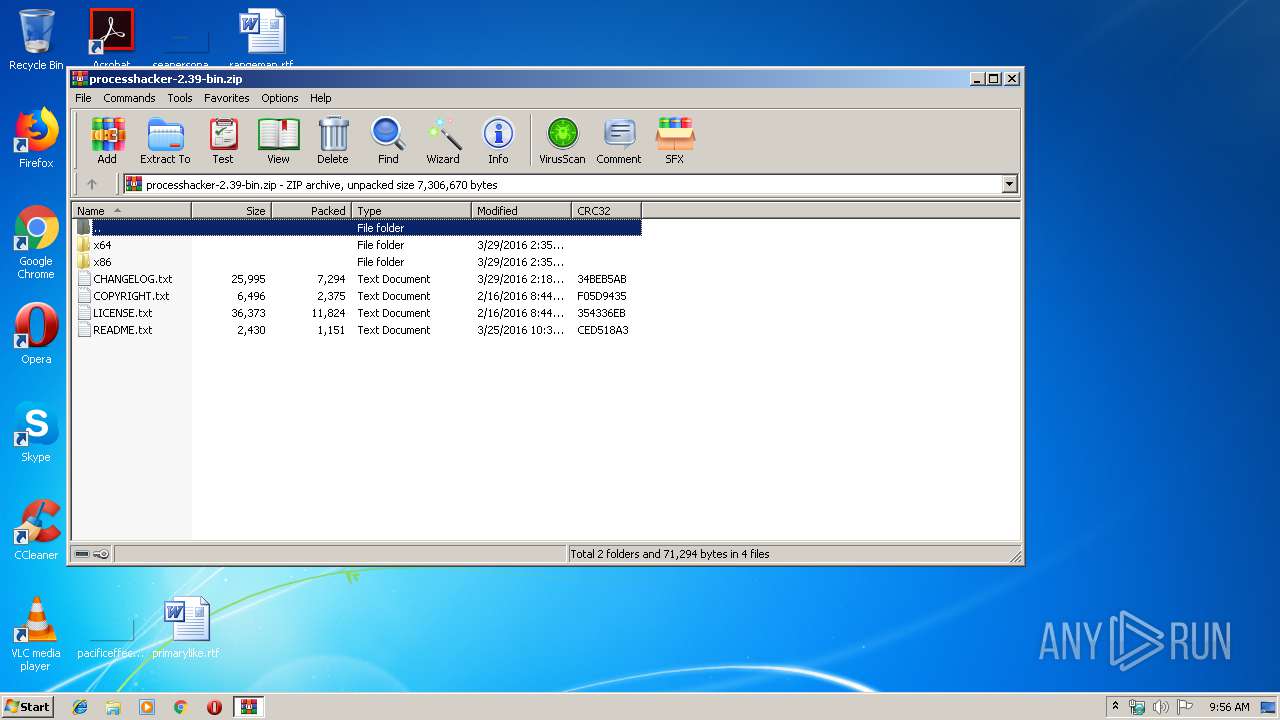
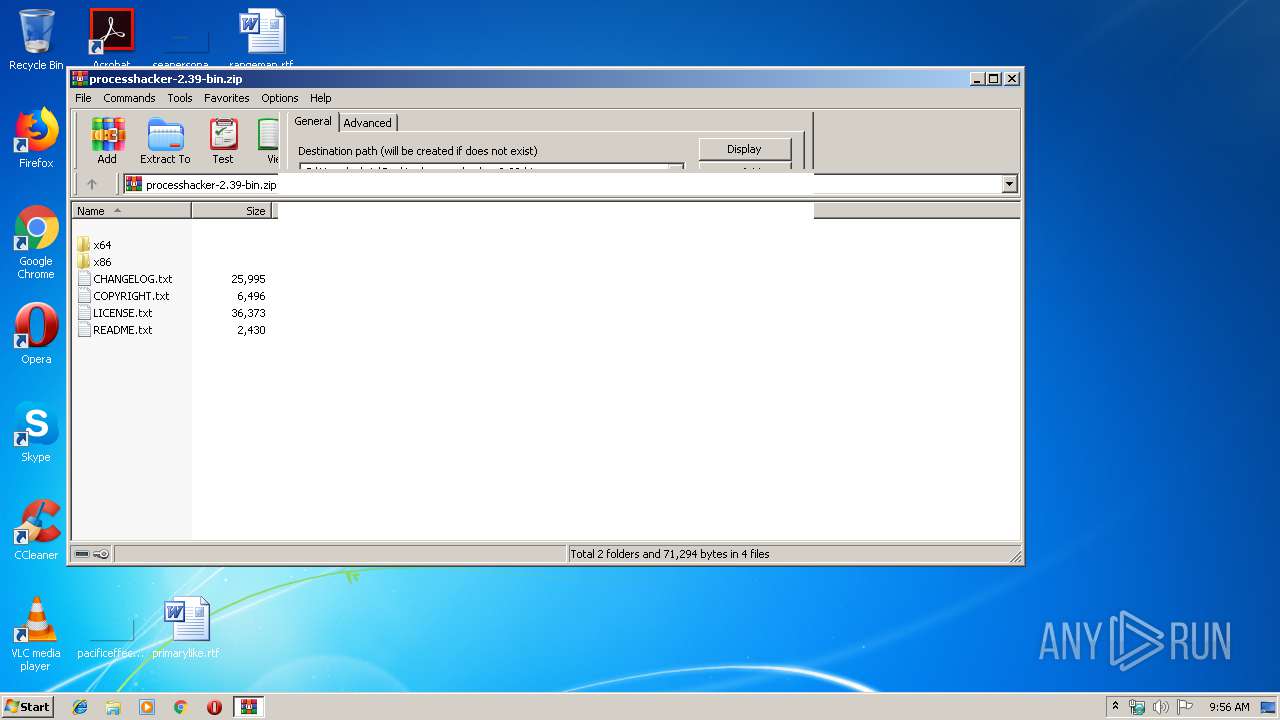
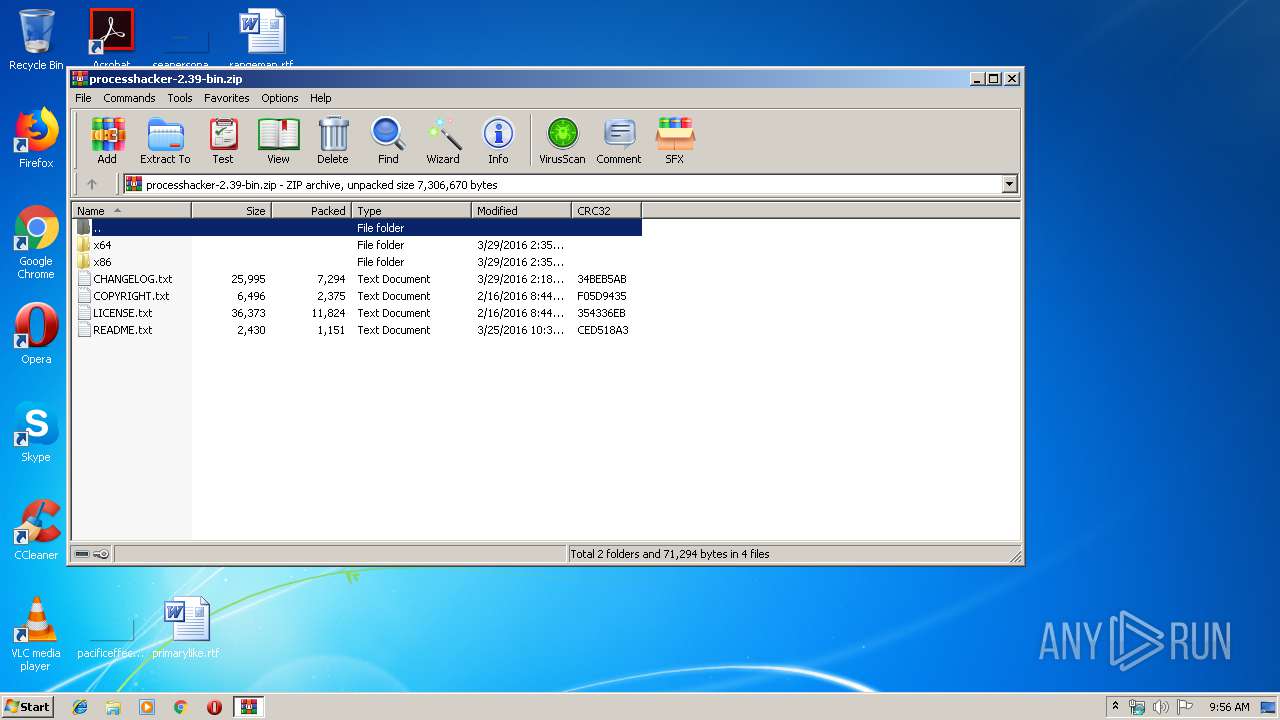
| File name: | processhacker-2.39-bin.zip |
| Full analysis: | https://app.any.run/tasks/dc6e1160-6bd6-4bc5-a98f-1ae0546eeed1 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 08:56:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B444CF14642CE9B8D75E079166A5DF0B |
| SHA1: | 8E8F8423D163D922242B8B7D85427664F77EDC97 |
| SHA256: | 2AFB5303E191DDE688C5626C3EE545E32E52F09DA3B35B20F5E0D29A418432F5 |
| SSDEEP: | 98304:jDqt5TrOmlLB/7rTOqcXfOzJR1qioDLK2EbhQ:3sTrHlB73OqX4ioDfshQ |
MALICIOUS
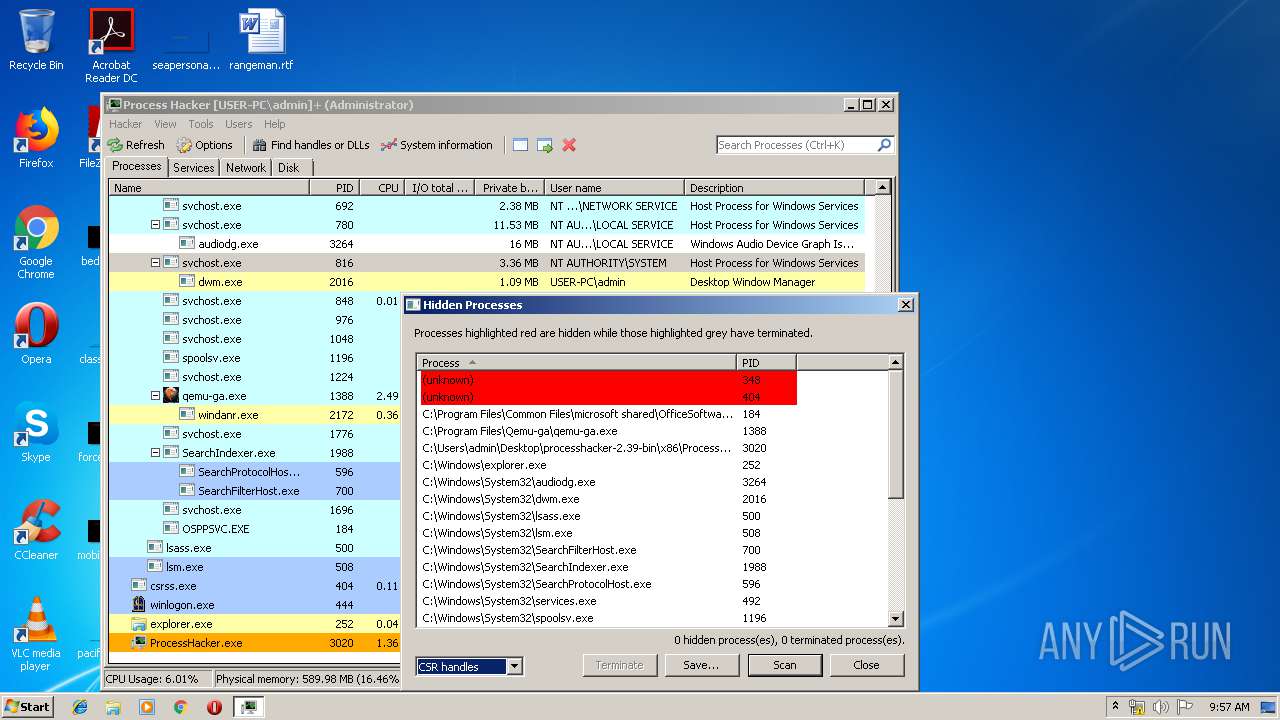
Loads dropped or rewritten executable
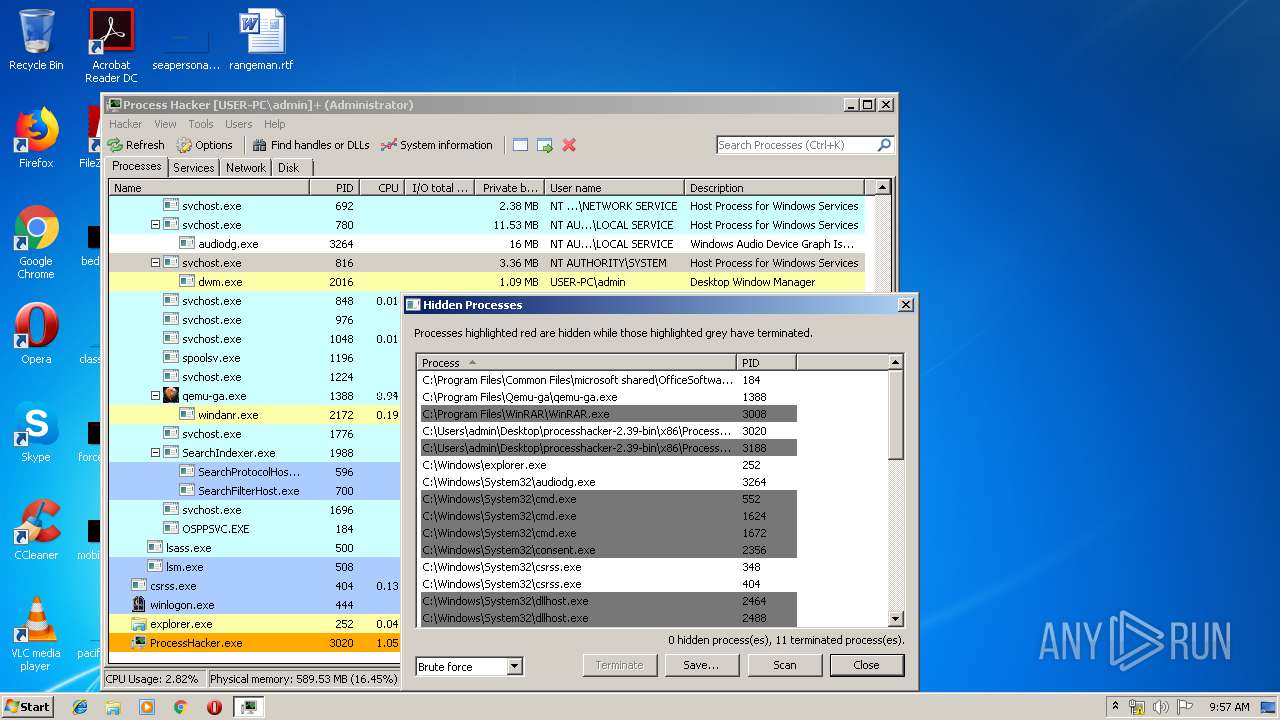
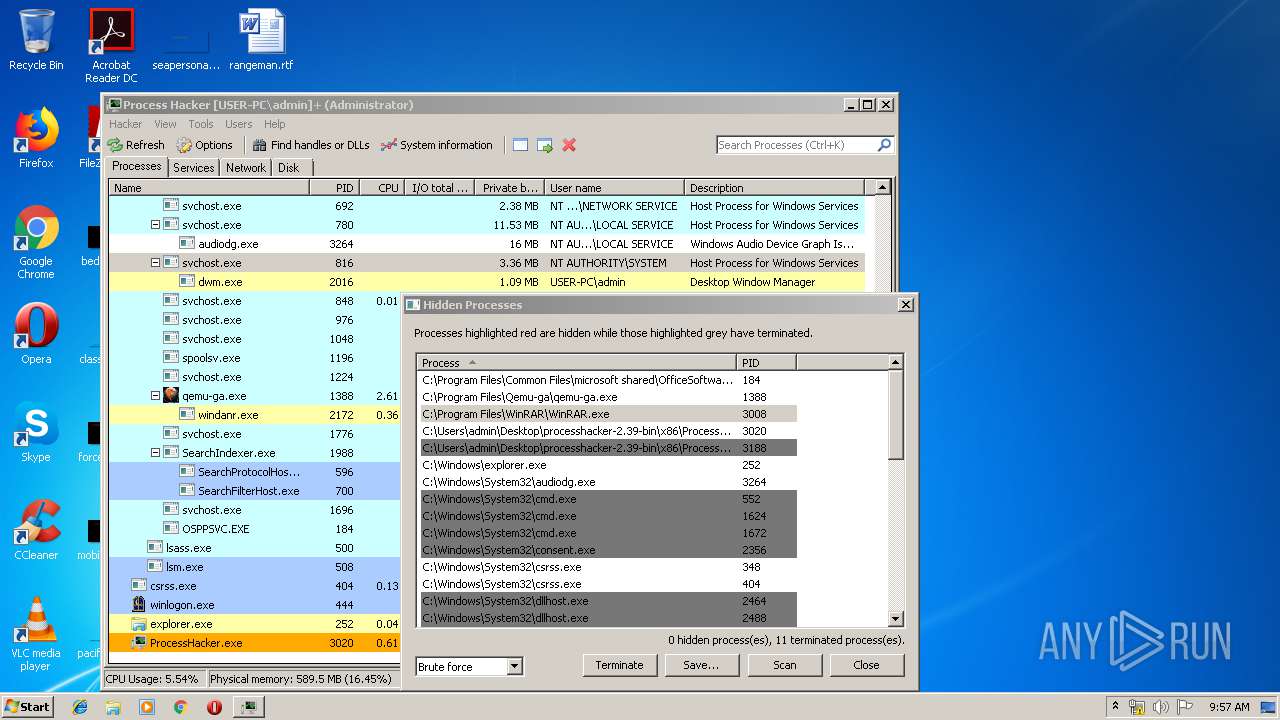
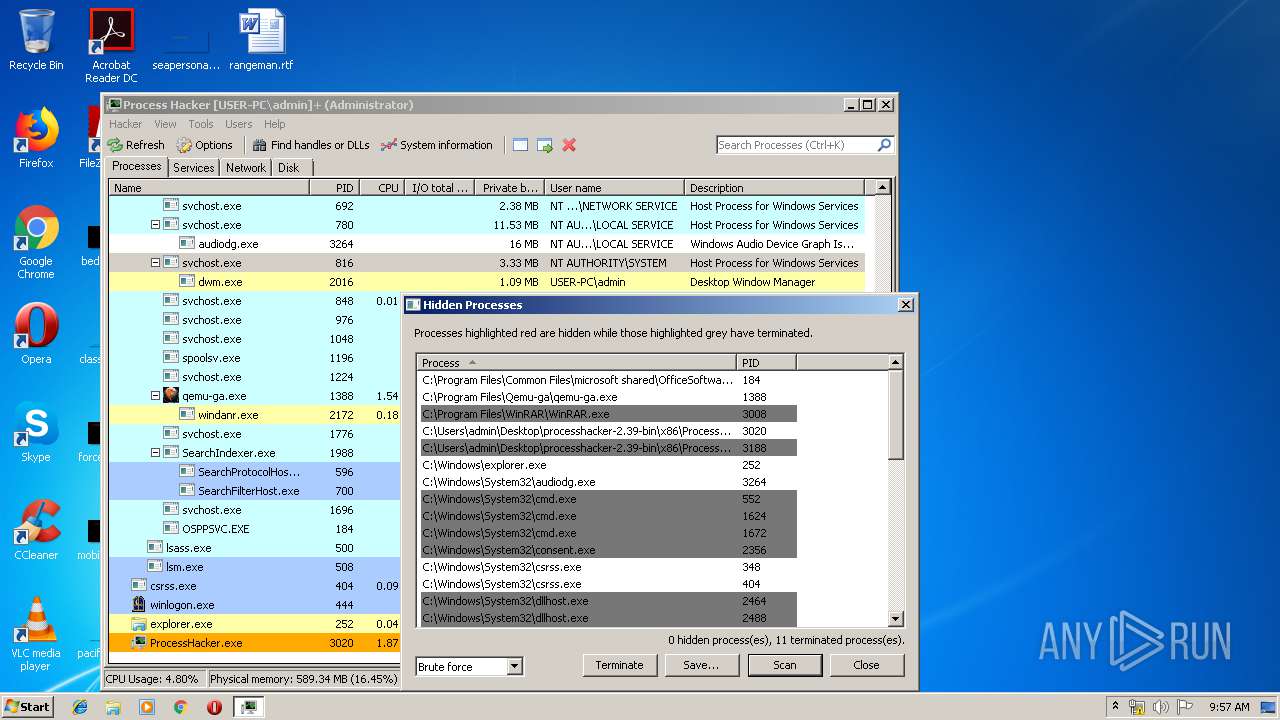
- ProcessHacker.exe (PID: 3188)
- SearchProtocolHost.exe (PID: 596)
- ProcessHacker.exe (PID: 3020)
Application was dropped or rewritten from another process
- ProcessHacker.exe (PID: 3188)
- ProcessHacker.exe (PID: 3020)
Changes settings of System certificates
- ProcessHacker.exe (PID: 3020)
SUSPICIOUS
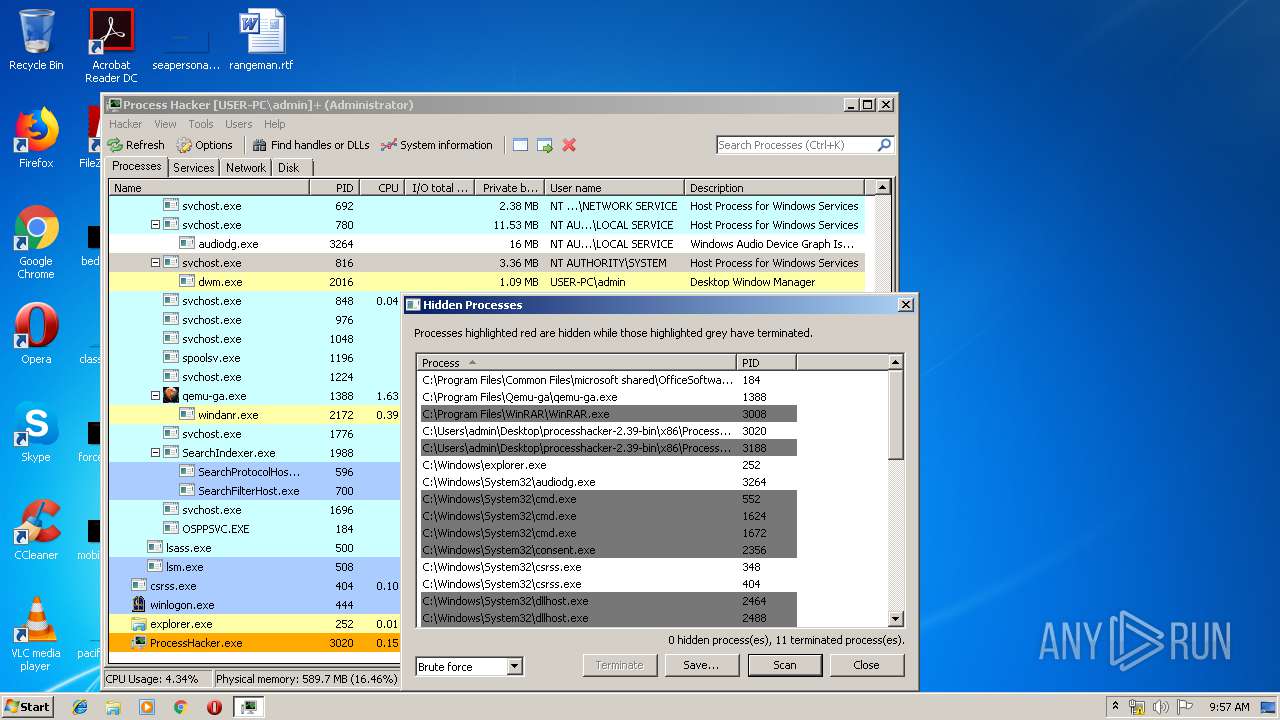
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3008)
Creates files in the user directory
- ProcessHacker.exe (PID: 3188)
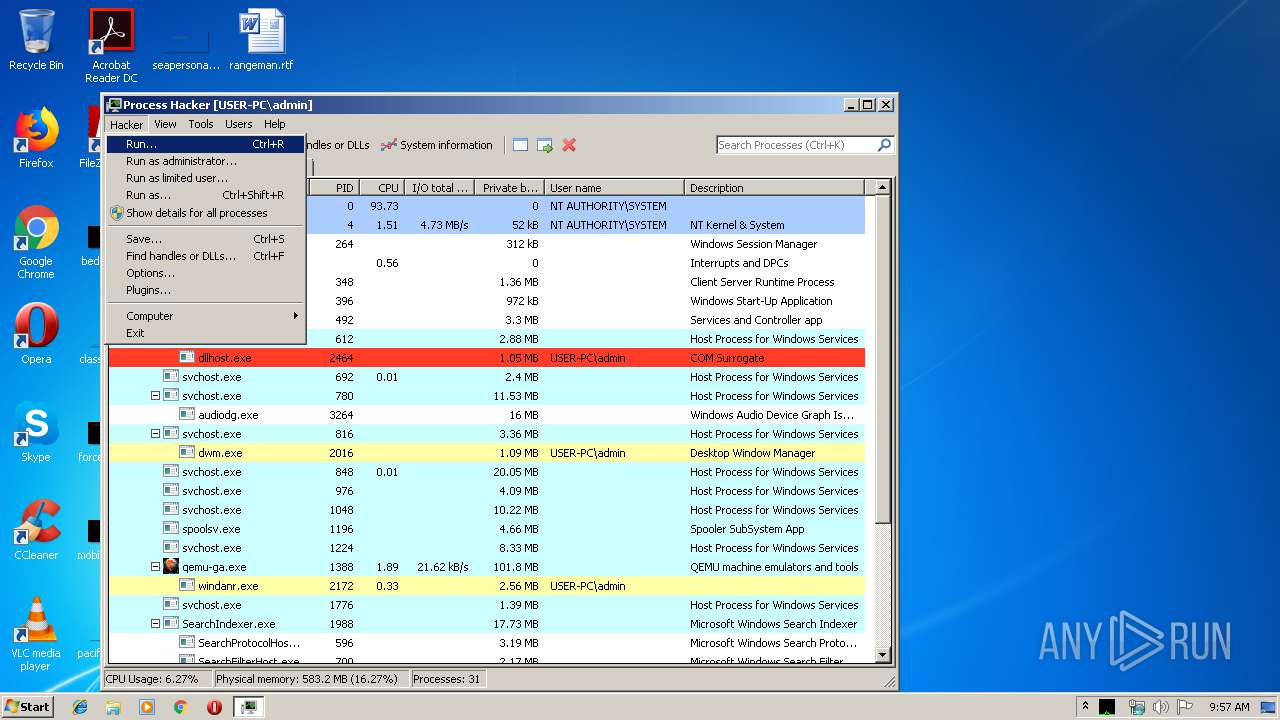
Application launched itself
- ProcessHacker.exe (PID: 3188)
Adds / modifies Windows certificates
- ProcessHacker.exe (PID: 3020)
INFO
Reads settings of System Certificates
- ProcessHacker.exe (PID: 3020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:03:29 12:18:04 |
| ZipCRC: | 0x34beb5ab |
| ZipCompressedSize: | 7294 |
| ZipUncompressedSize: | 25995 |
| ZipFileName: | CHANGELOG.txt |
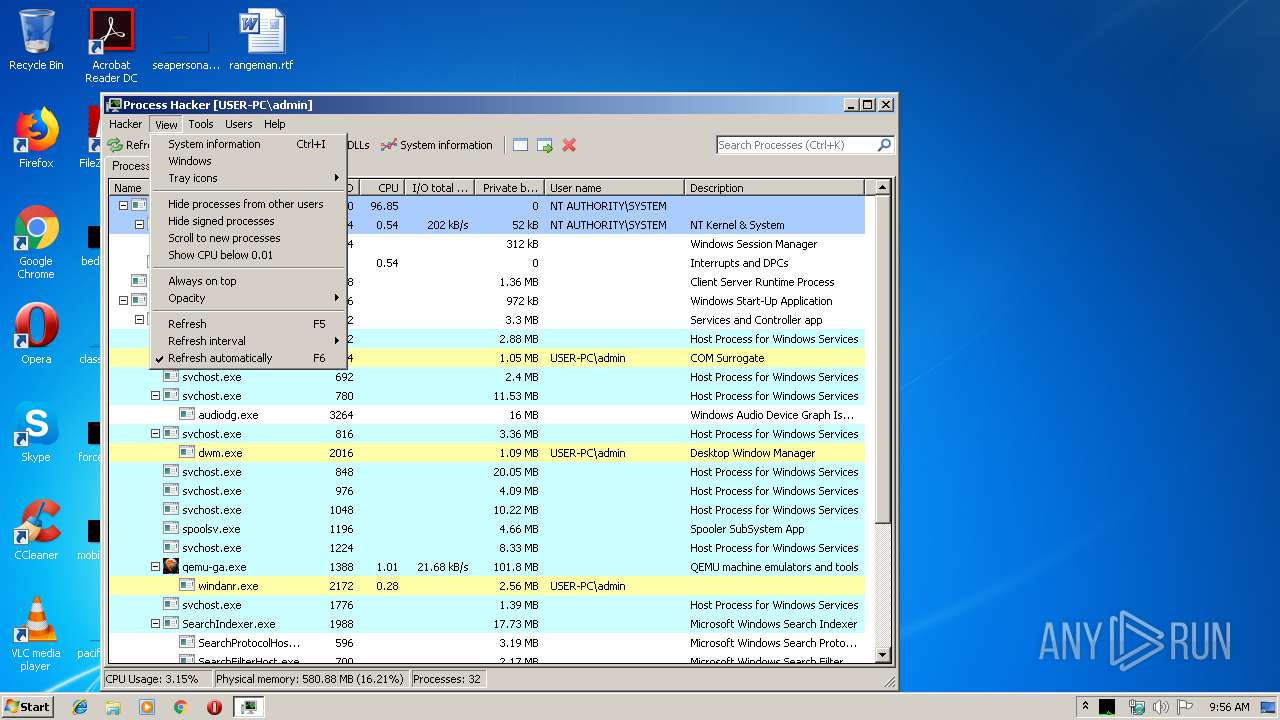
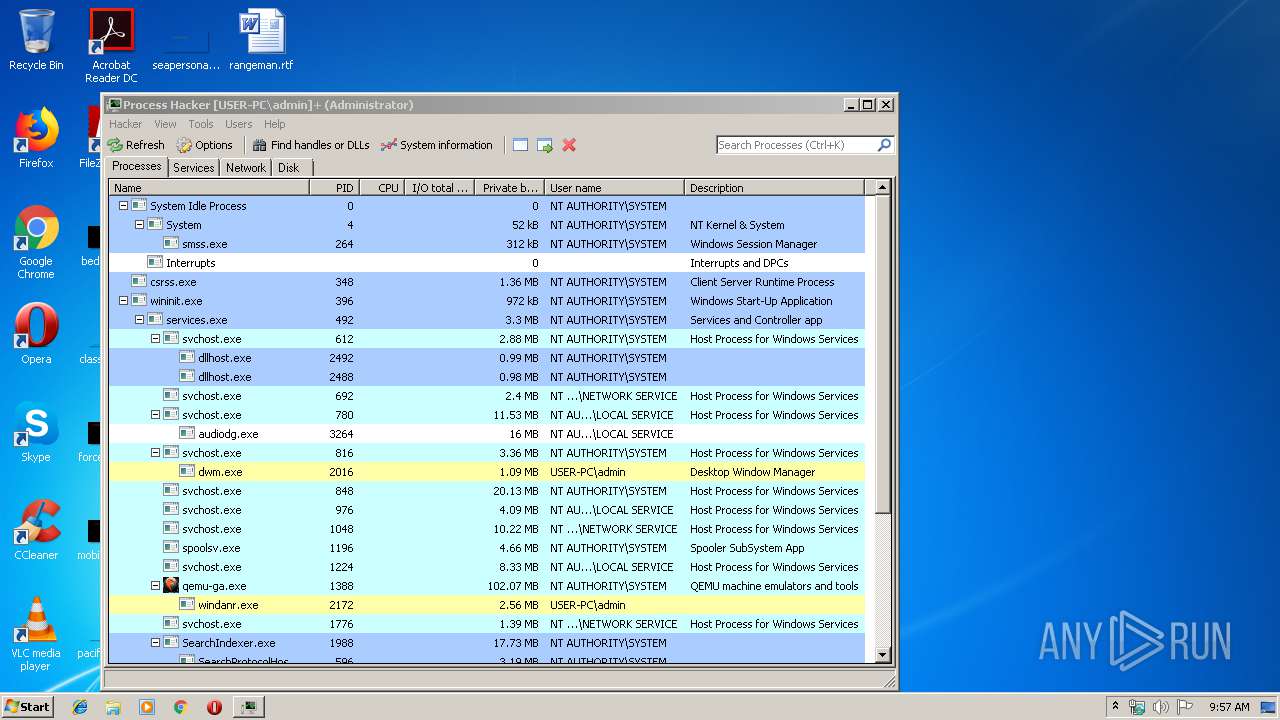
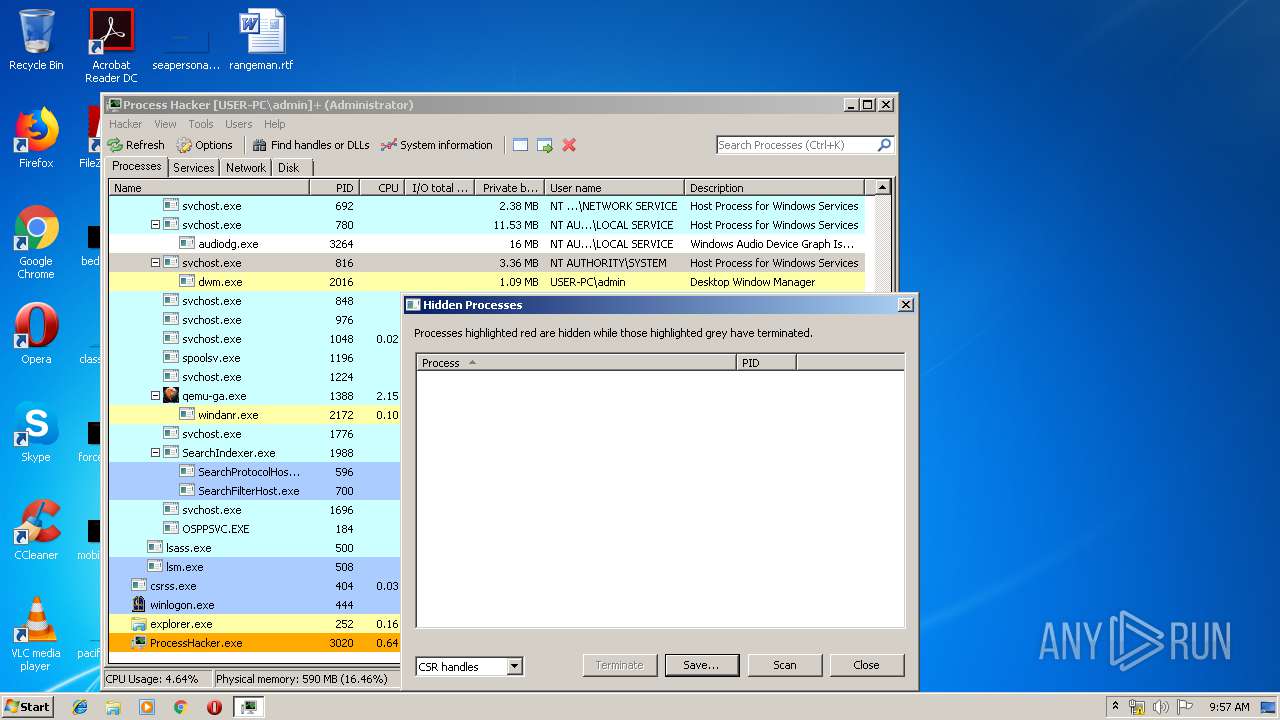
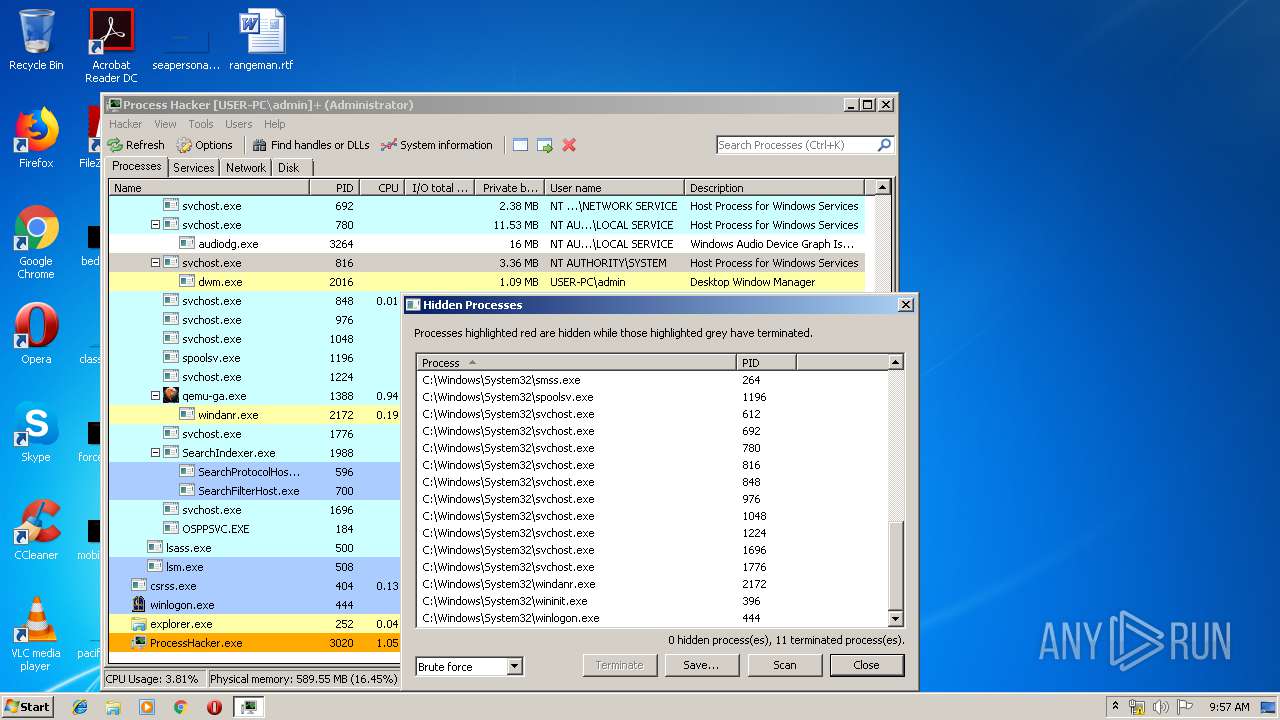
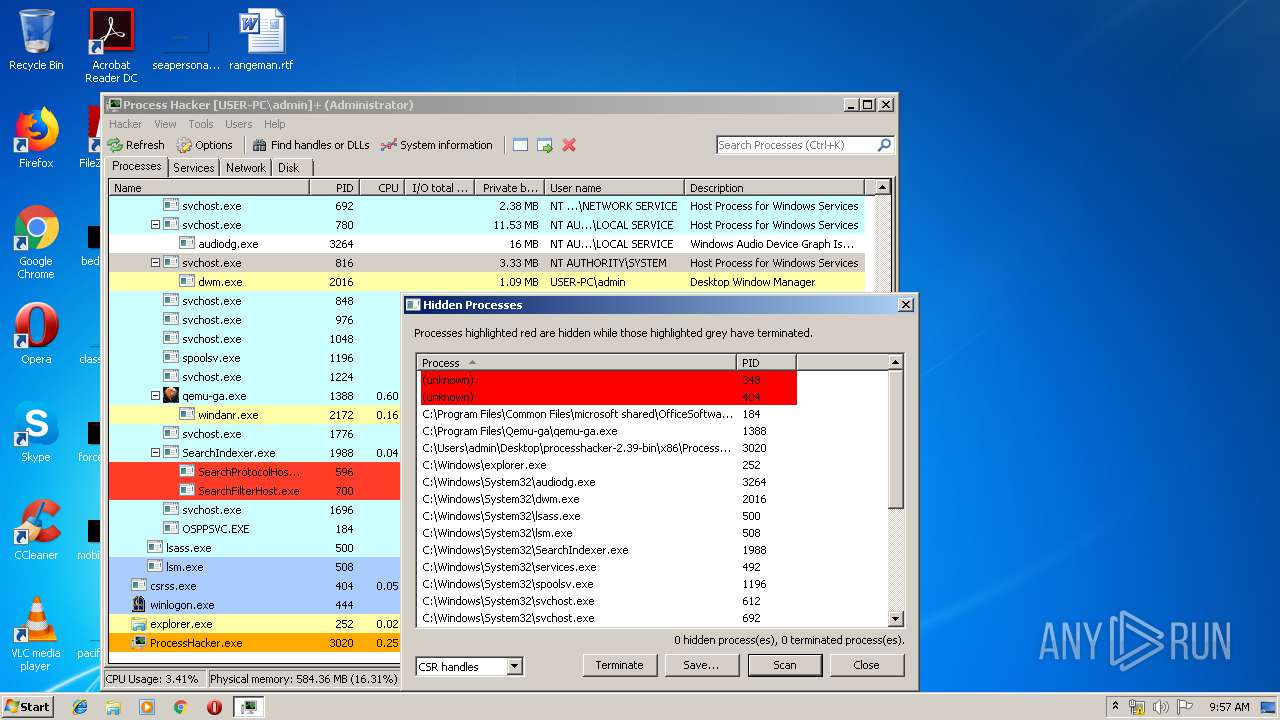
Total processes
40
Monitored processes
5
Malicious processes
3
Suspicious processes
0
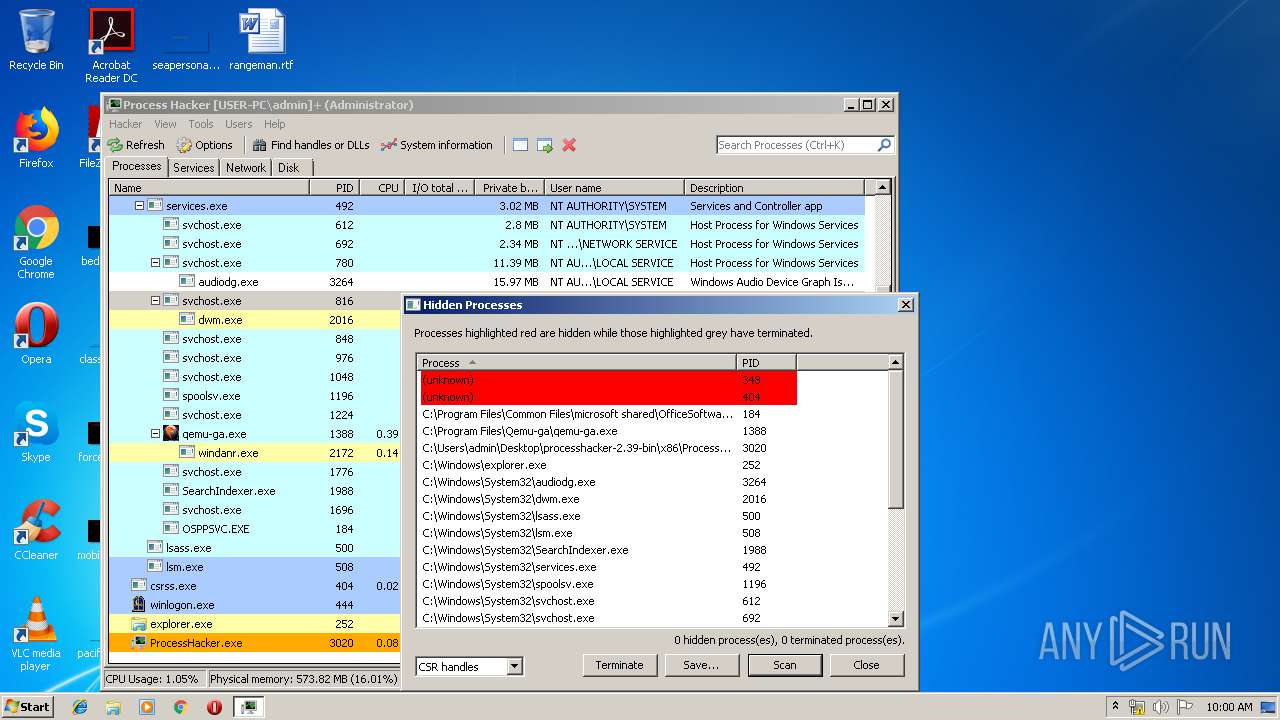
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 596 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3008 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\processhacker-2.39-bin.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
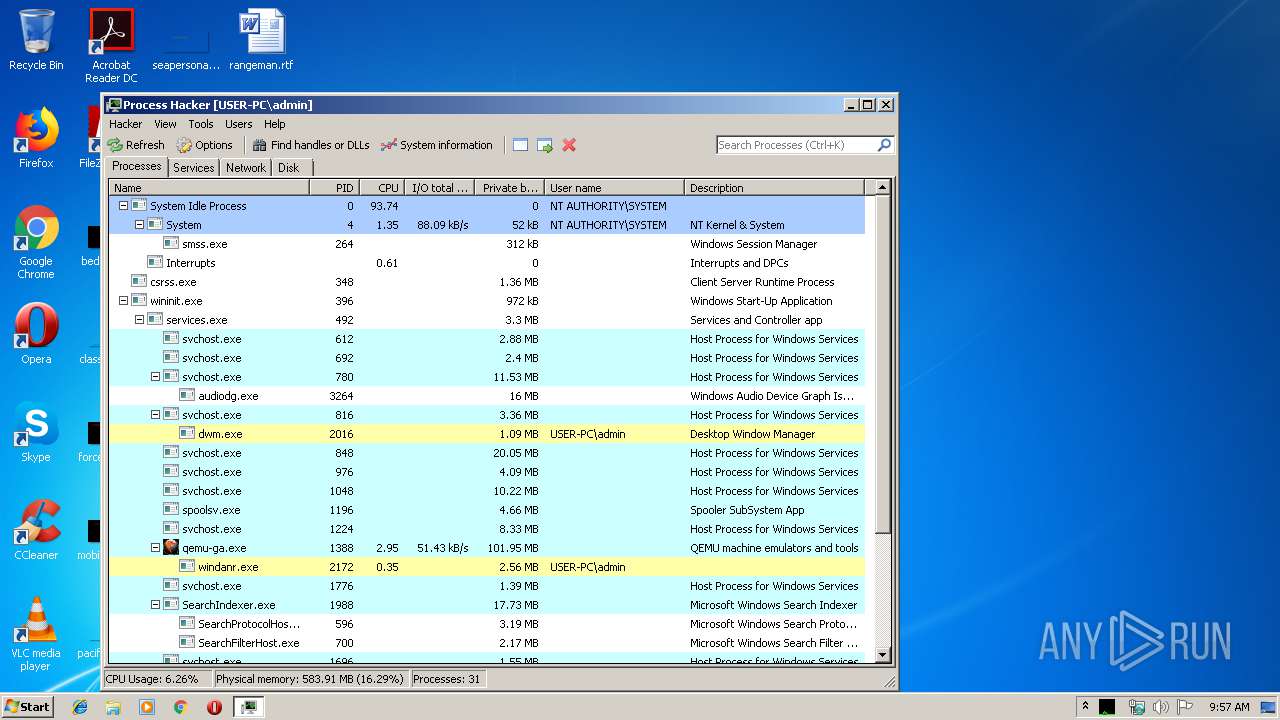
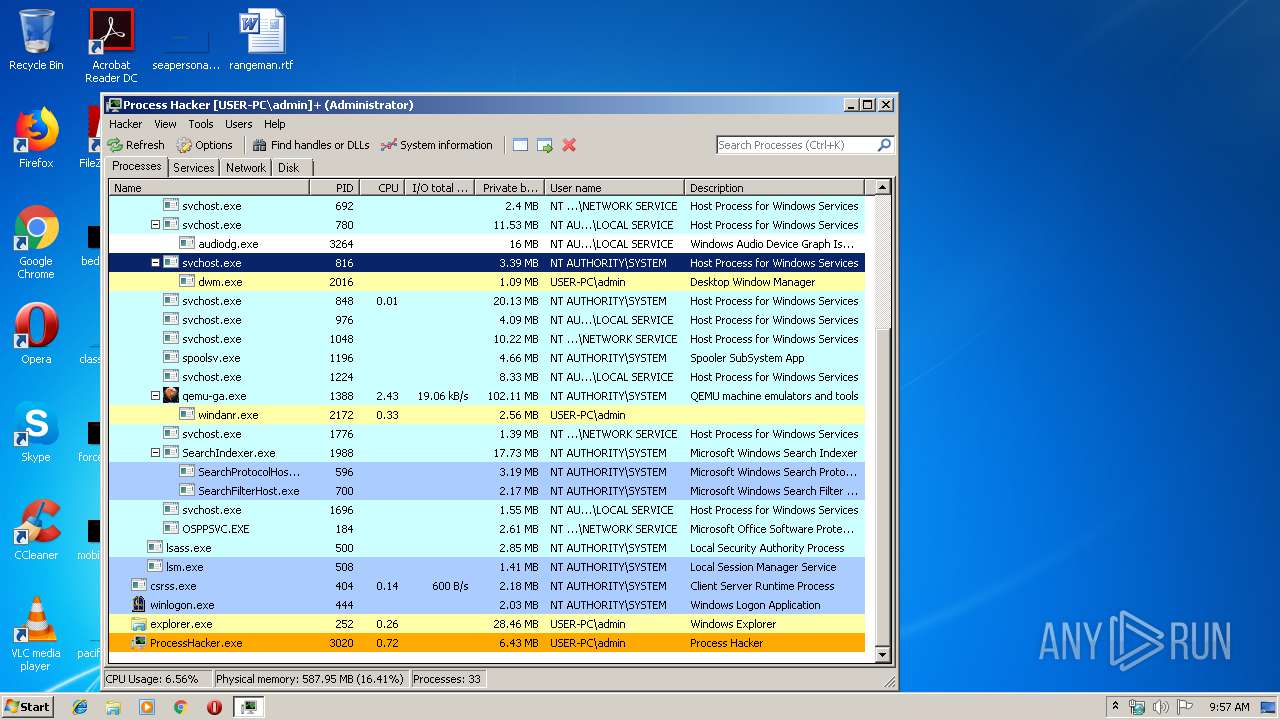
| 3020 | "C:\Users\admin\Desktop\processhacker-2.39-bin\x86\ProcessHacker.exe" -v | C:\Users\admin\Desktop\processhacker-2.39-bin\x86\ProcessHacker.exe | ProcessHacker.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: HIGH Description: Process Hacker Exit code: 0 Version: 2.39.0.124 Modules
| |||||||||||||||
| 3188 | "C:\Users\admin\Desktop\processhacker-2.39-bin\x86\ProcessHacker.exe" | C:\Users\admin\Desktop\processhacker-2.39-bin\x86\ProcessHacker.exe | explorer.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: MEDIUM Description: Process Hacker Exit code: 0 Version: 2.39.0.124 Modules
| |||||||||||||||
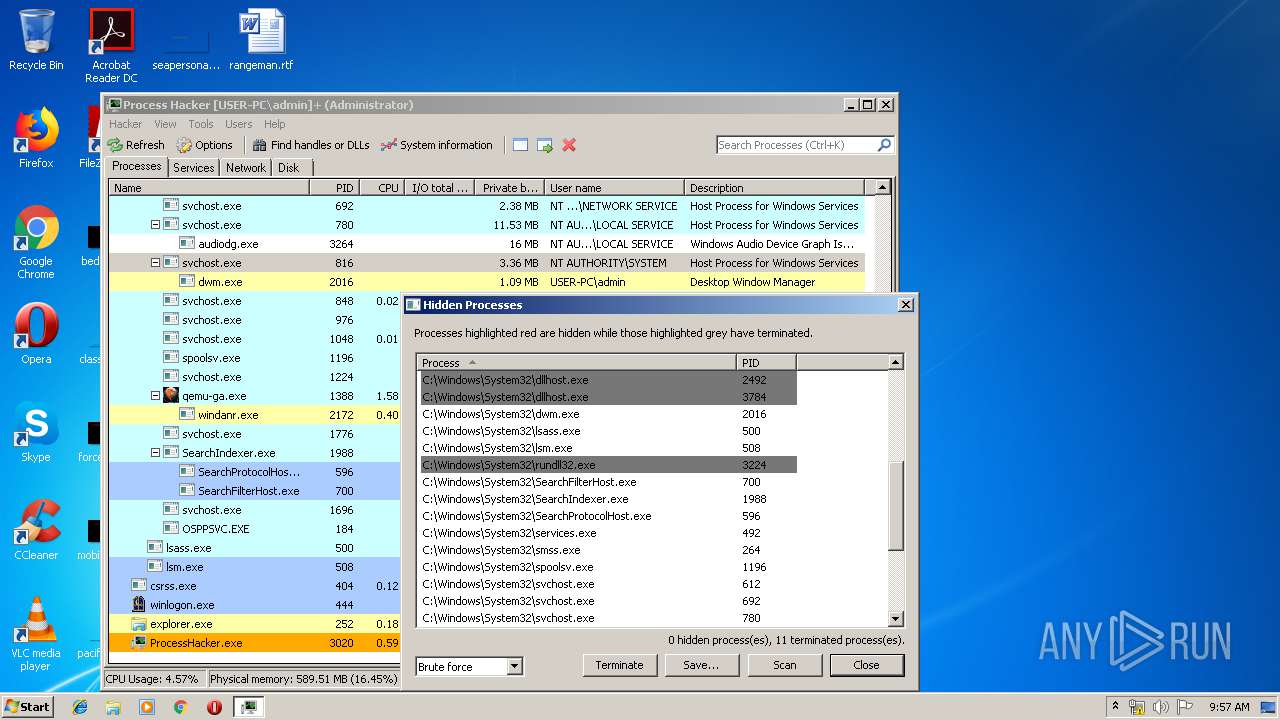
| 3224 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\processhacker-2.39-bin\x86\kprocesshacker.sys | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 572
Read events
1 481
Write events
89
Delete events
2
Modification events
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\processhacker-2.39-bin.zip | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
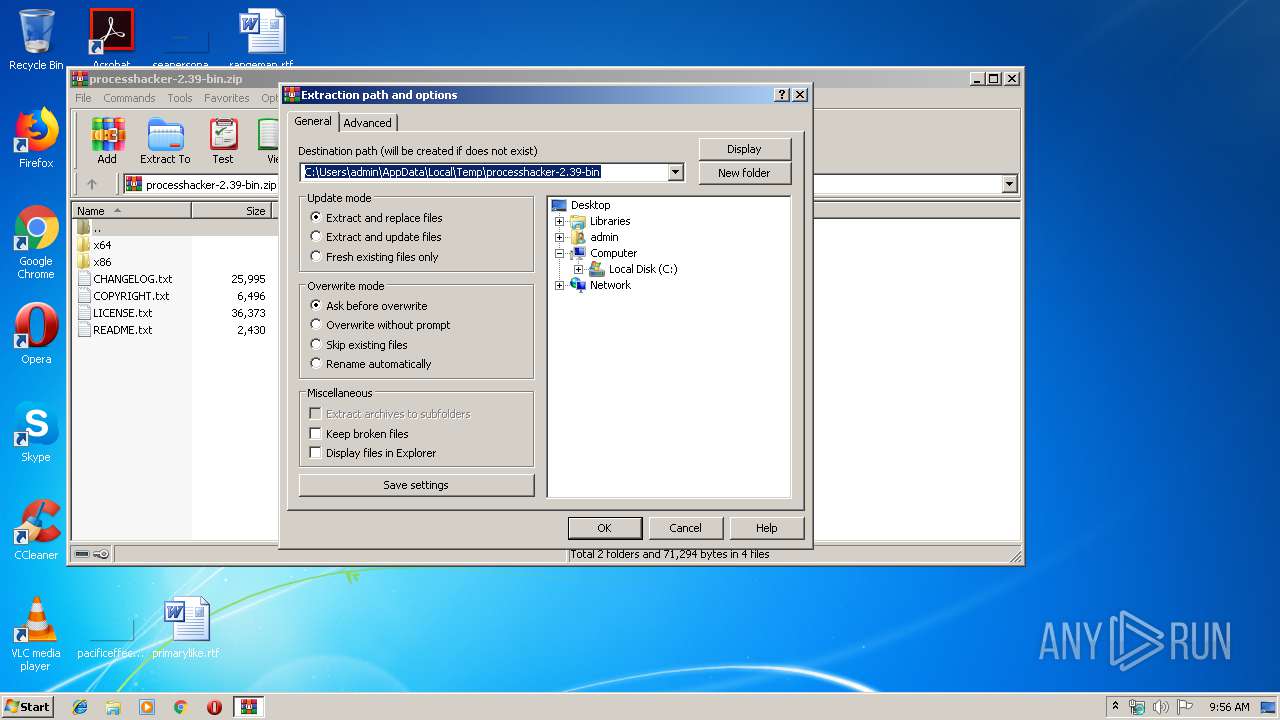
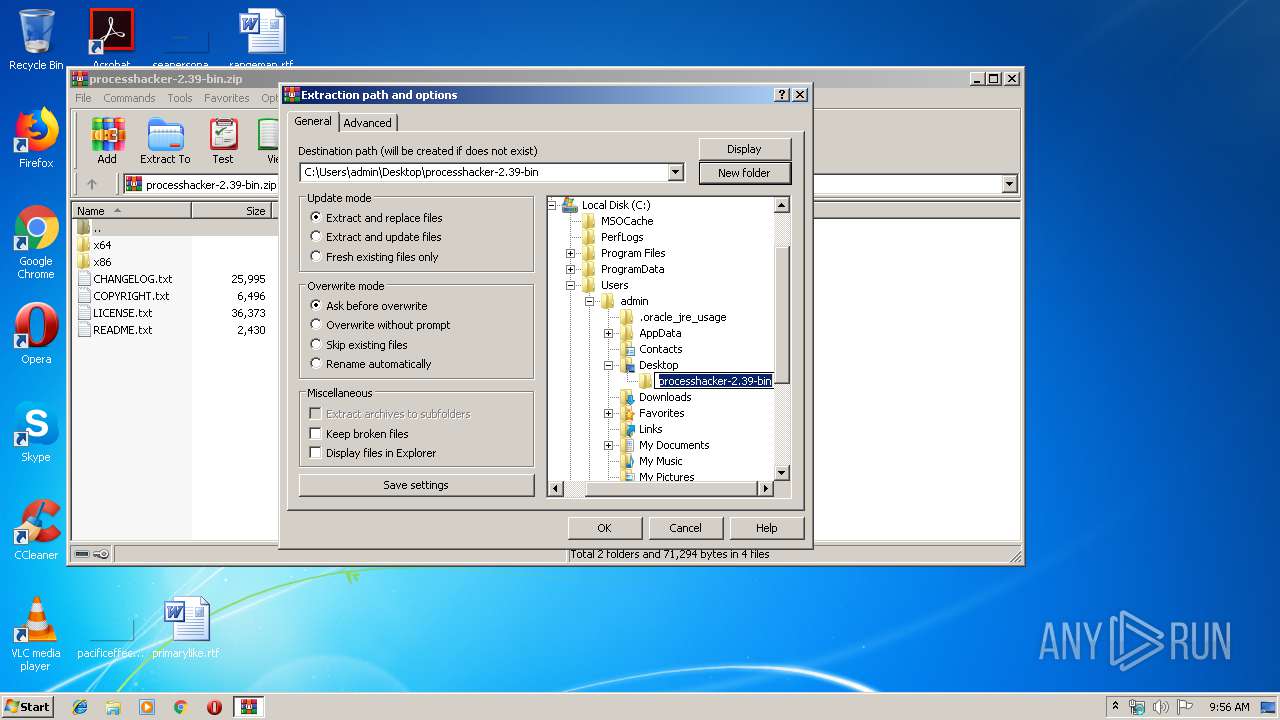
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\processhacker-2.39-bin | |||
Executable files
30
Suspicious files
1
Text files
6
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3008 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\peview.exe | executable | |
MD5:DDE1F44789CD50C1F034042D337DEAE3 | SHA256:4259E53D48A3FED947F561FF04C7F94446BEDD64C87F52400B2CB47A77666AAA | |||
| 3008 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\OnlineChecks.dll | executable | |
MD5:12C25FB356E51C3FD81D2D422A66BE89 | SHA256:7336D66588BBCFEA63351A2EB7C8D83BBD49B5D959BA56A94B1FE2E905A5B5DE | |||
| 3008 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\kprocesshacker.sys | executable | |
MD5:1B5C3C458E31BEDE55145D0644E88D75 | SHA256:70211A3F90376BBC61F49C22A63075D1D4DDD53F0AEFA976216C46E6BA39A9F4 | |||
| 3008 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\DotNetTools.dll | executable | |
MD5:B16CE8BA8E7F0EE83EC1D49F2D0AF0A7 | SHA256:B4CC0280E2CAA0335361172CB7D673F745DEFC78299DED808426FFBC2458E4D9 | |||
| 3008 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\Updater.dll | executable | |
MD5:6976B57C6391F54DBD2828A45CA81100 | SHA256:0C11CDC3765FFB53BA9707B6F99EC17AE4F7334578A935BA7BCBBC9C7BDEED2E | |||
| 3008 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\ExtendedTools.dll | executable | |
MD5:BC61E6FB02FBBFE16FB43CC9F4E949F1 | SHA256:F2805E0F81513641A440F1A21057A664961C22192CB33FCA3870362C8F872D87 | |||
| 3008 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\NetworkTools.dll | executable | |
MD5:D6BED1D6FDBED480E32FDD2DD4C13352 | SHA256:476AA6AF14DD0B268786E32543B9A6917A298D4D90E1015DAC6FB2B522CF5D2E | |||
| 3008 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\HardwareDevices.dll | executable | |
MD5:A46C8BB886E0B9290E5DBC6CA524D61F | SHA256:ACD49F2AA36D4EFB9C4949E2D3CC2BD7AEE384C2CED7AA9E66063DA4150FCB00 | |||
| 3008 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\README.txt | text | |
MD5:72AC5A8DD6491E525B9783C9BC439FE6 | SHA256:0C4F051675A690EA4DB6AB2EB81FDCED6990E2538AD21DC4610AA5925253A090 | |||
| 3008 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\COPYRIGHT.txt | text | |
MD5:39B07060A5C6199730219E29C747C061 | SHA256:319CD301CF40BE03C00CD086560D4E810E0F6D0DBFDC2D28D6AF3522C027CF49 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3188 | ProcessHacker.exe | 162.243.25.33:443 | wj32.org | Digital Ocean, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wj32.org |
| whitelisted |