 | /data/data/cybershieldx.rainbow/app_webview/Default/Local Storage/leveldb/000001.dbtmp | text | |
MD5:— | SHA256:— | |||
| 2255 | app_process64 | /data/data/cybershieldx.rainbow/app_webview/Default/Local Storage/leveldb/CURRENT | text | |
MD5:— | SHA256:— | |||
| 2255 | app_process64 | /data/data/cybershieldx.rainbow/cache/WebView/Default/HTTP Cache/Code Cache/webui_js/index-dir/temp-index | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
25
DNS requests
11
Threats
5
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
445 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
579 | app_process64 | 216.239.35.0:123 | — | — | — | unknown |
579 | app_process64 | 216.239.35.8:123 | — | — | — | whitelisted |
579 | app_process64 | 216.239.35.4:123 | — | — | — | unknown |
2255 | app_process64 | 216.24.57.252:443 | dogerat-free.onrender.com | RENDER | US | suspicious |
2457 | app_process32 | 172.217.18.3:443 | update.googleapis.com | GOOGLE | US | whitelisted |
2457 | app_process32 | 142.250.185.78:443 | dl.google.com | GOOGLE | US | whitelisted |
2457 | app_process32 | 142.250.186.164:443 | — | GOOGLE | US | whitelisted |
2255 | app_process64 | 142.250.186.164:443 | — | GOOGLE | US | whitelisted |
2407 | app_process32 | 172.217.18.3:443 | update.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
dogerat-free.onrender.com |
| unknown |
update.googleapis.com |
| whitelisted |
dl.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
apis.google.com |
| whitelisted |
play.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |
341 | netd | Not Suspicious Traffic | INFO [ANY.RUN] Host dynamic web apps service (.onrender .com) |
341 | netd | Misc activity | ET INFO DNS Query to Online Application Hosting Domain (onrender .com) |
2255 | app_process64 | Misc activity | ET INFO Observed Online Application Hosting Domain (onrender .com in TLS SNI) |
2255 | app_process64 | Misc activity | ET INFO Observed Online Application Hosting Domain (onrender .com in TLS SNI) |