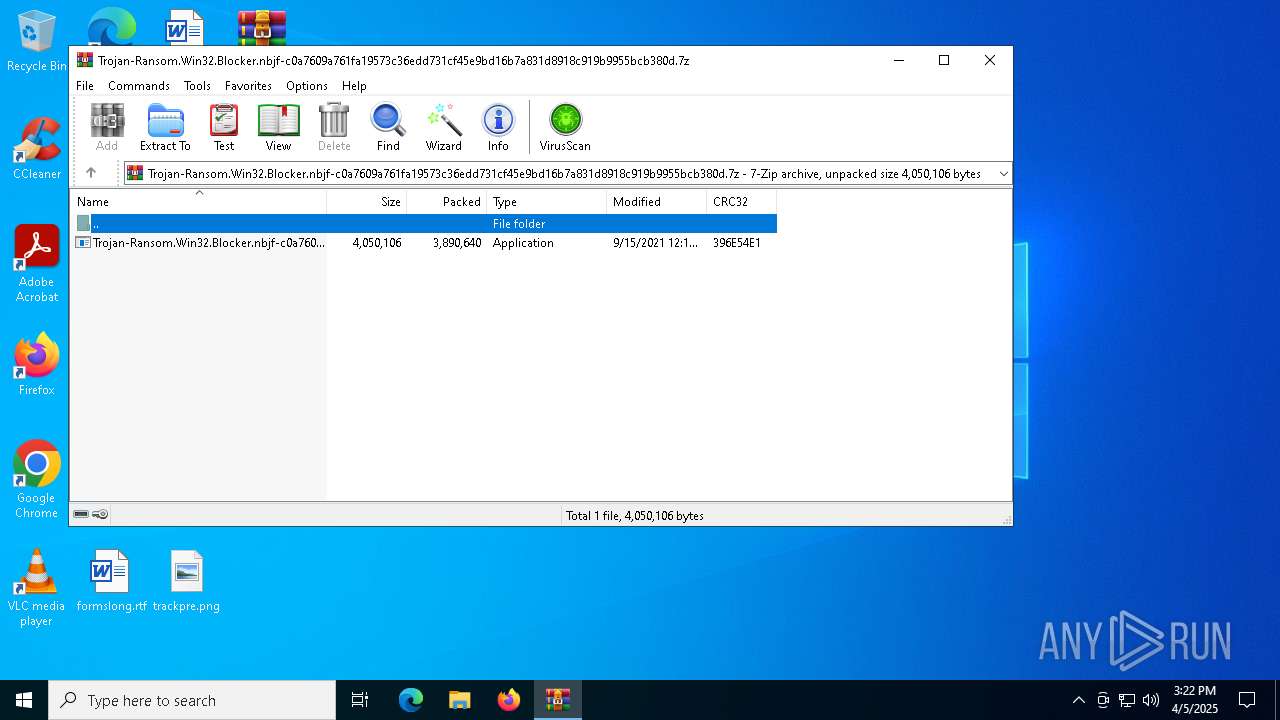
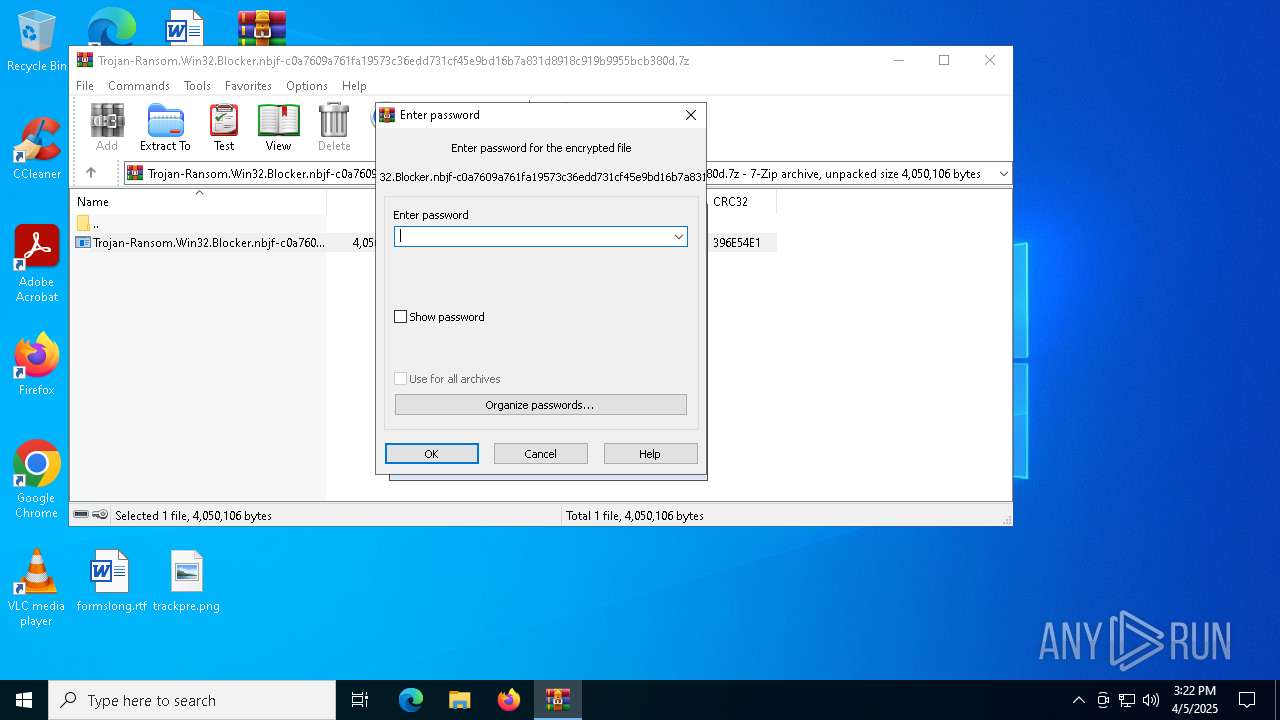
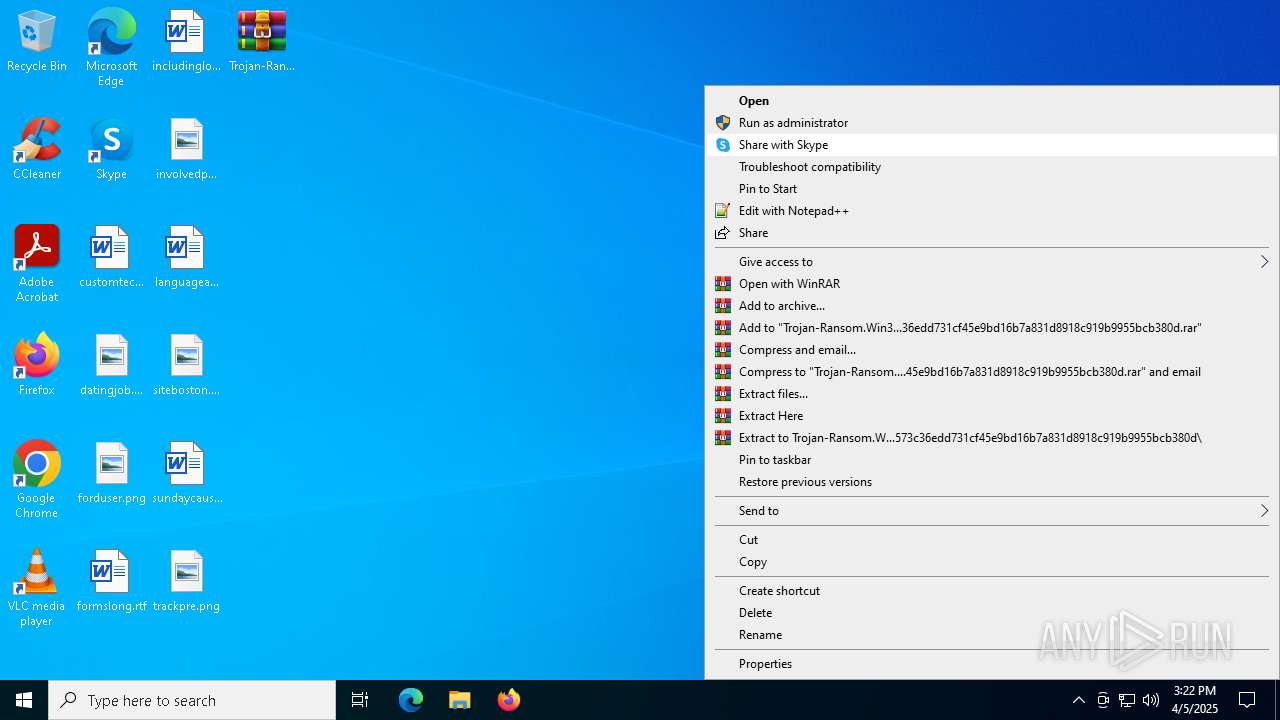
| File name: | Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.7z |
| Full analysis: | https://app.any.run/tasks/13b786b0-f5f5-4b41-b62d-4e630b735d87 |
| Verdict: | Malicious activity |
| Analysis date: | April 05, 2025, 15:22:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 7771E7F443172F804B9CCC12BB38721D |
| SHA1: | 5AEF7024085385CE846B517F33A651FBF86B6956 |
| SHA256: | 2B9F2A27B0887D19E7CE637E0E3B3DD4565BCA337317169A76C362B221F12468 |
| SSDEEP: | 98304:2CWOYNBQTNyR8TNO1ZEYAyoE9ZxRuDlbX9ouw1mwuq8zEK9zzBjTOA2T+by18XC2:wCfkBUMqu6 |
MALICIOUS
Gets %appdata% folder path (SCRIPT)
- wscript.exe (PID: 8184)
Reads the value of a key from the registry (SCRIPT)
- wscript.exe (PID: 8184)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- wscript.exe (PID: 8184)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 8184)
Modifies registry startup key (SCRIPT)
- wscript.exe (PID: 8184)
Uses Task Scheduler to run other applications
- wscript.exe (PID: 8184)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 8184)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 8184)
Gets username (SCRIPT)
- wscript.exe (PID: 8184)
Accesses information about the status of the installed antivirus(Win32_AntivirusProduct) via WMI (SCRIPT)
- wscript.exe (PID: 8184)
Gets %windir% folder path (SCRIPT)
- wscript.exe (PID: 8184)
Create files in the Startup directory
- wscript.exe (PID: 8184)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 8184)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 8184)
Changes the autorun value in the registry
- USBSafelyRemove.exe (PID: 1628)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 8184)
SUSPICIOUS
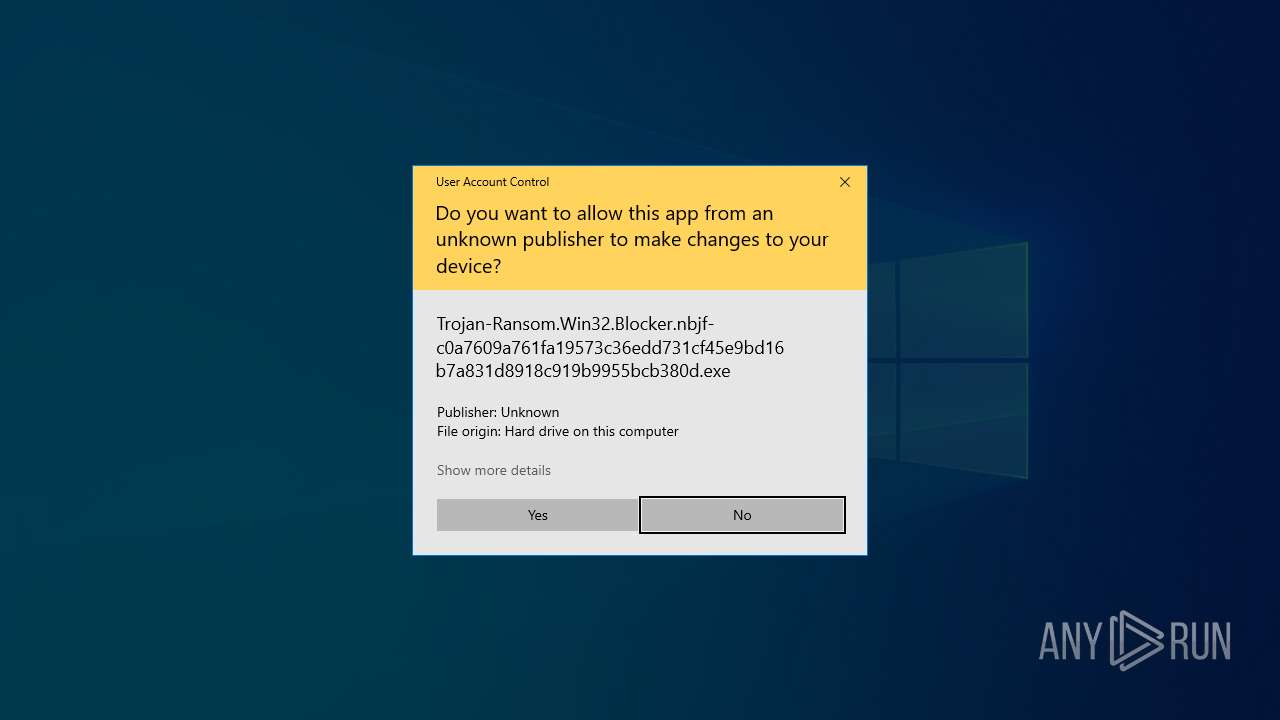
Executable content was dropped or overwritten
- Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe (PID: 8100)
- setup.exe (PID: 5576)
Reads security settings of Internet Explorer
- Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe (PID: 8100)
The process executes JS scripts
- Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe (PID: 8100)
Gets name of the script (SCRIPT)
- wscript.exe (PID: 8184)
Runs shell command (SCRIPT)
- wscript.exe (PID: 8184)
The process creates files with name similar to system file names
- setup.exe (PID: 5576)
Malware-specific behavior (creating "System.dll" in Temp)
- setup.exe (PID: 5576)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 8184)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 8184)
Accesses operating system name via WMI (SCRIPT)
- wscript.exe (PID: 8184)
Accesses current user name via WMI (SCRIPT)
- wscript.exe (PID: 8184)
Accesses computer name via WMI (SCRIPT)
- wscript.exe (PID: 8184)
Accesses WMI object caption (SCRIPT)
- wscript.exe (PID: 8184)
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 8184)
Accesses antivirus product name via WMI (SCRIPT)
- wscript.exe (PID: 8184)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 8184)
Accesses WMI object display name (SCRIPT)
- wscript.exe (PID: 8184)
Creates a Folder object (SCRIPT)
- wscript.exe (PID: 8184)
Gets computer name (SCRIPT)
- wscript.exe (PID: 8184)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 8184)
Drops a system driver (possible attempt to evade defenses)
- setup.exe (PID: 5576)
Executes as Windows Service
- USBSRService.exe (PID: 5404)
Creates a software uninstall entry
- setup.exe (PID: 5576)
There is functionality for taking screenshot (YARA)
- setup.exe (PID: 5576)
Connects to unusual port
- wscript.exe (PID: 8184)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7332)
The sample compiled with russian language support
- WinRAR.exe (PID: 7332)
- Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe (PID: 8100)
- setup.exe (PID: 5576)
Checks supported languages
- Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe (PID: 8100)
- setup.exe (PID: 5576)
- USBSRService.exe (PID: 780)
- USBSRService.exe (PID: 5404)
- USBSafelyRemove.exe (PID: 1628)
Manual execution by a user
- Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe (PID: 8100)
- USBSafelyRemove.exe (PID: 1628)
Reads the computer name
- Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe (PID: 8100)
- setup.exe (PID: 5576)
- USBSRService.exe (PID: 780)
- USBSRService.exe (PID: 5404)
- USBSafelyRemove.exe (PID: 1628)
Create files in a temporary directory
- Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe (PID: 8100)
- setup.exe (PID: 5576)
Process checks computer location settings
- Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe (PID: 8100)
The sample compiled with english language support
- setup.exe (PID: 5576)
Creates files in the program directory
- USBSRService.exe (PID: 780)
- setup.exe (PID: 5576)
Creates files or folders in the user directory
- setup.exe (PID: 5576)
- USBSafelyRemove.exe (PID: 1628)
Checks proxy server information
- wscript.exe (PID: 8184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2021:09:15 12:18:02+00:00 |
| ArchivedFileName: | Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe |
Total processes
141
Monitored processes
12
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 780 | "C:\Program Files (x86)\USB Safely Remove\USBSRService.exe" /install /silent | C:\Program Files (x86)\USB Safely Remove\USBSRService.exe | — | setup.exe | |||||||||||
User: admin Company: Crystal Rich Ltd Integrity Level: HIGH Description: USB Safely Remove assistant service Exit code: 0 Version: 6.4.2.1297 Modules
| |||||||||||||||
| 1628 | "C:\Program Files (x86)\USB Safely Remove\USBSafelyRemove.exe" | C:\Program Files (x86)\USB Safely Remove\USBSafelyRemove.exe | explorer.exe | ||||||||||||
User: admin Company: Crystal Rich Ltd Integrity Level: MEDIUM Description: USB Safely Remove Version: 6.4.2.1297 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5404 | "C:\Program Files (x86)\USB Safely Remove\USBSRService.exe" | C:\Program Files (x86)\USB Safely Remove\USBSRService.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Crystal Rich Ltd Integrity Level: SYSTEM Description: USB Safely Remove assistant service Version: 6.4.2.1297 Modules
| |||||||||||||||
| 5576 | "C:\Users\admin\AppData\Local\Temp\setup.exe" | C:\Users\admin\AppData\Local\Temp\setup.exe | Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe | ||||||||||||
User: admin Company: diakov.net Integrity Level: HIGH Description: USB Safely Remove 6.4.2.1297 Final Exit code: 0 Version: 6.4.2.1297 Modules
| |||||||||||||||
| 7228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7240 | "C:\Windows\System32\schtasks.exe" /create /sc minute /mo 30 /tn anydesk /tr "C:\Users\admin\AppData\Roaming\info.js | C:\Windows\SysWOW64\schtasks.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7332 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7452 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7484 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 141
Read events
4 081
Write events
59
Delete events
1
Modification events
| (PID) Process: | (7332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.7z | |||
| (PID) Process: | (7332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
13
Suspicious files
6
Text files
261
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5576 | setup.exe | C:\Users\admin\AppData\Local\Temp\nssE468.tmp\LangDLL.dll | executable | |
MD5:D6D8ADDFEA0EE1BBA9B841E3BEC0B5CD | SHA256:CCB76172C2565356A838D7867A51E021478FED4D83EB41FE1DBB703F8EFA28F9 | |||
| 7332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7332.37143\Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe | executable | |
MD5:252F829DCB9C1525934FE45286BD2957 | SHA256:C0A7609A761FA19573C36EDD731CF45E9BD16B7A831D8918C919B9955BCB380D | |||
| 8100 | Trojan-Ransom.Win32.Blocker.nbjf-c0a7609a761fa19573c36edd731cf45e9bd16b7a831d8918c919b9955bcb380d.exe | C:\Users\admin\AppData\Local\Temp\info.js | binary | |
MD5:C7CBC0FA19952860D891AD4E274696E3 | SHA256:C9DB1D188F95F8E4FFBEF289DC241D8BDD48CA7C6381F461D4D1A072538A53D2 | |||
| 5576 | setup.exe | C:\Users\admin\AppData\Local\Temp\nssE468.tmp\ukr-r.bmp | image | |
MD5:845319EA5DAF12BFCB59AC25EF606B71 | SHA256:AD73B701FFF2948E4502B8AC7CF8F4849CE36010A3BD8DAFFBD21E79B78EB811 | |||
| 5576 | setup.exe | C:\Users\admin\AppData\Local\Temp\nssE468.tmp\modern-wizard.bmp | image | |
MD5:88C6A918801418C462B1559DC105FC70 | SHA256:76C5D0CCE0661F4C94D031F3C224D573FEB1F1C3A28CABBB0A46806F4B3E85C9 | |||
| 5576 | setup.exe | C:\Users\admin\AppData\Local\Temp\nssE468.tmp\Aero.dll | executable | |
MD5:5155E506B908B41E113BBD7C10D4082F | SHA256:9BBBDD180DAC3CF4CE36CBC12BD862CDD00880D87027395F92EDE5476D1F0DD0 | |||
| 5576 | setup.exe | C:\Users\admin\AppData\Local\Temp\nssE468.tmp\BrandingURL.dll | executable | |
MD5:71C46B663BAA92AD941388D082AF97E7 | SHA256:BB2B9C272B8B66BC1B414675C2ACBA7AFAD03FFF66A63BABEE3EE57ED163D19E | |||
| 5576 | setup.exe | C:\Users\admin\AppData\Local\Temp\nssE468.tmp\rus-r.bmp | image | |
MD5:963E7FD0F5CCACA35D130E283761B514 | SHA256:951B7C09D2AD5031B37EBC09298EDB197DDF924DFA2C935EC2361C7E658650C0 | |||
| 8184 | wscript.exe | C:\Users\admin\AppData\Roaming\info.js | binary | |
MD5:C7CBC0FA19952860D891AD4E274696E3 | SHA256:C9DB1D188F95F8E4FFBEF289DC241D8BDD48CA7C6381F461D4D1A072538A53D2 | |||
| 8184 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\info.js | binary | |
MD5:C7CBC0FA19952860D891AD4E274696E3 | SHA256:C9DB1D188F95F8E4FFBEF289DC241D8BDD48CA7C6381F461D4D1A072538A53D2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
20
DNS requests
14
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1812 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1812 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 20.10.31.115:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
8184 | wscript.exe | 195.201.238.116:8082 | utcsvc.linkpc.net | Hetzner Online GmbH | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
utcsvc.linkpc.net |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS Observed DNS Query to DynDNS Domain (linkpc .net) |