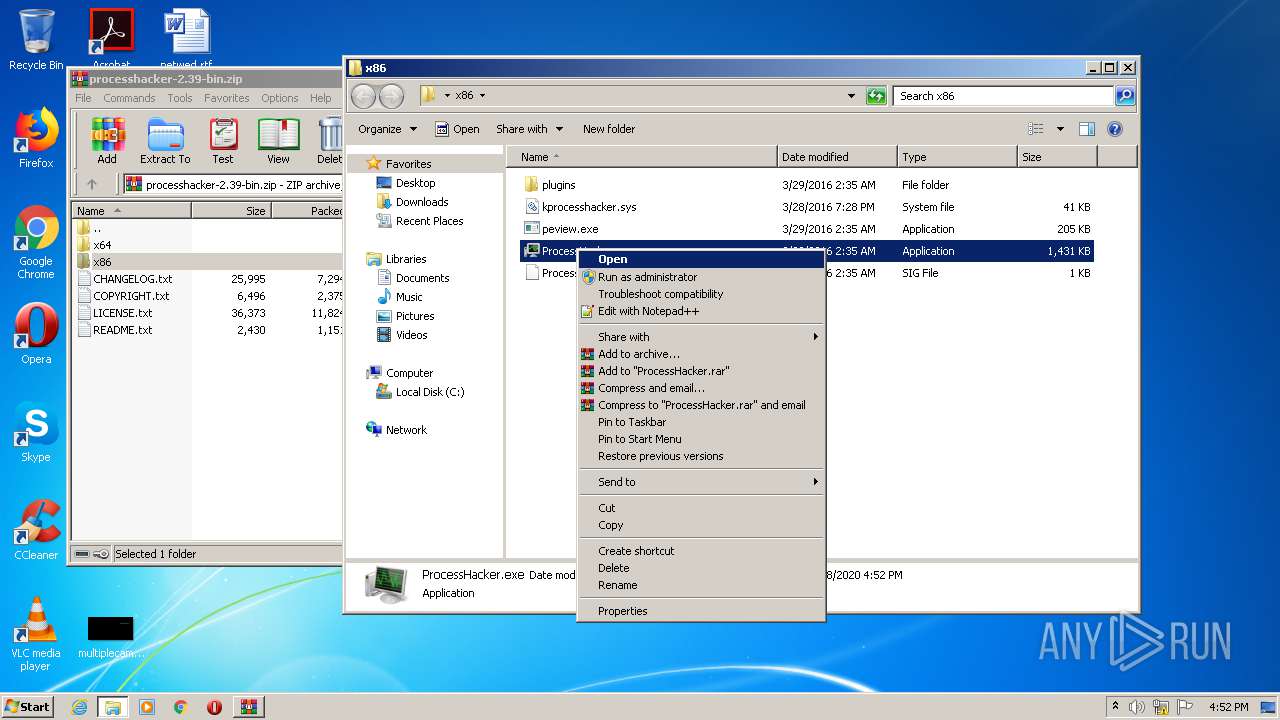
| download: | processhacker-2.39-bin.zip |
| Full analysis: | https://app.any.run/tasks/4790d116-3be4-4549-9ad1-c0ab86460776 |
| Verdict: | Malicious activity |
| Analysis date: | December 08, 2020, 16:51:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B444CF14642CE9B8D75E079166A5DF0B |
| SHA1: | 8E8F8423D163D922242B8B7D85427664F77EDC97 |
| SHA256: | 2AFB5303E191DDE688C5626C3EE545E32E52F09DA3B35B20F5E0D29A418432F5 |
| SSDEEP: | 98304:jDqt5TrOmlLB/7rTOqcXfOzJR1qioDLK2EbhQ:3sTrHlB73OqX4ioDfshQ |
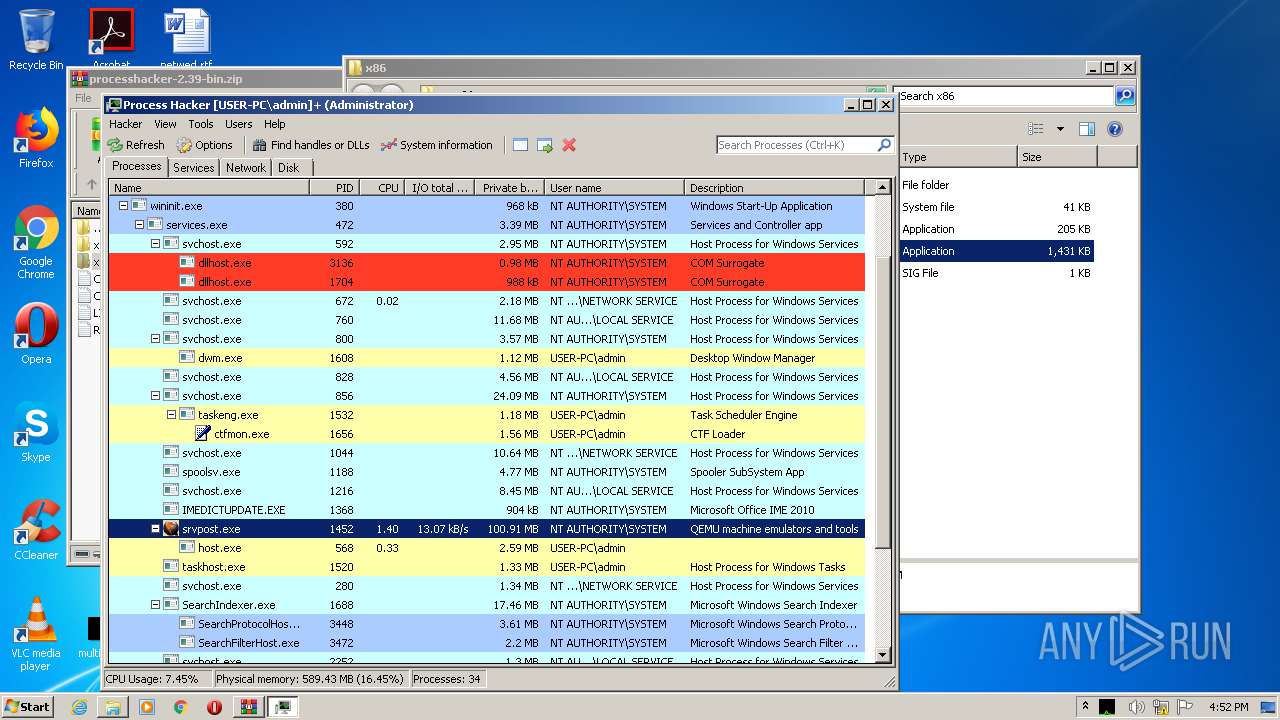
MALICIOUS
Loads dropped or rewritten executable
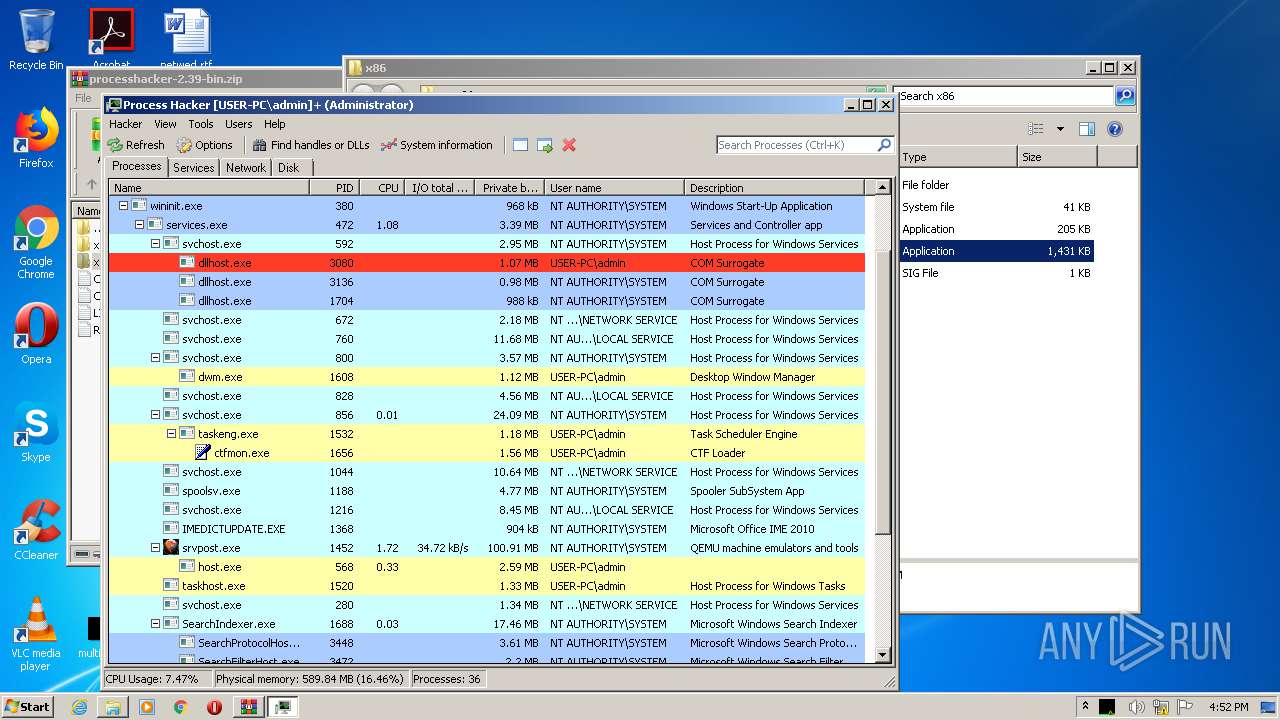
- SearchProtocolHost.exe (PID: 3448)
Application was dropped or rewritten from another process
- ProcessHacker.exe (PID: 2748)
Loads the Task Scheduler COM API
- ProcessHacker.exe (PID: 2748)
Changes settings of System certificates
- ProcessHacker.exe (PID: 2748)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2928)
Adds / modifies Windows certificates
- ProcessHacker.exe (PID: 2748)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2928)
INFO
Manual execution by user
- ProcessHacker.exe (PID: 2748)
Reads settings of System Certificates
- ProcessHacker.exe (PID: 2748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:03:29 12:18:04 |
| ZipCRC: | 0x34beb5ab |
| ZipCompressedSize: | 7294 |
| ZipUncompressedSize: | 25995 |
| ZipFileName: | CHANGELOG.txt |
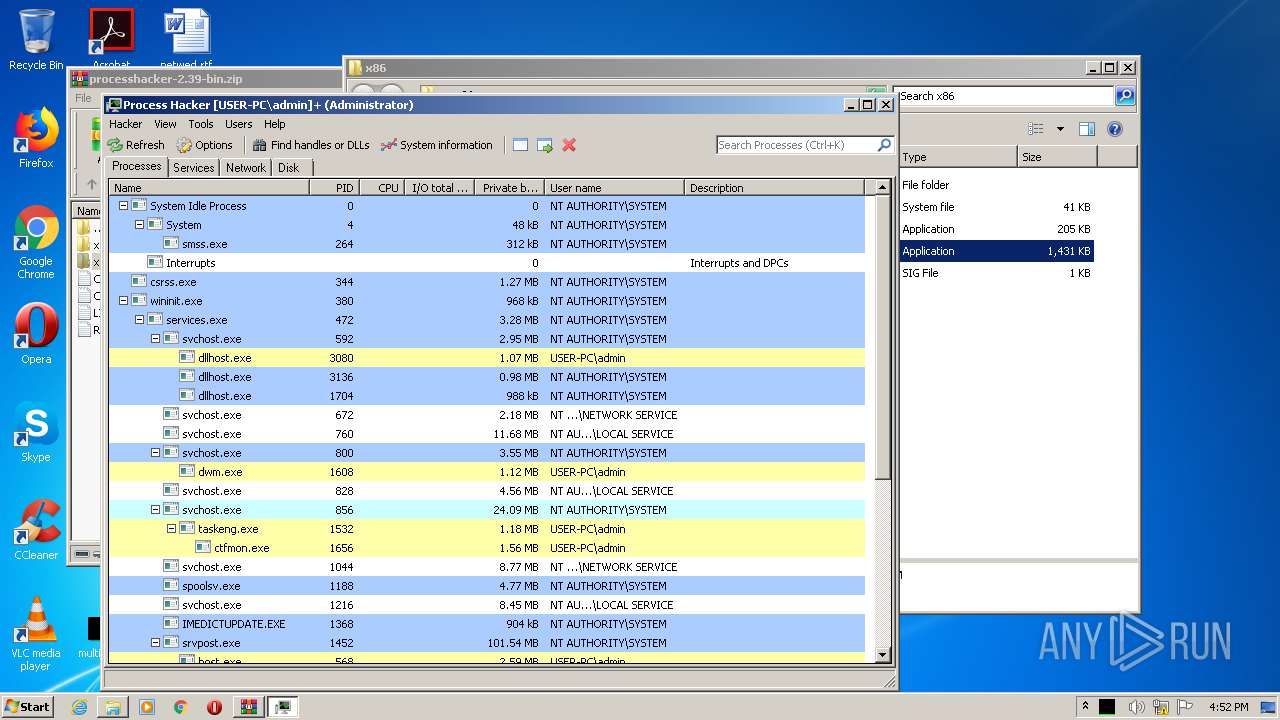
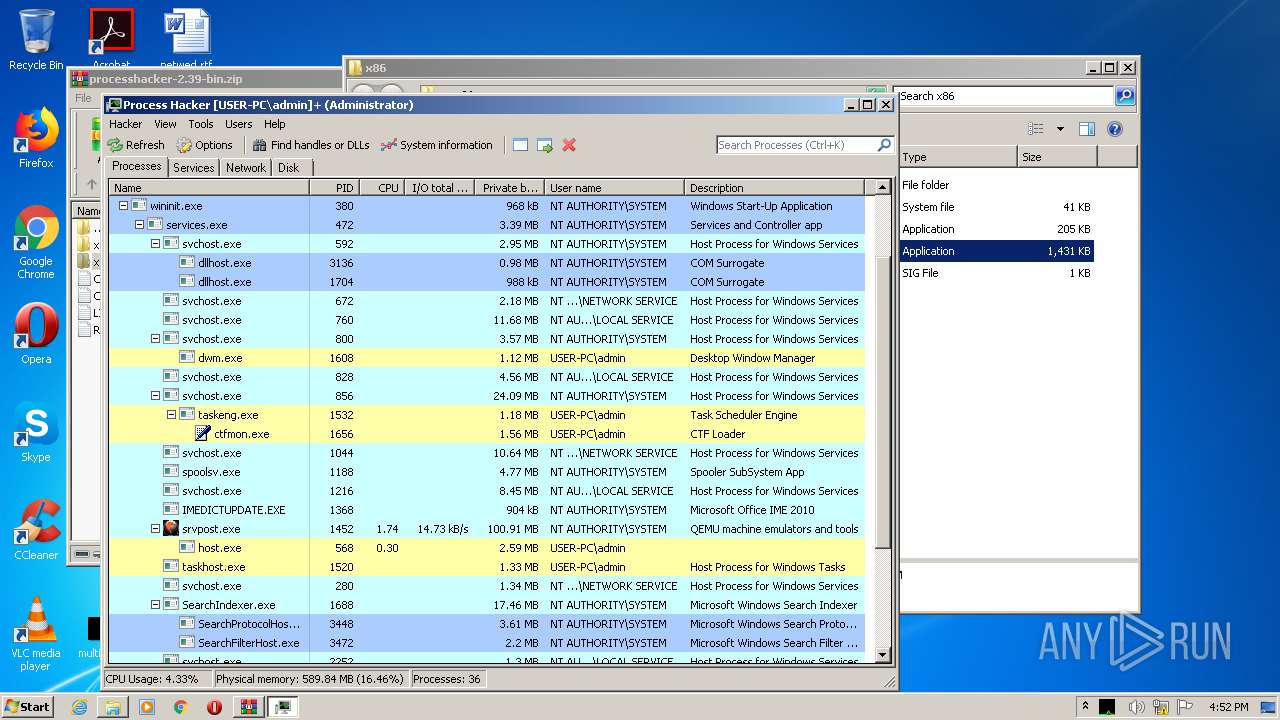
Total processes
40
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
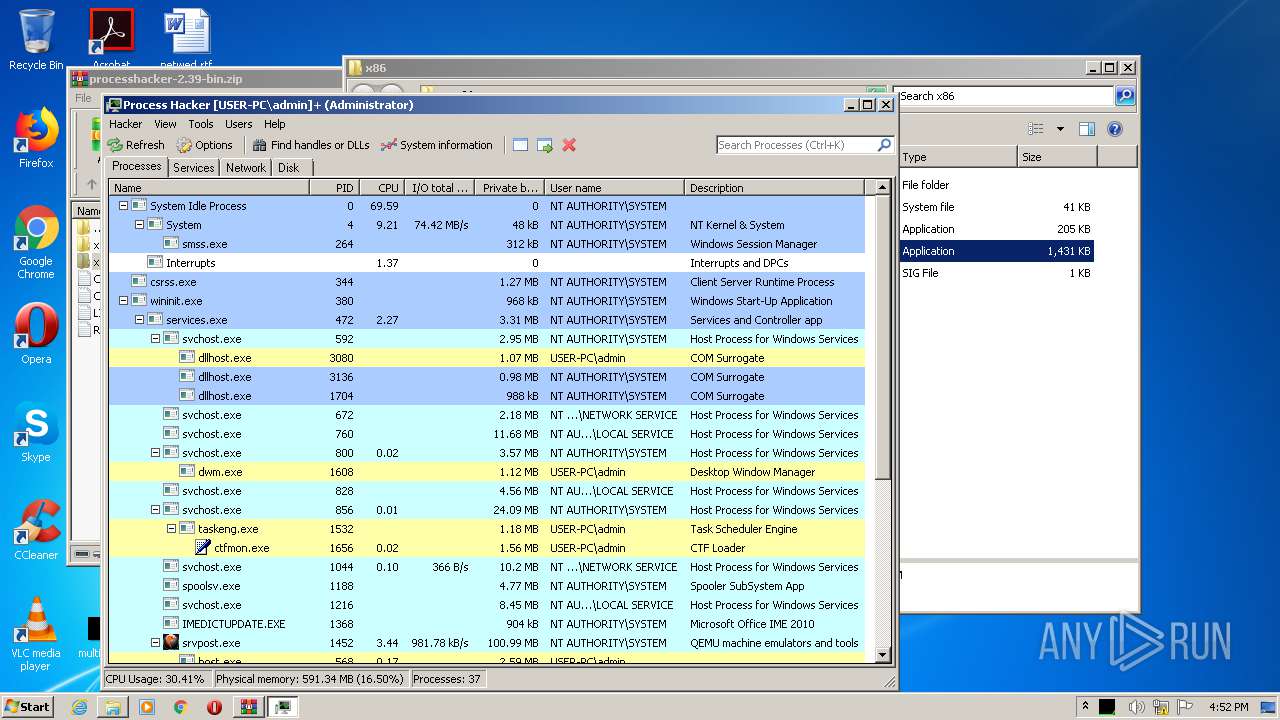
| 2748 | "C:\Users\admin\Desktop\x86\ProcessHacker.exe" | C:\Users\admin\Desktop\x86\ProcessHacker.exe | explorer.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: HIGH Description: Process Hacker Exit code: 0 Version: 2.39.0.124 Modules
| |||||||||||||||
| 2928 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\processhacker-2.39-bin.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
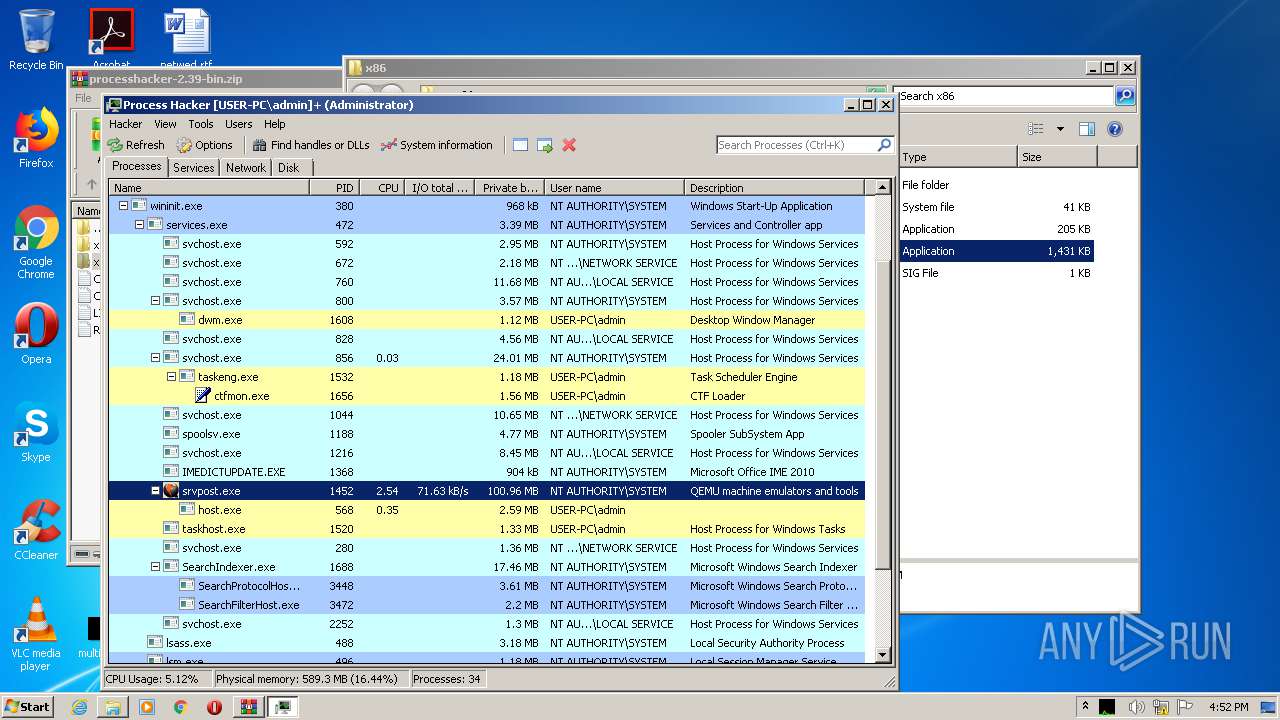
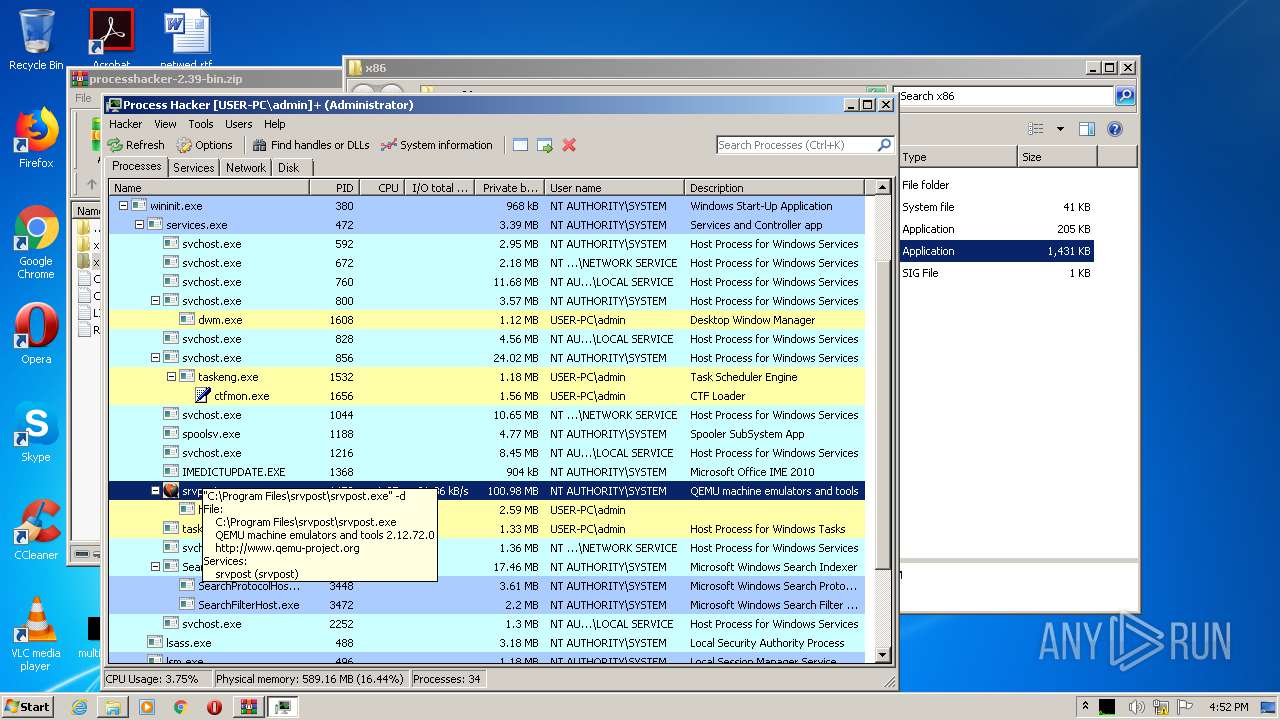
| 3448 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
901
Read events
872
Write events
29
Delete events
0
Modification events
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\processhacker-2.39-bin.zip | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2748) ProcessHacker.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\KProcessHacker3\Parameters |
| Operation: | write | Name: | SecurityLevel |
Value: 1 | |||
| (PID) Process: | (2748) ProcessHacker.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\KProcessHacker3\Parameters |
| Operation: | write | Name: | DynamicConfiguration |
Value: 0300000001000000060001000100FFFF3D0000000C00F400FFFFFFFFFFFF0800FFFF08001400FFFFFFFF0000 | |||
Executable files
15
Suspicious files
0
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.15293\x86\kprocesshacker.sys | executable | |
MD5:6365FE1D37545C71CBE2719AC7831BDD | SHA256:0F97F6D53FFF47914174BC3A05FB016E2C02ED0B43C827E5E5AADBA2D244AECC | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.15293\x86\plugins\OnlineChecks.dll | executable | |
MD5:D811B73D47B603E0D212FE311409B5D8 | SHA256:118192E0816876CB1AF3453A36FF2AFDD48C09591399779C7B12DD083B1EFCEA | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.15293\x86\plugins\Updater.dll | executable | |
MD5:0D69DBDAFE0A75066405C10413C7EB7B | SHA256:BADADDEEEF941610EB0912330848349A08FCAC0983D7FB749C45F70B86C59C7C | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.15293\x86\plugins\ExtendedServices.dll | executable | |
MD5:0C1A9C2A6190F1BAAB115316DA215F89 | SHA256:647611756CAC85D8FCC8CD78EFDC5712C68E4FE7BBCC8A64081900C68BCC0FEB | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.15293\x86\plugins\DotNetTools.dll | executable | |
MD5:15AB3740703138ED5C091EA7736620F4 | SHA256:0D7240D074BA544C90DF72D5E339978AA2EDC19F4A02C0A302718D851B11C384 | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.15293\x86\plugins\ExtendedNotifications.dll | executable | |
MD5:56CC0204D69BE9FE0987F6570783A138 | SHA256:C1A74CAA7DA222A78715D4307F6247CB8ABA4CB01434286E17D9CB18860AA612 | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.15293\x86\plugins\HardwareDevices.dll | executable | |
MD5:7C35A25859271E4550580A5B6EC769FA | SHA256:E0C91AD1EAD26BA93257059B5A7600C6FC3BAF3278499D850E9E884FEA409761 | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.15293\x86\plugins\UserNotes.dll | executable | |
MD5:7DE6AA4F0D79E4B243A66B4DB6F17FE9 | SHA256:A94D02D9645A4F4FE0388BB40775862AA3F90D22A93FDB14870389AB891B486D | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.15293\x86\ProcessHacker.sig | flc | |
MD5:98208B7641DE5BD8DC9B524FE87A3C5F | SHA256:35DB042E16C8A39C8289660ADC8CC493A800E392227D83380931DC28705AF86E | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.15293\x86\peview.exe | executable | |
MD5:711BE6337CB78A948F04759A0BD210CE | SHA256:41967C3EE8B8E2416DDB3E82D8DF1219365A7B180138CA8C3256192794E5F8FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2748 | ProcessHacker.exe | 162.243.25.33:443 | wj32.org | Digital Ocean, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wj32.org |
| whitelisted |