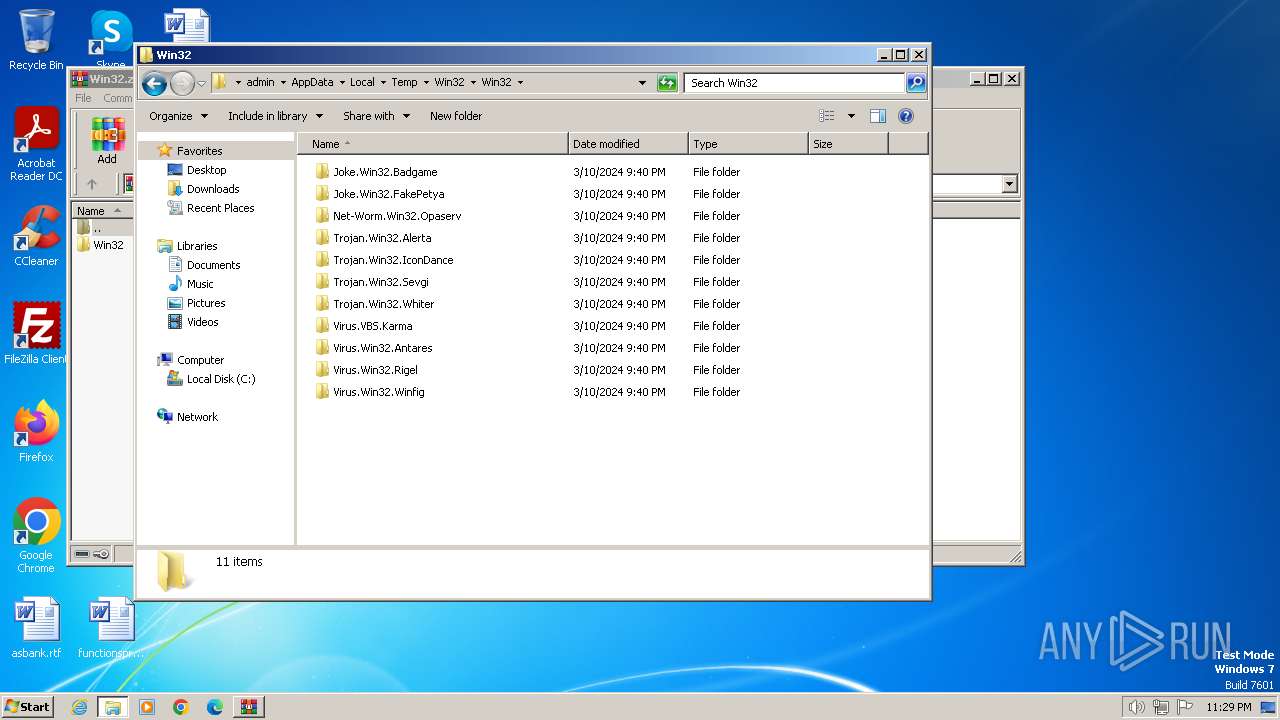
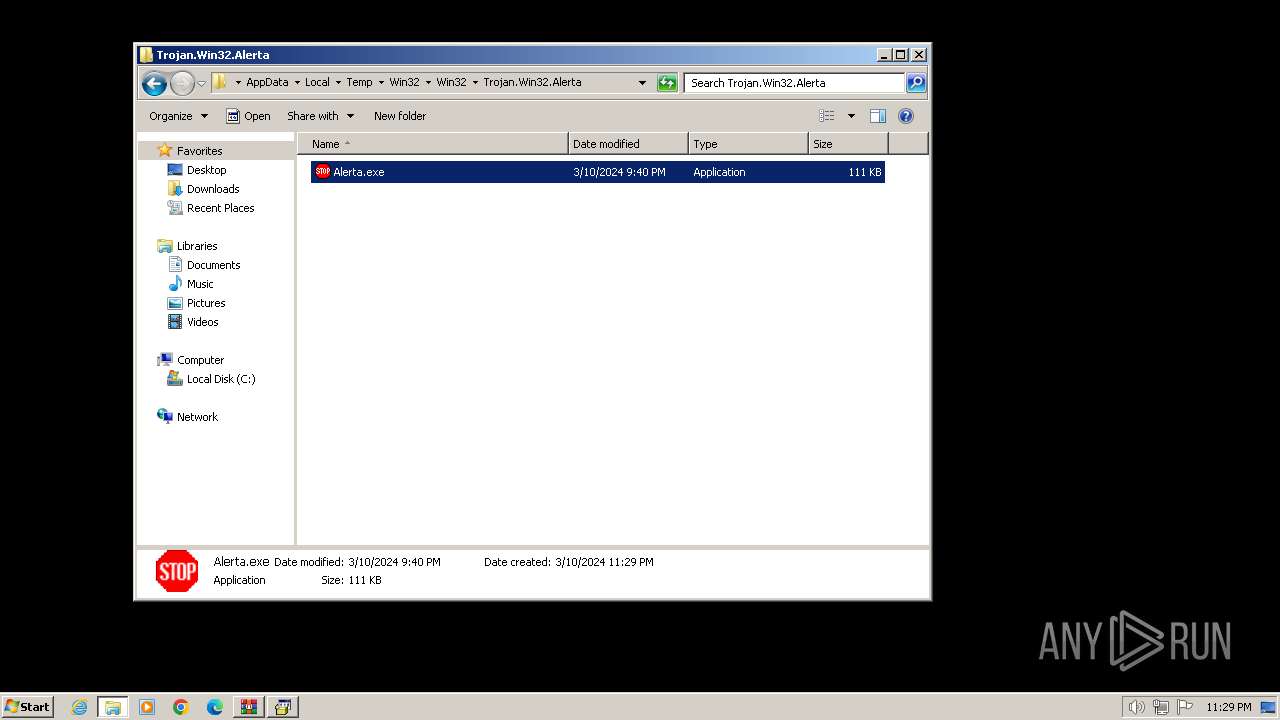
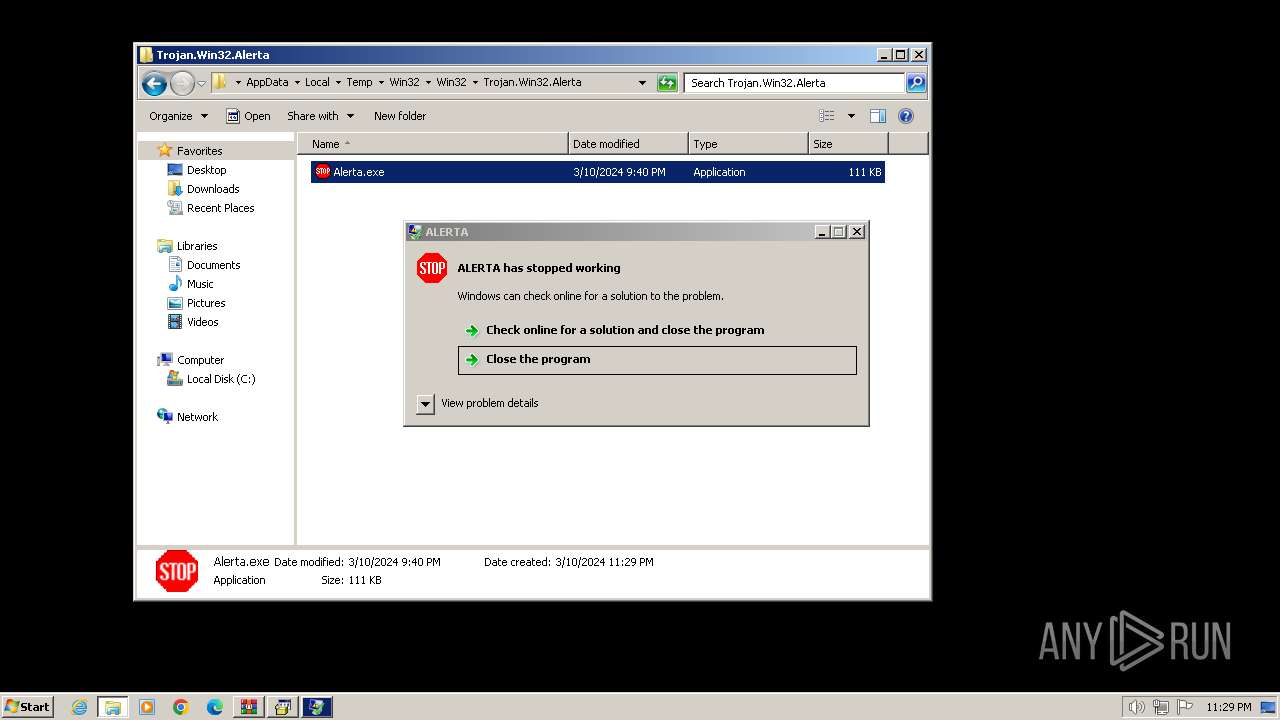
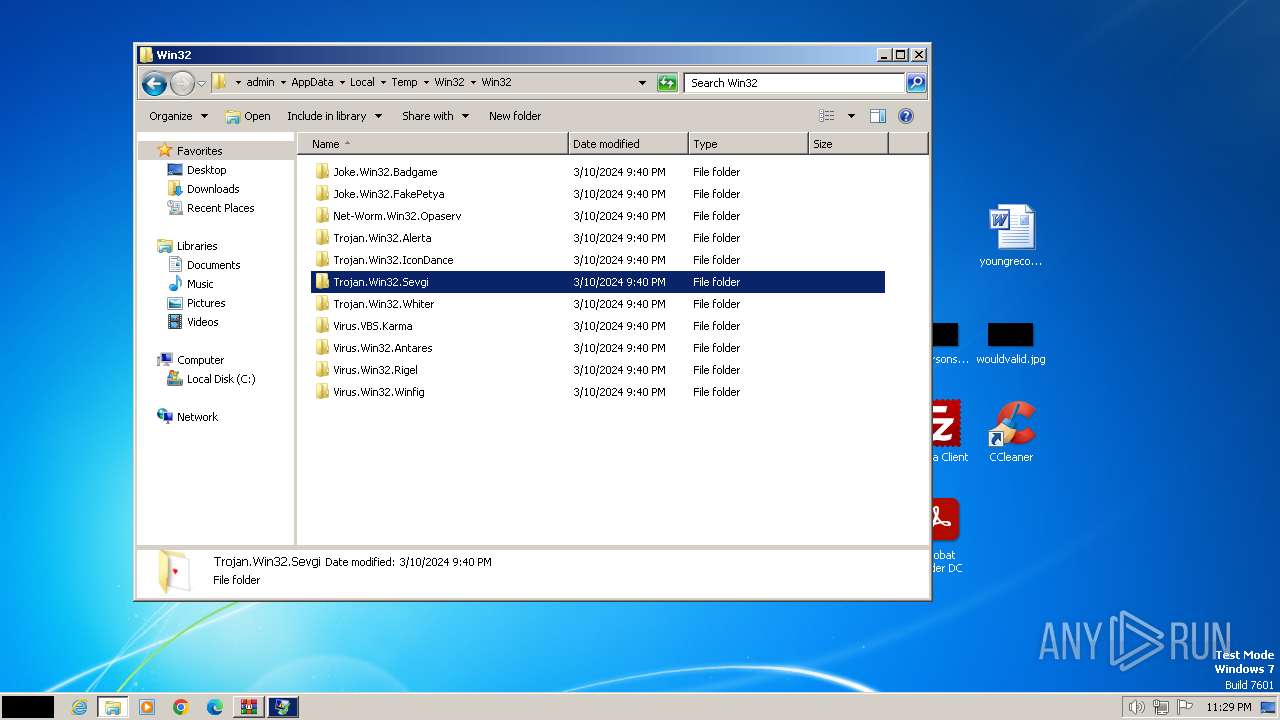
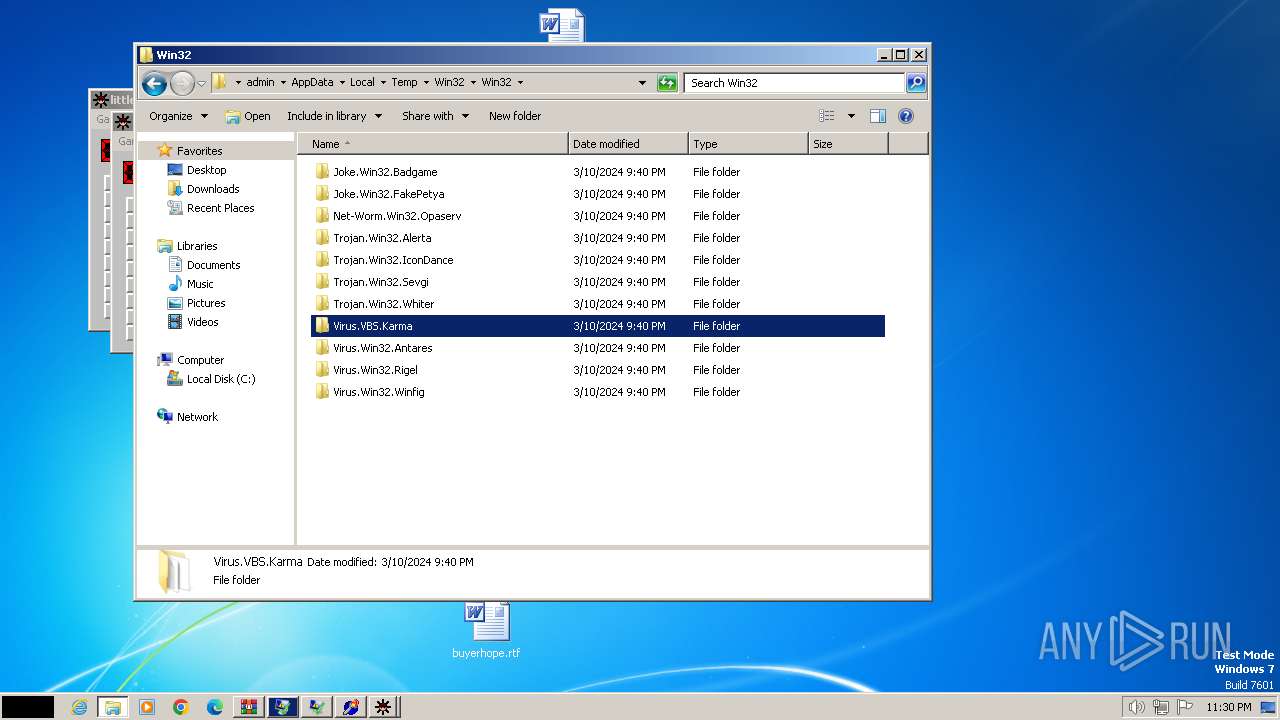
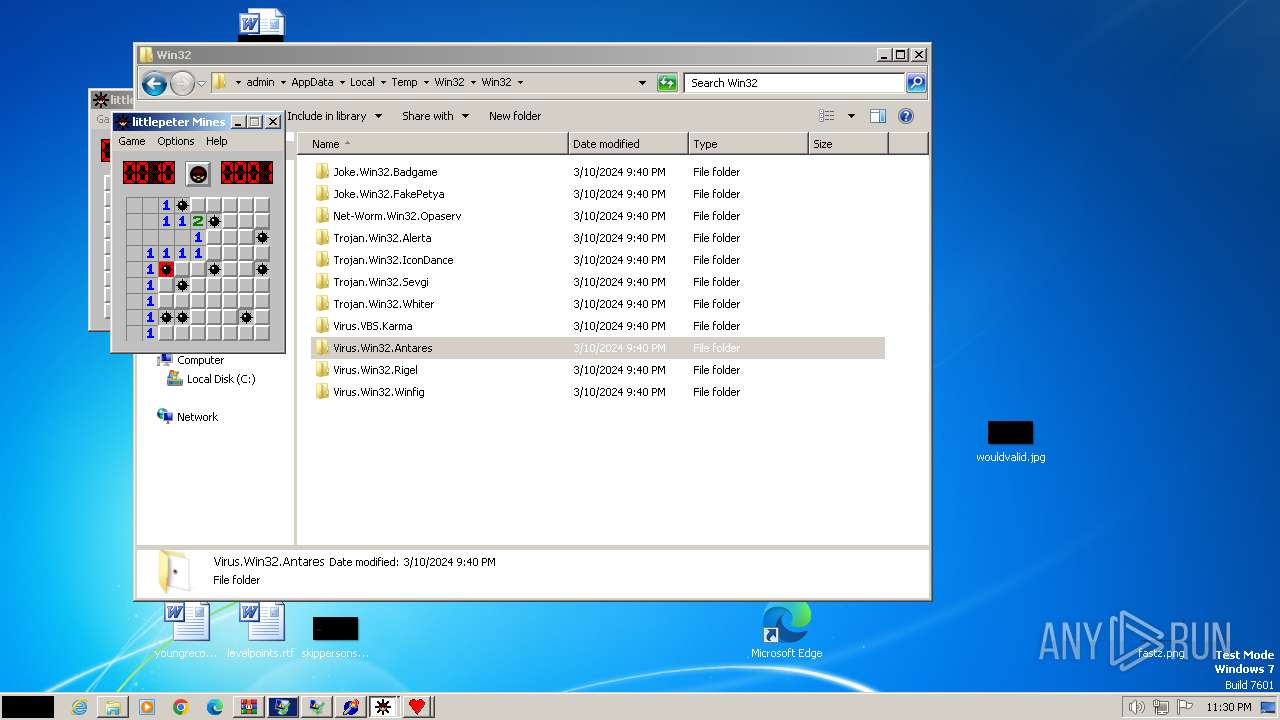
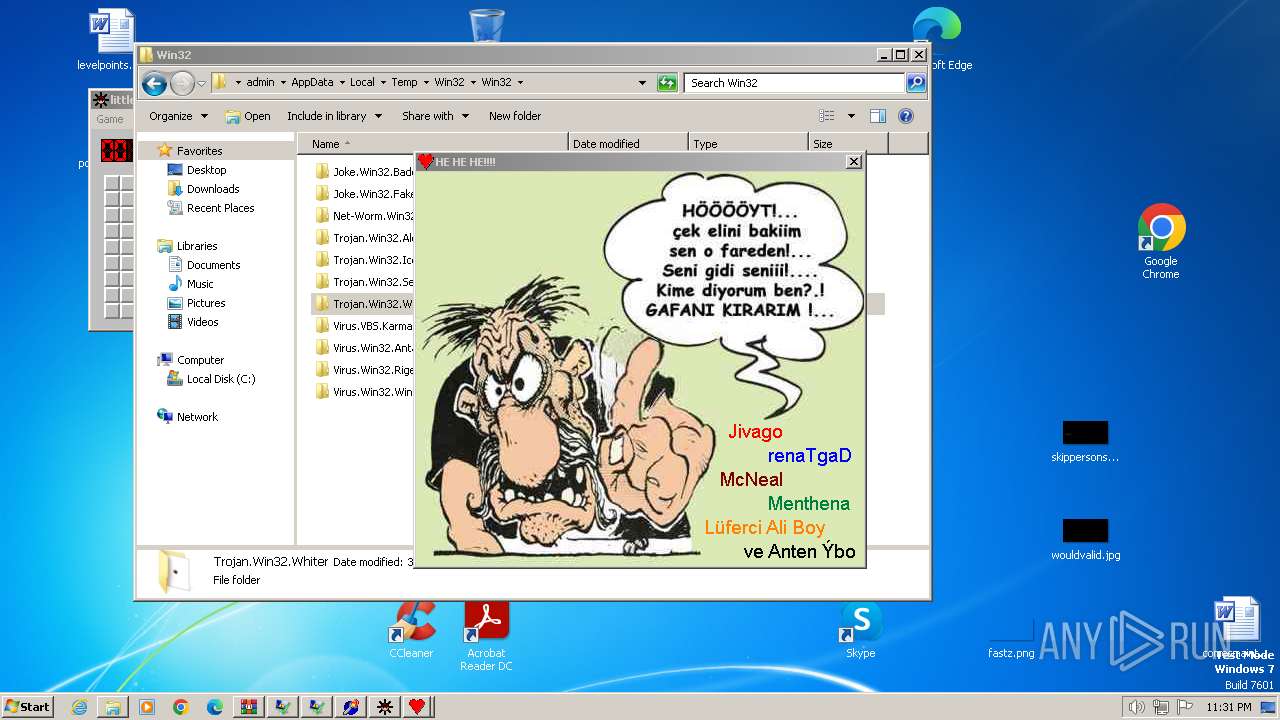
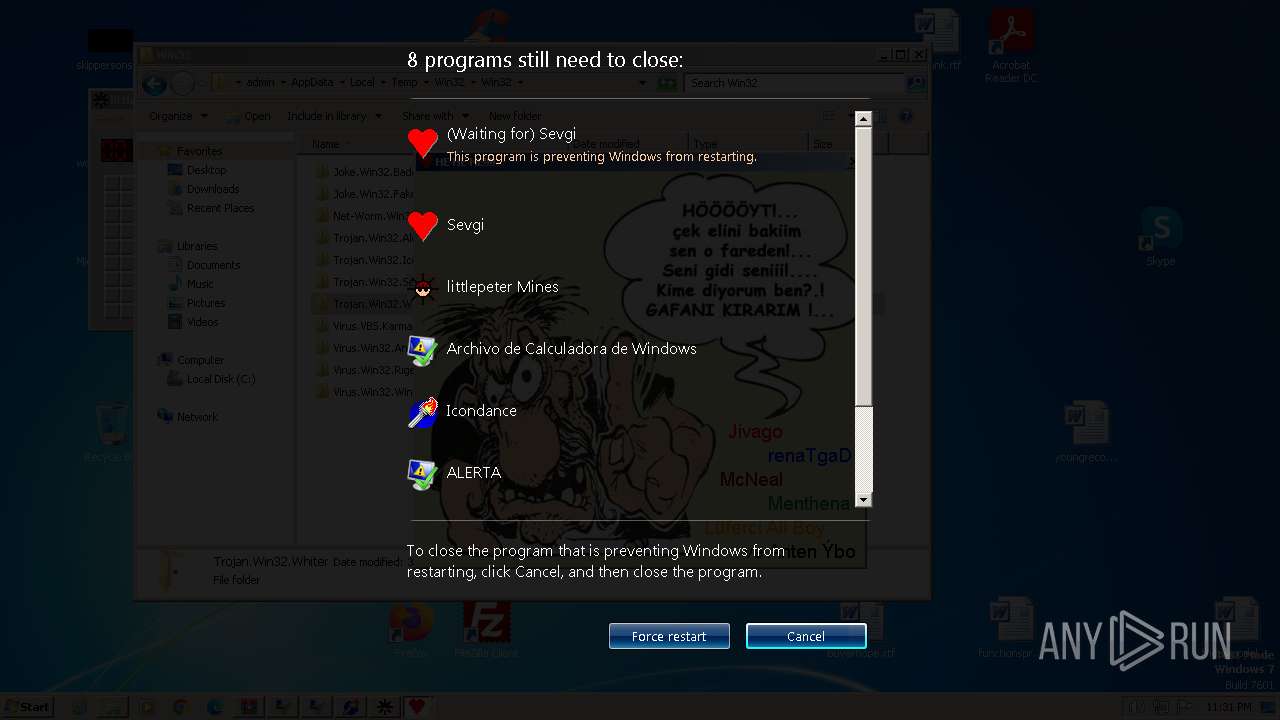
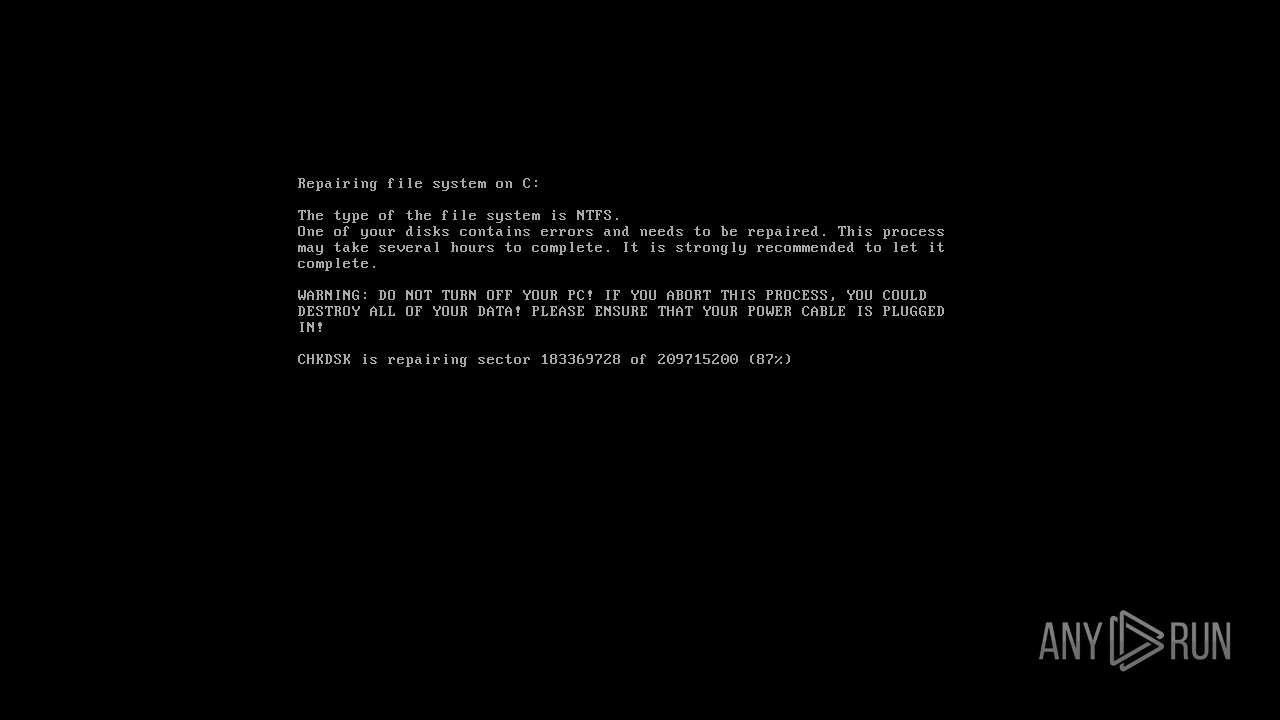
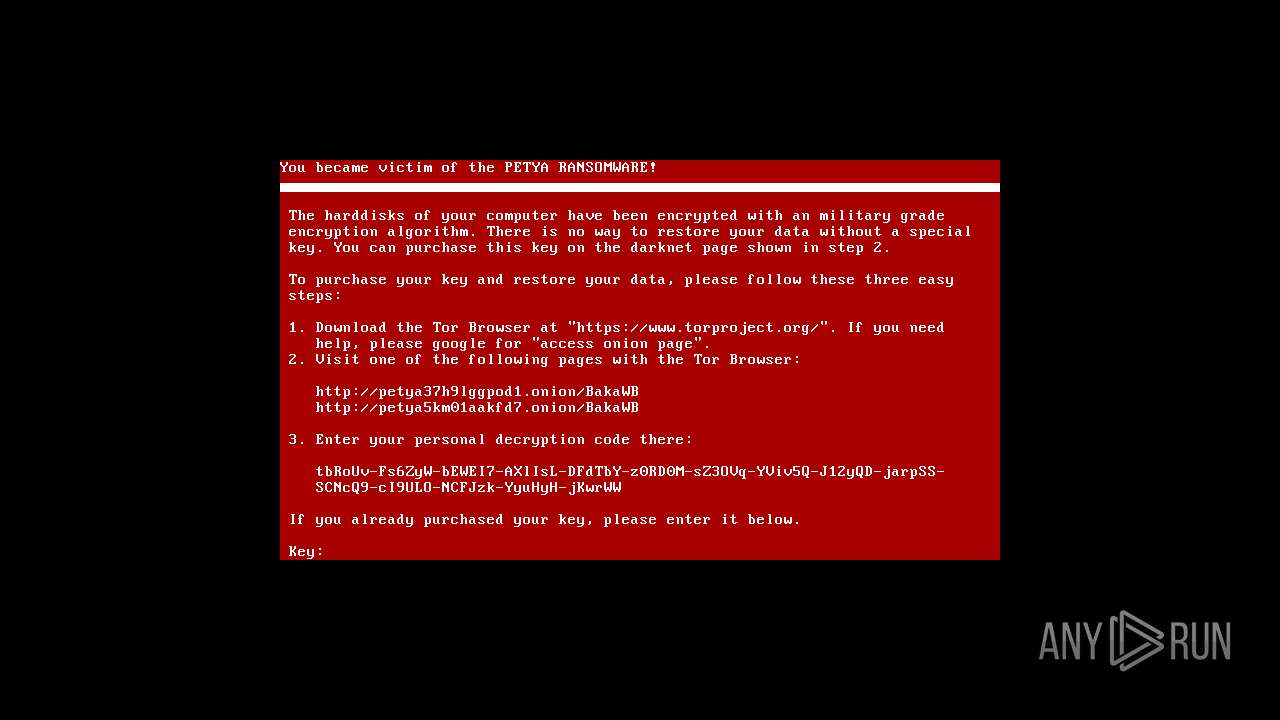
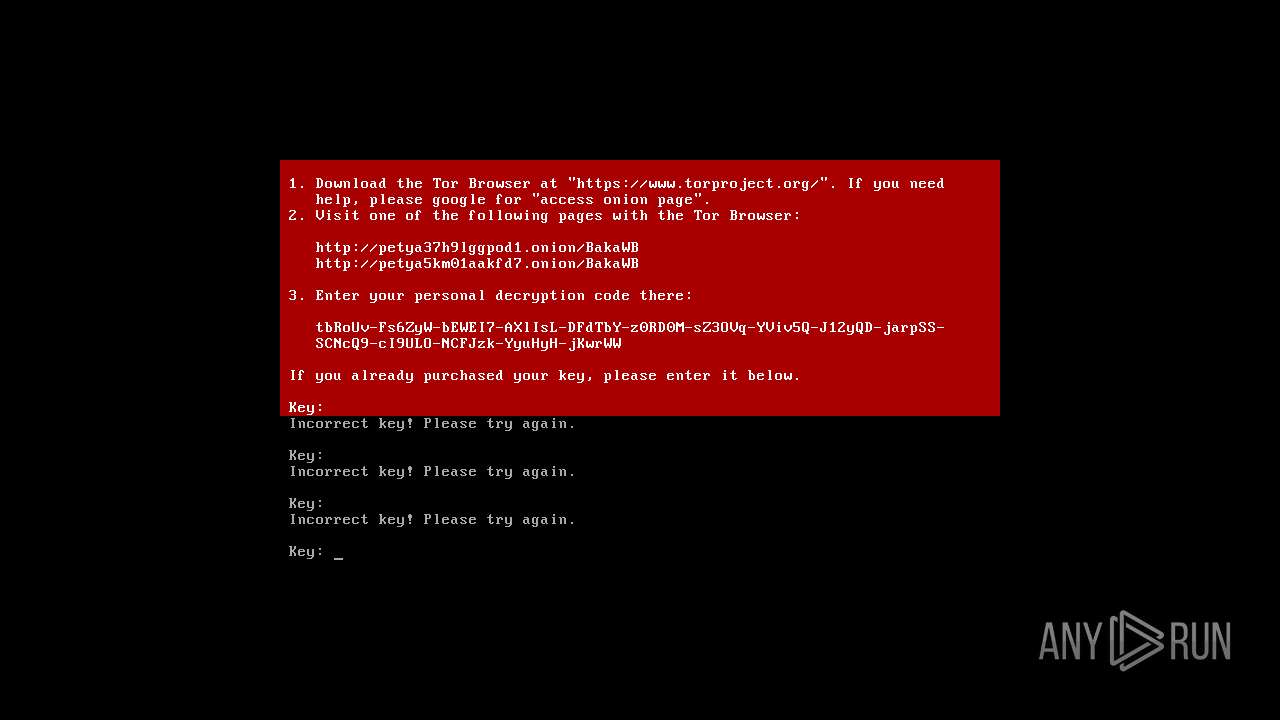
| File name: | Win32.zip |
| Full analysis: | https://app.any.run/tasks/48aa0e24-13d1-4922-b59e-a54731b72246 |
| Verdict: | Malicious activity |
| Analysis date: | March 10, 2024, 23:28:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | B251B30E1035C263C629C320F2C372E3 |
| SHA1: | A2B0C01EB6FCBB92FC6335ABB1522BA344651673 |
| SHA256: | 2B480727BE5CBF562BC6CBC8F4D840292451B703D20934B6C78DE8D2BF744E9C |
| SSDEEP: | 24576:JAzqvDYufXiUGYt3fYIeaYz9nhb8DOzVOiwjFmj/BtuGy6OkRS:JAzqvDYufXiUGYt3fYIeaYZnhb8DOzV8 |
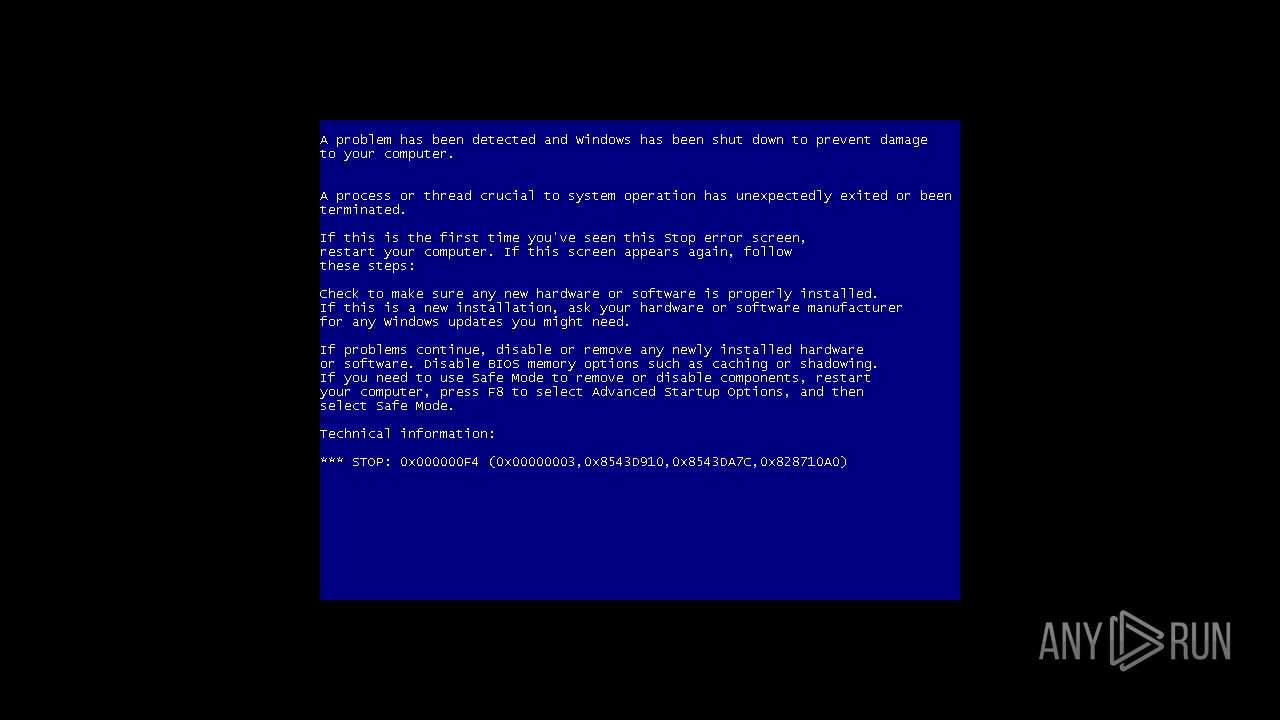
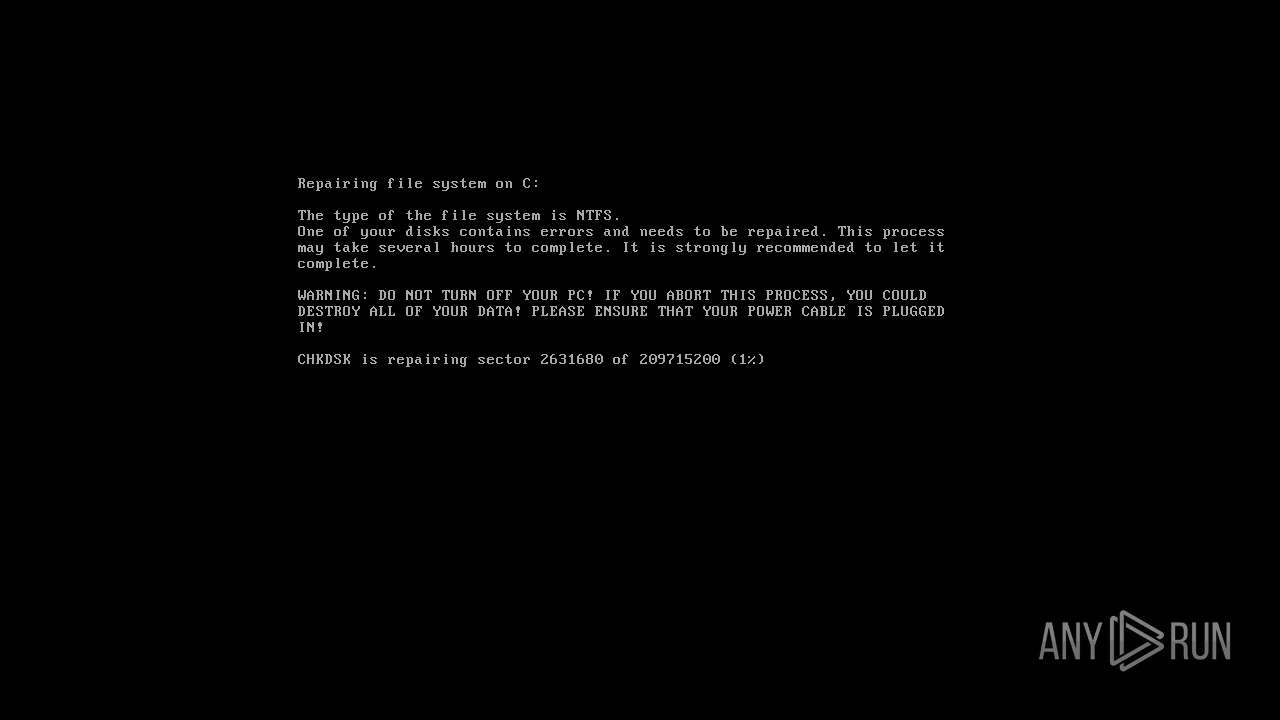
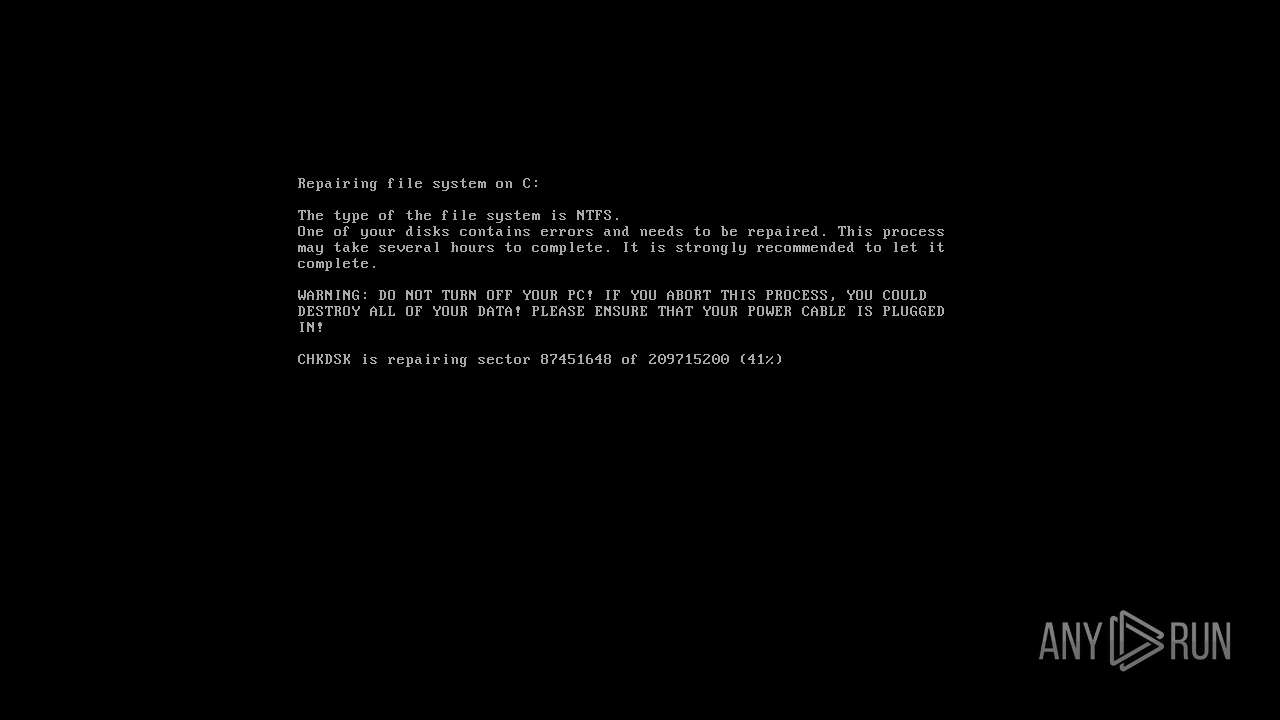
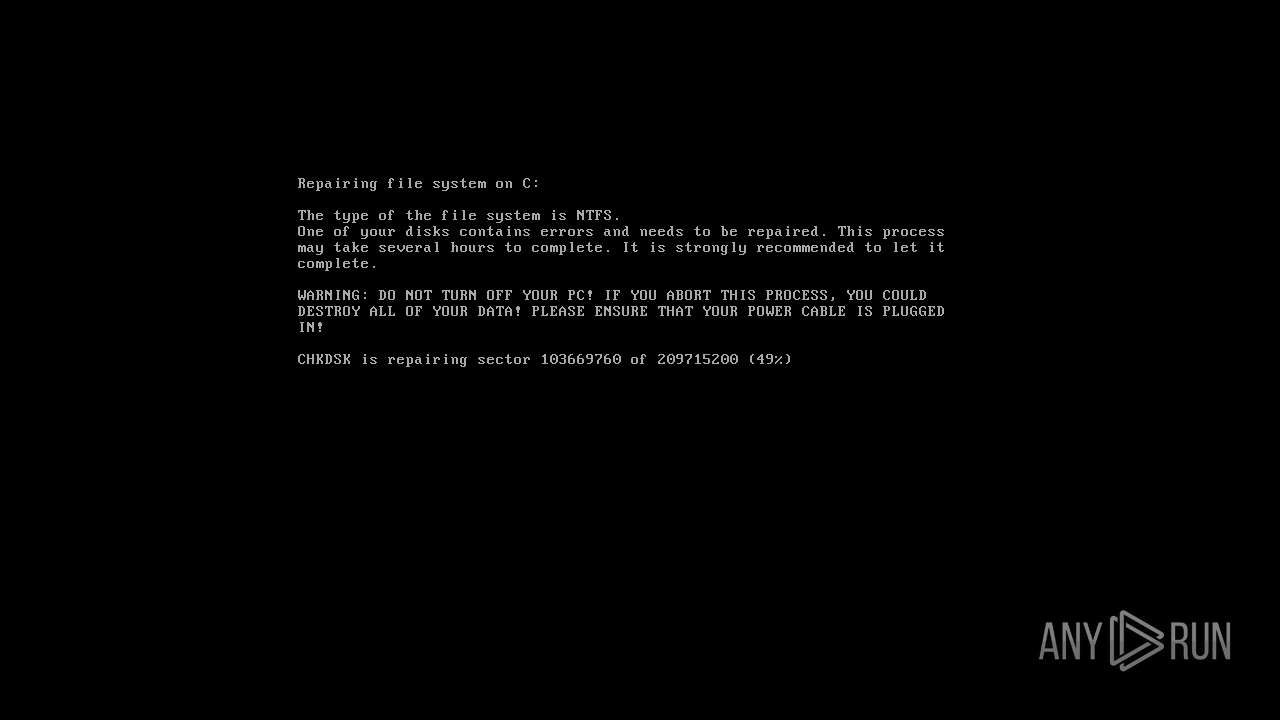
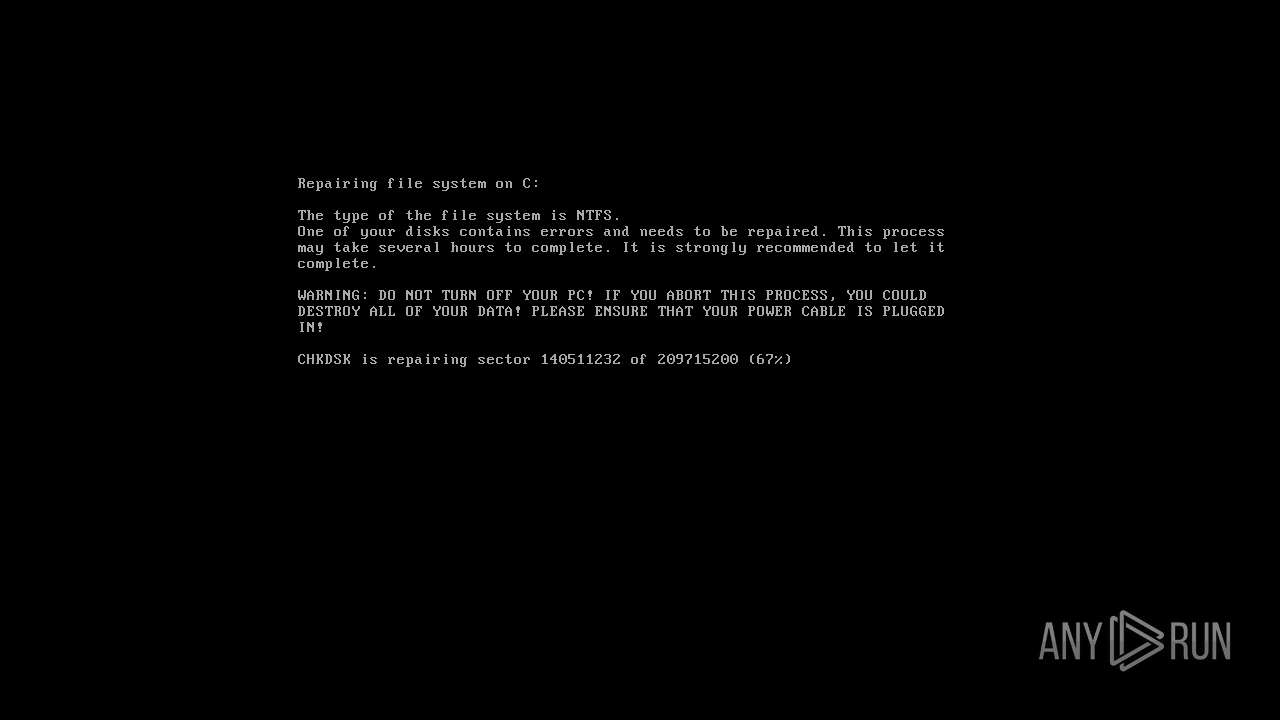
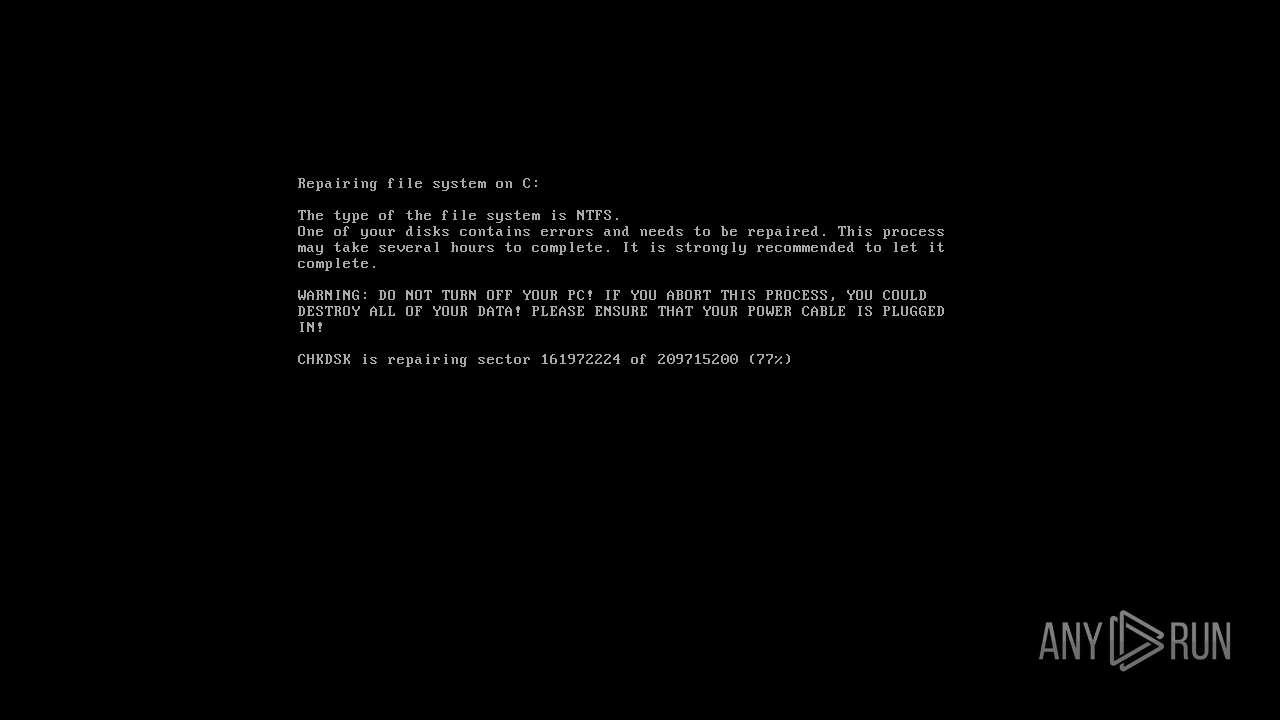
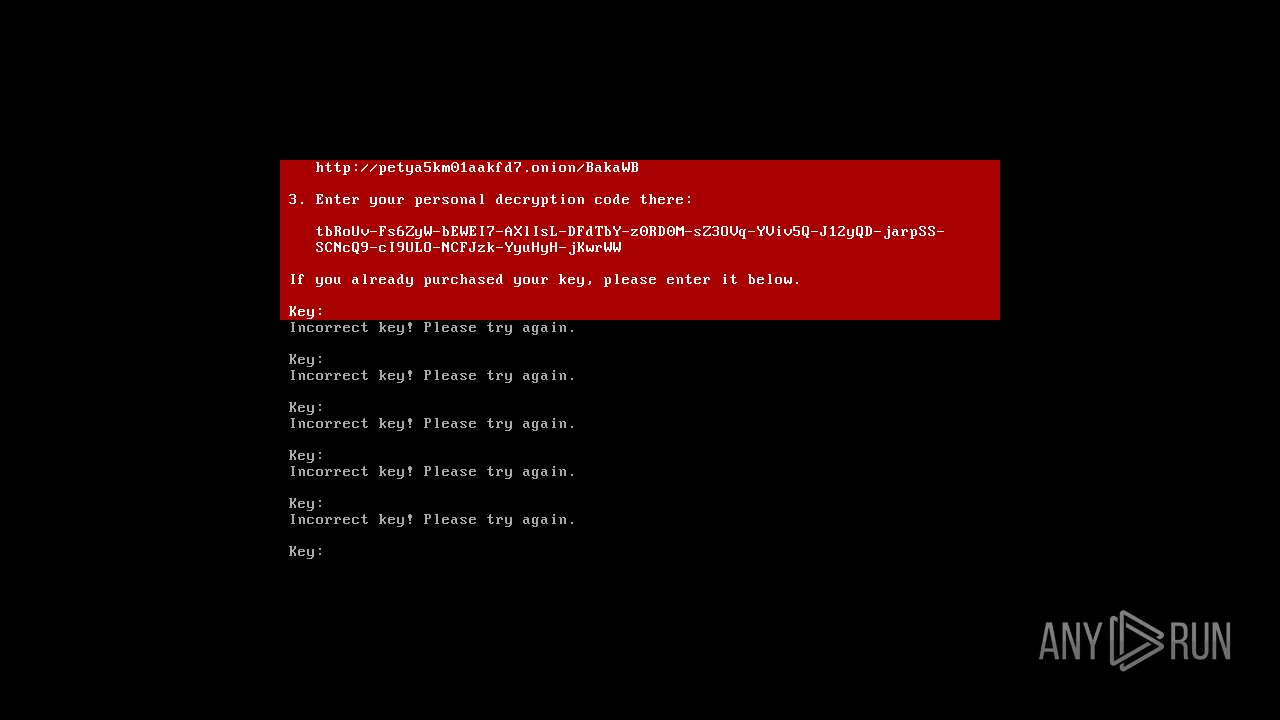
MALICIOUS
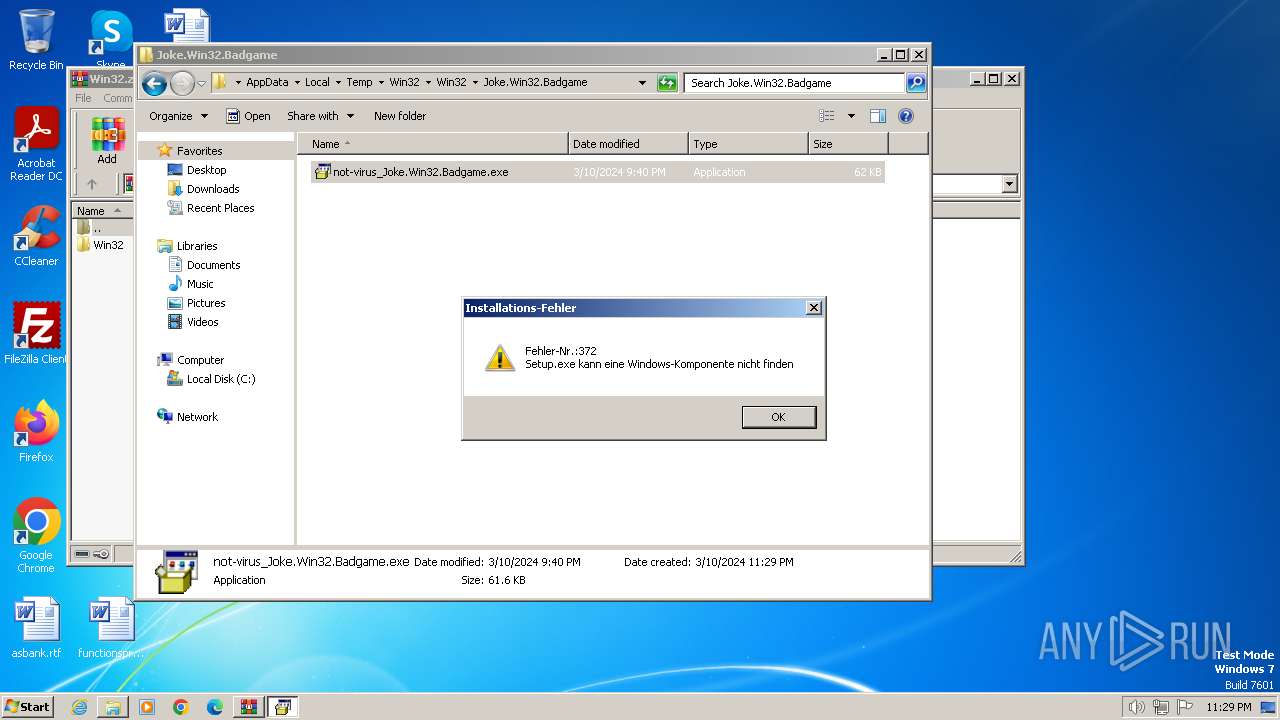
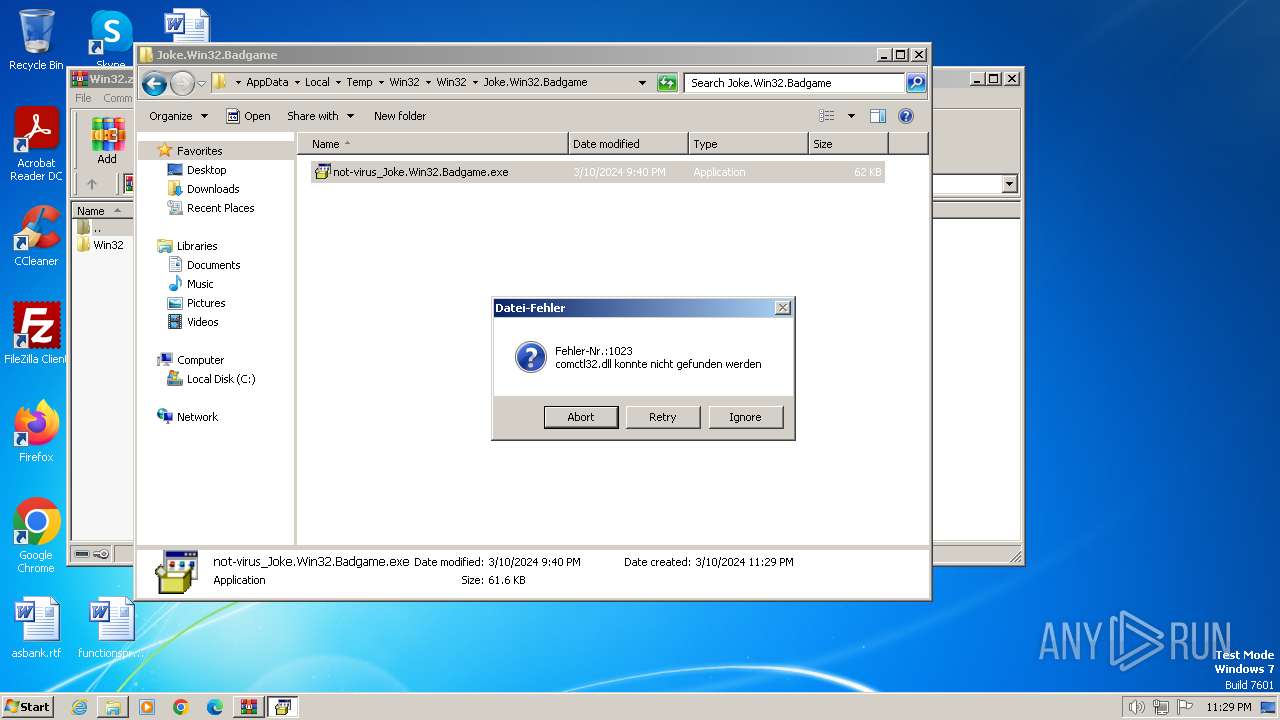
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3864)
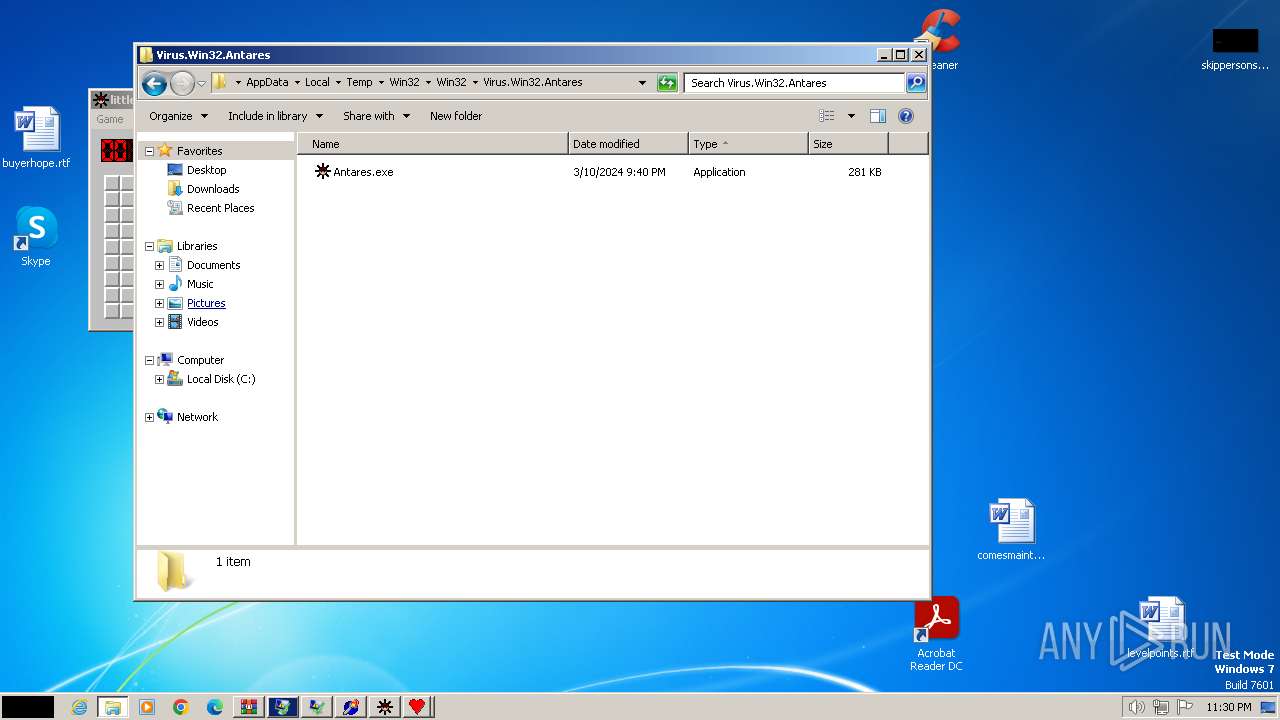
- Antares.exe (PID: 2572)
Starts NET.EXE for service management
- Opaserv.exe (PID: 3164)
- net.exe (PID: 796)
- net.exe (PID: 848)
- net.exe (PID: 2072)
- net.exe (PID: 2168)
- net.exe (PID: 1928)
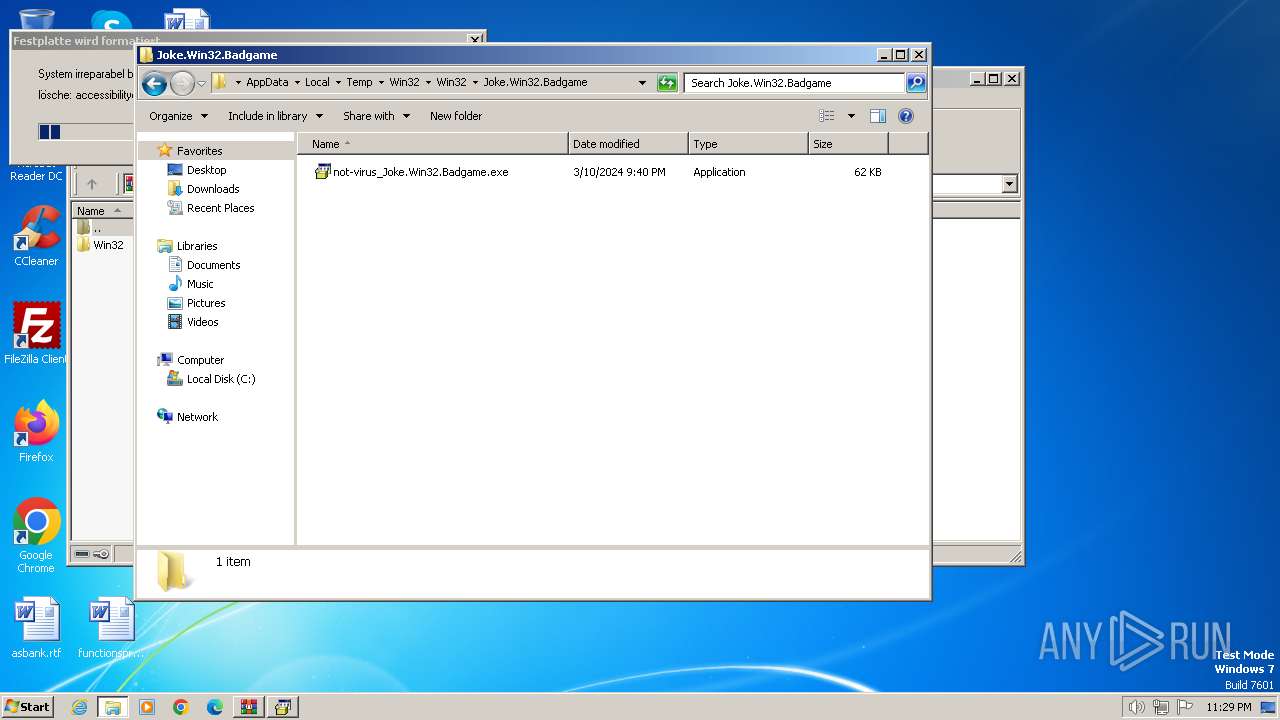
Changes the autorun value in the registry
- Opaserv.exe (PID: 3164)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3864)
- Antares.exe (PID: 2572)
Starts a Microsoft application from unusual location
- Rigel.exe (PID: 3728)
- Rigel.exe (PID: 3408)
Executable content was dropped or overwritten
- Antares.exe (PID: 2572)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3324)
Hides command output
- cmd.exe (PID: 3068)
The process executes via Task Scheduler
- ctfmon.exe (PID: 1660)
- sipnotify.exe (PID: 1448)
INFO
Checks supported languages
- not-virus_Joke.Win32.Badgame.exe (PID: 2340)
- Opaserv.exe (PID: 3164)
- IconDance.exe (PID: 664)
- Rigel.exe (PID: 3728)
- Rigel.exe (PID: 3408)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3864)
Manual execution by a user
- not-virus_Joke.Win32.Badgame.exe (PID: 2340)
- Opaserv.exe (PID: 3164)
- Alerta.exe (PID: 3800)
- IconDance.exe (PID: 664)
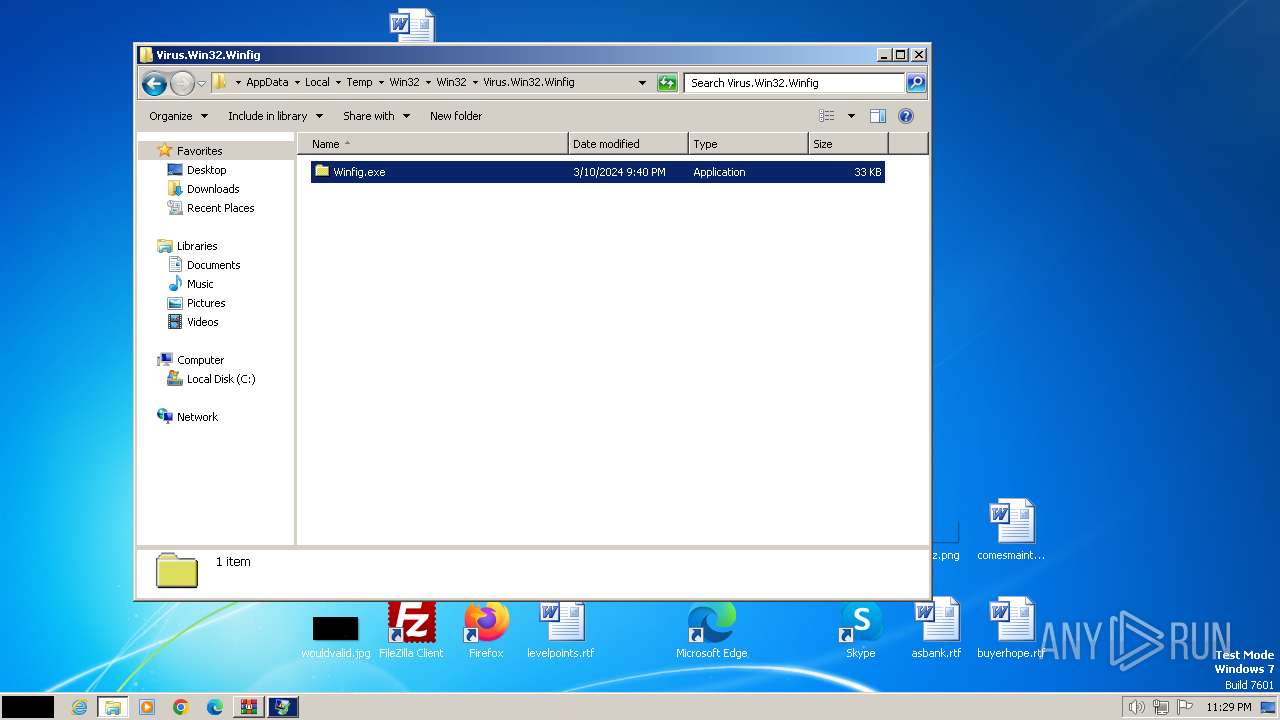
- Winfig.exe (PID: 668)
- Rigel.exe (PID: 3728)
- Antares.exe (PID: 2444)
- Antares.exe (PID: 2572)
- wscript.exe (PID: 3324)
- Whiter.exe (PID: 712)
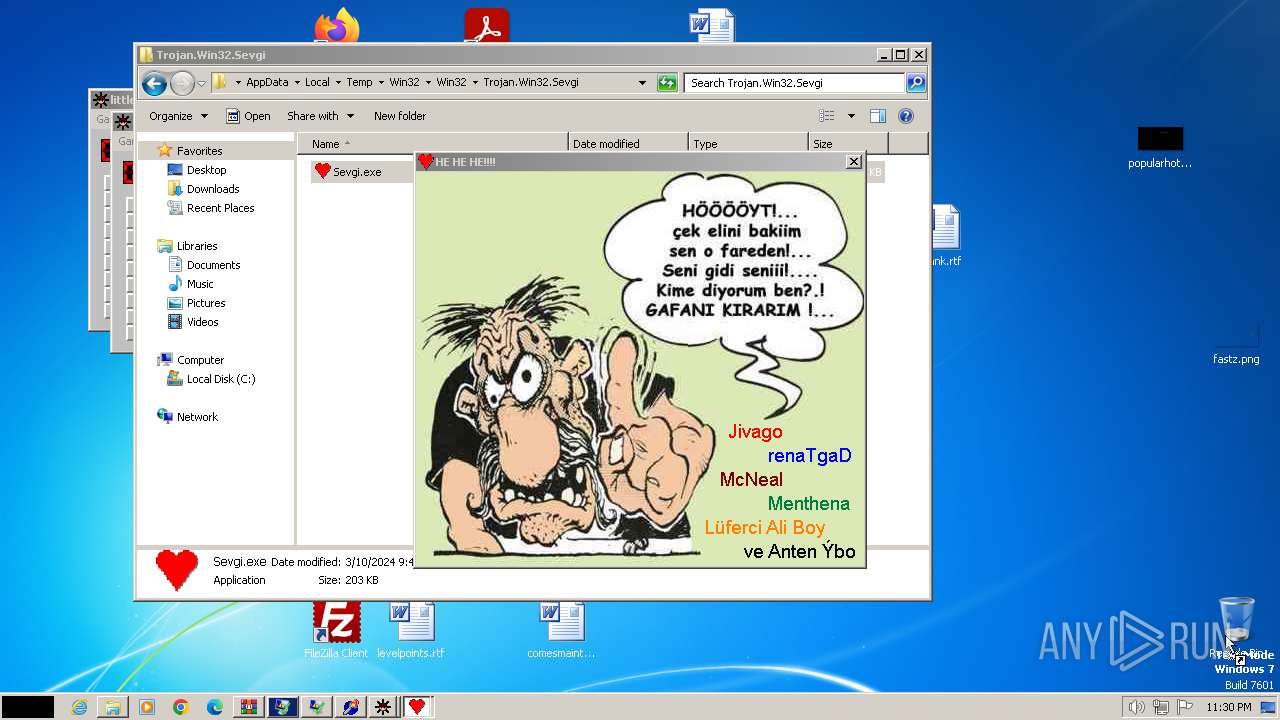
- Sevgi.exe (PID: 2308)
- Sevgi.exe (PID: 2616)
- Whiter.exe (PID: 3804)
- Rigel.exe (PID: 3408)
- Whiter.exe (PID: 3084)
- IMEKLMG.EXE (PID: 1504)
- IMEKLMG.EXE (PID: 1188)
- wmpnscfg.exe (PID: 2260)
- wmpnscfg.exe (PID: 2300)
- explorer.exe (PID: 2424)
- FakePetya.exe (PID: 2876)
- FakePetya.exe (PID: 2992)
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 3864)
Create files in a temporary directory
- not-virus_Joke.Win32.Badgame.exe (PID: 2340)
Reads the computer name
- Opaserv.exe (PID: 3164)
- not-virus_Joke.Win32.Badgame.exe (PID: 2340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:03:10 21:41:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | Win32/ |
Total processes
142
Monitored processes
36
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Users\admin\AppData\Local\Temp\Win32\Win32\Trojan.Win32.IconDance\IconDance.exe" | C:\Users\admin\AppData\Local\Temp\Win32\Win32\Trojan.Win32.IconDance\IconDance.exe | — | explorer.exe | |||||||||||
User: admin Company: Xavier LAURENT Integrity Level: MEDIUM Description: Danse des icônes Exit code: 1073807364 Version: 1.0.0.30 Modules
| |||||||||||||||
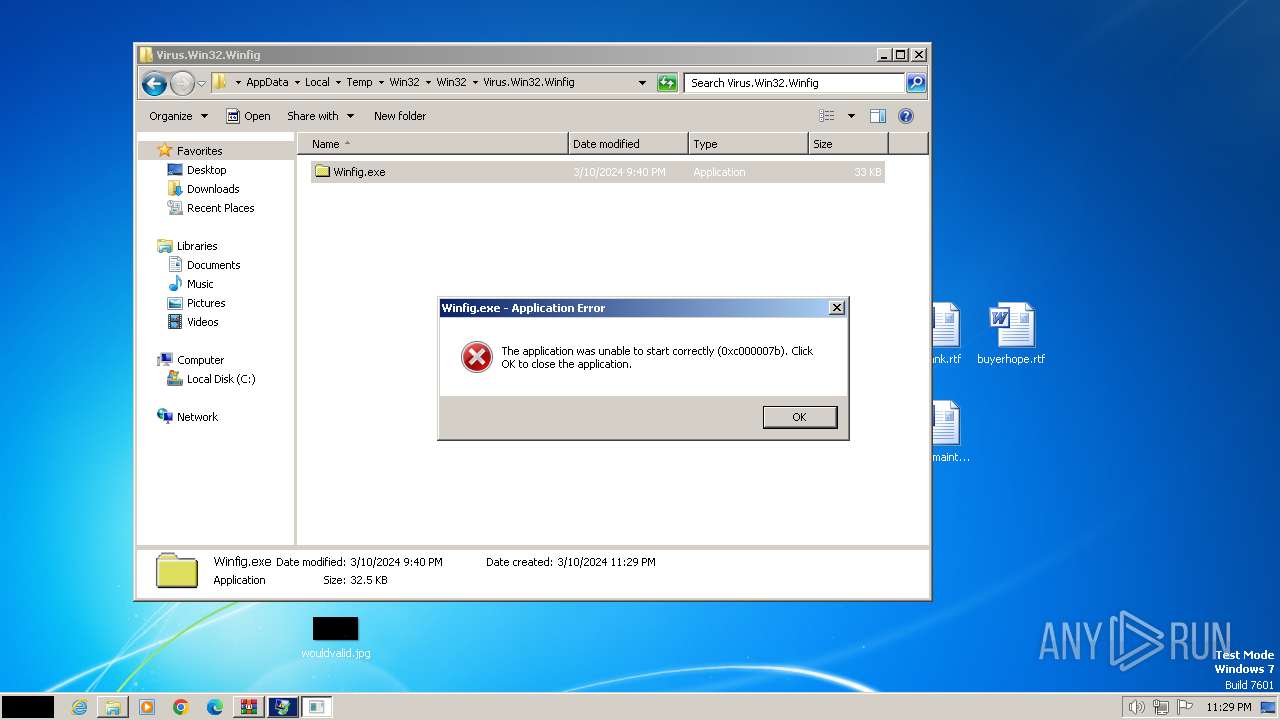
| 668 | "C:\Users\admin\AppData\Local\Temp\Win32\Win32\Virus.Win32.Winfig\Winfig.exe" | C:\Users\admin\AppData\Local\Temp\Win32\Win32\Virus.Win32.Winfig\Winfig.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225595 Version: 1.00 Modules
| |||||||||||||||
| 712 | "C:\Users\admin\AppData\Local\Temp\Win32\Win32\Trojan.Win32.Whiter\Whiter.exe" | C:\Users\admin\AppData\Local\Temp\Win32\Win32\Trojan.Win32.Whiter\Whiter.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 | |||||||||||||||
| 796 | NET STOP AVPCC | C:\Windows\System32\net.exe | — | Opaserv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 848 | NET STOP PERSFW | C:\Windows\System32\net.exe | — | Opaserv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1112 | C:\Windows\system32\net1 STOP SWEEPSRV.SYS | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1188 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 | |||||||||||||||
