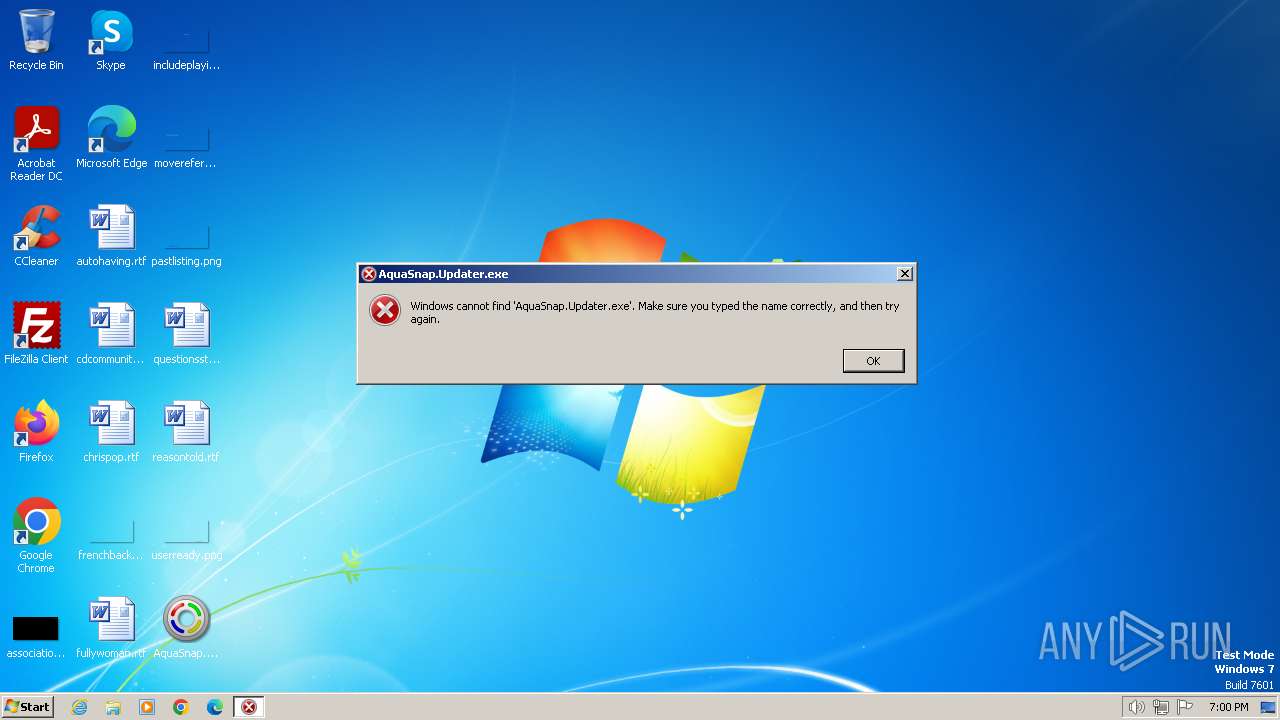
| File name: | AquaSnap.Daemon.exe |
| Full analysis: | https://app.any.run/tasks/06b6a4fb-c6d7-4c92-bc23-d46c5ea54b97 |
| Verdict: | Malicious activity |
| Analysis date: | March 23, 2024, 19:00:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7513B03741D0AC217BE10BB3609BB40E |
| SHA1: | 97005657DEDCEB53B1CD64A026B799F559176DD9 |
| SHA256: | 2AC44A23BC4DECAE148EF909F5CBE8C700A0B227D06C949B337C9E63B35F555F |
| SSDEEP: | 49152:0tfVko7yEbrFkKlYuBm52YjQuFXtk2pFkpimvDZNnnSfpEBW1kcmTjphojok7/:0Ao7rrFkKlYuBU2AZS2o3nEk9pg |
MALICIOUS
Drops the executable file immediately after the start
- AquaSnap.Daemon.exe (PID: 4008)
Changes the autorun value in the registry
- AquaSnap.Daemon.exe (PID: 4008)
SUSPICIOUS
Reads the Internet Settings
- AquaSnap.Daemon.exe (PID: 4008)
Reads security settings of Internet Explorer
- AquaSnap.Daemon.exe (PID: 4008)
Reads settings of System Certificates
- AquaSnap.Daemon.exe (PID: 4008)
Checks Windows Trust Settings
- AquaSnap.Daemon.exe (PID: 4008)
INFO
Checks supported languages
- AquaSnap.Daemon.exe (PID: 4008)
Reads the computer name
- AquaSnap.Daemon.exe (PID: 4008)
Checks proxy server information
- AquaSnap.Daemon.exe (PID: 4008)
Reads the machine GUID from the registry
- AquaSnap.Daemon.exe (PID: 4008)
Reads the software policy settings
- AquaSnap.Daemon.exe (PID: 4008)
Creates files or folders in the user directory
- AquaSnap.Daemon.exe (PID: 4008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:02:22 17:44:16+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 1441792 |
| InitializedDataSize: | 1388032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1063a6 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.23.7.0 |
| ProductVersionNumber: | 1.23.7.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Nurgo Software |
| FileDescription: | AquaSnap daemon |
| FileVersion: | 1.23.7.0 |
| InternalName: | WindowResizer |
| LegalCopyright: | Copyright © Nurgo Software. All rights reserved. |
| OriginalFileName: | AquaSnap.Daemon.exe |
| ProductName: | AquaSnap |
| ProductVersion: | 1.23.7.0 |
Total processes
38
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4008 | "C:\Users\admin\Desktop\AquaSnap.Daemon.exe" | C:\Users\admin\Desktop\AquaSnap.Daemon.exe | explorer.exe | ||||||||||||
User: admin Company: Nurgo Software Integrity Level: MEDIUM Description: AquaSnap daemon Exit code: 0 Version: 1.23.7.0 Modules
| |||||||||||||||
Total events
5 386
Read events
5 032
Write events
333
Delete events
21
Modification events
| (PID) Process: | (4008) AquaSnap.Daemon.exe | Key: | HKEY_CURRENT_USER\Software\Nurgo-Software\AquaSnap\WindowResizer |
| Operation: | write | Name: | Installed |
Value: 0 | |||
| (PID) Process: | (4008) AquaSnap.Daemon.exe | Key: | HKEY_CURRENT_USER\Software\Nurgo-Software\AquaSnap\WindowResizer |
| Operation: | write | Name: | InstallerName |
Value: | |||
| (PID) Process: | (4008) AquaSnap.Daemon.exe | Key: | HKEY_CURRENT_USER\Software\Nurgo-Software\AquaSnap\WindowResizer |
| Operation: | write | Name: | Instance |
Value: | |||
| (PID) Process: | (4008) AquaSnap.Daemon.exe | Key: | HKEY_CURRENT_USER\Software\Nurgo-Software\AquaSnap\WindowResizer |
| Operation: | write | Name: | AutoStartEnabled |
Value: 1 | |||
| (PID) Process: | (4008) AquaSnap.Daemon.exe | Key: | HKEY_CURRENT_USER\Software\Nurgo-Software\AquaSnap\WindowResizer |
| Operation: | write | Name: | AutoUpdate |
Value: 1 | |||
| (PID) Process: | (4008) AquaSnap.Daemon.exe | Key: | HKEY_CURRENT_USER\Software\Nurgo-Software\AquaSnap\WindowResizer |
| Operation: | write | Name: | AutoUpdateEnabled |
Value: 1 | |||
| (PID) Process: | (4008) AquaSnap.Daemon.exe | Key: | HKEY_CURRENT_USER\Software\Nurgo-Software\AquaSnap\WindowResizer |
| Operation: | write | Name: | ShowTray |
Value: 1 | |||
| (PID) Process: | (4008) AquaSnap.Daemon.exe | Key: | HKEY_CURRENT_USER\Software\Nurgo-Software\AquaSnap\WindowResizer |
| Operation: | write | Name: | ShowTrayEnabled |
Value: 1 | |||
| (PID) Process: | (4008) AquaSnap.Daemon.exe | Key: | HKEY_CURRENT_USER\Software\Nurgo-Software\AquaSnap\WindowResizer |
| Operation: | write | Name: | AskForNewsLetterSubscription |
Value: 1 | |||
| (PID) Process: | (4008) AquaSnap.Daemon.exe | Key: | HKEY_CURRENT_USER\Software\Nurgo-Software\AquaSnap\WindowResizer |
| Operation: | write | Name: | NewsLetterSubscriber |
Value: | |||
Executable files
0
Suspicious files
6
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4008 | AquaSnap.Daemon.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:2EBBF68BCA5CBF20D85B636267EA8FCA | SHA256:7F6E3F0669AD3DAE668494D15ABF604CDA50C97C312288EDCB172E85B364F033 | |||
| 4008 | AquaSnap.Daemon.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:E66F0C8E64F85F4E3209EDAFFC6B4F24 | SHA256:FF20BB38A5C4A6D066753ACD1508D78889E527B9DFF4355A60A5E412B88301EA | |||
| 4008 | AquaSnap.Daemon.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:72F34BCC1BA0ADF0807D2FE1D0D6A334 | SHA256:3E99E9693E36C27ED1EA8FBC7D0BF29ABBCB4E25A73DF1E0E81337813C55DBD0 | |||
| 4008 | AquaSnap.Daemon.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A16C6C16D94F76E0808C087DFC657D99_99430B8B5F4E113F6193E2BF9312EF16 | binary | |
MD5:472160358A3D331FA8B6EBA433E6C044 | SHA256:369F7939B115FC5A3E211FE4687484F35876A1C877135BCA04FF77CB75B74693 | |||
| 4008 | AquaSnap.Daemon.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:53FBF6342FB90F8654AF6342D85F06FD | SHA256:C98491F1D975C9E559A9DC35B15931D3961191ED2477610471FFF9040D264E7E | |||
| 4008 | AquaSnap.Daemon.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 4008 | AquaSnap.Daemon.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A16C6C16D94F76E0808C087DFC657D99_99430B8B5F4E113F6193E2BF9312EF16 | binary | |
MD5:141B4F07FE5BF832FBB38892A65099FC | SHA256:44E44208FA16C7862EBB2ED78C66F32AA2EA84D48D5EA6FB8834A07353D2FCED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
8
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4008 | AquaSnap.Daemon.exe | GET | 304 | 23.32.238.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?441b05e5c053f230 | unknown | — | — | unknown |
4008 | AquaSnap.Daemon.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
4008 | AquaSnap.Daemon.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
4008 | AquaSnap.Daemon.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD6BeWhIbleexId20FpK0af | unknown | binary | 472 b | unknown |
1080 | svchost.exe | GET | 200 | 23.32.238.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?89bca2e7018c82c0 | unknown | compressed | 67.5 Kb | unknown |
1080 | svchost.exe | GET | 304 | 23.32.238.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1b8fee253118cbef | unknown | compressed | 67.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4008 | AquaSnap.Daemon.exe | 142.250.186.168:443 | ssl.google-analytics.com | GOOGLE | US | unknown |
4008 | AquaSnap.Daemon.exe | 23.32.238.50:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4008 | AquaSnap.Daemon.exe | 172.217.16.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 23.32.238.50:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ssl.google-analytics.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |