| File name: | 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe |
| Full analysis: | https://app.any.run/tasks/3120680f-798f-44ff-9ac3-98551c5fb8f0 |
| Verdict: | Malicious activity |
| Analysis date: | July 05, 2024, 09:38:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | FCB1D3F10BAB0D68CB50FE8DBCE9DBE7 |
| SHA1: | ACA74F1767843CBE1DBD7A5310409ACC9C1D68F5 |
| SHA256: | 2B15F9988D849C591FC1639F2BA9E8005E5B32635EE2922D0A56482B81561605 |
| SSDEEP: | 393216:pWpGpfZeRL2ccU+eB8FrDlRi+09Bn3s8m9P461oM/s7EzC+sNmuJwQpMNN:pdpfZU2eB8di+NQ61DhC5HfpW |
MALICIOUS
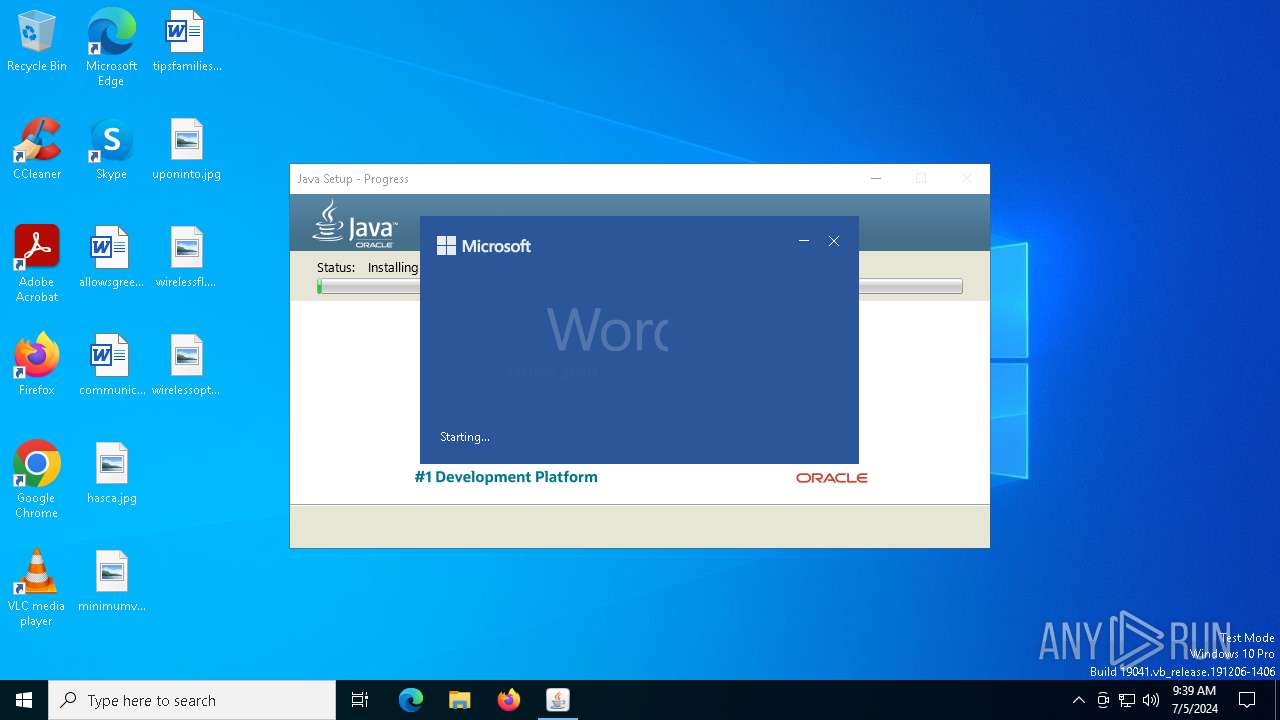
Drops the executable file immediately after the start
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6616)
- installer.exe (PID: 5532)
- msiexec.exe (PID: 2452)
Creates a writable file in the system directory
- installer.exe (PID: 5532)
SUSPICIOUS
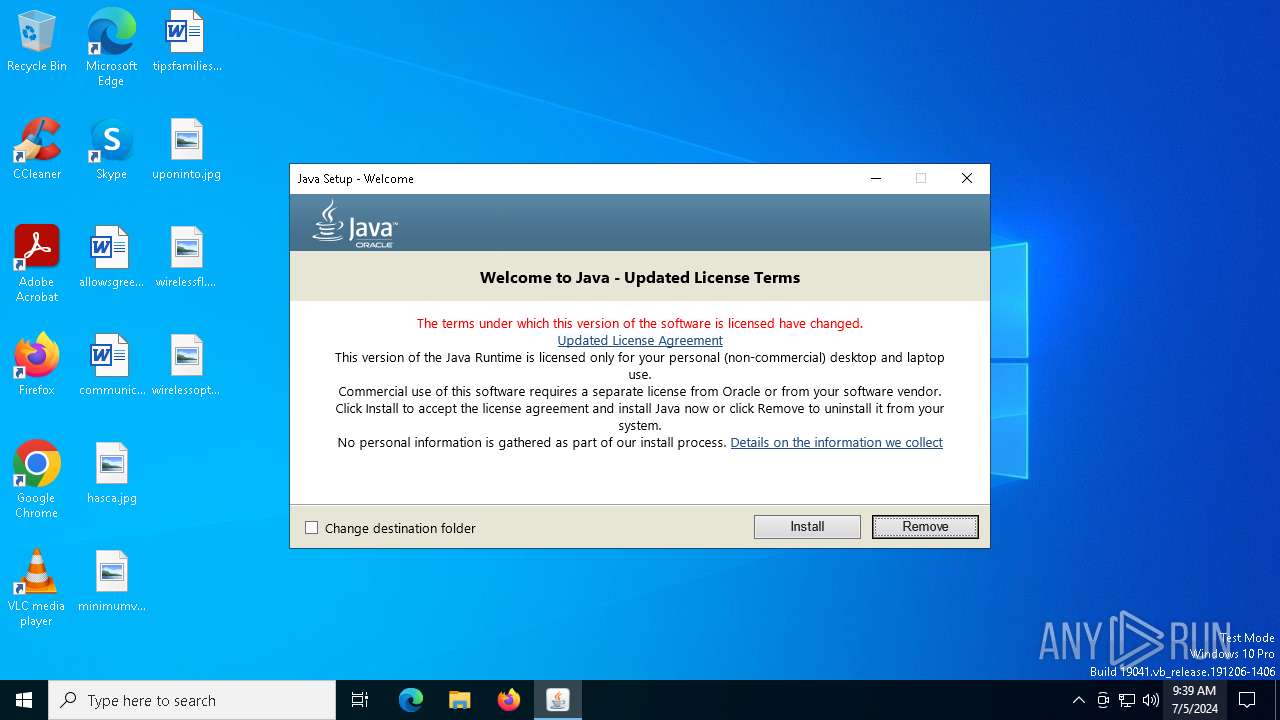
Checks for Java to be installed
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
- msiexec.exe (PID: 6752)
- msiexec.exe (PID: 2452)
- ssvagent.exe (PID: 6508)
- installer.exe (PID: 5532)
- jp2launcher.exe (PID: 6988)
- jp2launcher.exe (PID: 7244)
- javaw.exe (PID: 7556)
Reads security settings of Internet Explorer
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
- installer.exe (PID: 5532)
- jp2launcher.exe (PID: 6988)
- jp2launcher.exe (PID: 7244)
Reads Microsoft Outlook installation path
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
Checks Windows Trust Settings
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
- msiexec.exe (PID: 2452)
Reads Internet Explorer settings
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
Reads Mozilla Firefox installation path
- MSI6B78.tmp (PID: 7088)
- installer.exe (PID: 5532)
Process drops legitimate windows executable
- msiexec.exe (PID: 2452)
The process drops C-runtime libraries
- msiexec.exe (PID: 2452)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2452)
Executable content was dropped or overwritten
- installer.exe (PID: 5532)
Creates/Modifies COM task schedule object
- ssvagent.exe (PID: 6508)
- installer.exe (PID: 5532)
INFO
Reads the machine GUID from the registry
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
- msiexec.exe (PID: 2452)
Checks supported languages
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6616)
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
- msiexec.exe (PID: 2452)
- MSI6B78.tmp (PID: 7088)
- jaureg.exe (PID: 5968)
- msiexec.exe (PID: 6752)
- installer.exe (PID: 5532)
- javaw.exe (PID: 5392)
- javaws.exe (PID: 6652)
- ssvagent.exe (PID: 6508)
- javaws.exe (PID: 7224)
- jp2launcher.exe (PID: 7244)
- msiexec.exe (PID: 7416)
- javaw.exe (PID: 7556)
- jp2launcher.exe (PID: 6988)
- msiexec.exe (PID: 7676)
- javaw.exe (PID: 7724)
Create files in a temporary directory
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6616)
- MSI6B78.tmp (PID: 7088)
- javaw.exe (PID: 5392)
- jp2launcher.exe (PID: 6988)
- jp2launcher.exe (PID: 7244)
Reads the computer name
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6616)
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
- msiexec.exe (PID: 2452)
- MSI6B78.tmp (PID: 7088)
- installer.exe (PID: 5532)
- msiexec.exe (PID: 6752)
- javaws.exe (PID: 6652)
- jp2launcher.exe (PID: 6988)
- javaws.exe (PID: 7224)
- msiexec.exe (PID: 7416)
- jp2launcher.exe (PID: 7244)
- javaw.exe (PID: 7556)
- msiexec.exe (PID: 7676)
- javaw.exe (PID: 7724)
Creates files or folders in the user directory
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
- msiexec.exe (PID: 2452)
Checks proxy server information
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
- jp2launcher.exe (PID: 7244)
- jp2launcher.exe (PID: 6988)
Reads Environment values
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
Reads the software policy settings
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
- msiexec.exe (PID: 2452)
Process checks Internet Explorer phishing filters
- 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe (PID: 6884)
Manual execution by a user
- WINWORD.EXE (PID: 5380)
Application launched itself
- msiexec.exe (PID: 2452)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2452)
Starts application with an unusual extension
- msiexec.exe (PID: 2452)
Reads CPU info
- msiexec.exe (PID: 2452)
Creates files in the program directory
- installer.exe (PID: 5532)
- javaw.exe (PID: 5392)
Reads Microsoft Office registry keys
- installer.exe (PID: 5532)
Creates a software uninstall entry
- msiexec.exe (PID: 2452)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (53.4) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (35.5) |
| .exe | | | Win32 Executable (generic) (5.8) |
| .exe | | | Generic Win/DOS Executable (2.5) |
| .exe | | | DOS Executable Generic (2.5) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:03:13 08:05:42+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.31 |
| CodeSize: | 253440 |
| InitializedDataSize: | 68533760 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x18fe4 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.0.4110.9 |
| ProductVersionNumber: | 8.0.4110.9 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Oracle Corporation |
| FileDescription: | Java Platform SE binary |
| FileVersion: | 8.0.4110.9 |
| FullVersion: | 1.8.0_411-b09 |
| InternalName: | Setup Launcher |
| LegalCopyright: | Copyright © 2024 |
| OriginalFileName: | wrapper_jre_offline.exe |
| ProductName: | Java Platform SE 8 U411 |
| ProductVersion: | 8.0.4110.9 |
Total processes
162
Monitored processes
24
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2052 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2452 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4452 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "1DA9B206-97D2-46B6-AFAE-104D3990CF6D" "3873DD46-8443-44E8-AC19-0E0CB41B395F" "5380" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 4860 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5380 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\allowsgreen.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5392 | "C:\Program Files\Java\jre-1.8\bin\javaw.exe" -Xshare:dump -Djdk.disableLastUsageTracking | C:\Program Files\Java\jre-1.8\bin\javaw.exe | installer.exe | ||||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.4110.9 Modules
| |||||||||||||||
| 5532 | "C:\Program Files\Java\jre-1.8\installer.exe" /s INSTALLDIR="C:\Program Files\Java\jre-1.8\\" INSTALL_SILENT=1 AUTO_UPDATE=0 SPONSORS=0 REPAIRMODE=0 ProductCode={77924AE4-039E-4CA4-87B4-2F64180411F0} | C:\Program Files\Java\jre-1.8\installer.exe | msiexec.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.4110.9 Modules
| |||||||||||||||
| 5584 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | jaureg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5968 | "C:\Program Files (x86)\Common Files\Java\Java Update\jaureg.exe" -u auto-update | C:\Program Files (x86)\Common Files\Java\Java Update\jaureg.exe | MSI6B78.tmp | ||||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java Update Registration Version: 2.8.271.9 Modules
| |||||||||||||||
| 6356 | "C:\Users\admin\AppData\Local\Temp\2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe" | C:\Users\admin\AppData\Local\Temp\2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Platform SE binary Exit code: 3221226540 Version: 8.0.4110.9 Modules
| |||||||||||||||
Total events
60 712
Read events
33 649
Write events
12 653
Delete events
14 410
Modification events
| (PID) Process: | (6884) 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft |
| Operation: | delete value | Name: | InstallStatus |
Value: | |||
| (PID) Process: | (6884) 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6884) 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6884) 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6884) 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6884) 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6884) 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6884) 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6884) 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | Country |
Value: DE | |||
| (PID) Process: | (6884) 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
Executable files
341
Suspicious files
211
Text files
248
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6616 | 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | C:\Users\admin\AppData\Local\Temp\jds1912781.tmp\jds1912781.tmp | — | |
MD5:— | SHA256:— | |||
| 6616 | 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | C:\Users\admin\AppData\Local\Temp\jds1912781.tmp\2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | — | |
MD5:— | SHA256:— | |||
| 6884 | 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_411_x64\jre1.8.0_41164.msi | — | |
MD5:— | SHA256:— | |||
| 2452 | msiexec.exe | C:\WINDOWS\Installer\1d5b03.msi | — | |
MD5:— | SHA256:— | |||
| 6616 | 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | C:\Users\admin\AppData\Local\Temp\jusched.log | text | |
MD5:A5A78C8847A0C20F445BECCD2002E2CC | SHA256:2AC4E8DC95889CF2DCA2637069A4CE5152A493134285D1ADA2F3B47EBC2965E4 | |||
| 6884 | 2b15f9988d849c591fc1639f2ba9e8005e5b32635ee2922d0a56482b81561605.exe | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_411_x64\Java3BillDevices.png | image | |
MD5:8E52EFC6798ED074072F527309A1BA25 | SHA256:12491EBC4EB99BF014D3BC44F770114BDE013E84CBEC2633303559A8C6E5F991 | |||
| 2452 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:8E363443549111FE84076AFCD4076C49 | SHA256:0D382DFBAB5FFE48235299ACD49AD6C51D2451649B0F9D395671E6CA5F6C6ECA | |||
| 2452 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:20DD2F2A1D093D9AF285489B784E5698 | SHA256:0A3FB699ECBEACF681351BF5E72FBAB63D34944CF1F8FC09DEB6C97F1B9773AA | |||
| 2452 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:D17B6852B198F5E7D56FF19B51239940 | SHA256:EDB402BFCDFD2F3BD27F5CE51B9D4151B8898497E7E70B9BA6C92B80B6B39E16 | |||
| 2452 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:04DC8658585FB8C5CE3BED30BC267FC4 | SHA256:A2156AB261F278F7EE31E45CDCC69E1E2F2694E898A01EA1A460BB4197796A31 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
136
DNS requests
41
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4084 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
2452 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | unknown |
6520 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2452 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | unknown |
5380 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | unknown |
6600 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2452 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAYOL4%2BeG4vlGNX%2BK2nPzLE%3D | unknown | — | — | unknown |
5380 | WINWORD.EXE | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | unknown |
5380 | WINWORD.EXE | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | unknown |
5380 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1888 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1888 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2088 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3656 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4656 | SearchApp.exe | 2.23.209.185:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
javadl-esd-secure.oracle.com |
| whitelisted |
rps-svcs.oracle.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|