| 1448 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) | |||||||||||||||
| 1504 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 | |||||||||||||||
| 1572 | C:\Windows\system32\net1 STOP AVPCC | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
4 069
Read events
4 048
Write events
21
Delete events
0
Modification events
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Win32.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
17
Suspicious files
1
Text files
1 553
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Win32\Win32\Virus.Win32.Rigel\Rigel.exe | executable | |
MD5:CBE1998FFE6C8F068CC9BB635483E56F | SHA256:88D44FE77AAB69615BC105BC16F38479178157700519883403D2B95B68CF2490 | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Win32\Win32\Trojan.Win32.IconDance\IconDance.exe | executable | |
MD5:7AD8C84DEA7BD1E9CBB888734DB28961 | SHA256:A4B6E53453D1874A6F78F0D7AA14DFAFBA778062F4B85B42B4C1001E1FC17095 | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Win32\Win32\Virus.Win32.Antares\Antares.exe | executable | |
MD5:EDD7A751B4676DCD2065D7D44DD4C902 | SHA256:5BC2D85780A31474C02E92A9A5EA73A82C8EEAFE483197CDDF1D2FFEE473266B | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Win32\Win32\Trojan.Win32.Sevgi\Sevgi.exe | executable | |
MD5:B28505A8050446AF4638319060E006E9 | SHA256:750E37D1FDD64E9EA015272A0DB6720AC9A8D803DC0CAAD29D0653756A8E5B17 | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Win32\Win32\Trojan.Win32.Alerta\Alerta.exe | executable | |
MD5:E8ED8AAF35E6059BA28504C19FF50BAB | SHA256:2D2A22DB20A44474AFBD7B0E6488690BAD584DCAE9789A5DB776CC1A00B98728 | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Win32\Win32\Virus.Win32.Winfig\Winfig.exe | executable | |
MD5:C82B6D5A8496064ABB5E66A26AA6717B | SHA256:50AED187373623BE982BCAC479CF729F08BF945B0976ECC48BC4047FF67A938D | |||
| 2340 | not-virus_Joke.Win32.Badgame.exe | C:\Users\admin\AppData\Local\Temp\bad536A.tmp | binary | |
MD5:6AE417F27F9ABB907AC735A67C5DE392 | SHA256:973A2650F2ECF8861692EAFC19087067C8FFD41B7FA6C29C8B9147F56DD2FA4A | |||
| 2572 | Antares.exe | C:\Windows\Alcrmv.exe | executable | |
MD5:5DBB5F9C1C71D6F07B12C6EE1B089DB7 | SHA256:26F29C6C0580D94BF4683D2E32226969C54E54EE1301449EB3B1F9278E963498 | |||
| 2572 | Antares.exe | C:\Windows\SOUNDMAN.EXE | executable | |
MD5:D16CFC936A479C375DF2D8BDFB1933EB | SHA256:7594DB9CCF2A22AB89FE35E2A2AA09B9157E35576B19488F24DFBB3C6338F318 | |||
| 2572 | Antares.exe | C:\Windows\system32\ALSNDMGR.CPL | executable | |
MD5:D76F3217F0474AF1DDAF0BF27ED405B4 | SHA256:FF74864B49602173F4B69F77F7BD4425E38693A7596C0353923158F94B4FBB9C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
9
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 23.207.104.5:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133545871188280000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 23.207.104.5:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | JP | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |