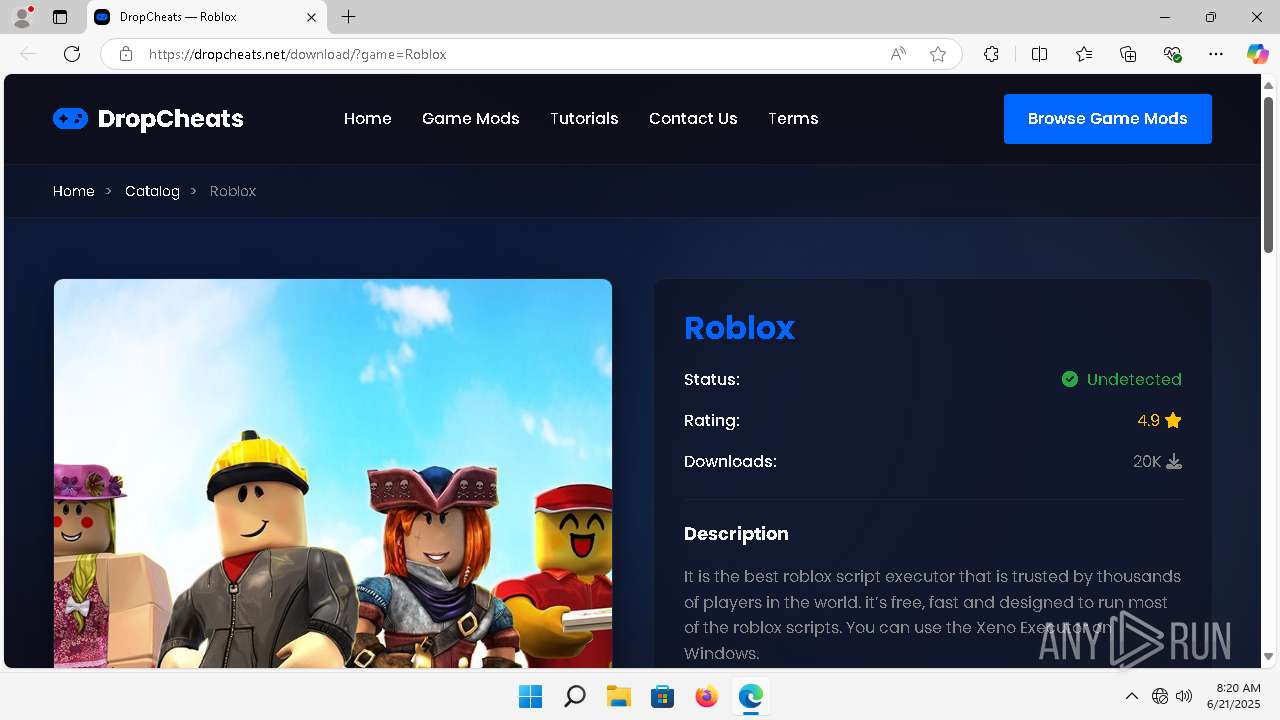
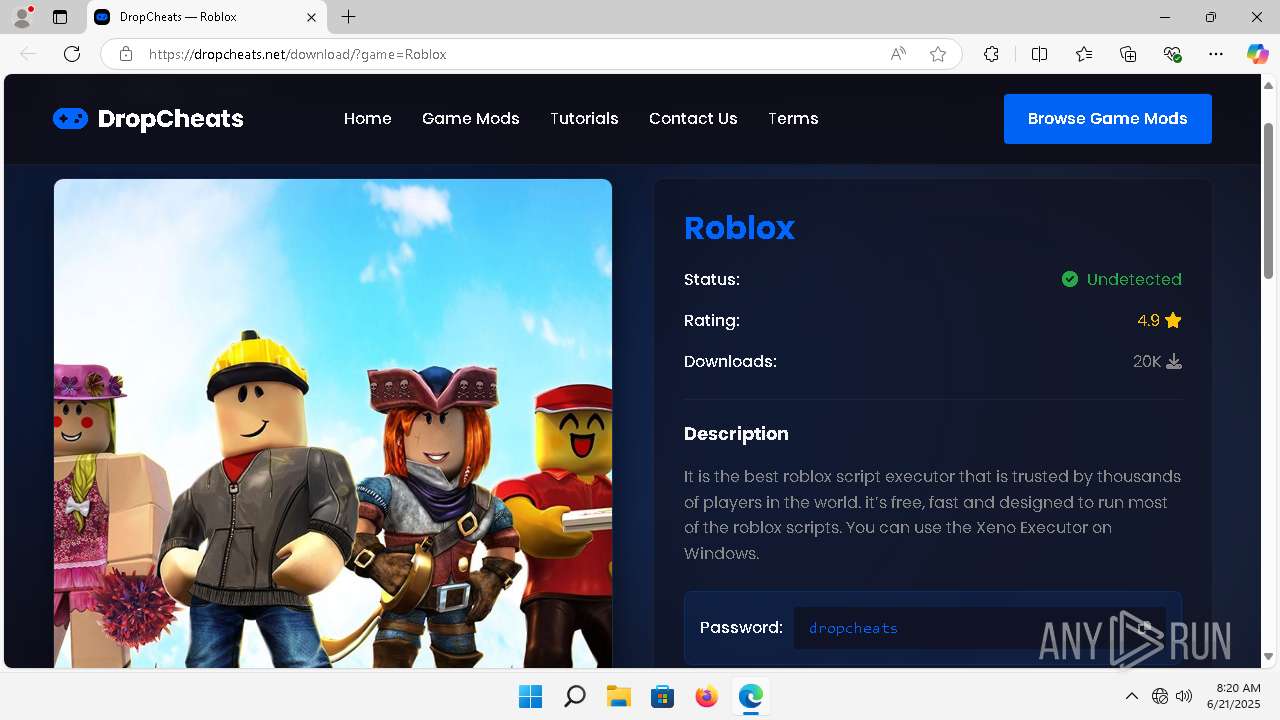
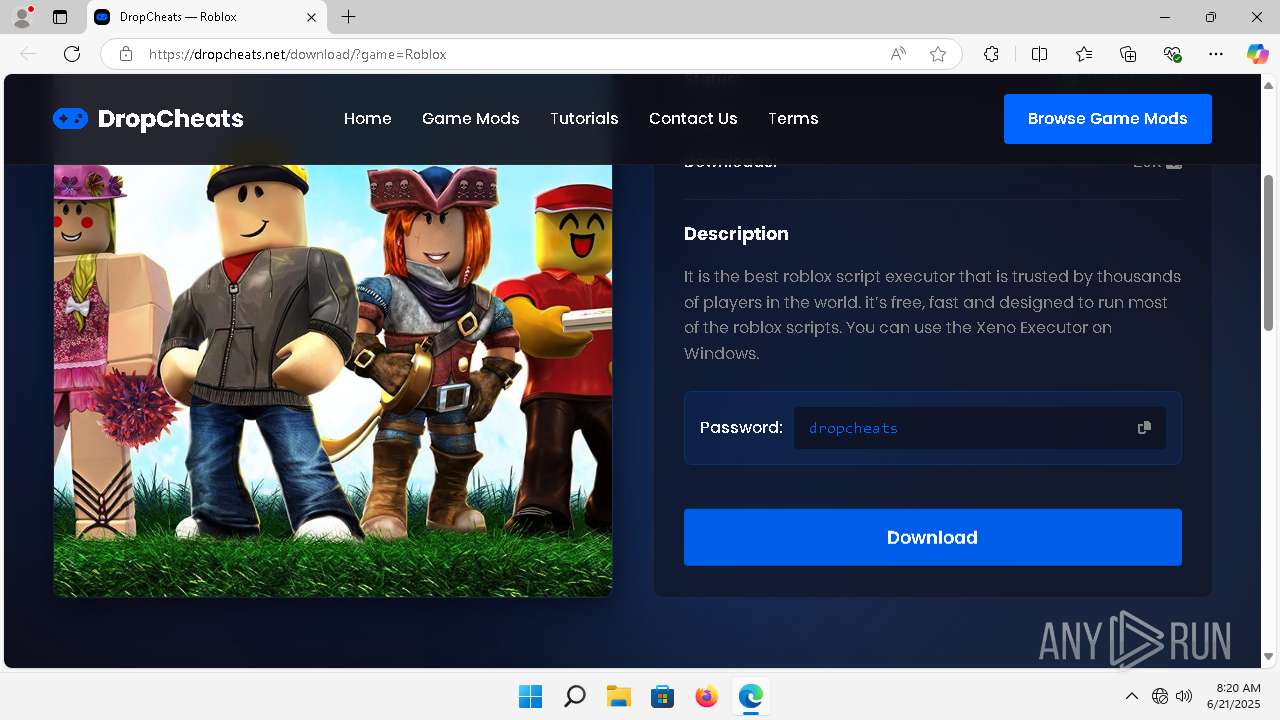
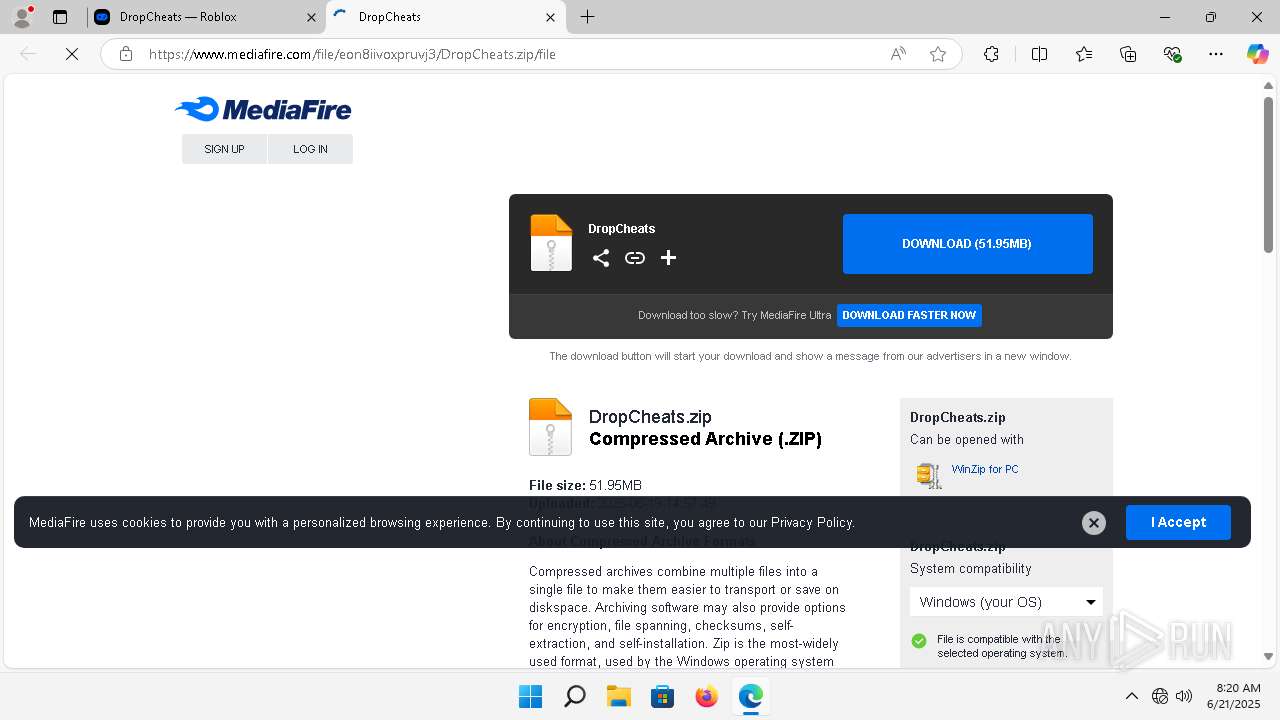
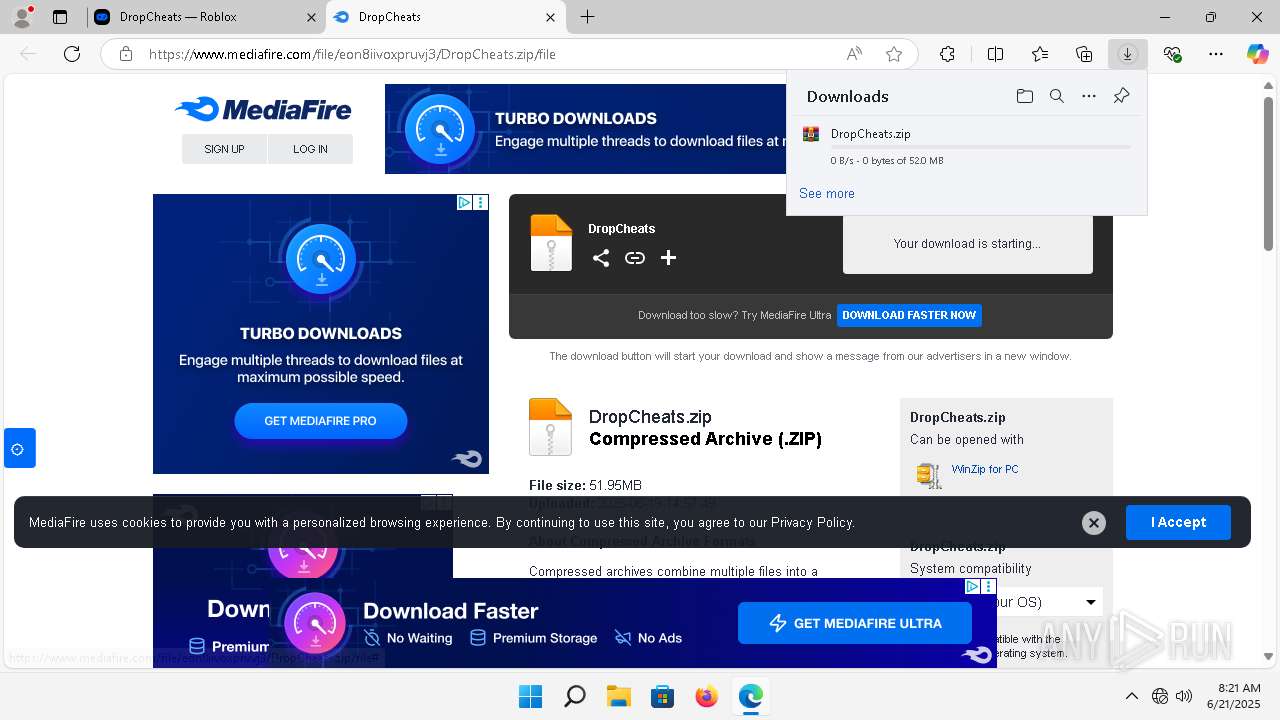
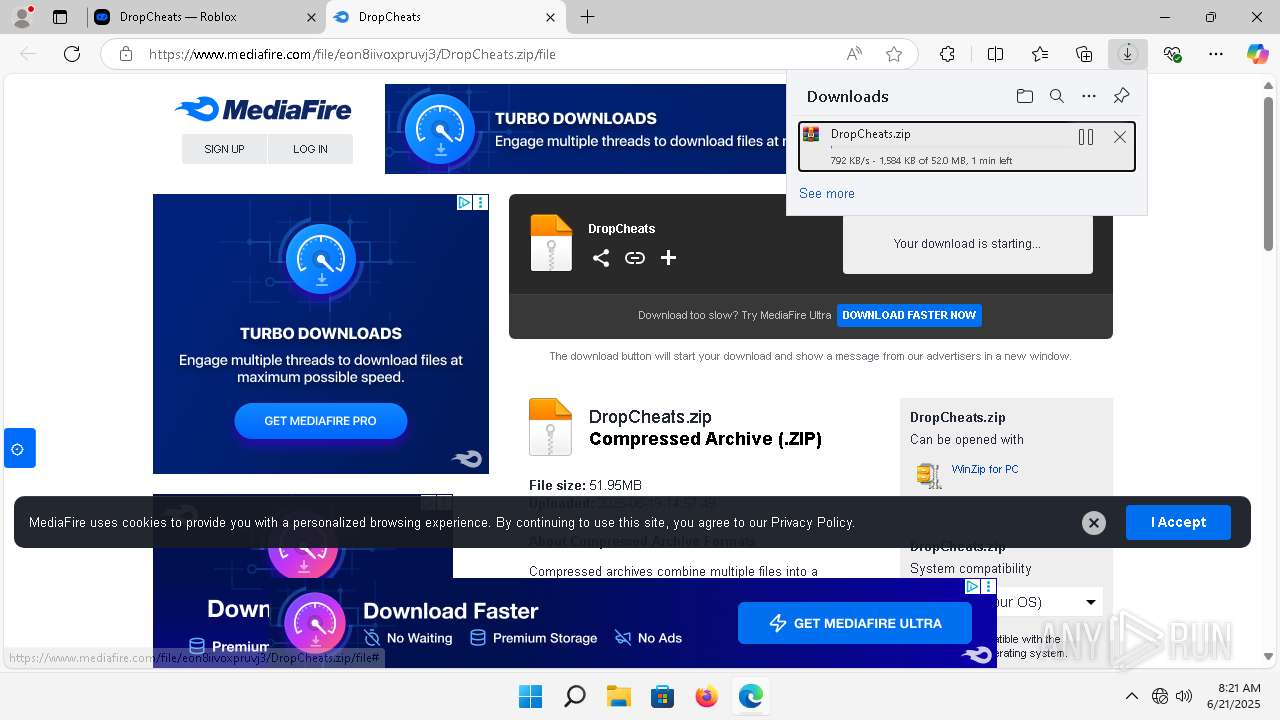
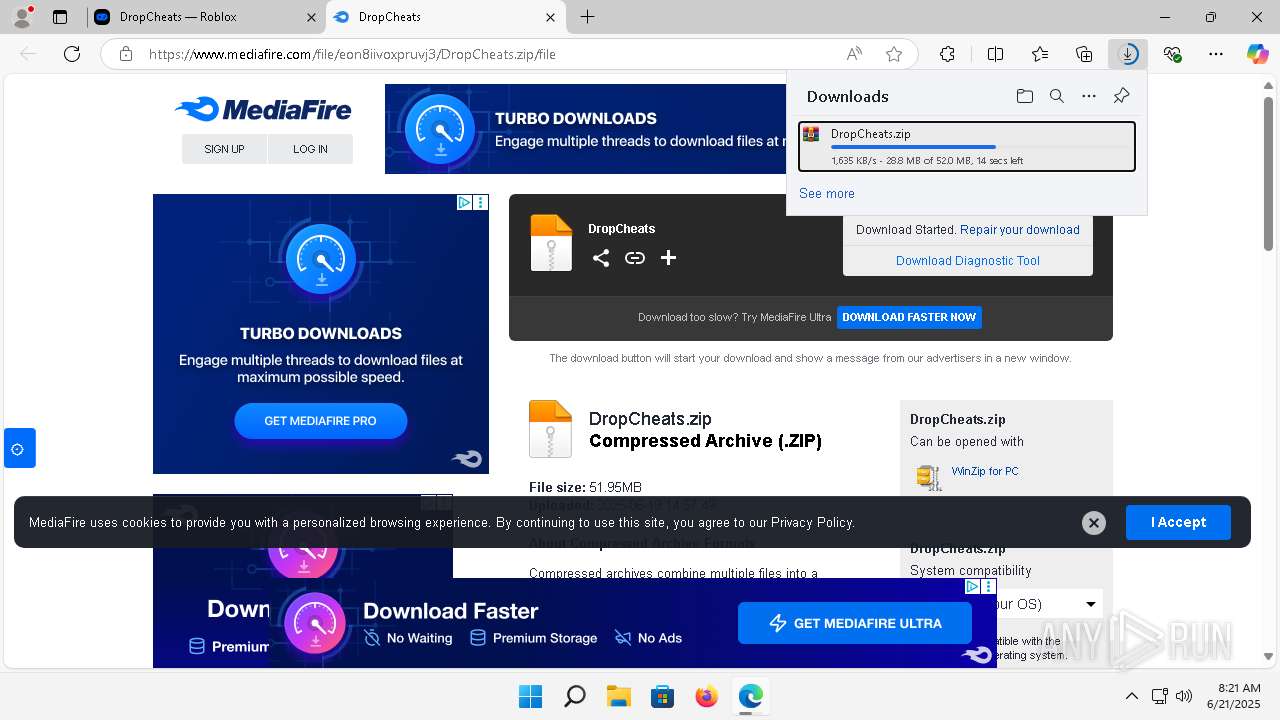
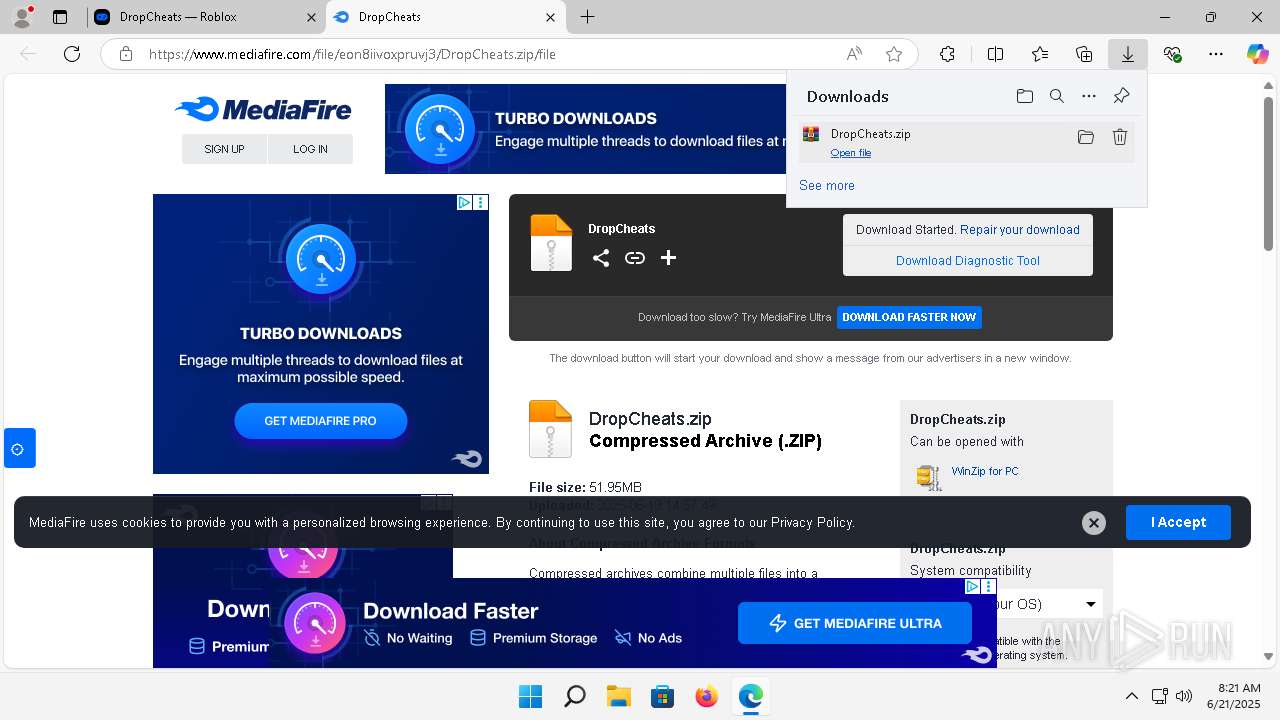
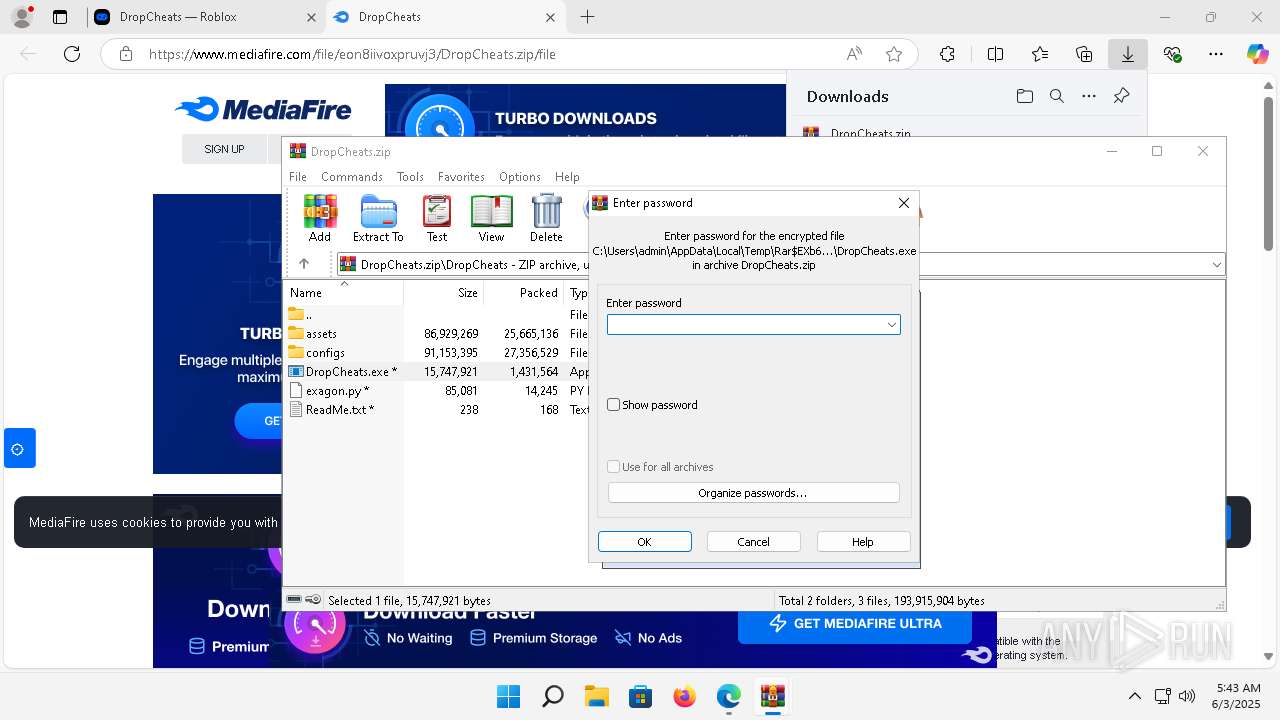
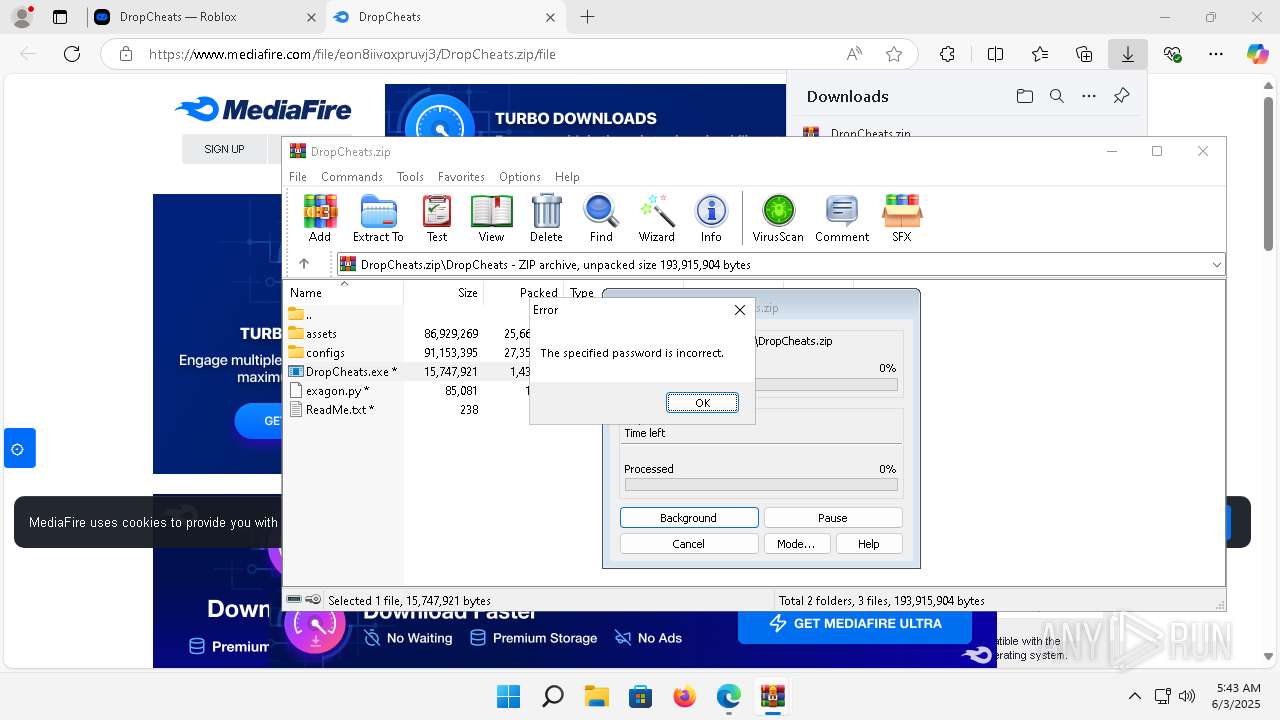
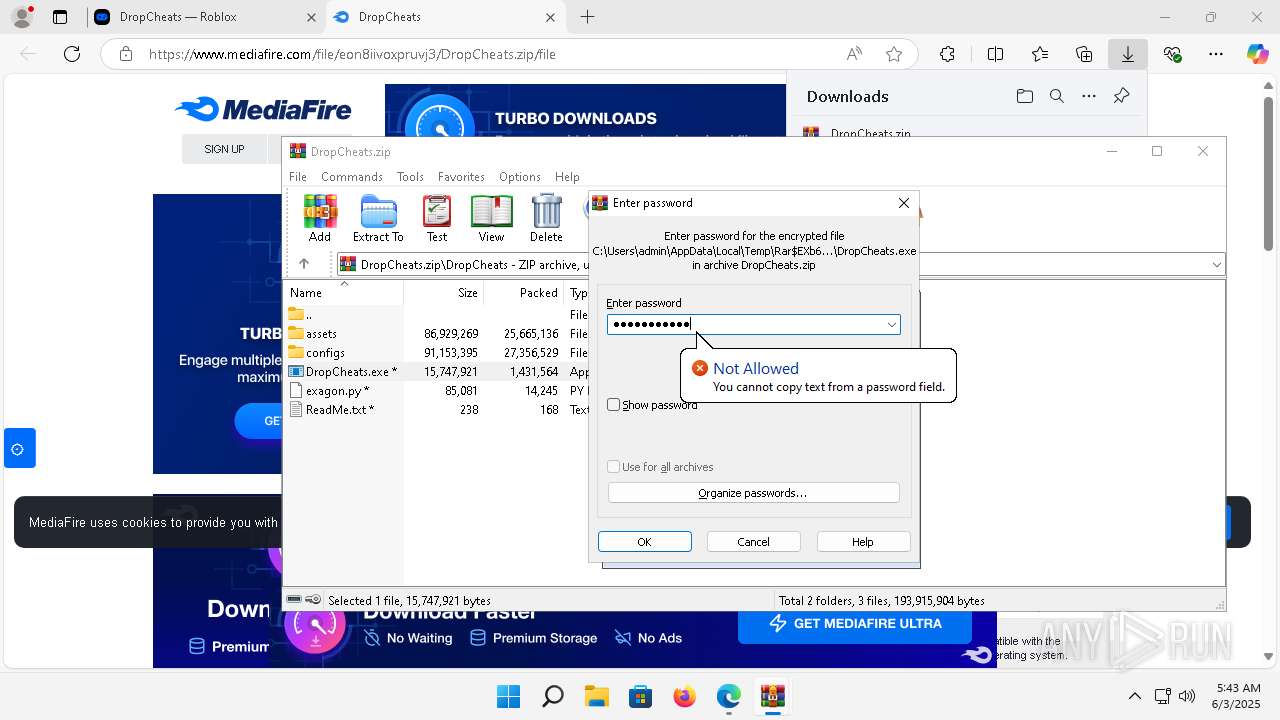
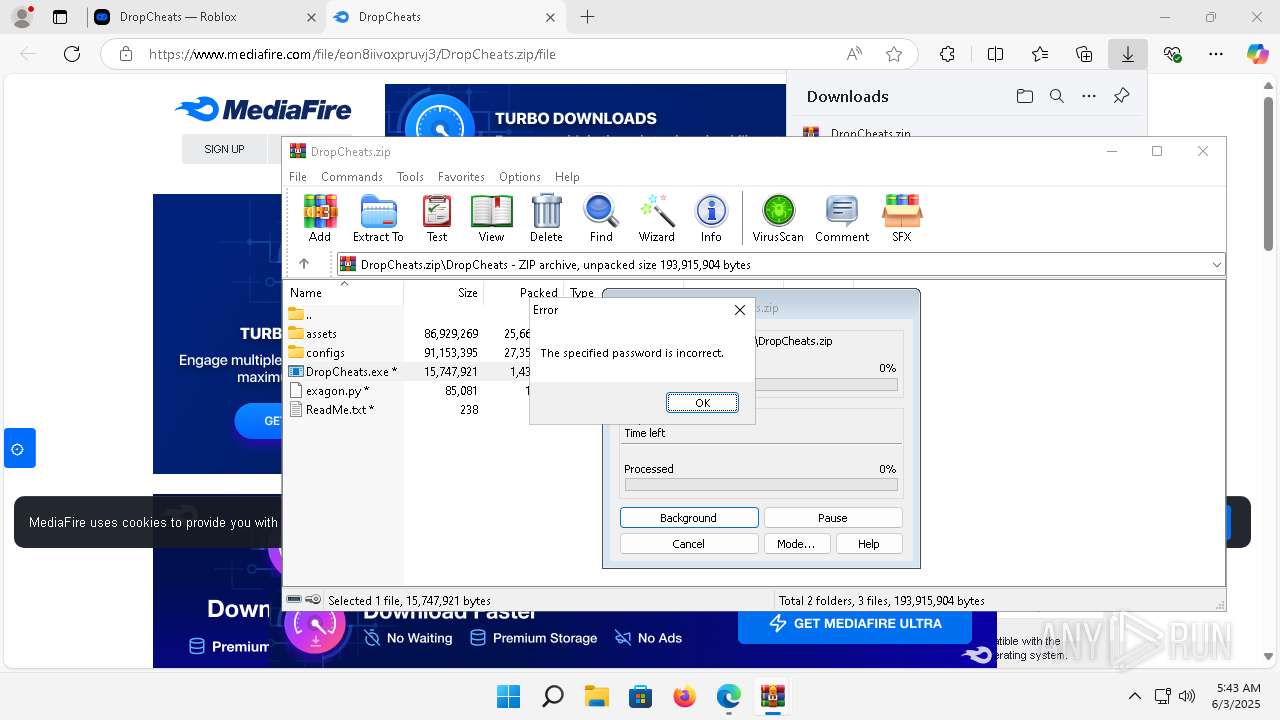
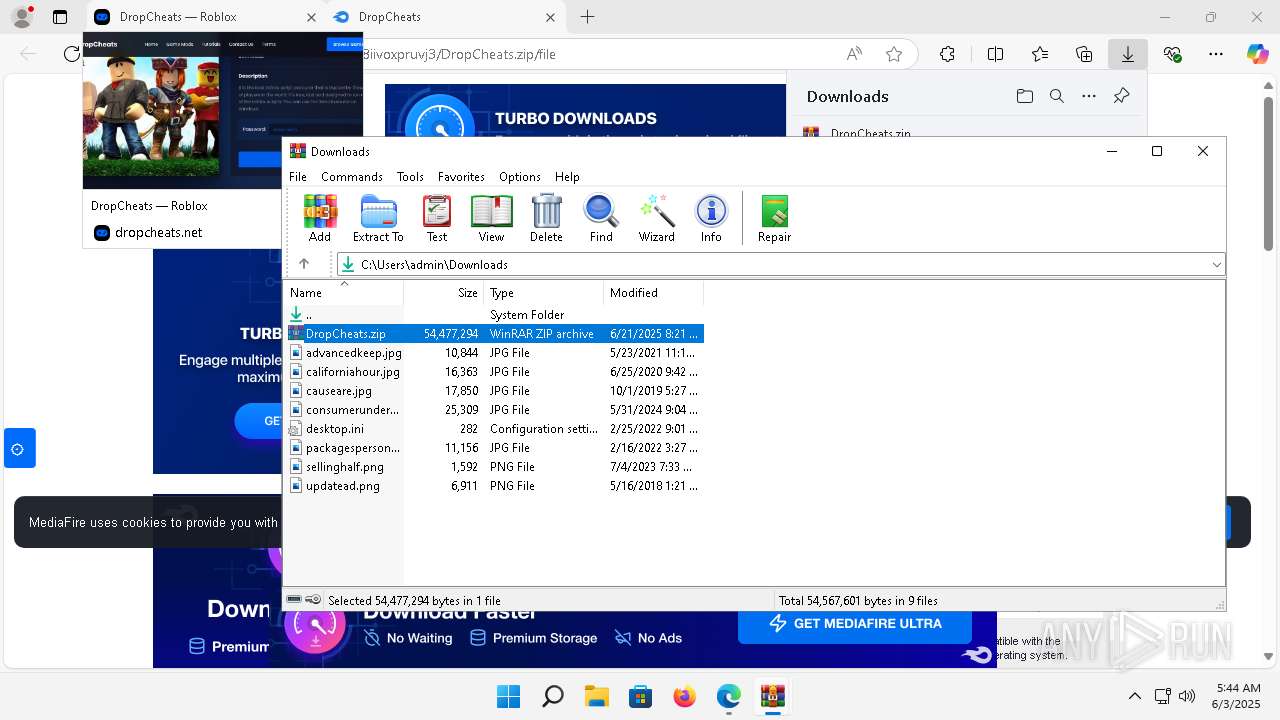
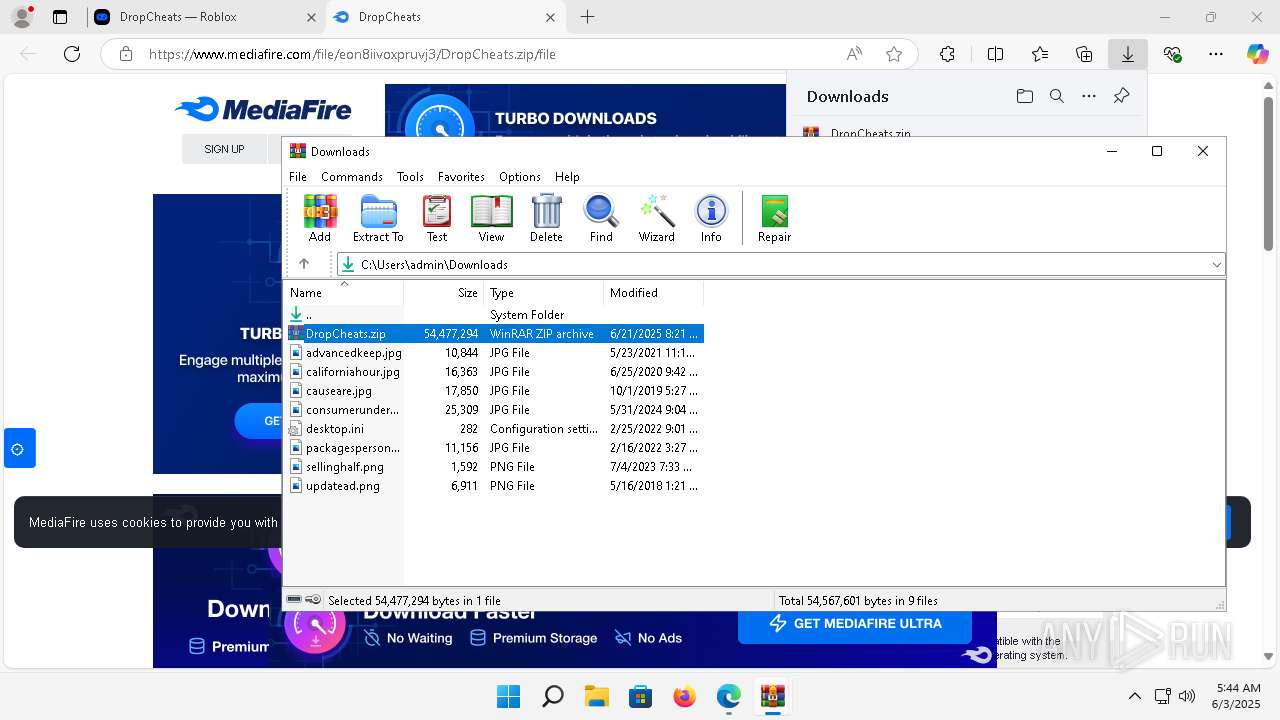
| URL: | https://dropcheats.net/download/?game=Roblox |
| Full analysis: | https://app.any.run/tasks/f5d3ab41-d8e1-4c06-a5b3-453529124774 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 08:20:44 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3C53A1DC70D2D6145111358938E1664D |
| SHA1: | 6F135DAFBBBAEC919329A861EE4CDAD6F4830FBB |
| SHA256: | 2B0E21C428D097EB557BBD8CF994310550880AF24334F39B4421F5D9B3FA5C1B |
| SSDEEP: | 3:N8PKVILao93c0:23uoVc0 |
MALICIOUS
AutoIt loader has been detected (YARA)
- Swedish.com (PID: 3608)
Executing a file with an untrusted certificate
- DropCheats.exe (PID: 6232)
SUSPICIOUS
Starts CMD.EXE for commands execution
- DropCheats.exe (PID: 6232)
Get information on the list of running processes
- cmd.exe (PID: 4424)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6932)
Executing commands from a ".bat" file
- DropCheats.exe (PID: 6232)
Starts the AutoIt3 executable file
- cmd.exe (PID: 4424)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4424)
The executable file from the user directory is run by the CMD process
- Swedish.com (PID: 3608)
Starts application with an unusual extension
- cmd.exe (PID: 4424)
Executes application which crashes
- Swedish.com (PID: 3608)
There is functionality for taking screenshot (YARA)
- DropCheats.exe (PID: 6232)
- Swedish.com (PID: 3608)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6932)
Connects to unusual port
- OpenWith.exe (PID: 7388)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6932)
The sample compiled with chinese language support
- WinRAR.exe (PID: 6932)
The sample compiled with english language support
- WinRAR.exe (PID: 6932)
Application launched itself
- chrome.exe (PID: 2736)
- msedge.exe (PID: 6860)
- msedge.exe (PID: 5052)
Checks supported languages
- identity_helper.exe (PID: 6224)
Reads the computer name
- identity_helper.exe (PID: 6224)
Reads Environment values
- identity_helper.exe (PID: 6224)
Reads Microsoft Office registry keys
- msedge.exe (PID: 5052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
207
Monitored processes
89
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=8052,i,4333281607968744494,11022926406272646925,262144 --variations-seed-version --mojo-platform-channel-handle=6080 /prefetch:14 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 520 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2496,i,4333281607968744494,11022926406272646925,262144 --variations-seed-version --mojo-platform-channel-handle=2508 /prefetch:13 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 620 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Local\Temp\chr48D.tmp /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Local\Temp\chr48D.tmp\Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=134.0.6998.36 --initial-client-data=0x10c,0x110,0x114,0xe8,0x118,0x7ffc96c44f38,0x7ffc96c44f44,0x7ffc96c44f50 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 134.0.6998.36 Modules
| |||||||||||||||
| 852 | findstr /V "Involvement" Queens | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.22000.653 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --always-read-main-dll --field-trial-handle=4352,i,1830905957775360539,7064325363661602486,262144 --variations-seed-version --mojo-platform-channel-handle=4364 /prefetch:9 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 868 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=16 --always-read-main-dll --field-trial-handle=7012,i,4333281607968744494,11022926406272646925,262144 --variations-seed-version --mojo-platform-channel-handle=7128 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 876 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3452,i,4333281607968744494,11022926406272646925,262144 --variations-seed-version --mojo-platform-channel-handle=3464 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 928 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=1904,i,550474012170085146,18436284846297859303,262144 --variations-seed-version --mojo-platform-channel-handle=3512 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 134.0.6998.36 Modules
| |||||||||||||||
| 956 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --always-read-main-dll --field-trial-handle=6932,i,4333281607968744494,11022926406272646925,262144 --variations-seed-version --mojo-platform-channel-handle=7000 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1120 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=3500,i,1830905957775360539,7064325363661602486,262144 --variations-seed-version --mojo-platform-channel-handle=3364 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
12 433
Read events
12 293
Write events
137
Delete events
3
Modification events
| (PID) Process: | (1984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (1984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
Executable files
34
Suspicious files
470
Text files
108
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6932.40933\DropCheats\assets\lib\SystemAdministration | — | |
MD5:— | SHA256:— | |||
| 6932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6932.40933\DropCheats\assets\lib\rt.jar | — | |
MD5:— | SHA256:— | |||
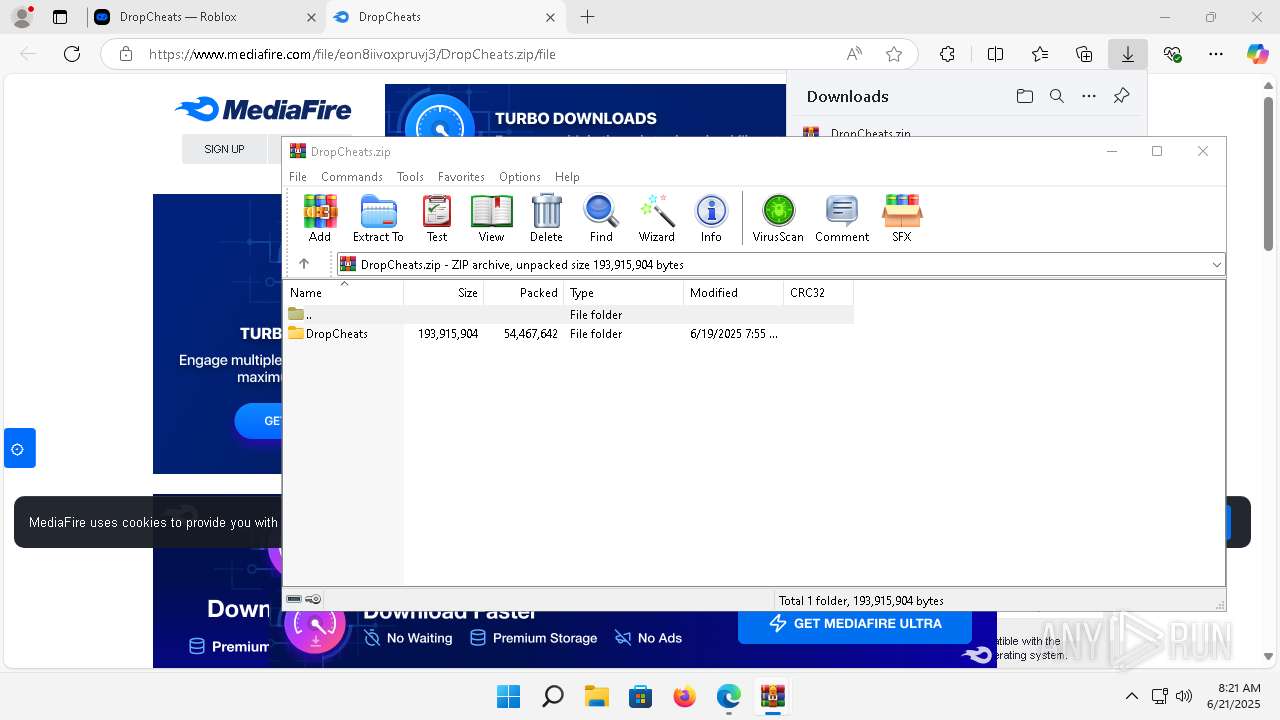
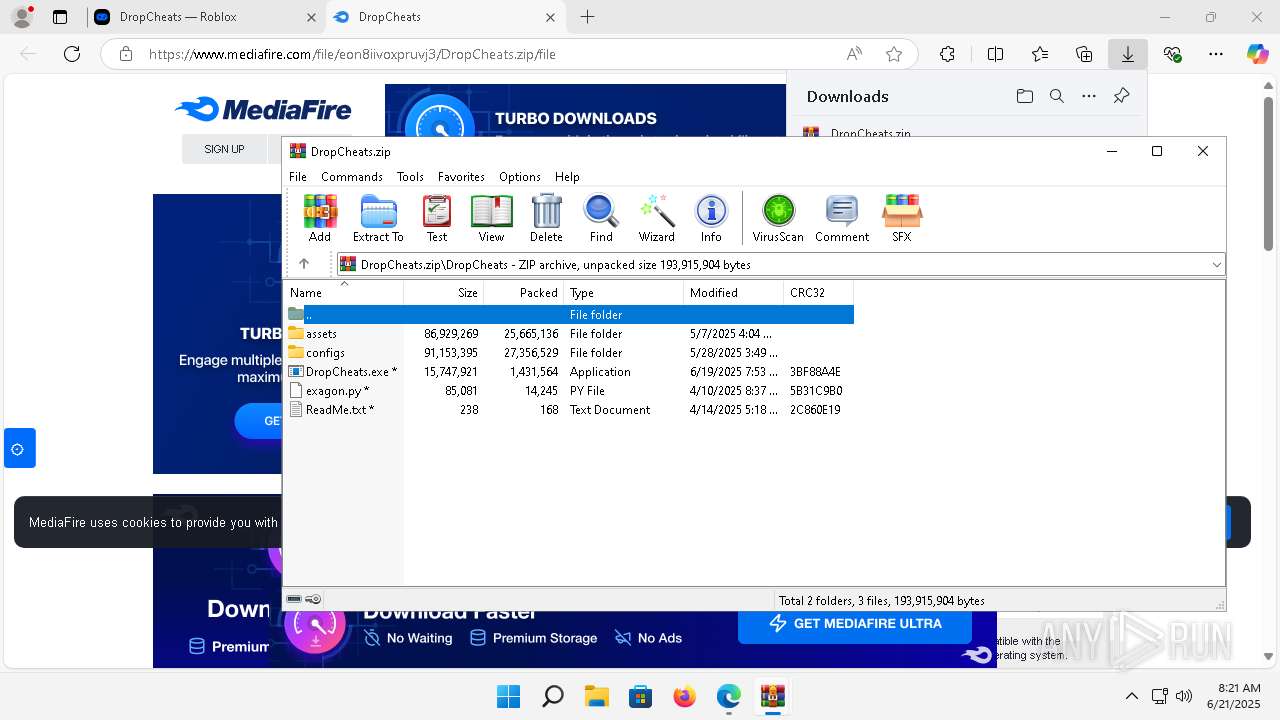
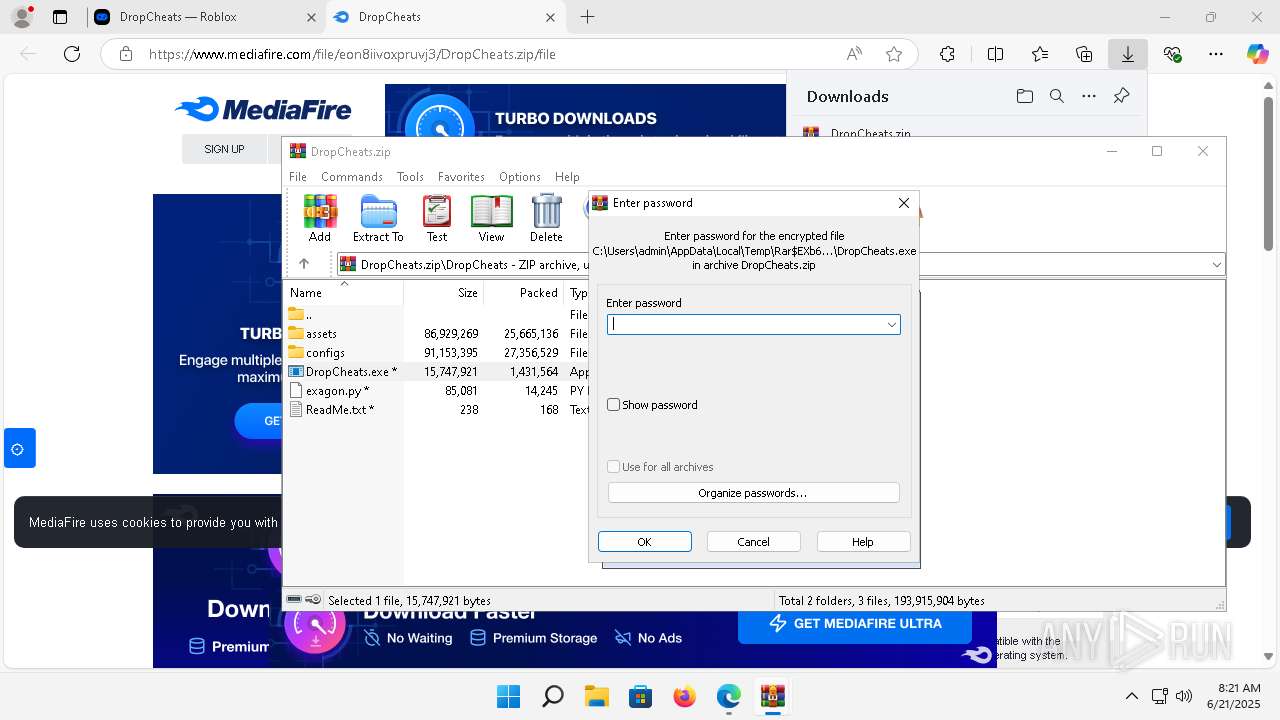
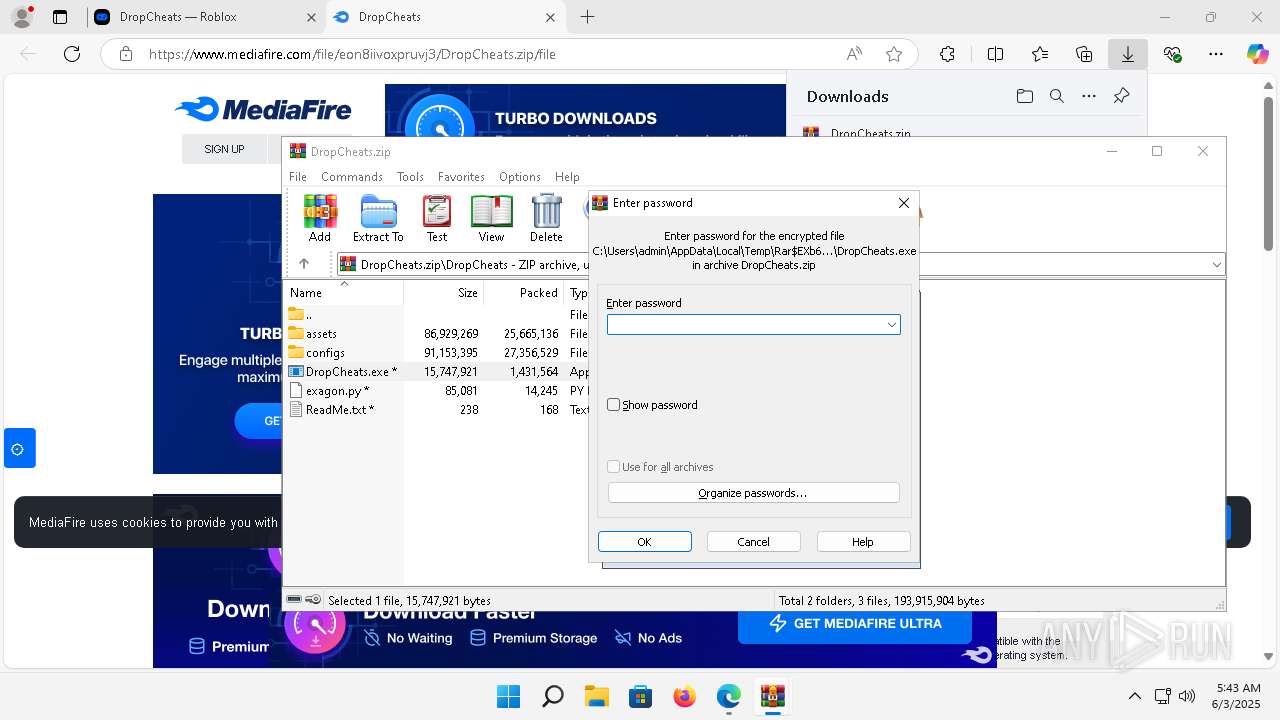
| 6932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6932.40933\DropCheats\DropCheats.exe | executable | |
MD5:6DDEEAA1E804463A7CDEF7FF791493CA | SHA256:88454D9B05CC4ADF03D4499AF5E5ADA6043E355D95F3E17BE010A8C2291A69CC | |||
| 6932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6932.40933\DropCheats\assets\ActiveSyncProvider.dll | executable | |
MD5:AE097D6FACA854A02642F6FDBFD1D967 | SHA256:4EF9B2E7A0BFE36AAF1D2205FA72E3C82A3A7D43A26018535887E4F9BF1D9E30 | |||
| 6932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6932.40933\DropCheats\assets\alibabacloud.dll | executable | |
MD5:2698F138E8C4D573BB0DAEDC47ACD123 | SHA256:2EE24618C12271B7C9C18DF5F2BEDDF02FD93EE7457707E0A6A54D8D8E88AAA2 | |||
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Edge Cloud Config\CloudConfigLog | binary | |
MD5:864F6EC995C31D2484D5DCCE33B2DD76 | SHA256:CD8D625A236E9CE6B2FB5DF044893DB152B1789061E29C19EFD871E92CAB304F | |||
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Edge Cloud Config\76e8f035-ac54-4d84-8351-c8c77166ae54.tmp | binary | |
MD5:411BFAE61BA5B1B4FCF5EBC037EF9EDA | SHA256:DF2A77E18262529B4DC2546C0004D18BAD146BA7064E5B5A3C2CB4307EECB489 | |||
| 5052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Edge Cloud Config\d49923d0-87f7-4c65-ad81-289027f30b64.tmp | binary | |
MD5:F85E2EDB50F55108E12902B365F880B6 | SHA256:AD02963B6DF18847191C56C5486561EC0EF25783F57C1FAE7513670765216708 | |||
| 6932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6932.40933\DropCheats\ReadMe.txt | text | |
MD5:86851F0AE000F744375226D71B1269A4 | SHA256:9C357E9778B381142FA90A42D6AACF62F5C9717DEF39099816A8B782302165E4 | |||
| 6932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6932.40933\DropCheats\assets\csgo_icons.ttf | binary | |
MD5:15A58B8434E672BB272F655759D898CB | SHA256:885EDB828B3BDB0A2BD61ED9F588D2B6FD5540A234C0BD25CCB0ADC44A64205A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
236
DNS requests
333
Threats
23
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5268 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/46df2db5-82ac-46a7-9d9e-cf1580d73a96?P1=1750793257&P2=404&P3=2&P4=CnVMNgTXvD5Nun57TE6zZ%2fQYstCAgHBR6dmCWys8d6BD4takG6GWvYw7GllE54G6j1LuJEWLXex1YVTYyRA60w%3d%3d | unknown | — | — | whitelisted |
5268 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2ef98485-cbad-4d99-b4c2-cd4abac73fb4?P1=1750793256&P2=404&P3=2&P4=gI3%2bxWjWKm%2fQUjoiA2zYNArY4IEh88Xkgdz7rz3ifr%2fc46cth6nV5xi8w9X%2bE8zoVbsgixCAPT8TVdyOpkjJMQ%3d%3d | unknown | — | — | whitelisted |
5268 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/46df2db5-82ac-46a7-9d9e-cf1580d73a96?P1=1750793257&P2=404&P3=2&P4=CnVMNgTXvD5Nun57TE6zZ%2fQYstCAgHBR6dmCWys8d6BD4takG6GWvYw7GllE54G6j1LuJEWLXex1YVTYyRA60w%3d%3d | unknown | — | — | whitelisted |
5268 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2ef98485-cbad-4d99-b4c2-cd4abac73fb4?P1=1750793256&P2=404&P3=2&P4=gI3%2bxWjWKm%2fQUjoiA2zYNArY4IEh88Xkgdz7rz3ifr%2fc46cth6nV5xi8w9X%2bE8zoVbsgixCAPT8TVdyOpkjJMQ%3d%3d | unknown | — | — | whitelisted |
5268 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cc4d2190-4e60-426c-b864-b772d14b4acc?P1=1750793257&P2=404&P3=2&P4=IM1K2gyh9w8Plc7Wzhgc9HSxfz82dftZKggtULGiCeS6RO0XJLcqX1xlVNYHMKIQLi7iYyFiuCYSuRVfFYWsjQ%3d%3d | unknown | — | — | whitelisted |
2840 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6c478a3cb1f9bc68 | unknown | — | — | whitelisted |
2840 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?13436be0d10cbdfe | unknown | — | — | whitelisted |
2840 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?bab80a0e0e91e0ea | unknown | — | — | whitelisted |
6284 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:H_hf0nwS_p8-DF1kRFT5bY2h8Ndc0JYtPWi7bhb9MVM&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1524 | svchost.exe | GET | 200 | 2.18.64.212:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3716 | rundll32.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6424 | OfficeC2RClient.exe | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
— | — | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
6964 | firefox.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
4424 | pingsender.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
1524 | svchost.exe | 2.18.64.200:80 | — | Administracion Nacional de Telecomunicaciones | UY | unknown |
2860 | svchost.exe | 20.42.65.90:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2840 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
6284 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
incoming.telemetry.mozilla.org |
| whitelisted |
telemetry-incoming.r53-2.services.mozilla.com |
| whitelisted |
google.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
dropcheats.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6284 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image Sharing Service (imgur.com) |
6284 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6284 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6284 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image Sharing Service (imgur.com) |
6284 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image Sharing Service (imgur.com) |
6284 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image Sharing Service (imgur.com) |
6284 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
6284 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
6284 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
6284 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chr48D.tmp directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chr171C.tmp directory exists )
|