analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
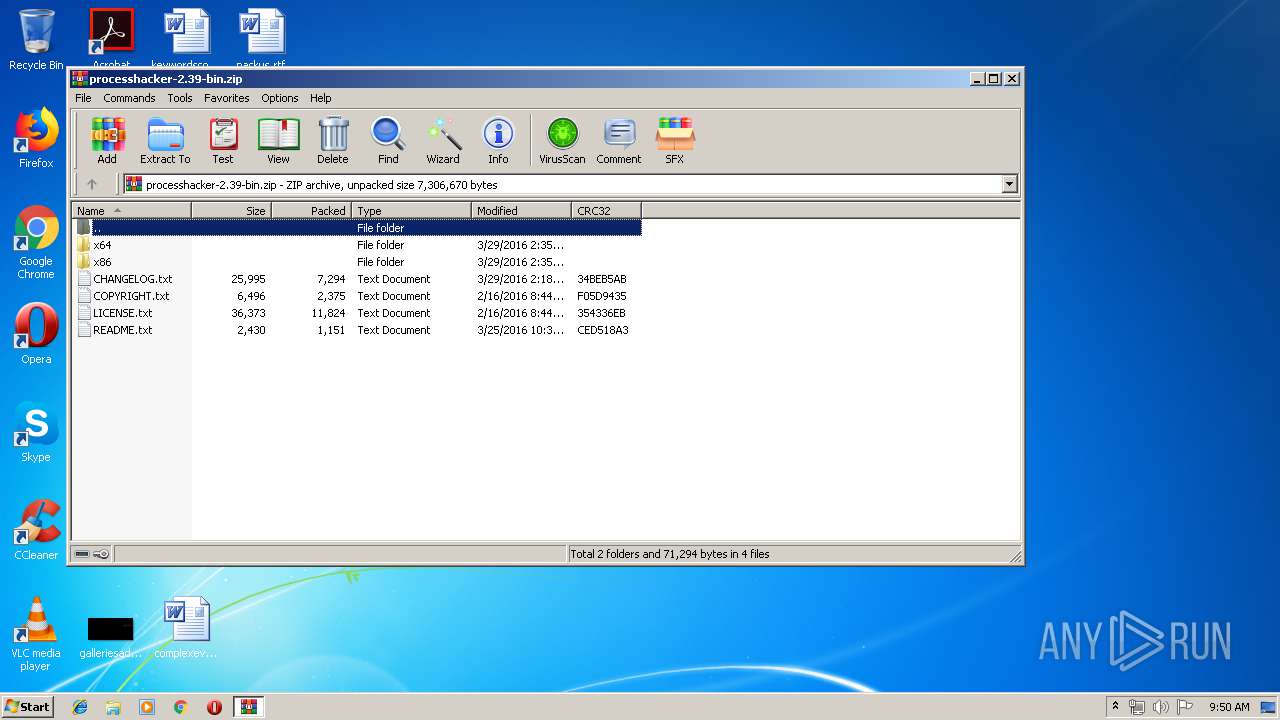
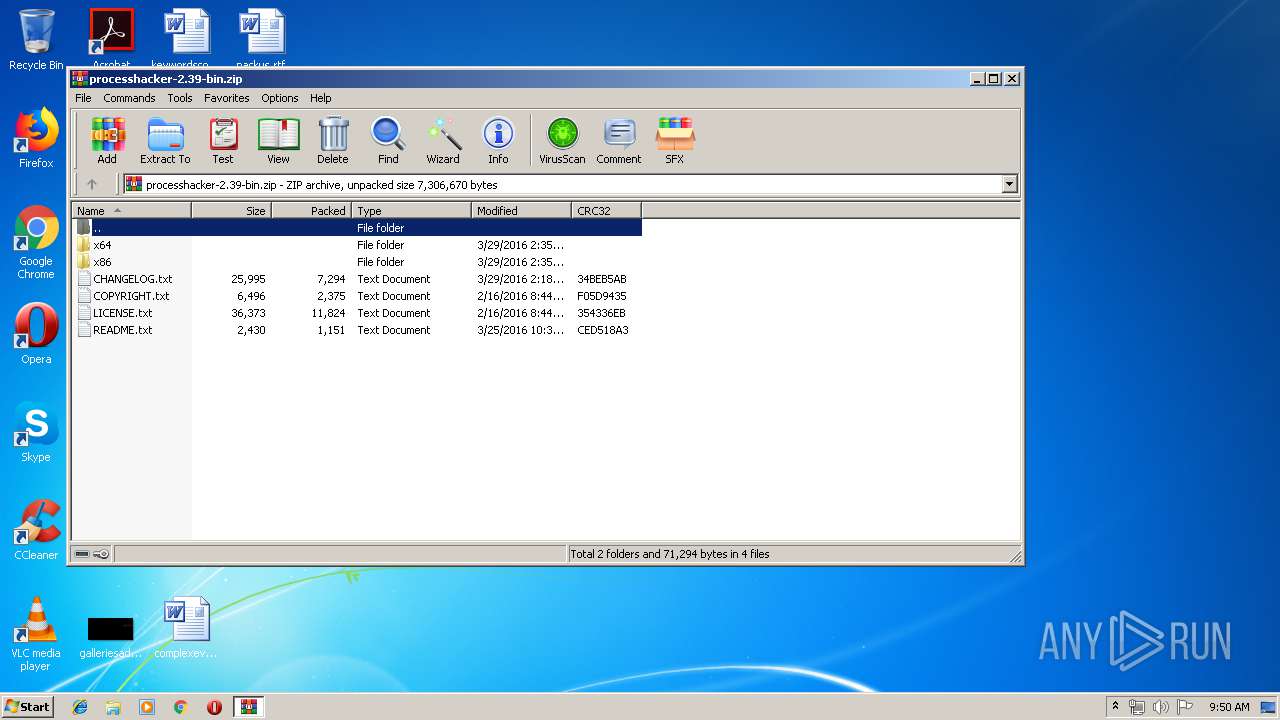
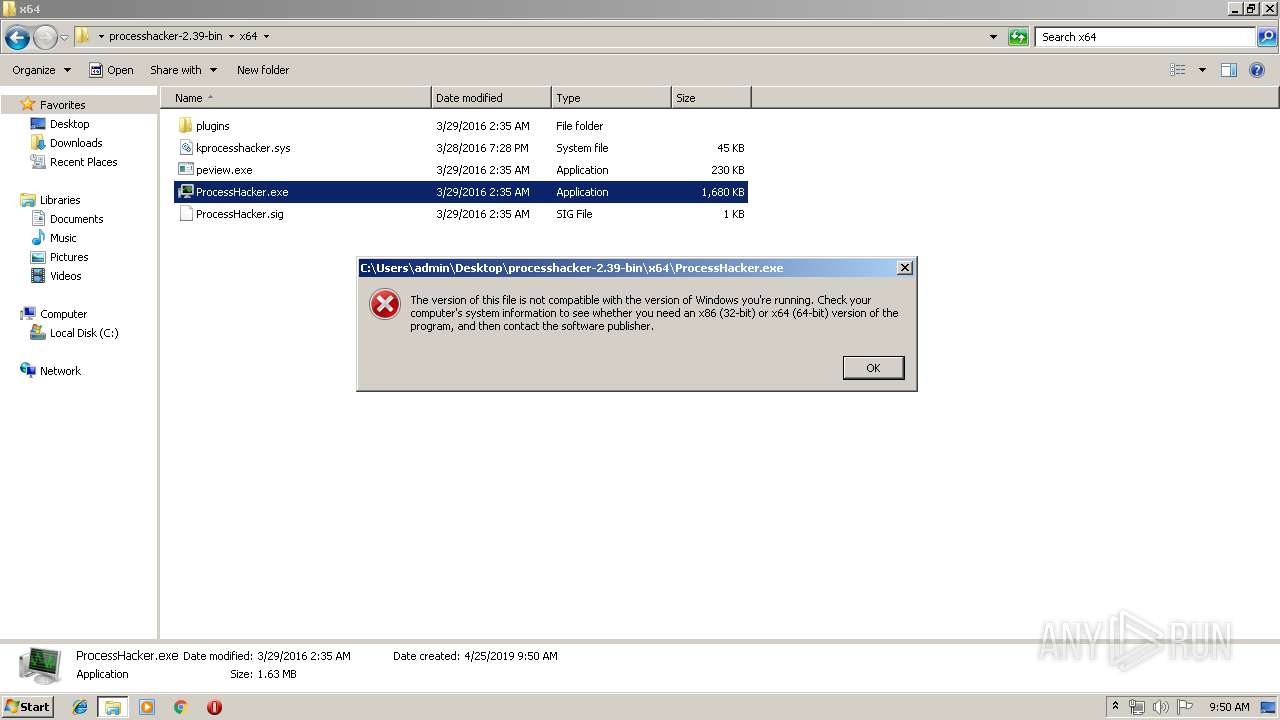
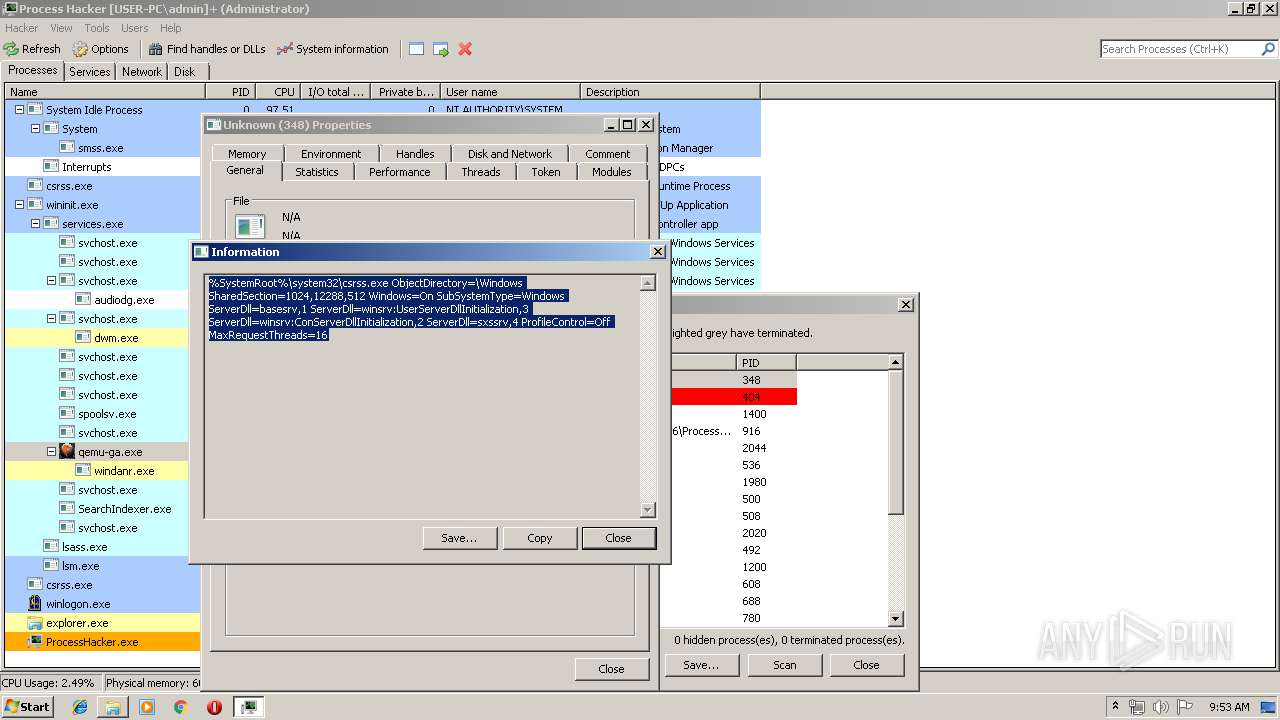
| File name: | processhacker-2.39-bin.zip |
| Full analysis: | https://app.any.run/tasks/2a29031f-cce9-47e5-8279-198fe57d23e5 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 08:49:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B444CF14642CE9B8D75E079166A5DF0B |
| SHA1: | 8E8F8423D163D922242B8B7D85427664F77EDC97 |
| SHA256: | 2AFB5303E191DDE688C5626C3EE545E32E52F09DA3B35B20F5E0D29A418432F5 |
| SSDEEP: | 98304:jDqt5TrOmlLB/7rTOqcXfOzJR1qioDLK2EbhQ:3sTrHlB73OqX4ioDfshQ |
MALICIOUS
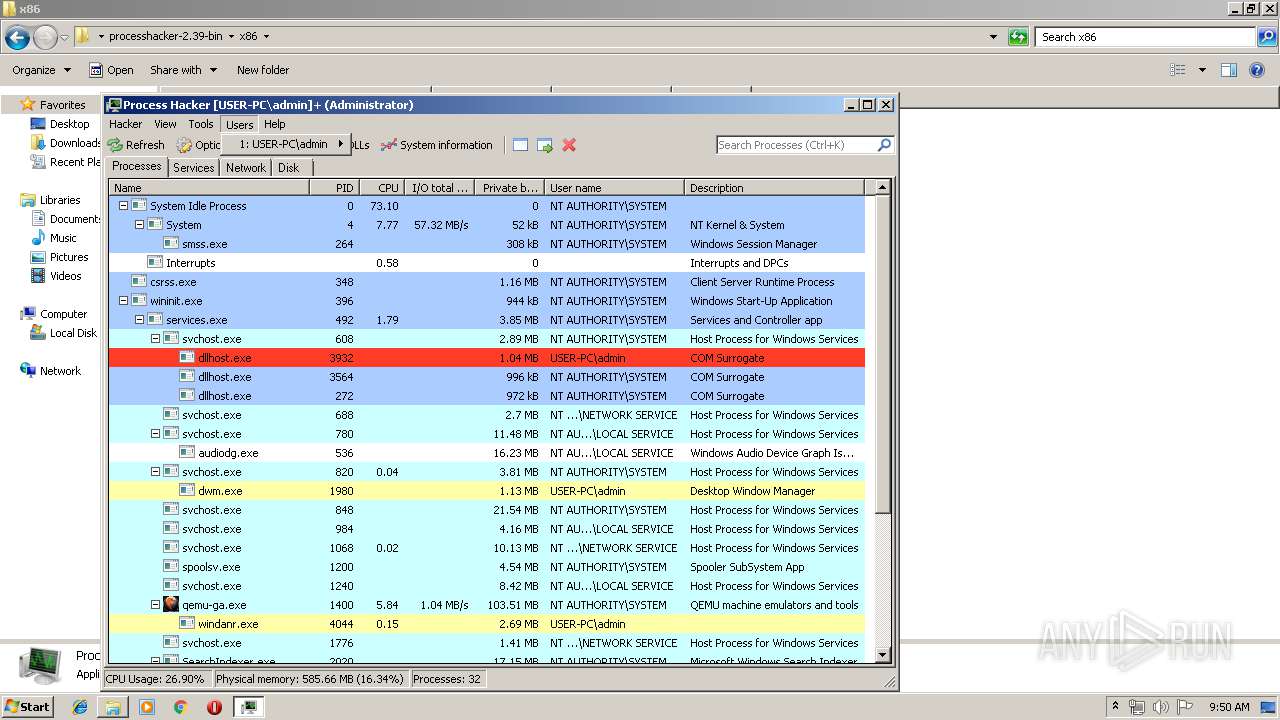
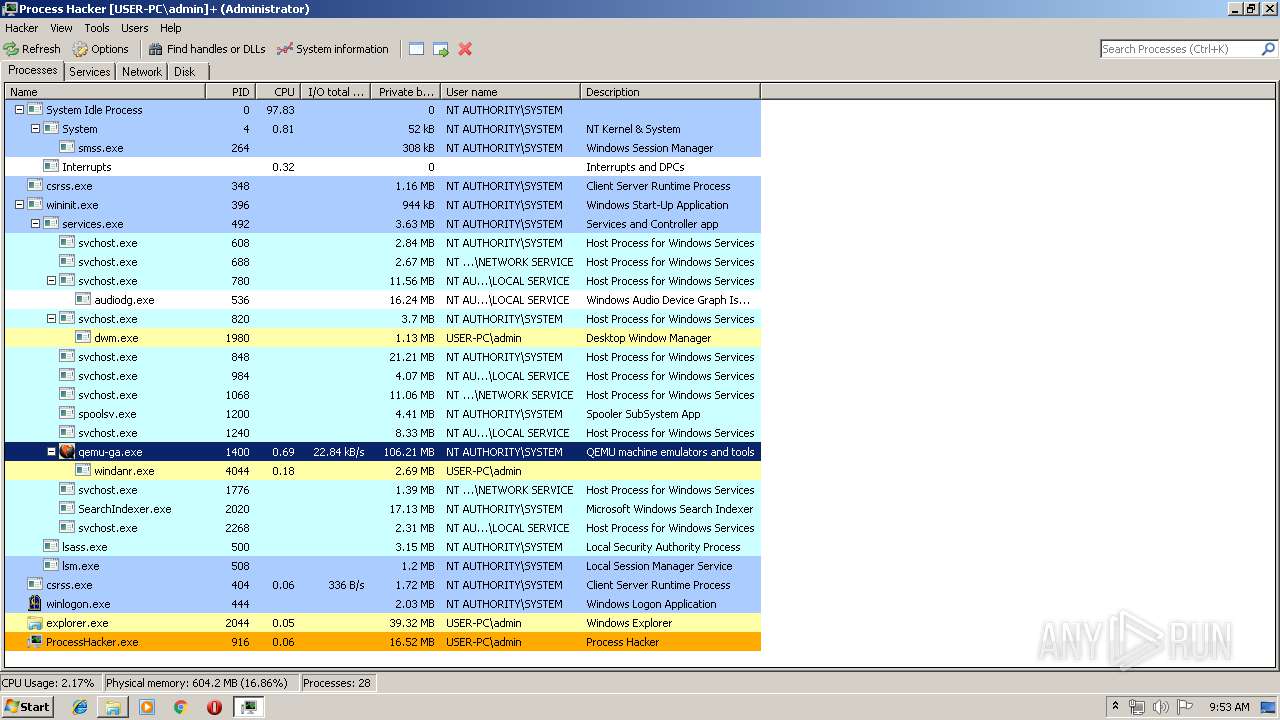
Application was dropped or rewritten from another process
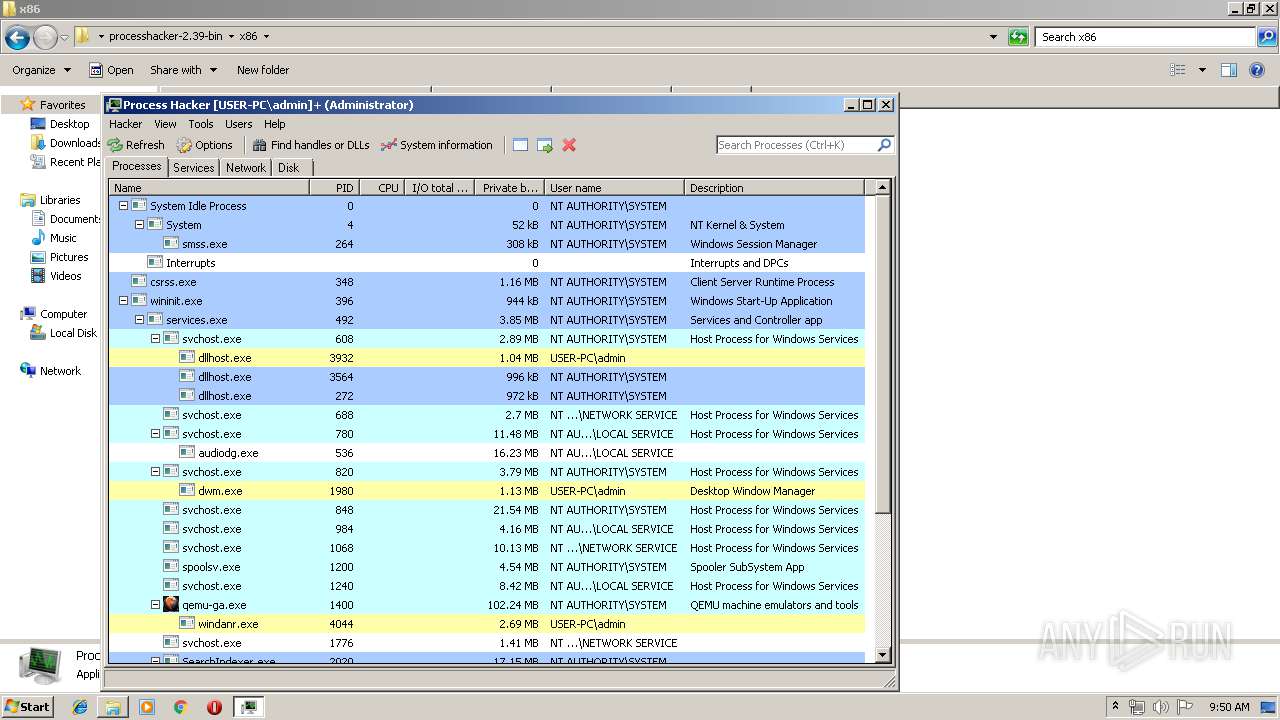
- ProcessHacker.exe (PID: 916)
- ProcessHacker.exe (PID: 2480)
Loads dropped or rewritten executable
- ProcessHacker.exe (PID: 2480)
- SearchProtocolHost.exe (PID: 3224)
- ProcessHacker.exe (PID: 916)
Changes settings of System certificates
- ProcessHacker.exe (PID: 916)
SUSPICIOUS
Application launched itself
- ProcessHacker.exe (PID: 2480)
Creates files in the user directory
- ProcessHacker.exe (PID: 2480)
- notepad++.exe (PID: 3568)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2052)
Adds / modifies Windows certificates
- ProcessHacker.exe (PID: 916)
INFO
Reads settings of System Certificates
- chrome.exe (PID: 2812)
- ProcessHacker.exe (PID: 916)
Application launched itself
- chrome.exe (PID: 2812)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:03:29 12:18:04 |
| ZipCRC: | 0x34beb5ab |
| ZipCompressedSize: | 7294 |
| ZipUncompressedSize: | 25995 |
| ZipFileName: | CHANGELOG.txt |
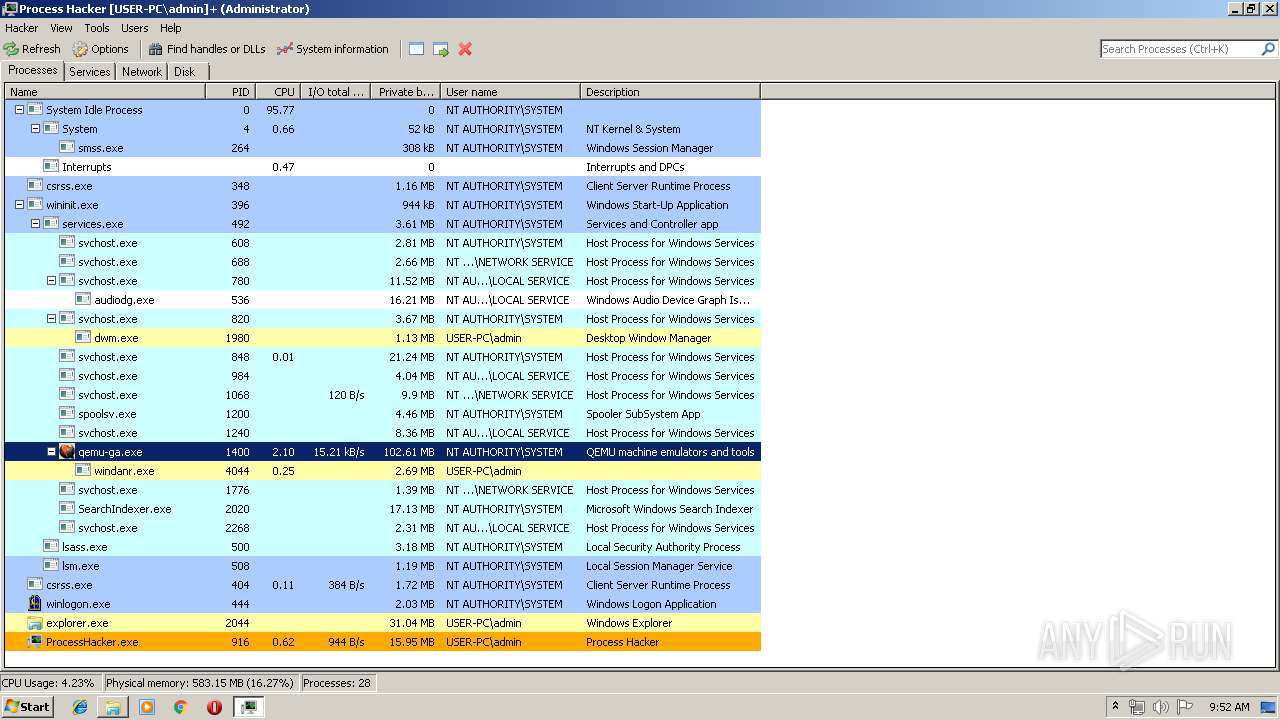
Total processes
65
Monitored processes
24
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2052 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\processhacker-2.39-bin.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 | ||||
| 3224 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) | ||||
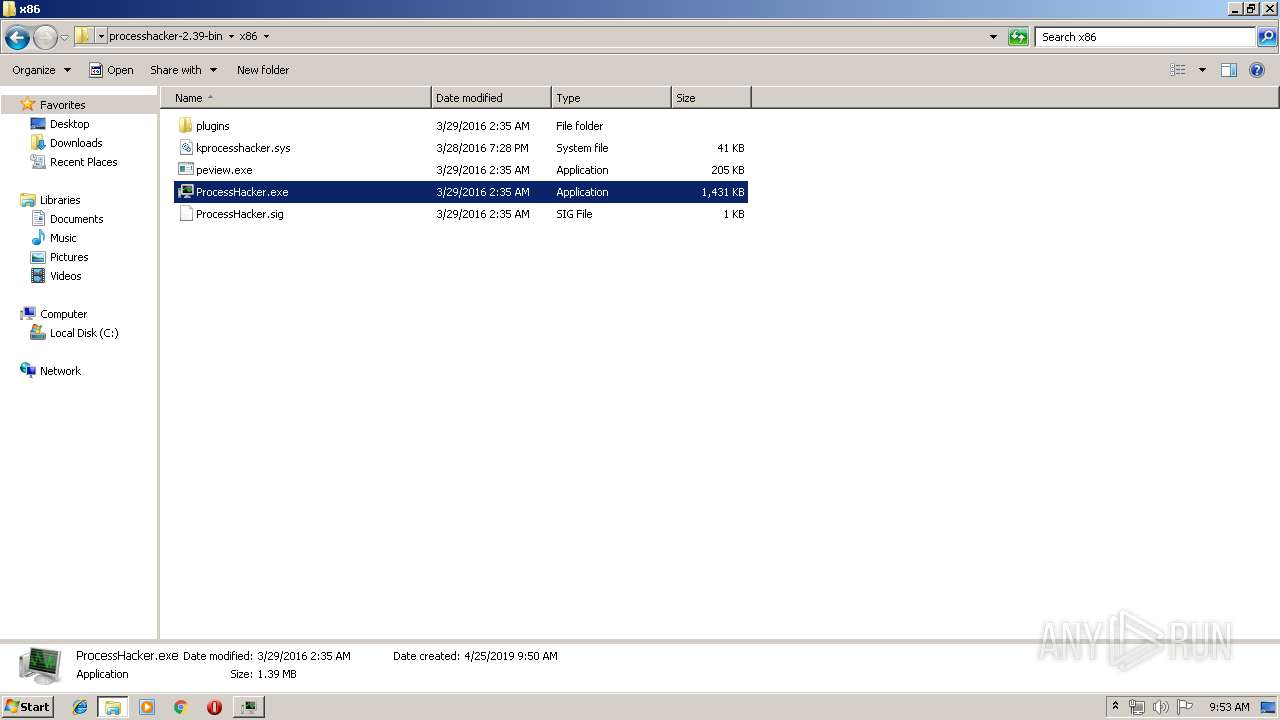
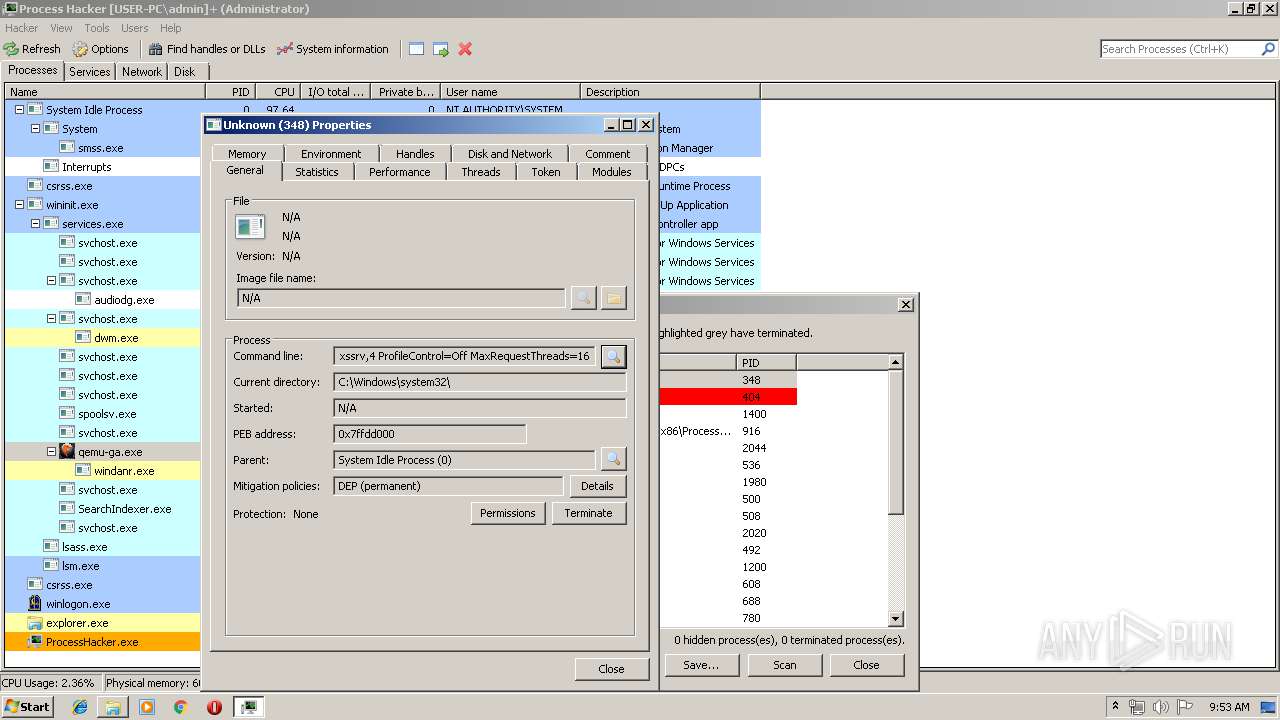
| 2480 | "C:\Users\admin\Desktop\processhacker-2.39-bin\x86\ProcessHacker.exe" | C:\Users\admin\Desktop\processhacker-2.39-bin\x86\ProcessHacker.exe | explorer.exe | |
User: admin Company: wj32 Integrity Level: MEDIUM Description: Process Hacker Exit code: 0 Version: 2.39.0.124 | ||||
| 916 | "C:\Users\admin\Desktop\processhacker-2.39-bin\x86\ProcessHacker.exe" -v | C:\Users\admin\Desktop\processhacker-2.39-bin\x86\ProcessHacker.exe | ProcessHacker.exe | |
User: admin Company: wj32 Integrity Level: HIGH Description: Process Hacker Version: 2.39.0.124 | ||||
| 2812 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | |
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 73.0.3683.75 | ||||
| 3560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=73.0.3683.75 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6d850f18,0x6d850f28,0x6d850f34 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 | ||||
| 588 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2220 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 | ||||
| 3180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=980,11724036674344745164,15824269247204196827,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=14349820158884791533 --mojo-platform-channel-handle=1028 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 | ||||
| 1060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=980,11724036674344745164,15824269247204196827,131072 --enable-features=PasswordImport --service-pipe-token=16918110969818351033 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16918110969818351033 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1964 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 | ||||
| 3980 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=980,11724036674344745164,15824269247204196827,131072 --enable-features=PasswordImport --service-pipe-token=18296787436934961883 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=18296787436934961883 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2204 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 | ||||
Total events
2 493
Read events
2 201
Write events
0
Delete events
0
Modification events
Executable files
30
Suspicious files
68
Text files
148
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2052 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\LICENSE.txt | text | |
MD5:EB59E0A5D01D0A5B02DA0C9E7786969F | SHA256:C38E811F6F83428921D0CECD998A44B717149B577B4C1A63B66064F03C34E4E7 | |||
| 2052 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\CHANGELOG.txt | text | |
MD5:B13DE4E8531AF294F87FFDDCCB08D7CE | SHA256:69E38F590A9A25F656E7507AF76229A3A6678A8C57B4E879FF8CE7E52FD704FF | |||
| 2052 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\ExtendedTools.dll | executable | |
MD5:BC61E6FB02FBBFE16FB43CC9F4E949F1 | SHA256:F2805E0F81513641A440F1A21057A664961C22192CB33FCA3870362C8F872D87 | |||
| 2052 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\ExtendedServices.dll | executable | |
MD5:4858BDB7731BF0B46B247A1F01F4A282 | SHA256:5AE7C0972FD4E4C4AE14C0103602CA854377FEFCBCCD86FA68CFC5A6D1F99F60 | |||
| 2052 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\HardwareDevices.dll | executable | |
MD5:A46C8BB886E0B9290E5DBC6CA524D61F | SHA256:ACD49F2AA36D4EFB9C4949E2D3CC2BD7AEE384C2CED7AA9E66063DA4150FCB00 | |||
| 2052 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\ToolStatus.dll | executable | |
MD5:3788EFFF135F8B17A179D02334D505E6 | SHA256:5713D40DEC146DBC819230DAEFE1B886FA6D6F6DBD619301BB8899562195CBAB | |||
| 2052 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\COPYRIGHT.txt | text | |
MD5:39B07060A5C6199730219E29C747C061 | SHA256:319CD301CF40BE03C00CD086560D4E810E0F6D0DBFDC2D28D6AF3522C027CF49 | |||
| 2052 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\kprocesshacker.sys | executable | |
MD5:1B5C3C458E31BEDE55145D0644E88D75 | SHA256:70211A3F90376BBC61F49C22A63075D1D4DDD53F0AEFA976216C46E6BA39A9F4 | |||
| 2052 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\plugins\SbieSupport.dll | executable | |
MD5:37CBFA73883E7E361D3FA67C16D0F003 | SHA256:57C56F7B312DC1F759E6AD039AAC3F36CE5130D259EB9FAAD77239083398308B | |||
| 2052 | WinRAR.exe | C:\Users\admin\Desktop\processhacker-2.39-bin\x64\peview.exe | executable | |
MD5:DDE1F44789CD50C1F034042D337DEAE3 | SHA256:4259E53D48A3FED947F561FF04C7F94446BEDD64C87F52400B2CB47A77666AAA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
35
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2812 | chrome.exe | GET | 200 | 52.85.188.213:80 | http://d1lxhc4jvstzrp.cloudfront.net/themes/cleanPeppermintBlack_14170d94/style.css | US | text | 671 b | shared |
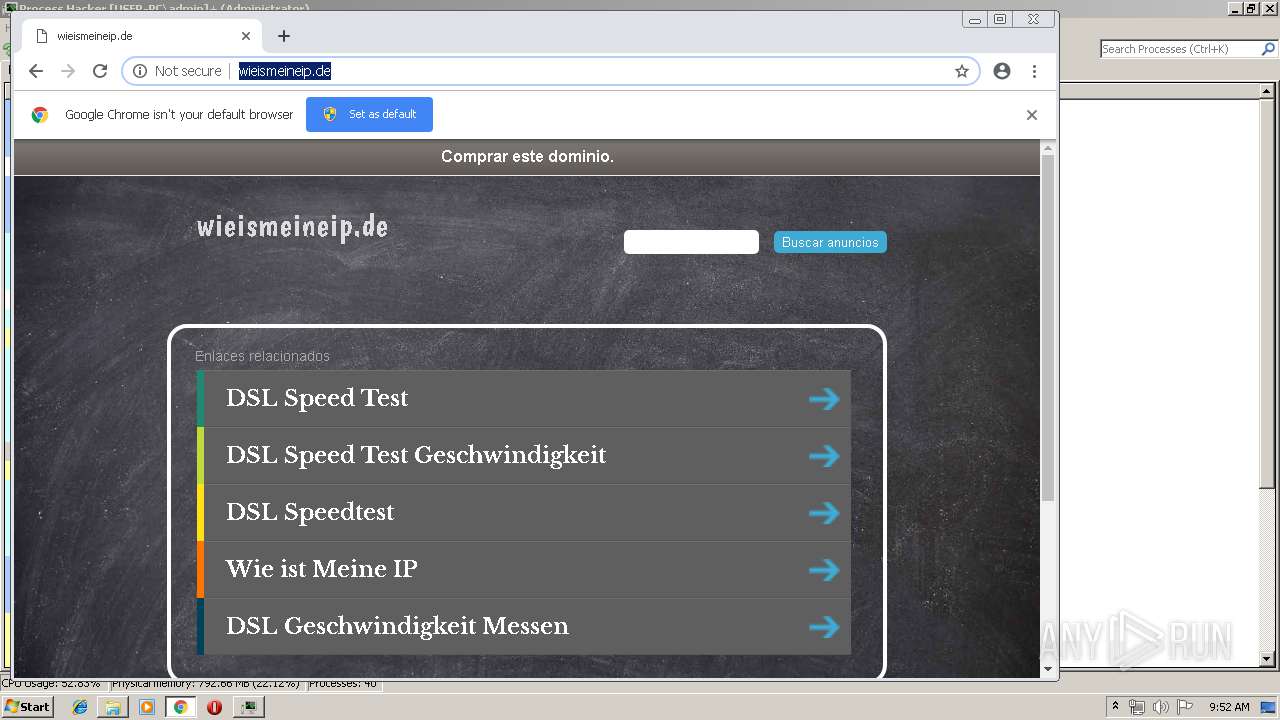
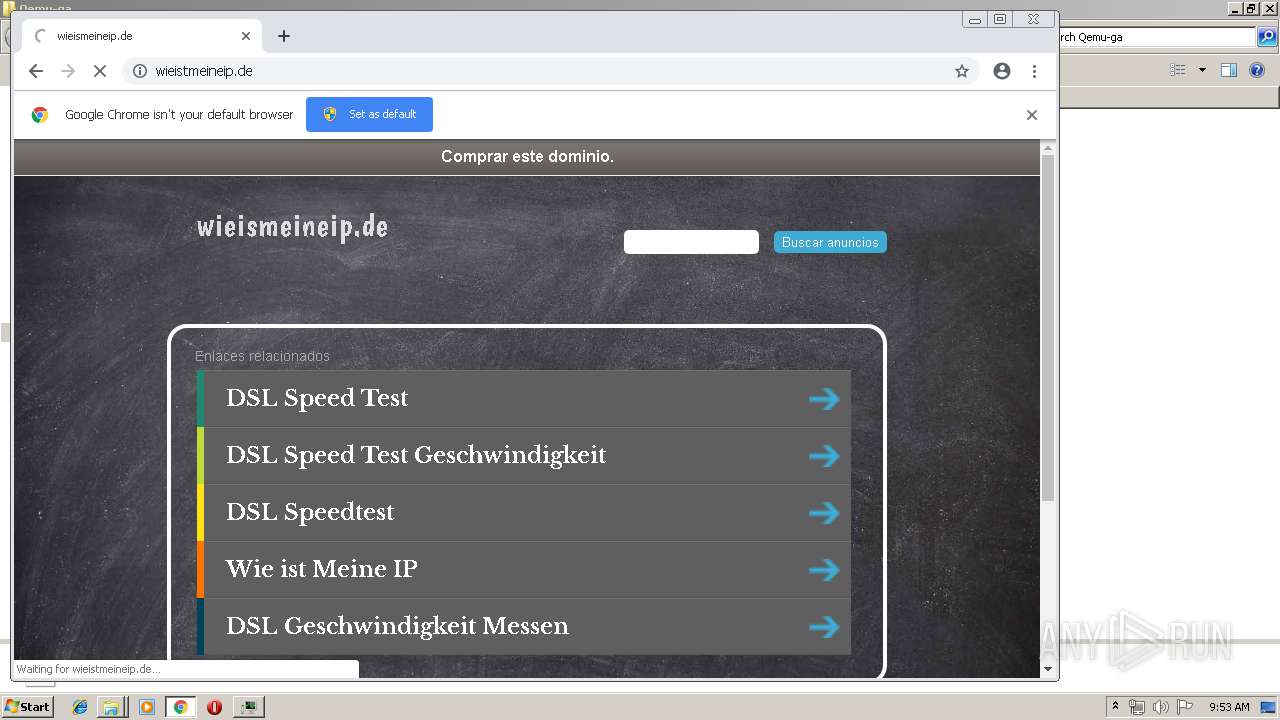
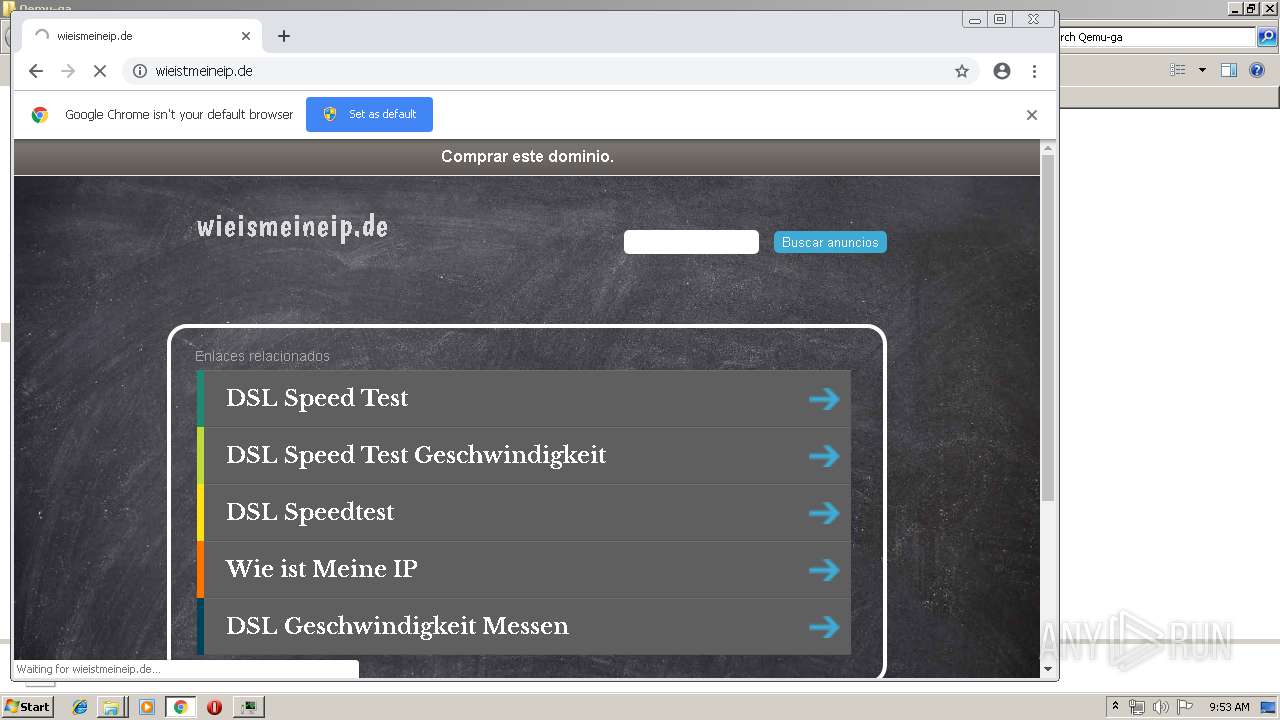
2812 | chrome.exe | GET | 200 | 185.53.178.9:80 | http://wieismeineip.de/ | DE | html | 3.82 Kb | malicious |
2812 | chrome.exe | GET | 200 | 216.58.210.10:80 | http://fonts.googleapis.com/css?family=Boogaloo | US | text | 289 b | whitelisted |
2812 | chrome.exe | GET | 200 | 216.58.210.10:80 | http://fonts.googleapis.com/css?family=Libre+Baskerville:400,700 | US | text | 432 b | whitelisted |
2812 | chrome.exe | GET | 200 | 209.85.230.202:80 | http://r4---sn-h5q7dnlk.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=185.253.99.196&mm=28&mn=sn-h5q7dnlk&ms=nvh&mt=1556181881&mv=u&pl=24&shardbypass=yes | US | crx | 842 Kb | whitelisted |
2812 | chrome.exe | GET | 200 | 185.53.178.30:80 | http://c.parkingcrew.net/scripts/sale_form.js | DE | text | 767 b | whitelisted |
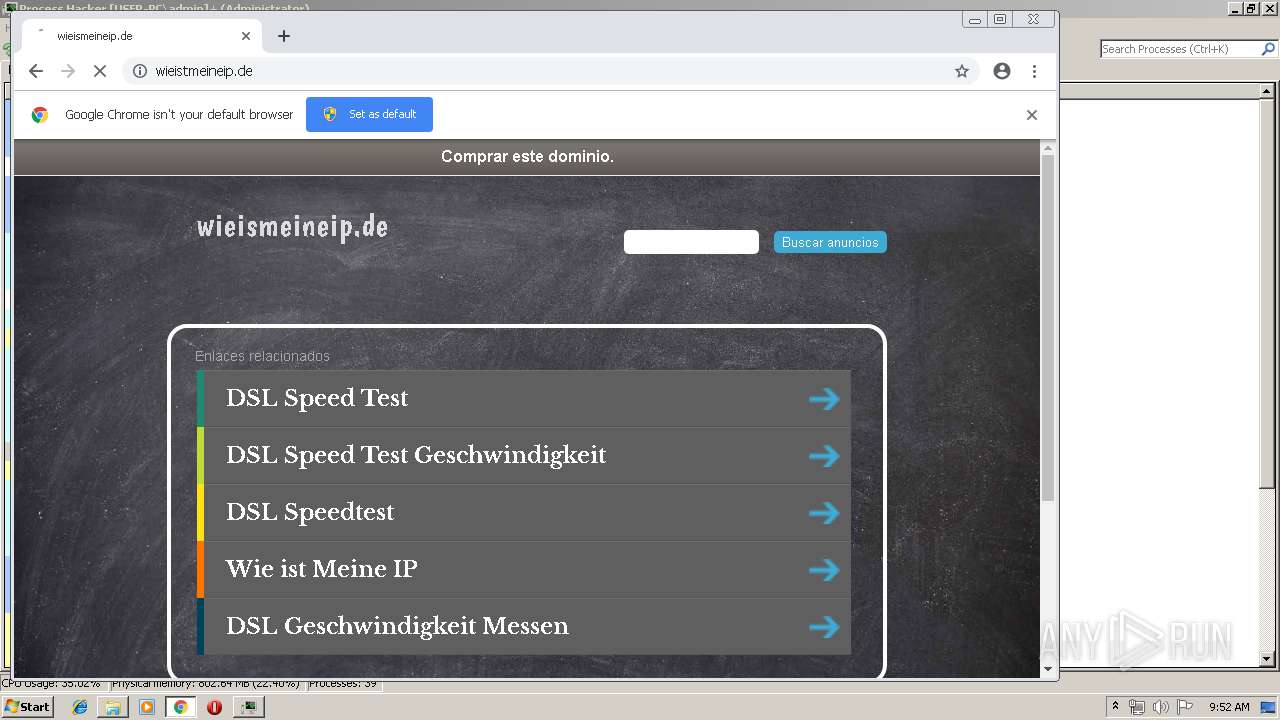
2812 | chrome.exe | GET | — | 52.29.79.39:80 | http://wieistmeineip.de/ | DE | — | — | unknown |
2812 | chrome.exe | GET | 302 | 172.217.18.14:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 505 b | whitelisted |
2812 | chrome.exe | GET | 200 | 52.85.188.213:80 | http://d1lxhc4jvstzrp.cloudfront.net/themes/assets/style.css | US | text | 343 b | shared |
2812 | chrome.exe | GET | 200 | 172.217.18.3:80 | http://fonts.gstatic.com/s/boogaloo/v10/kmK-Zq45GAvOdnaW6y1C9ys.woff2 | US | woff2 | 10.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2812 | chrome.exe | 172.217.18.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2812 | chrome.exe | 172.217.18.99:443 | www.google.com.ua | Google Inc. | US | whitelisted |
2812 | chrome.exe | 216.58.207.46:443 | clients1.google.com | Google Inc. | US | whitelisted |
2812 | chrome.exe | 172.217.23.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2480 | ProcessHacker.exe | 162.243.25.33:443 | wj32.org | Digital Ocean, Inc. | US | suspicious |
2812 | chrome.exe | 216.58.206.3:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2812 | chrome.exe | 172.217.22.109:443 | accounts.google.com | Google Inc. | US | whitelisted |
2812 | chrome.exe | 172.217.21.206:443 | apis.google.com | Google Inc. | US | whitelisted |
2812 | chrome.exe | 209.85.230.202:80 | r4---sn-h5q7dnlk.gvt1.com | Google Inc. | US | whitelisted |
2812 | chrome.exe | 172.217.22.36:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wj32.org |
| whitelisted |
www.google.com.ua |
| whitelisted |
accounts.google.com |
| shared |
clients1.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
wieismeineip.de |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2812 | chrome.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|