| File name: | report - 2020-10-20T144335.308.eml |
| Full analysis: | https://app.any.run/tasks/d21198df-88e0-448a-8a9f-093177932081 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 09:26:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | D63B5E4023179AB84864DAA600FC055F |
| SHA1: | BA5A23EA6E819FF1BD38A4446FFE8376ED205BA4 |
| SHA256: | 2AB5E52A57B4488EA28CB10790DABAEAE8C893F1CF8AEB5855050B8BCE09A3B2 |
| SSDEEP: | 49152:Ejo3SJ4L14hAy5KToVqntKUREo/LXOiAgcY84HuM4LEv:3 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 1496)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 1496)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 1496)
Creates files in the program directory
- AdobeARM.exe (PID: 2484)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1496)
Reads settings of System Certificates
- iexplore.exe (PID: 2752)
- iexplore.exe (PID: 3340)
- AcroRd32.exe (PID: 716)
Reads Internet Cache Settings
- iexplore.exe (PID: 2752)
- iexplore.exe (PID: 3340)
- AcroRd32.exe (PID: 3880)
- AcroRd32.exe (PID: 716)
- iexplore.exe (PID: 3972)
Changes internet zones settings
- iexplore.exe (PID: 3340)
Reads internet explorer settings
- iexplore.exe (PID: 2752)
- iexplore.exe (PID: 3972)
Application launched itself
- iexplore.exe (PID: 3340)
- AcroRd32.exe (PID: 716)
- RdrCEF.exe (PID: 3564)
- AcroRd32.exe (PID: 2552)
- AcroRd32.exe (PID: 2780)
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 716)
Reads the hosts file
- RdrCEF.exe (PID: 3564)
Creates files in the user directory
- iexplore.exe (PID: 2752)
- iexplore.exe (PID: 3340)
- iexplore.exe (PID: 3972)
Changes settings of System certificates
- iexplore.exe (PID: 3340)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3340)
Dropped object may contain Bitcoin addresses
- OUTLOOK.EXE (PID: 1496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 7) (100) |
|---|
Total processes
55
Monitored processes
17
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
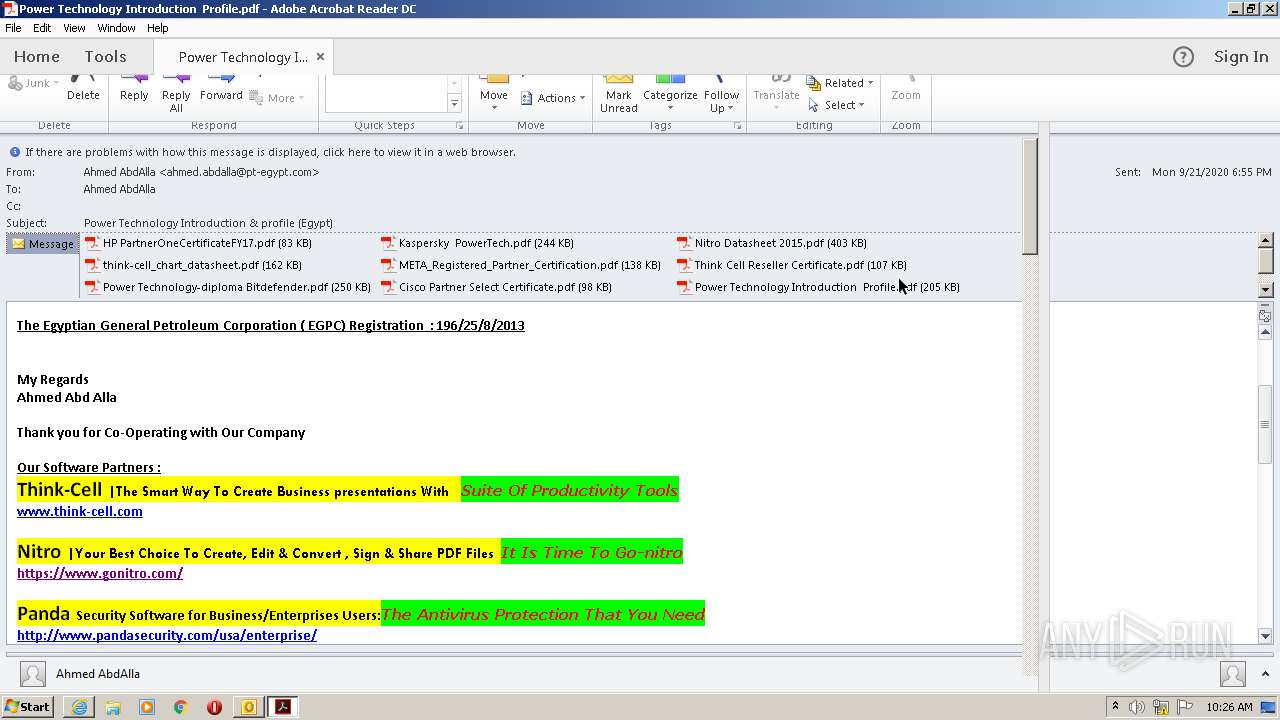
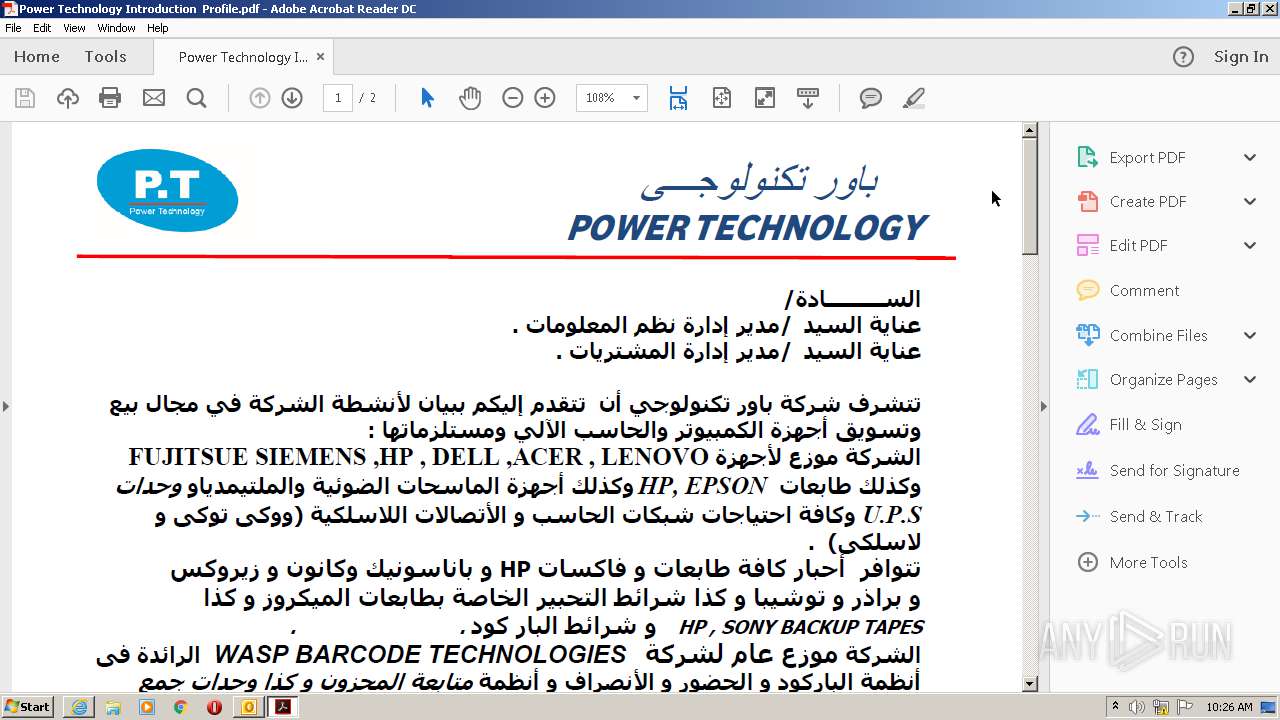
| 716 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\BWQ9XF7N\Power Technology Introduction Profile.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
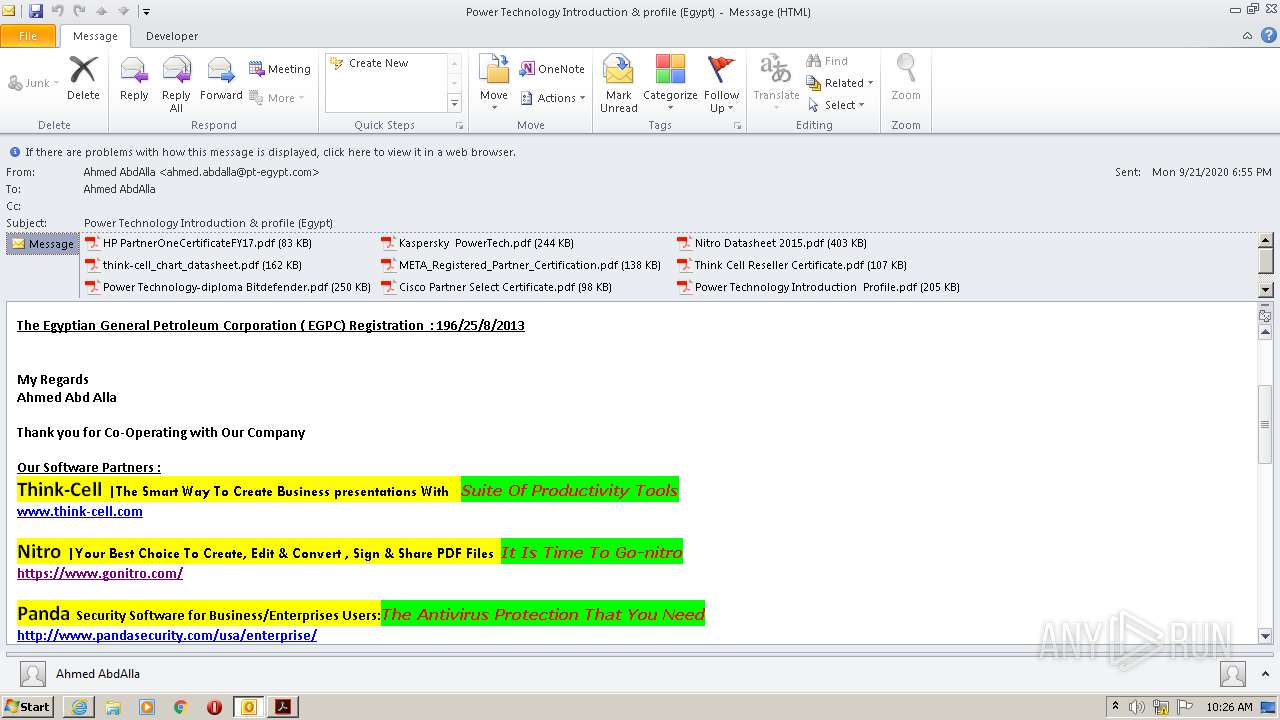
| 1496 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\report - 2020-10-20T144335.308.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 1724 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3564.1.1421288441\1971626436" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2416 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3564.2.1220506981\1802915536" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2484 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
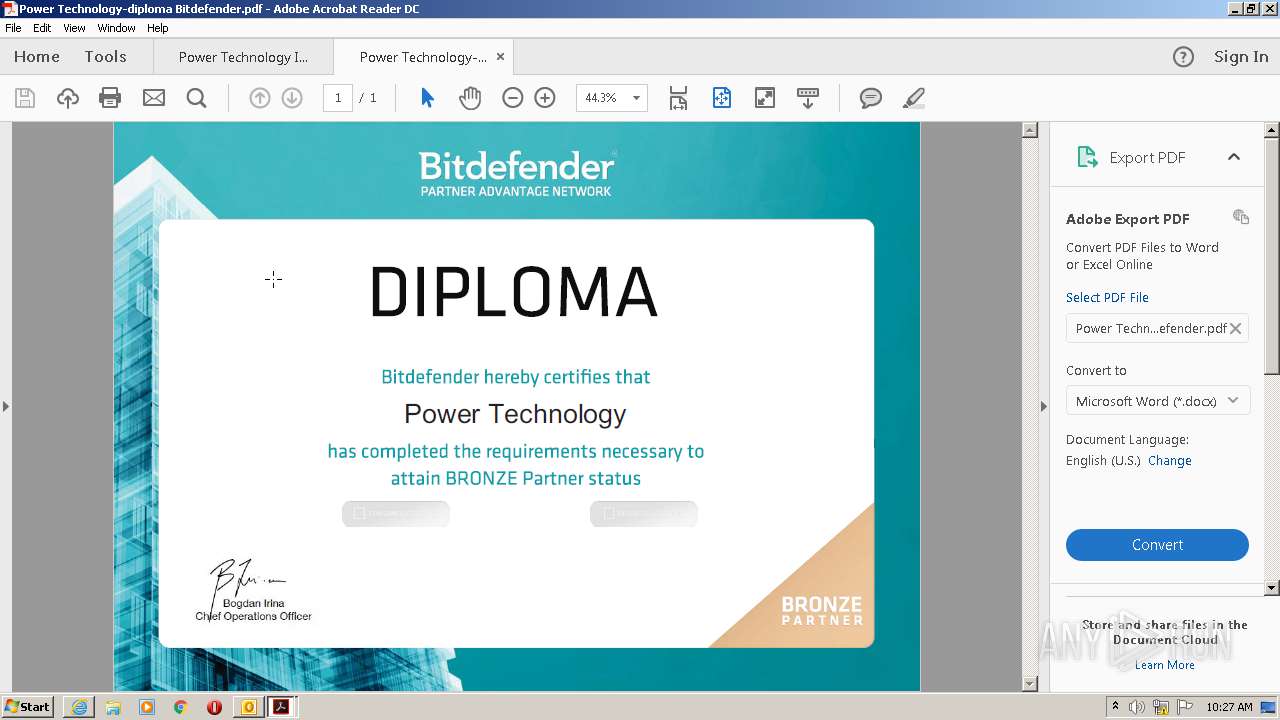
| 2552 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\BWQ9XF7N\Power Technology-diploma Bitdefender.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2576 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3564.0.585824643\323948710" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2716 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2752 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3340 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2780 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\BWQ9XF7N\META_Registered_Partner_Certification.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
Total events
2 968
Read events
2 219
Write events
726
Delete events
23
Modification events
| (PID) Process: | (1496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (1496) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
240
Text files
193
Unknown types
139
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR450C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp477E.tmp | — | |
MD5:— | SHA256:— | |||
| 1496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp478F.tmp | — | |
MD5:— | SHA256:— | |||
| 1496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp47A0.tmp | — | |
MD5:— | SHA256:— | |||
| 1496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp47A1.tmp | — | |
MD5:— | SHA256:— | |||
| 1496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp47B1.tmp | — | |
MD5:— | SHA256:— | |||
| 1496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp47B2.tmp | — | |
MD5:— | SHA256:— | |||
| 1496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp47C3.tmp | — | |
MD5:— | SHA256:— | |||
| 1496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 1496 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
116
TCP/UDP connections
233
DNS requests
91
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2752 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJ9L2KGL92BpjF3kAtaDtxauTmhgQUPdNQpdagre7zSmAKZdMh1Pj41g8CEAZG7HHPRJlckO6ZxX5YrAc%3D | US | der | 471 b | whitelisted |
2752 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | US | der | 471 b | whitelisted |
2752 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2752 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | US | der | 471 b | whitelisted |
2752 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAlNyNE9BgW%2BsnXiFAL5KJ0%3D | US | der | 279 b | whitelisted |
2752 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJ9L2KGL92BpjF3kAtaDtxauTmhgQUPdNQpdagre7zSmAKZdMh1Pj41g8CEAZG7HHPRJlckO6ZxX5YrAc%3D | US | der | 471 b | whitelisted |
2752 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAGC%2BAmOouYmuRo7J4Qfua8%3D | US | der | 1.47 Kb | whitelisted |
2752 | iexplore.exe | GET | 304 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2752 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAwkjOauwchyCqq7K0nUKbU%3D | US | der | 280 b | whitelisted |
2752 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2752 | iexplore.exe | 209.197.3.15:443 | maxcdn.bootstrapcdn.com | Highwinds Network Group, Inc. | US | whitelisted |
2752 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
2752 | iexplore.exe | 151.101.2.110:443 | js-agent.newrelic.com | Fastly | US | suspicious |
3340 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2752 | iexplore.exe | 104.18.20.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
1496 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2752 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2752 | iexplore.exe | 104.16.119.102:443 | www.gonitro.com | Cloudflare Inc | US | shared |
2752 | iexplore.exe | 216.58.212.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2752 | iexplore.exe | 104.16.95.80:443 | app-ab27.marketo.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www.gonitro.com |
| unknown |
ocsp.digicert.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
cf-nitroengassets-prod.s3.amazonaws.com |
| shared |
app-ab27.marketo.com |
| suspicious |
cdn.gonitro.com |
| unknown |
dev.visualwebsiteoptimizer.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2752 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2752 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |