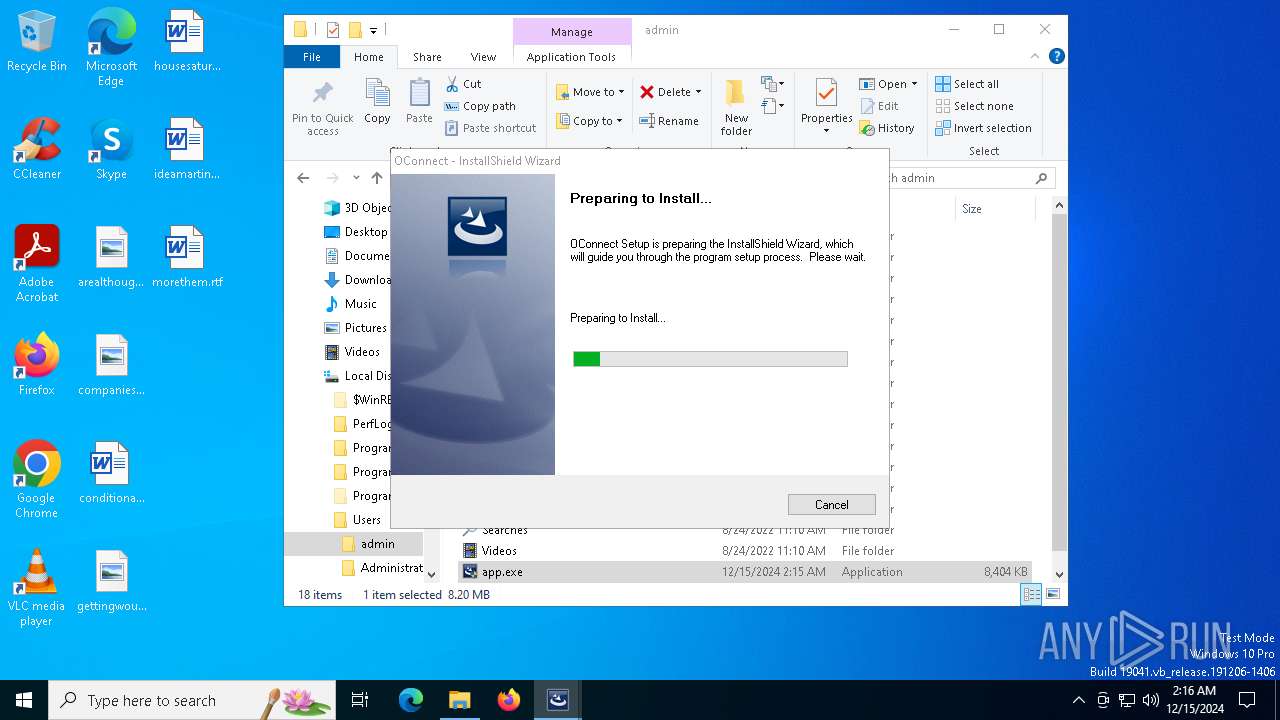
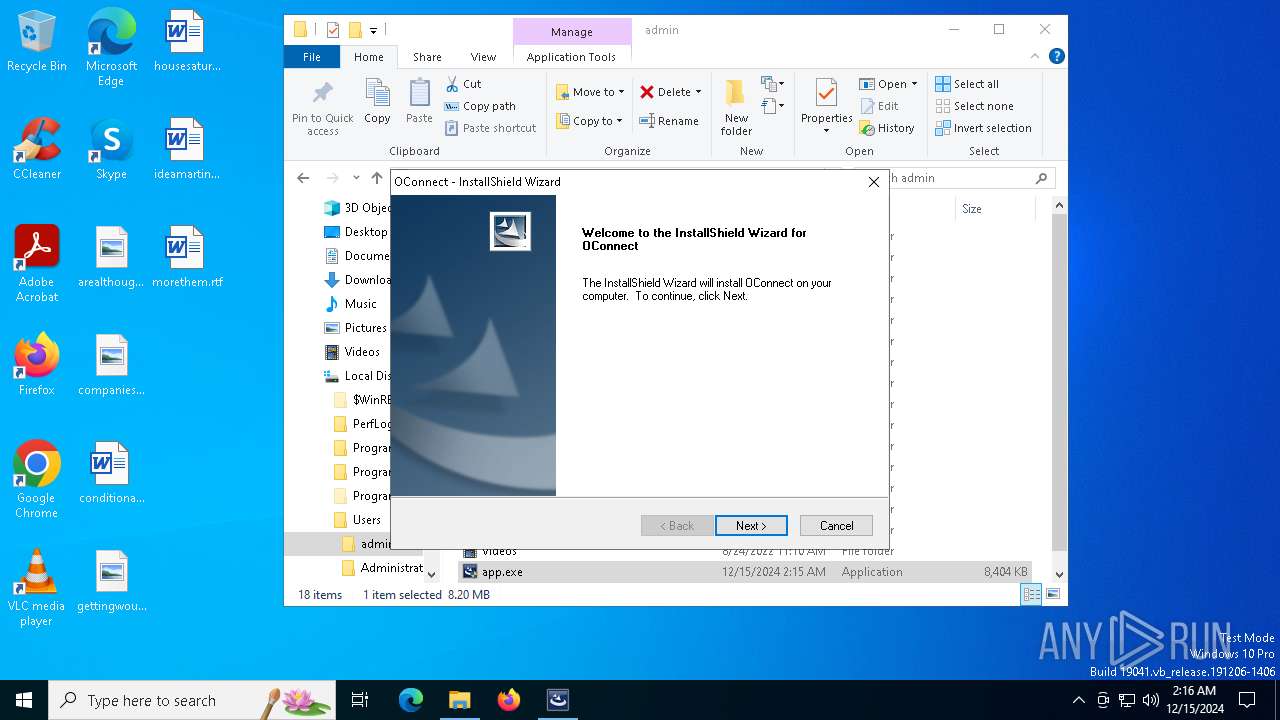
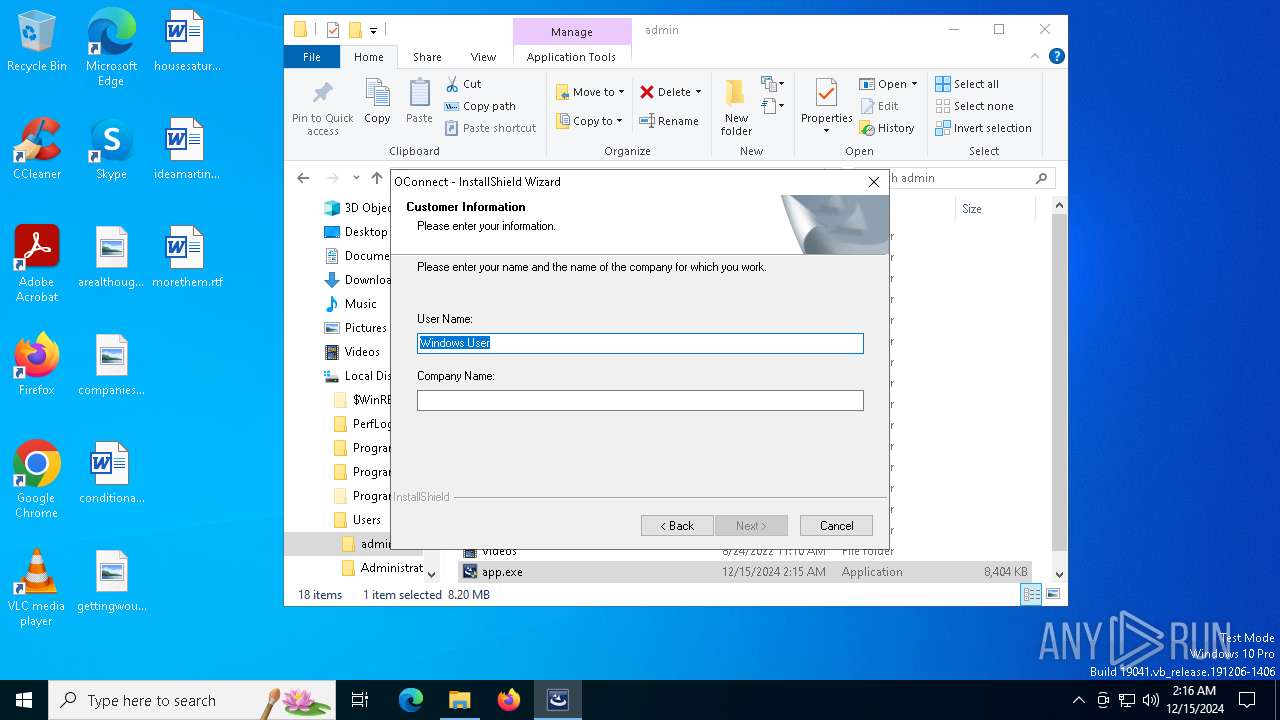
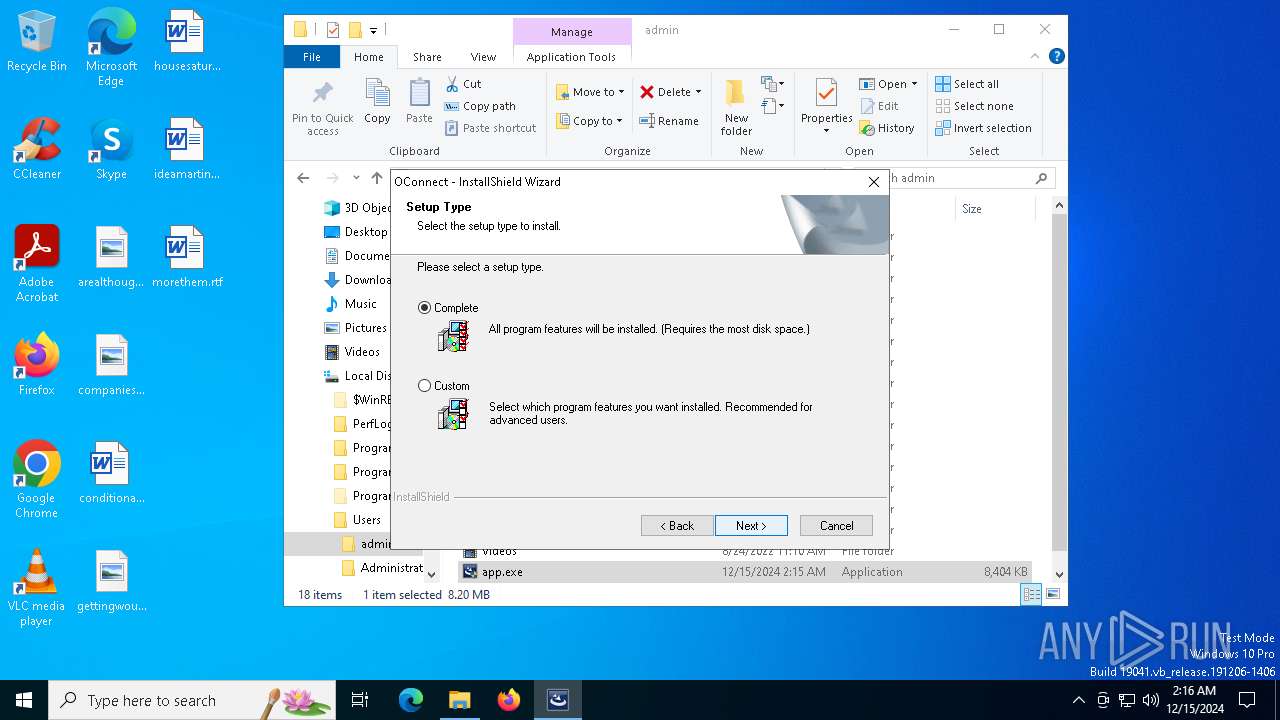
| File name: | app.exe |
| Full analysis: | https://app.any.run/tasks/93b50d82-9325-4723-8551-ea394eacf302 |
| Verdict: | Malicious activity |
| Analysis date: | December 15, 2024, 02:15:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 57ECE16B37DBDAC6E714CA391AEABB13 |
| SHA1: | 5E82C0A3BD381DBD60C2D8EC5BABECFC9A0F1091 |
| SHA256: | 2B1508BA0570C9842E4128FEB9C8EE35C2E99AC8A76B37E0A221C883BE48E91E |
| SSDEEP: | 98304:VnI8ZRtCk4weIL+PxMJKlyyaiCBGxLdJcGK8fHwH9rgcOgzreD1ggOFyxXX0yZ+g:N3GKpp/txKxT8BikI |
MALICIOUS
Executing a file with an untrusted certificate
- ISBEW64.exe (PID: 1296)
SUSPICIOUS
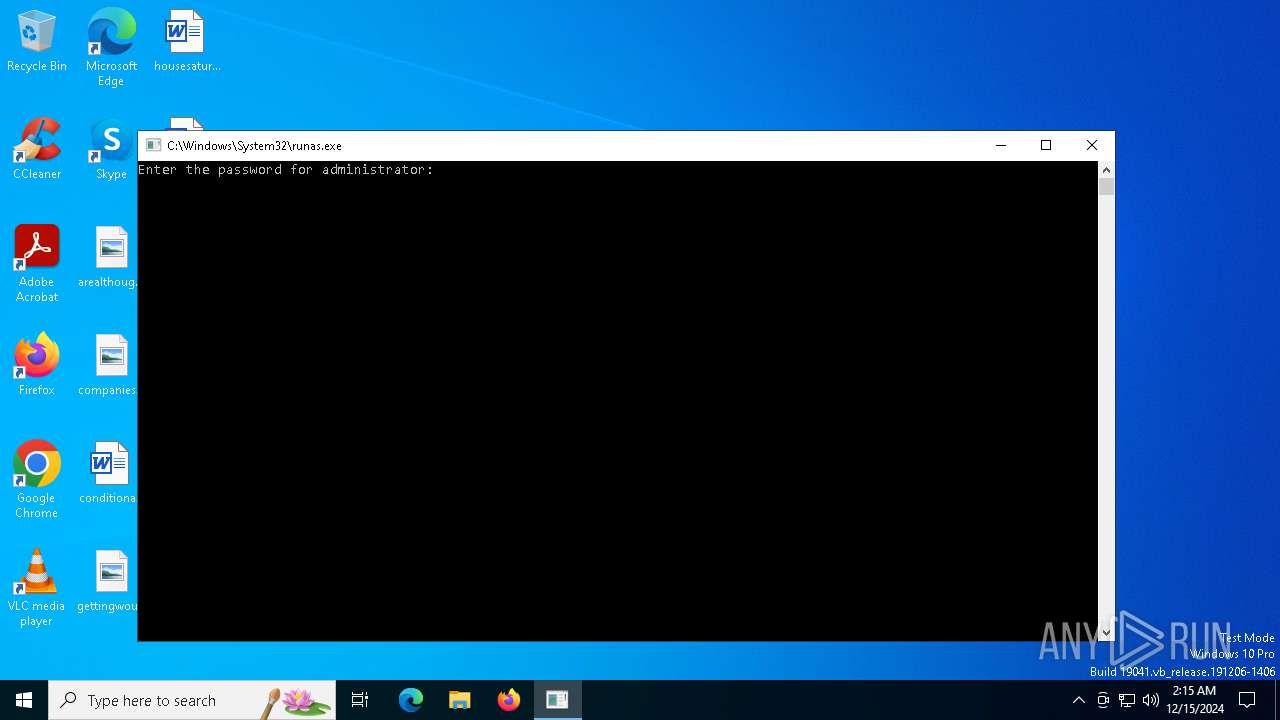
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 2456)
Executable content was dropped or overwritten
- app.exe (PID: 5604)
- netcfg.exe (PID: 1200)
- drvinst.exe (PID: 1540)
Reads the Windows owner or organization settings
- app.exe (PID: 5604)
Searches for installed software
- dllhost.exe (PID: 396)
- app.exe (PID: 5604)
Executes as Windows Service
- VSSVC.exe (PID: 4556)
Process drops legitimate windows executable
- msiexec.exe (PID: 2744)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 2744)
- netcfg.exe (PID: 1200)
- drvinst.exe (PID: 1540)
Creates a software uninstall entry
- app.exe (PID: 5604)
Starts a Microsoft application from unusual location
- ocupdater.exe (PID: 4500)
Checks Windows Trust Settings
- drvinst.exe (PID: 1540)
INFO
The sample compiled with english language support
- runas.exe (PID: 2456)
- app.exe (PID: 5604)
- msiexec.exe (PID: 2744)
Reads the computer name
- msiexec.exe (PID: 2744)
- app.exe (PID: 5604)
- ISBEW64.exe (PID: 1296)
- drvinst.exe (PID: 1540)
Manual execution by a user
- app.exe (PID: 5604)
- app.exe (PID: 5748)
Checks supported languages
- app.exe (PID: 5604)
- msiexec.exe (PID: 2744)
- ISBEW64.exe (PID: 1296)
- drvinst.exe (PID: 1540)
Create files in a temporary directory
- app.exe (PID: 5604)
Manages system restore points
- SrTasks.exe (PID: 648)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2744)
Creates a software uninstall entry
- msiexec.exe (PID: 2744)
Reads the software policy settings
- drvinst.exe (PID: 1540)
Reads the machine GUID from the registry
- drvinst.exe (PID: 1540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (54.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (34.8) |
| .exe | | | Win32 Executable (generic) (5.6) |
| .exe | | | Generic Win/DOS Executable (2.5) |
| .exe | | | DOS Executable Generic (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:09:22 04:58:50+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 563200 |
| InitializedDataSize: | 423424 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6984b |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 16.0.0.400 |
| ProductVersionNumber: | 16.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | star |
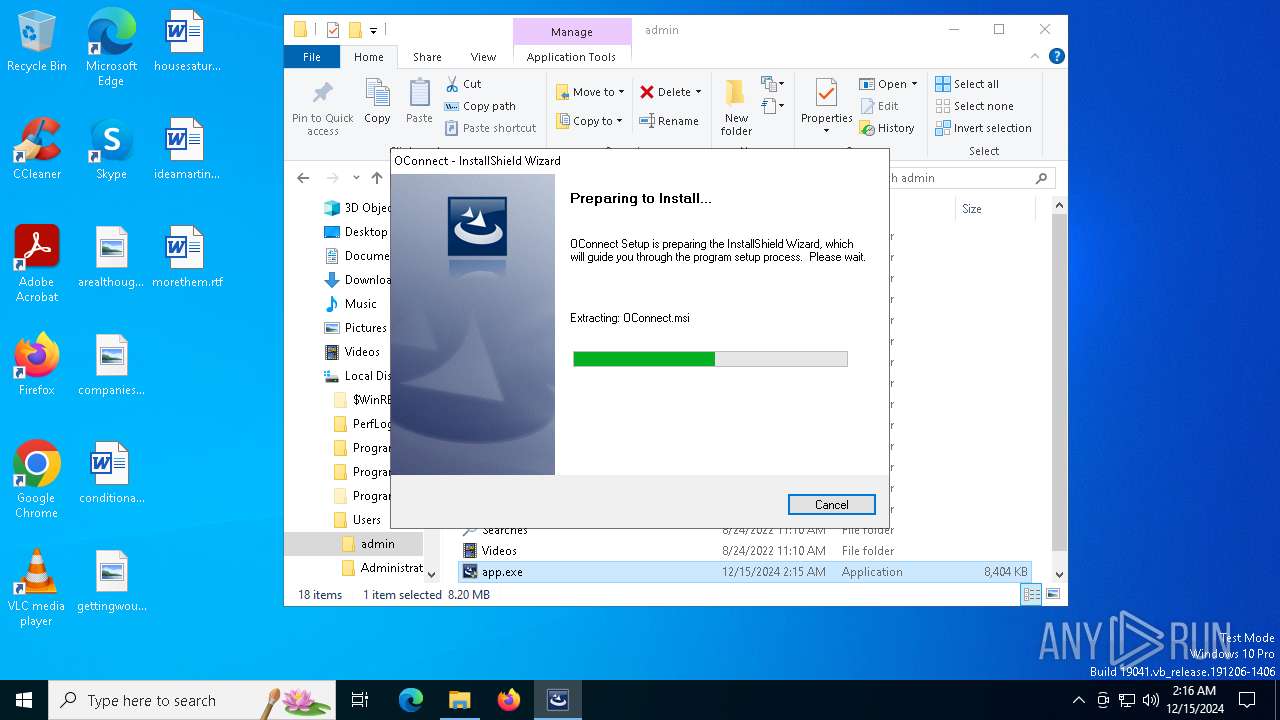
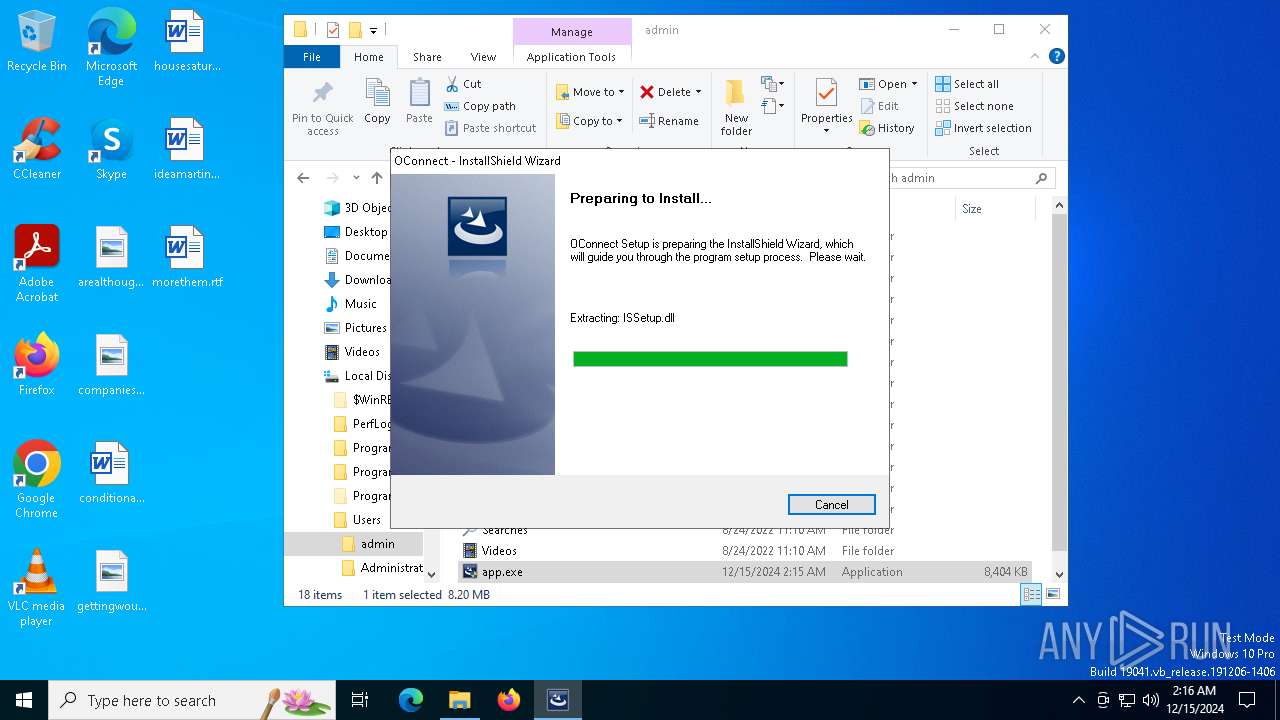
| FileDescription: | Setup Launcher |
| FileVersion: | 5.8 |
| InternalName: | Setup |
| LegalCopyright: | Copyright (C) 2009 Acresso Software Inc. and/or InstallShield Co. Inc. All Rights Reserved. |
| OriginalFileName: | Setup.exe |
| ProductName: | OConnect |
| ProductVersion: | 5.8 |
| InternalBuildNumber: | 92881 |
Total processes
140
Monitored processes
19
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 648 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | C:\WINDOWS\\sysnative\netcfg.exe -l C:\WINDOWS\\syswow64\temp\ndisrd_lwf.inf -c s -i nt_ndisrd | C:\Windows\System32\netcfg.exe | app.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WinPE network installer Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1224 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netcfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | C:\Users\admin\AppData\Local\Temp\{9D8226D1-CACF-4A23-B009-DED32536A977}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{6239B91E-958D-4E71-9474-08FC195B6A2E} | C:\Users\admin\AppData\Local\Temp\{9D8226D1-CACF-4A23-B009-DED32536A977}\ISBEW64.exe | — | app.exe | |||||||||||
User: admin Company: Acresso Software Inc. Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Version: 16.0.328 Modules
| |||||||||||||||
| 1540 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{b35eadc4-f831-1f45-8fe2-253cb6317b8e}\ndisrd_lwf.inf" "9" "41b779883" "00000000000001D0" "WinSta0\Default" "00000000000001E0" "208" "C:\WINDOWS\syswow64\temp" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | runas.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\app.exe | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2744 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 415
Read events
6 094
Write events
304
Delete events
17
Modification events
| (PID) Process: | (5604) app.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F5911F5E974EDB01E4150000400A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (396) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000F5911F5E974EDB018C01000084000000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (396) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000065F85F5E974EDB018C01000084000000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (396) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000065F85F5E974EDB018C01000084000000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (396) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000275C625E974EDB018C01000084000000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (396) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000009923675E974EDB018C01000084000000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (396) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (396) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000FDCAD45E974EDB018C01000084000000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4556) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000009B21E35E974EDB01CC11000044130000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4556) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000009B21E35E974EDB01CC110000F80E0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
26
Suspicious files
43
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5604 | app.exe | C:\Users\admin\AppData\Local\Temp\_isD672.tmp | — | |
MD5:— | SHA256:— | |||
| 5604 | app.exe | C:\Users\admin\AppData\Local\Temp\{379D5F4C-DB47-48EC-9757-8833E2634183}\OConnect.msi | — | |
MD5:— | SHA256:— | |||
| 5604 | app.exe | C:\Users\admin\AppData\Local\Temp\_isD5C2.tmp | binary | |
MD5:4278EB0F1D8EE6231AEEE812F423ACE0 | SHA256:B70C3A70E6BC16A0D92B2E238D9A48053D42A5FA29CD5A0809F8A82FE0233C7D | |||
| 5604 | app.exe | C:\Users\admin\AppData\Local\Temp\_isE0B7.tmp | binary | |
MD5:3BFB0B343C9506BEE9A8C5A5090F6992 | SHA256:192741BEA0D0537A1625D5CFE5618F30908D519C6E8E02801A3866F073AEE4D9 | |||
| 5604 | app.exe | C:\Users\admin\AppData\Local\Temp\{379D5F4C-DB47-48EC-9757-8833E2634183}\Setup.INI | text | |
MD5:BE102B49CFEDC06873FCF3554C6D7CDD | SHA256:E2A66313E4BC607A2F2FEDB338B4FB11B4FF1AF3774BD268BB188A0724E691EA | |||
| 5604 | app.exe | C:\Users\admin\AppData\Local\Temp\{379D5F4C-DB47-48EC-9757-8833E2634183}\_ISMSIDEL.INI | text | |
MD5:CF4F83BC92B87C12E0720E0D10D9318B | SHA256:5984D87C05AFCF4F7C2BE90A0032D5201839910B4EAB4EAFC274EB66A45B154B | |||
| 396 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2744 | msiexec.exe | C:\Windows\Installer\143c7b.msi | — | |
MD5:— | SHA256:— | |||
| 5604 | app.exe | C:\Users\admin\AppData\Local\Temp\_isE096.tmp | binary | |
MD5:56E8DB7CABEB22212EA61D7F70E381C1 | SHA256:B4AD36F9B7A15B4F4184704F1EB51320DF158970743FAF0A4566F1281D2AA1FA | |||
| 5604 | app.exe | C:\Users\admin\AppData\Local\Temp\{9D8226D1-CACF-4A23-B009-DED32536A977}\ISRT.dll | executable | |
MD5:ED5AA645392883B21507C8D097FDA277 | SHA256:613D91093EB5FEC10CF56DA5C33C8C66EE8EABA8C81319CEDD9D73C1CE9DCE22 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
14
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.79.89.142:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 104.79.89.142:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.79.89.142:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.55.110.211:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.55.110.211:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 104.79.89.142:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 104.79.89.142:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2736 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |