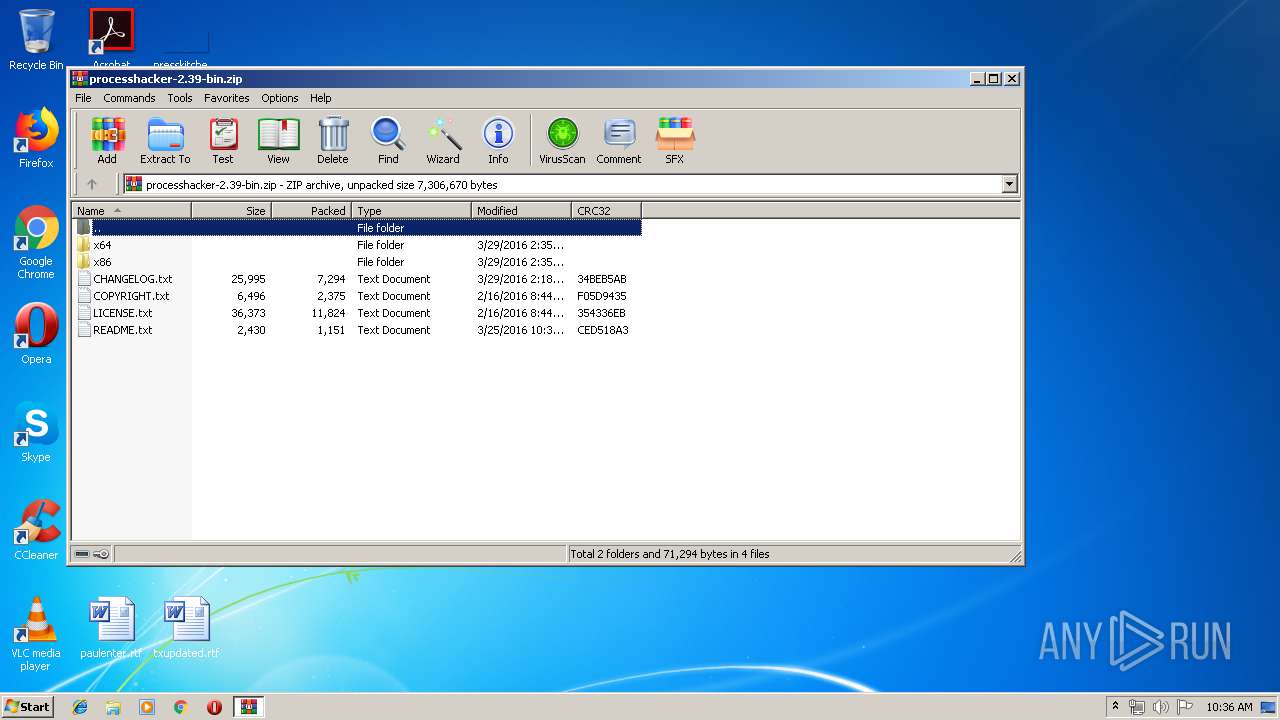
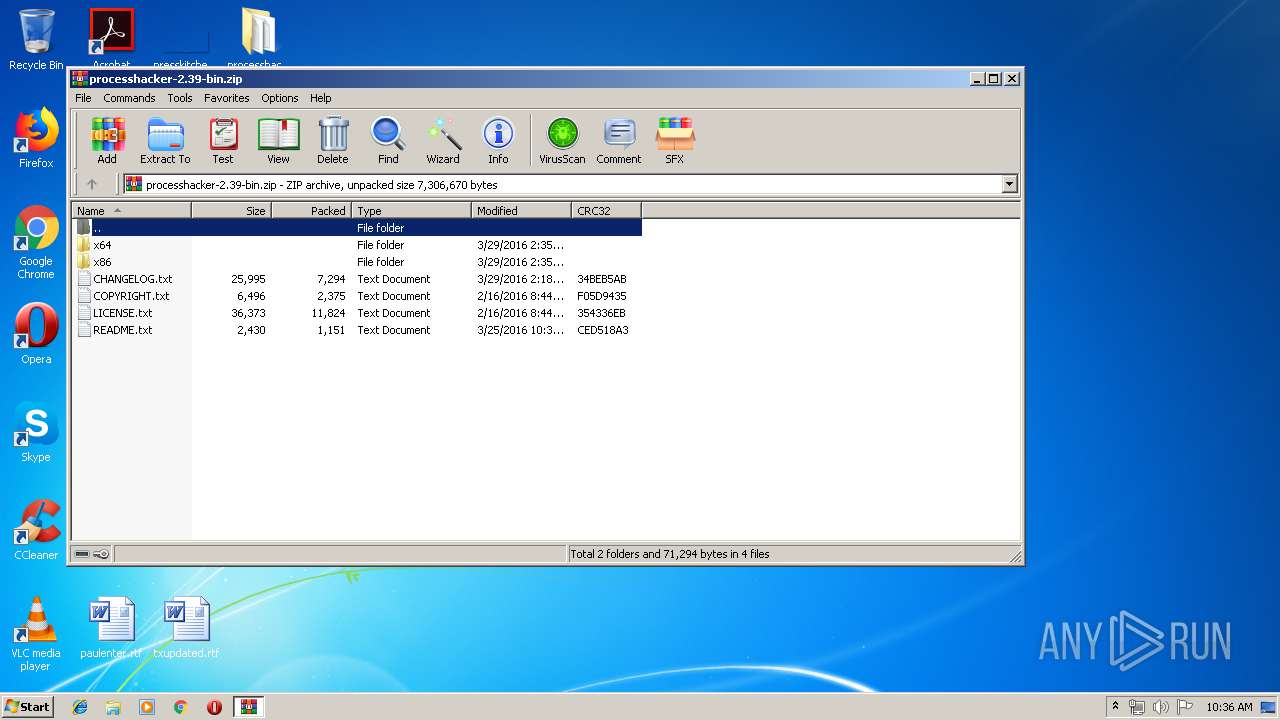
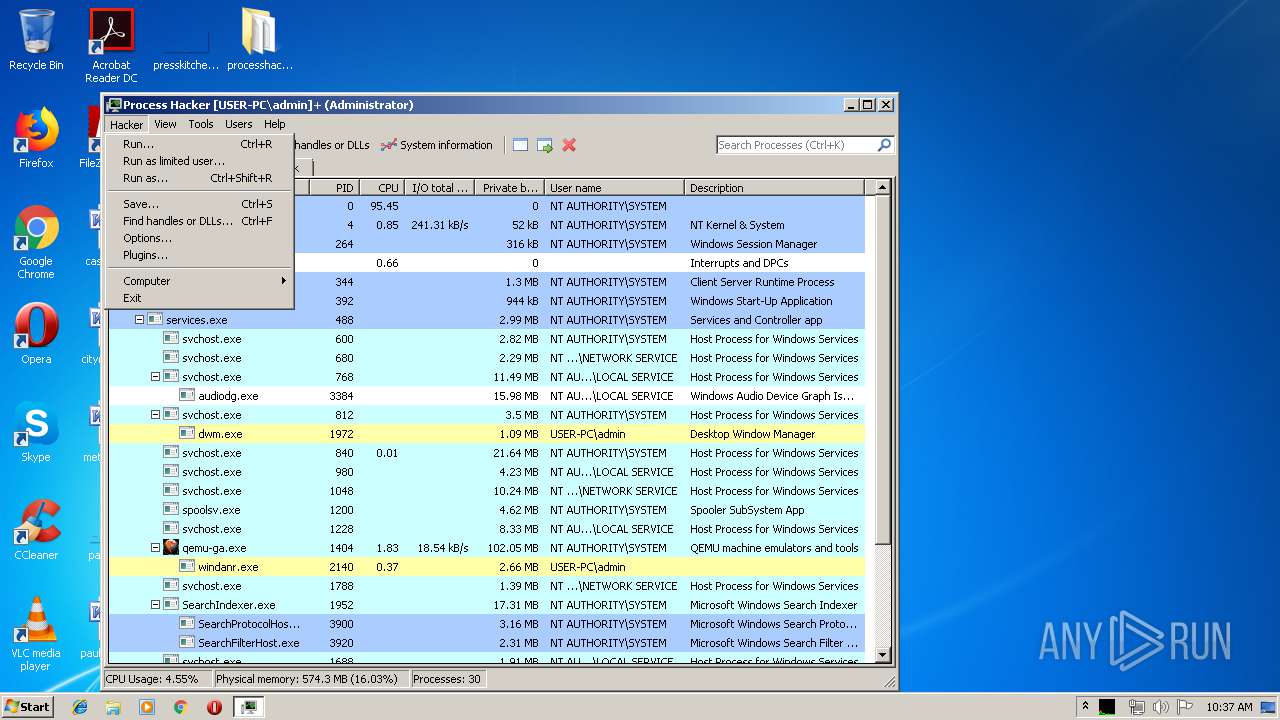
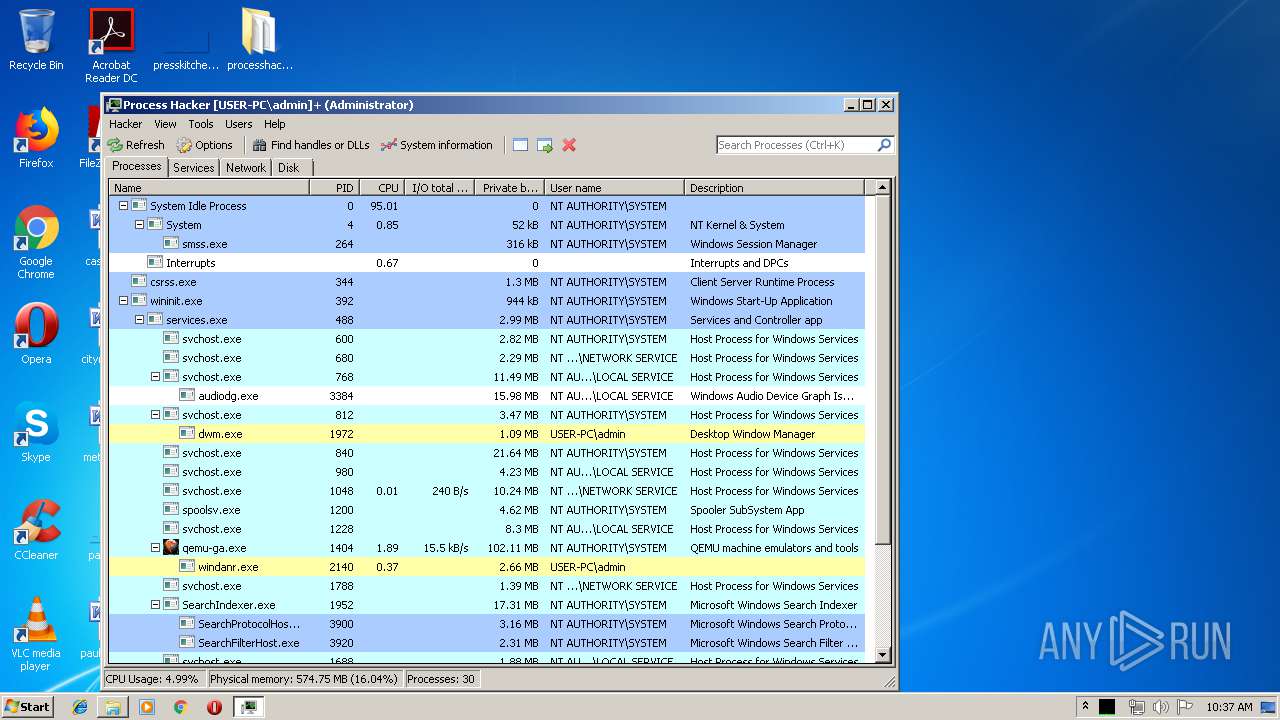
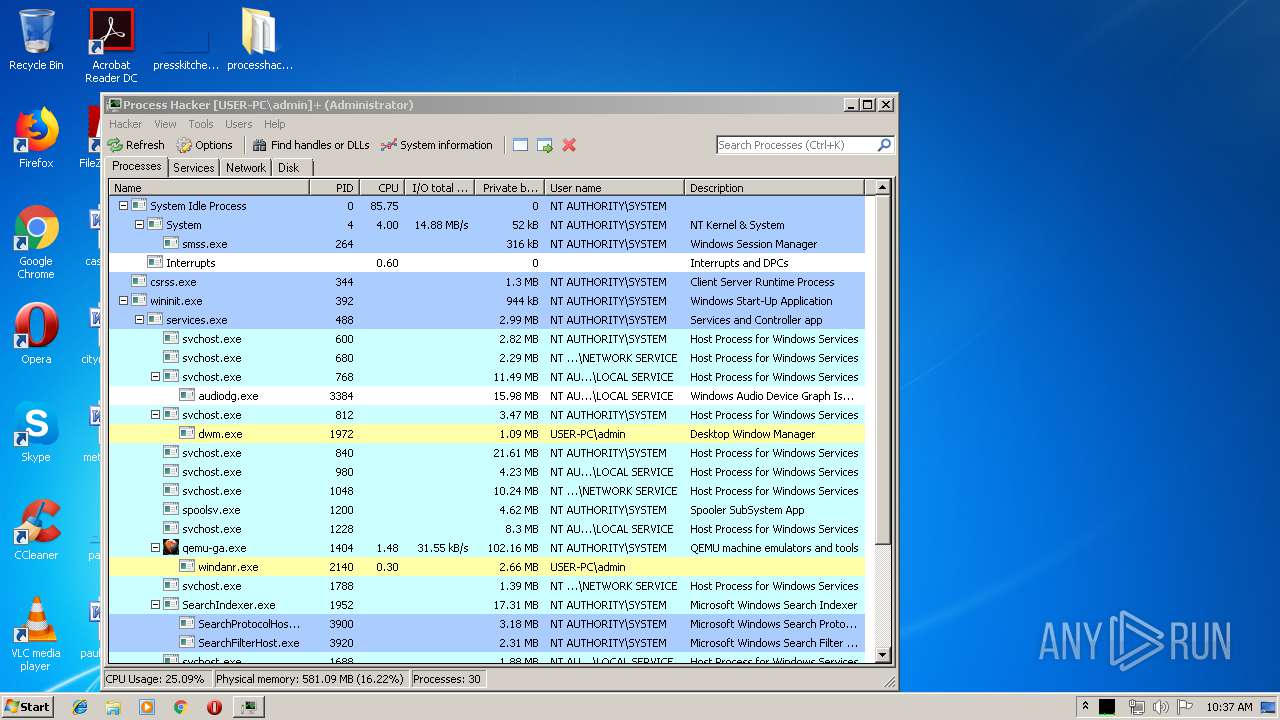
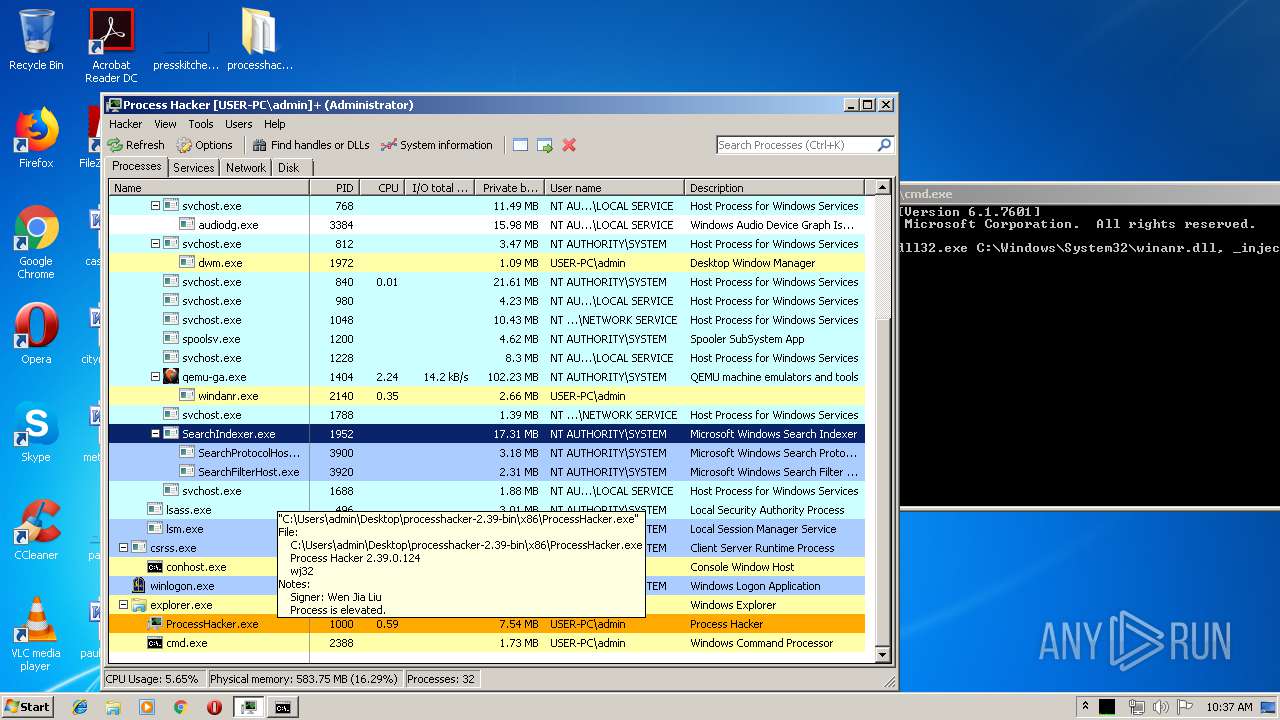
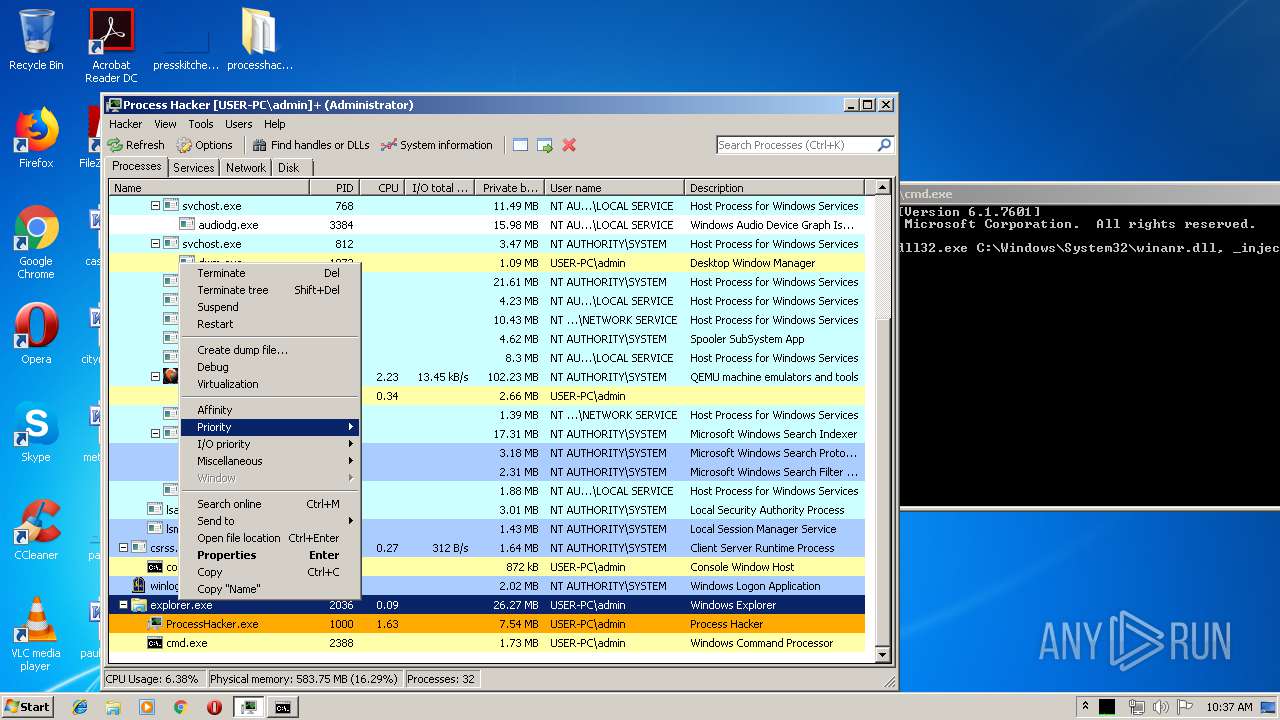
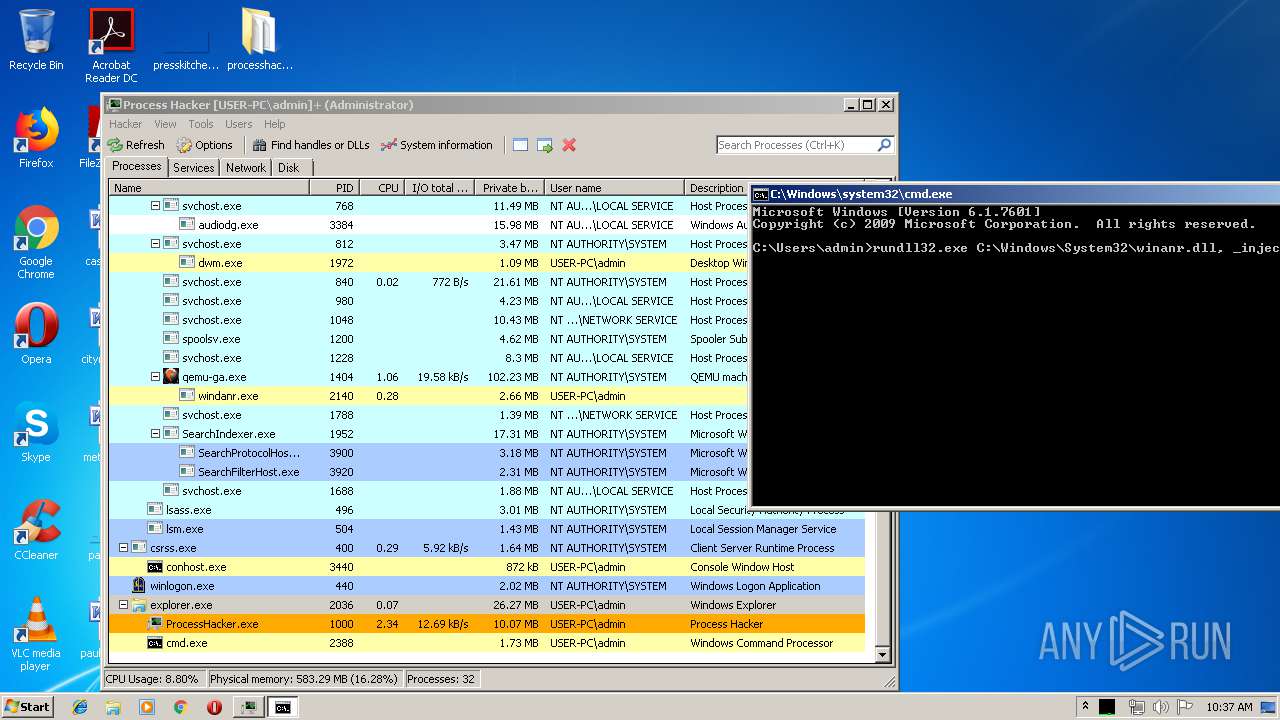
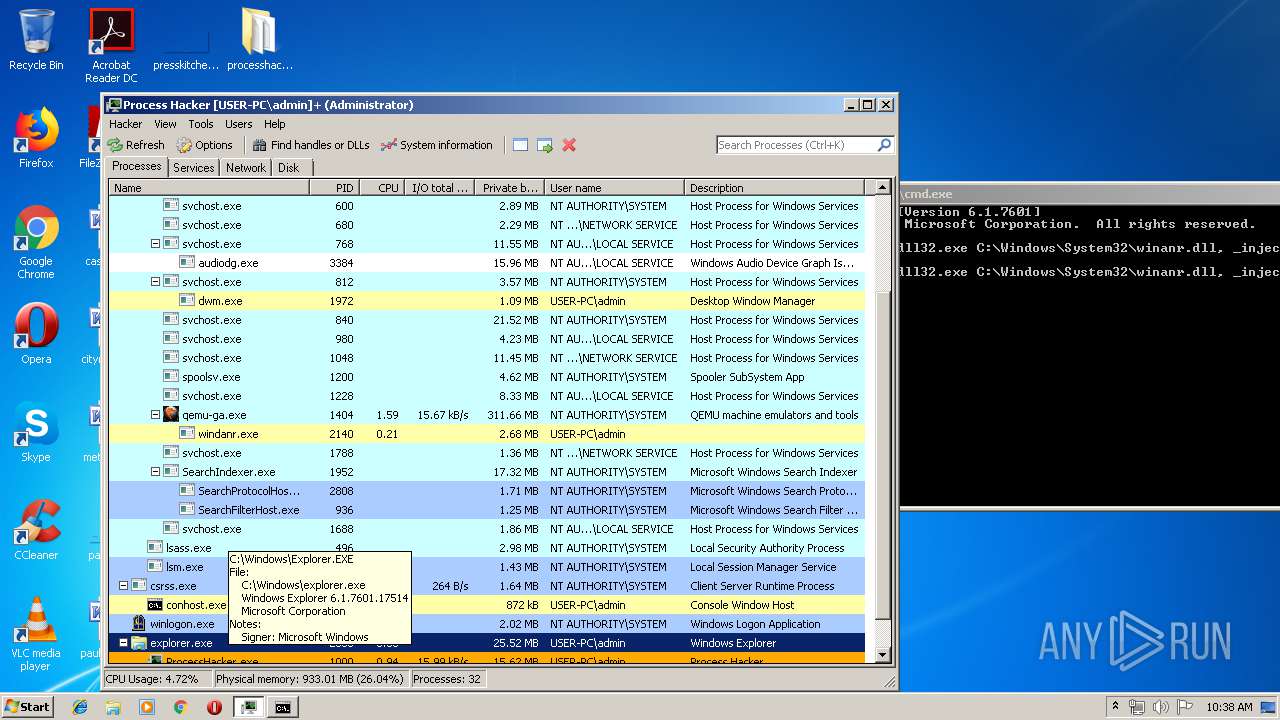
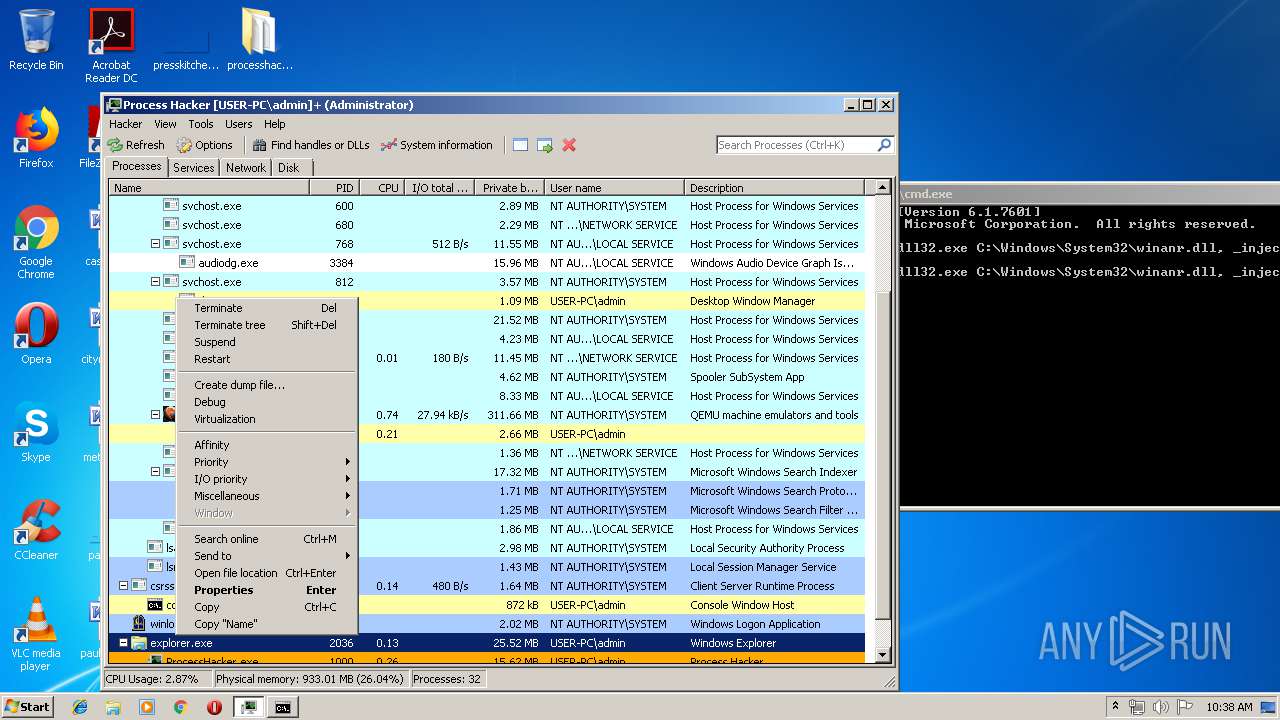
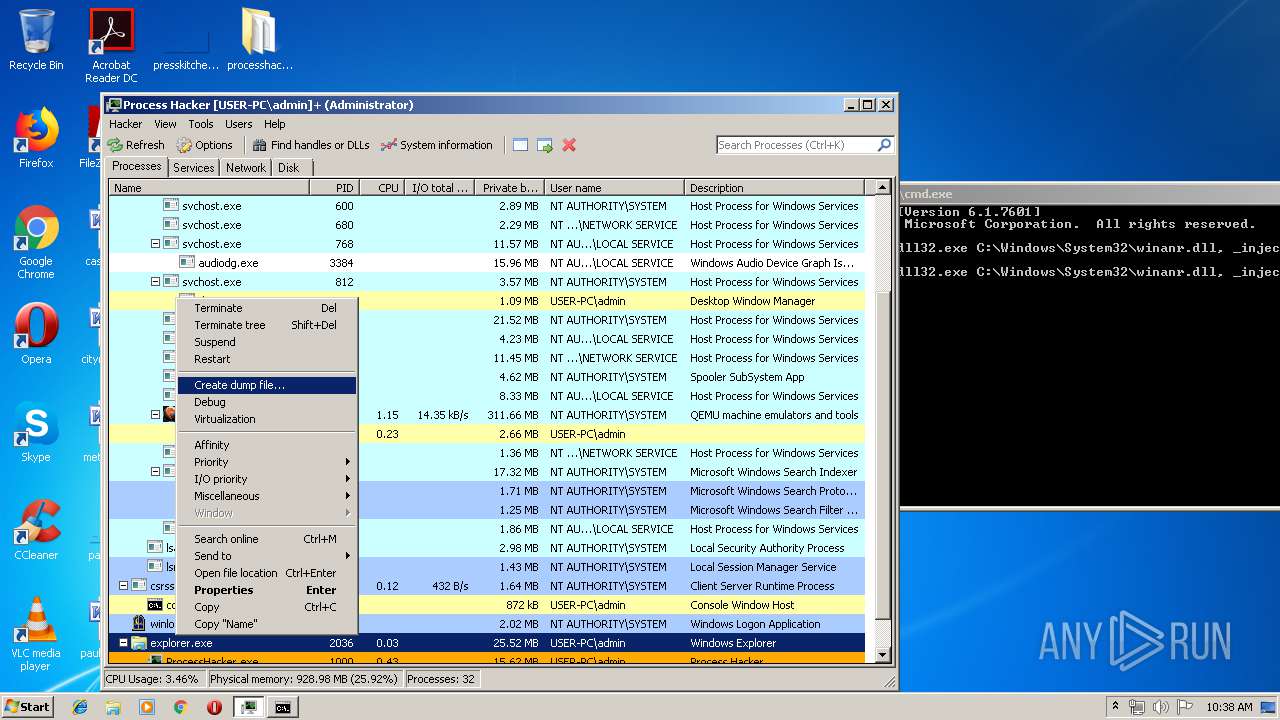
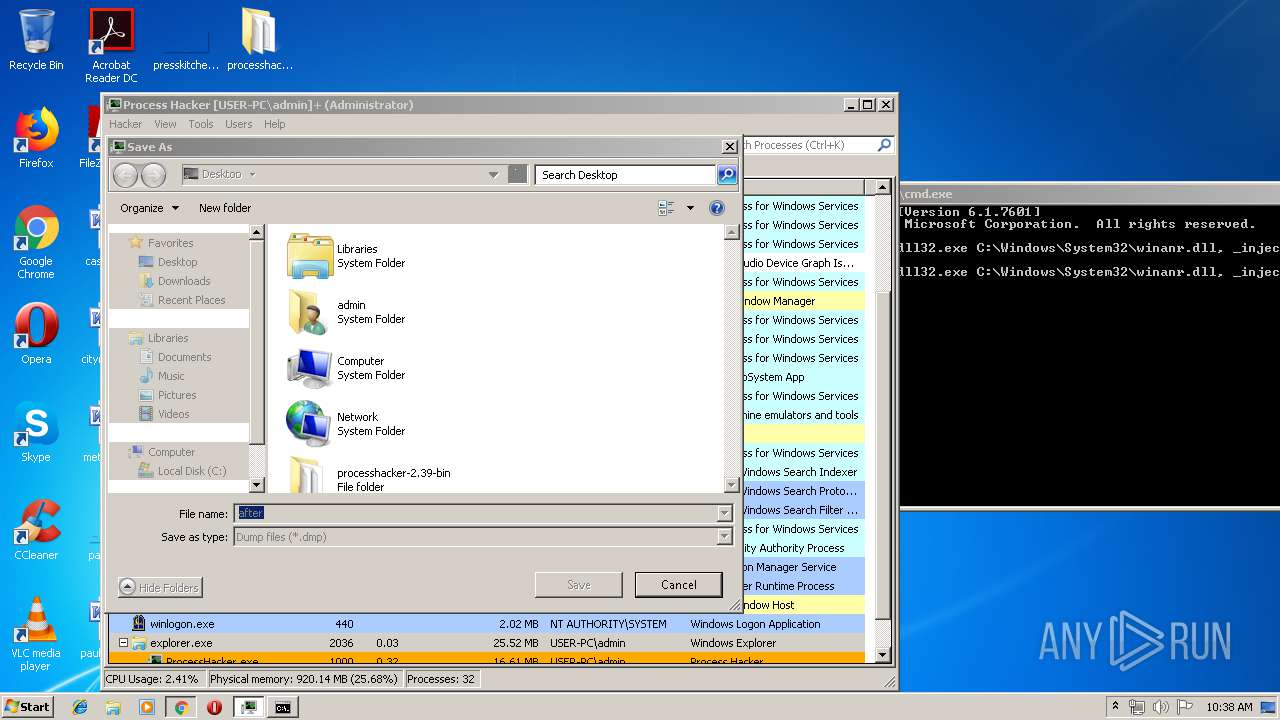
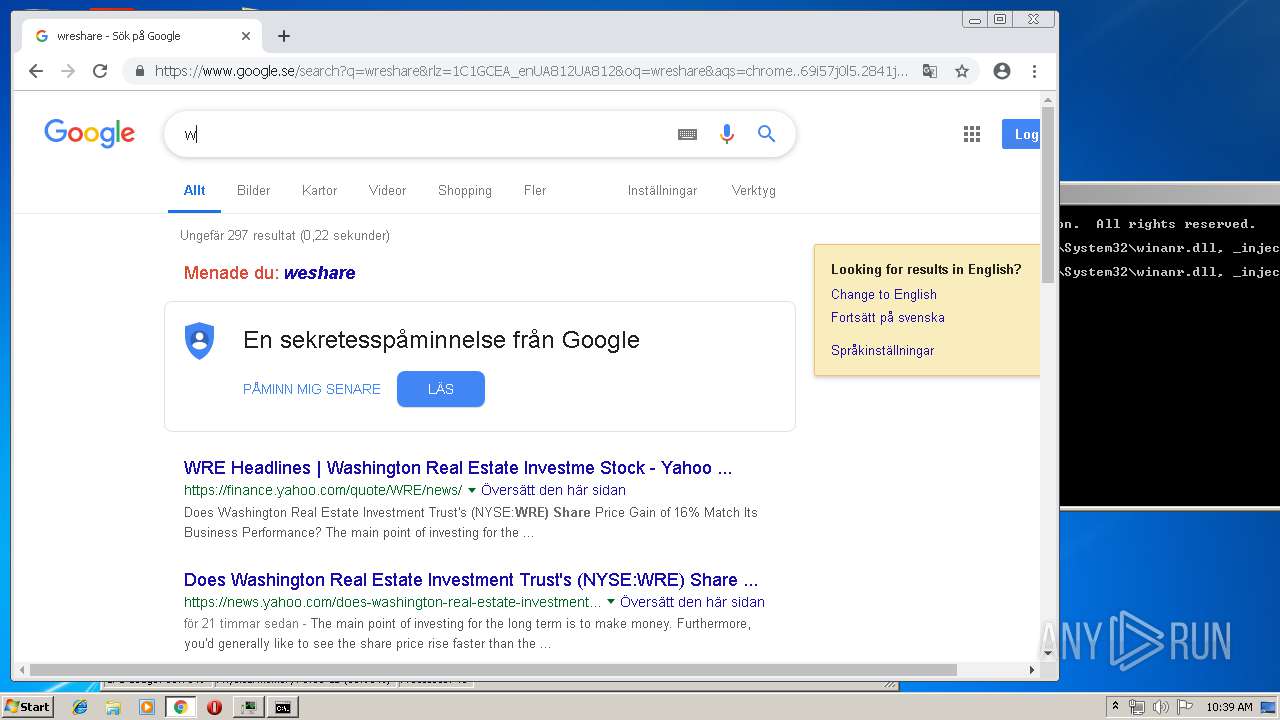
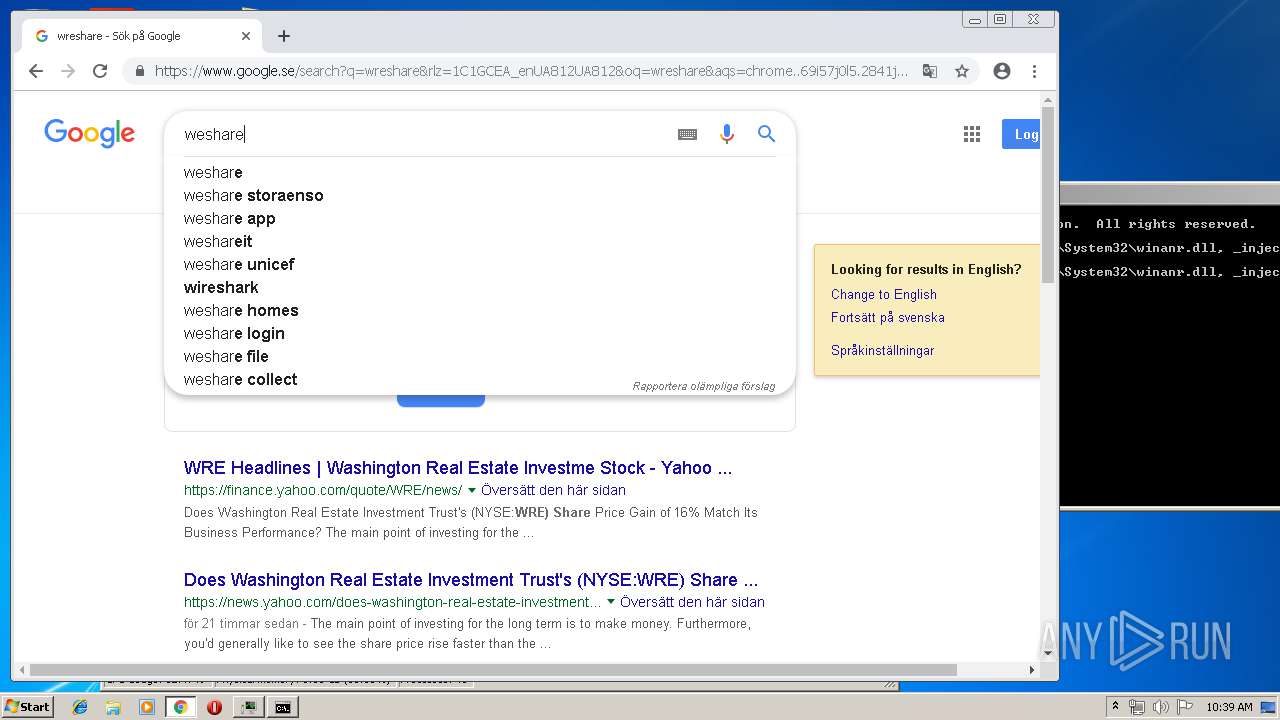
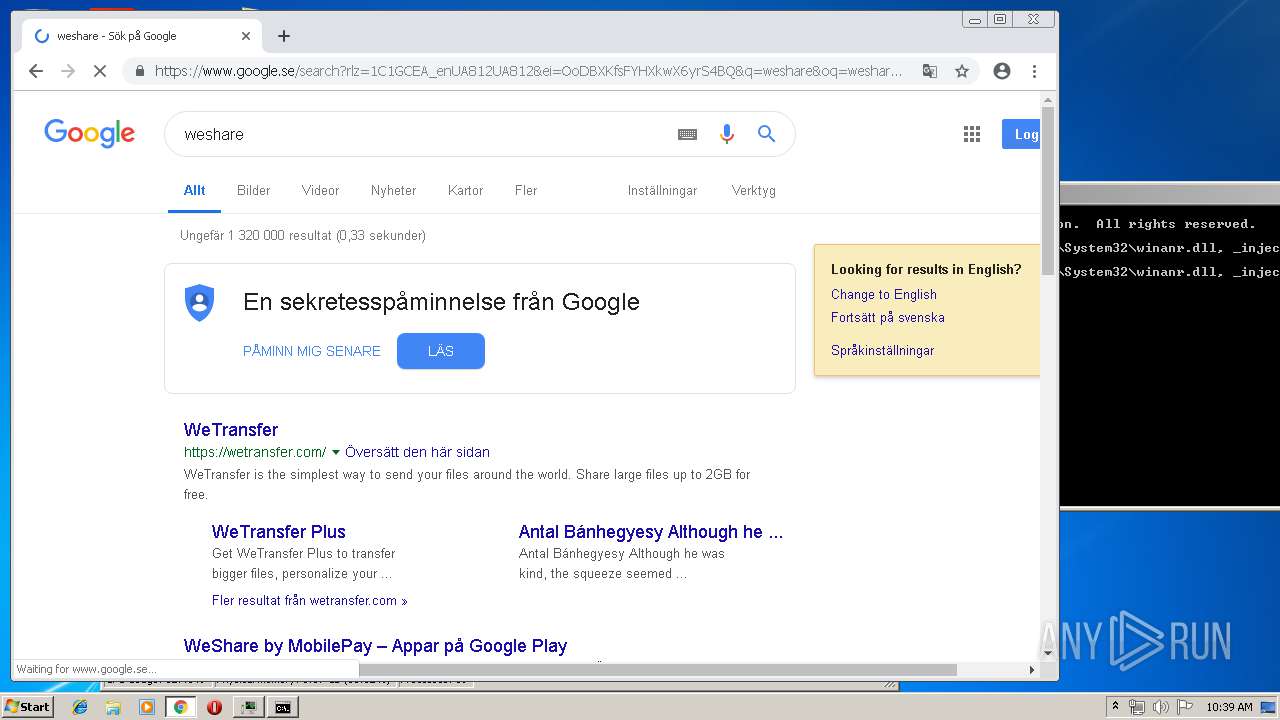
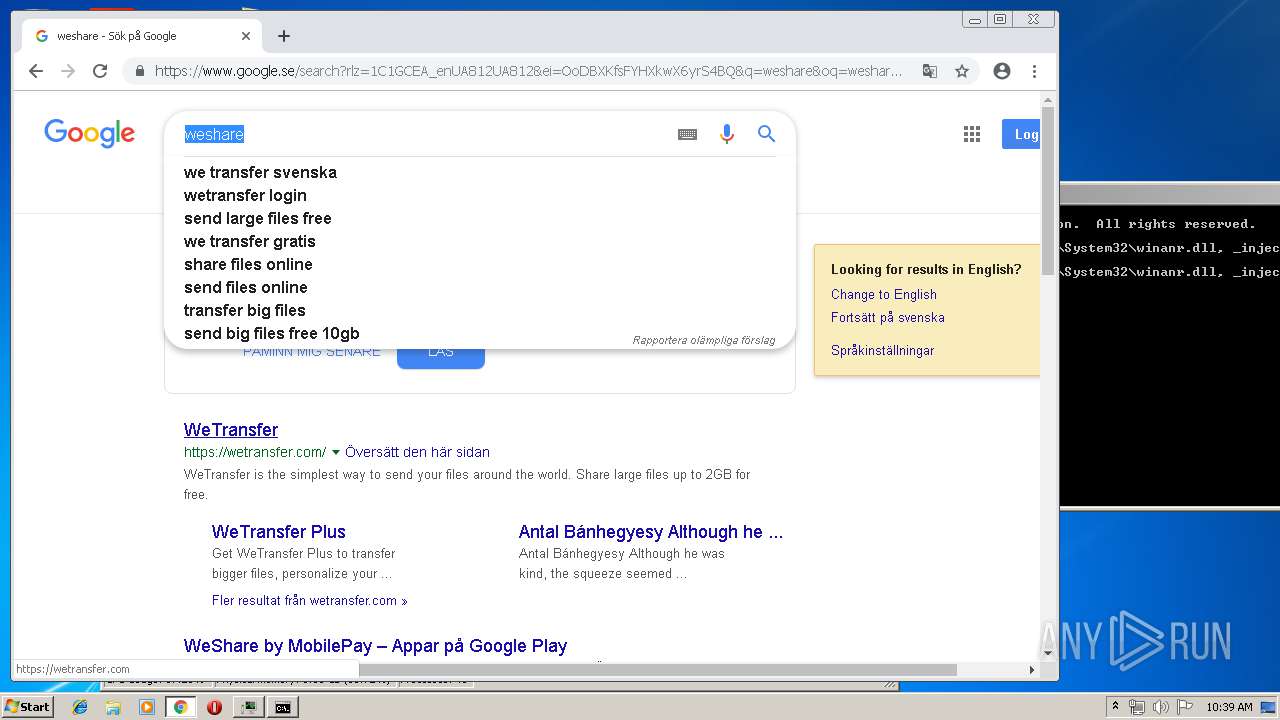
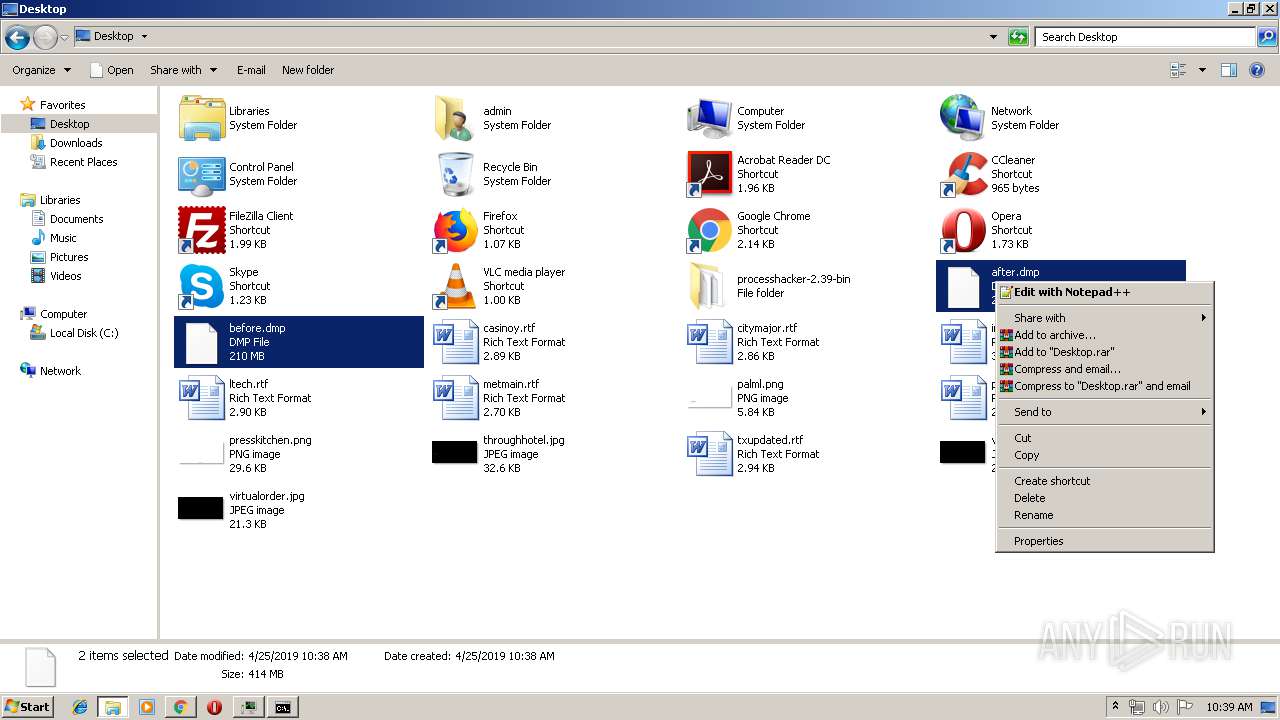
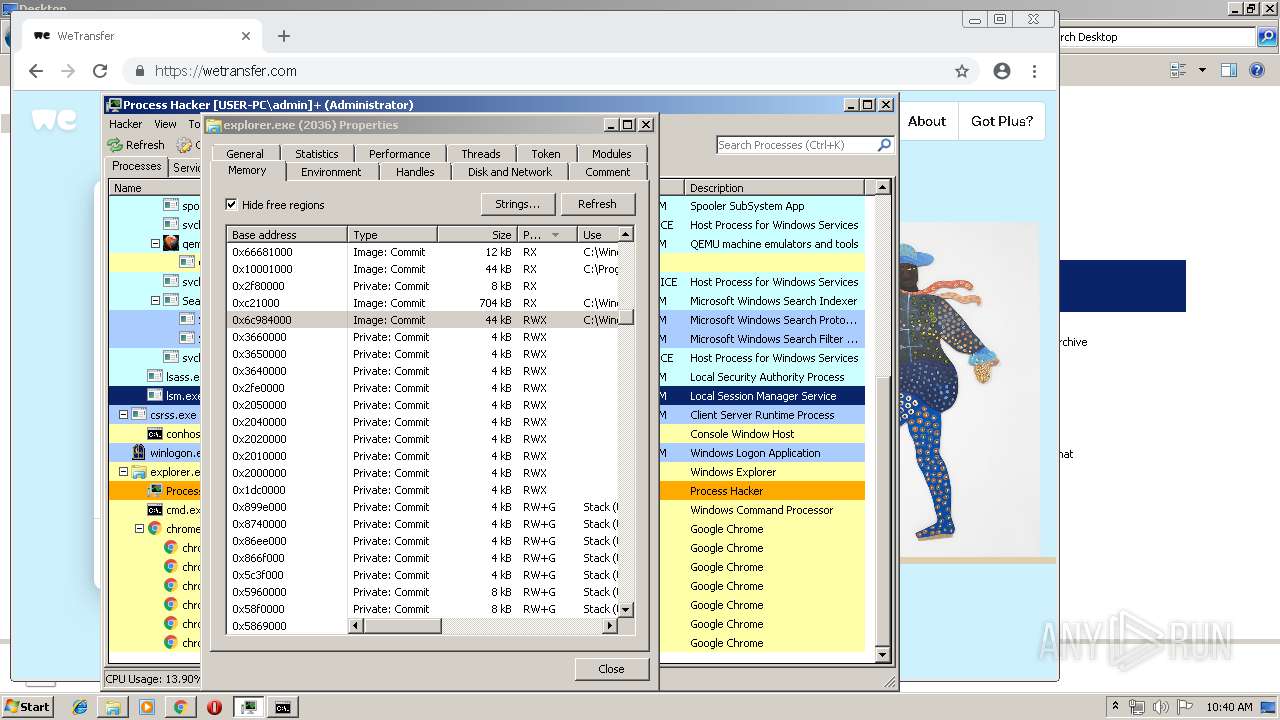
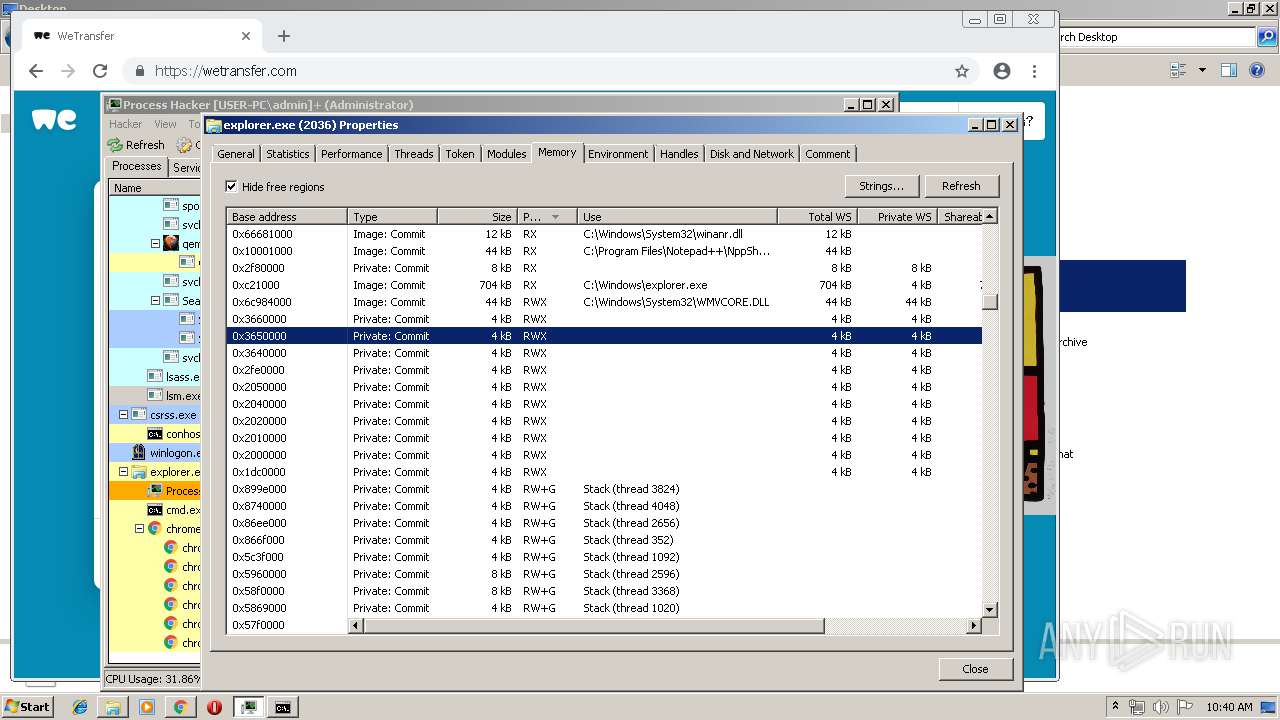
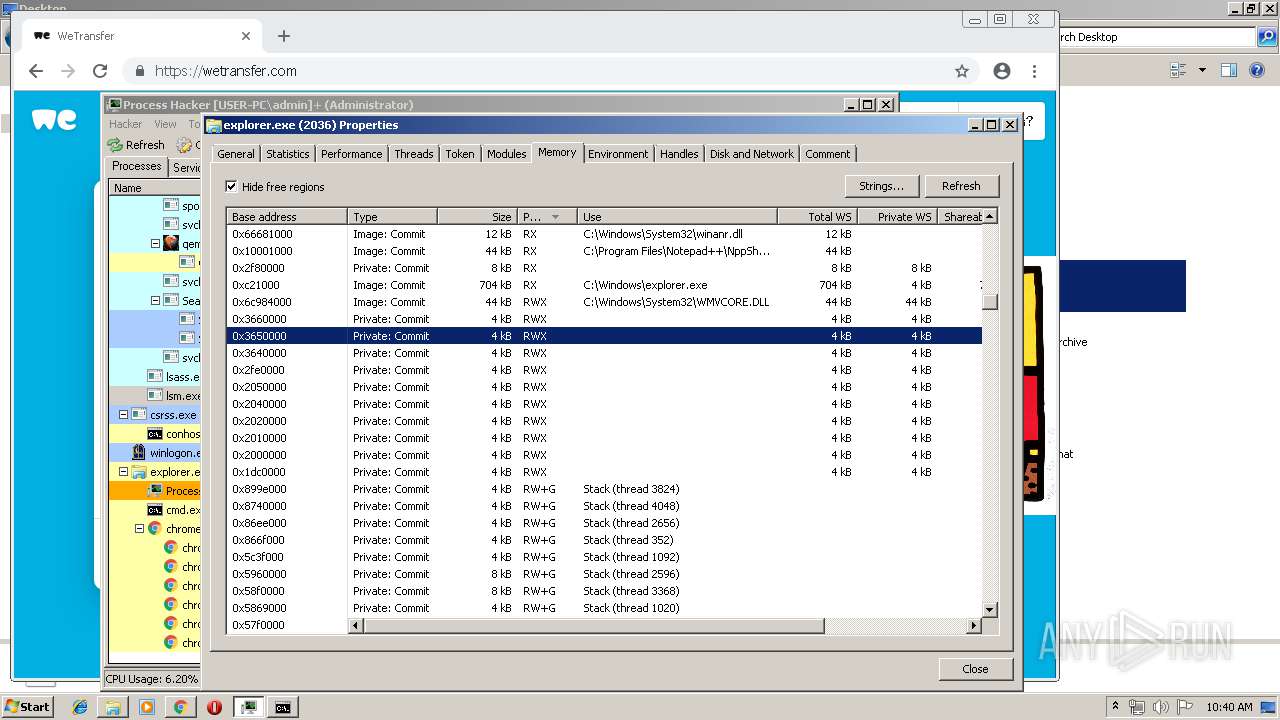
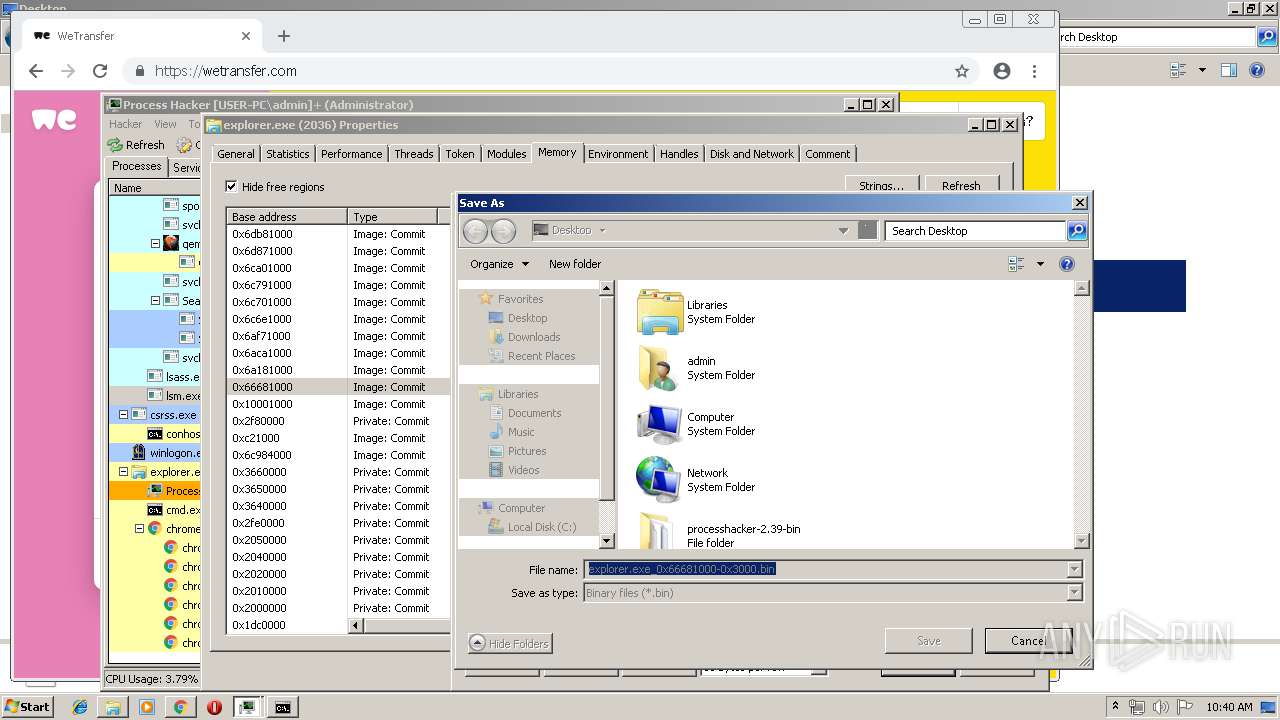
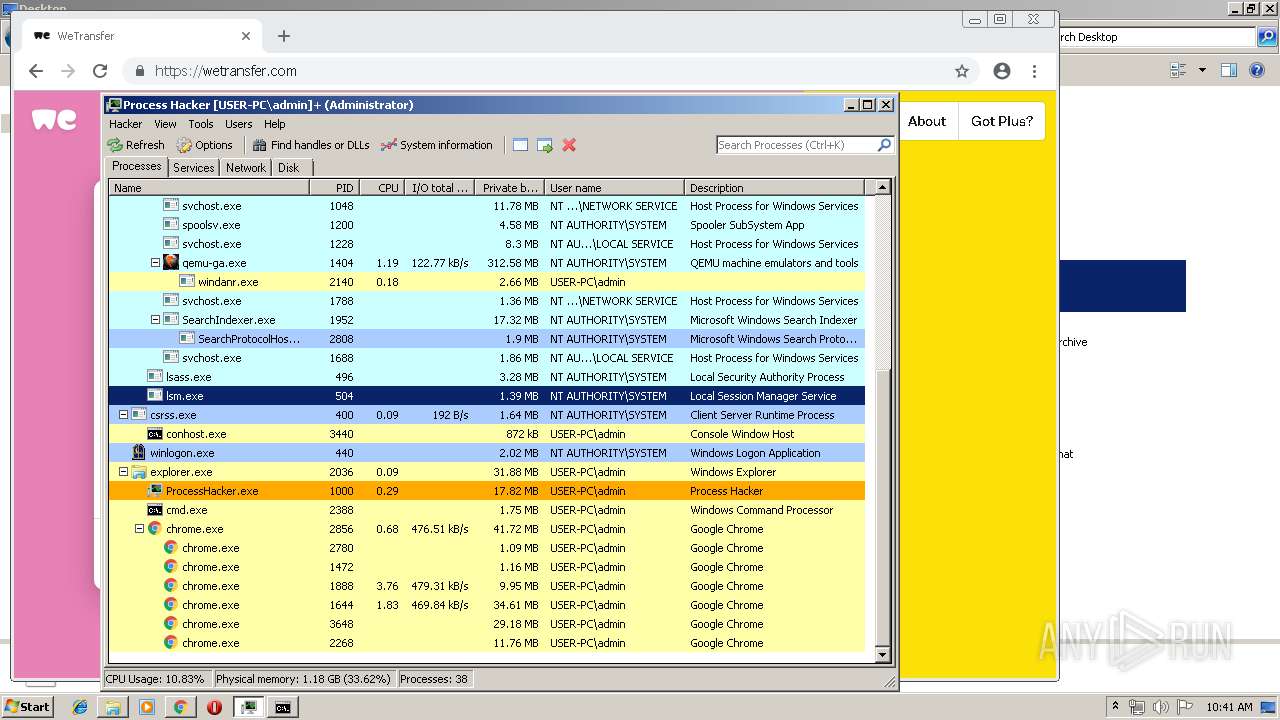
| File name: | processhacker-2.39-bin.zip |
| Full analysis: | https://app.any.run/tasks/2d75dfa3-3aa2-4e03-a616-29bd027e7ec6 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 09:35:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B444CF14642CE9B8D75E079166A5DF0B |
| SHA1: | 8E8F8423D163D922242B8B7D85427664F77EDC97 |
| SHA256: | 2AFB5303E191DDE688C5626C3EE545E32E52F09DA3B35B20F5E0D29A418432F5 |
| SSDEEP: | 98304:jDqt5TrOmlLB/7rTOqcXfOzJR1qioDLK2EbhQ:3sTrHlB73OqX4ioDfshQ |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3900)
- ProcessHacker.exe (PID: 1000)
Changes settings of System certificates
- ProcessHacker.exe (PID: 1000)
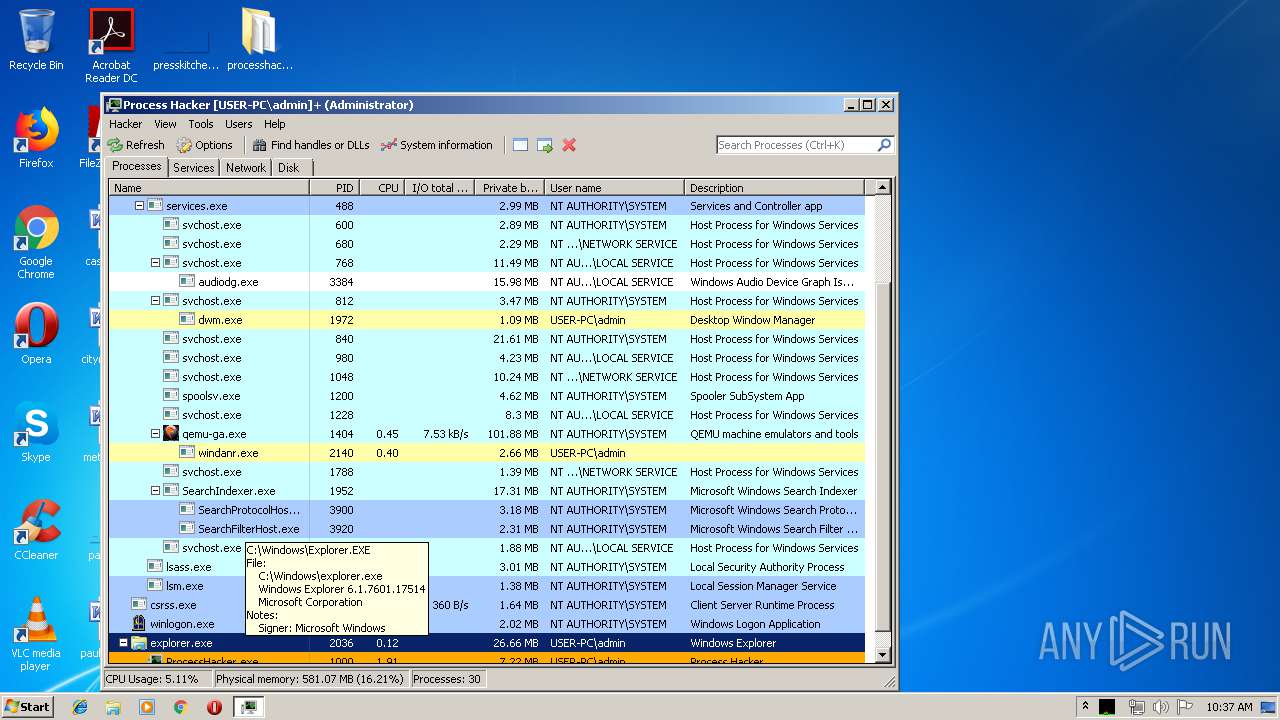
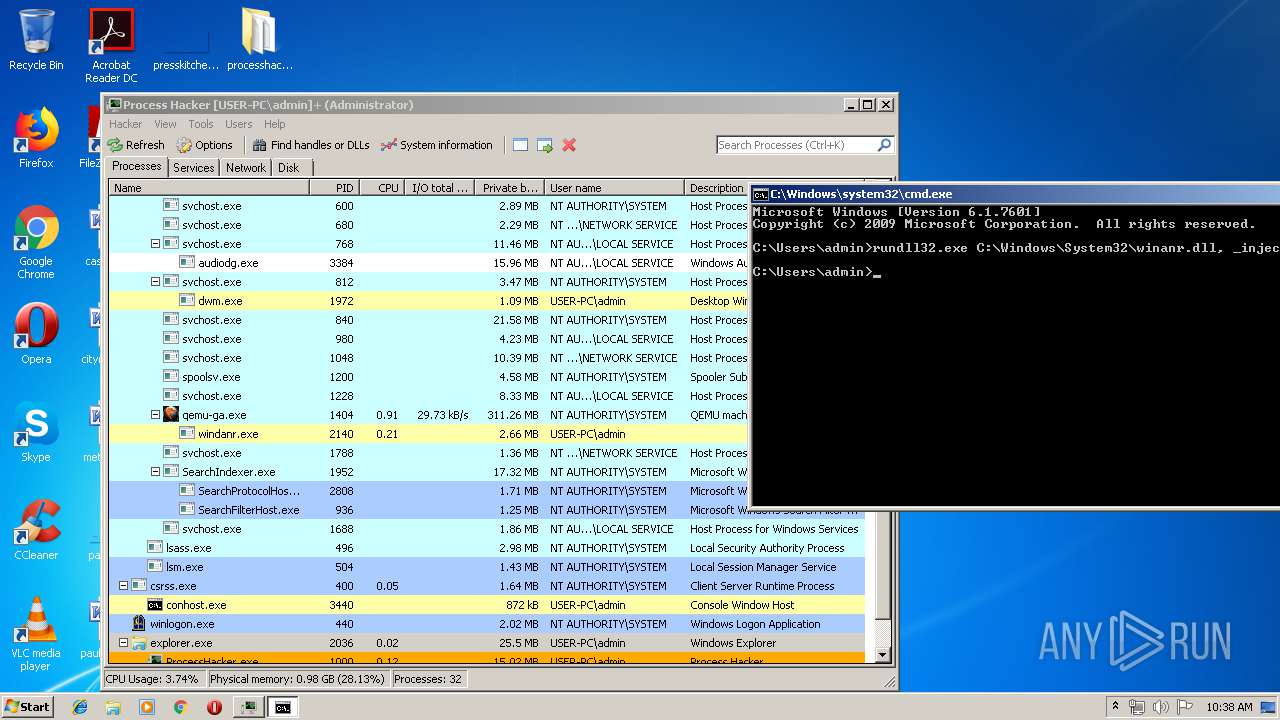
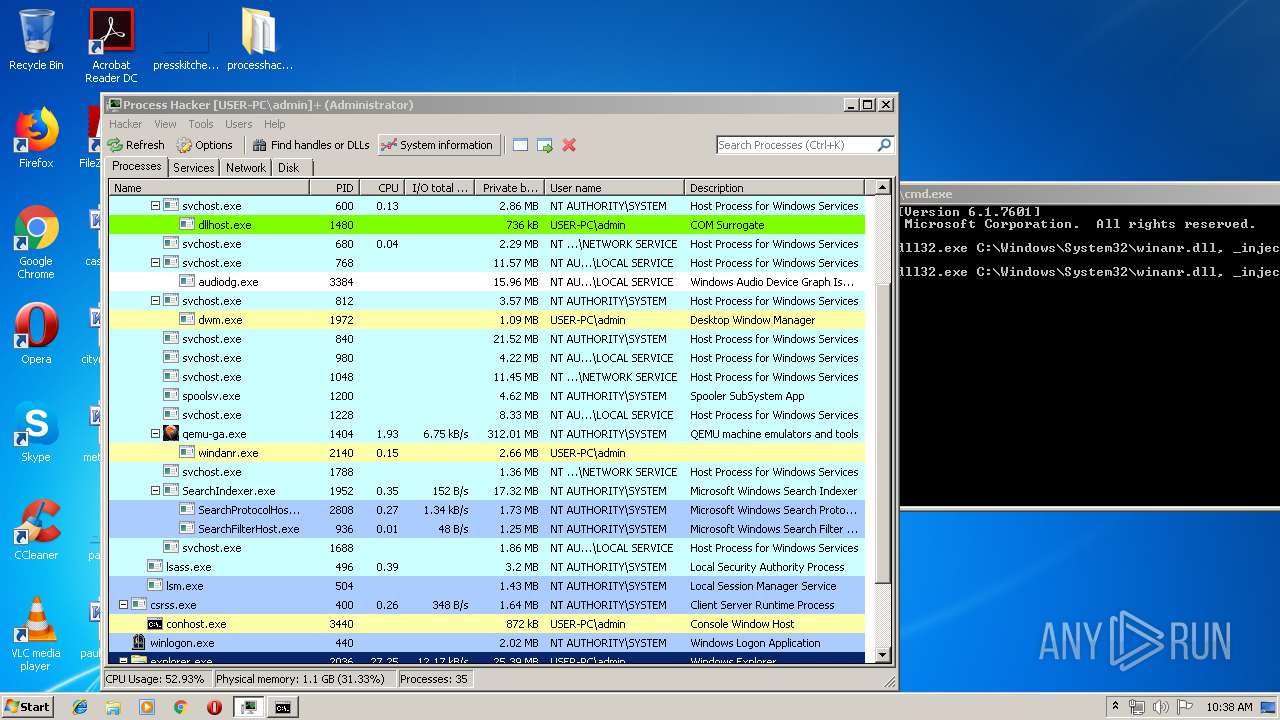
Application was injected by another process
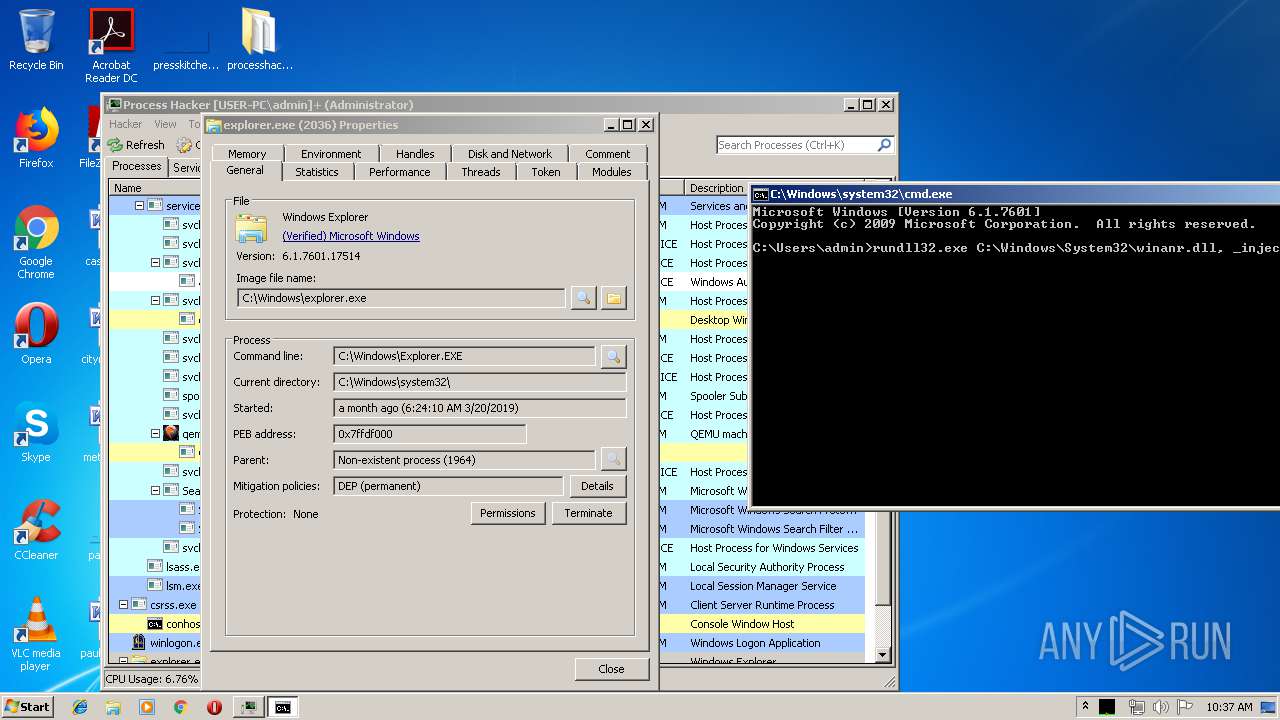
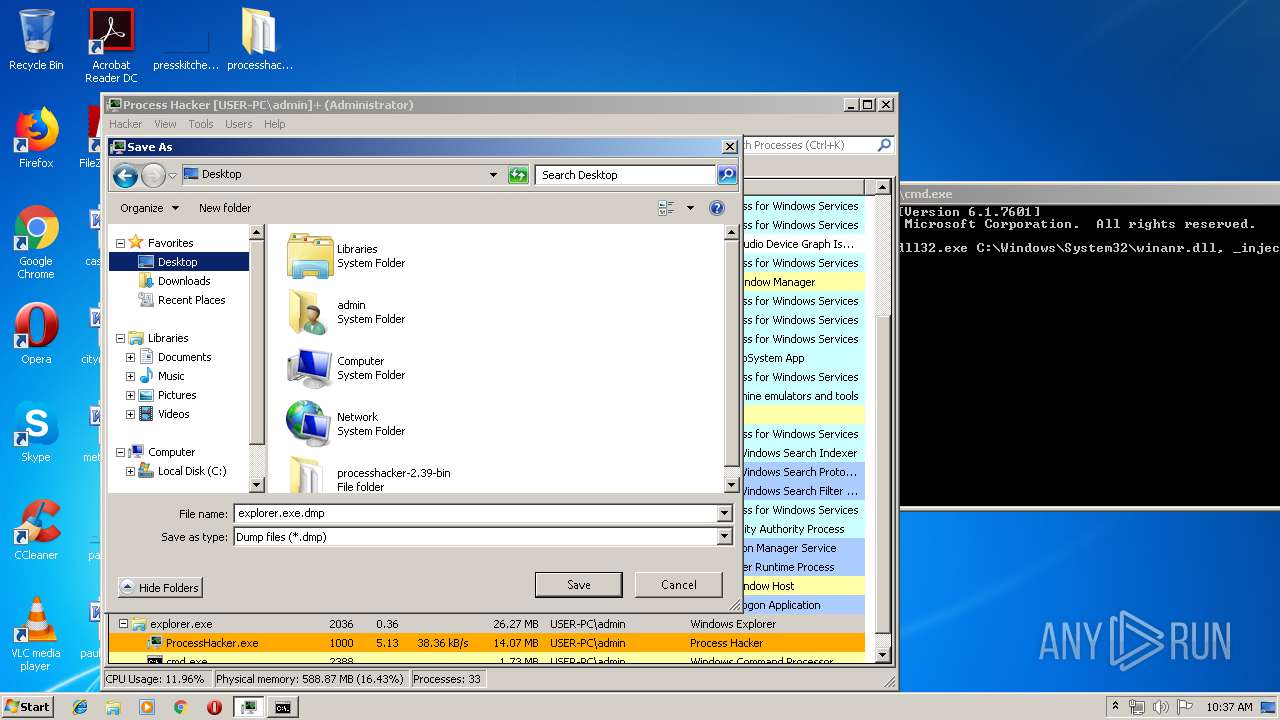
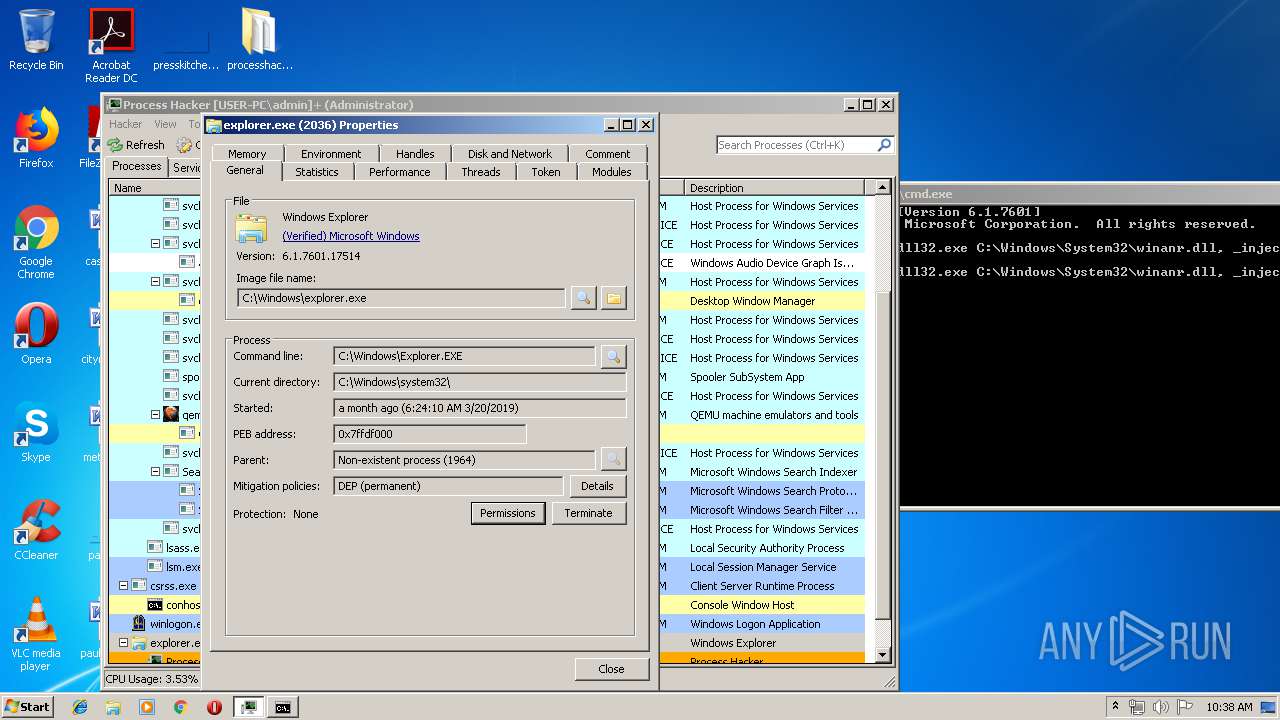
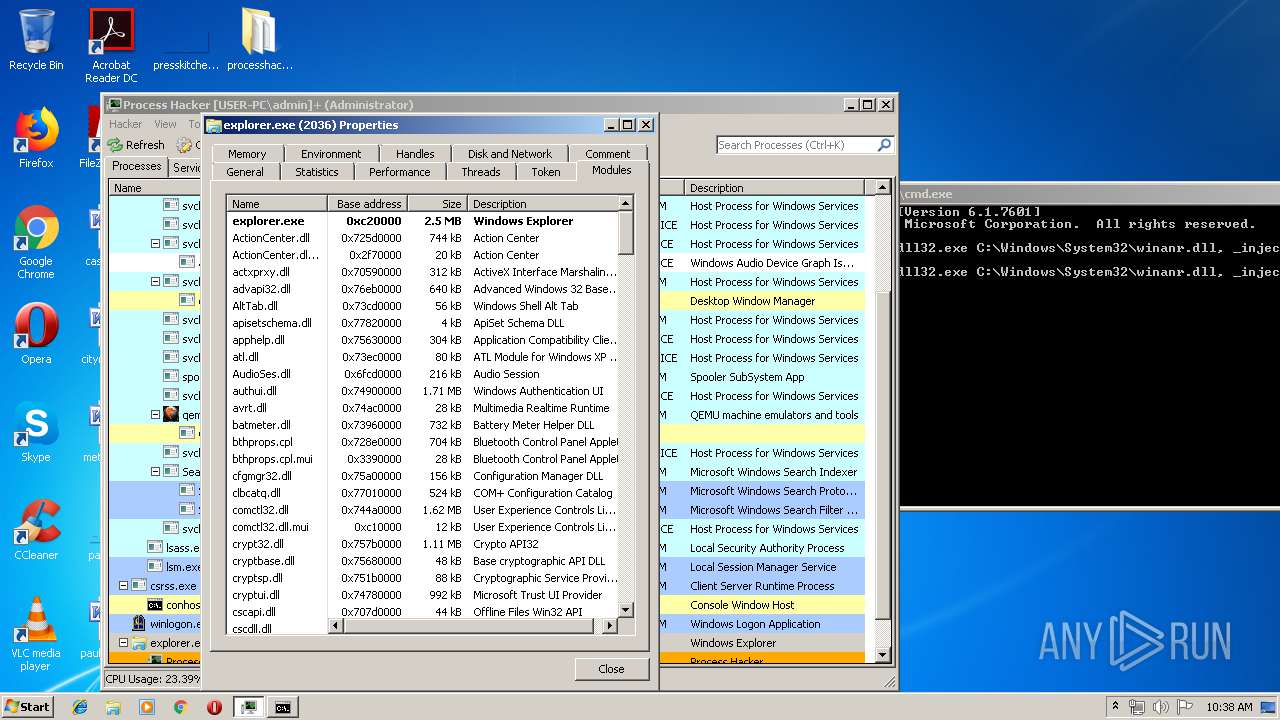
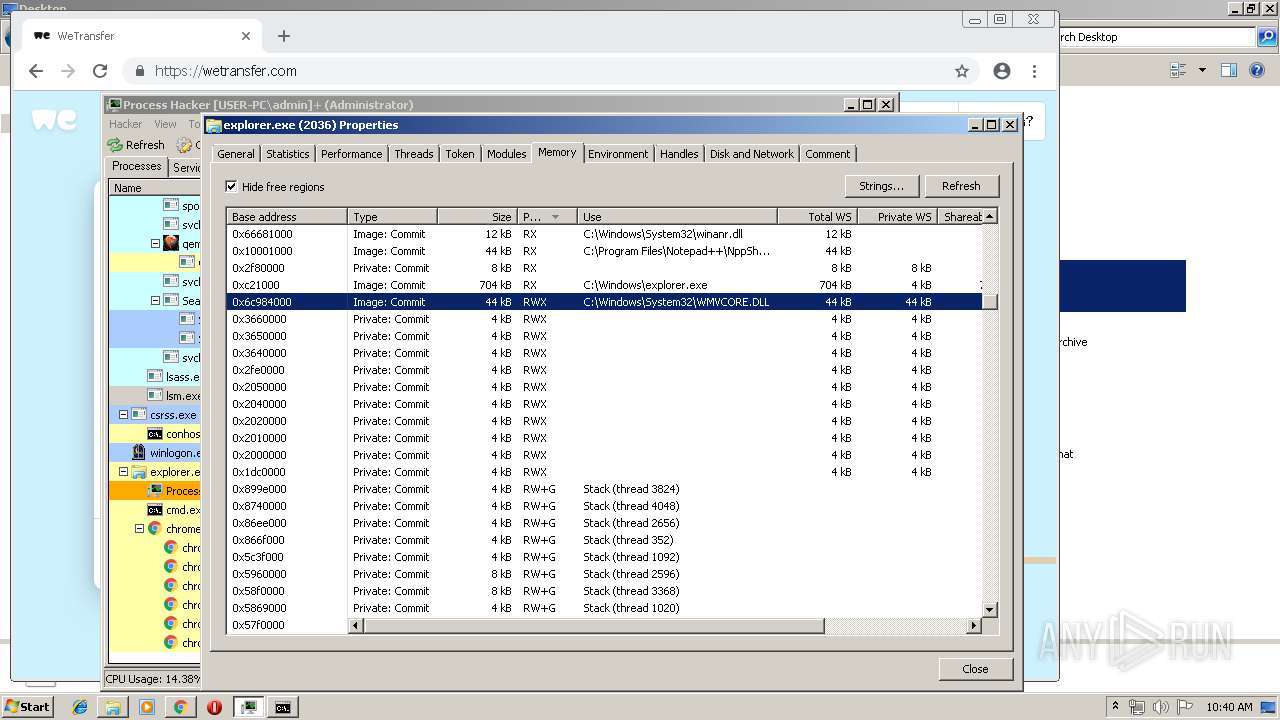
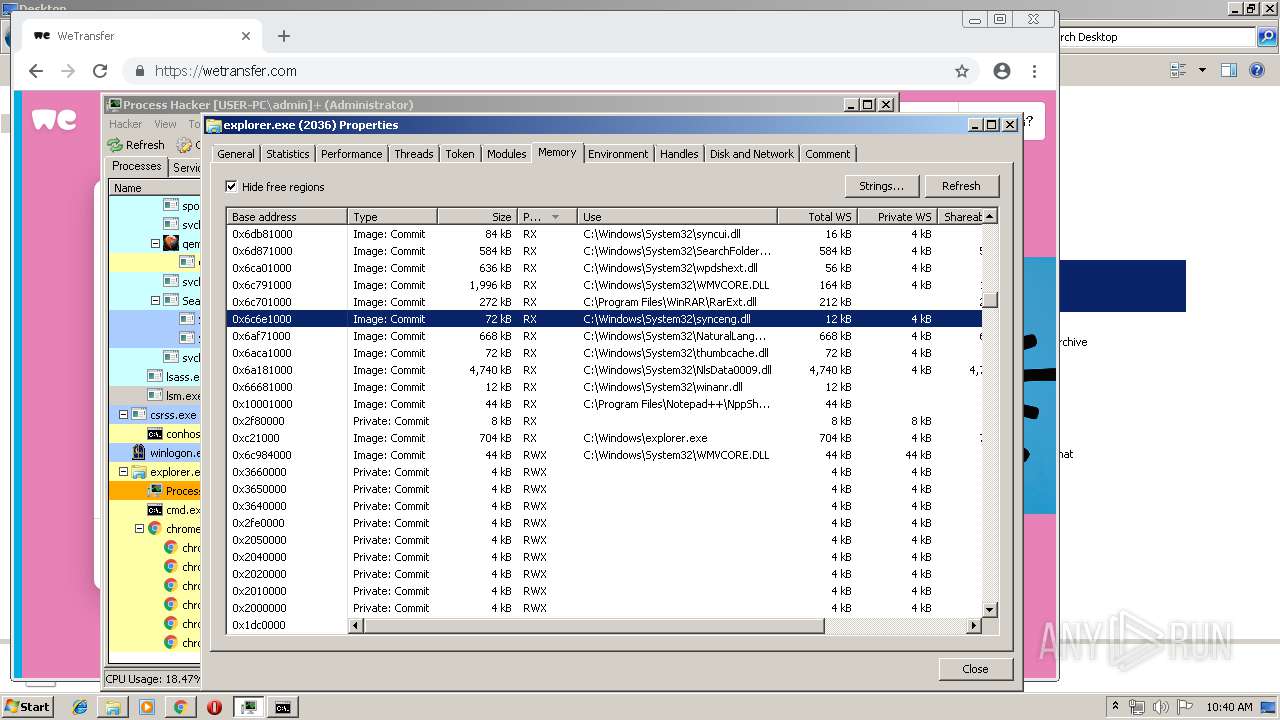
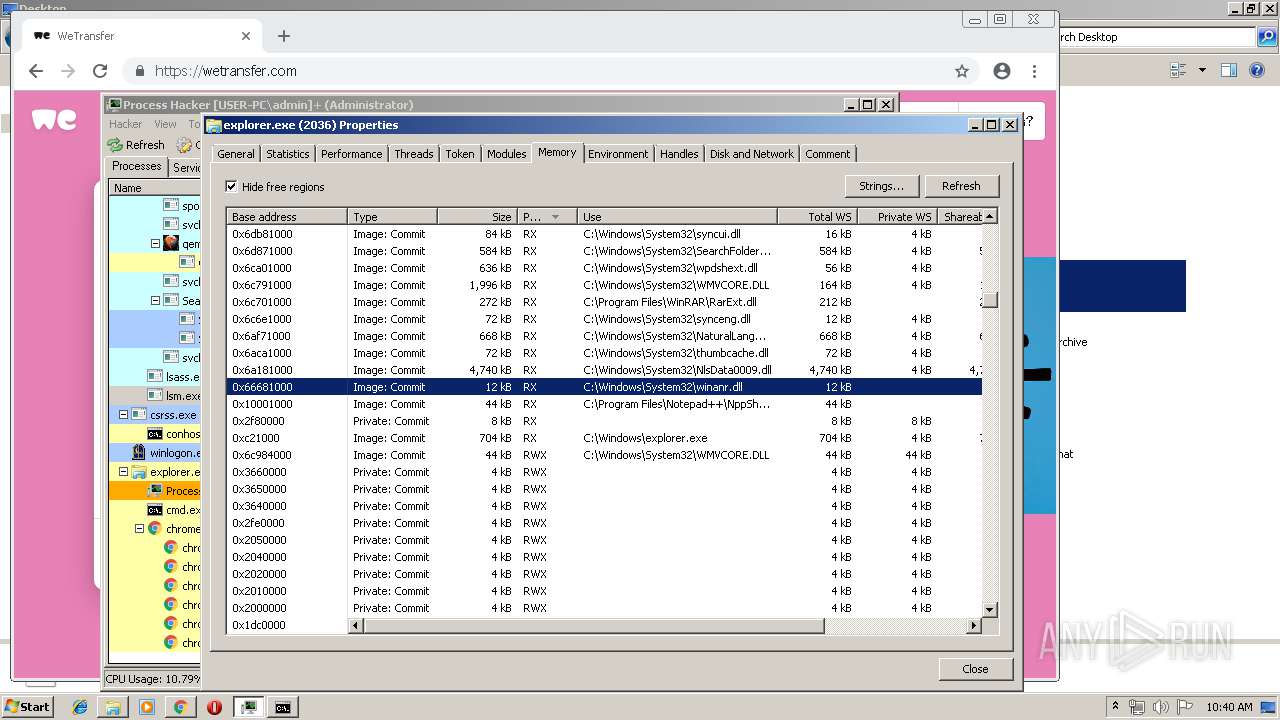
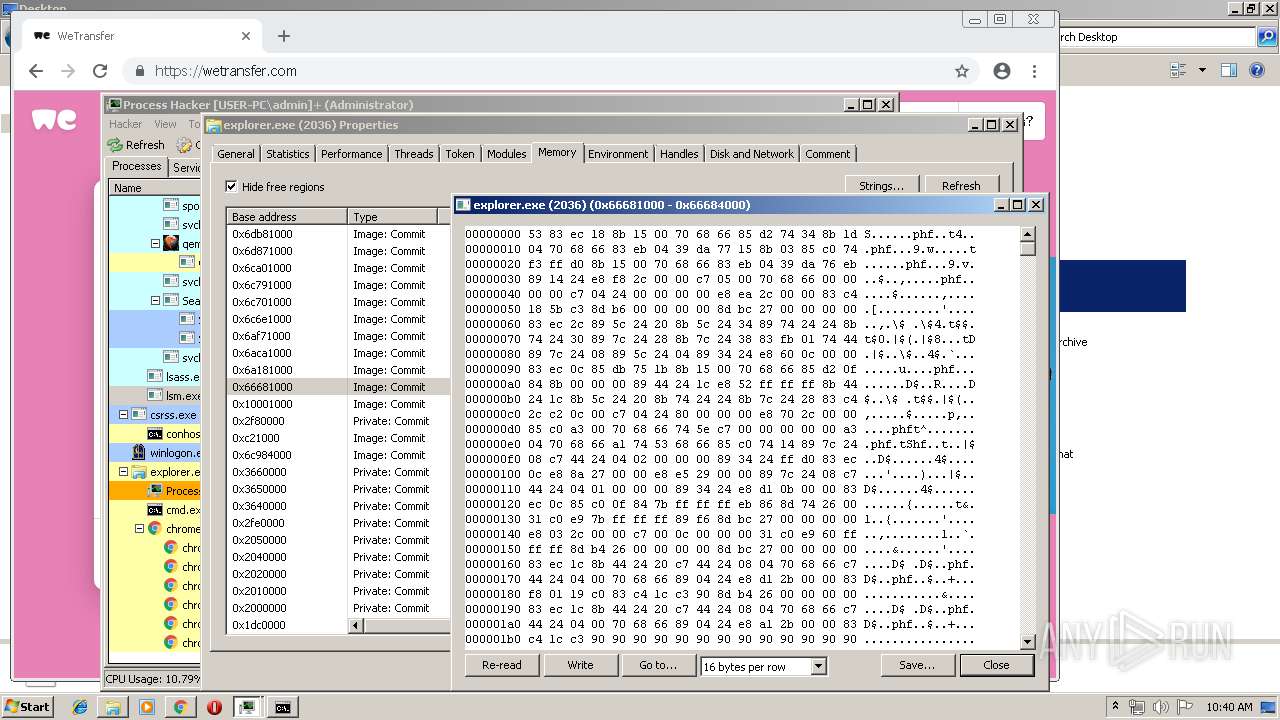
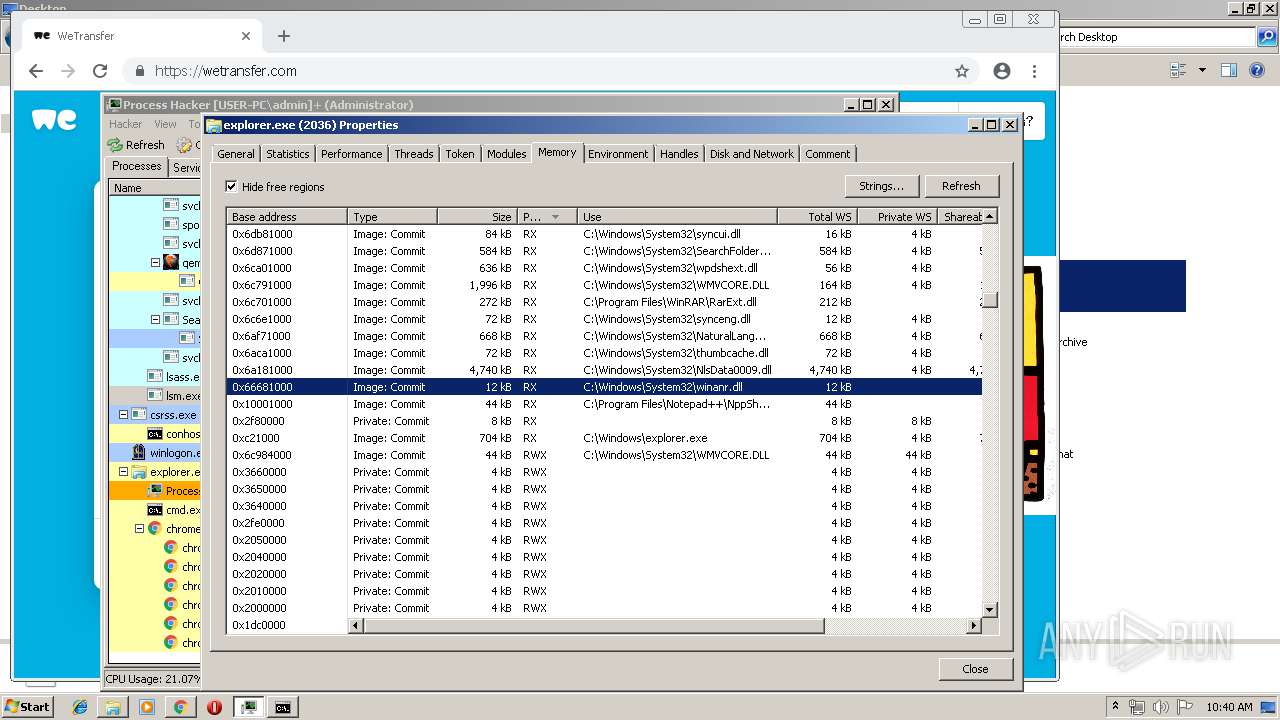
- explorer.exe (PID: 2036)
Application was dropped or rewritten from another process
- ProcessHacker.exe (PID: 1000)
- peview.exe (PID: 1928)
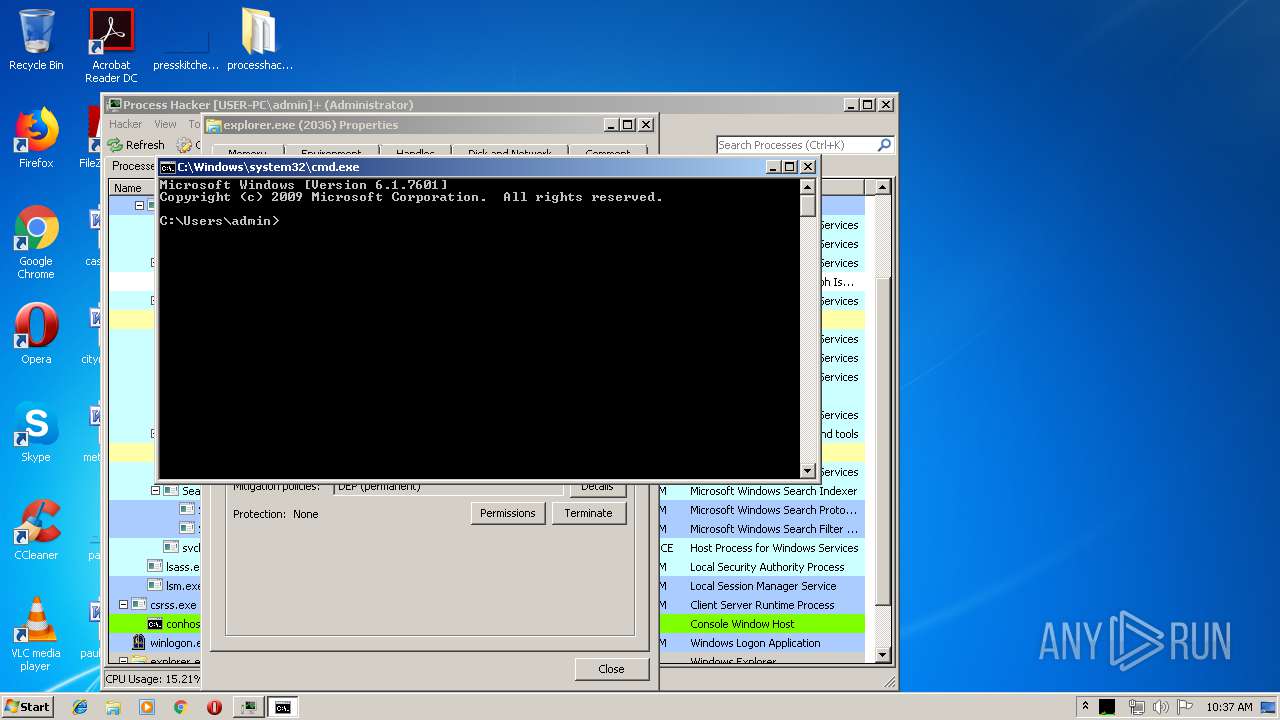
Runs app for hidden code execution
- explorer.exe (PID: 2036)
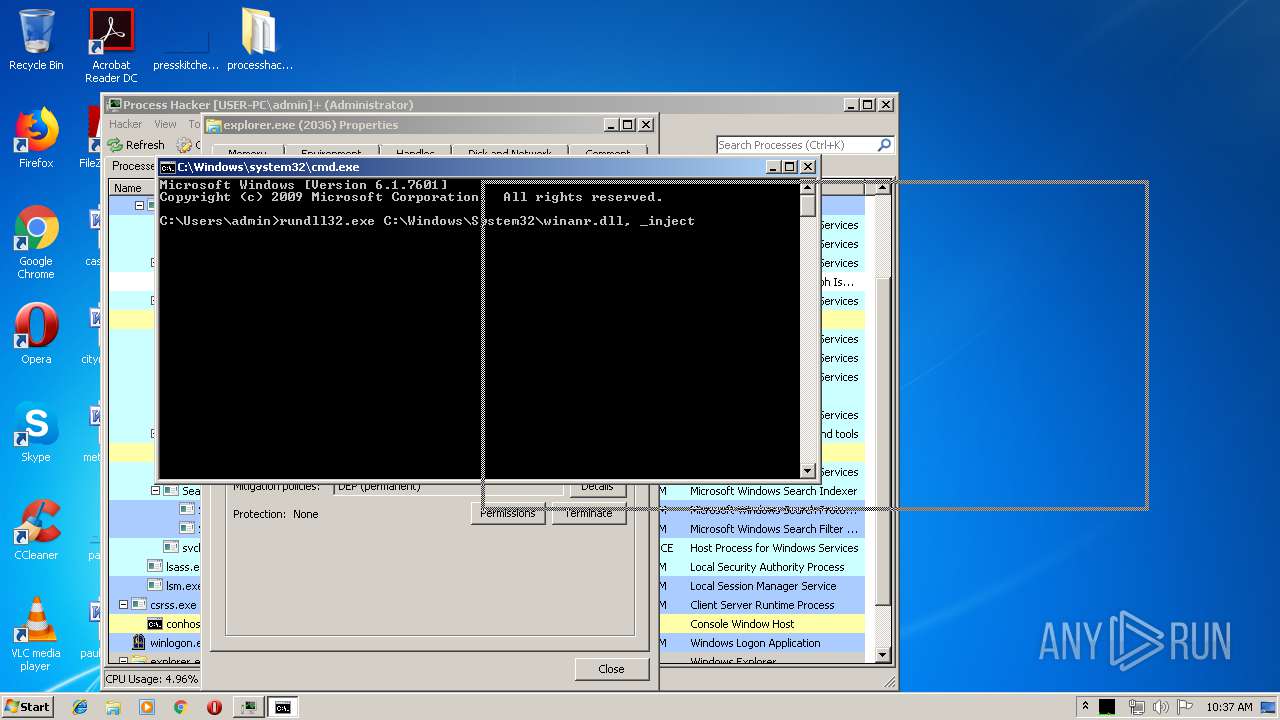
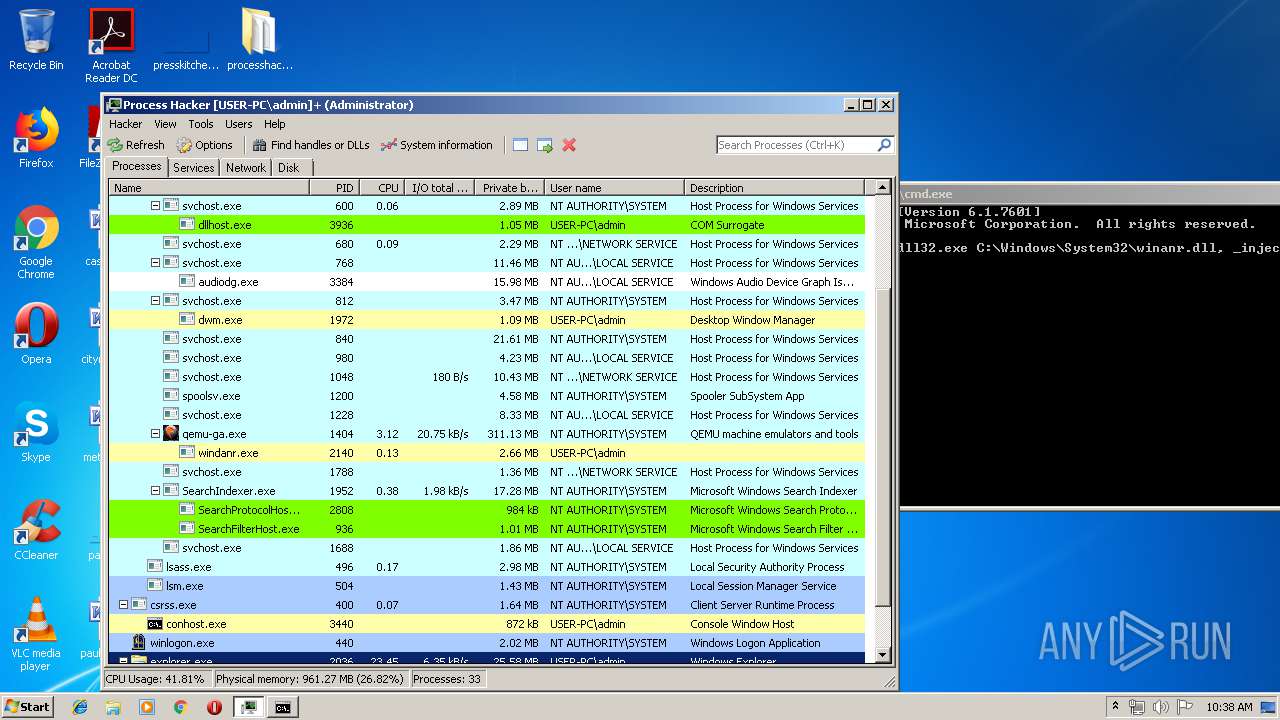
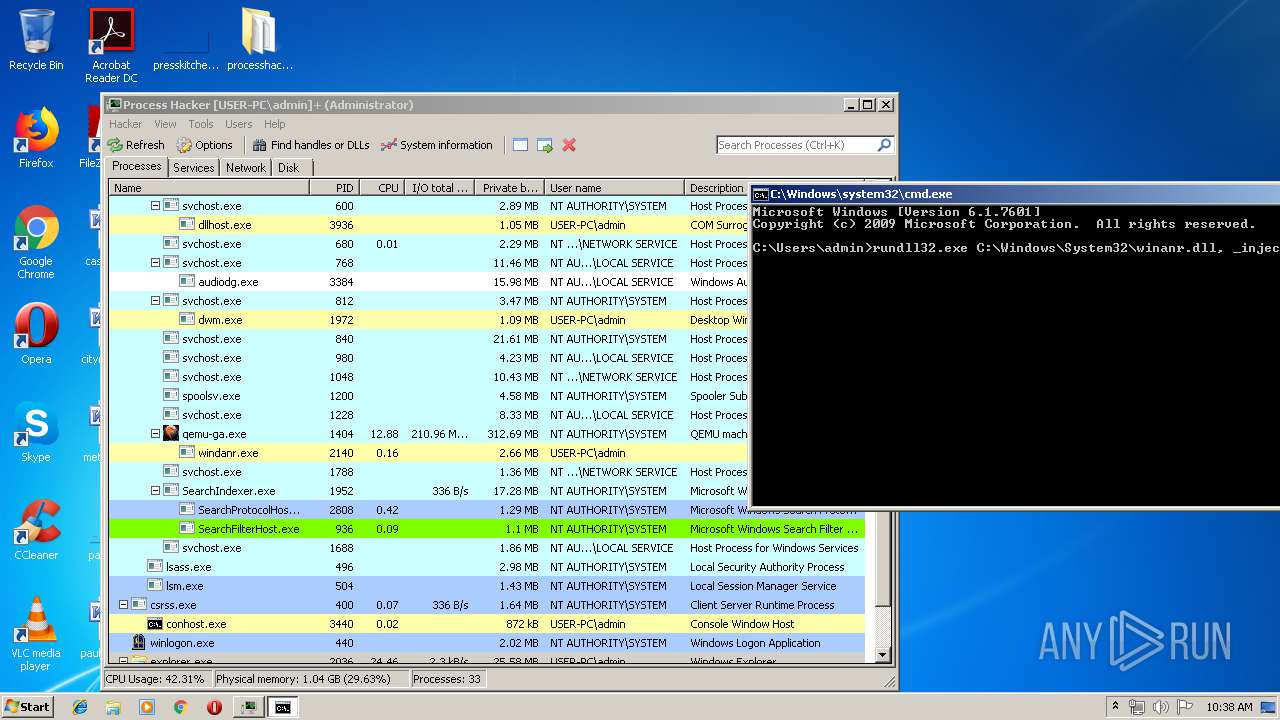
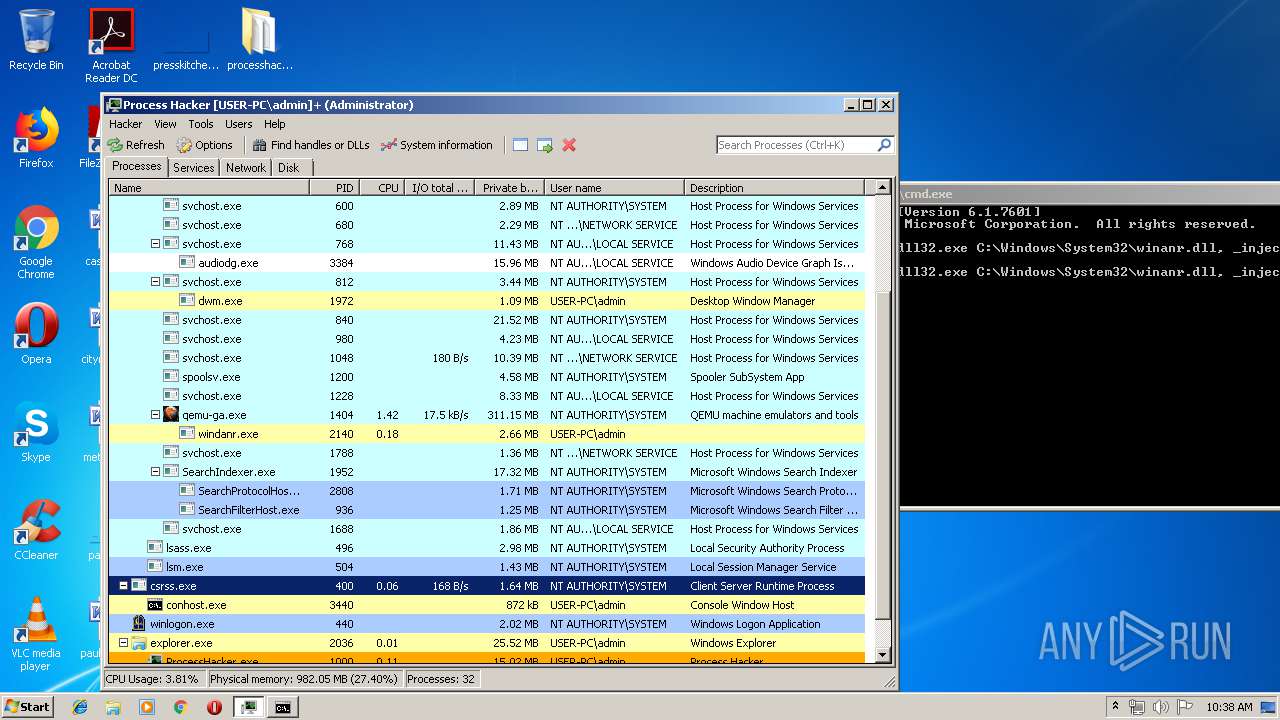
Runs injected code in another process
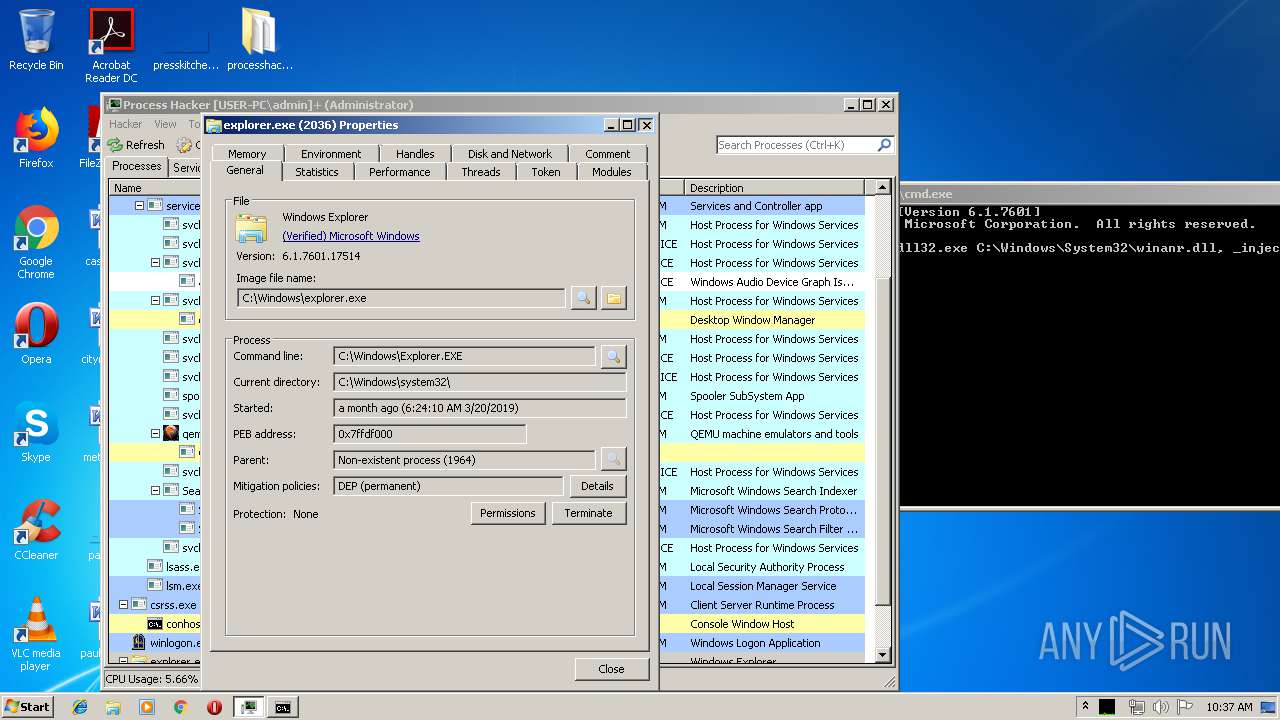
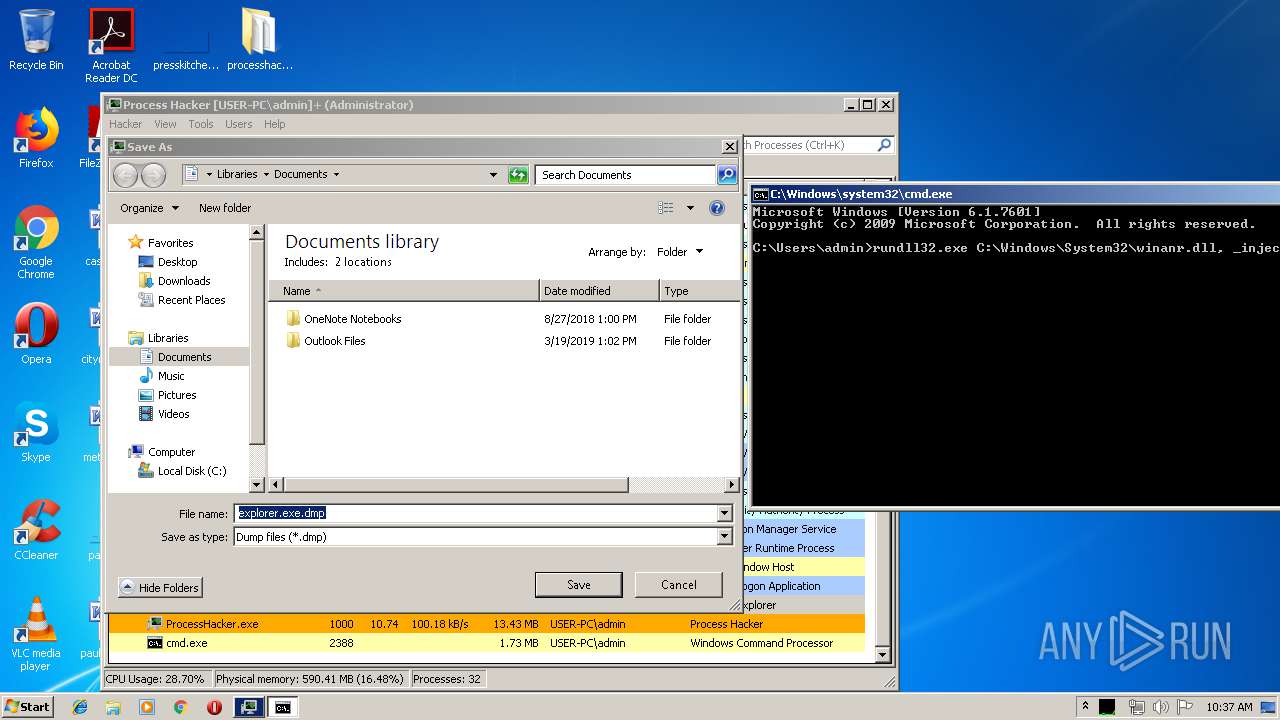
- rundll32.exe (PID: 1476)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2976)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 2036)
Creates files in the user directory
- explorer.exe (PID: 2036)
Reads Internet Cache Settings
- explorer.exe (PID: 2036)
Adds / modifies Windows certificates
- ProcessHacker.exe (PID: 1000)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2856)
Creates executable files which already exist in Windows
- ProcessHacker.exe (PID: 1000)
- explorer.exe (PID: 2036)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 2388)
INFO
Reads settings of System Certificates
- ProcessHacker.exe (PID: 1000)
- chrome.exe (PID: 2856)
Application launched itself
- chrome.exe (PID: 2856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:03:29 12:18:04 |
| ZipCRC: | 0x34beb5ab |
| ZipCompressedSize: | 7294 |
| ZipUncompressedSize: | 25995 |
| ZipFileName: | CHANGELOG.txt |
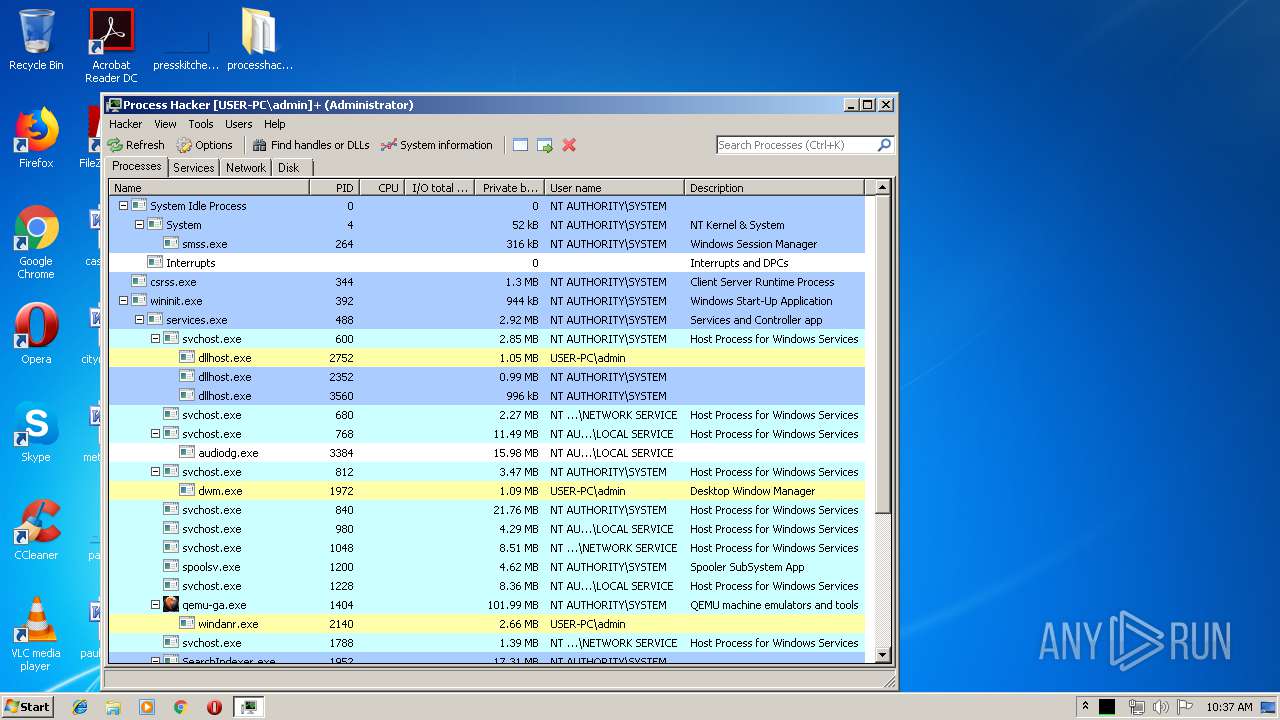
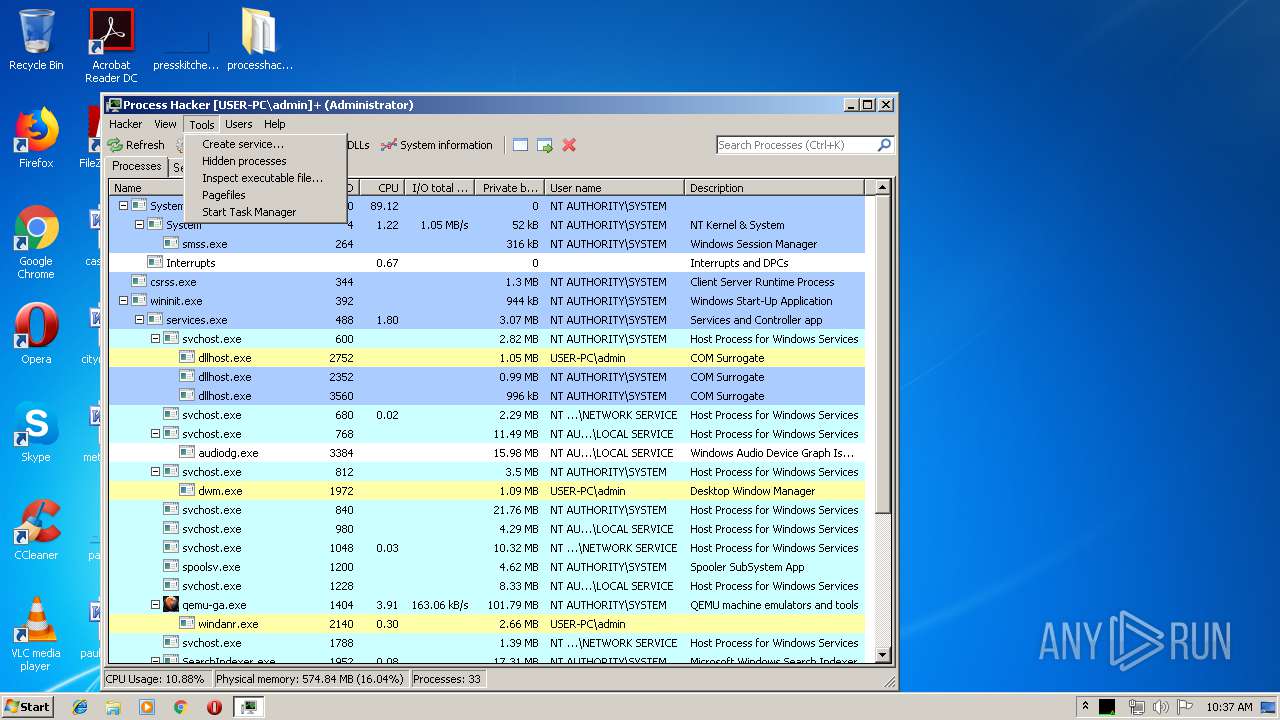
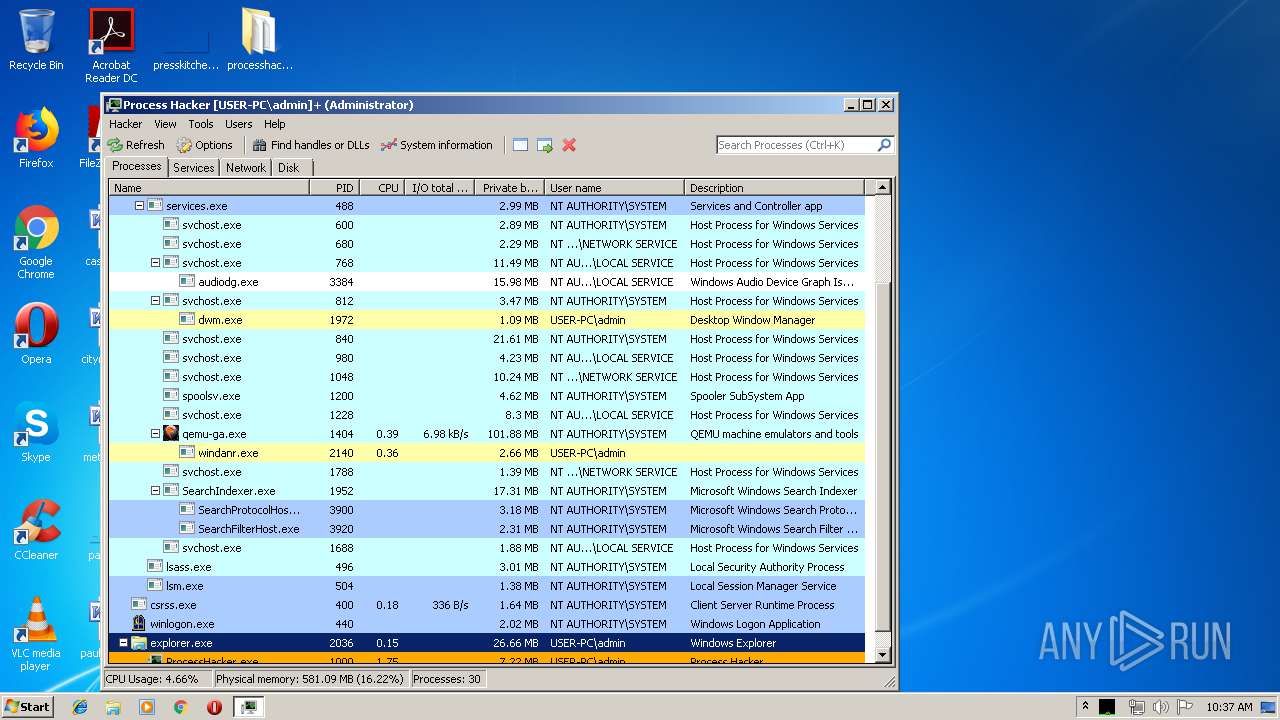
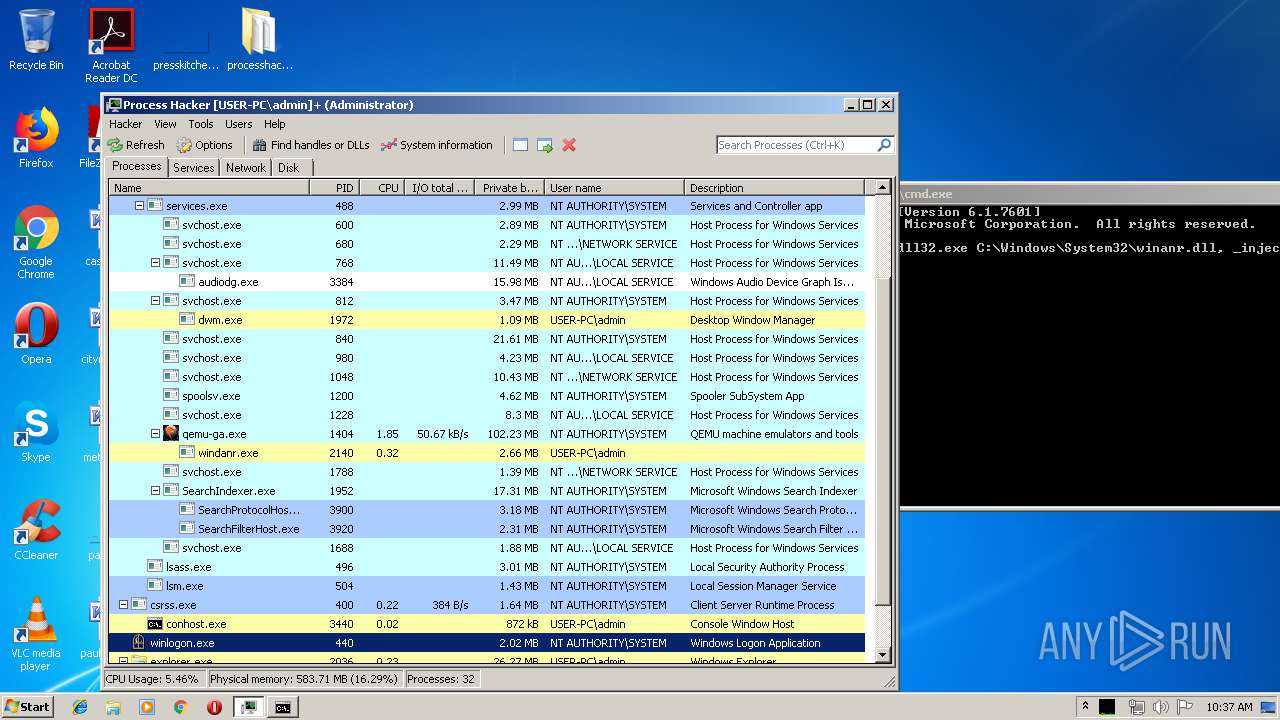
Total processes
76
Monitored processes
33
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
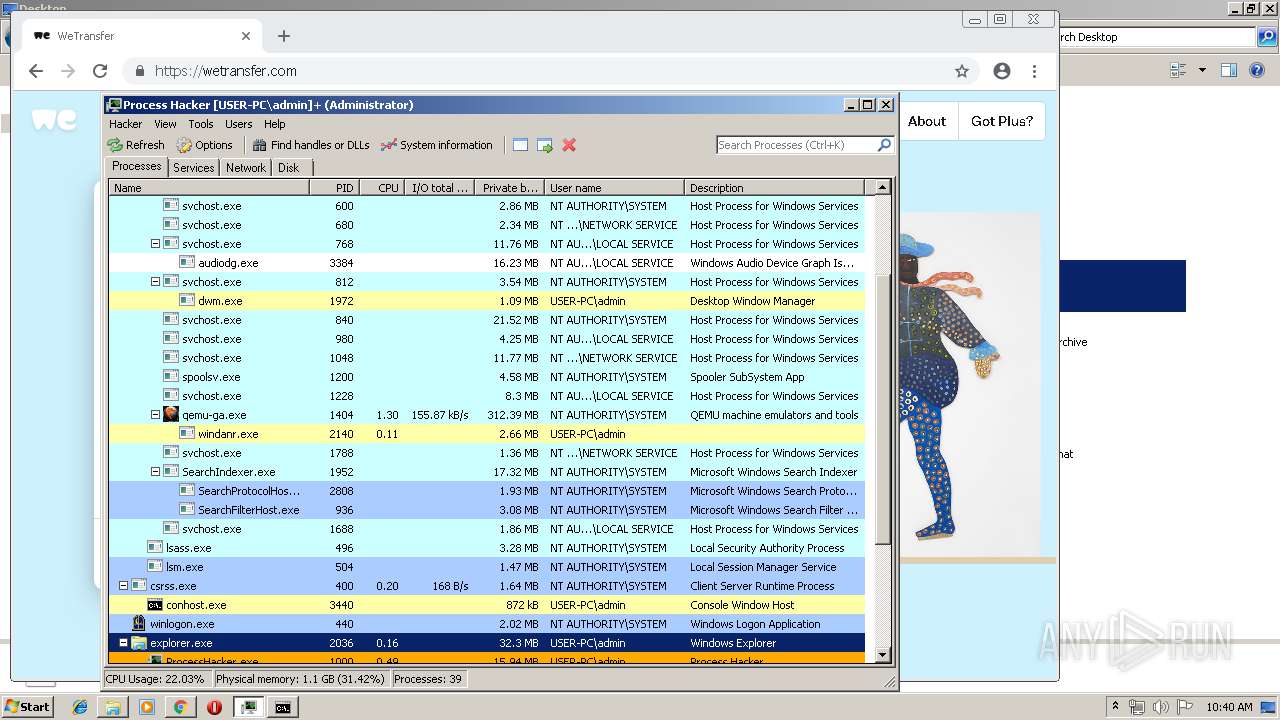
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
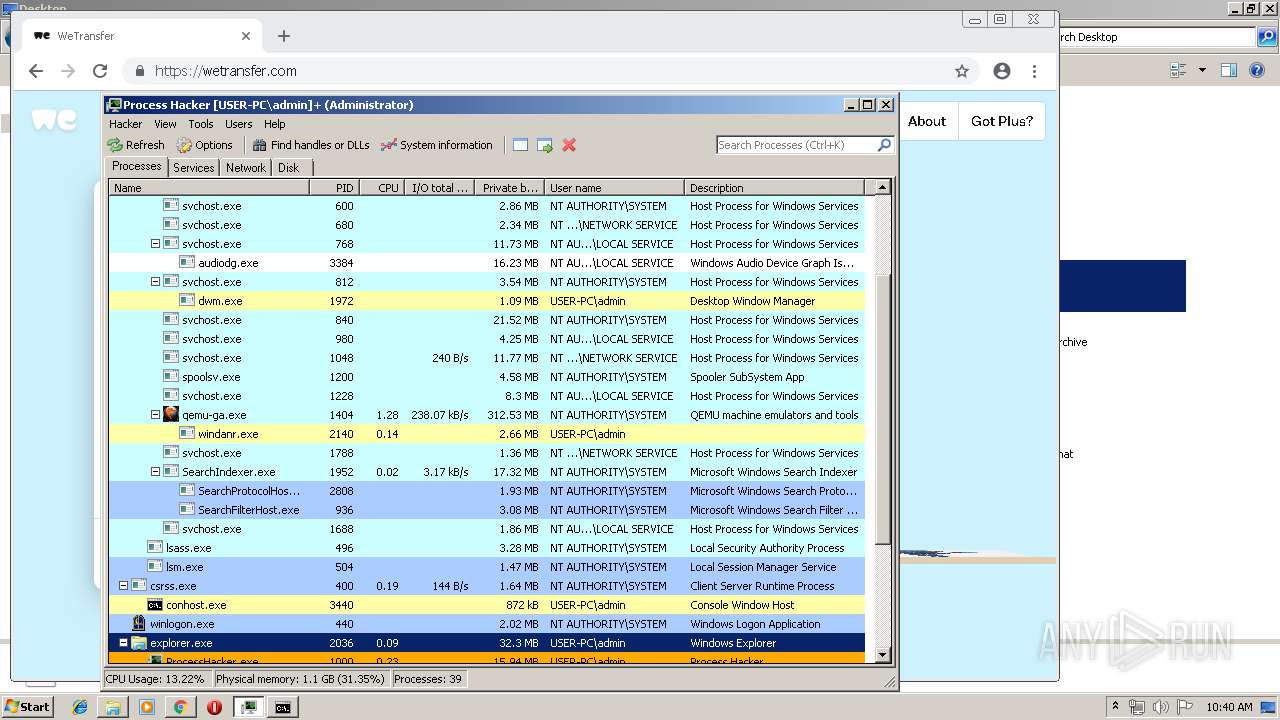
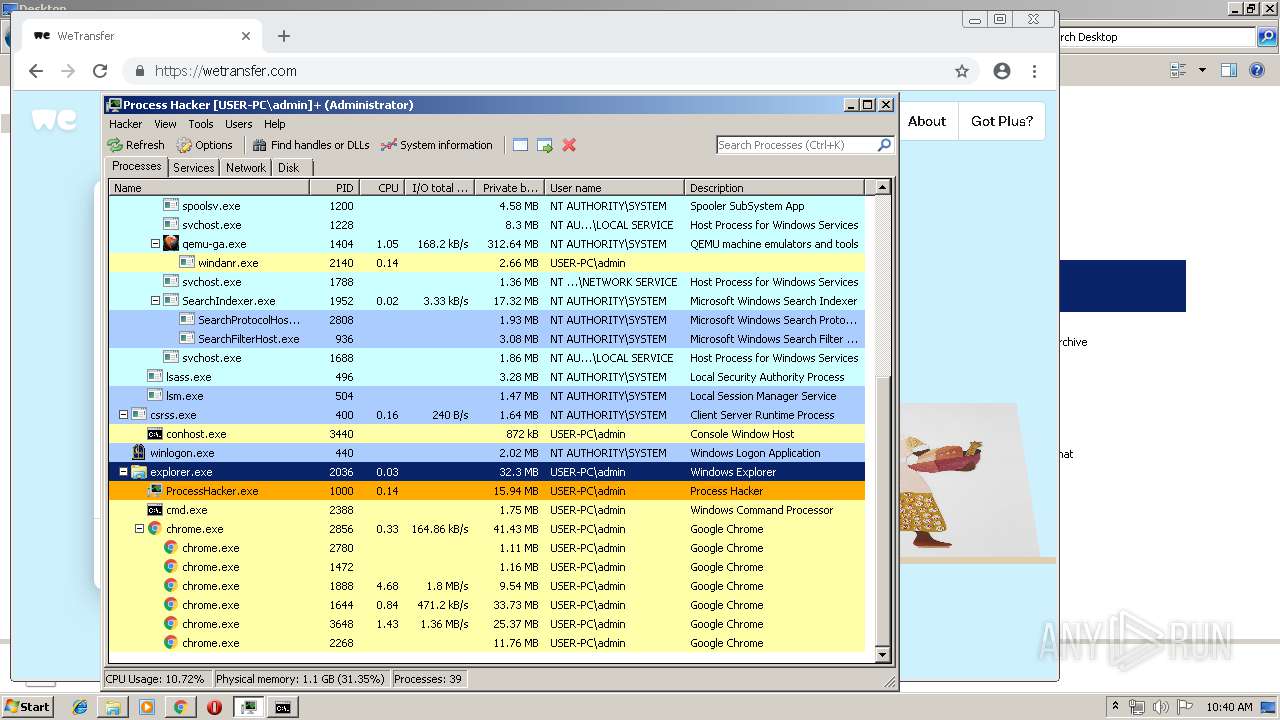
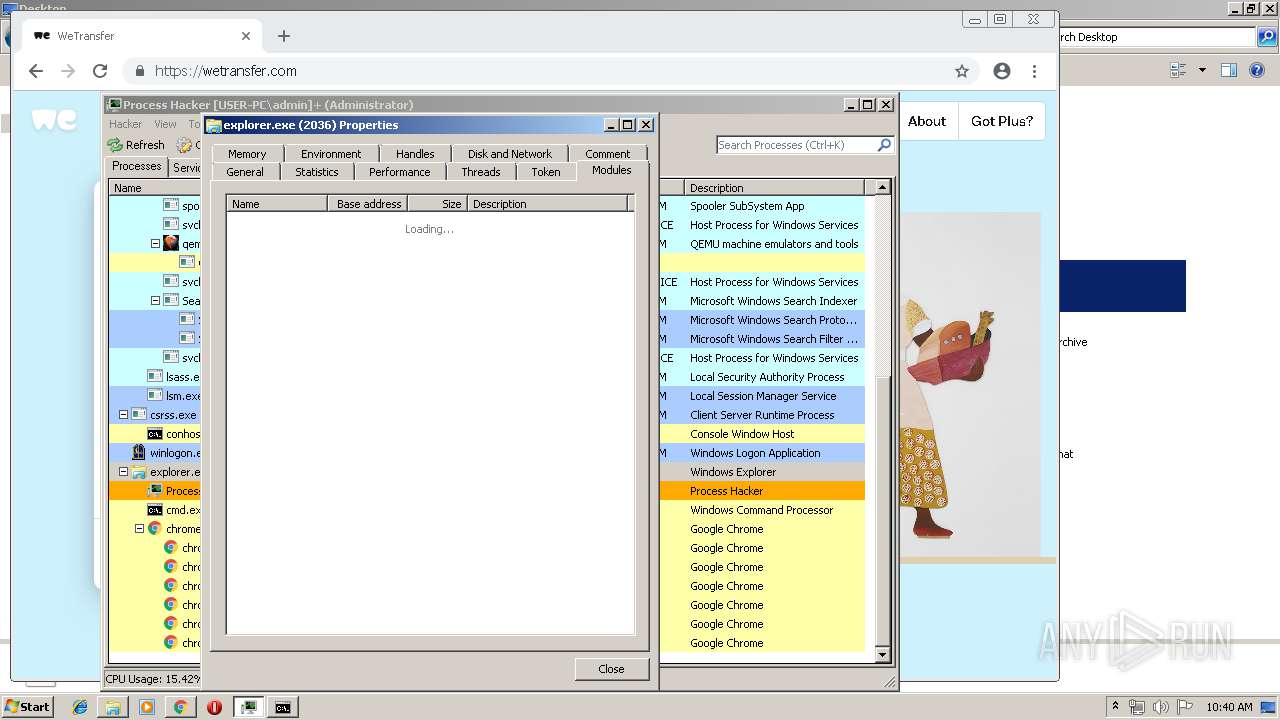
| 1000 | "C:\Users\admin\Desktop\processhacker-2.39-bin\x86\ProcessHacker.exe" | C:\Users\admin\Desktop\processhacker-2.39-bin\x86\ProcessHacker.exe | explorer.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: HIGH Description: Process Hacker Exit code: 0 Version: 2.39.0.124 Modules
| |||||||||||||||
| 1344 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,8808596263185871859,463505187431544779,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15876661237101600206 --mojo-platform-channel-handle=3840 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1472 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=788 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1476 | rundll32.exe C:\Windows\System32\winanr.dll, _inject | C:\Windows\system32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1644 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,8808596263185871859,463505187431544779,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=15961084079874012625 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15961084079874012625 --renderer-client-id=17 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3216 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1888 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=960,8808596263185871859,463505187431544779,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=10161113768632205691 --mojo-platform-channel-handle=952 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1928 | C:\Users\admin\Desktop\processhacker-2.39-bin\x86\peview.exe "C:\ProgramData\Microsoft\Windows\Caches\{DDF571F2-BE98-426D-8288-1A9A39C3FDA2}.2.ver0x0000000000000002.db" | C:\Users\admin\Desktop\processhacker-2.39-bin\x86\peview.exe | — | ProcessHacker.exe | |||||||||||
User: admin Company: wj32 Integrity Level: HIGH Description: PE Viewer Exit code: 0 Version: 2.39.0.123 Modules
| |||||||||||||||
| 2036 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2152 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=960,8808596263185871859,463505187431544779,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=8456175623639356247 --mojo-platform-channel-handle=4248 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2208 | rundll32.exe C:\Windows\System32\winanr.dll, _inject | C:\Windows\system32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
11 965
Read events
10 939
Write events
1 010
Delete events
16
Modification events
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\processhacker-2.39-bin.zip | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (2036) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
Executable files
30
Suspicious files
113
Text files
174
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2976 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\Updater.dll | executable | |
MD5:6976B57C6391F54DBD2828A45CA81100 | SHA256:0C11CDC3765FFB53BA9707B6F99EC17AE4F7334578A935BA7BCBBC9C7BDEED2E | |||
| 2976 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\ExtendedNotifications.dll | executable | |
MD5:BE4DC4D2D1D05001AB0BB2BB8659BFAD | SHA256:61E8CD8DE80A5C0D7CED280FE04AD8387A846A7BF2EE51BCBBA96B971C7C1795 | |||
| 2976 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\OnlineChecks.dll | executable | |
MD5:12C25FB356E51C3FD81D2D422A66BE89 | SHA256:7336D66588BBCFEA63351A2EB7C8D83BBD49B5D959BA56A94B1FE2E905A5B5DE | |||
| 2976 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\ToolStatus.dll | executable | |
MD5:3788EFFF135F8B17A179D02334D505E6 | SHA256:5713D40DEC146DBC819230DAEFE1B886FA6D6F6DBD619301BB8899562195CBAB | |||
| 2976 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\README.txt | text | |
MD5:72AC5A8DD6491E525B9783C9BC439FE6 | SHA256:0C4F051675A690EA4DB6AB2EB81FDCED6990E2538AD21DC4610AA5925253A090 | |||
| 2976 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\SbieSupport.dll | executable | |
MD5:37CBFA73883E7E361D3FA67C16D0F003 | SHA256:57C56F7B312DC1F759E6AD039AAC3F36CE5130D259EB9FAAD77239083398308B | |||
| 2976 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\peview.exe | executable | |
MD5:DDE1F44789CD50C1F034042D337DEAE3 | SHA256:4259E53D48A3FED947F561FF04C7F94446BEDD64C87F52400B2CB47A77666AAA | |||
| 2976 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\kprocesshacker.sys | executable | |
MD5:1B5C3C458E31BEDE55145D0644E88D75 | SHA256:70211A3F90376BBC61F49C22A63075D1D4DDD53F0AEFA976216C46E6BA39A9F4 | |||
| 2976 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\LICENSE.txt | text | |
MD5:EB59E0A5D01D0A5B02DA0C9E7786969F | SHA256:C38E811F6F83428921D0CECD998A44B717149B577B4C1A63B66064F03C34E4E7 | |||
| 2976 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\DotNetTools.dll | executable | |
MD5:B16CE8BA8E7F0EE83EC1D49F2D0AF0A7 | SHA256:B4CC0280E2CAA0335361172CB7D673F745DEFC78299DED808426FFBC2458E4D9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
53
DNS requests
44
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2856 | chrome.exe | GET | 200 | 172.217.130.73:80 | http://r4---sn-2gb7sn7r.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=185.76.9.72&mm=28&mn=sn-2gb7sn7r&ms=nvh&mt=1556184733&mv=u&pl=25&shardbypass=yes | US | crx | 842 Kb | whitelisted |
2856 | chrome.exe | GET | 302 | 172.217.22.78:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 502 b | whitelisted |
2856 | chrome.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.6 Kb | whitelisted |
2856 | chrome.exe | GET | 200 | 52.85.182.64:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1000 | ProcessHacker.exe | 162.243.25.33:443 | wj32.org | Digital Ocean, Inc. | US | suspicious |
2856 | chrome.exe | 172.217.16.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2856 | chrome.exe | 172.217.23.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
2856 | chrome.exe | 216.58.208.35:443 | www.google.com.ua | Google Inc. | US | whitelisted |
2856 | chrome.exe | 172.217.22.14:443 | clients1.google.com | Google Inc. | US | whitelisted |
2856 | chrome.exe | 172.217.22.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2856 | chrome.exe | 172.217.130.73:80 | r4---sn-2gb7sn7r.gvt1.com | Google Inc. | US | whitelisted |
2856 | chrome.exe | 172.217.16.132:443 | www.google.com | Google Inc. | US | whitelisted |
2856 | chrome.exe | 172.217.23.131:443 | www.google.se | Google Inc. | US | whitelisted |
2856 | chrome.exe | 172.217.22.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wj32.org |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
accounts.google.com |
| shared |
clients1.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
redirector.gvt1.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2856 | chrome.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
2856 | chrome.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |