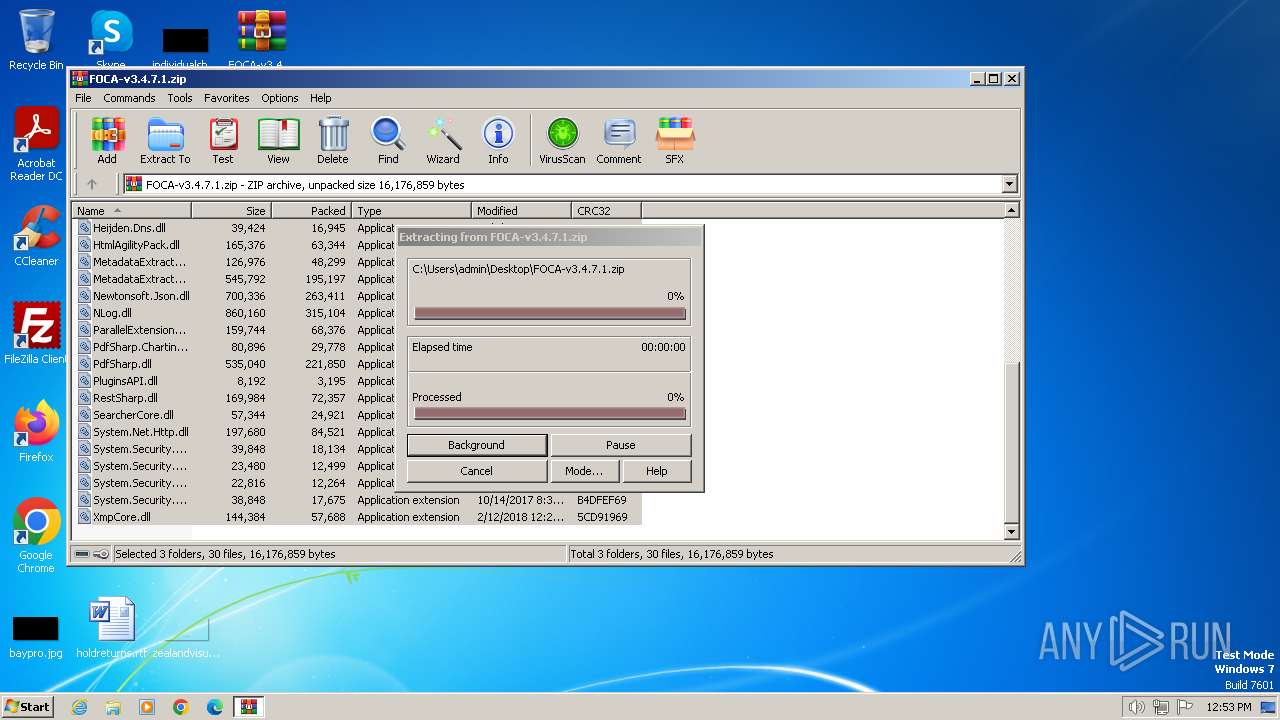
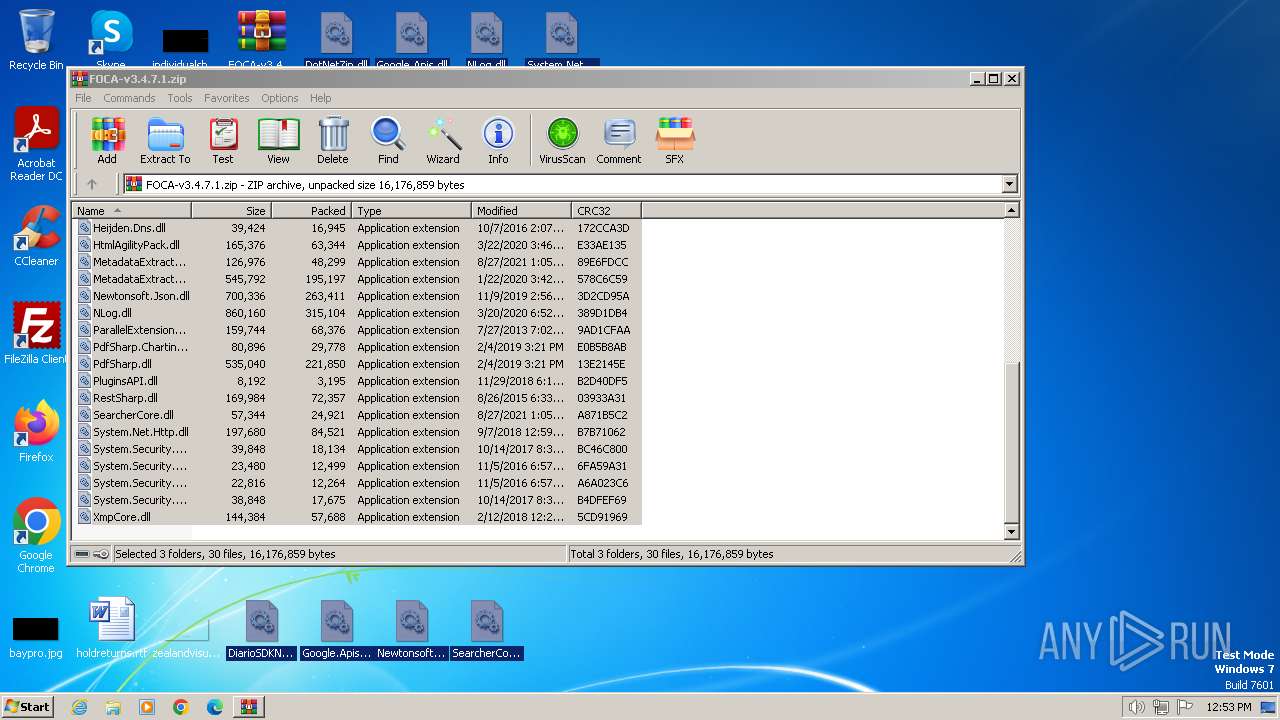
| File name: | FOCA-v3.4.7.1.zip |
| Full analysis: | https://app.any.run/tasks/59e6b3da-878b-41a4-98cf-c39e26d87b54 |
| Verdict: | Malicious activity |
| Analysis date: | January 08, 2024, 12:53:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 22E6D94D033016C0A98832EBC6480A1B |
| SHA1: | 32C437FE0C06D2E11F6B574B3CF72731289AFEE7 |
| SHA256: | 2B7F2CA60DC56245C0101BF171F13A1AE3E89AB93022A969011A08D06270E7FD |
| SSDEEP: | 98304:Tbt+/Y1nt2gIteDX5Xr82ziM7lDdtxlkEMl7RDrlEZkT8dN7ufXvIfK+BxNm0ohN:BxcWMF+o3v |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- FOCA.exe (PID: 1632)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 124)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 124)
Manual execution by a user
- FOCA.exe (PID: 1632)
- taskmgr.exe (PID: 1544)
Creates files in the program directory
- FOCA.exe (PID: 1632)
Reads the computer name
- FOCA.exe (PID: 1632)
Connects to unusual port
- FOCA.exe (PID: 1632)
Process drops legitimate windows executable
- WinRAR.exe (PID: 124)
Checks supported languages
- FOCA.exe (PID: 1632)
Reads the machine GUID from the registry
- FOCA.exe (PID: 1632)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:02:20 12:36:06 |
| ZipCRC: | 0x5d948e30 |
| ZipCompressedSize: | 7880 |
| ZipUncompressedSize: | 17408 |
| ZipFileName: | BaseSDK.dll |
Total processes
37
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\FOCA-v3.4.7.1.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1544 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1632 | "C:\Users\admin\Desktop\FOCA.exe" | C:\Users\admin\Desktop\FOCA.exe | explorer.exe | ||||||||||||
User: admin Company: elevenpaths Integrity Level: MEDIUM Description: FOCA (Open Source) Exit code: 0 Version: 3.4.7.1 Modules
| |||||||||||||||
Total events
1 305
Read events
1 277
Write events
28
Delete events
0
Modification events
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
41
Suspicious files
1
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.41910\BaseSDK.dll | executable | |
MD5:851DEE90865690896F6F1663DE15C071 | SHA256:A1E629EA93A69BAC2D7503076444D7DC9CDF4A8D98D223BC2C9E8DB1D7727A34 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.41910\FOCA.exe.config | xml | |
MD5:6C92329C05FCF57D272273807D5E63CD | SHA256:729FD10327A1EE98D0FF877FE2F6A6A20261CD81F7CBED7057DBCF8513173EBC | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.41910\EntityFramework.dll | executable | |
MD5:2354C79962BF18BD66C7C34F6104B02F | SHA256:ECF7EE2EFFCD6E91E792FA5658D58D85D69A19C9F7C06E533ECBDCC9F61A9A4C | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.41910\DiarioSDKNet.dll | executable | |
MD5:2156CF81A4D7F0F83807154B9D4DB88F | SHA256:9742747AF034A1E8DFD0BA897F9FBF6FF9BC217D27C609DFCF874068575DF6FF | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.41910\EntityFramework.SqlServer.dll | executable | |
MD5:1F16D47FACE0CD4A0B0335923FD5AB84 | SHA256:A82C08834CEEDA5B49F28E934687F71AF2300BDAD6DF5EB4A9DB51F6CFEEBE56 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.41910\FOCA.exe | executable | |
MD5:BDEAF3E240B199E642D16CD6C6535F90 | SHA256:1A1654F5F3B39A563BDCC5F17149C9514D075ABC25C18E637DA7C0DA92AA1523 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.41910\Google.Apis.dll | executable | |
MD5:5B2C23423508F76127887988EC4256DE | SHA256:E5AAF584571CBAB1BA1797A9B330F80B06326C4D36F251BF82405F96377A617A | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.41910\Google.Apis.Core.dll | executable | |
MD5:0605AA0C816BAB200FD43B8E2A9D837B | SHA256:7F50A9027F40A941831E47C716837FE4E9BFDA328E0D214F55CC7AB5AD07912E | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.41910\Google.Apis.Customsearch.v1.dll | executable | |
MD5:6B56E5A3CCA6473DA6807D1A54392E93 | SHA256:FEE3A2E3F33F28AC3729069AC3F10B979394997DEA56093040551581A205165E | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.41910\Google.Apis.PlatformServices.dll | executable | |
MD5:7C2DF27D09820B6E74EE7AADECAB447D | SHA256:B9E3BB1B3E14B2CA104B6D906464A7A4BE1A39D54B27CC1164C0BD8C5ED793B3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
13
DNS requests
5
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
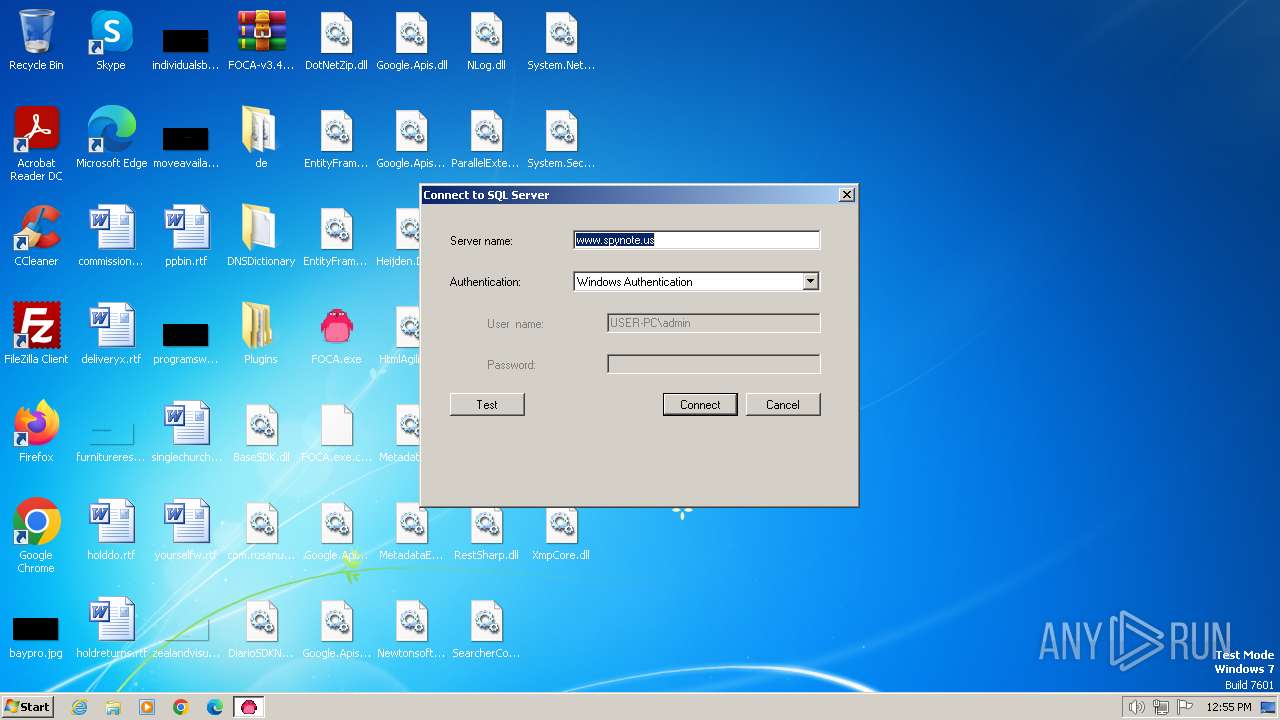
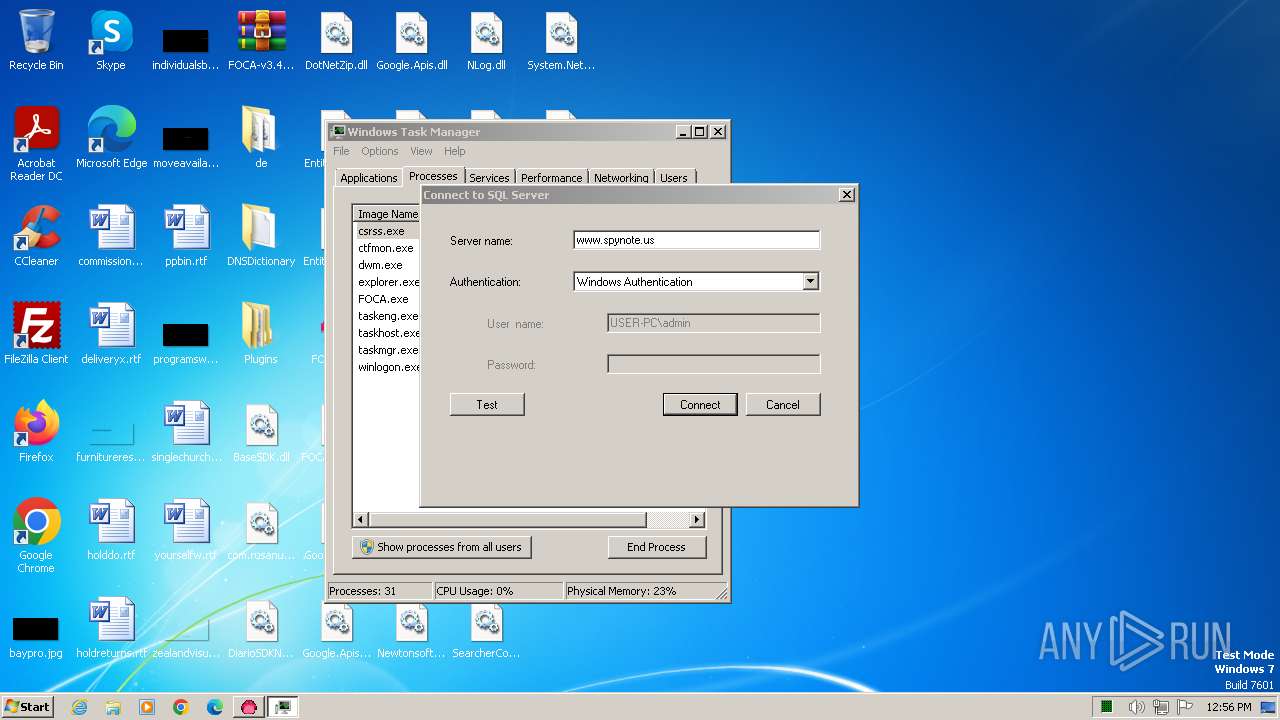
1632 | FOCA.exe | 188.114.97.3:1433 | www.spynote.us | CLOUDFLARENET | NL | unknown |
1632 | FOCA.exe | 188.114.96.3:1433 | www.spynote.us | CLOUDFLARENET | NL | unknown |
4 | System | 188.114.97.3:445 | www.spynote.us | CLOUDFLARENET | NL | unknown |
4 | System | 188.114.96.3:445 | www.spynote.us | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.spynote.us |
| malicious |
dns.msftncsi.com |
| shared |