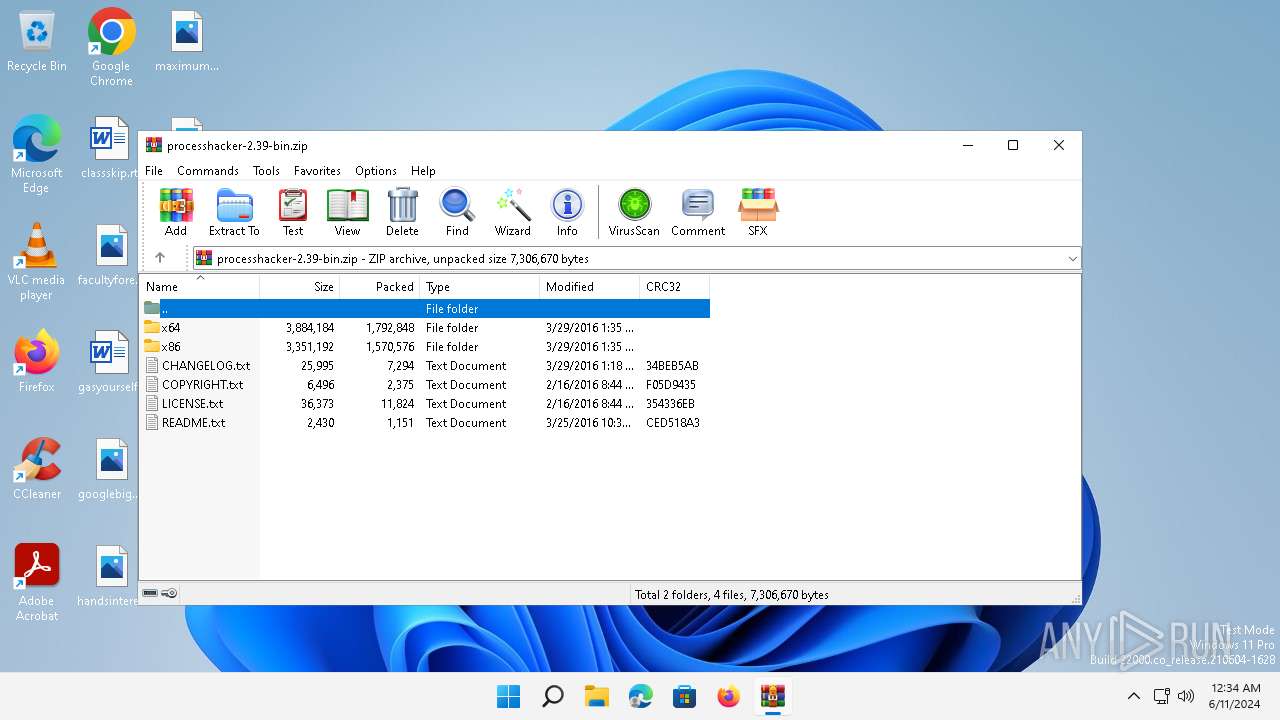
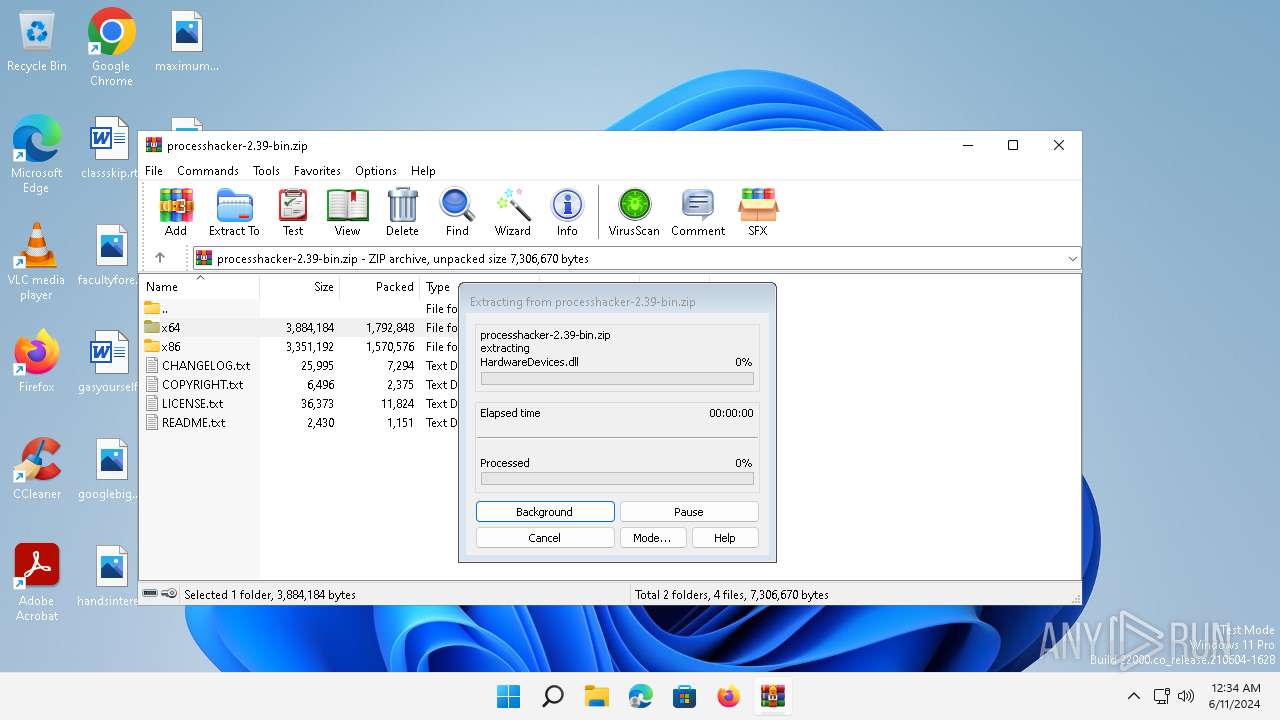
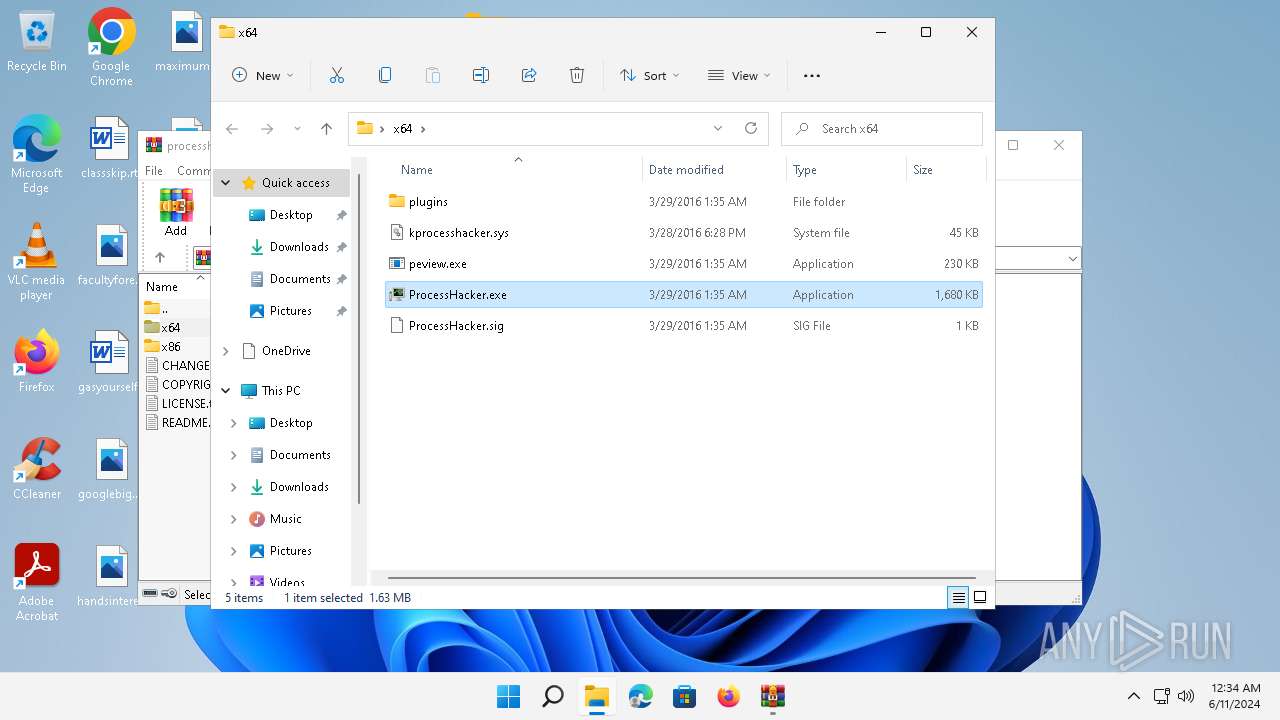
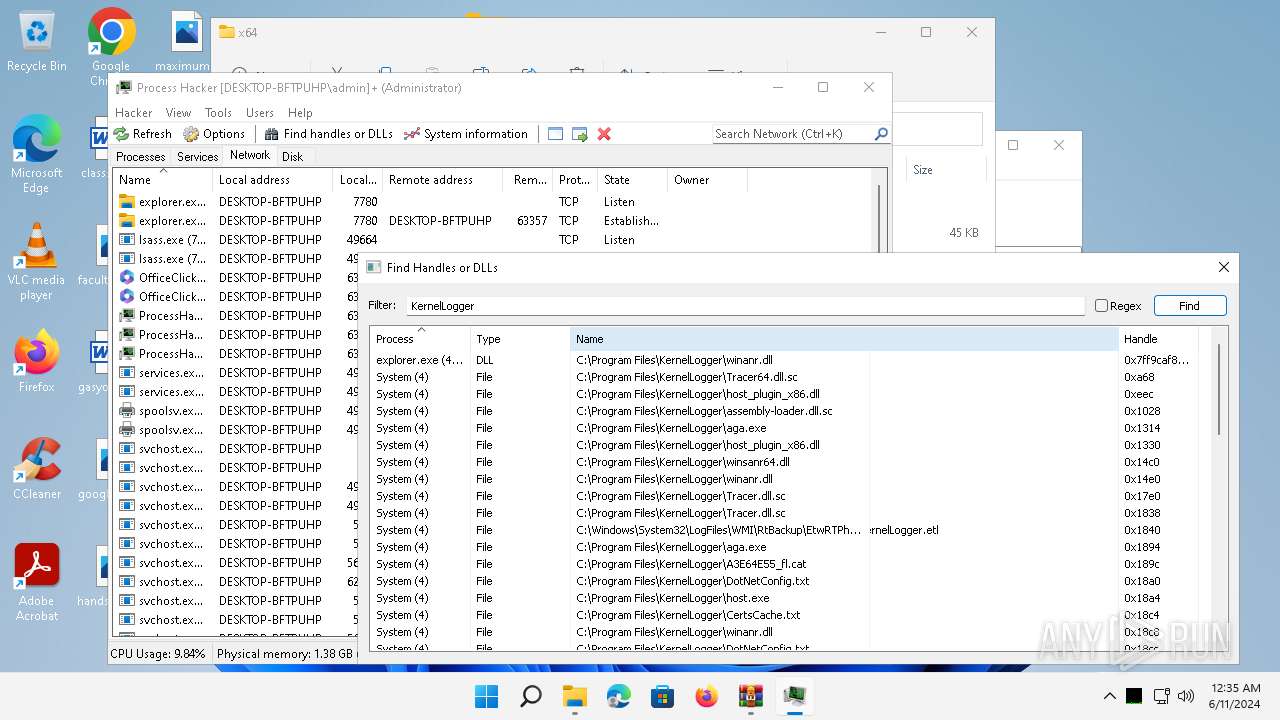
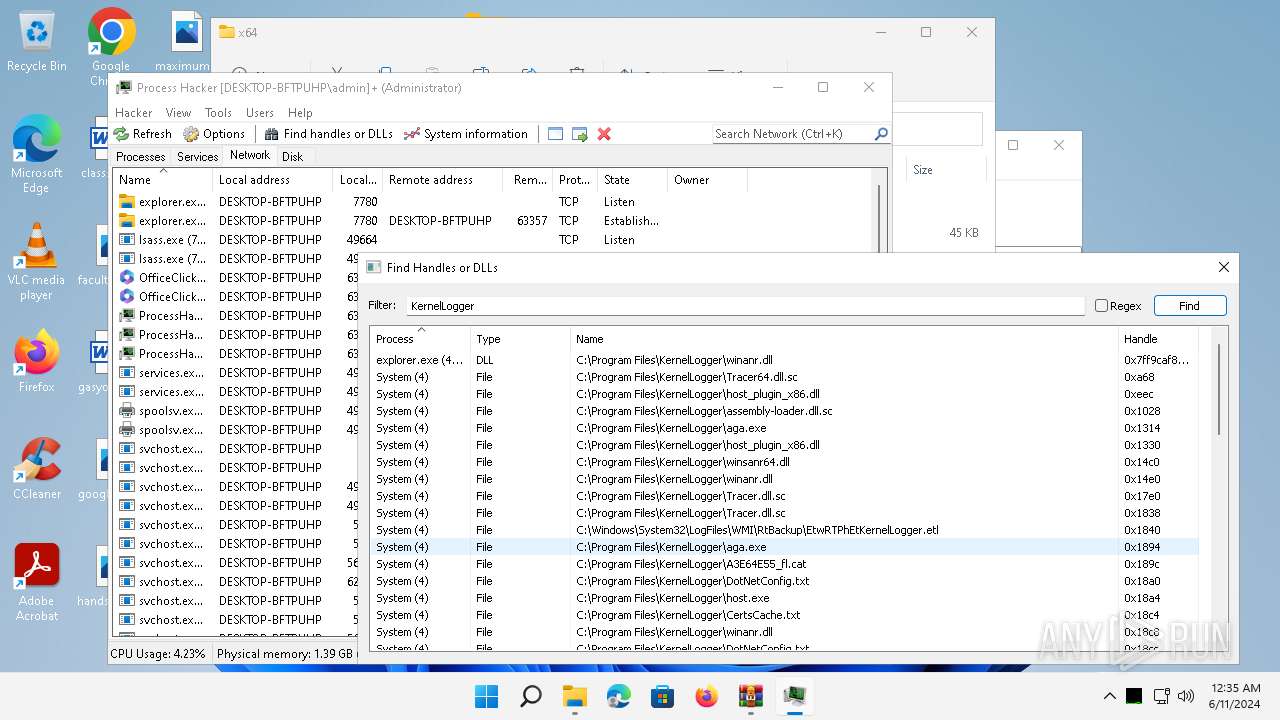
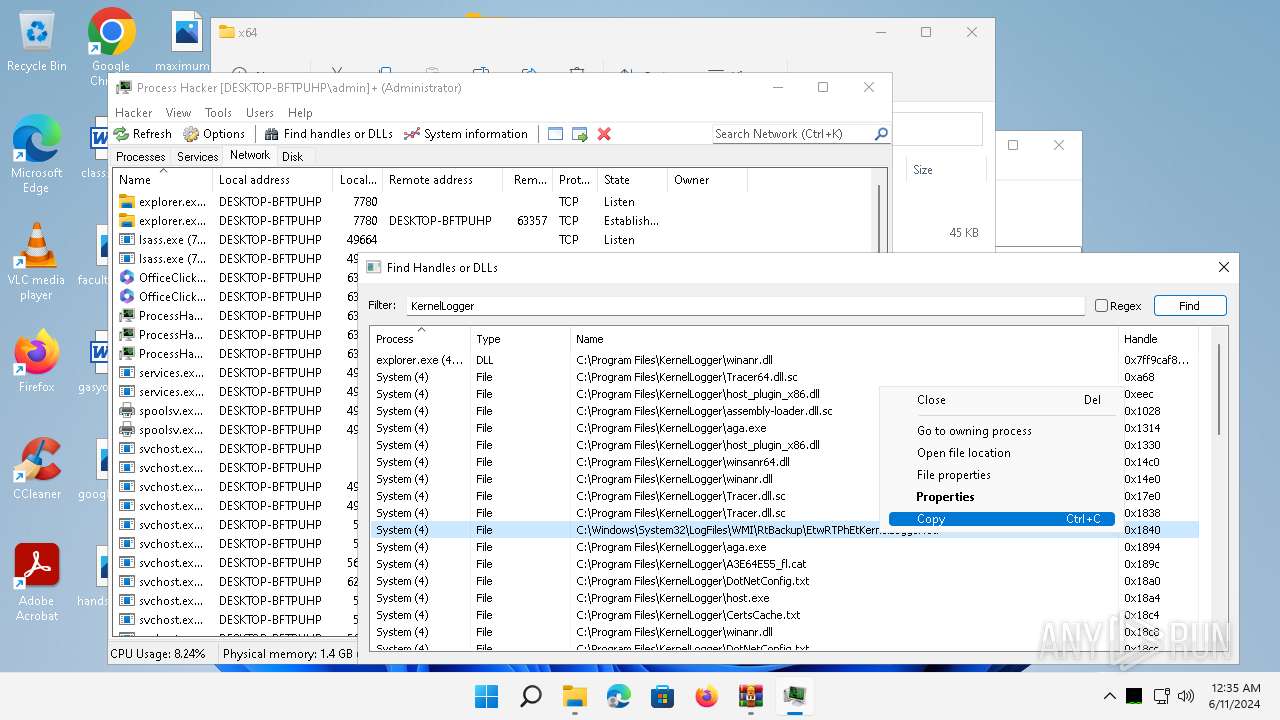
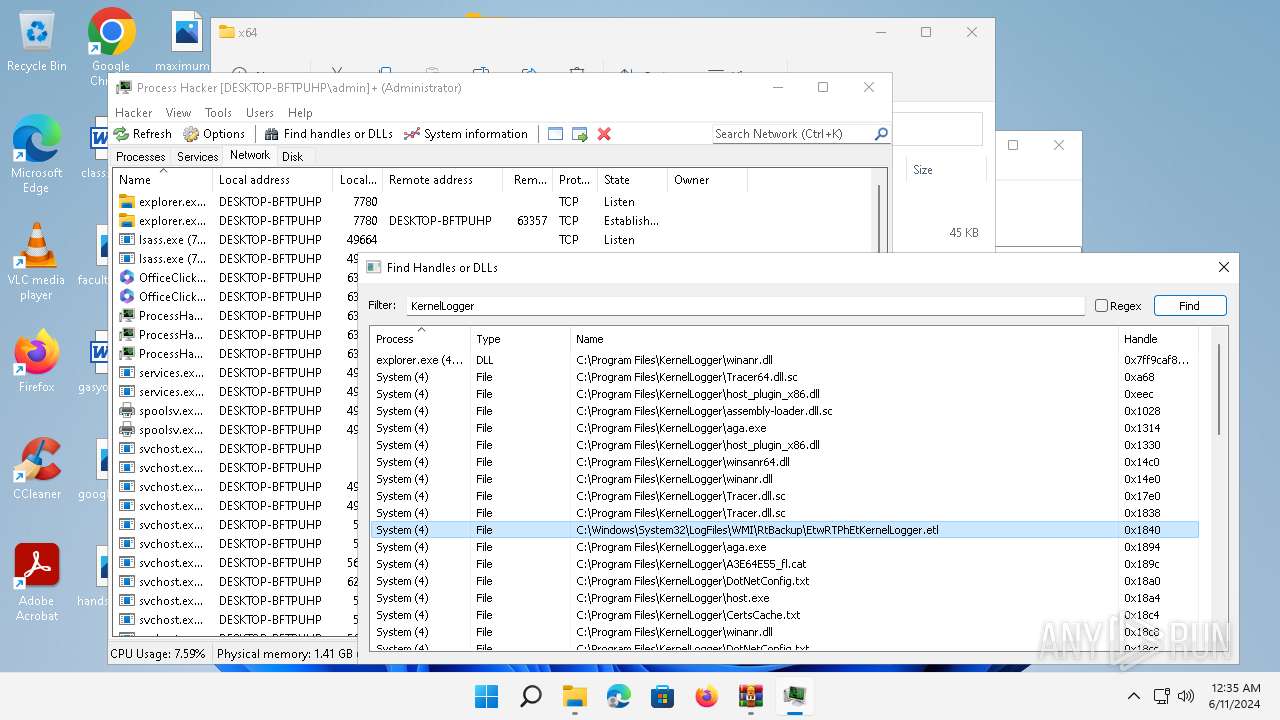
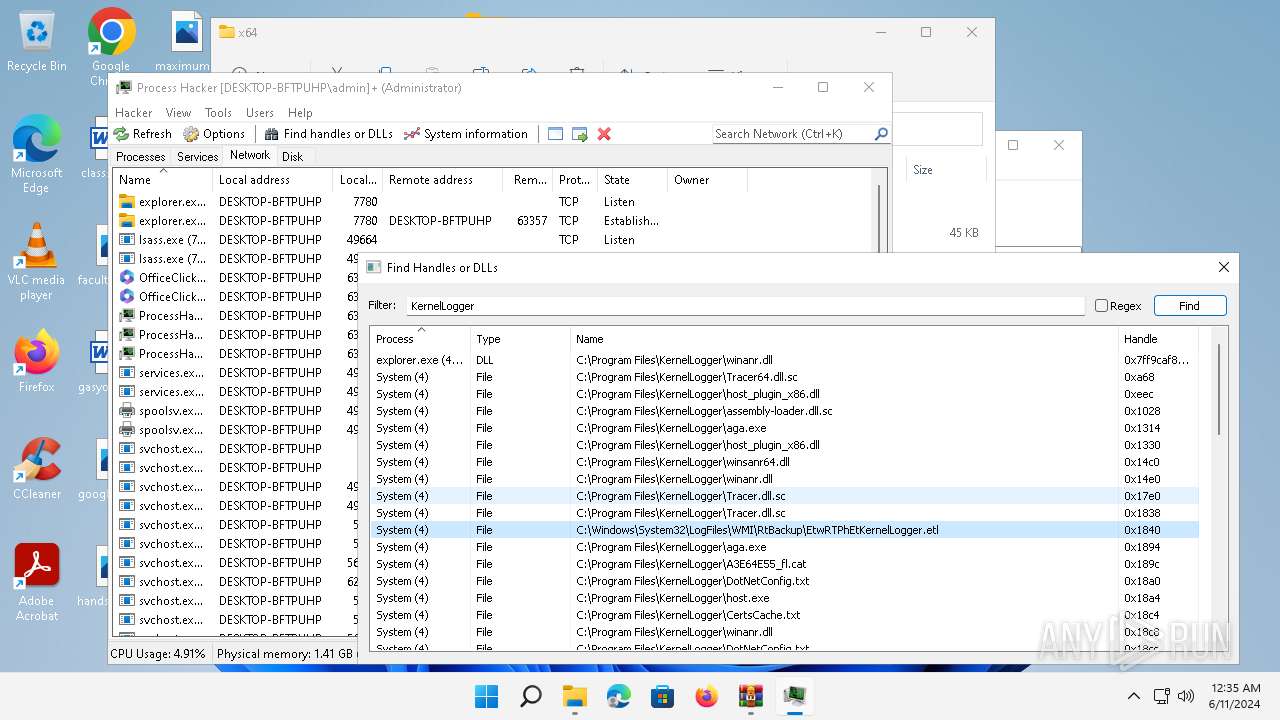
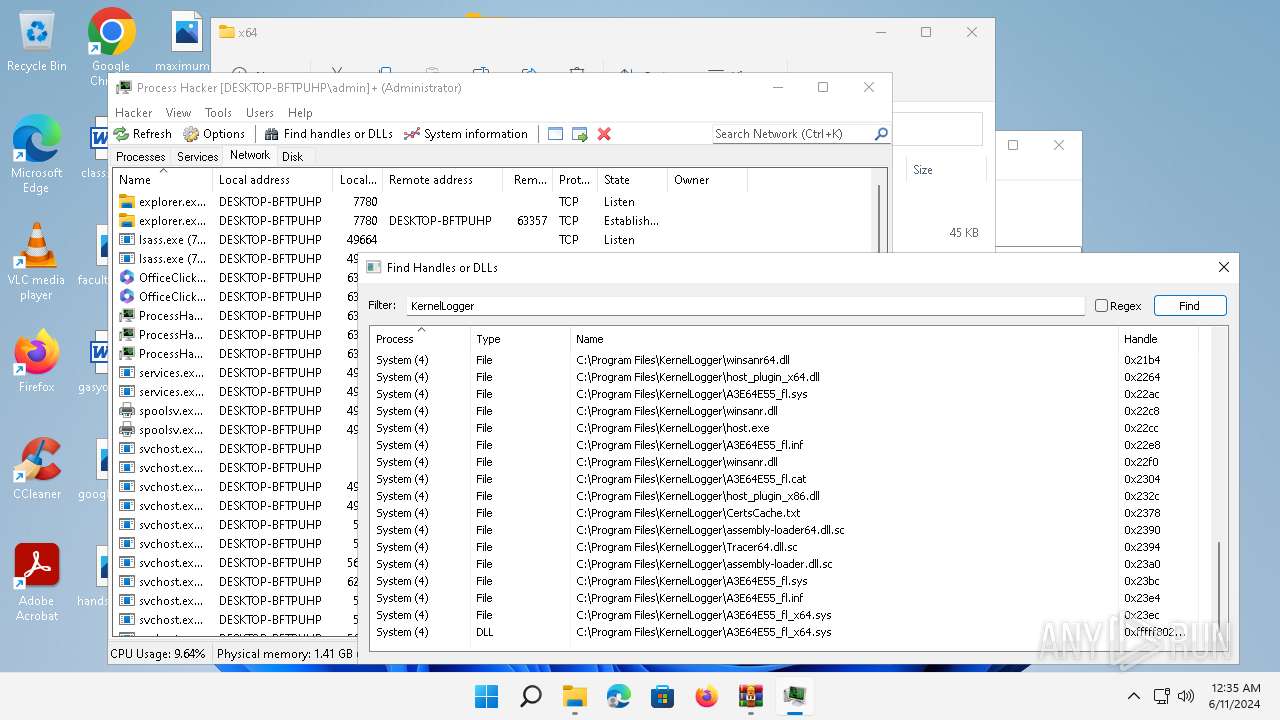
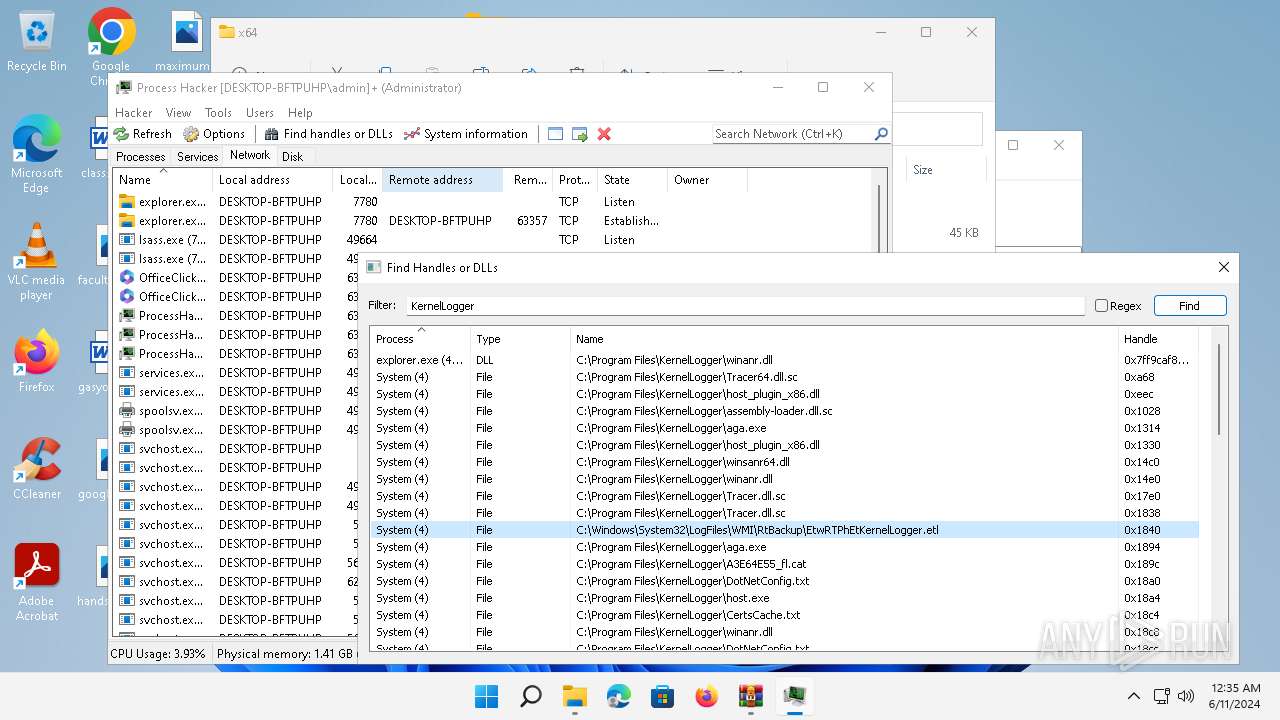
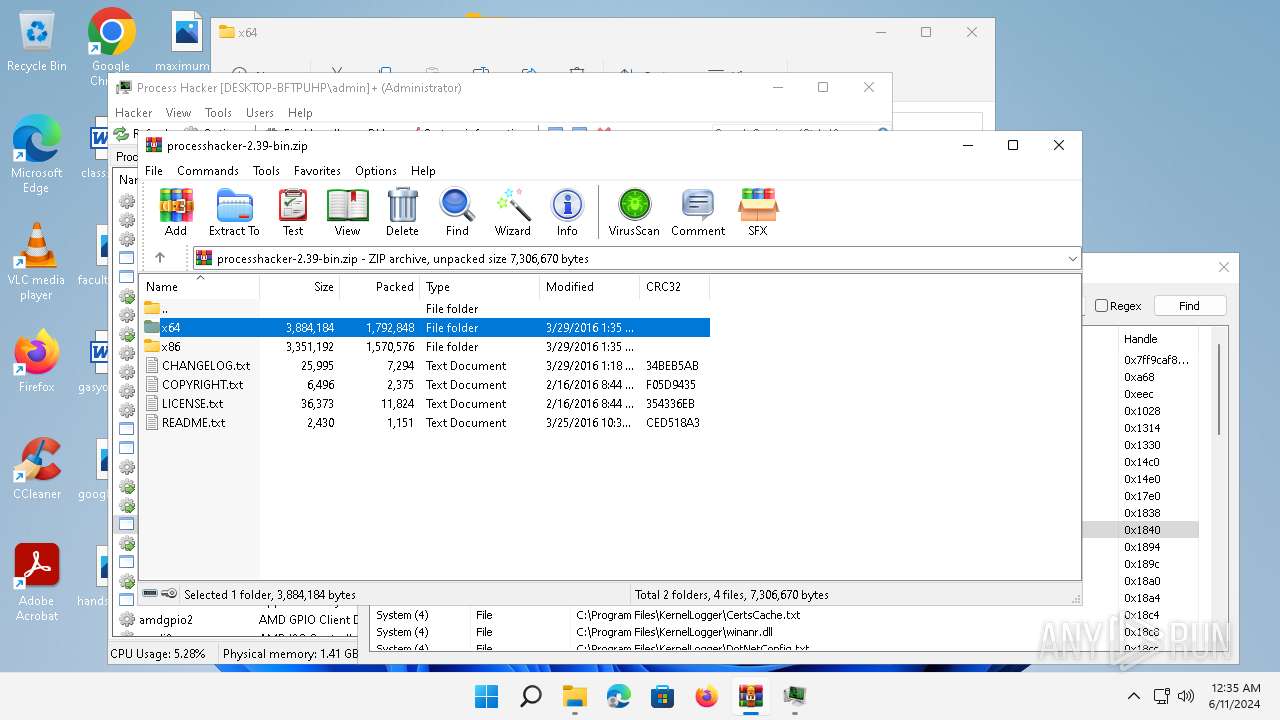
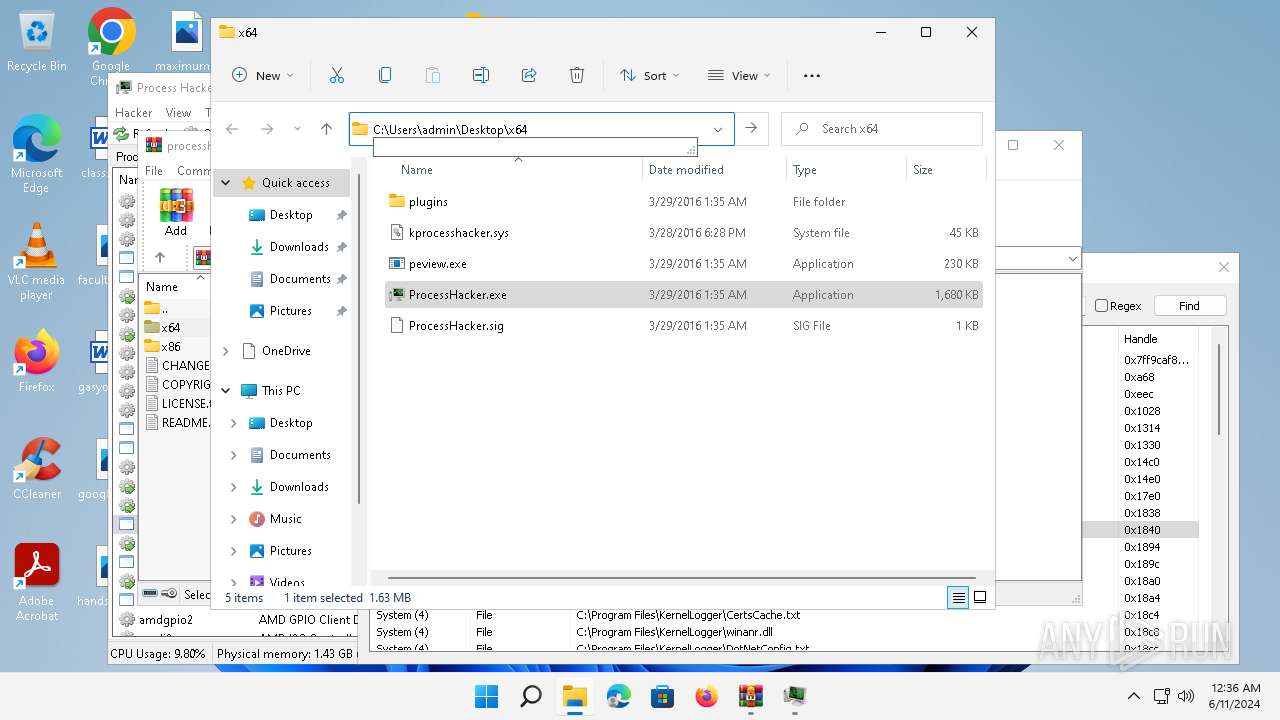
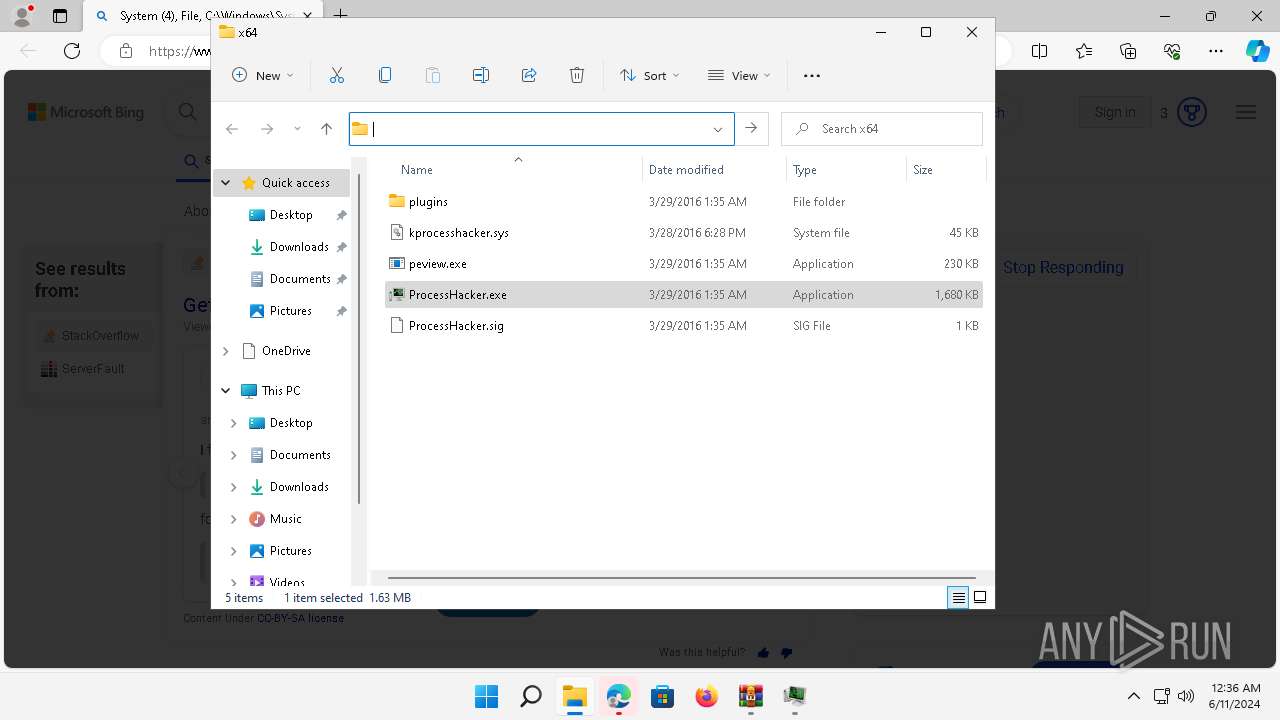
| File name: | processhacker-2.39-bin.zip |
| Full analysis: | https://app.any.run/tasks/7af2d1e6-2929-47bb-ba83-23ff7c92e774 |
| Verdict: | Malicious activity |
| Analysis date: | June 11, 2024, 00:34:03 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | B444CF14642CE9B8D75E079166A5DF0B |
| SHA1: | 8E8F8423D163D922242B8B7D85427664F77EDC97 |
| SHA256: | 2AFB5303E191DDE688C5626C3EE545E32E52F09DA3B35B20F5E0D29A418432F5 |
| SSDEEP: | 98304:jDqt5TrOmlLB/7rTOqcXfOzJR1qioDLK2EbhQ:3sTrHlB73OqX4ioDfshQ |
MALICIOUS
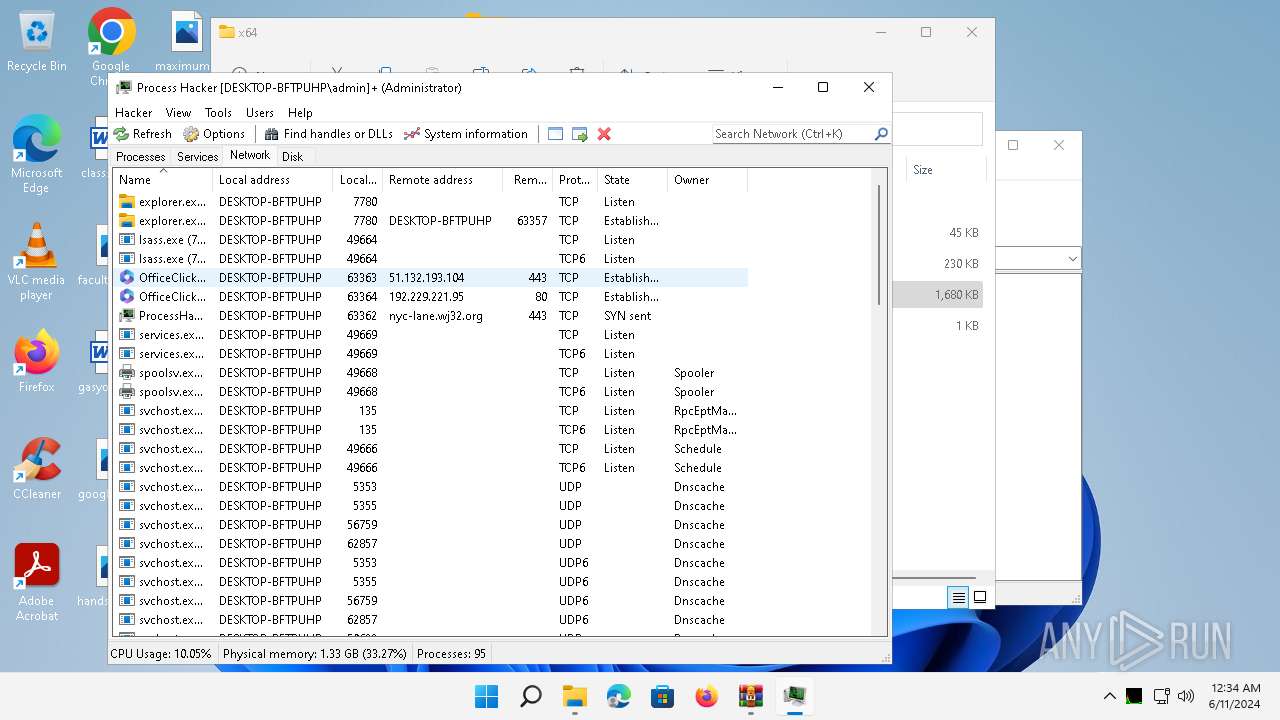
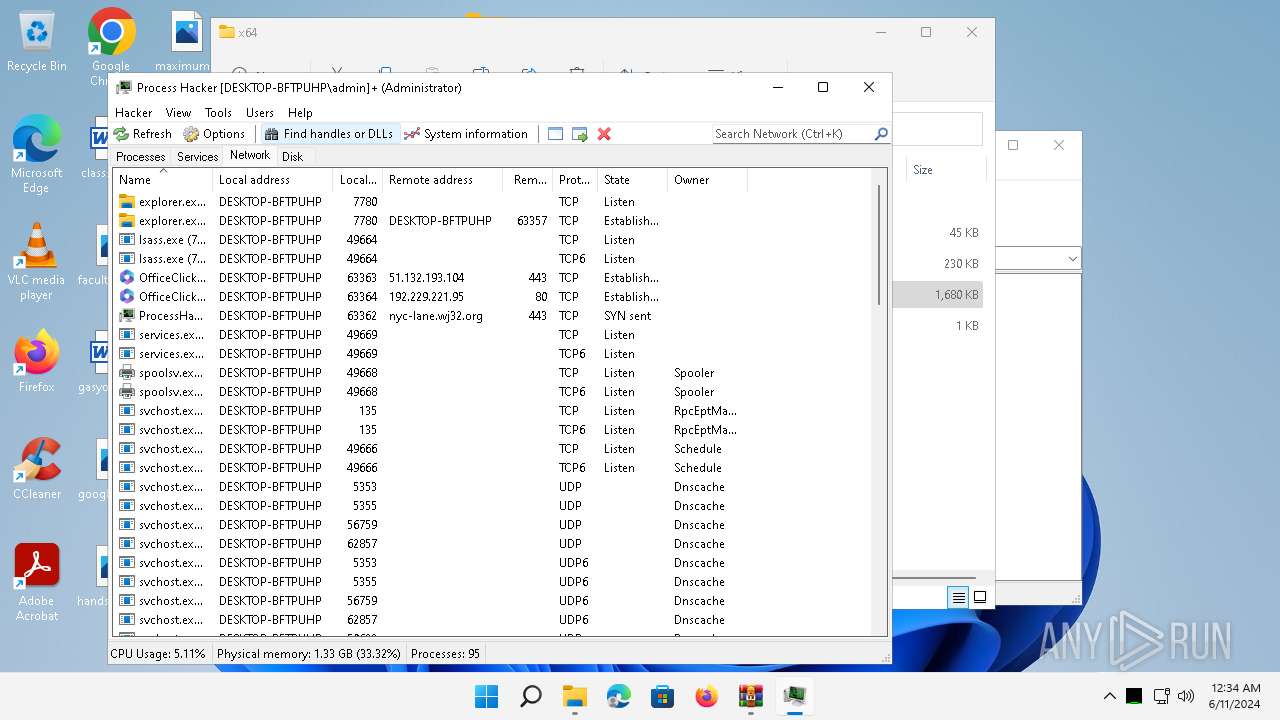
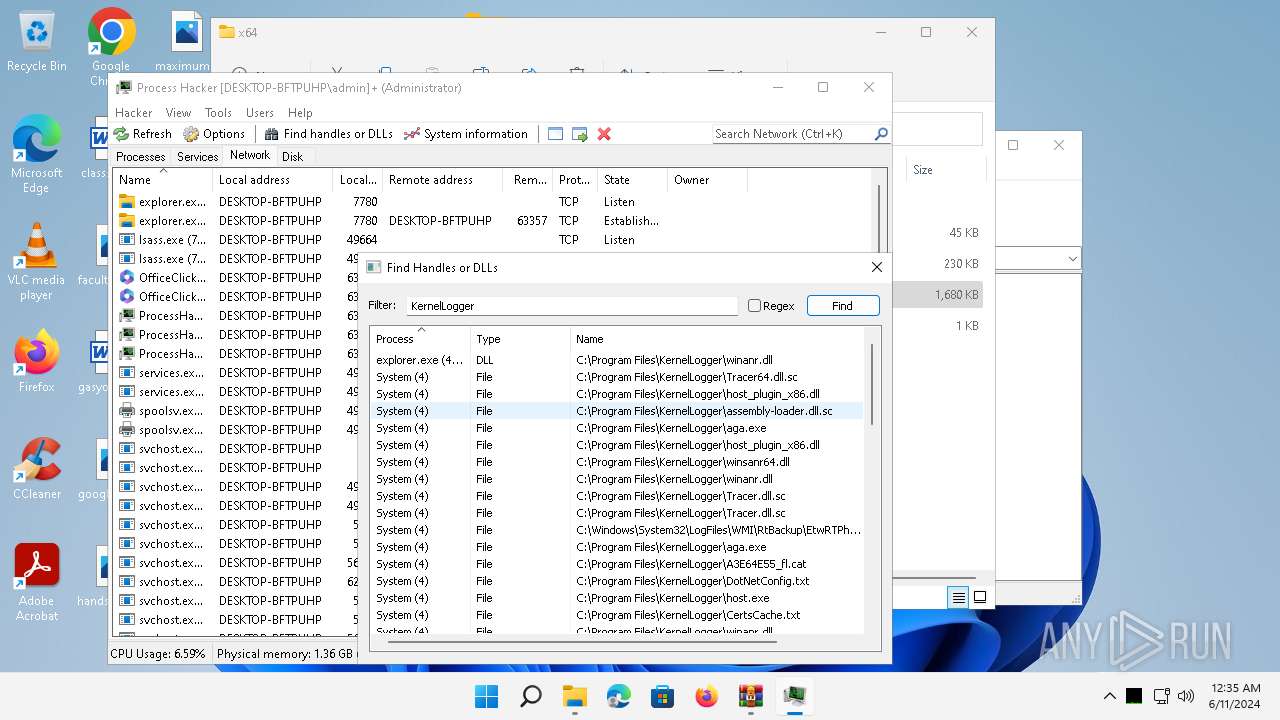
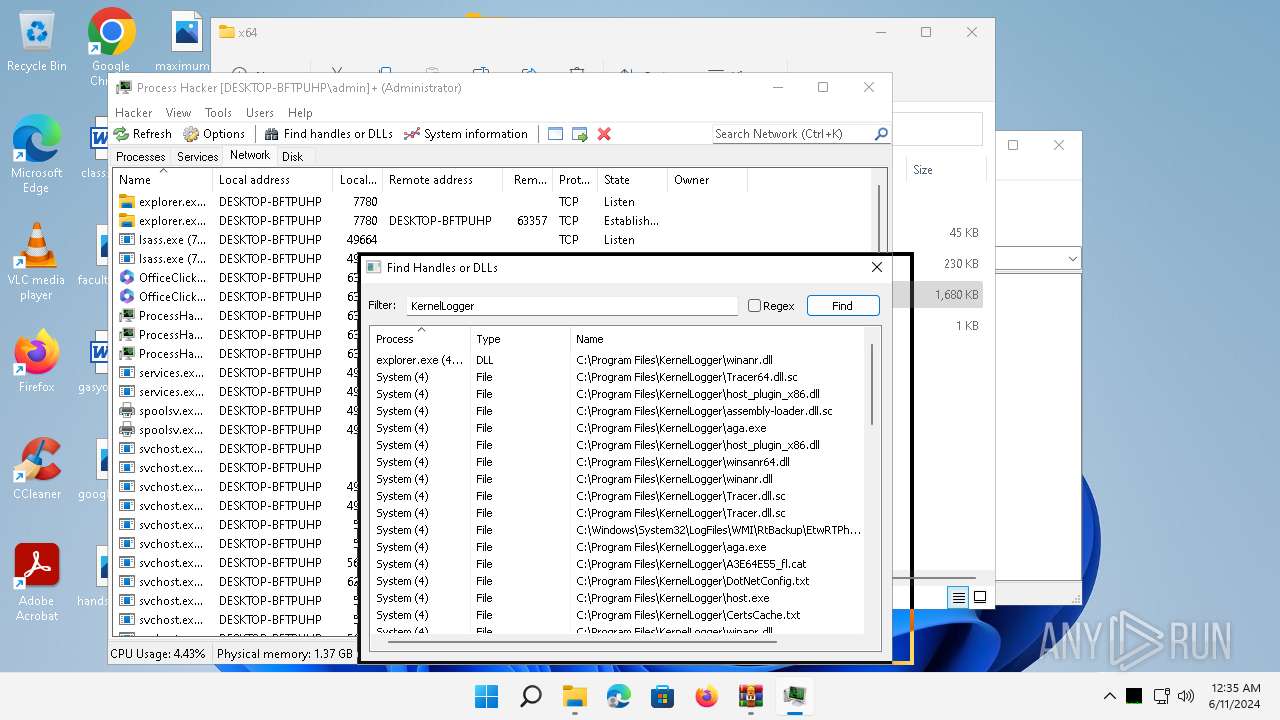
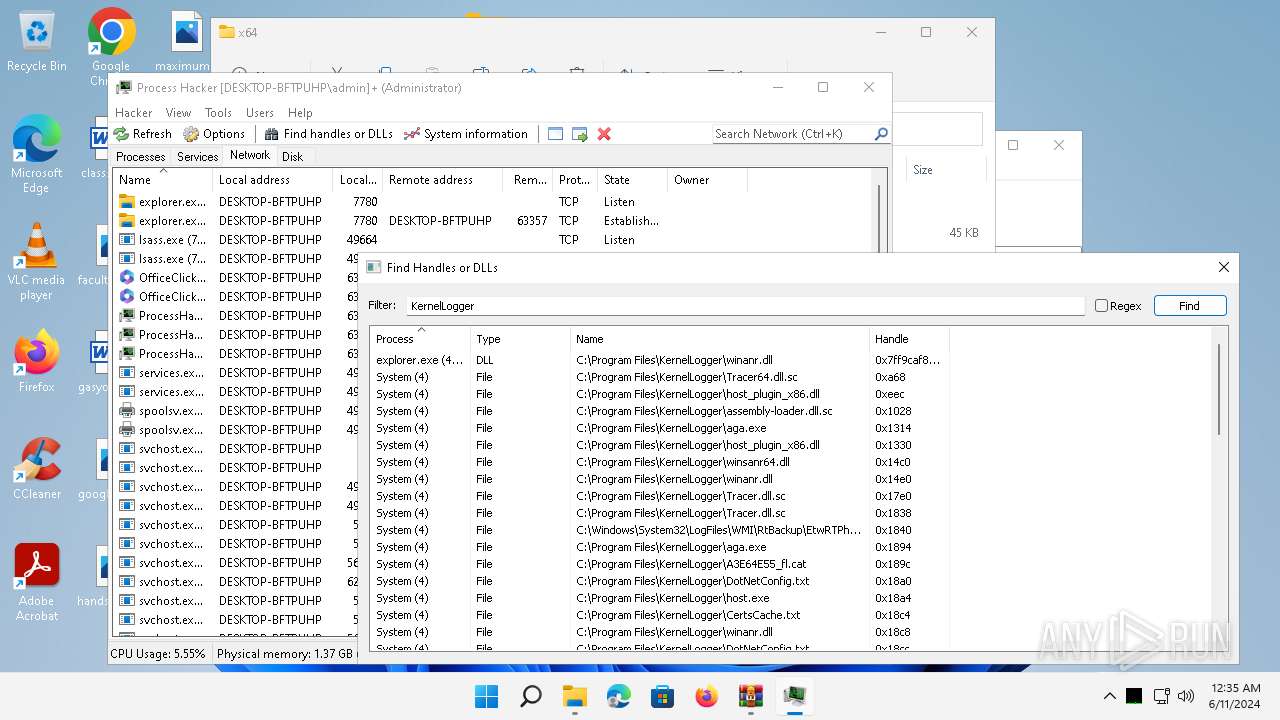
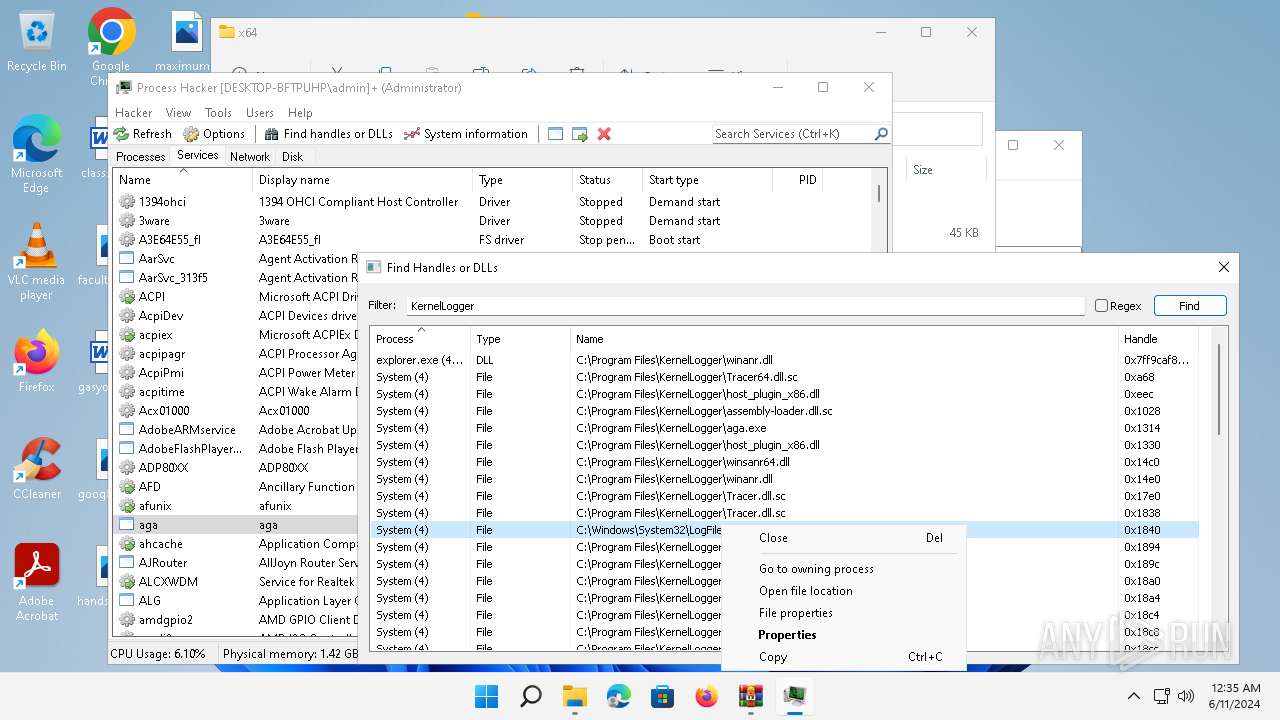
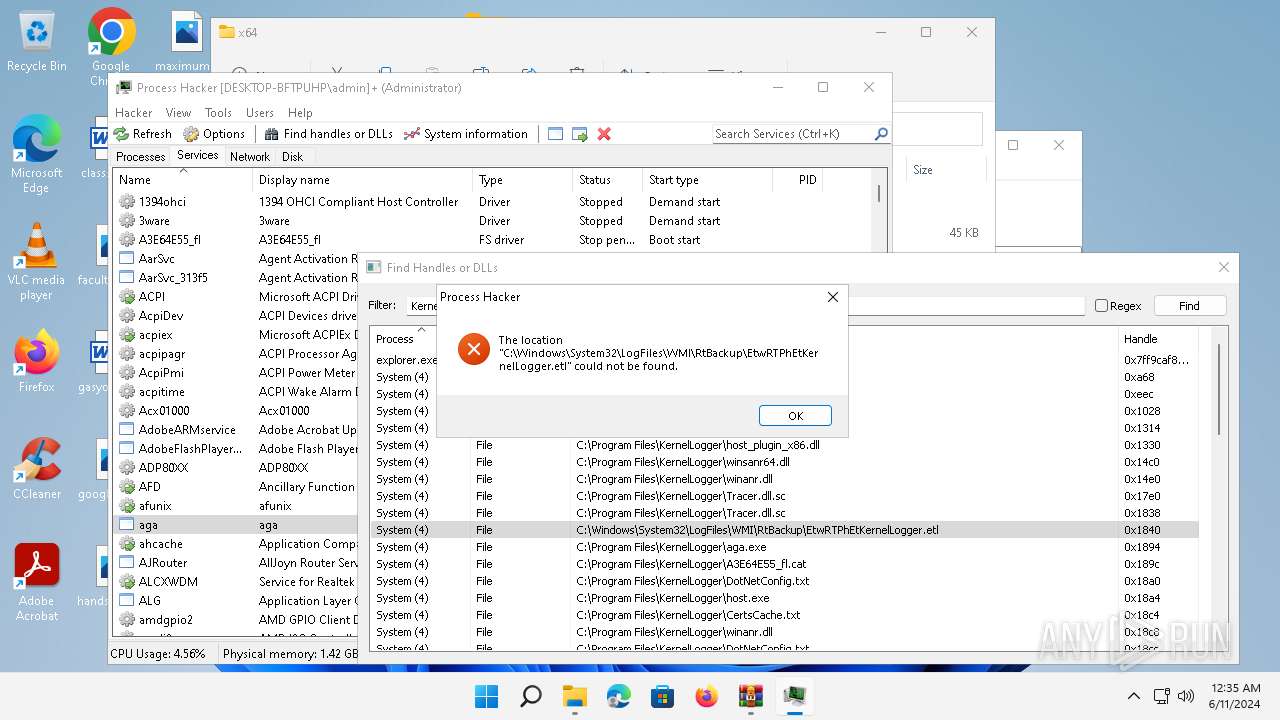
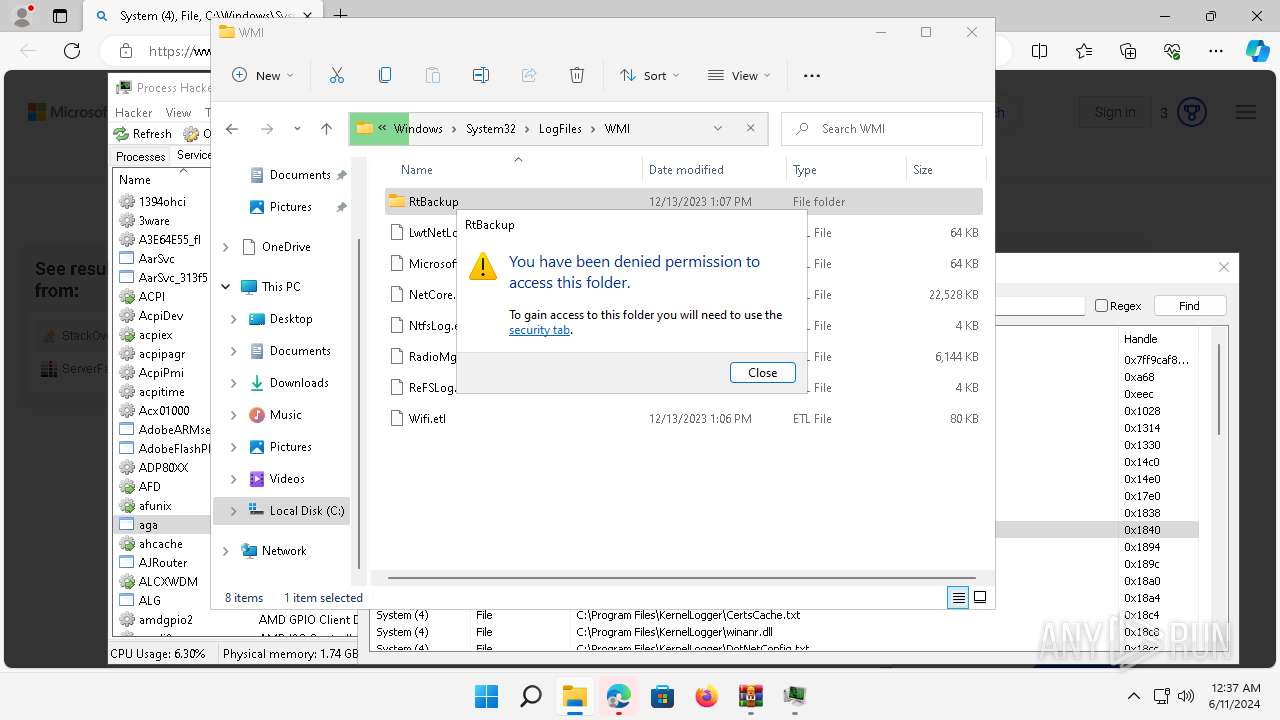
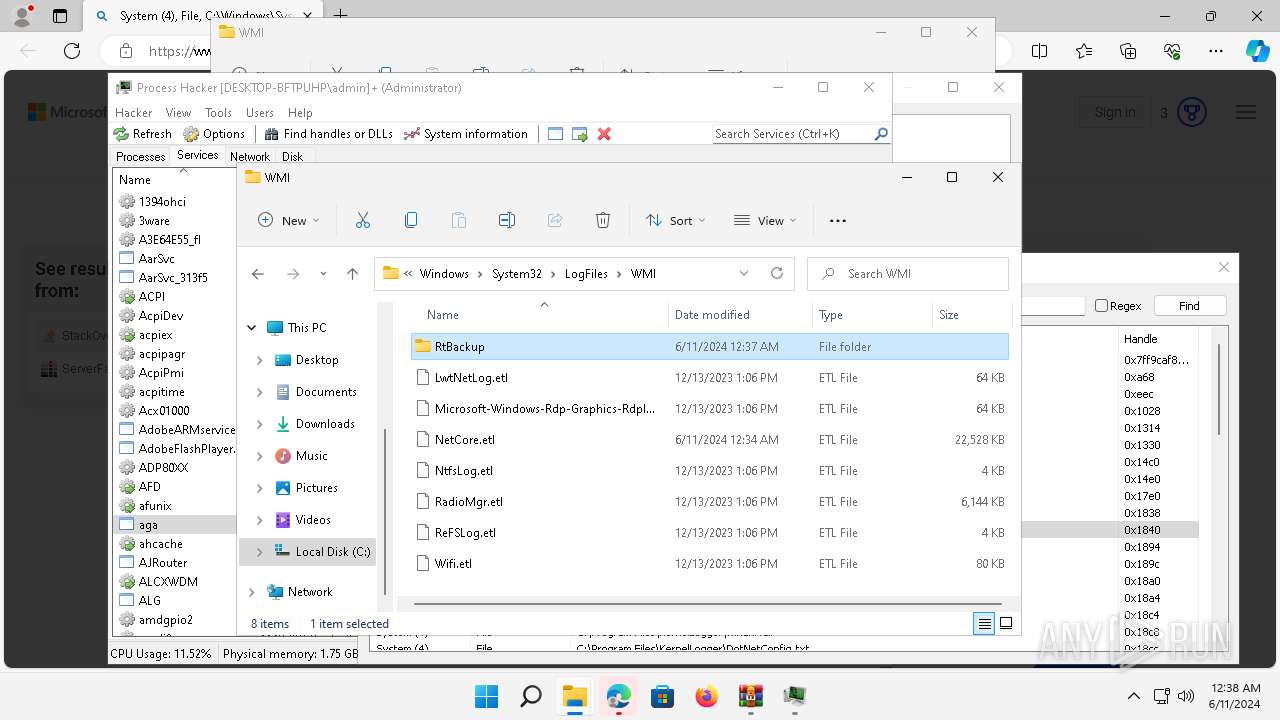
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2808)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2808)
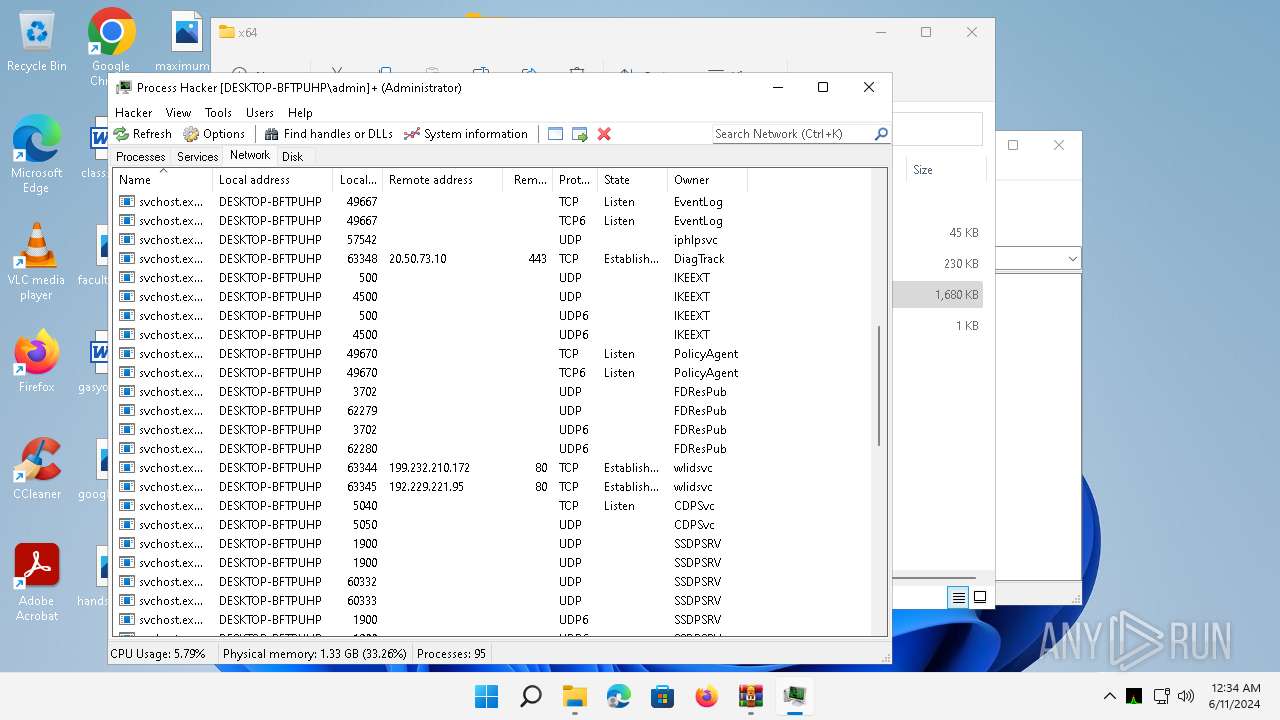
- ProcessHacker.exe (PID: 1536)
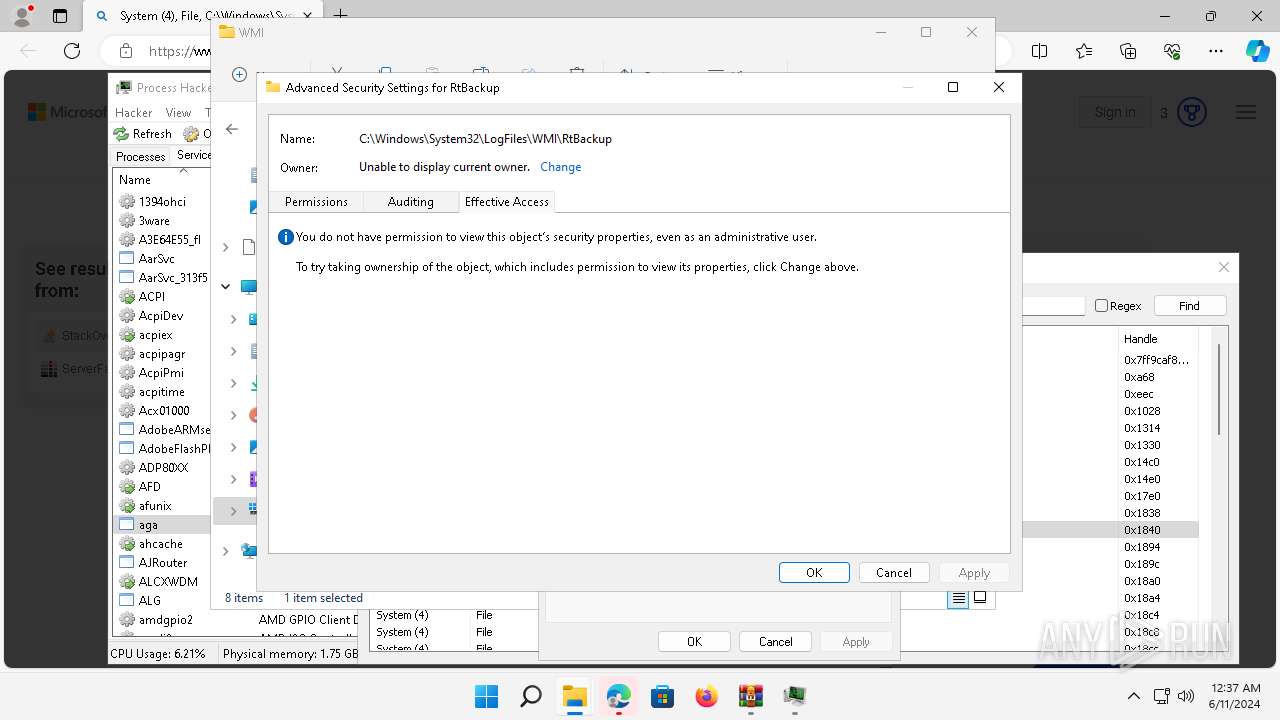
Checks Windows Trust Settings
- ProcessHacker.exe (PID: 1536)
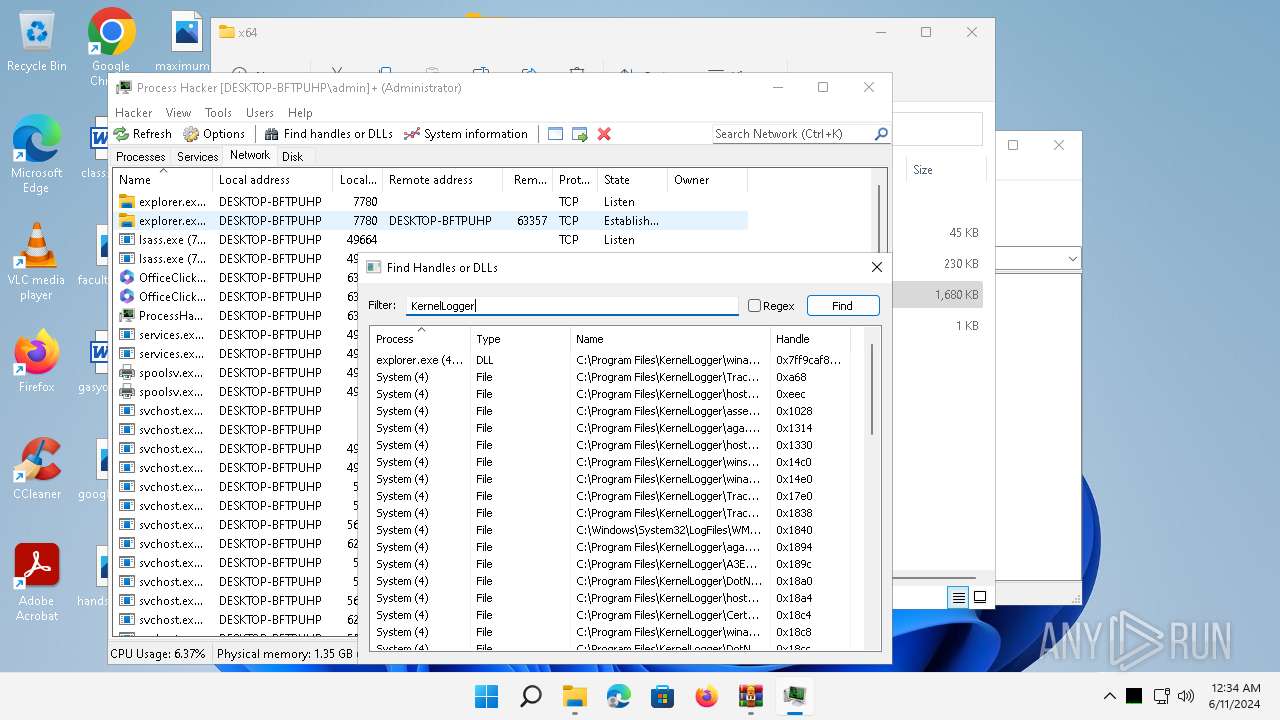
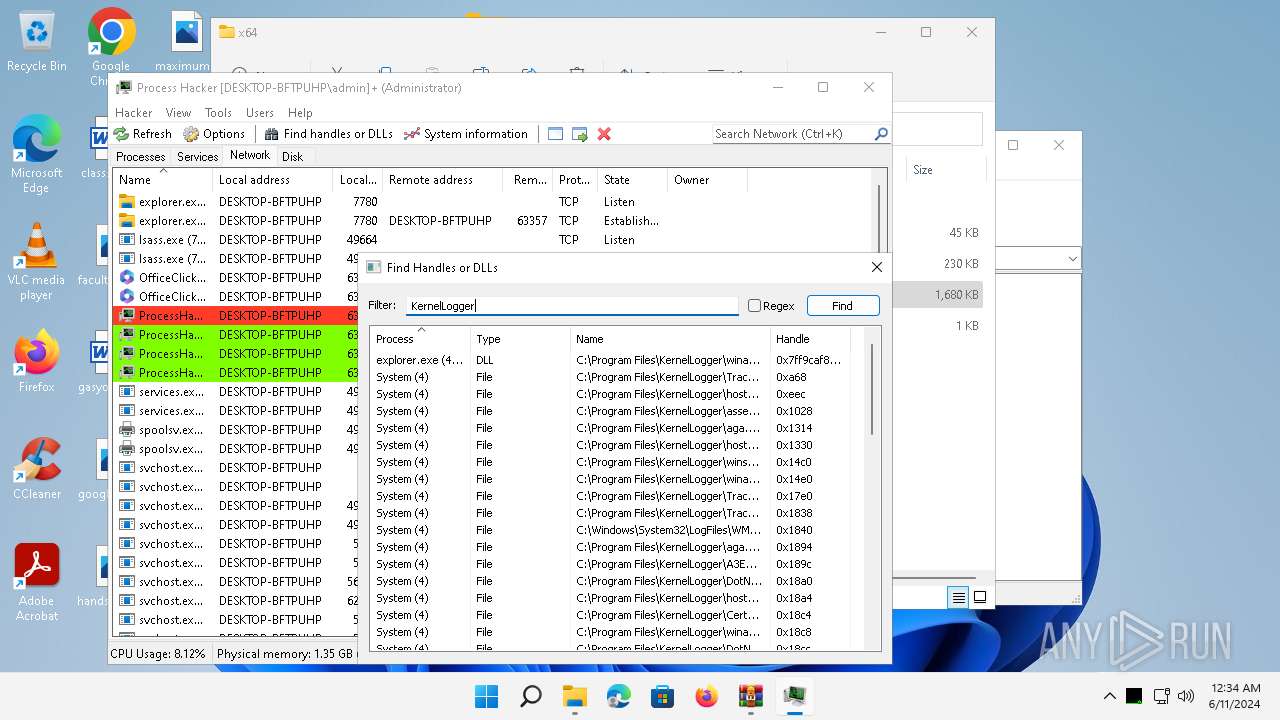
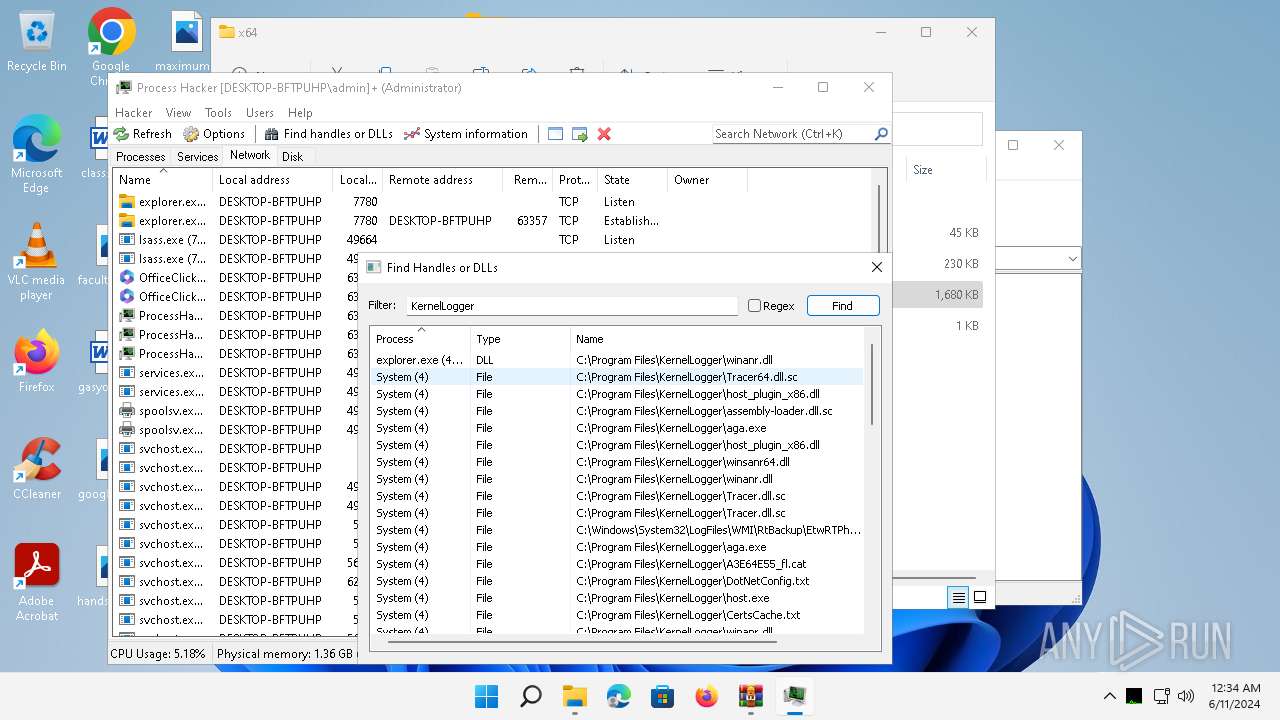
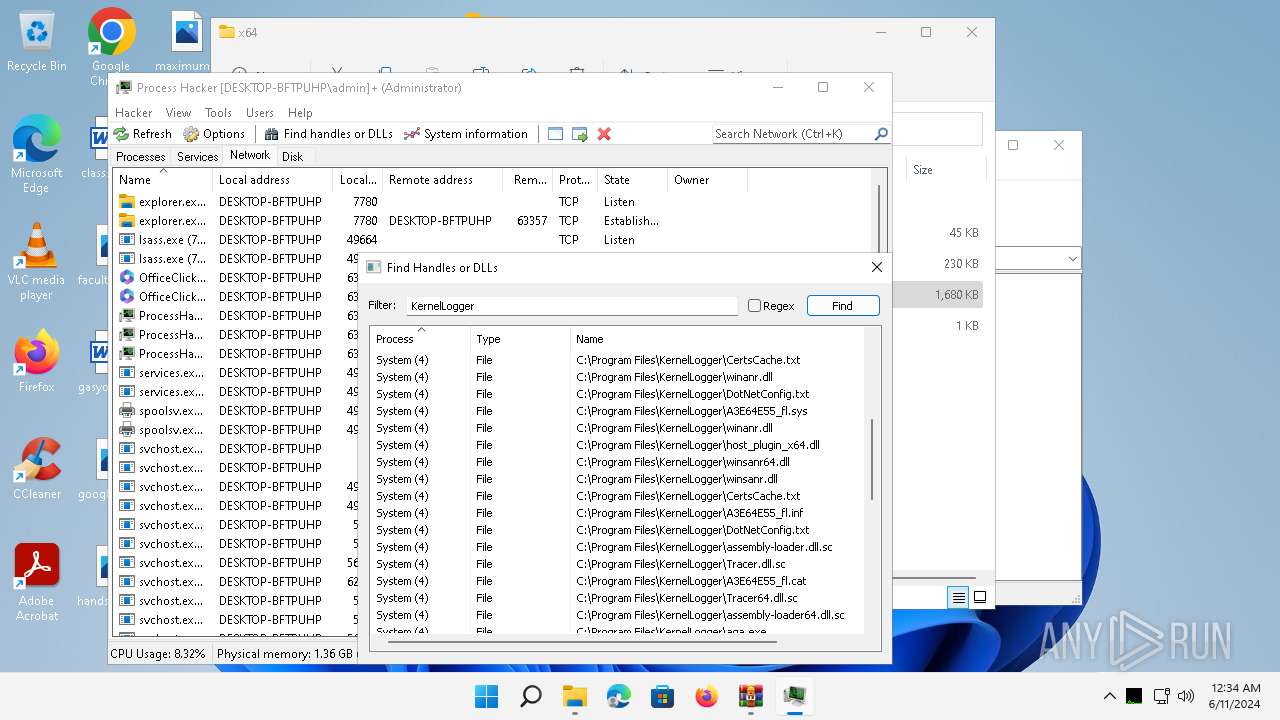
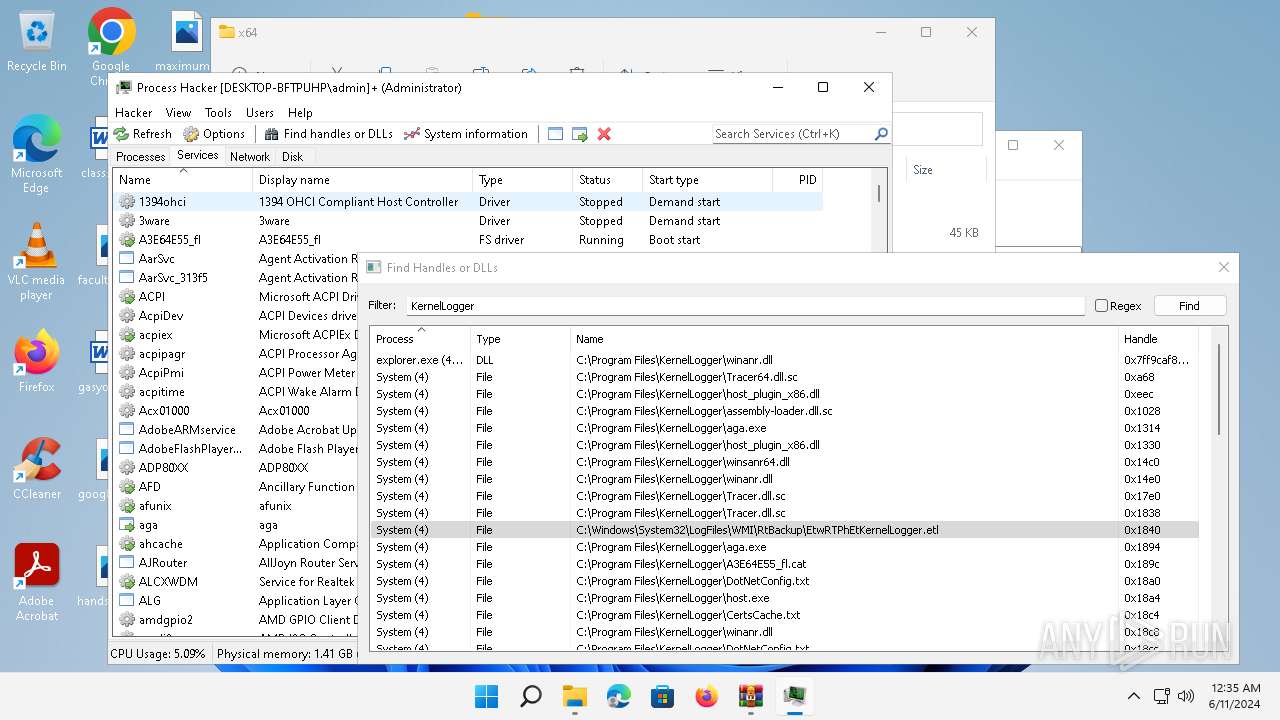
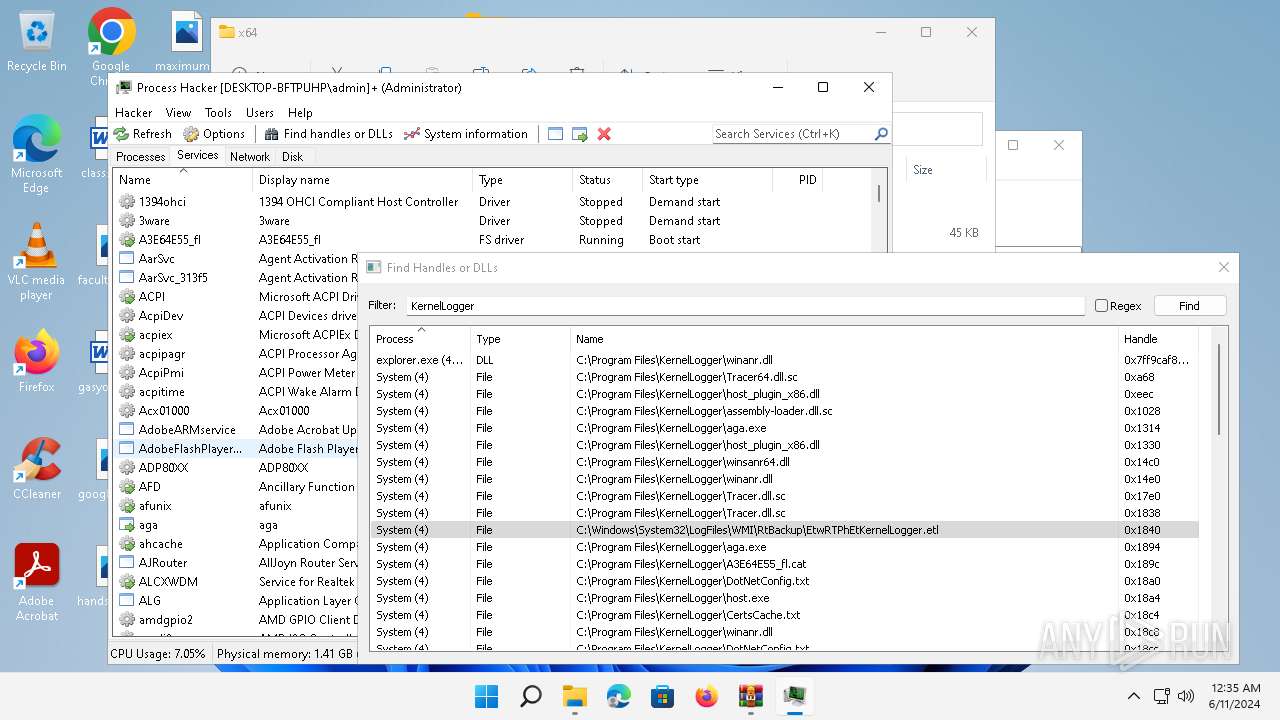
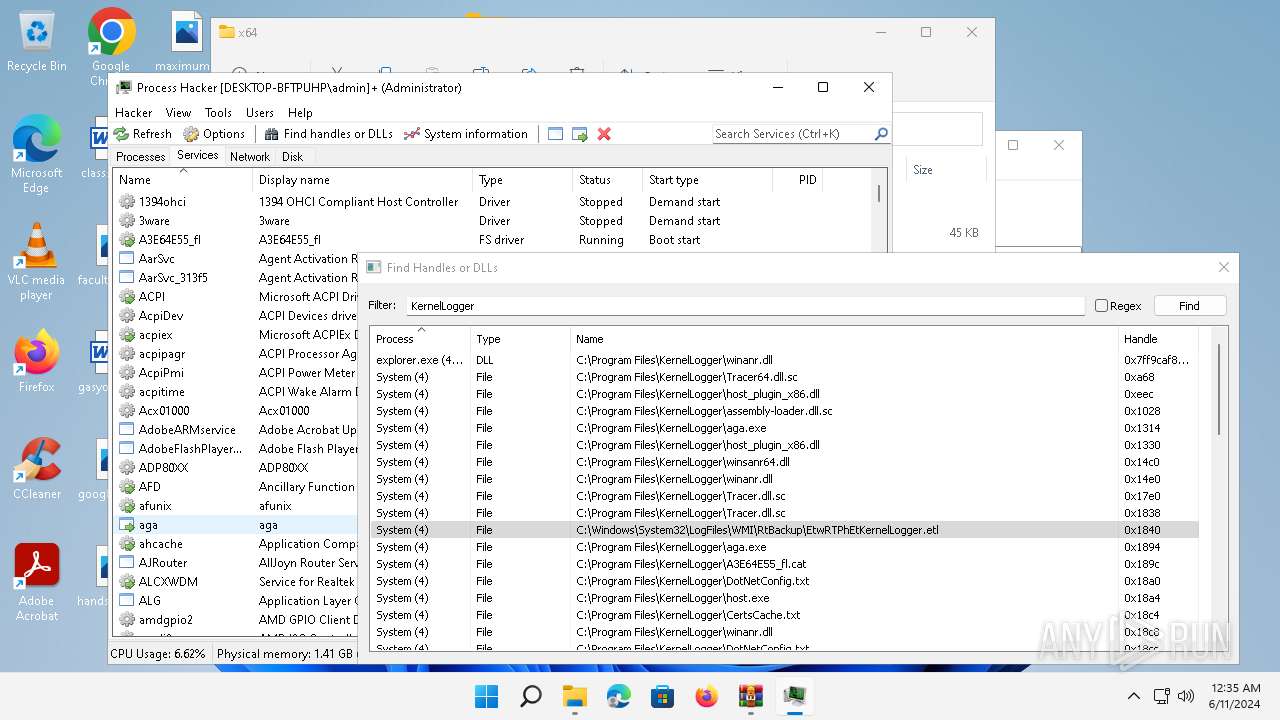
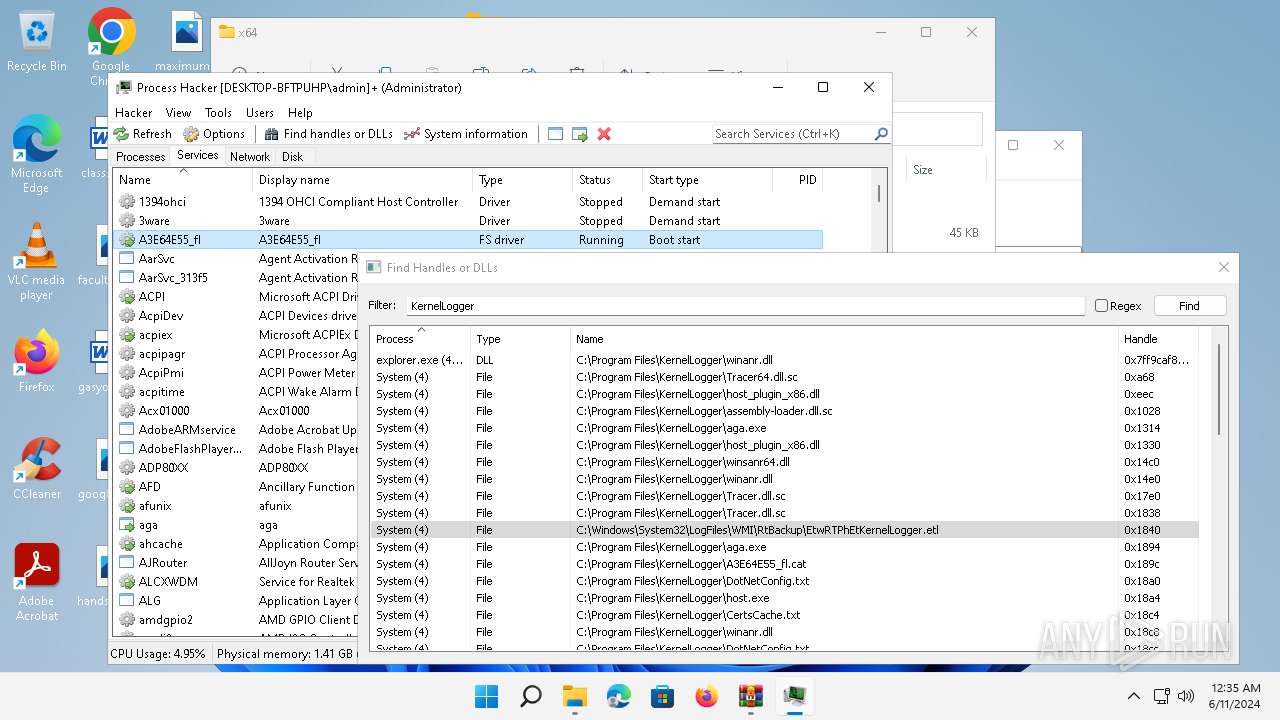
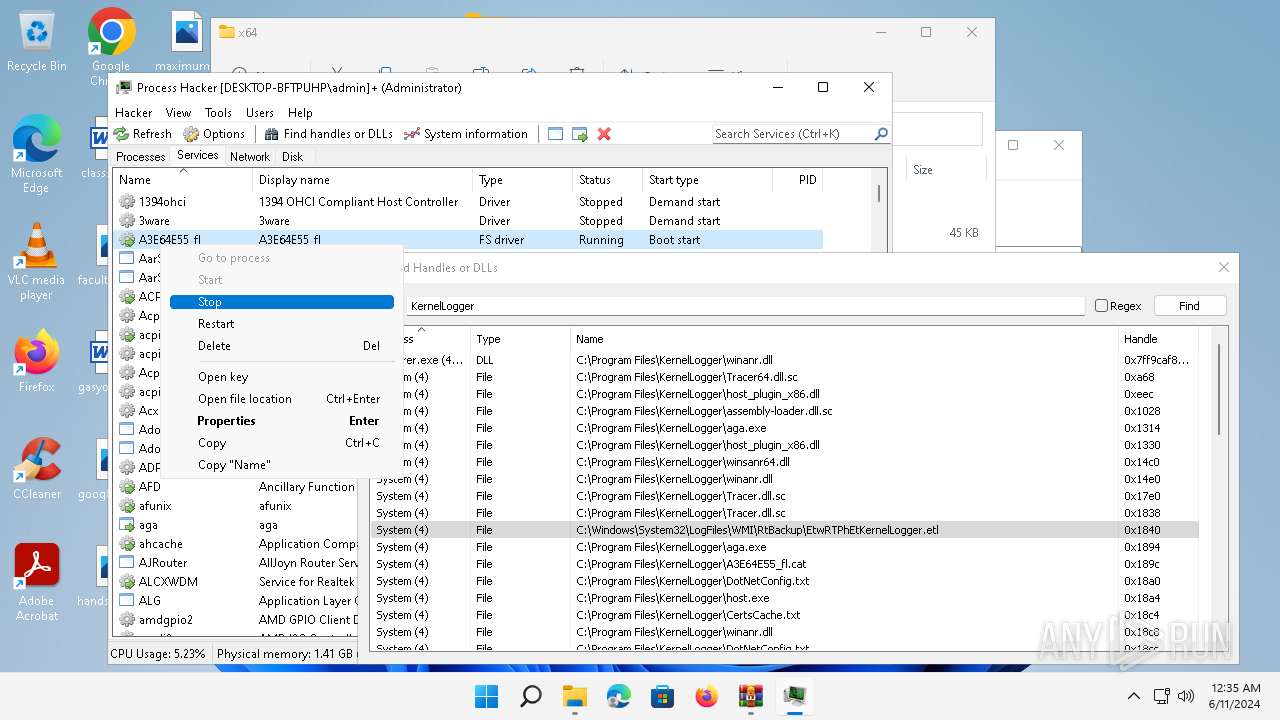
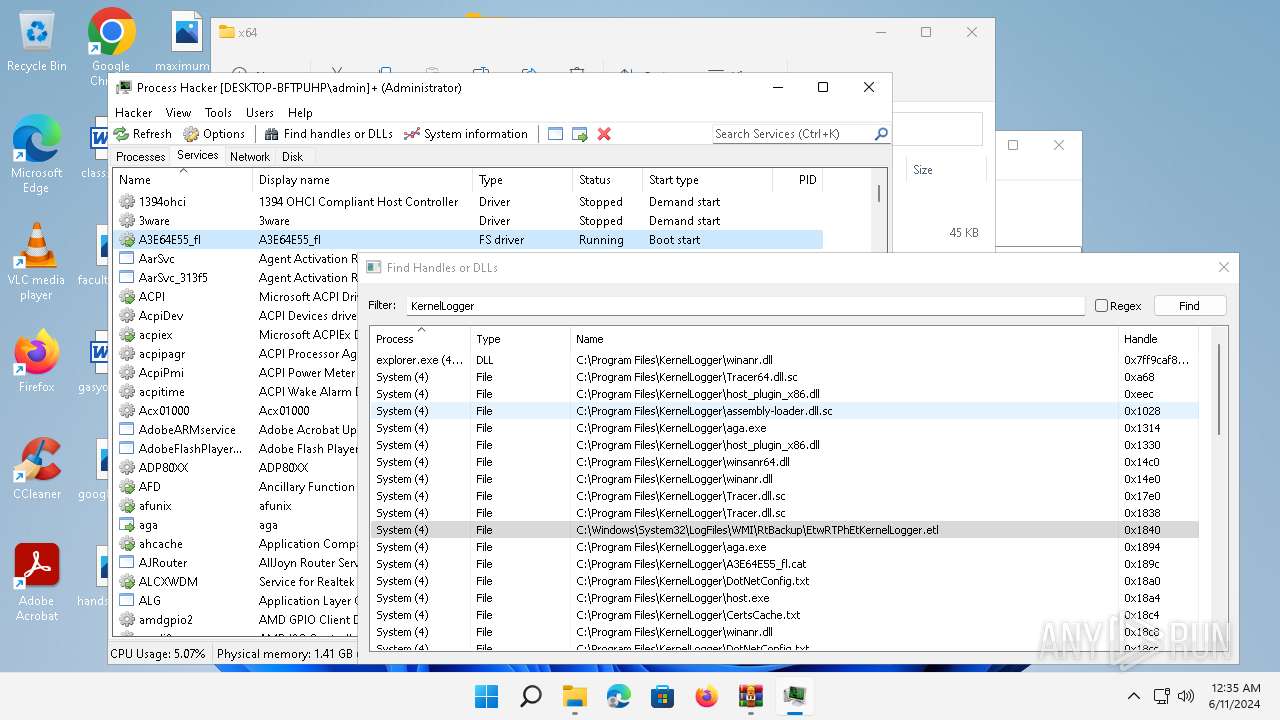
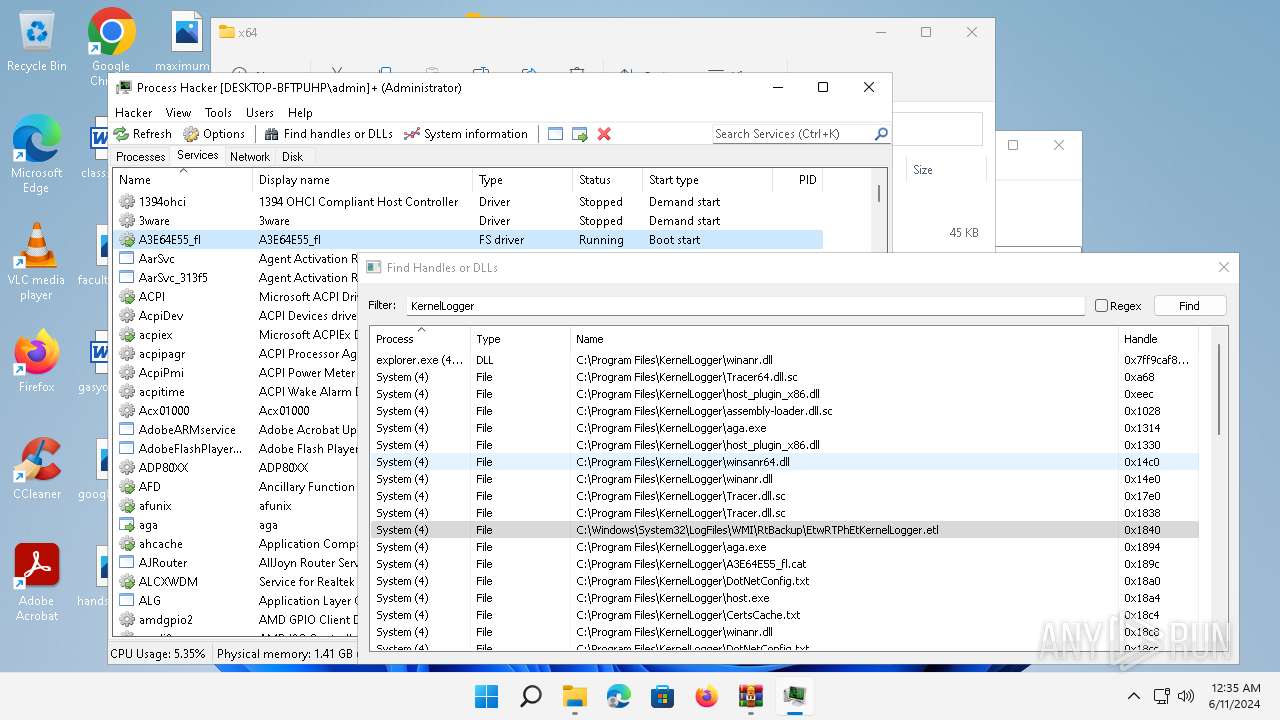
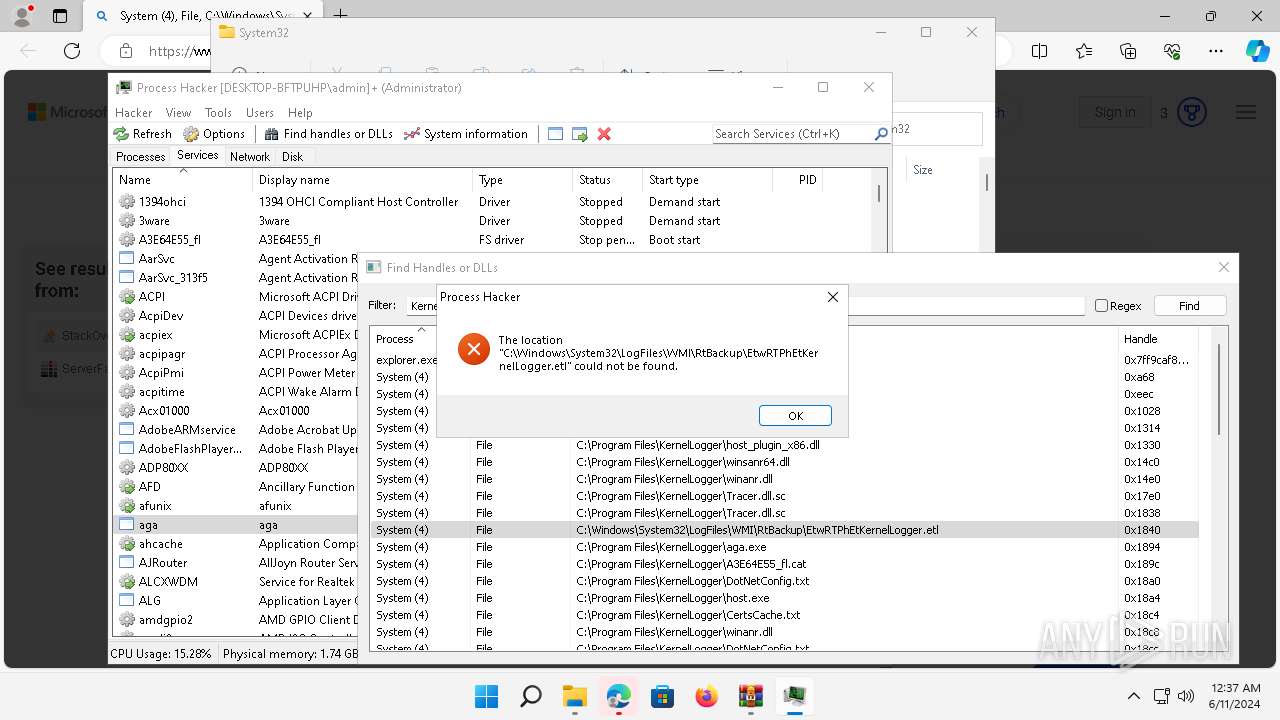
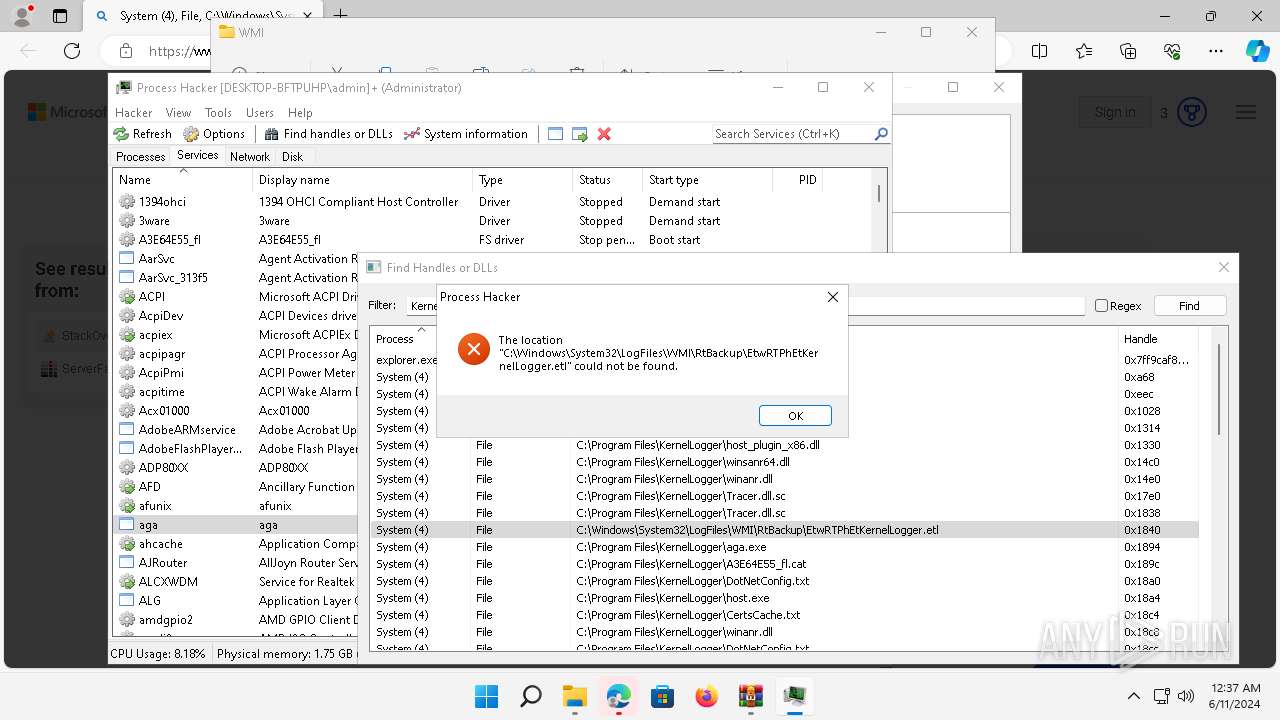
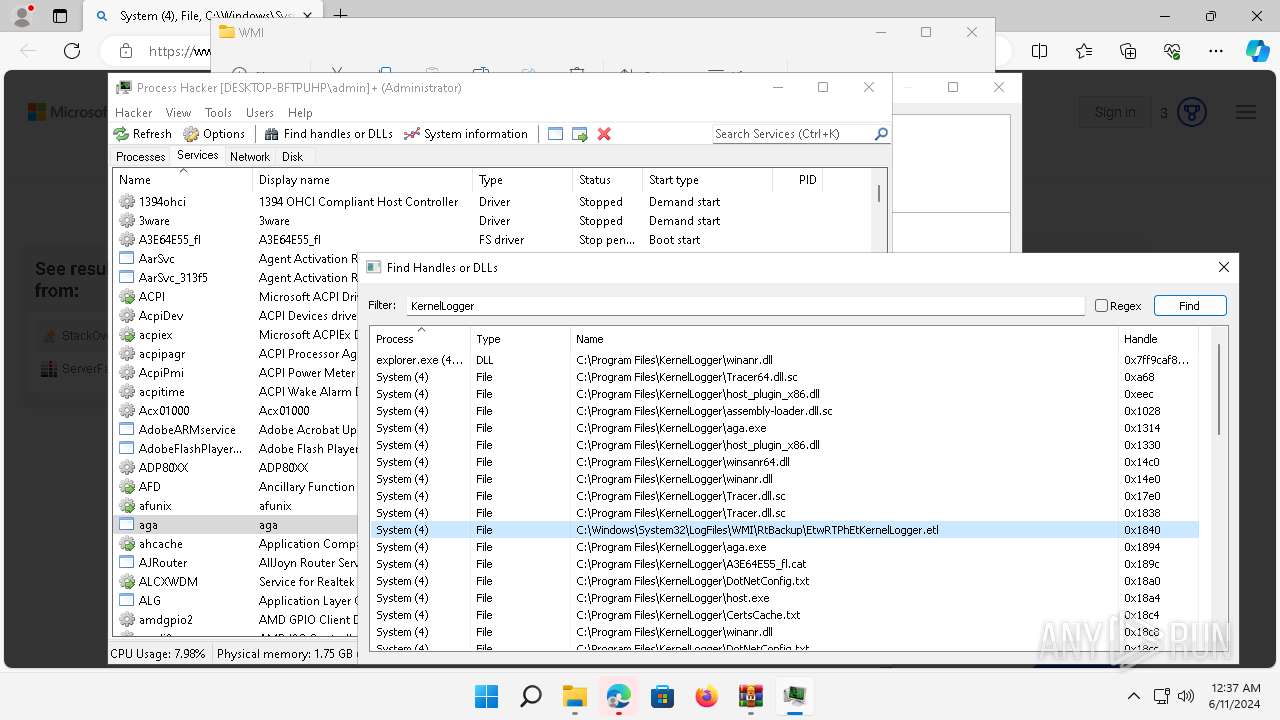
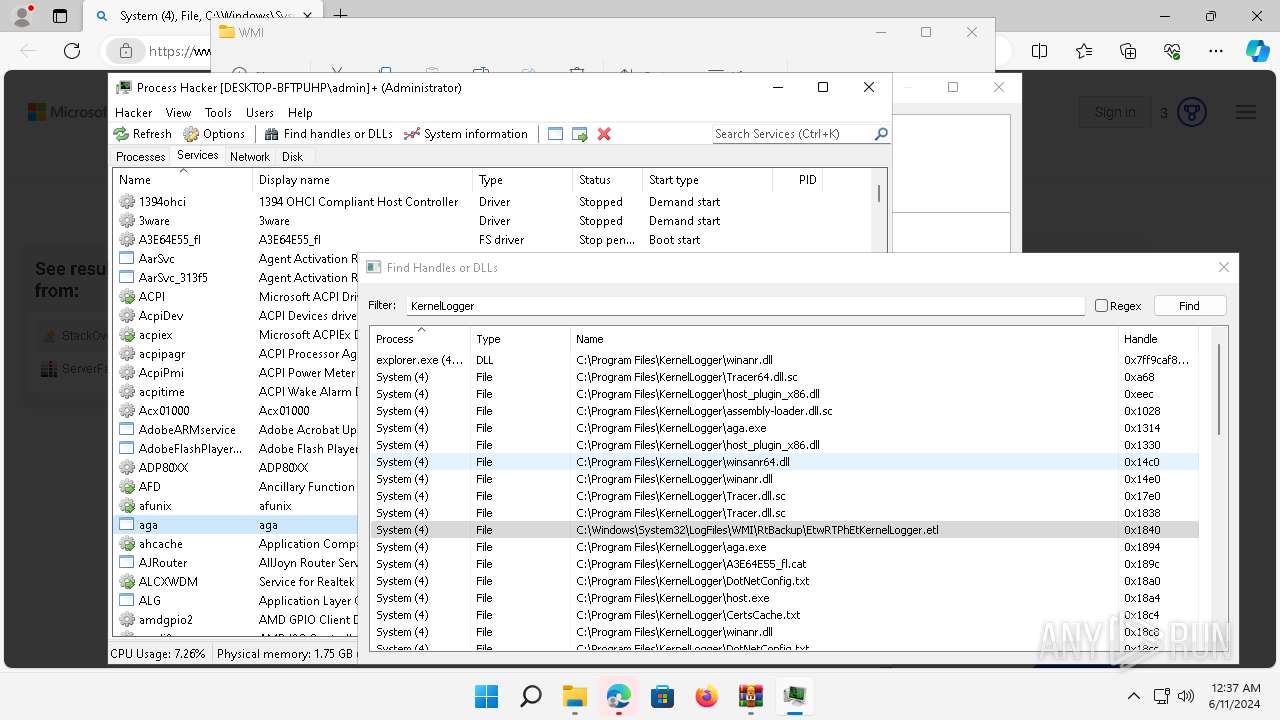
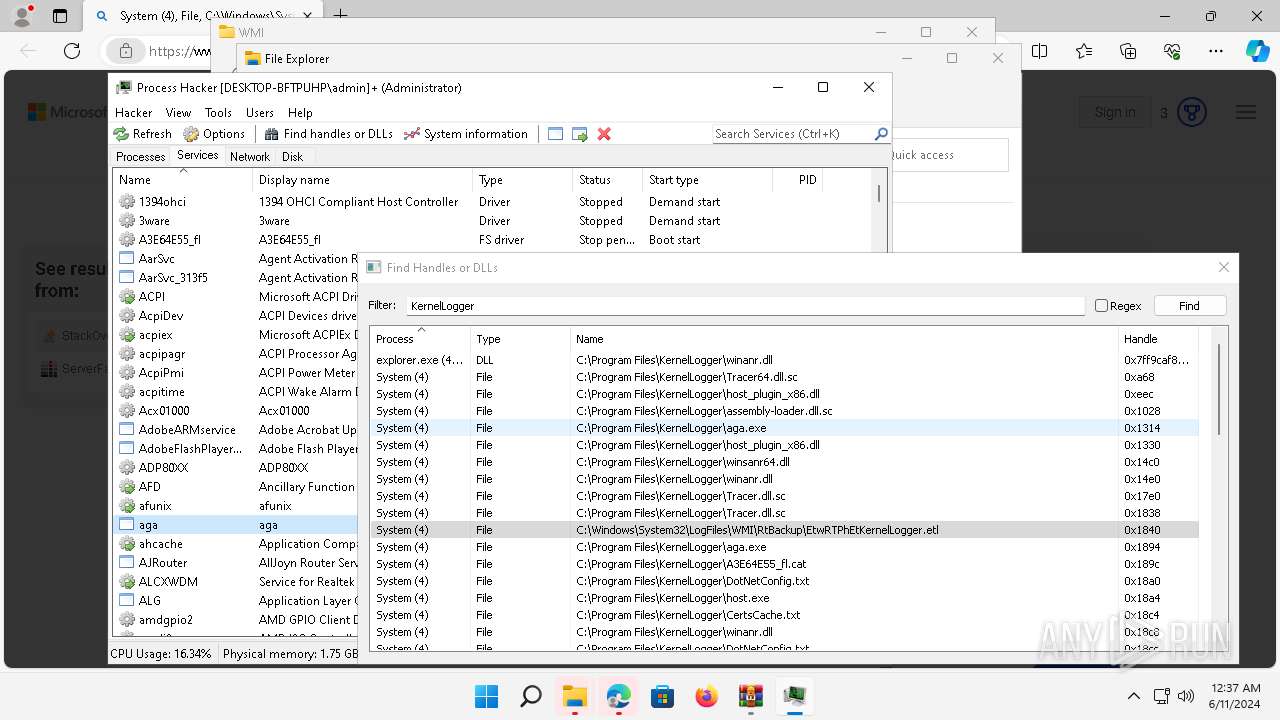
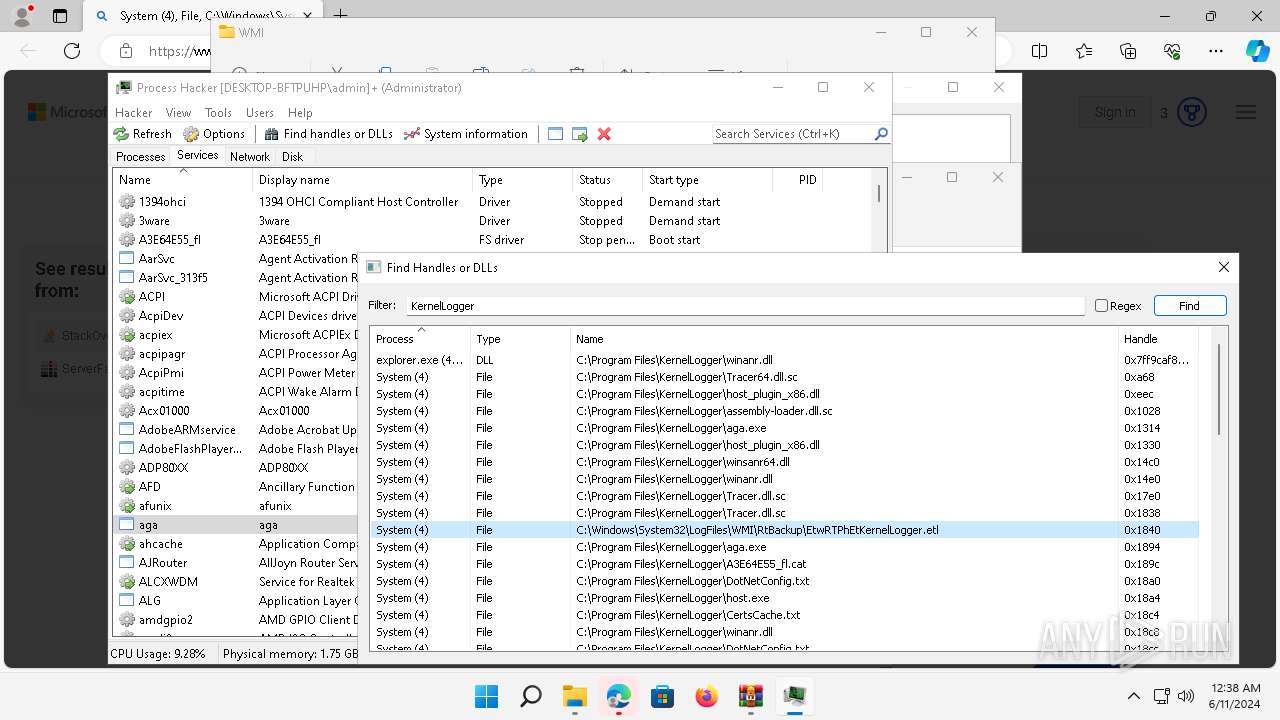
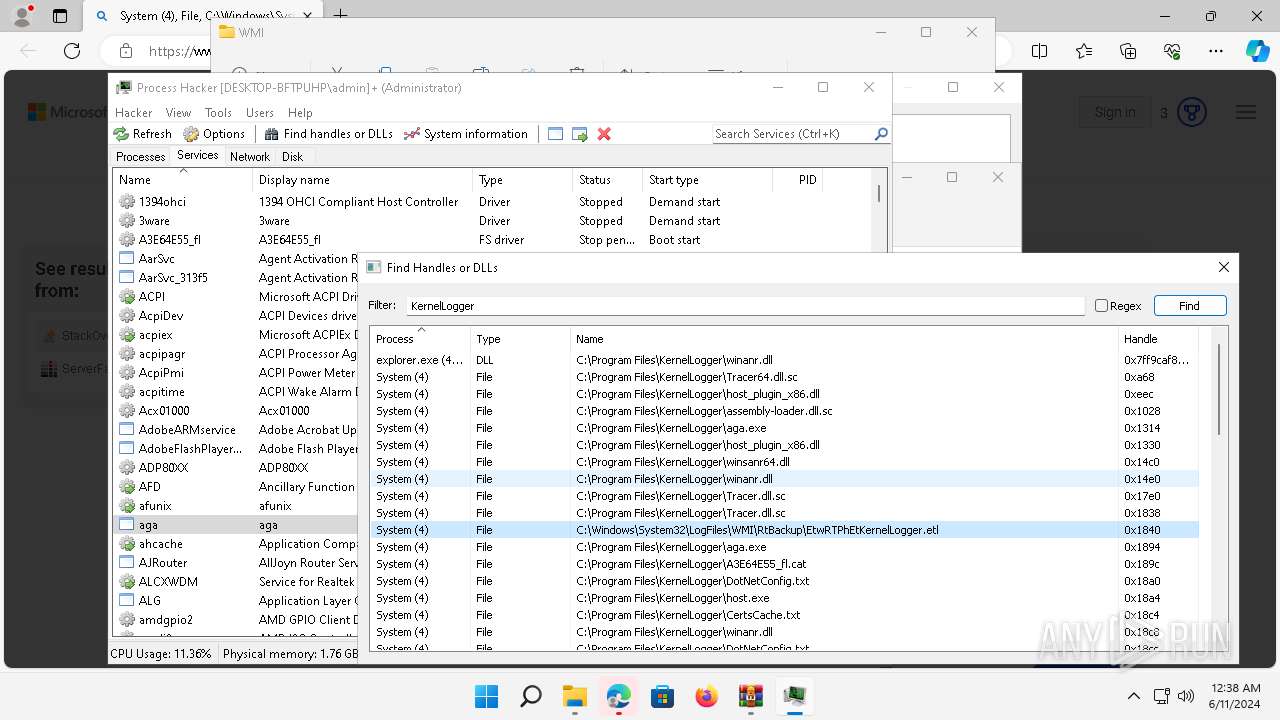
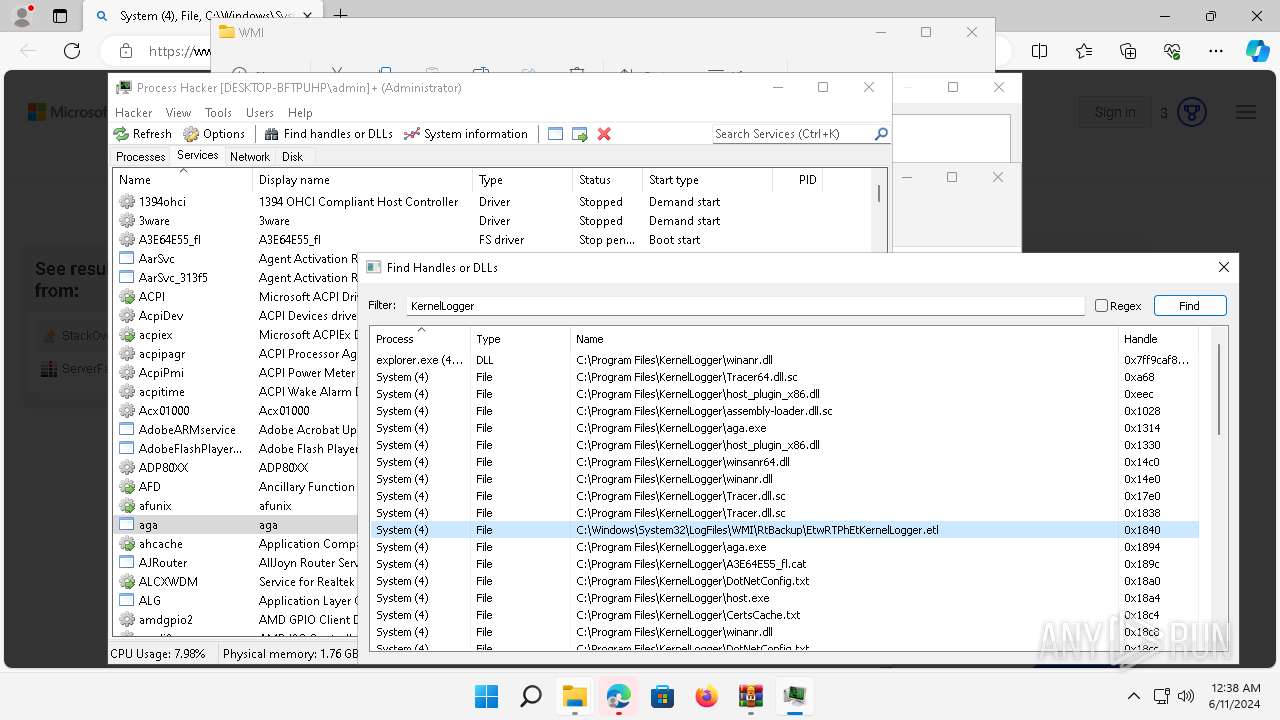
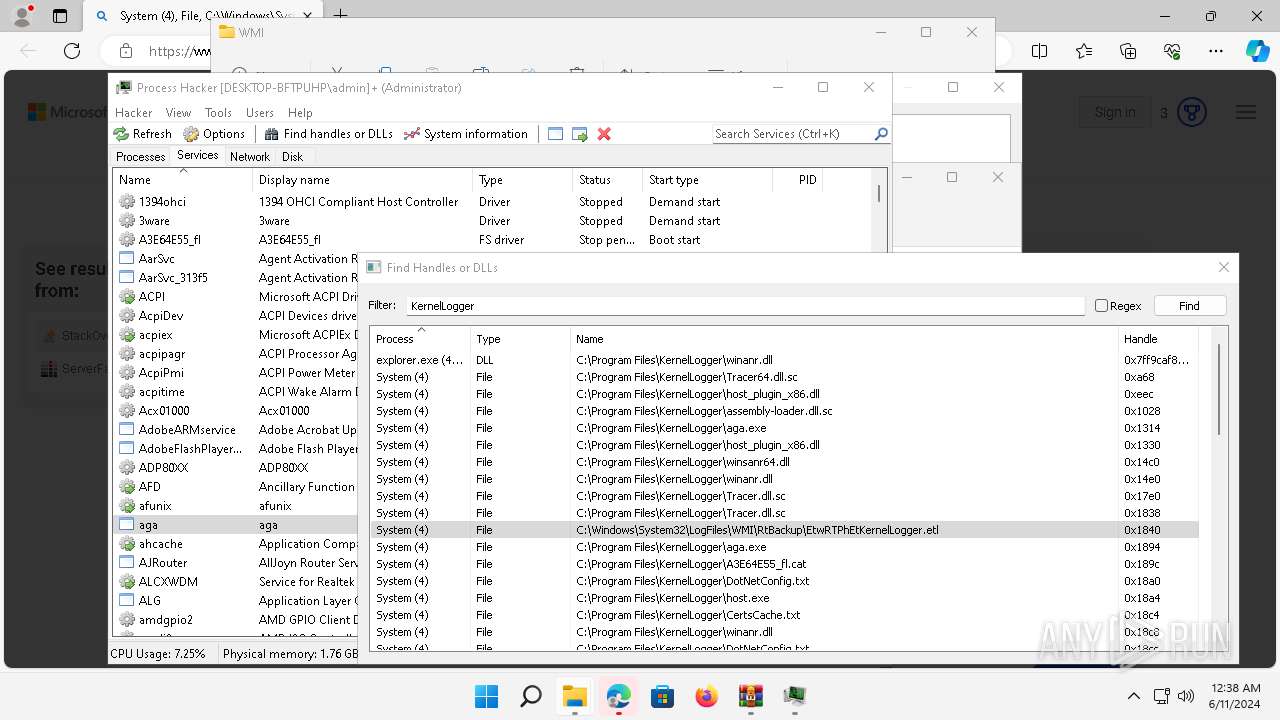
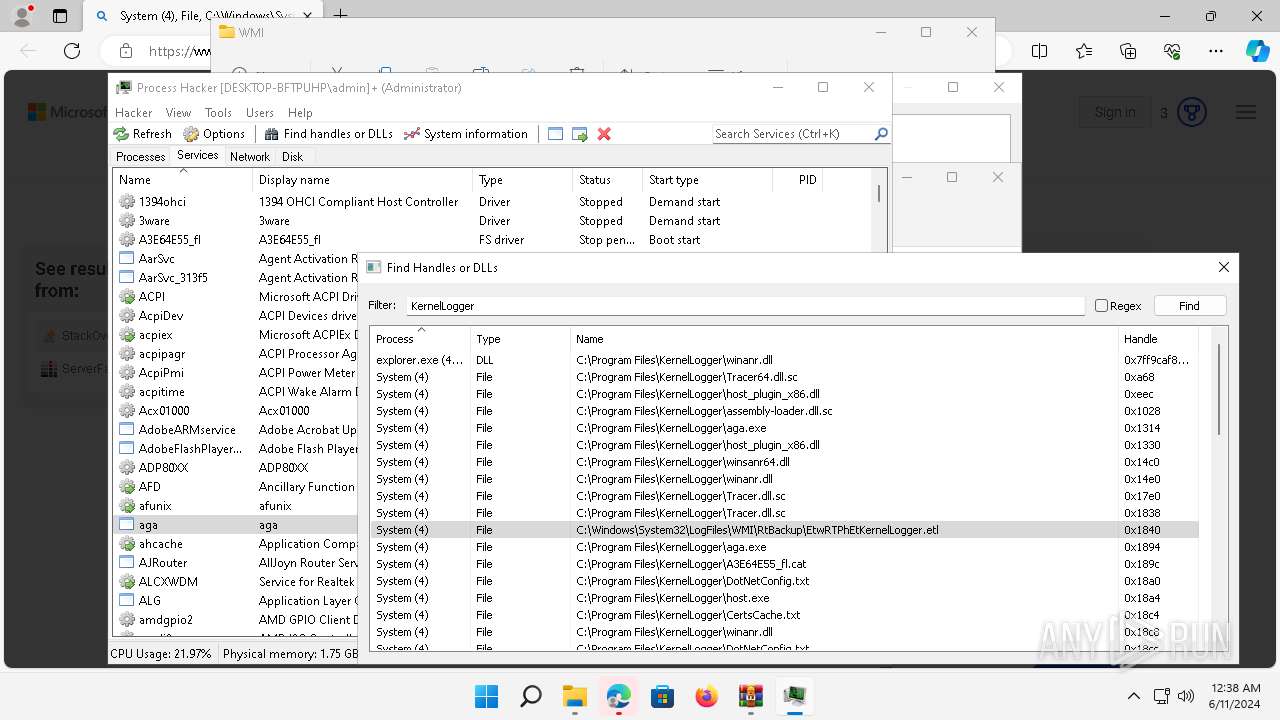
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 2808)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 2808)
Reads the Internet Settings
- ProcessHacker.exe (PID: 1536)
Reads settings of System Certificates
- ProcessHacker.exe (PID: 1536)
INFO
Checks supported languages
- ProcessHacker.exe (PID: 1536)
Reads the computer name
- ProcessHacker.exe (PID: 1536)
Reads the time zone
- ProcessHacker.exe (PID: 1536)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2808)
Reads CPU info
- ProcessHacker.exe (PID: 1536)
Manual execution by a user
- ProcessHacker.exe (PID: 1536)
Reads the machine GUID from the registry
- ProcessHacker.exe (PID: 1536)
Reads Environment values
- ProcessHacker.exe (PID: 1536)
Checks proxy server information
- ProcessHacker.exe (PID: 1536)
Reads the software policy settings
- ProcessHacker.exe (PID: 1536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:03:29 12:18:08 |
| ZipCRC: | 0x34beb5ab |
| ZipCompressedSize: | 7294 |
| ZipUncompressedSize: | 25995 |
| ZipFileName: | CHANGELOG.txt |
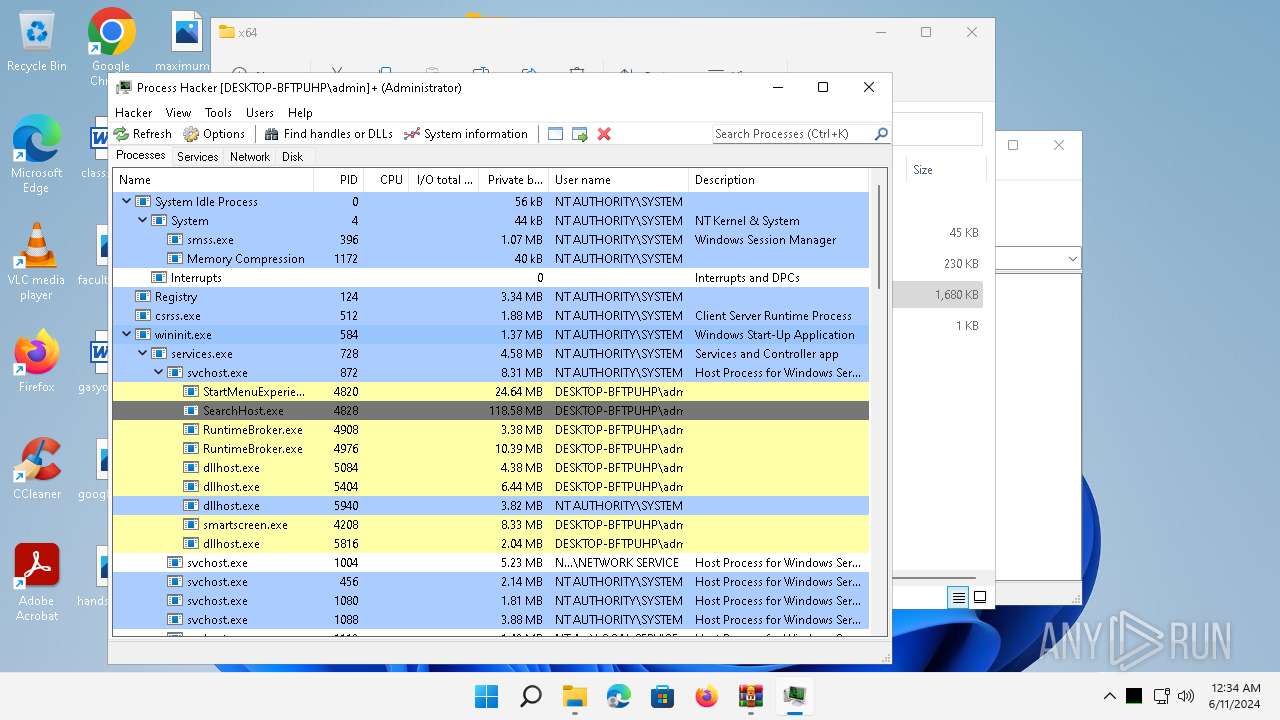
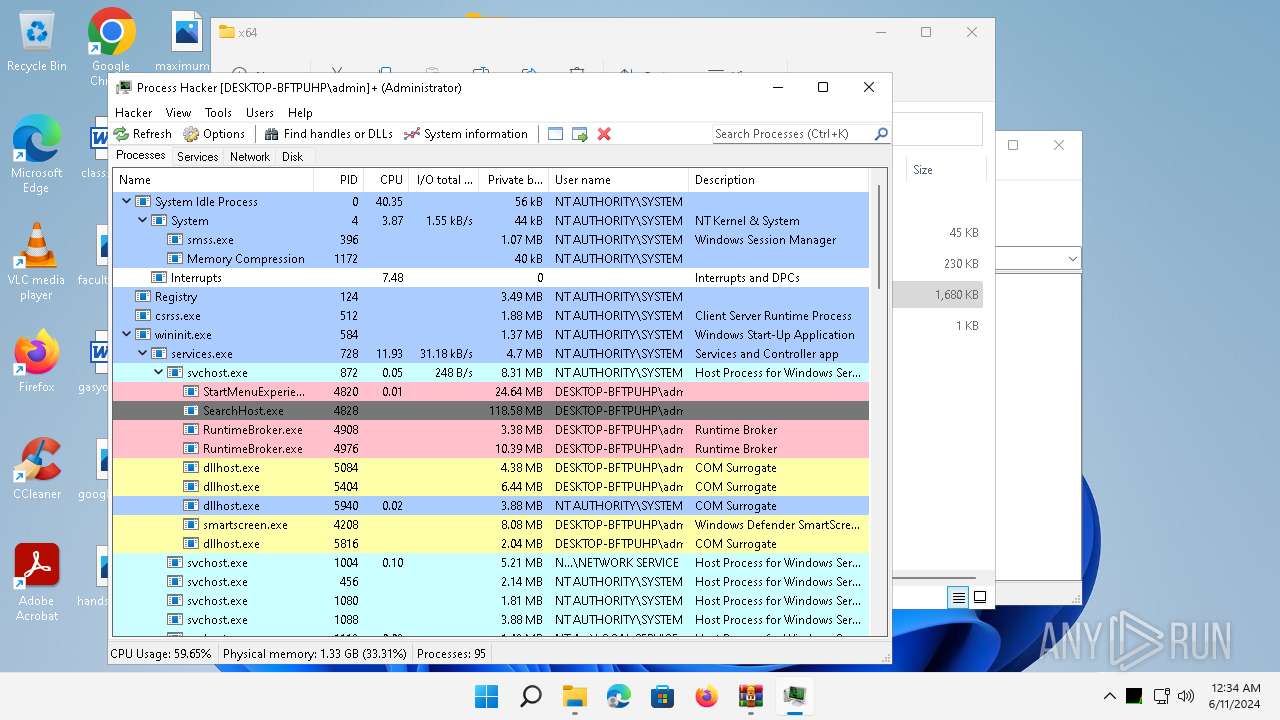
Total processes
97
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1536 | "C:\Users\admin\Desktop\x64\ProcessHacker.exe" | C:\Users\admin\Desktop\x64\ProcessHacker.exe | explorer.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: HIGH Description: Process Hacker Version: 2.39.0.124 Modules
| |||||||||||||||
| 2808 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\processhacker-2.39-bin.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5816 | "C:\Windows\system32\DllHost.exe" /Processid:{B41DB860-64E4-11D2-9906-E49FADC173CA} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 415
Read events
10 406
Write events
9
Delete events
0
Modification events
| (PID) Process: | (2808) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 005B0500590AC81797BBDA01 | |||
| (PID) Process: | (2808) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2808) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2808) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\processhacker-2.39-bin.zip | |||
| (PID) Process: | (2808) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2808) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2808) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2808) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
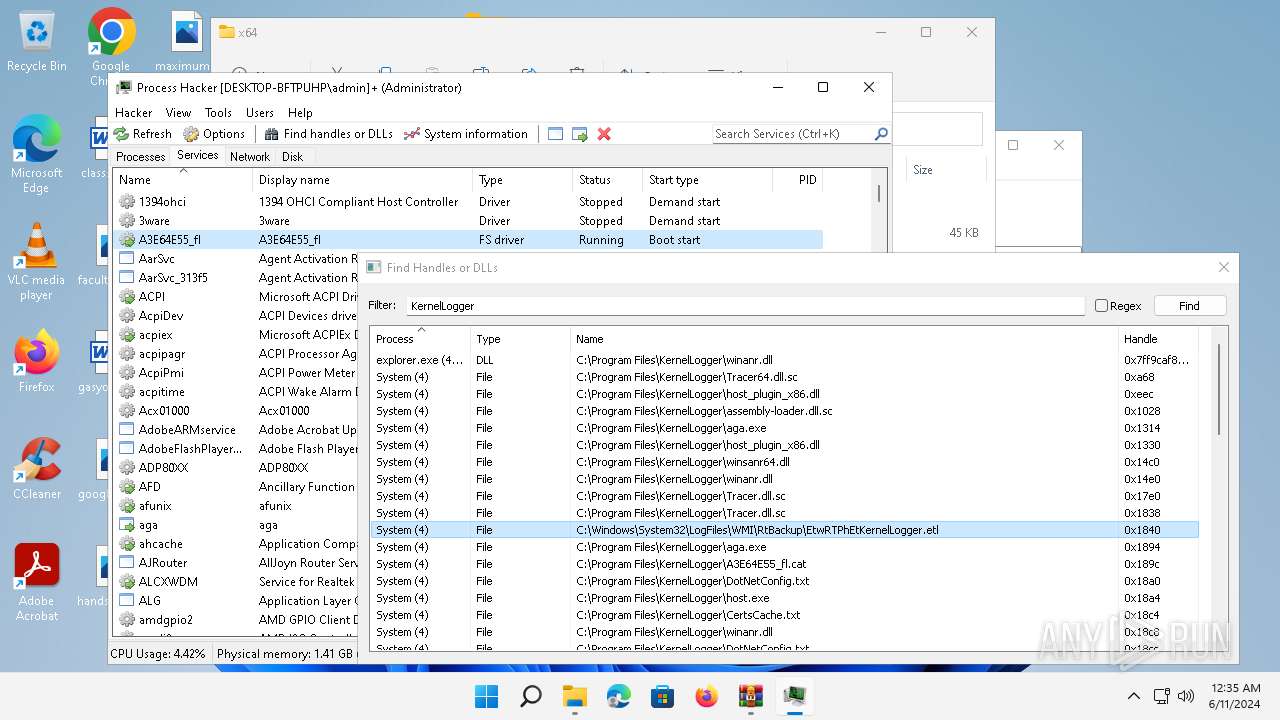
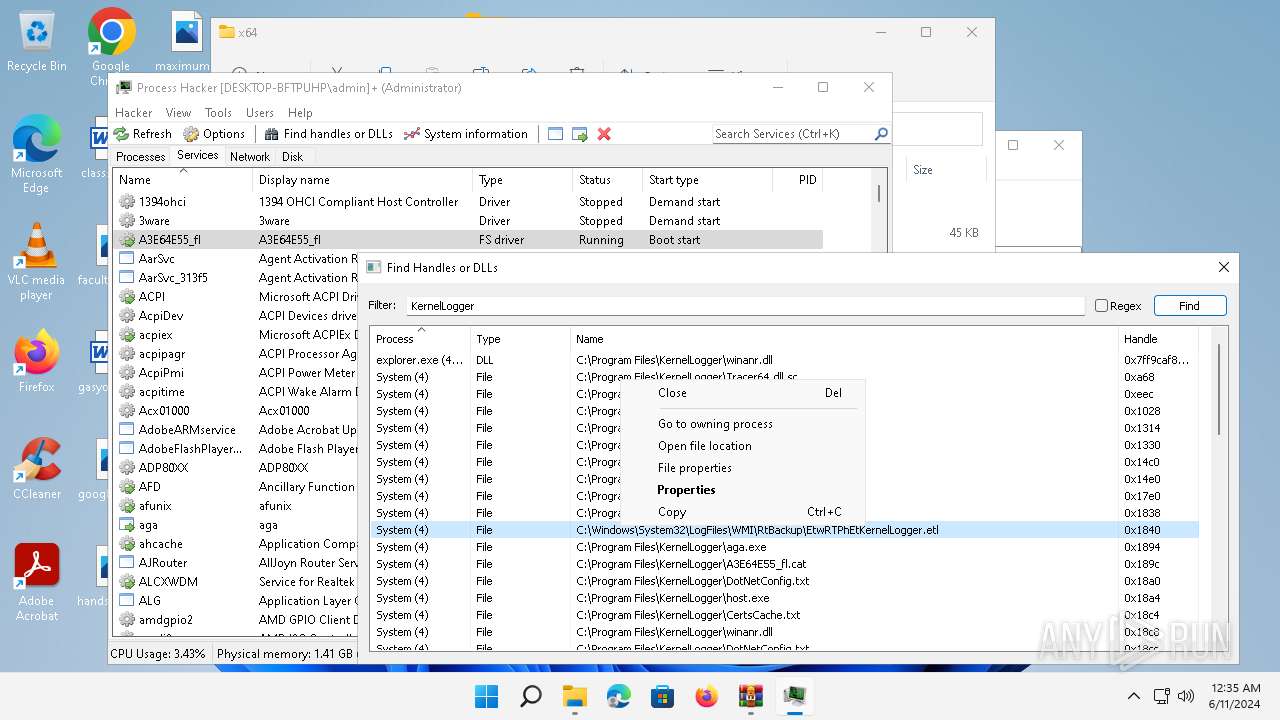
| (PID) Process: | (1536) ProcessHacker.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\KProcessHacker3\Parameters |
| Operation: | write | Name: | SecurityLevel |
Value: 1 | |||
Executable files
15
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2808.37254\x64\kprocesshacker.sys | executable | |
MD5:1B5C3C458E31BEDE55145D0644E88D75 | SHA256:70211A3F90376BBC61F49C22A63075D1D4DDD53F0AEFA976216C46E6BA39A9F4 | |||
| 2808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2808.37254\x64\plugins\SbieSupport.dll | executable | |
MD5:37CBFA73883E7E361D3FA67C16D0F003 | SHA256:57C56F7B312DC1F759E6AD039AAC3F36CE5130D259EB9FAAD77239083398308B | |||
| 2808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2808.37254\x64\peview.exe | executable | |
MD5:DDE1F44789CD50C1F034042D337DEAE3 | SHA256:4259E53D48A3FED947F561FF04C7F94446BEDD64C87F52400B2CB47A77666AAA | |||
| 2808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2808.37254\x64\plugins\NetworkTools.dll | executable | |
MD5:D6BED1D6FDBED480E32FDD2DD4C13352 | SHA256:476AA6AF14DD0B268786E32543B9A6917A298D4D90E1015DAC6FB2B522CF5D2E | |||
| 2808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2808.37254\x64\plugins\ToolStatus.dll | executable | |
MD5:3788EFFF135F8B17A179D02334D505E6 | SHA256:5713D40DEC146DBC819230DAEFE1B886FA6D6F6DBD619301BB8899562195CBAB | |||
| 2808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2808.37254\x64\plugins\OnlineChecks.dll | executable | |
MD5:12C25FB356E51C3FD81D2D422A66BE89 | SHA256:7336D66588BBCFEA63351A2EB7C8D83BBD49B5D959BA56A94B1FE2E905A5B5DE | |||
| 2808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2808.37254\x64\plugins\ExtendedTools.dll | executable | |
MD5:BC61E6FB02FBBFE16FB43CC9F4E949F1 | SHA256:F2805E0F81513641A440F1A21057A664961C22192CB33FCA3870362C8F872D87 | |||
| 2808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2808.37254\x64\plugins\ExtendedServices.dll | executable | |
MD5:4858BDB7731BF0B46B247A1F01F4A282 | SHA256:5AE7C0972FD4E4C4AE14C0103602CA854377FEFCBCCD86FA68CFC5A6D1F99F60 | |||
| 2808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2808.37254\x64\plugins\UserNotes.dll | executable | |
MD5:E48C789C425F966F5E5EE3187934174F | SHA256:FC9D0D0482C63AB7F238BC157C3C0FED97951CCF2D2E45BE45C06C426C72CB52 | |||
| 2808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2808.37254\x64\plugins\DotNetTools.dll | executable | |
MD5:B16CE8BA8E7F0EE83EC1D49F2D0AF0A7 | SHA256:B4CC0280E2CAA0335361172CB7D673F745DEFC78299DED808426FFBC2458E4D9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
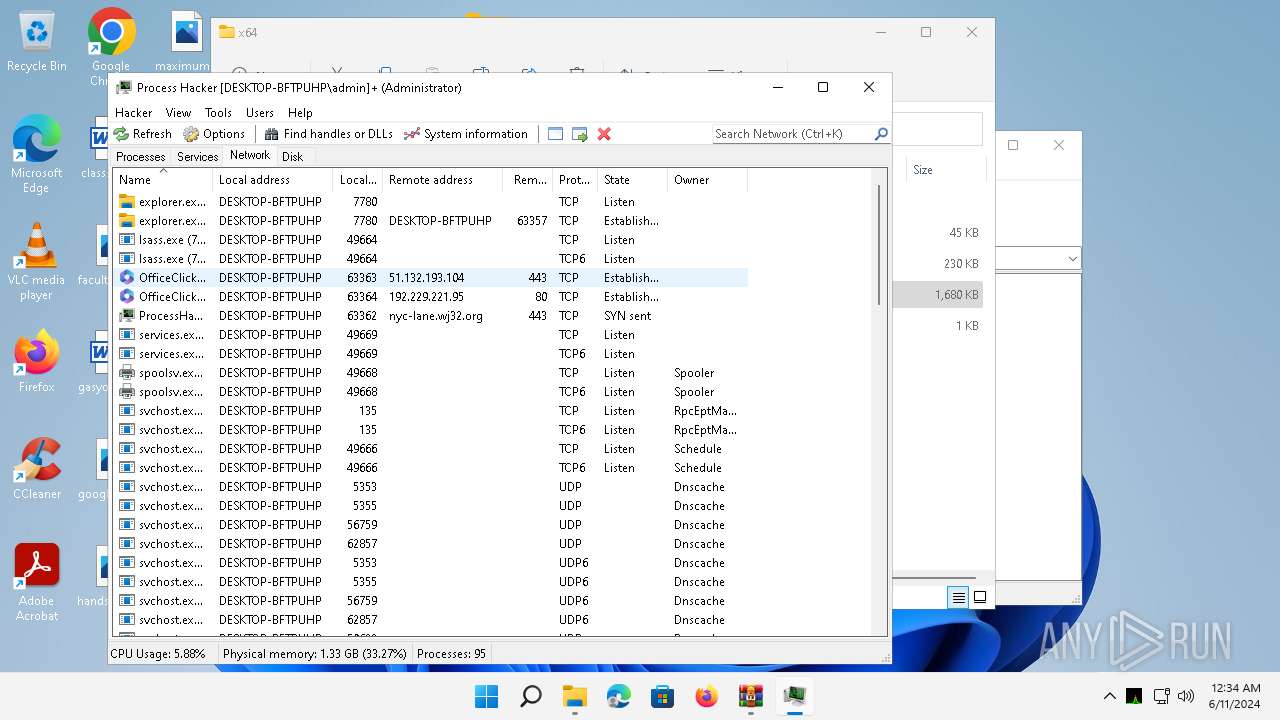
HTTP(S) requests
40
TCP/UDP connections
79
DNS requests
82
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 403 | 2.19.105.250:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | 403 | 2.19.105.250:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | 403 | 2.19.105.250:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | 403 | 2.19.105.250:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | 403 | 2.19.105.250:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | 403 | 2.19.105.250:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | 403 | 2.19.105.250:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
2868 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | unknown |
1536 | ProcessHacker.exe | GET | 301 | 104.18.37.111:80 | http://processhacker.sourceforge.net/update.php | unknown | — | — | unknown |
2828 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?02514b431d1af569 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.19.105.250:80 | go.microsoft.com | AKAMAI-AS | DE | unknown |
4552 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5264 | svchost.exe | 184.28.90.27:443 | fs.microsoft.com | AKAMAI-AS | US | unknown |
1536 | ProcessHacker.exe | 162.243.25.33:443 | wj32.org | DIGITALOCEAN-ASN | US | unknown |
2868 | OfficeClickToRun.exe | 51.132.193.104:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
2868 | OfficeClickToRun.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
1536 | ProcessHacker.exe | 104.18.37.111:80 | processhacker.sourceforge.net | CLOUDFLARENET | — | unknown |
1536 | ProcessHacker.exe | 104.18.37.111:443 | processhacker.sourceforge.net | CLOUDFLARENET | — | unknown |
1536 | ProcessHacker.exe | 172.64.150.83:443 | processhacker.sourceforge.io | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
wj32.org |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
172.210.232.199.in-addr.arpa |
| unknown |
95.221.229.192.in-addr.arpa |
| unknown |
10.73.50.20.in-addr.arpa |
| unknown |
158.240.127.40.in-addr.arpa |
| unknown |
250.105.19.2.in-addr.arpa |
| unknown |
27.90.28.184.in-addr.arpa |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |