| File name: | eduroam-W10-UPC.exe |
| Full analysis: | https://app.any.run/tasks/202b8cf7-cf53-41d5-a4be-489a45bc1f00 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 01:15:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, 8 sections |
| MD5: | 313B366F410DF63AACCB22FD52A863B6 |
| SHA1: | A1187A019F3E73BF86A681A7E0FCC8CB335DA0B5 |
| SHA256: | 2B12A5857BD1384A05E35A2DFA3A643D7DA81588FD08A7767797E7E2DE104D48 |
| SSDEEP: | 12288:I7G+38+trIqvMMrM4OPnl05CtctqKiN2g3JOb:x+JtrIqvMMrnOPnlMCtctpiN24JOb |
MALICIOUS
Executing a file with an untrusted certificate
- eduroam-W10-UPC.exe (PID: 7384)
SUSPICIOUS
Executable content was dropped or overwritten
- eduroam-W10-UPC.exe (PID: 7384)
Malware-specific behavior (creating "System.dll" in Temp)
- eduroam-W10-UPC.exe (PID: 7384)
The process creates files with name similar to system file names
- eduroam-W10-UPC.exe (PID: 7384)
INFO
The sample compiled with french language support
- eduroam-W10-UPC.exe (PID: 7384)
Checks supported languages
- eduroam-W10-UPC.exe (PID: 7384)
- wlan_test.exe (PID: 7412)
The sample compiled with english language support
- eduroam-W10-UPC.exe (PID: 7384)
Create files in a temporary directory
- eduroam-W10-UPC.exe (PID: 7384)
Reads the computer name
- wlan_test.exe (PID: 7412)
- eduroam-W10-UPC.exe (PID: 7384)
Checks proxy server information
- slui.exe (PID: 4408)
Reads the software policy settings
- slui.exe (PID: 4408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:12:04 09:14:19+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.37 |
| CodeSize: | 36864 |
| InitializedDataSize: | 48640 |
| UninitializedDataSize: | 3794944 |
| EntryPoint: | 0x44da |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.1.3.0 |
| ProductVersionNumber: | 2.1.3.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | French |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | GÉANT |
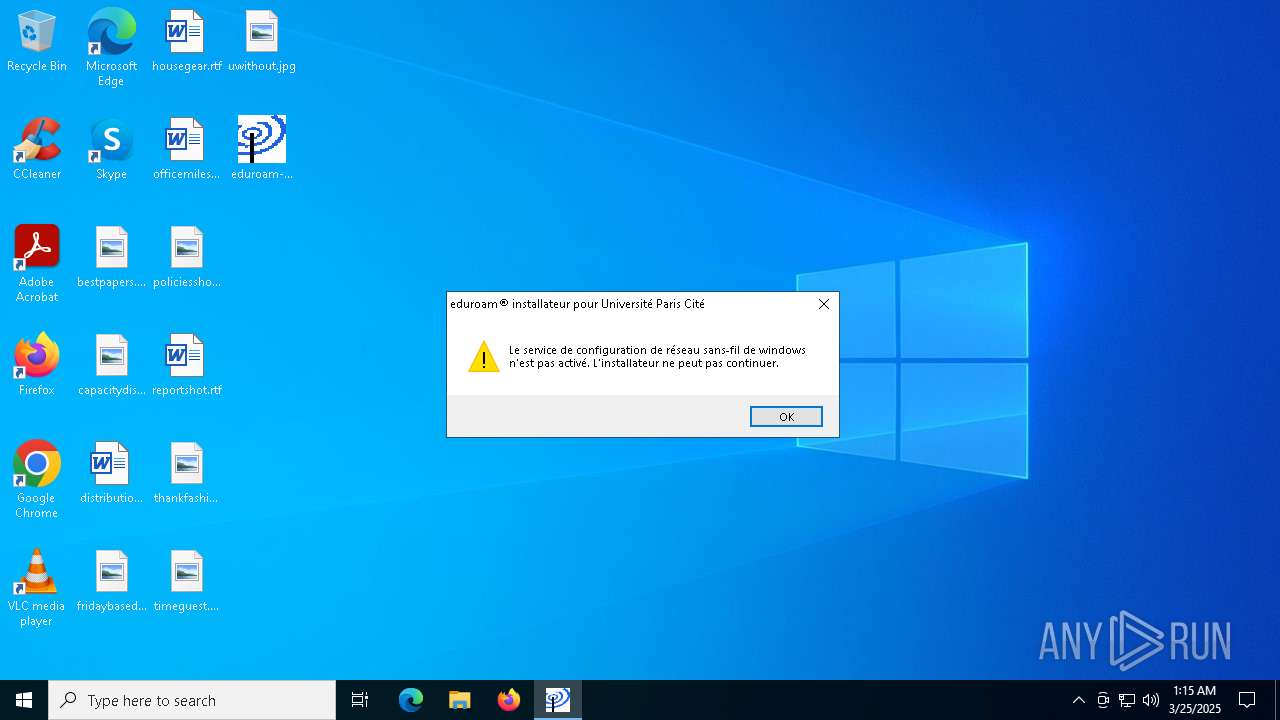
| FileDescription: | eduroam® installateur pour Université Paris Cité |
| ProductName: | eduroam® installateur pour Université Paris Cité |
| ProductVersion: | 2.1.3 |
Total processes
137
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4408 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7384 | "C:\Users\admin\Desktop\eduroam-W10-UPC.exe" | C:\Users\admin\Desktop\eduroam-W10-UPC.exe | explorer.exe | ||||||||||||
User: admin Company: GÉANT Integrity Level: MEDIUM Description: eduroam® installateur pour Université Paris Cité Exit code: 2 Modules
| |||||||||||||||
| 7412 | C:\Users\admin\AppData\Local\Temp\wlan_test.exe | C:\Users\admin\AppData\Local\Temp\wlan_test.exe | — | eduroam-W10-UPC.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 7420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wlan_test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 473
Read events
3 473
Write events
0
Delete events
0
Modification events
Executable files
5
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7384 | eduroam-W10-UPC.exe | C:\Users\admin\AppData\Local\Temp\nszC130.tmp\nsArray.dll | executable | |
MD5:DA4BC09439ED21FAF7620A53433AAC92 | SHA256:216D68D3F0B37BB2203B3A438A84A089E8C388608F46377AD7E7D6A2709CF9B0 | |||
| 7384 | eduroam-W10-UPC.exe | C:\Users\admin\AppData\Local\Temp\nszC130.tmp\nsExec.dll | executable | |
MD5:7C0DC12CDC807A3BB4AFDA989A663F95 | SHA256:0D022CC0AA60A3F41DBEB6776E9ACB016FF3D42396E3371F15CC22352E621EB5 | |||
| 7384 | eduroam-W10-UPC.exe | C:\Users\admin\AppData\Local\Temp\wlan_test.exe | executable | |
MD5:40BCA6124FA7EEF106C0D76C428D9471 | SHA256:FC03209D76E6C41C11DDE8621F1EB03FF348A12566CB9B63E7AA2D6CEF8086AA | |||
| 7384 | eduroam-W10-UPC.exe | C:\Users\admin\AppData\Local\Temp\nszC130.tmp\System.dll | executable | |
MD5:26C8A92678F1B970AC2A700BB844C309 | SHA256:2A7B5D1CAB96A5280B0694D0ED54510129626A1BA36A51BD34D546972B7D18B8 | |||
| 7384 | eduroam-W10-UPC.exe | C:\Users\admin\AppData\Local\Temp\cat_background.bmp | image | |
MD5:ADC03705136D6A3718094C52299465ED | SHA256:B7D55CDD0D4808BB7EE10AC5BAF8F1962FEB67549C7CB8C212A5A1DF35D46C20 | |||
| 7384 | eduroam-W10-UPC.exe | C:\Users\admin\AppData\Local\Temp\nszC130.tmp\LangDLL.dll | executable | |
MD5:E5240DCD169ABE69A7332D01106E1D84 | SHA256:96C40847D52270061C25743BC9EC4843BE1991F3AC36C2D1B78EC04A04437EA4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
52
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5024 | RUXIMICS.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8156 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 4.175.87.197:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 200 | 20.190.160.131:443 | https://login.live.com/RST2.srf | unknown | xml | 1.35 Kb | whitelisted |
— | — | GET | 200 | 20.223.35.26:443 | https://arc.msn.com/v3/Delivery/Placement?pubid=da63df93-3dbc-42ae-a505-b34988683ac7&pid=280815&adm=2&w=1&h=1&wpx=1&hpx=1&fmt=json&cltp=app&dim=le&rafb=0&nct=1&pm=1&cfmt=text,image,poly&sft=jpeg,png,gif&topt=1&poptin=0&localid=w:AC7699B0-48EA-FD22-C8DC-06A02098A0F0&ctry=US&time=20250325T011517Z&lc=en-US&pl=en-US&idtp=mid&uid=9115d6d1-9f4e-4053-9297-2a8c833b3912&aid=00000000-0000-0000-0000-000000000000&ua=WindowsShellClient%2F9.0.40929.0%20%28Windows%29&asid=e394452f72de4aa889aac1916bc639de&ctmode=MultiSession&arch=x64&betaedgever=0.0.0.0&canedgever=0.0.0.0&cdm=1&cdmver=10.0.19041.3636&currsel=137271744000000000&devedgever=0.0.0.0&devfam=Windows.Desktop&devform=Unknown&devosver=10.0.19045.4046&disphorzres=1280&dispsize=15.3&dispvertres=720&fosver=16299&isu=0&lo=3968234&metered=false&nettype=ethernet&npid=sc-280815&oemName=DELL&oemid=DELL&ossku=Professional&prevosver=15063&smBiosDm=DELL&stabedgever=122.0.2365.59&tl=2&tsu=1358764&waasBldFlt=1&waasCfgExp=1&waasCfgSet=1&waasRetail=1&waasRing=&svoffered=2 | unknown | binary | 2.95 Kb | whitelisted |
— | — | POST | 400 | 40.126.32.76:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 200 | 40.126.32.134:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
8156 | SIHClient.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 20.31.169.57:443 | https://arc.msn.com/v3/Delivery/Placement?pubid=da63df93-3dbc-42ae-a505-b34988683ac7&pid=280815&adm=2&w=1&h=1&wpx=1&hpx=1&fmt=json&cltp=app&dim=le&rafb=0&nct=1&pm=1&cfmt=text,image,poly&sft=jpeg,png,gif&topt=1&poptin=0&localid=w:AC7699B0-48EA-FD22-C8DC-06A02098A0F0&ctry=US&time=20250325T011528Z&lc=en-US&pl=en-US&idtp=mid&uid=9115d6d1-9f4e-4053-9297-2a8c833b3912&aid=00000000-0000-0000-0000-000000000000&ua=WindowsShellClient%2F9.0.40929.0%20%28Windows%29&asid=099c2e9a1b784de0ac70dbf3cf5f1507&ctmode=MultiSession&arch=x64&betaedgever=0.0.0.0&canedgever=0.0.0.0&cdm=1&cdmver=10.0.19041.3636&currsel=137271744000000000&devedgever=0.0.0.0&devfam=Windows.Desktop&devform=Unknown&devosver=10.0.19045.4046&disphorzres=1280&dispsize=15.3&dispvertres=720&fosver=16299&isu=0&lo=3968234&metered=false&nettype=ethernet&npid=sc-280815&oemName=DELL&oemid=DELL&ossku=Professional&prevosver=15063&smBiosDm=DELL&stabedgever=122.0.2365.59&tl=2&tsu=1358764&waasBldFlt=1&waasCfgExp=1&waasCfgSet=1&waasRetail=1&waasRing=&svoffered=2 | unknown | binary | 2.96 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5024 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5024 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |