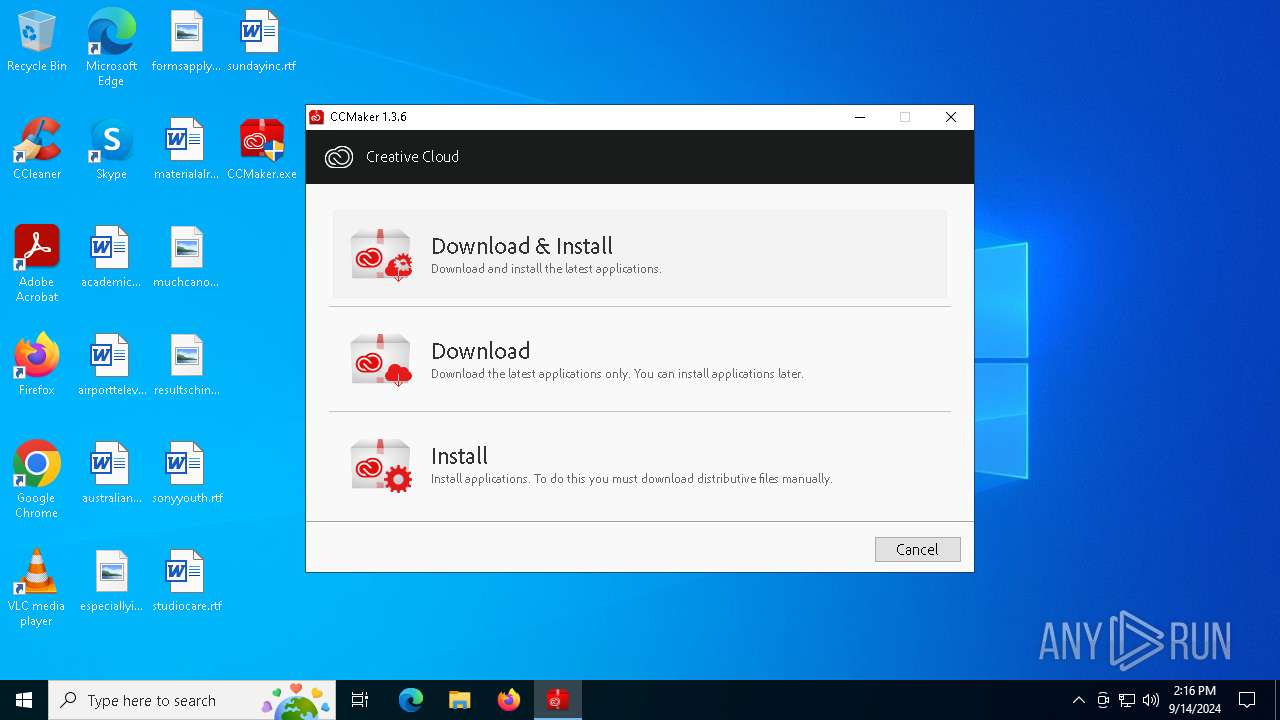
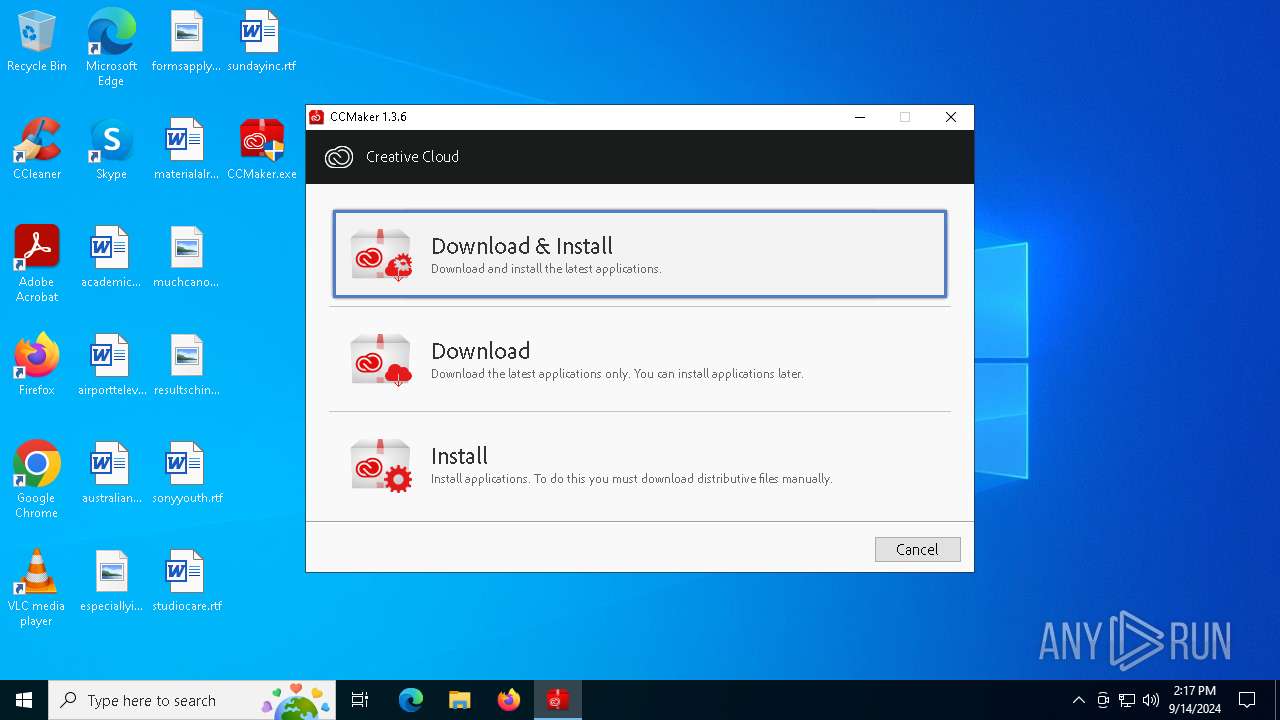
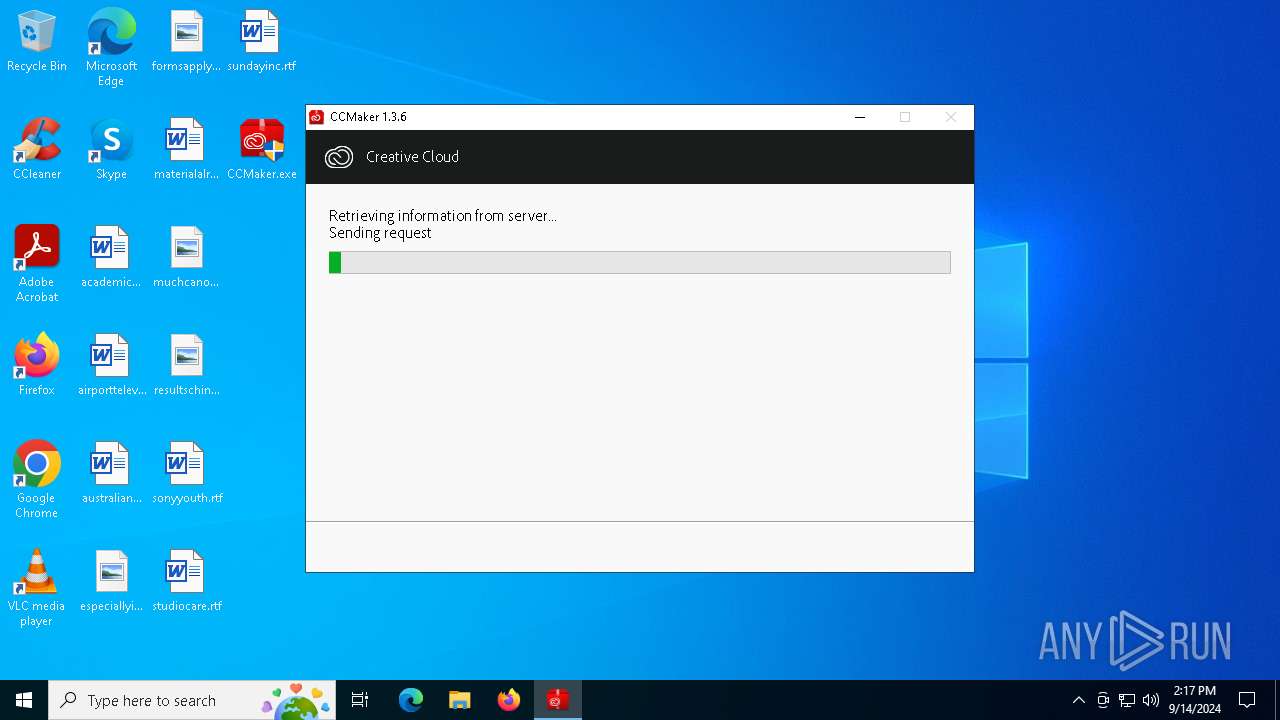
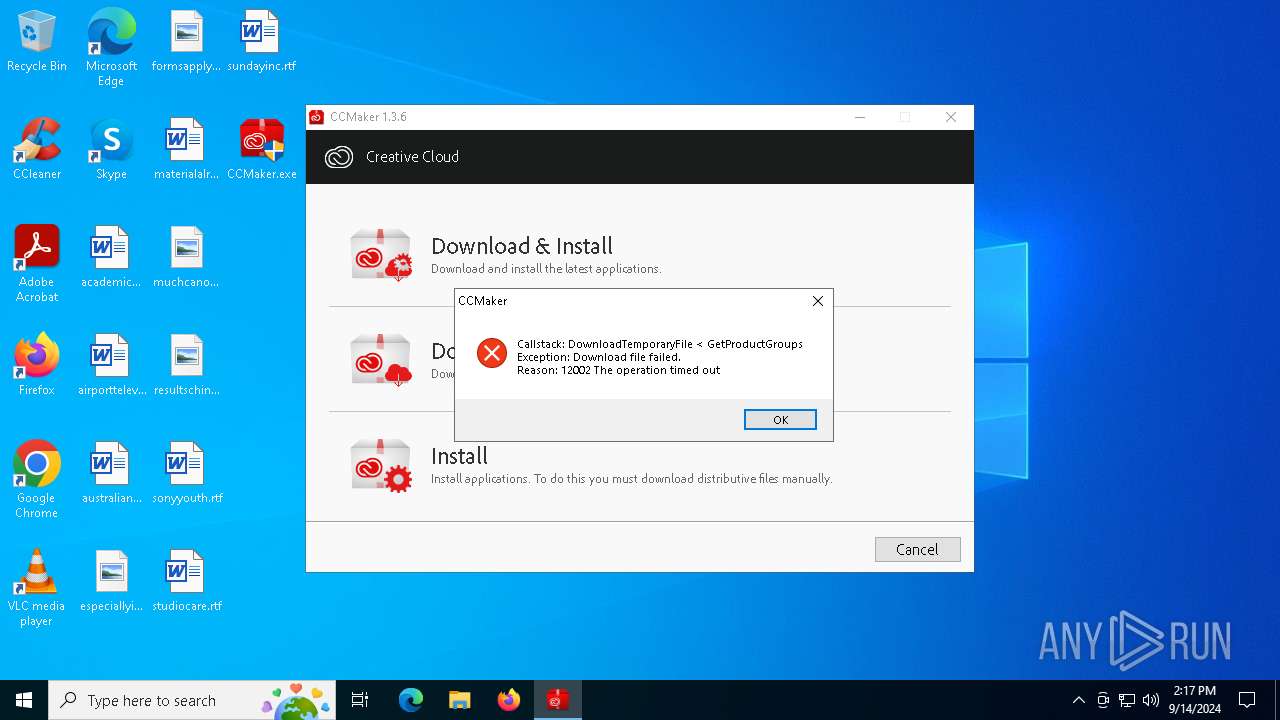
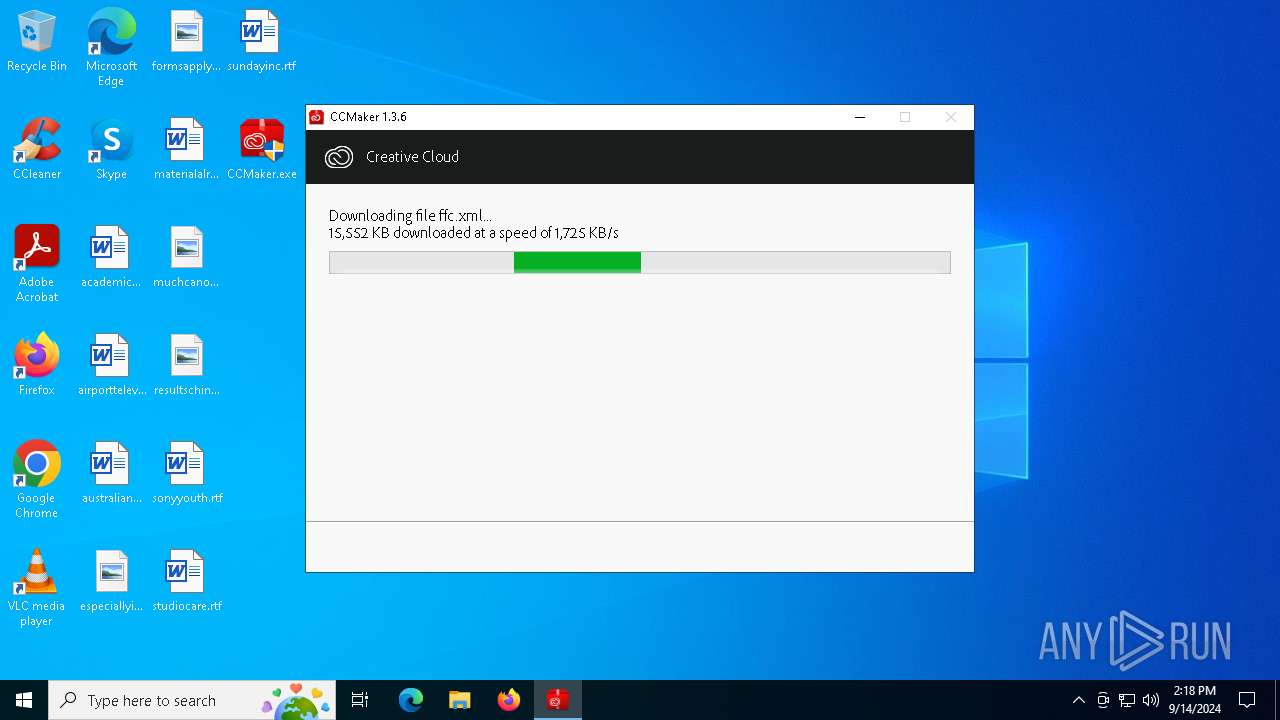
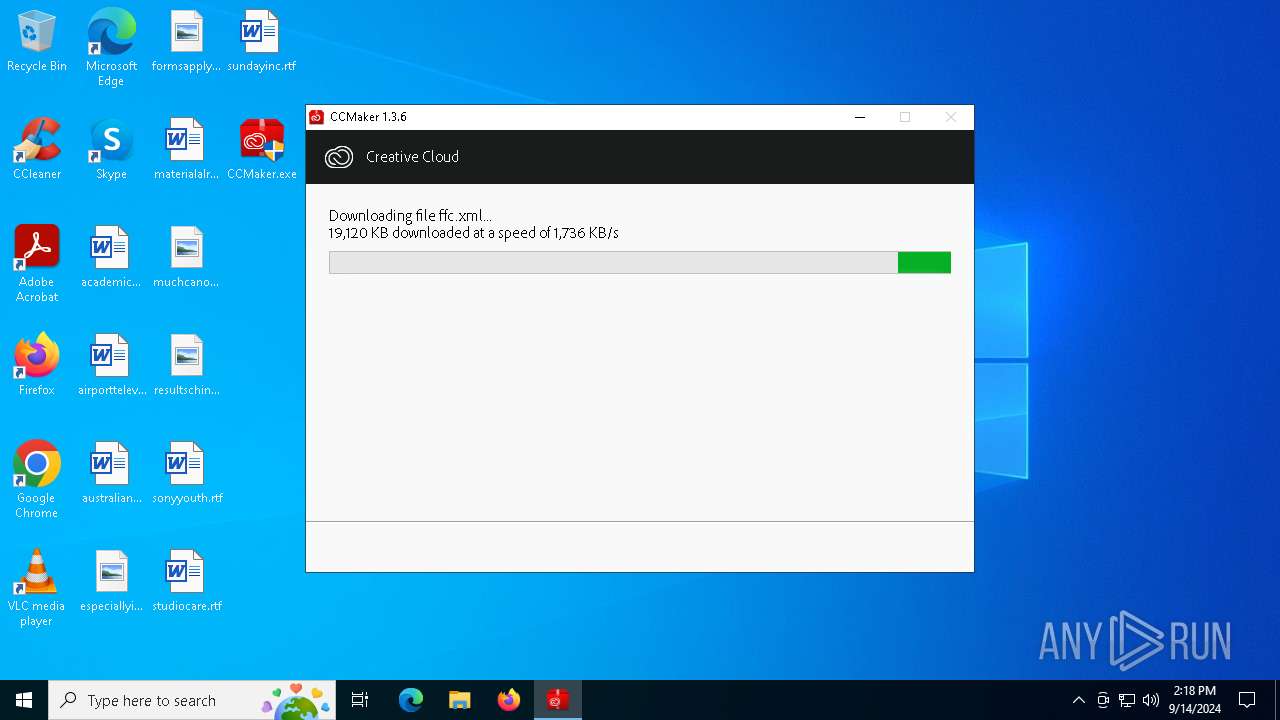
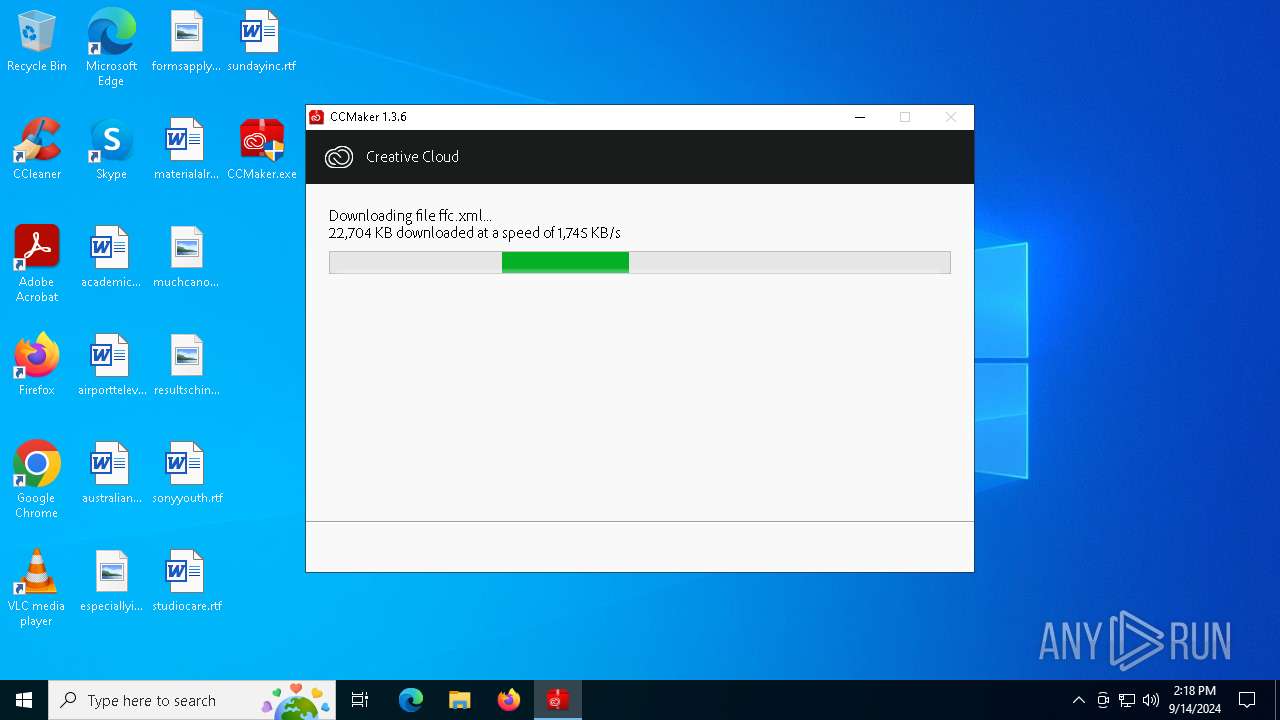
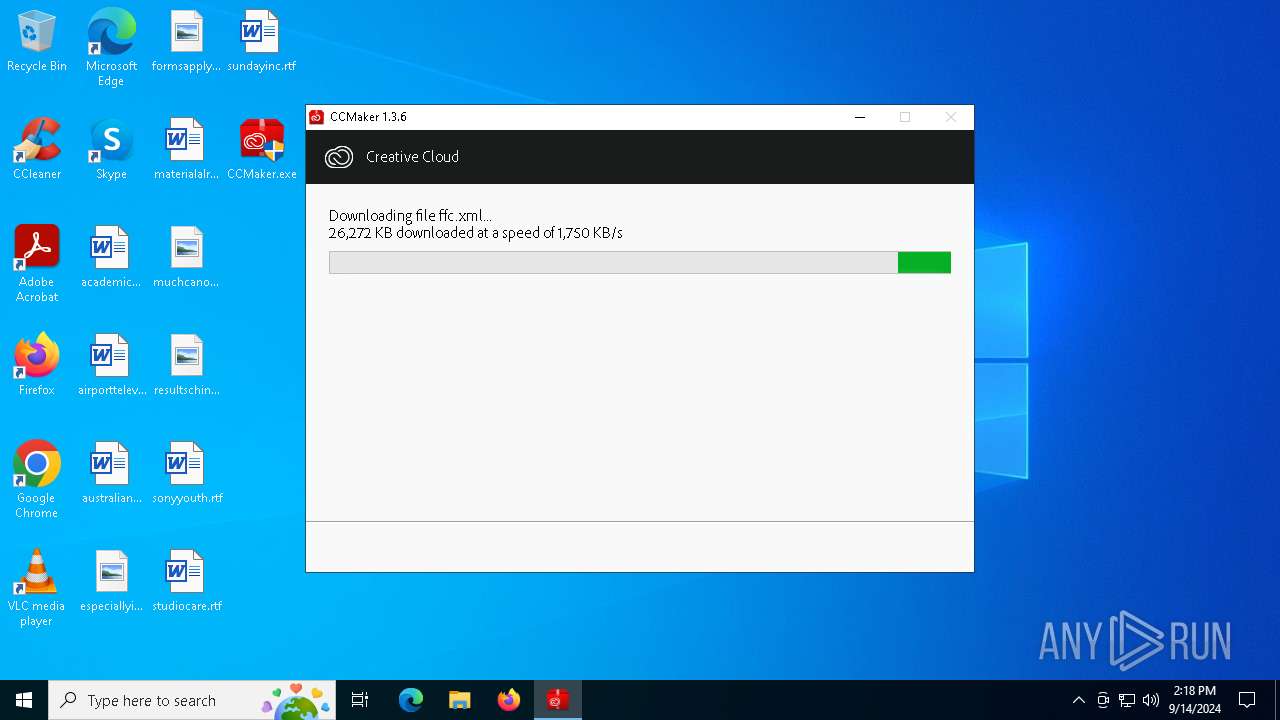
| File name: | CCMaker.exe |
| Full analysis: | https://app.any.run/tasks/f05eb54e-5388-4d0b-8ff5-959a9aea859d |
| Verdict: | Malicious activity |
| Analysis date: | September 14, 2024, 14:16:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 8245FB097BE69F9204BACBC431C77E9E |
| SHA1: | 7D65E54A41874036A52887FD470E562891B89711 |
| SHA256: | 2B4B5EB89FE8A52F93A2E2D484E5B00BBCD706E04D3919C42619FDE1FADFB99E |
| SSDEEP: | 98304:ZILEhPjkG+WPiGvTcCYzqg2zCcwce51zQbQMzvPbxv7hQgnydL7bRikWYmwqq268:h+M++p |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- CCMaker.exe (PID: 4920)
- CCMaker.tmp (PID: 7132)
Reads the Windows owner or organization settings
- CCMaker.tmp (PID: 7132)
Reads security settings of Internet Explorer
- CCMaker.tmp (PID: 7132)
Checks Windows Trust Settings
- CCMaker.tmp (PID: 7132)
Creates FileSystem object to access computer's file system (SCRIPT)
- CCMaker.tmp (PID: 7132)
Checks whether a specific file exists (SCRIPT)
- CCMaker.tmp (PID: 7132)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- CCMaker.tmp (PID: 7132)
INFO
Checks supported languages
- CCMaker.exe (PID: 4920)
- CCMaker.tmp (PID: 7132)
Create files in a temporary directory
- CCMaker.exe (PID: 4920)
- CCMaker.tmp (PID: 7132)
Reads the computer name
- CCMaker.tmp (PID: 7132)
Checks proxy server information
- CCMaker.tmp (PID: 7132)
Reads the machine GUID from the registry
- CCMaker.tmp (PID: 7132)
Reads the software policy settings
- CCMaker.tmp (PID: 7132)
Sends debugging messages
- CCMaker.tmp (PID: 7132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (81.5) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10.5) |
| .exe | | | Win32 Executable (generic) (3.3) |
| .exe | | | Win16/32 Executable Delphi generic (1.5) |
| .exe | | | Generic Win/DOS Executable (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:10:02 05:04:04+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 86016 |
| InitializedDataSize: | 82944 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16478 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.6.0 |
| ProductVersionNumber: | 1.3.6.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Pendejo Software |
| FileDescription: | CCMaker |
| FileVersion: | 1.3.6 |
| LegalCopyright: | |
| ProductName: | CCMaker |
| ProductVersion: | 1.3.6 |
Total processes
125
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3964 | "C:\Users\admin\Desktop\CCMaker.exe" | C:\Users\admin\Desktop\CCMaker.exe | — | explorer.exe | |||||||||||
User: admin Company: Pendejo Software Integrity Level: MEDIUM Description: CCMaker Exit code: 3221226540 Version: 1.3.6 Modules
| |||||||||||||||
| 4920 | "C:\Users\admin\Desktop\CCMaker.exe" | C:\Users\admin\Desktop\CCMaker.exe | explorer.exe | ||||||||||||
User: admin Company: Pendejo Software Integrity Level: HIGH Description: CCMaker Version: 1.3.6 Modules
| |||||||||||||||
| 7132 | "C:\Users\admin\AppData\Local\Temp\is-46CG1.tmp\CCMaker.tmp" /SL5="$503A8,2152483,169984,C:\Users\admin\Desktop\CCMaker.exe" | C:\Users\admin\AppData\Local\Temp\is-46CG1.tmp\CCMaker.tmp | CCMaker.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
3 791
Read events
3 787
Write events
4
Delete events
0
Modification events
| (PID) Process: | (7132) CCMaker.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7132) CCMaker.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7132) CCMaker.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7132) CCMaker.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\ccmaker.tmp |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: CD29140000000000 | |||
Executable files
5
Suspicious files
0
Text files
40
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7132 | CCMaker.tmp | C:\Users\admin\AppData\Local\Temp\is-68565.tmp\ffc.xml.partial | — | |
MD5:— | SHA256:— | |||
| 7132 | CCMaker.tmp | C:\Users\admin\AppData\Local\Temp\is-68565.tmp\ffc.xml | — | |
MD5:— | SHA256:— | |||
| 4920 | CCMaker.exe | C:\Users\admin\AppData\Local\Temp\is-46CG1.tmp\CCMaker.tmp | executable | |
MD5:5E74B852A8E6B62494464A25A86E9C05 | SHA256:473BF28C3F87A5C7D8404B763E528B448C5C2975765D65876BE0C4D3A615DC76 | |||
| 7132 | CCMaker.tmp | C:\Users\admin\AppData\Local\Temp\is-68565.tmp\sqlite3.dll | executable | |
MD5:B6F45FBF727F8D872D5DC6FDD6393802 | SHA256:07B9F5C9858F3477F3BB6A11C8283C3A34AA7085F578AEC95DE37053430DE83F | |||
| 7132 | CCMaker.tmp | C:\Users\admin\AppData\Local\Temp\is-68565.tmp\WARN.PNG | image | |
MD5:EE00EBAA590C55414CA70AD2D0468E52 | SHA256:EC8945F6A27365C2F0176625F2192BAA624FC60CAAD8FC67D67A900F43AAB1FE | |||
| 7132 | CCMaker.tmp | C:\Users\admin\AppData\Local\Temp\is-68565.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 7132 | CCMaker.tmp | C:\Users\admin\AppData\Local\Temp\is-68565.tmp\NEW.PNG | image | |
MD5:FBC7B44203331CF5F8DCF9755F30655F | SHA256:10E24D516C91102369CA03E9F4F47836B4271A0A7B359AC3AA2292BA47F4651E | |||
| 7132 | CCMaker.tmp | C:\Users\admin\AppData\Local\Temp\is-68565.tmp\7-zip32.dll | executable | |
MD5:3EC079B620BFD16CFDABB17C86CDB14E | SHA256:1AEF0B307388747ED75D3907D128D9EC382777970A1962E3A7BA9015123E411C | |||
| 7132 | CCMaker.tmp | C:\Users\admin\AppData\Local\Temp\is-68565.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
| 7132 | CCMaker.tmp | C:\Users\admin\AppData\Local\Temp\is-68565.tmp\group.png.partial | image | |
MD5:F9735C0A850443A37FD3EF6E6F464A39 | SHA256:637CB88CA98BC2DE3CED77318BD91E6E1367083745028B524966BB1C5D34B9AA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
41
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6208 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6056 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 23.22.254.206:443 | https://prod-rel-ffc-ccm.oobesaas.adobe.com/adobe-ffc-external/core/v1/ccm/products | unknown | — | — | unknown |
— | — | HEAD | 200 | 23.22.254.206:443 | https://prod-rel-ffc-ccm.oobesaas.adobe.com/adobe-ffc-external/core/v1/ccm/products | unknown | — | — | unknown |
— | — | GET | 200 | 18.66.102.25:443 | https://ffc-static-cdn.oobesaas.adobe.com/icons/ESHR/4.0.3/64x64.png | unknown | image | 1.50 Kb | unknown |
— | — | GET | 200 | 54.227.187.23:443 | https://prod-rel-ffc-ccm.oobesaas.adobe.com/adobe-ffc-external/core/v4/products/all?_type=xml&channel=ccm,sti&platform=win32,win64&productType=Desktop | unknown | xml | 31.3 Mb | unknown |
— | — | GET | 200 | 18.66.102.25:443 | https://ffc-static-cdn.oobesaas.adobe.com/icons/AEFT/24.6.2/64x64.png | unknown | image | 1.65 Kb | unknown |
— | — | GET | 200 | 18.66.102.10:443 | https://ffc-static-cdn.oobesaas.adobe.com/icons/AERO/0.24.4/64x64.png | unknown | image | 1.65 Kb | unknown |
— | — | GET | 200 | 18.66.102.25:443 | https://ffc-static-cdn.oobesaas.adobe.com/icons/AME/24.6.1/64x64.png | unknown | image | 1.63 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6056 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6208 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6056 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6208 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4324 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7132 | CCMaker.tmp | 18.207.85.246:443 | prod-rel-ffc-ccm.oobesaas.adobe.com | AMAZON-AES | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
prod-rel-ffc-ccm.oobesaas.adobe.com |
| whitelisted |
ffc-static-cdn.oobesaas.adobe.com |
| whitelisted |
Threats
Process | Message |
|---|---|
CCMaker.tmp | Extra call to Release() !!!
|
CCMaker.tmp | Extra call to Release() !!!
|