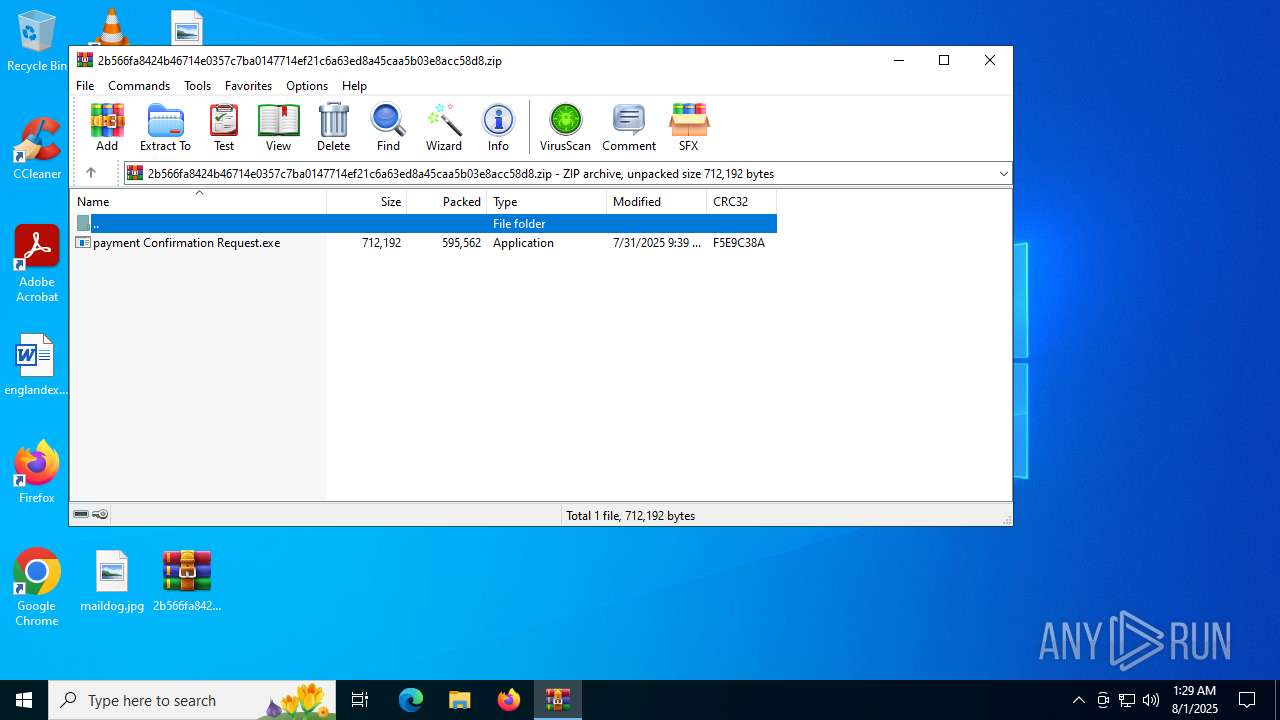
| File name: | 2b566fa8424b46714e0357c7ba0147714ef21c6a63ed8a45caa5b03e8acc58d8.zip |
| Full analysis: | https://app.any.run/tasks/b7b98ff0-fdc8-4e05-aaef-e79f20719a98 |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2025, 01:29:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | ACECB43C815DD85C7B55AEEA608F16D3 |
| SHA1: | DDF0228C25AB9EE888A3801F4848C3C205FC22A6 |
| SHA256: | 2B566FA8424B46714E0357C7BA0147714EF21C6A63ED8A45CAA5B03E8ACC58D8 |
| SSDEEP: | 24576:3sFPyBhBPgxJujbhZZD7oZyBMj+0I7Y/RJ97UHDgtpInS:3sFPmhBPgxJujbhZZD7oZyKj+0I7Y/fP |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6508)
Uses Task Scheduler to run other applications
- payment Confirmation Request.exe (PID: 6488)
SNAKE has been detected (YARA)
- RegSvcs.exe (PID: 7124)
SUSPICIOUS
Reads security settings of Internet Explorer
- payment Confirmation Request.exe (PID: 6488)
- WinRAR.exe (PID: 6508)
Executes application which crashes
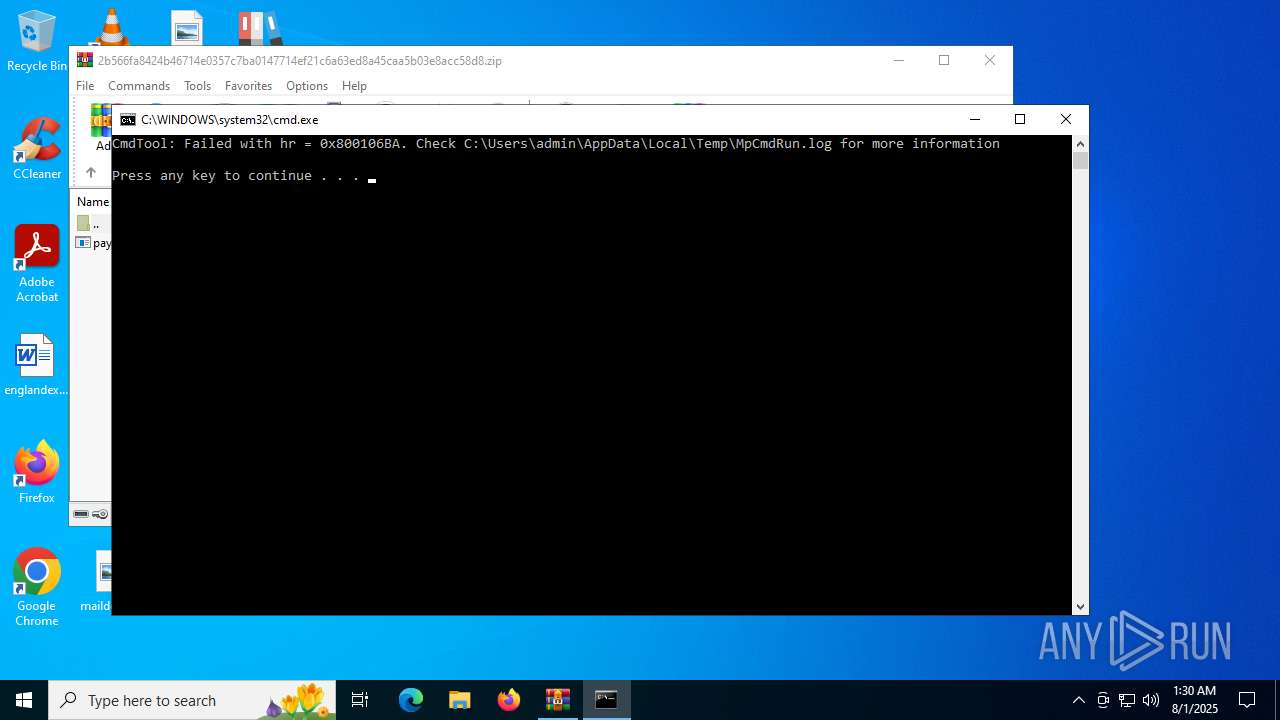
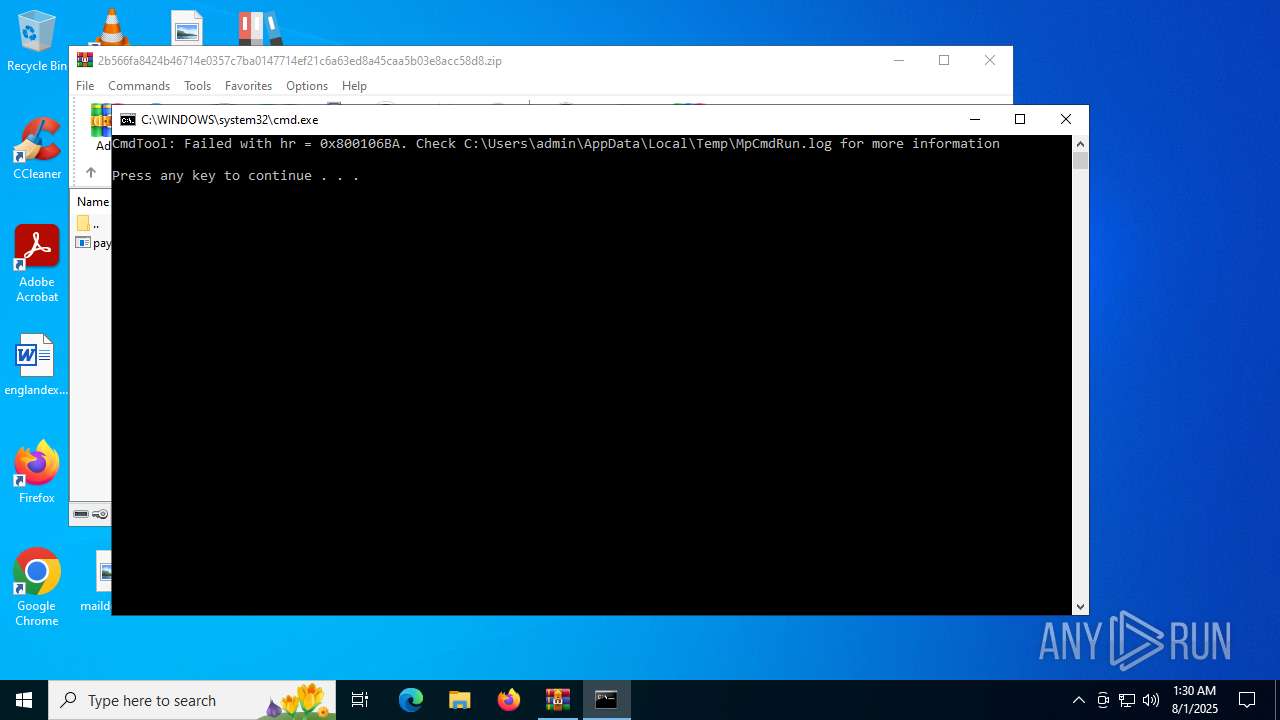
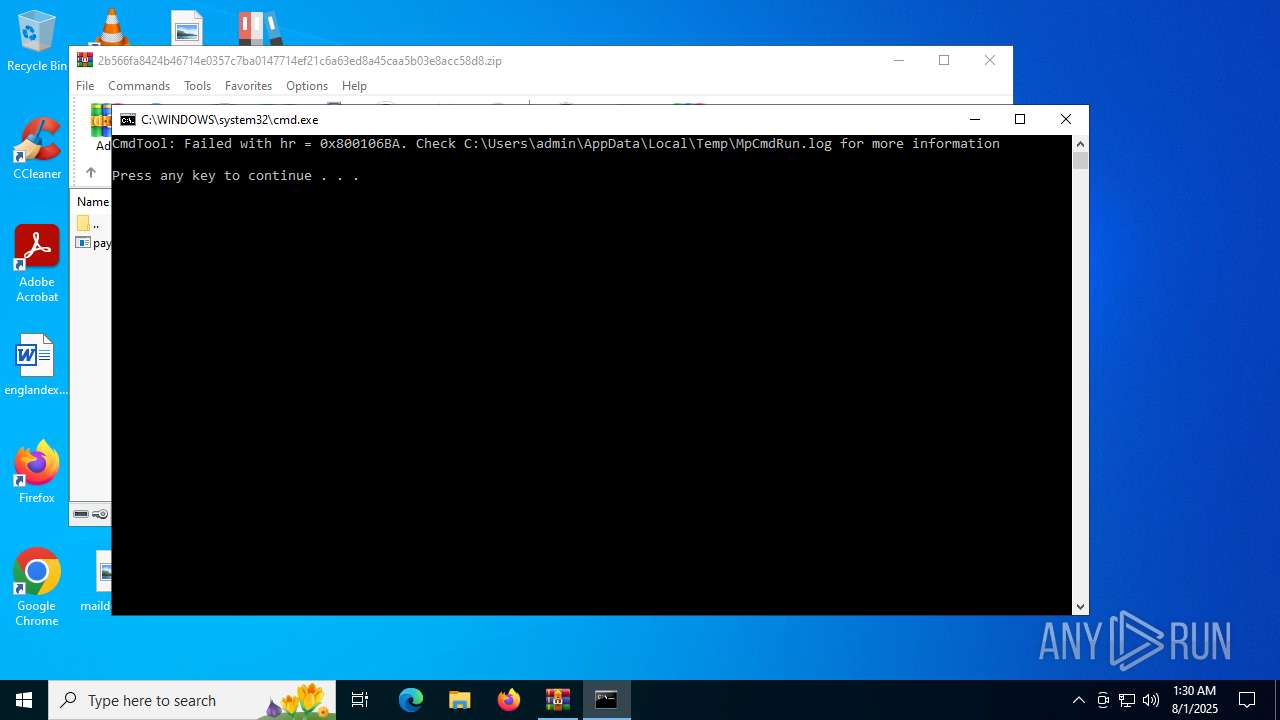
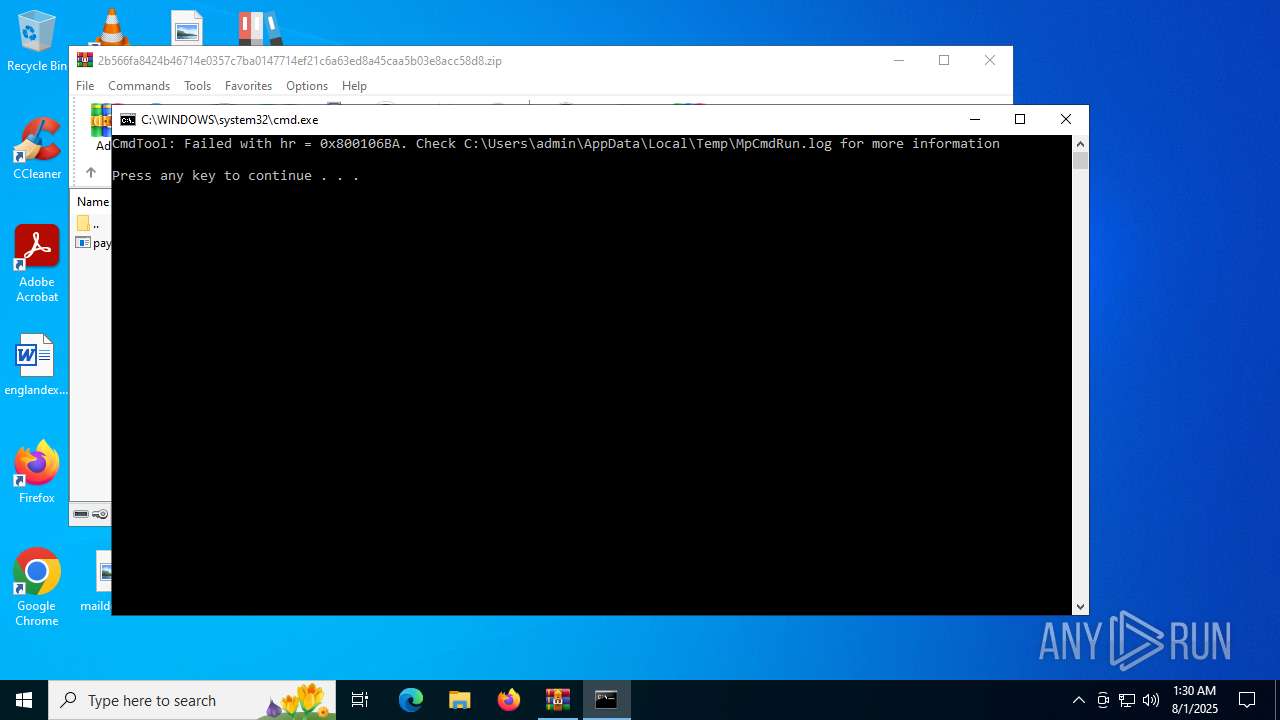
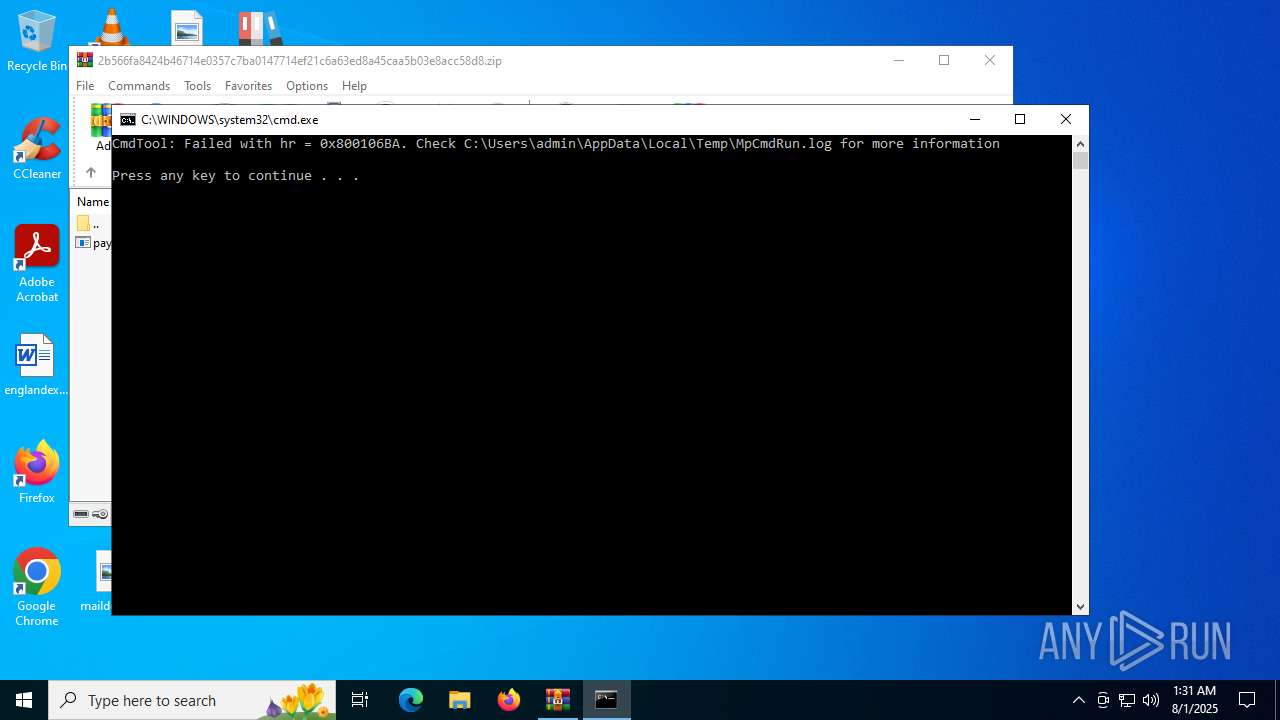
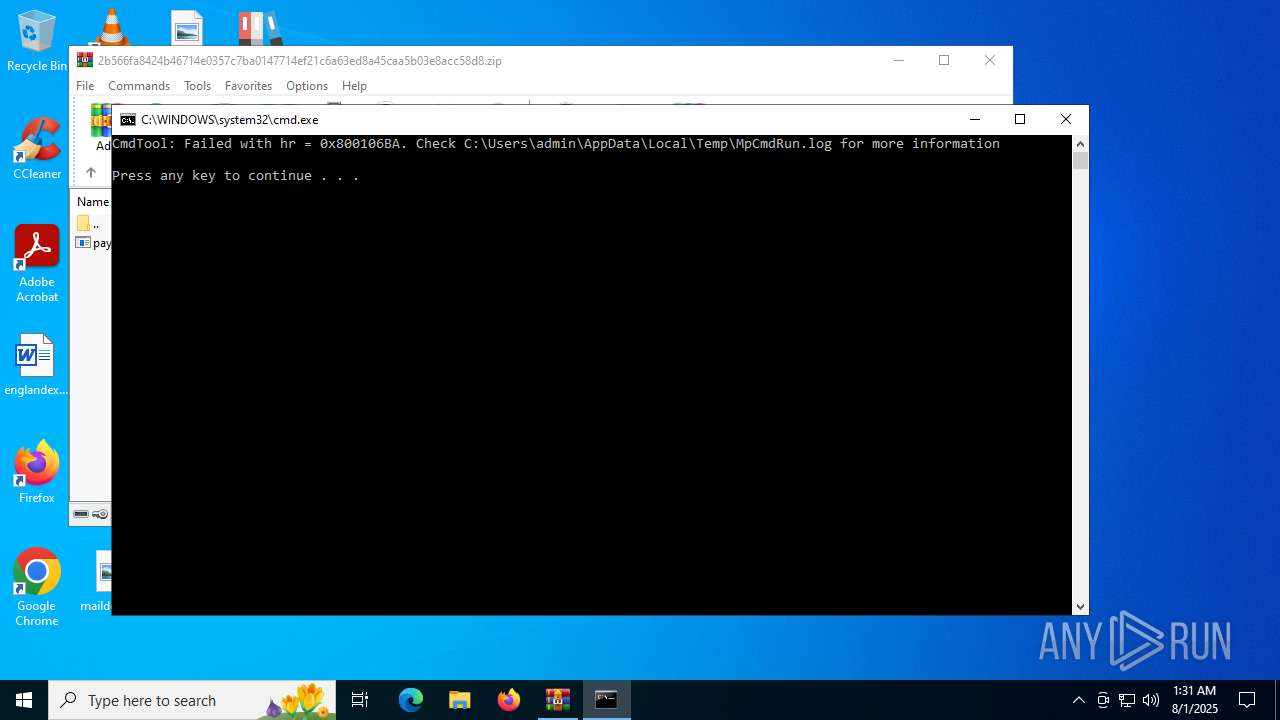
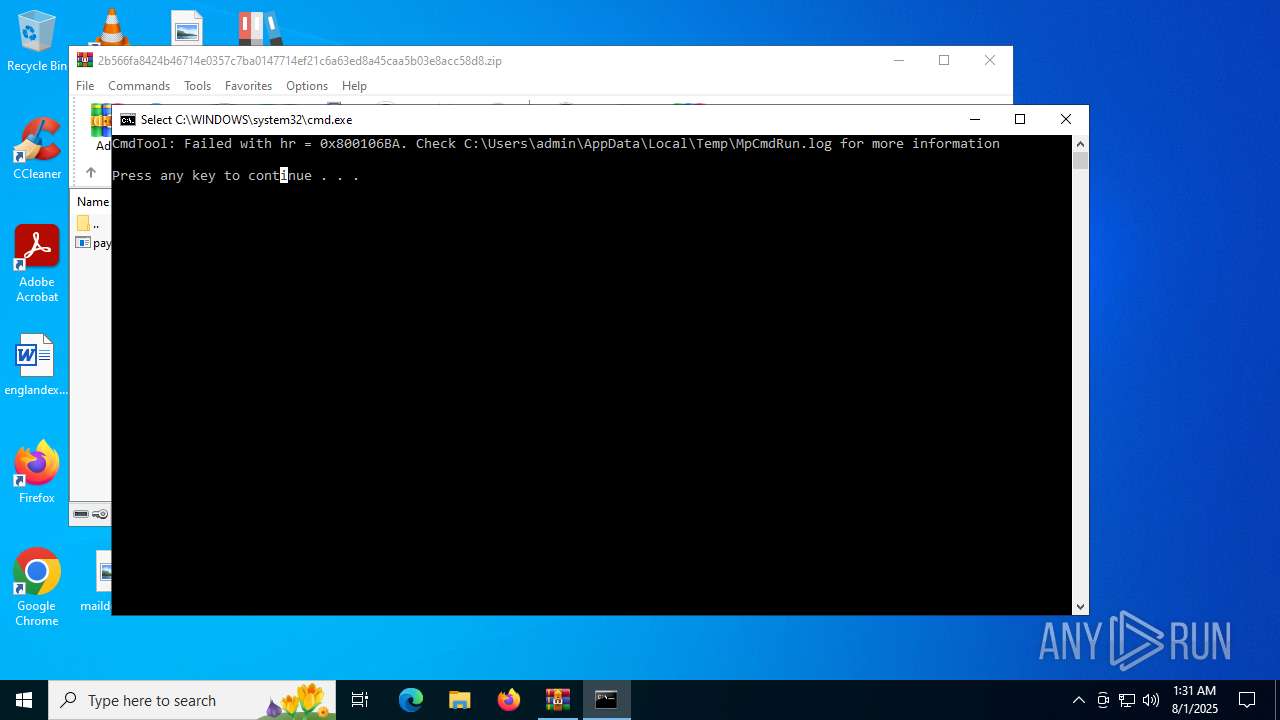
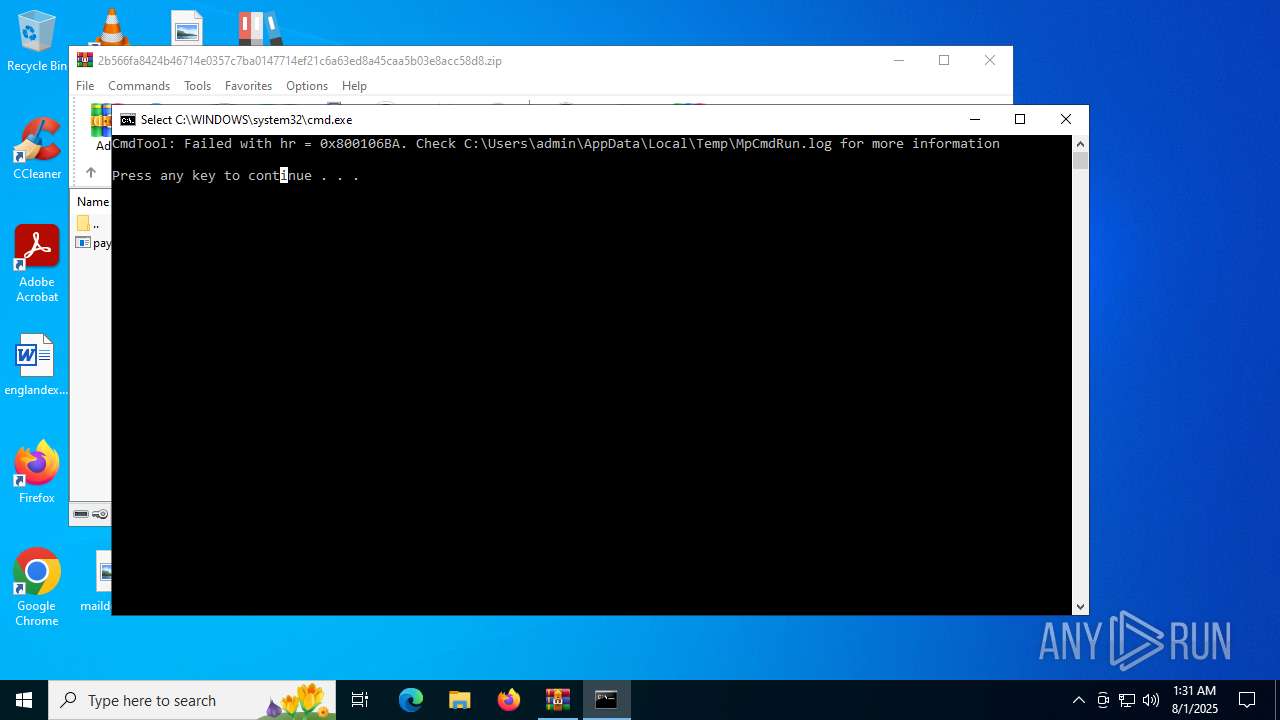
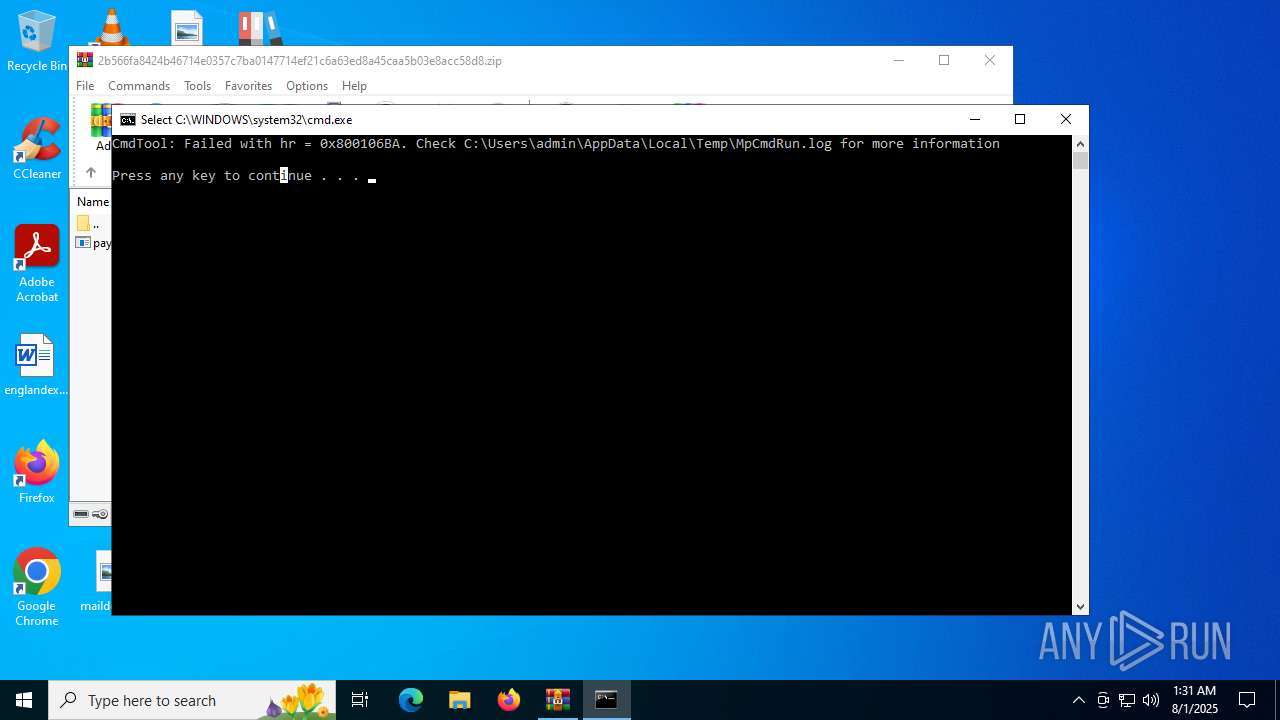
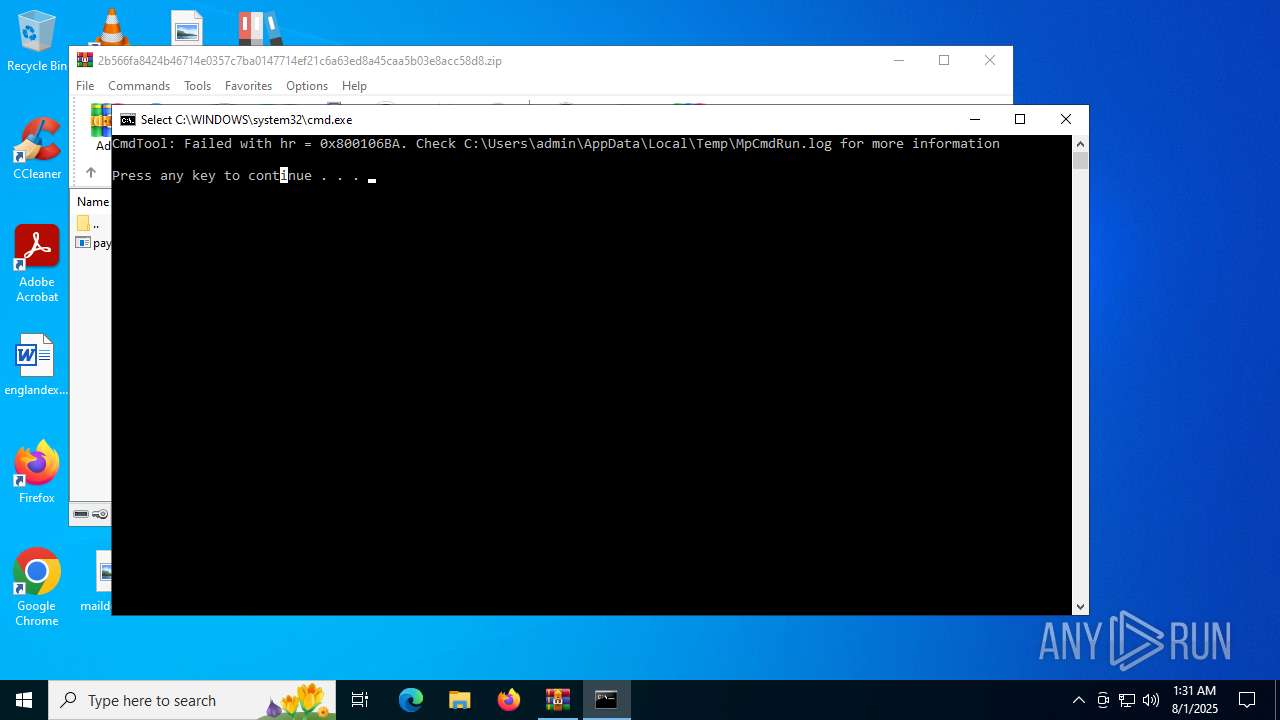
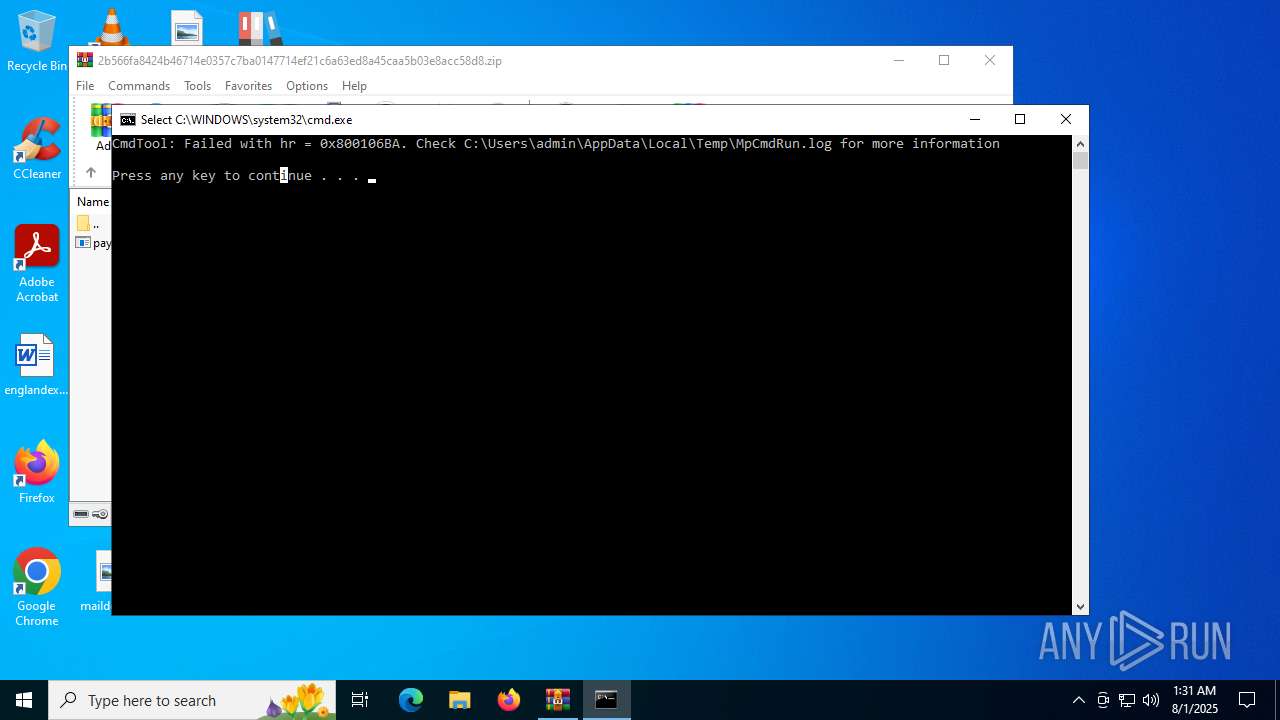
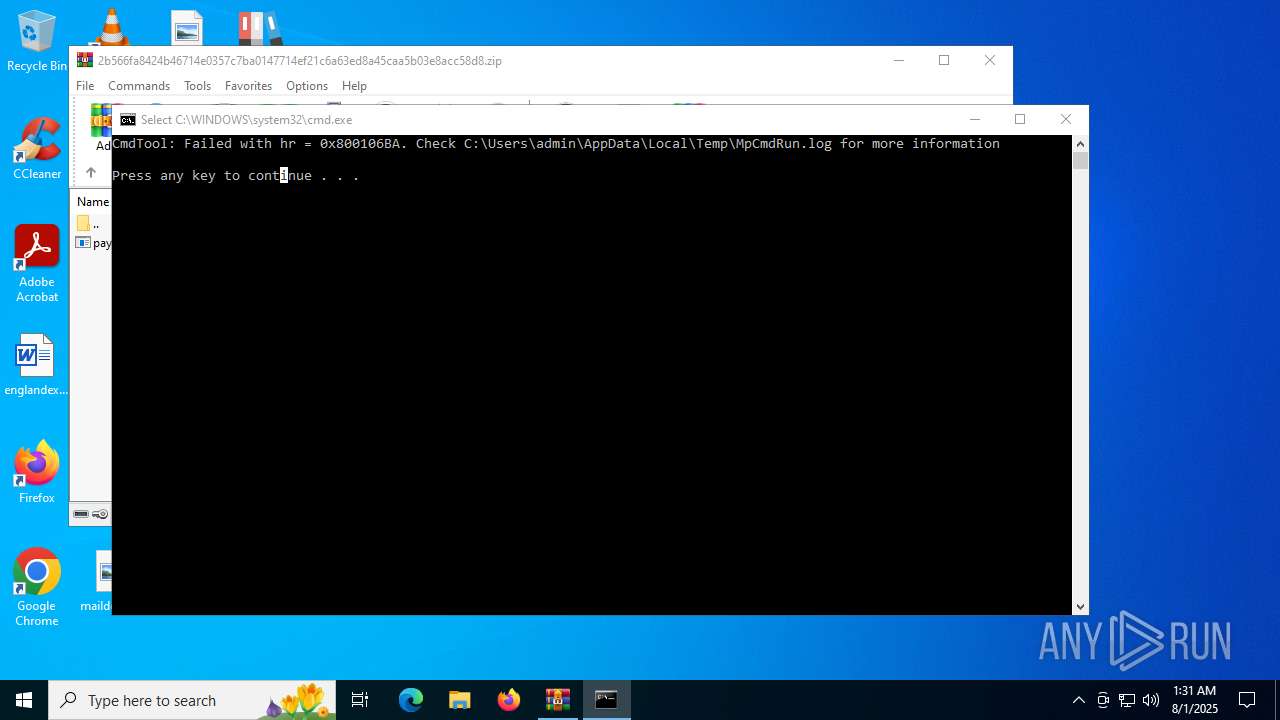
- RegSvcs.exe (PID: 7124)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6508)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6508)
Executable content was dropped or overwritten
- payment Confirmation Request.exe (PID: 6488)
INFO
Process checks computer location settings
- payment Confirmation Request.exe (PID: 6488)
Manual execution by a user
- payment Confirmation Request.exe (PID: 6488)
- djnmKTAabuPDpa.exe (PID: 4864)
Reads the computer name
- payment Confirmation Request.exe (PID: 6488)
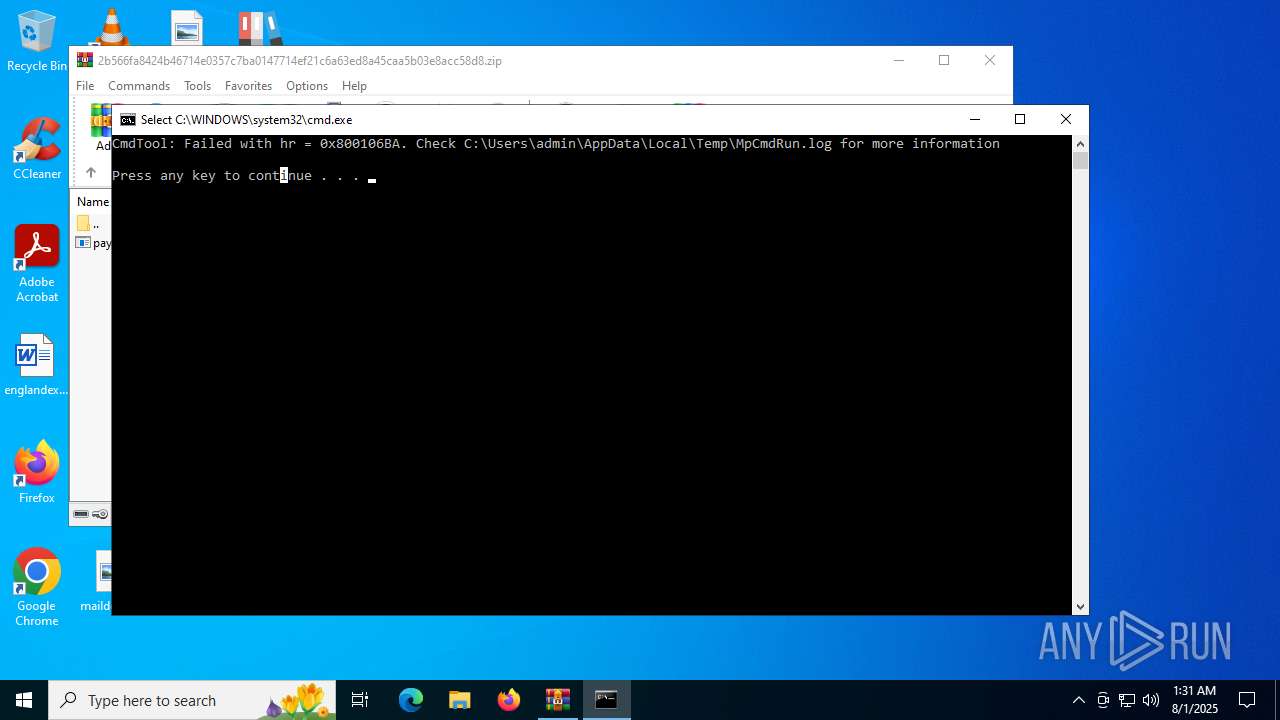
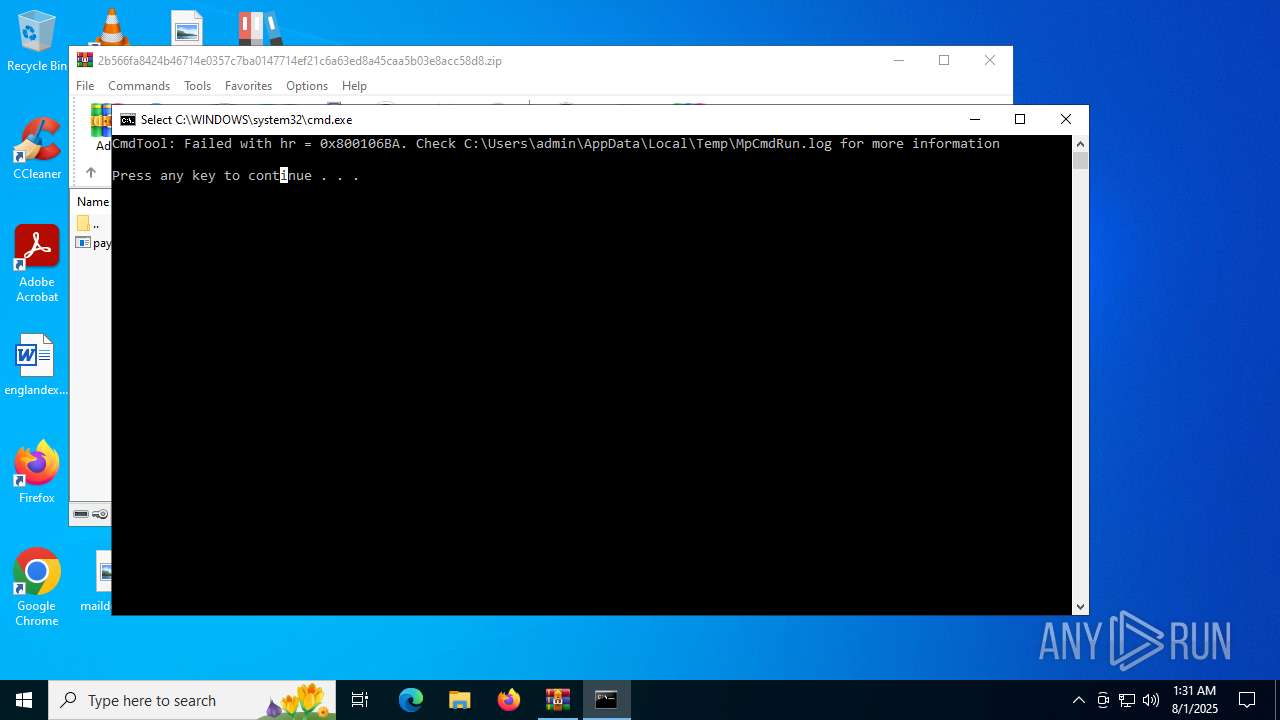
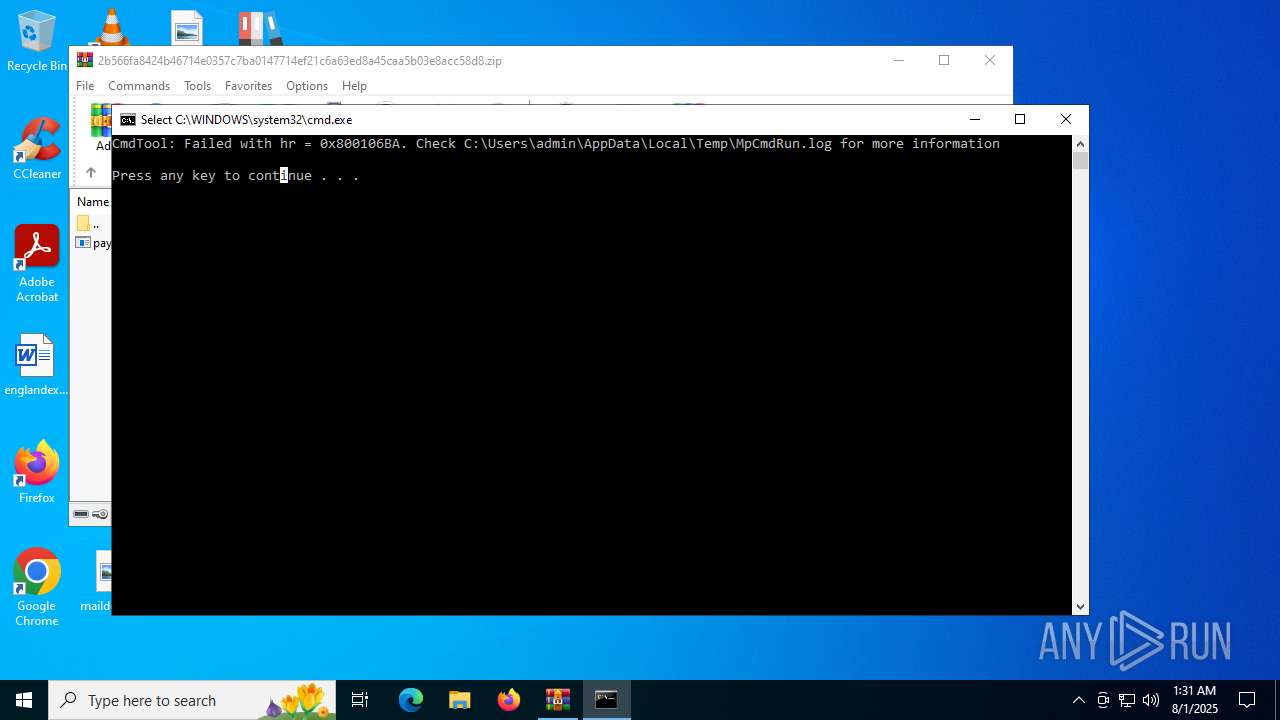
- MpCmdRun.exe (PID: 5928)
- RegSvcs.exe (PID: 7124)
- djnmKTAabuPDpa.exe (PID: 4864)
Checks supported languages
- payment Confirmation Request.exe (PID: 6488)
- RegSvcs.exe (PID: 7124)
- djnmKTAabuPDpa.exe (PID: 4864)
- MpCmdRun.exe (PID: 5928)
Reads the machine GUID from the registry
- payment Confirmation Request.exe (PID: 6488)
- RegSvcs.exe (PID: 7124)
- djnmKTAabuPDpa.exe (PID: 4864)
Disables trace logs
- RegSvcs.exe (PID: 7124)
Checks proxy server information
- RegSvcs.exe (PID: 7124)
- WerFault.exe (PID: 1132)
- slui.exe (PID: 684)
Reads the software policy settings
- RegSvcs.exe (PID: 7124)
- WerFault.exe (PID: 1132)
- slui.exe (PID: 684)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6508)
Creates files or folders in the user directory
- WerFault.exe (PID: 1132)
- payment Confirmation Request.exe (PID: 6488)
Create files in a temporary directory
- MpCmdRun.exe (PID: 5928)
- payment Confirmation Request.exe (PID: 6488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
SnakeKeylogger
(PID) Process(7124) RegSvcs.exe
Keys
DES6fc98cd68a1aab8b
Options
Telegram Bot Token7811075287:AAEsR_gg1PtwDdagycf03iL8s4jWtgyn-Hs
Telegram Chat ID6244366695
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:07:31 21:39:30 |
| ZipCRC: | 0xf5e9c38a |
| ZipCompressedSize: | 595562 |
| ZipUncompressedSize: | 712192 |
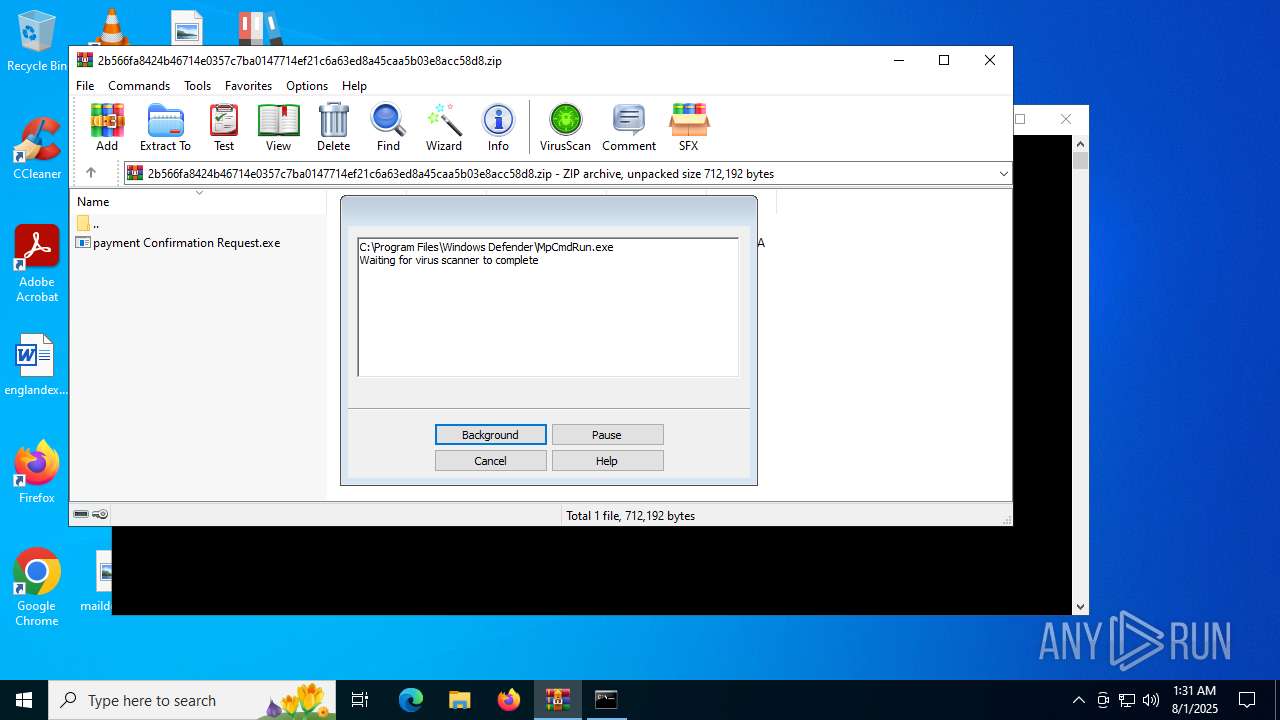
| ZipFileName: | payment Confirmation Request.exe |
Total processes
147
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR6508.15266\Rar$Scan61574.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7124 -s 2384 | C:\Windows\SysWOW64\WerFault.exe | RegSvcs.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1380 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\djnmKTAabuPDpa" /XML "C:\Users\admin\AppData\Local\Temp\tmp4C22.tmp" | C:\Windows\SysWOW64\schtasks.exe | — | payment Confirmation Request.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4864 | "C:\Users\admin\AppData\Roaming\djnmKTAabuPDpa.exe" | C:\Users\admin\AppData\Roaming\djnmKTAabuPDpa.exe | — | explorer.exe | |||||||||||
User: admin Company: BookFlow1 Integrity Level: MEDIUM Description: BookFlow Library Version: 0.0.0.0 Modules
| |||||||||||||||
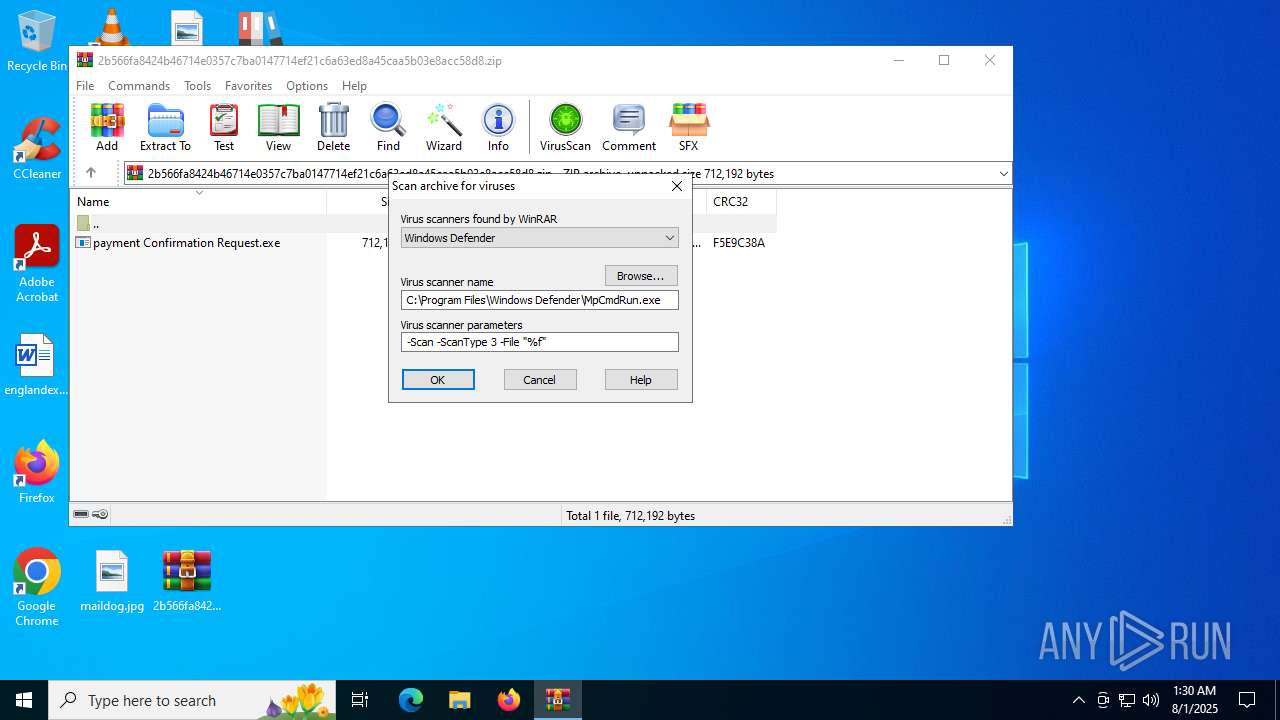
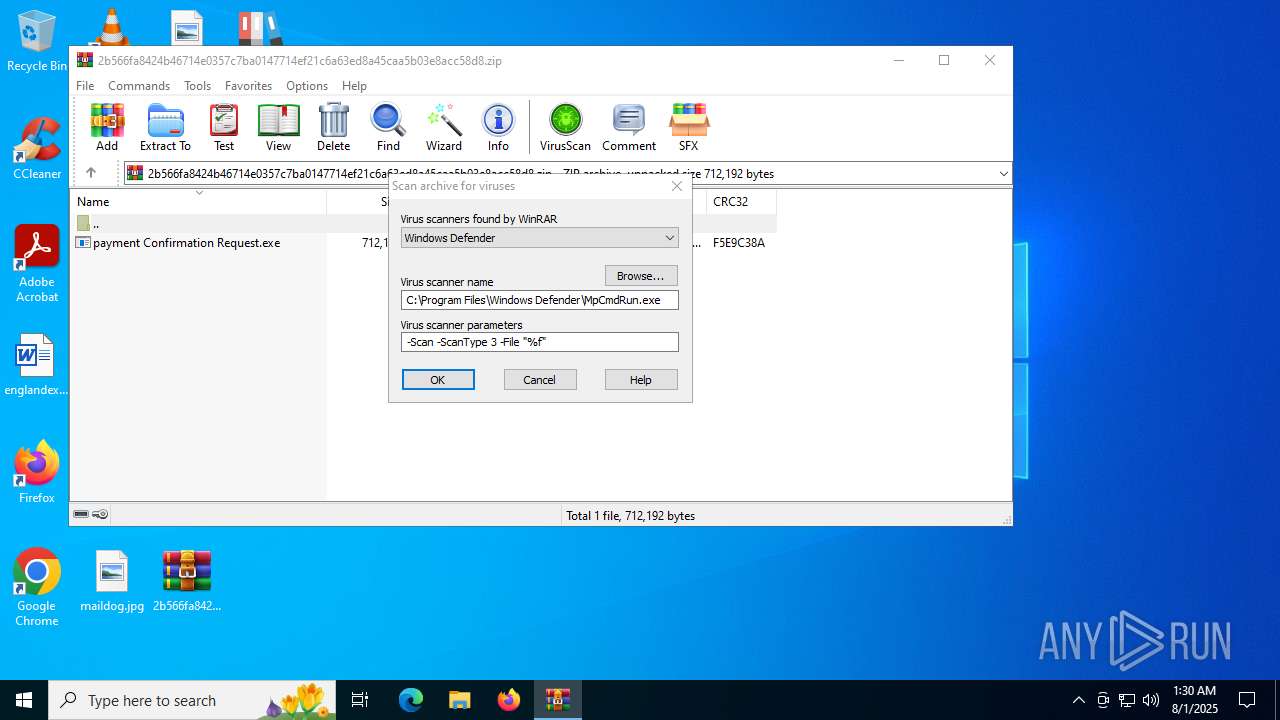
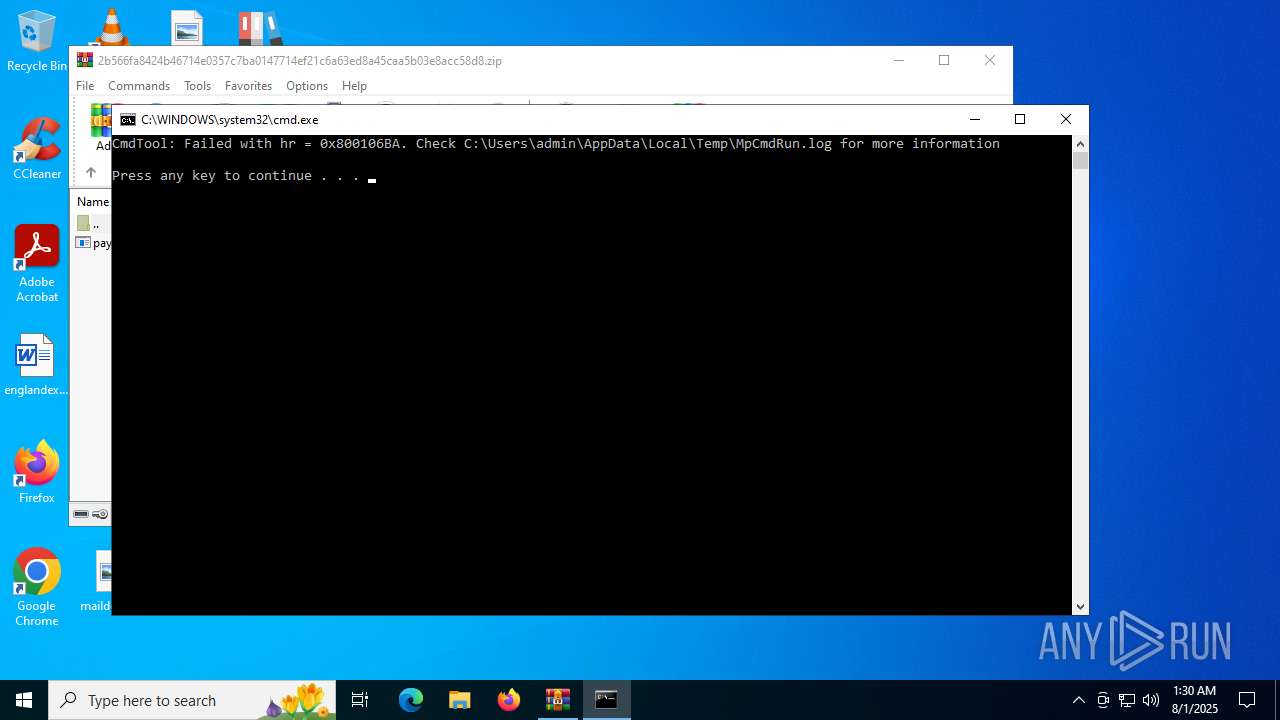
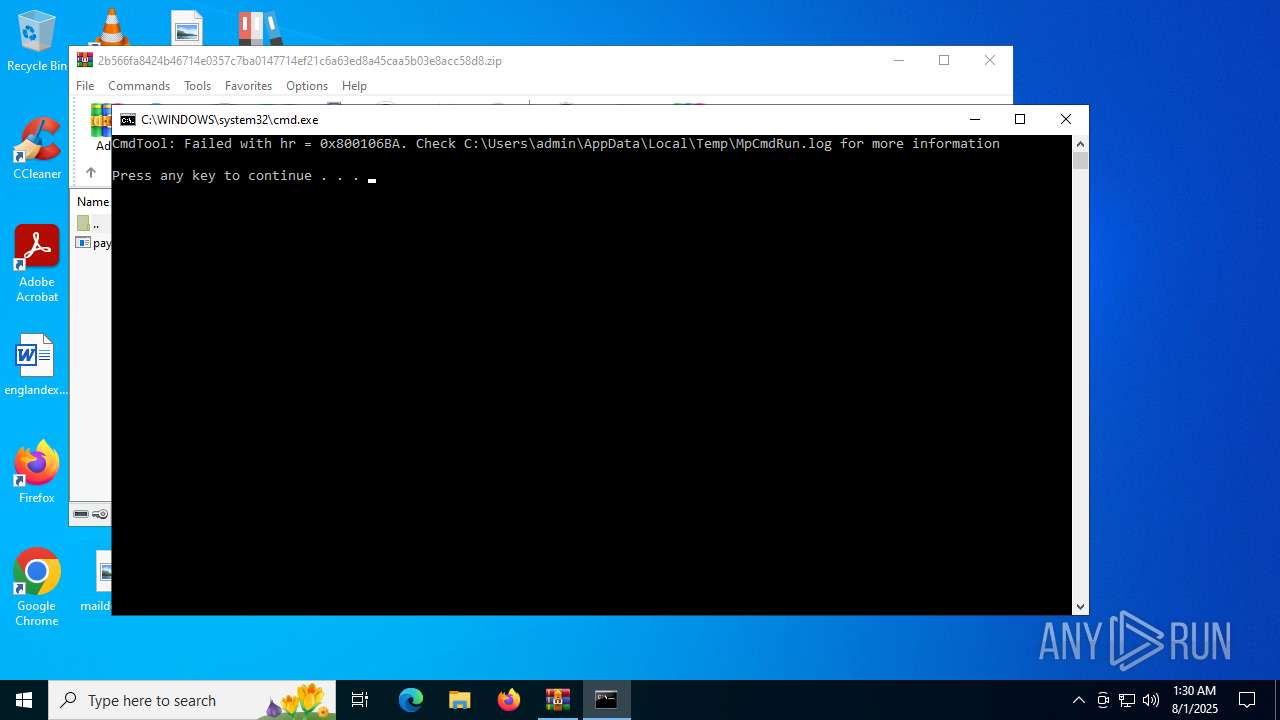
| 5928 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR6508.15266" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6488 | "C:\Users\admin\Desktop\payment Confirmation Request.exe" | C:\Users\admin\Desktop\payment Confirmation Request.exe | explorer.exe | ||||||||||||
User: admin Company: BookFlow1 Integrity Level: MEDIUM Description: BookFlow Library Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
17 766
Read events
17 740
Write events
26
Delete events
0
Modification events
| (PID) Process: | (6508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\2b566fa8424b46714e0357c7ba0147714ef21c6a63ed8a45caa5b03e8acc58d8.zip | |||
| (PID) Process: | (6508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
0
Text files
5
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1132 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_RegSvcs.exe_887b6fb525c7c5e5f253acdbcd291d7cd6a15618_30ee27f1_82791df4-3055-47ff-87a3-9b427b017fe3\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1132 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\RegSvcs.exe.7124.dmp | — | |
MD5:— | SHA256:— | |||
| 1132 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER9B4D.tmp.WERInternalMetadata.xml | xml | |
MD5:B8248FC565C0FF0D78BD978473DEDE90 | SHA256:B5F7458E56A32758E447E4B7CD94162A55759B10364FABA369AB834D693547DD | |||
| 1132 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER9B5D.tmp.xml | xml | |
MD5:54BBE4DDC187D86118F7445ABDF64218 | SHA256:B1E092AFB0E739BDA1C63B99291CC1E27DB042471E818049C015384DD945E0AD | |||
| 5928 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:5477F5249EBD24663E67E887CEF44911 | SHA256:0A248B80A8274C55A10FD4FF1423762E99589942F3C4C035507631DC77AE8916 | |||
| 1132 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER9A61.tmp.dmp | dmp | |
MD5:AF9021FA9241740A42173D73DA30F9FD | SHA256:B01274871C2B4E4188CB00975BFBF7C0A527148FE3453043B3F5CEC14901227E | |||
| 6488 | payment Confirmation Request.exe | C:\Users\admin\AppData\Local\Temp\tmp4C22.tmp | xml | |
MD5:8DACD03F2BE37C5D0AB7A3FB5D2A7192 | SHA256:8B3D591866A37401513A618291EDC92575EA0ED10B60798ED3AB38EBEC6332C5 | |||
| 6508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6508.15266\2b566fa8424b46714e0357c7ba0147714ef21c6a63ed8a45caa5b03e8acc58d8.zip\payment Confirmation Request.exe | executable | |
MD5:50AD8CA4DE5B8D6ADF27C215D1201E41 | SHA256:18511EC36F7D5820423CE0E5D2E8C128100F8C5D522FAC1DF573296E0C590F71 | |||
| 6508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6508.15266\Rar$Scan61574.bat | text | |
MD5:319071E50CDDC7B8619A211C9060DDAB | SHA256:37A213A04B1896AAA2090B22712A42EE016C7DAAC33BB8779C1CCFAB5D0864EC | |||
| 6488 | payment Confirmation Request.exe | C:\Users\admin\AppData\Roaming\djnmKTAabuPDpa.exe | executable | |
MD5:50AD8CA4DE5B8D6ADF27C215D1201E41 | SHA256:18511EC36F7D5820423CE0E5D2E8C128100F8C5D522FAC1DF573296E0C590F71 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
46
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 40.126.31.71:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.71:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 20.190.159.75:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.64:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
6732 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.159.129:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | GET | 200 | 74.178.76.128:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | compressed | 23.9 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.64:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | GET | 304 | 74.178.76.128:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6732 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6732 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
checkip.dyndns.org |
| whitelisted |
client.wns.windows.com |
| whitelisted |
reallyfreegeoip.org |
| malicious |