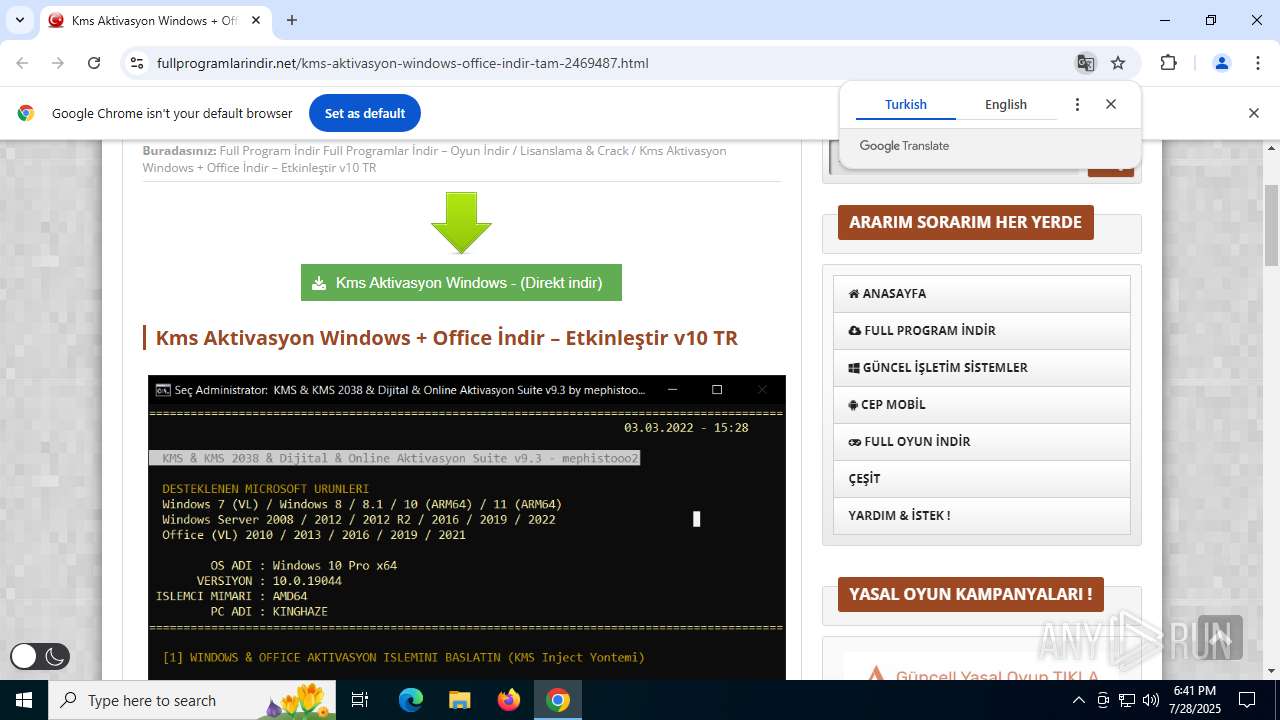
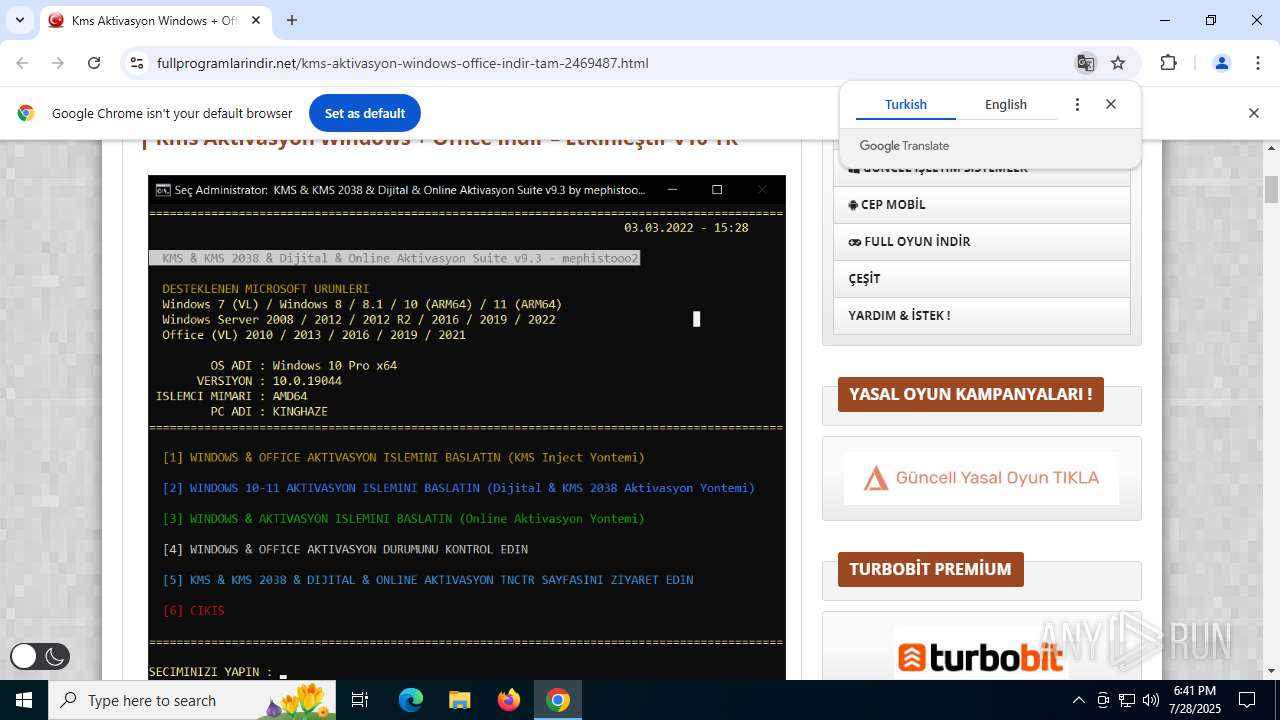
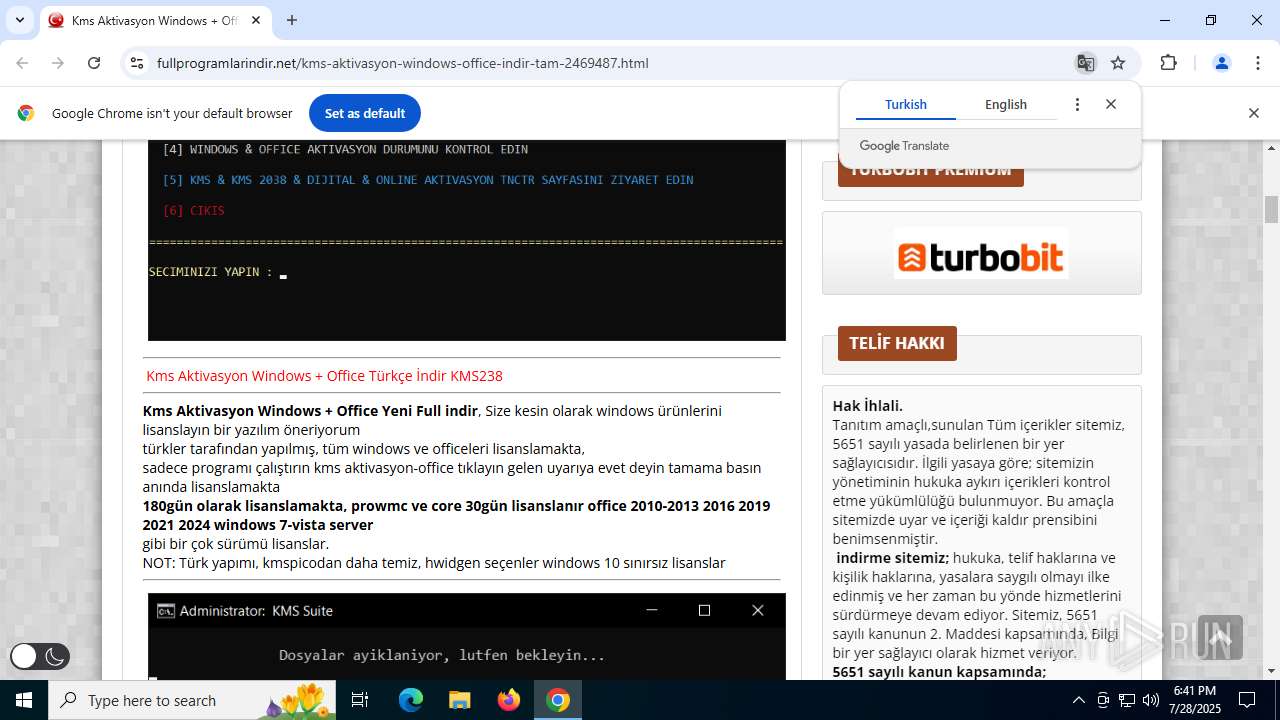
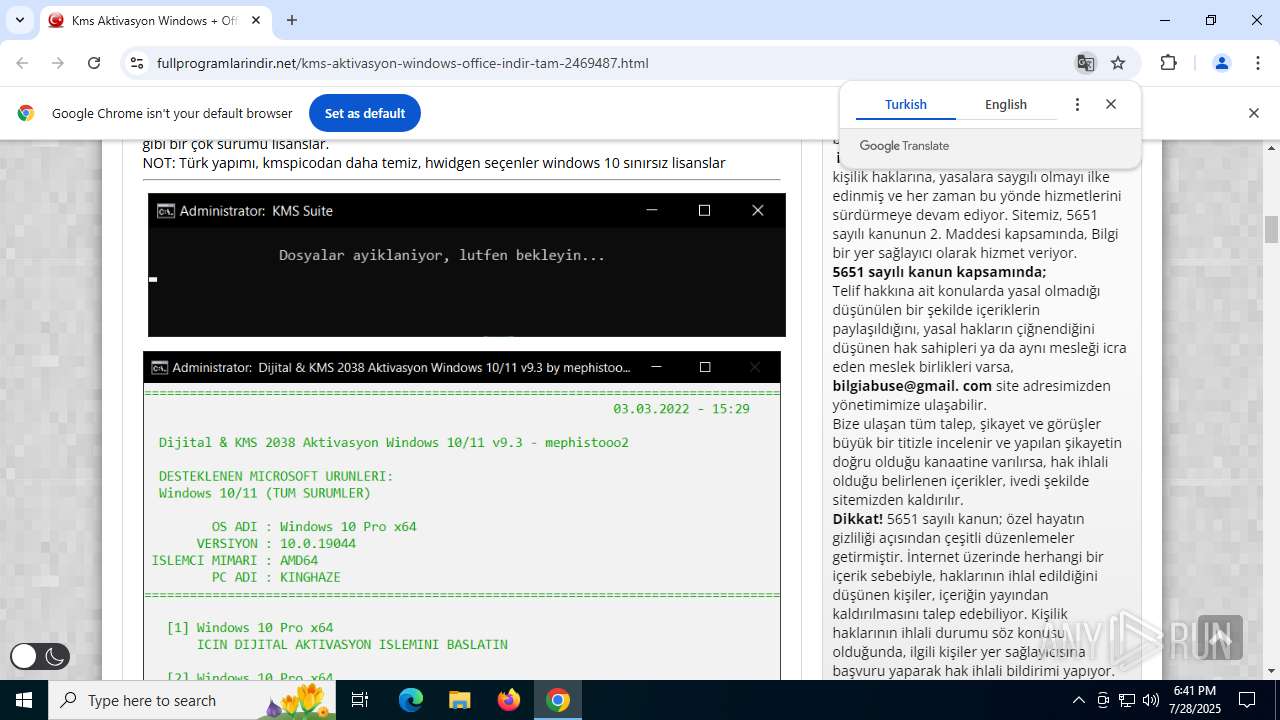
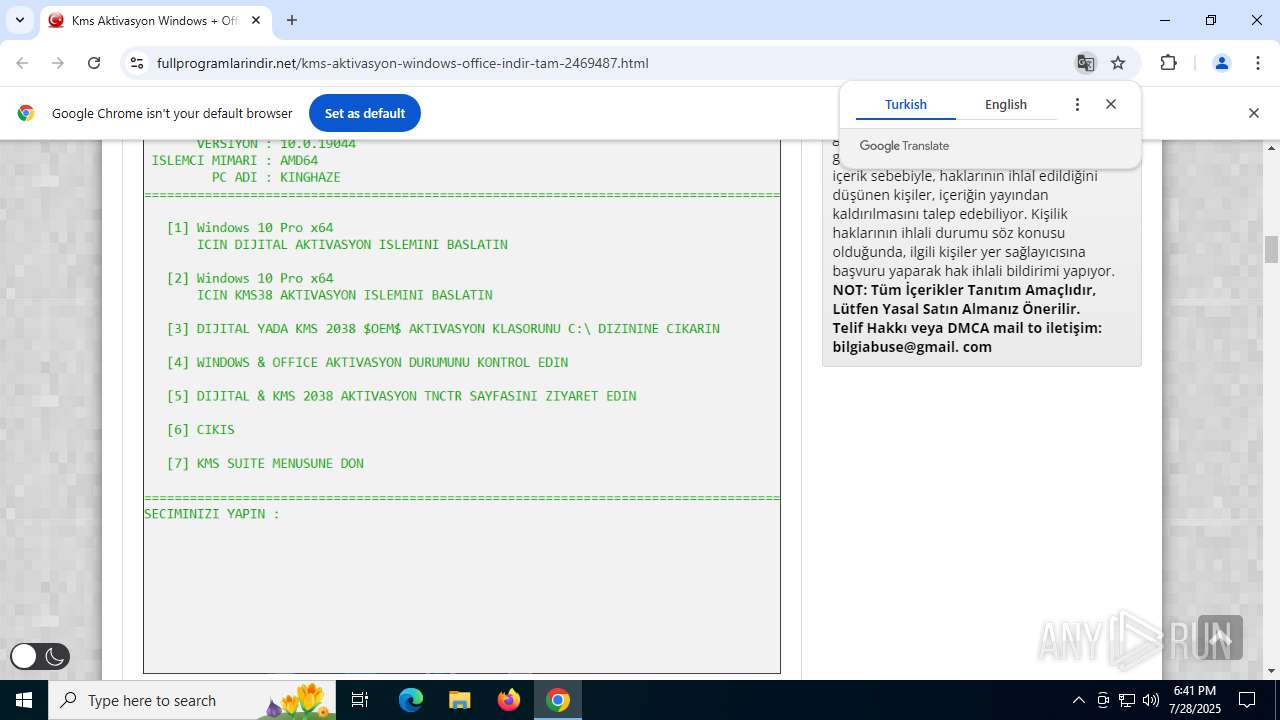
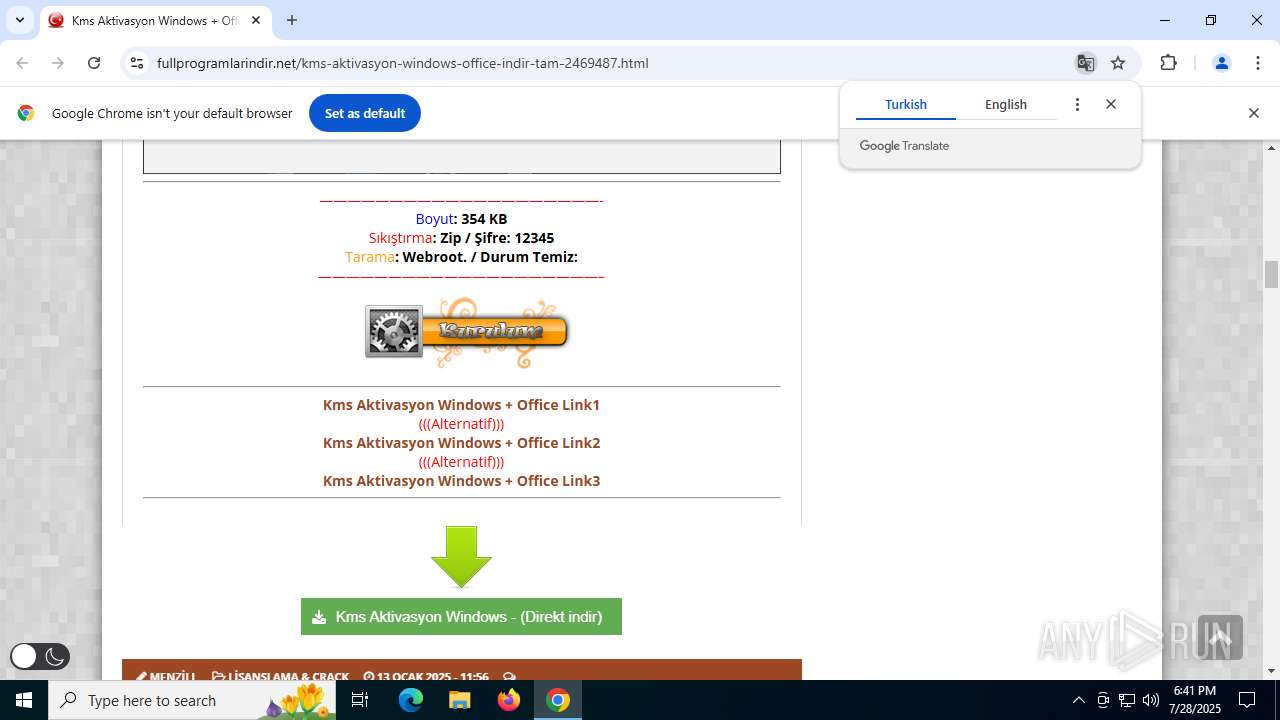
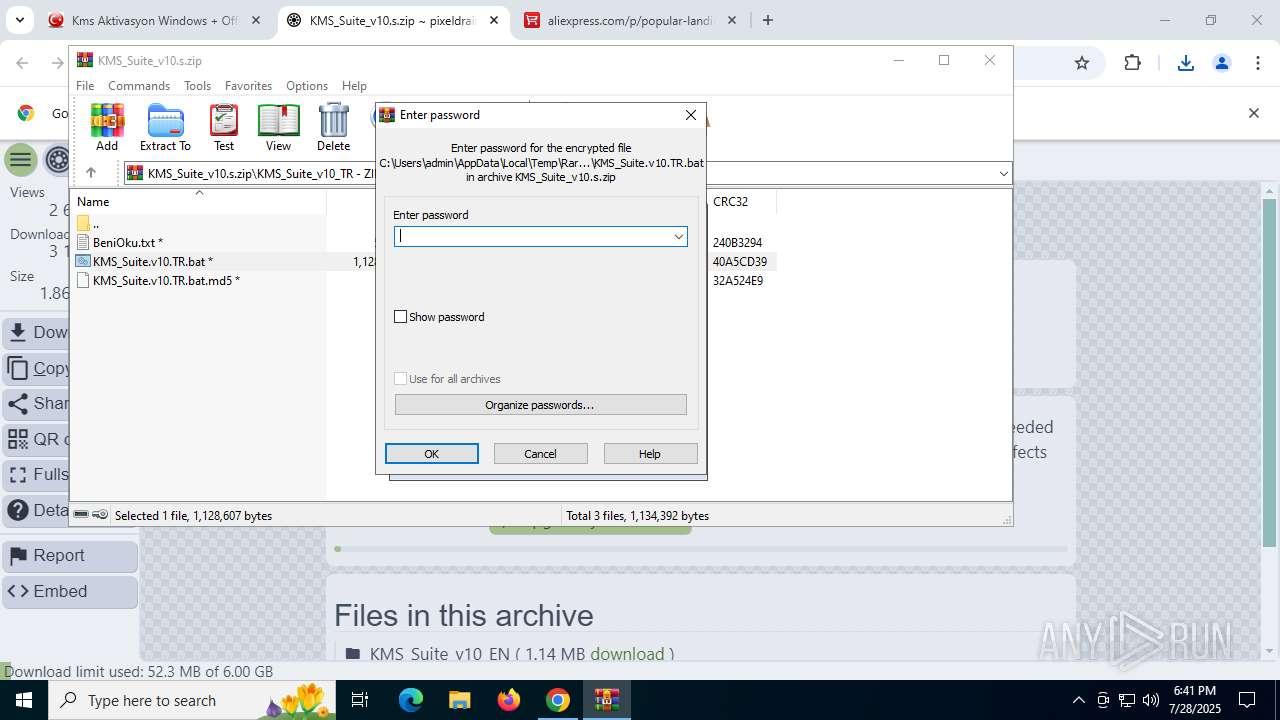
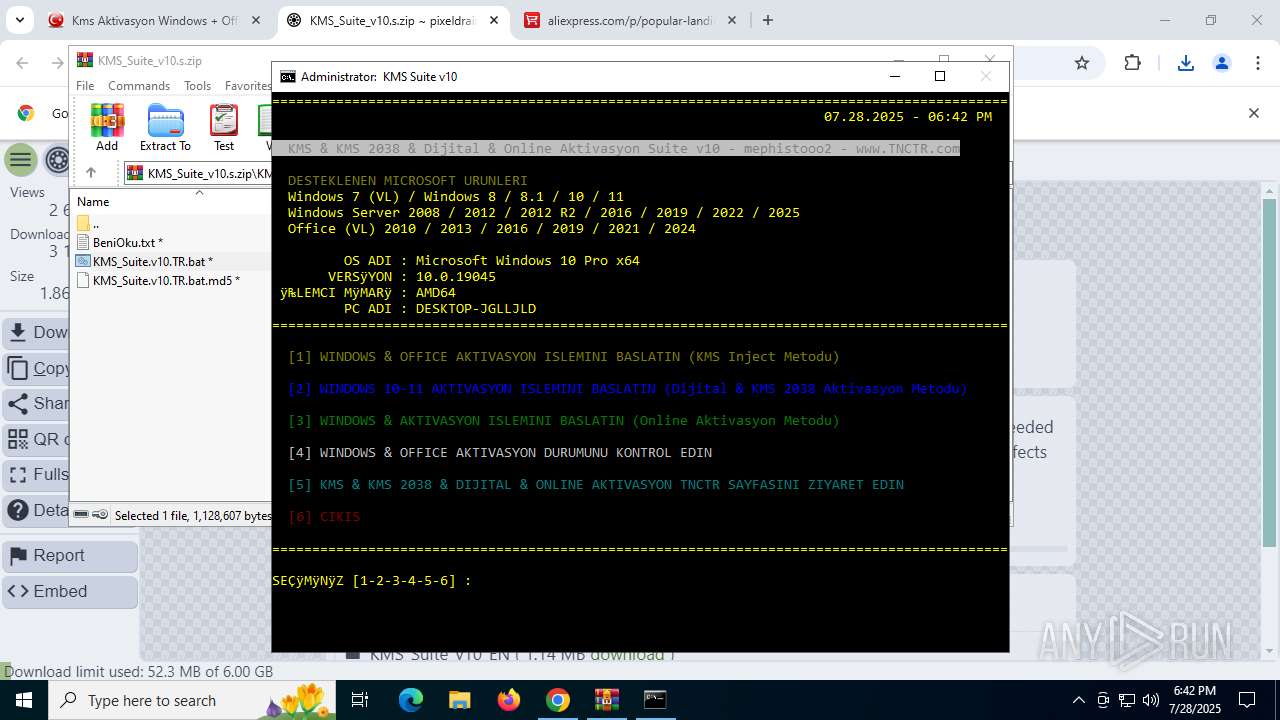
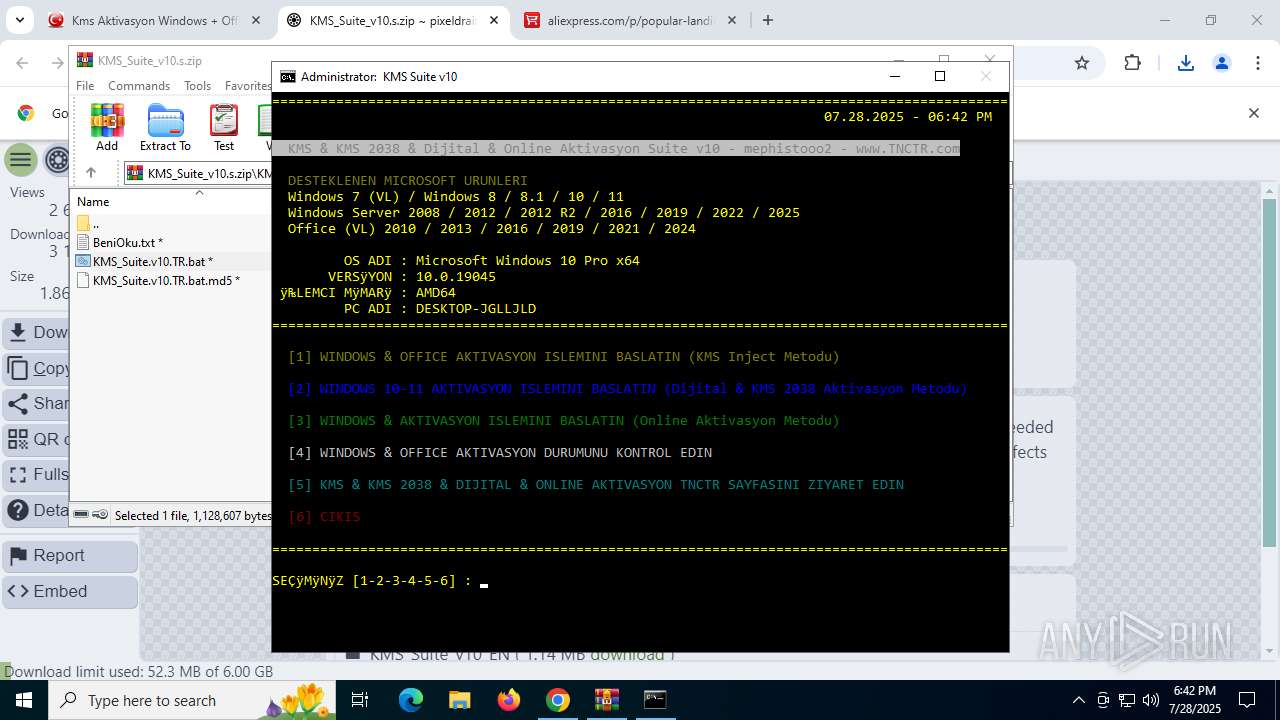
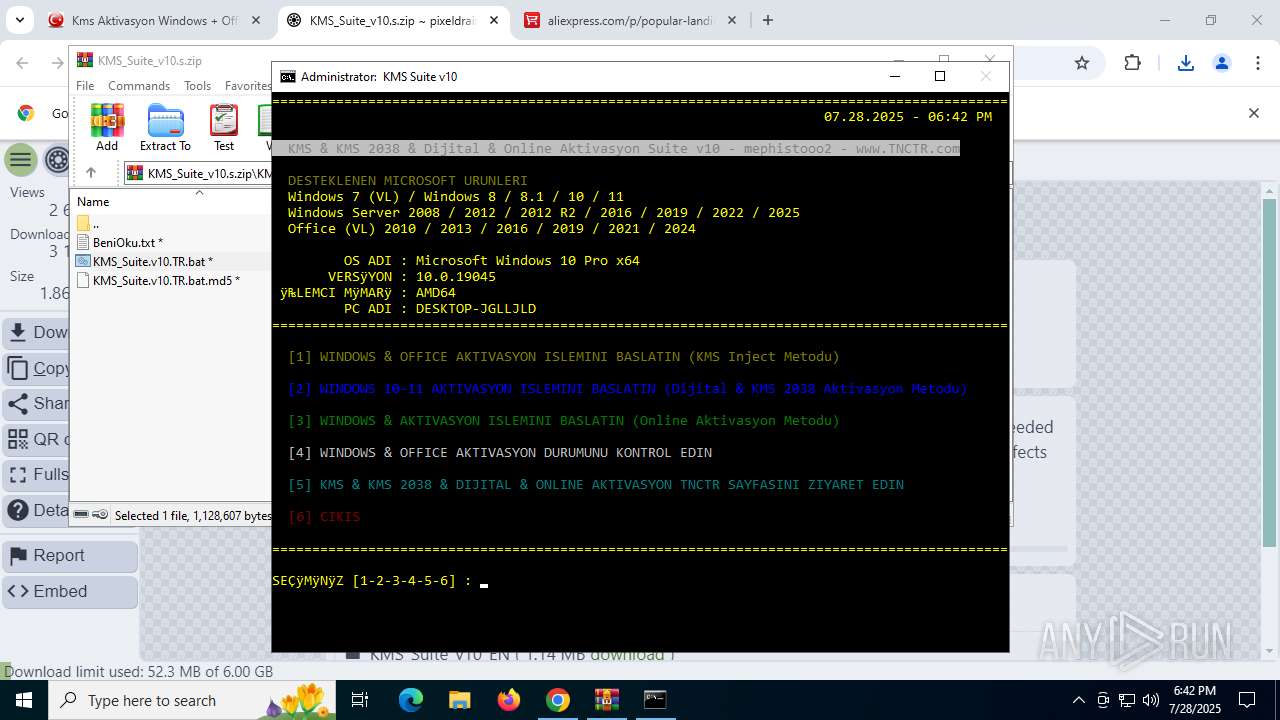
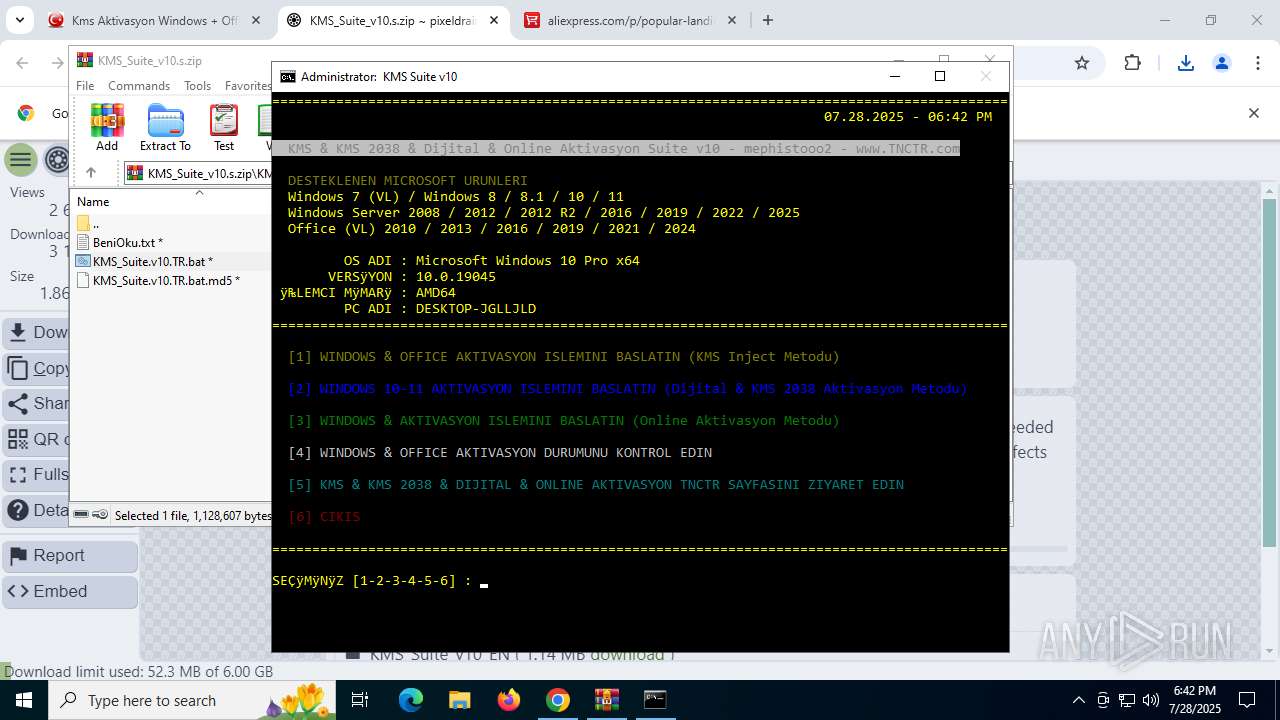
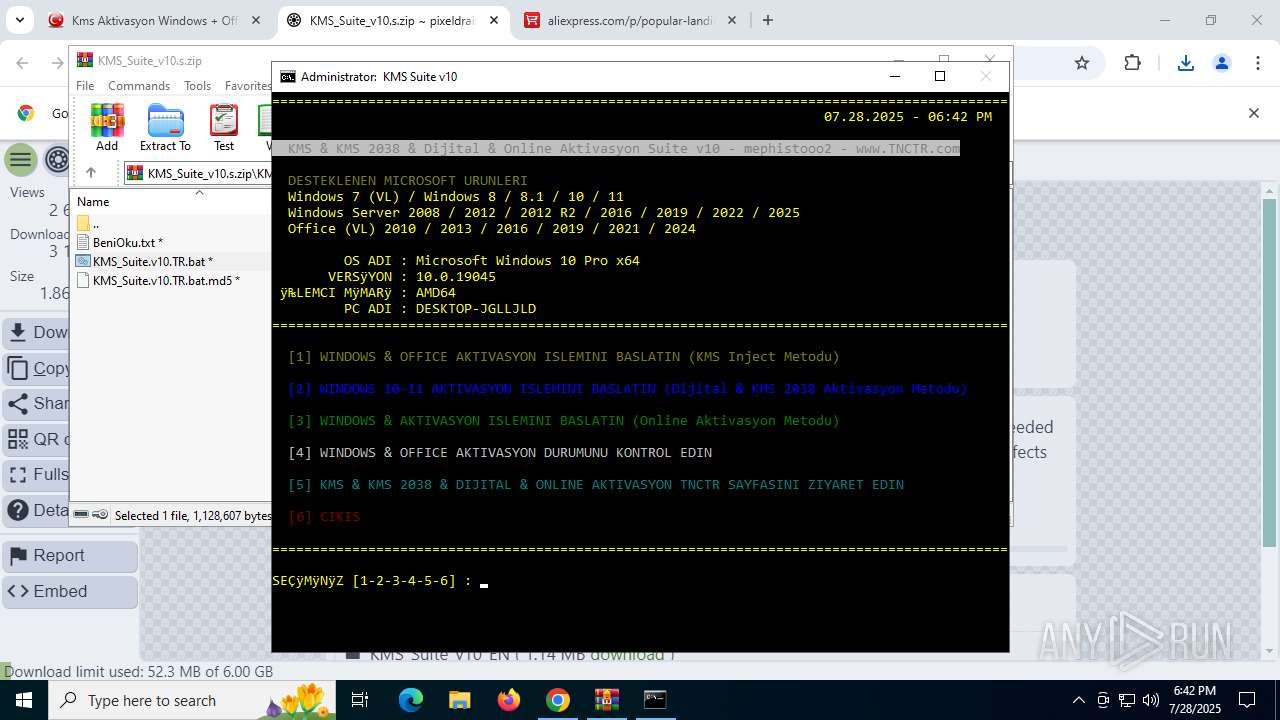
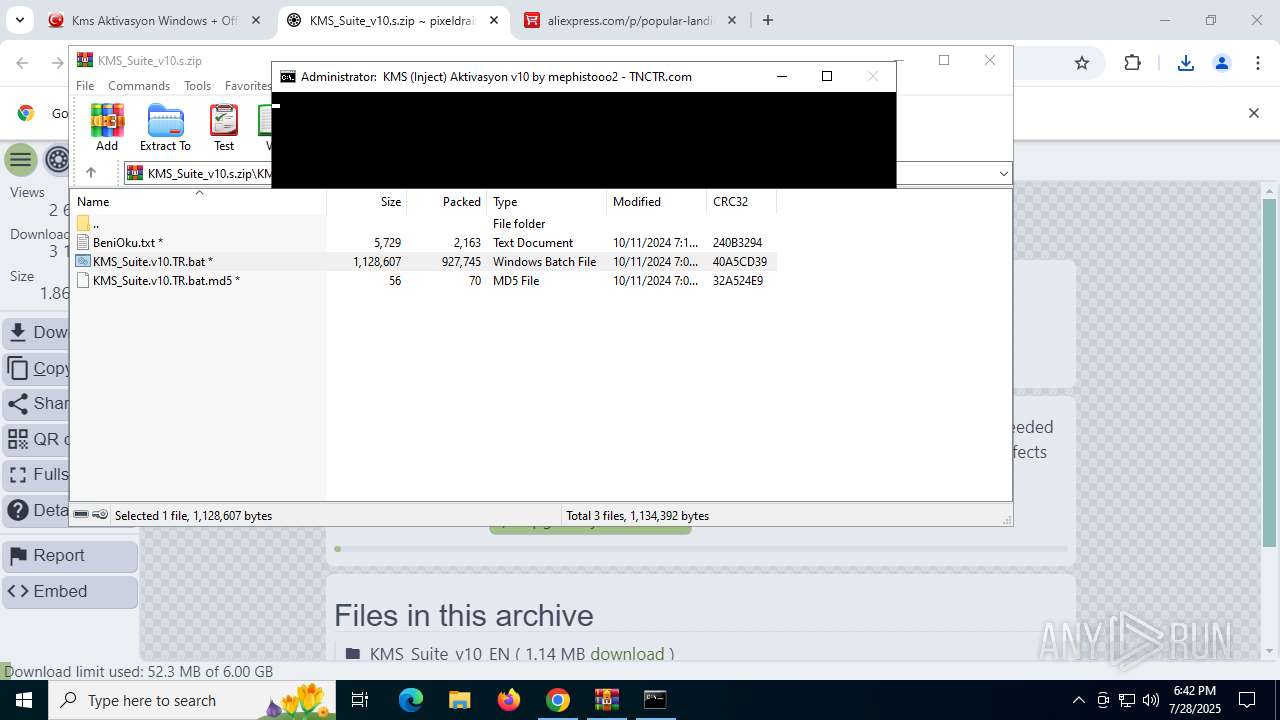
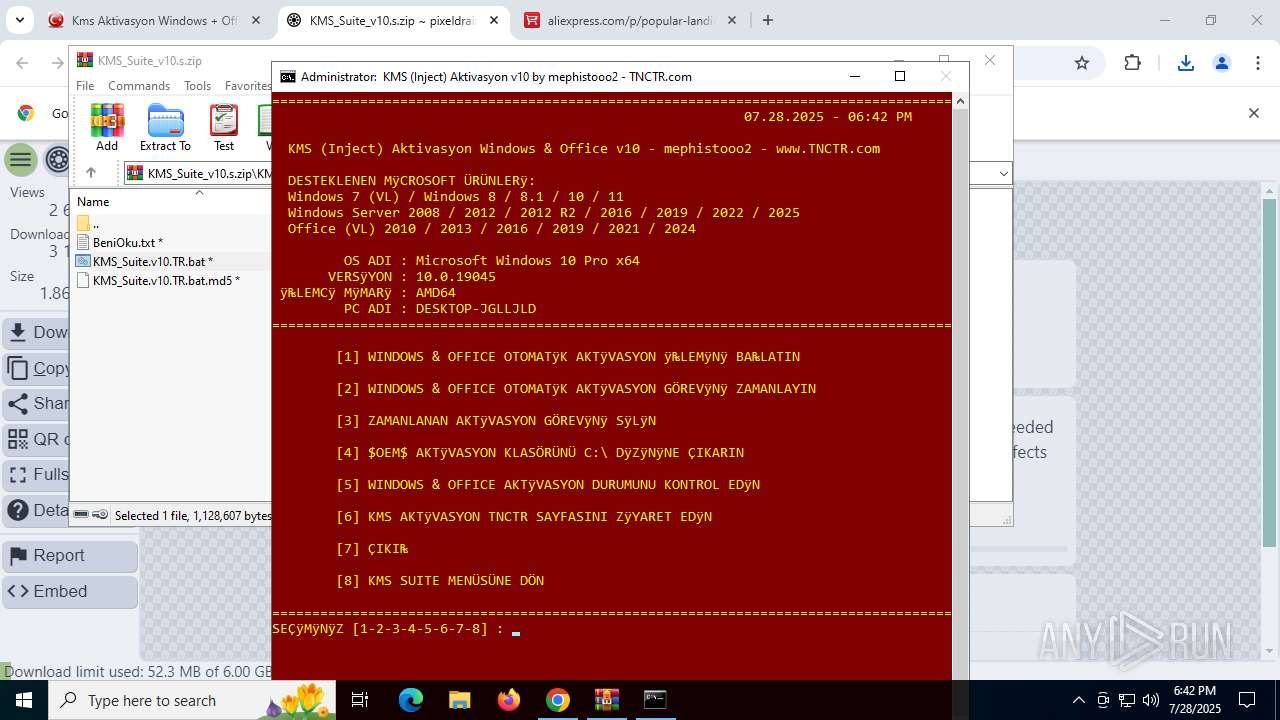
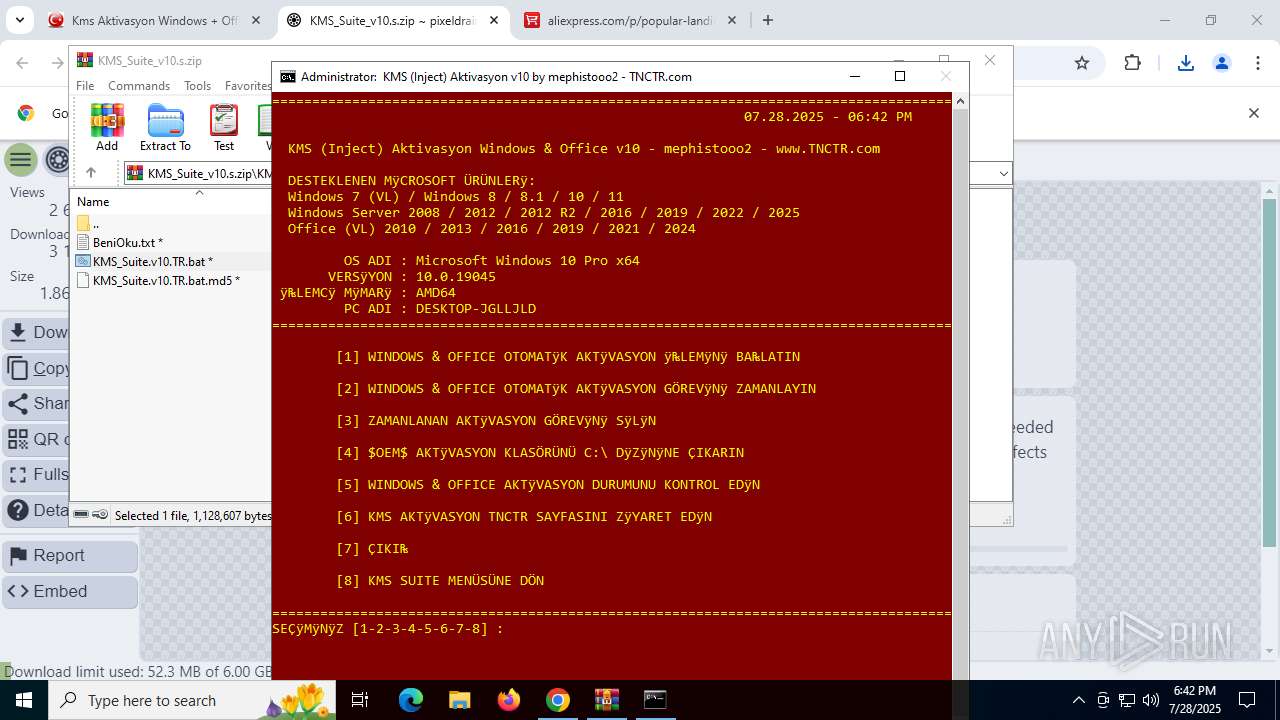
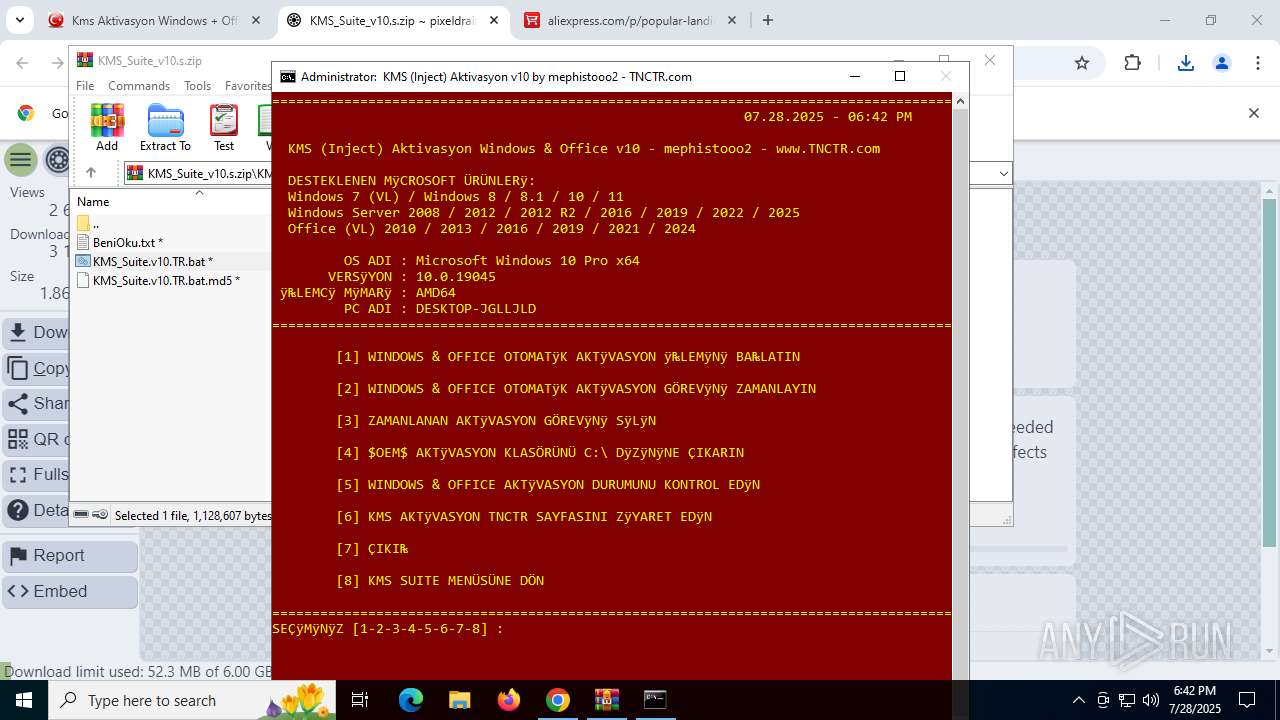
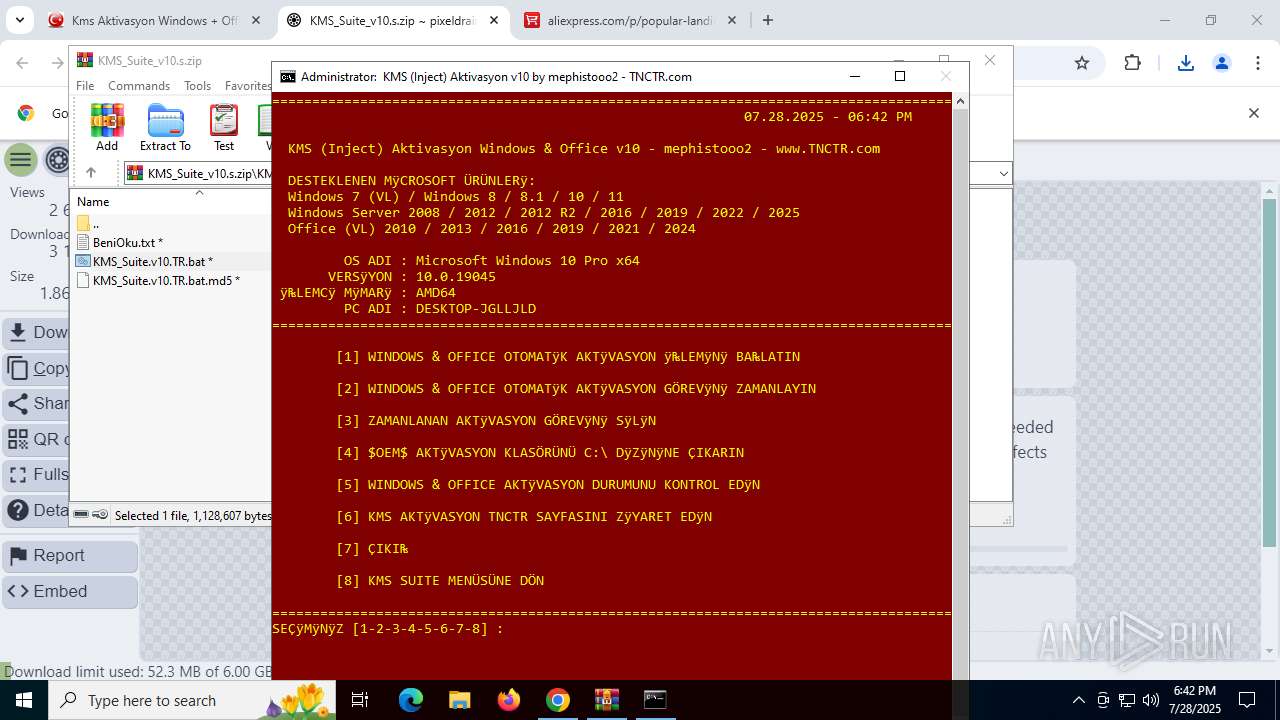
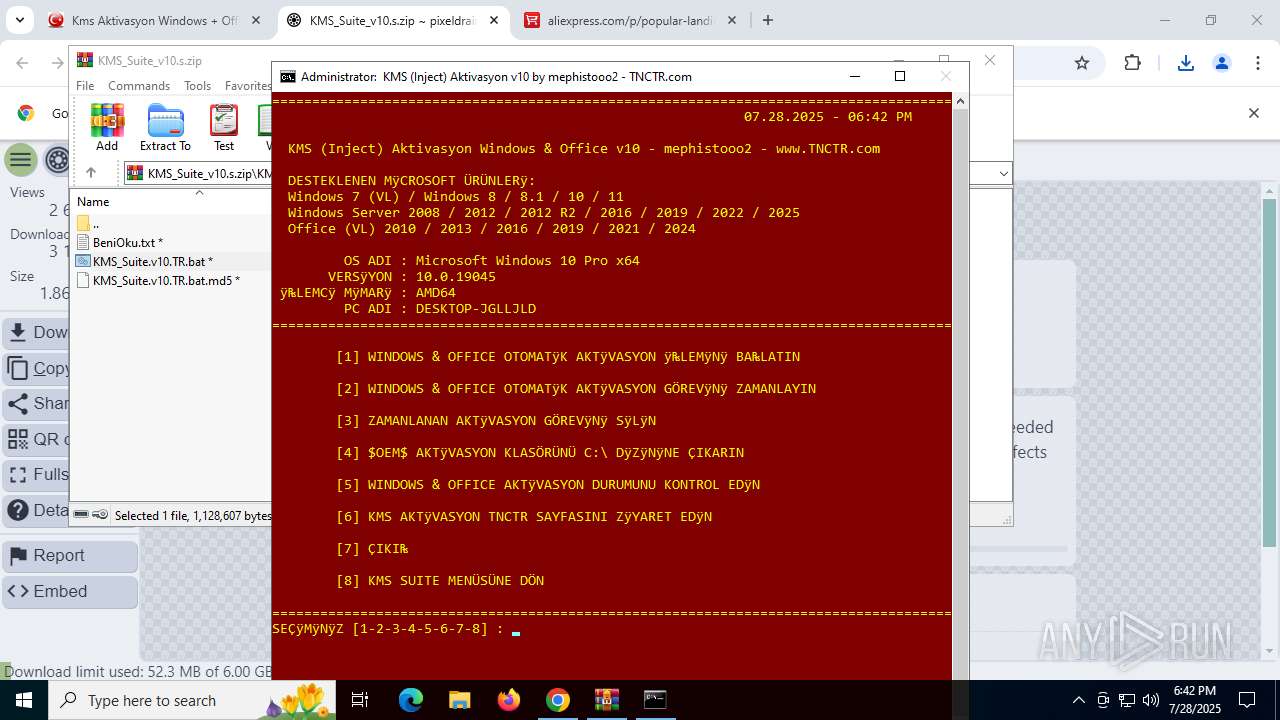
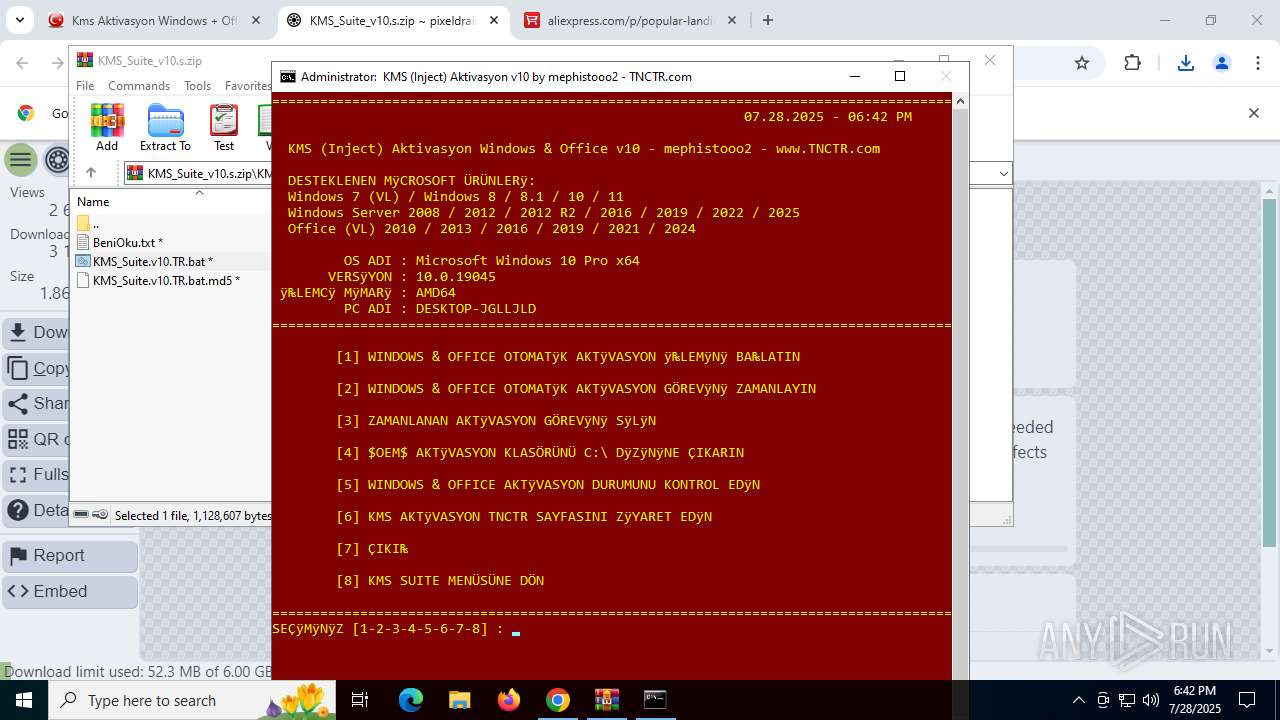
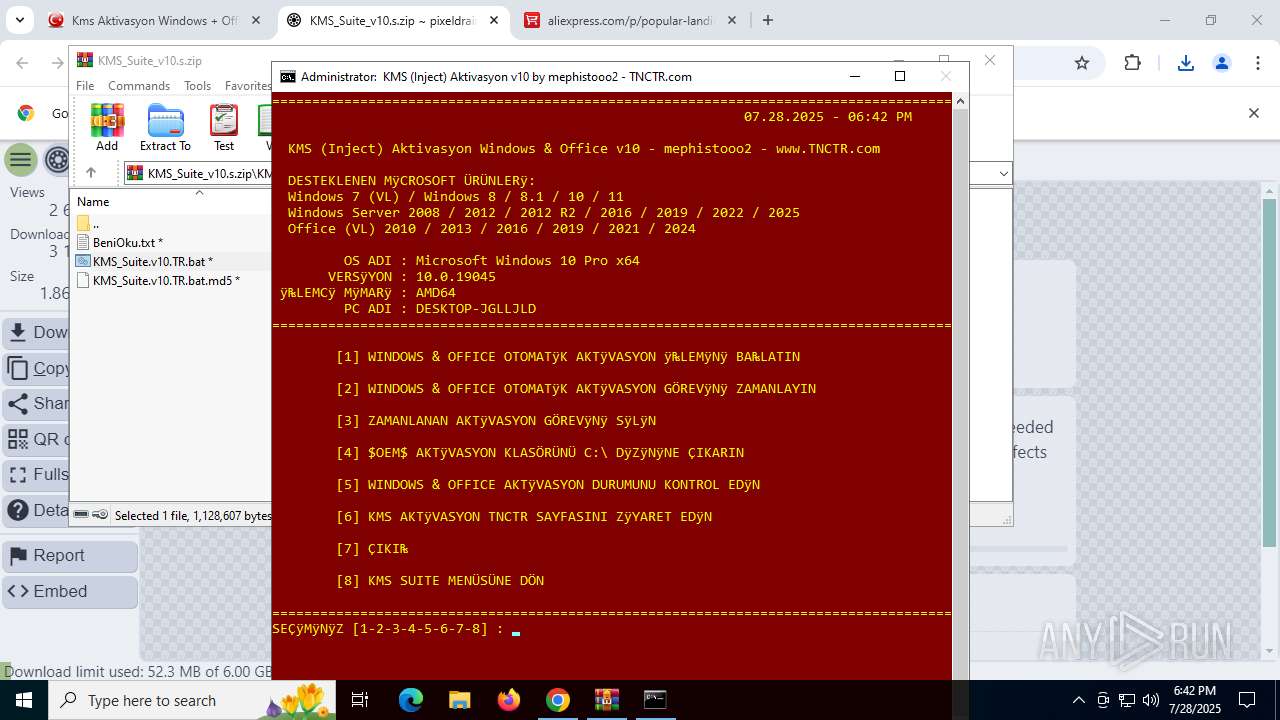
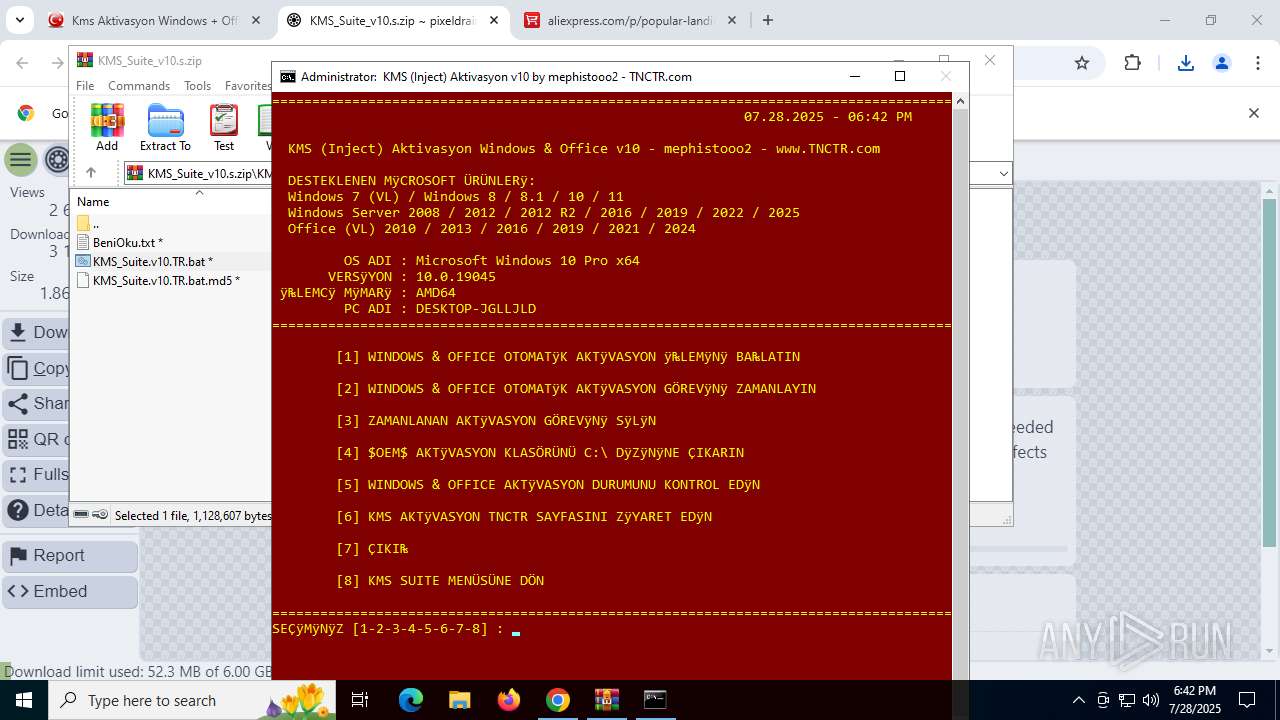
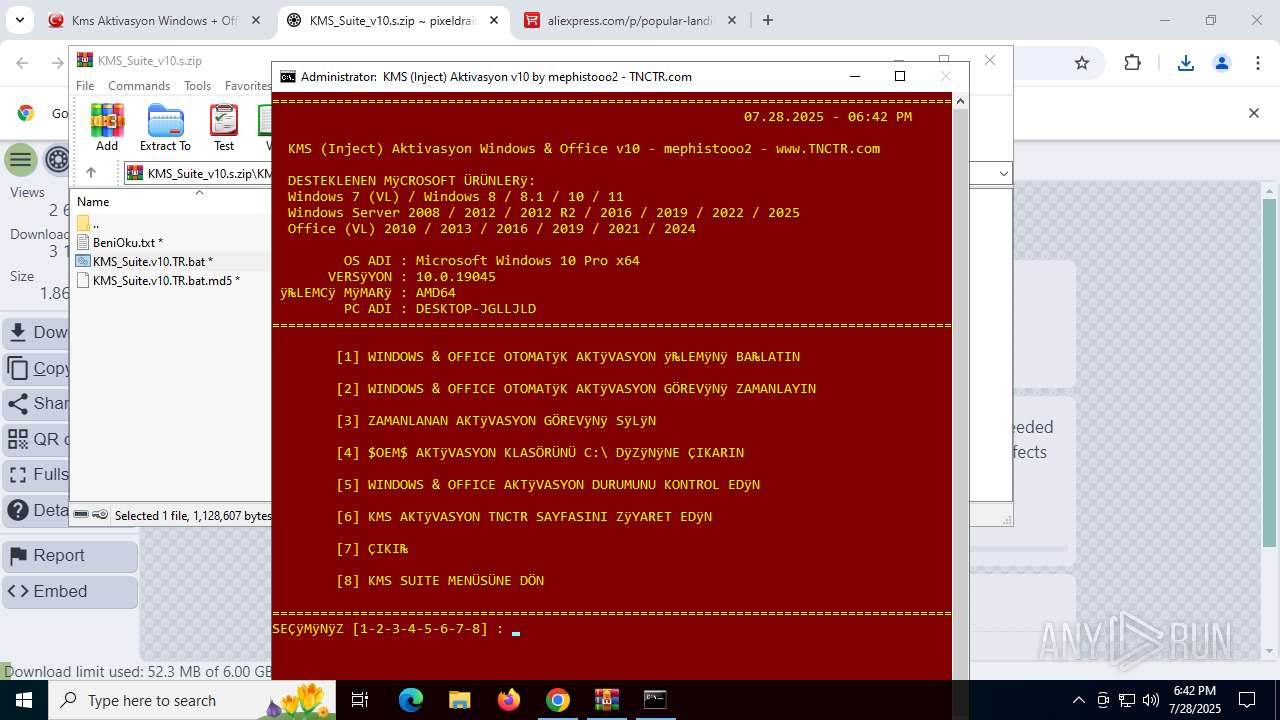
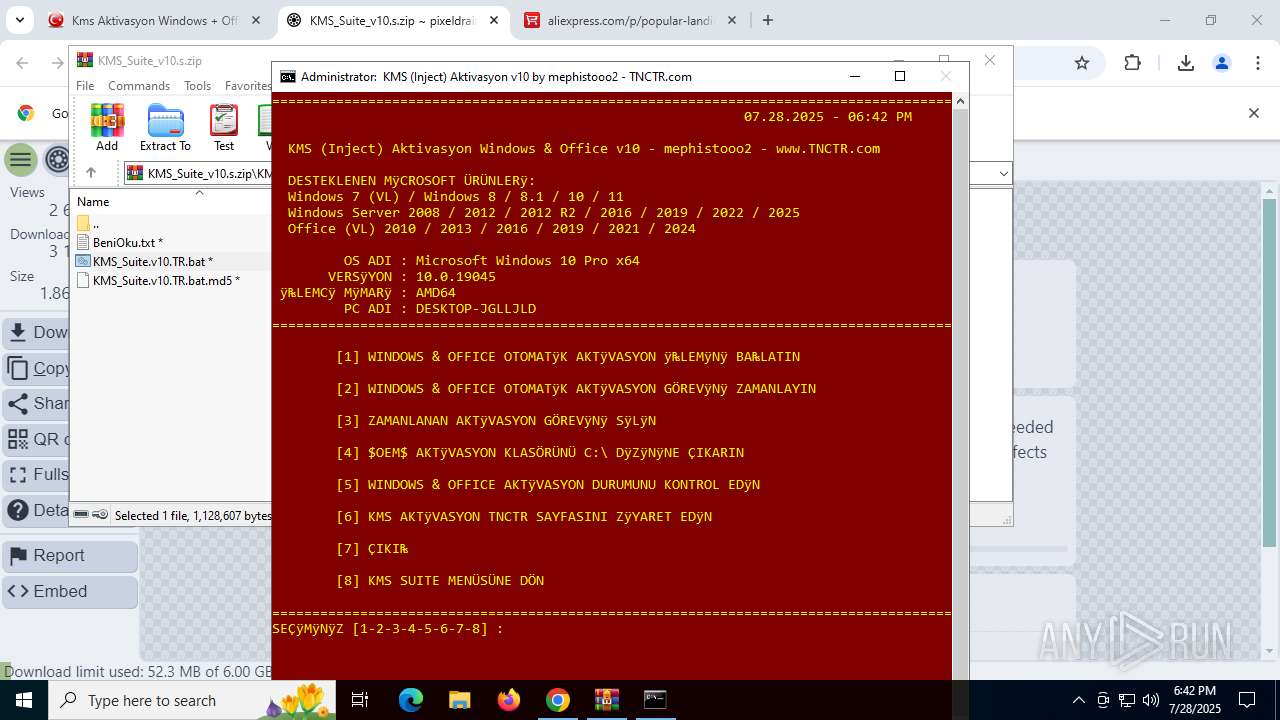
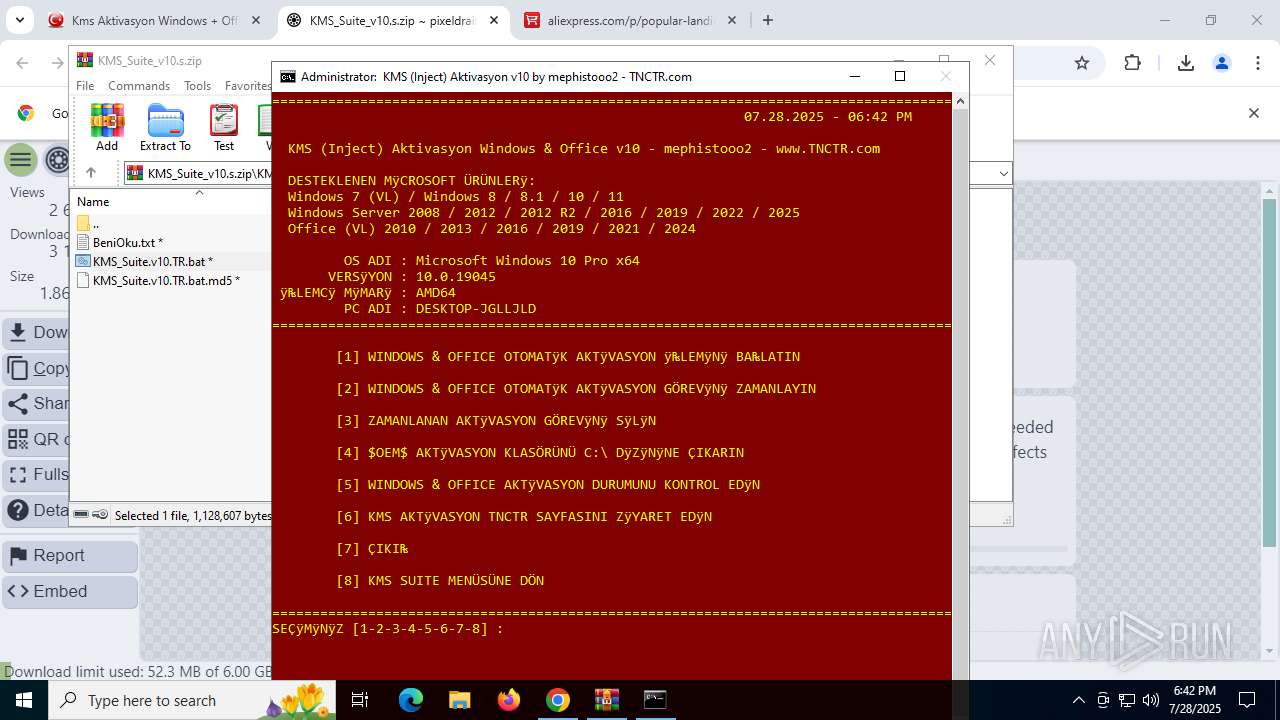
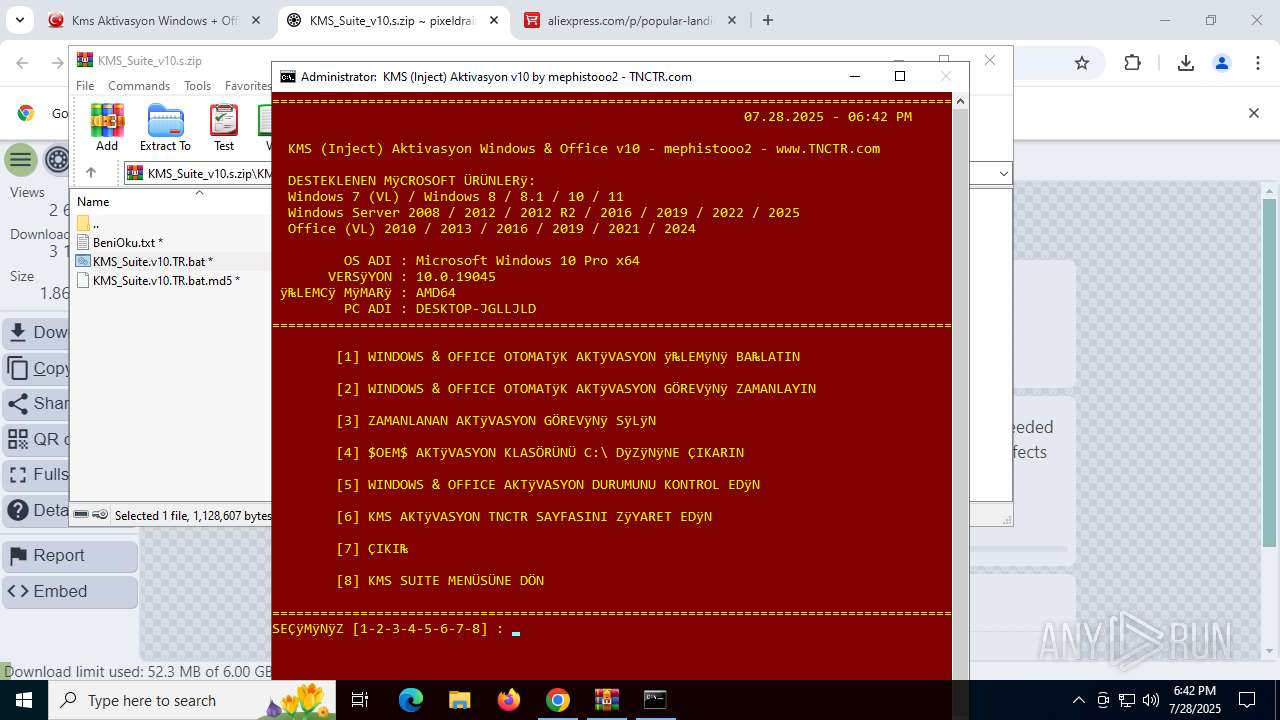
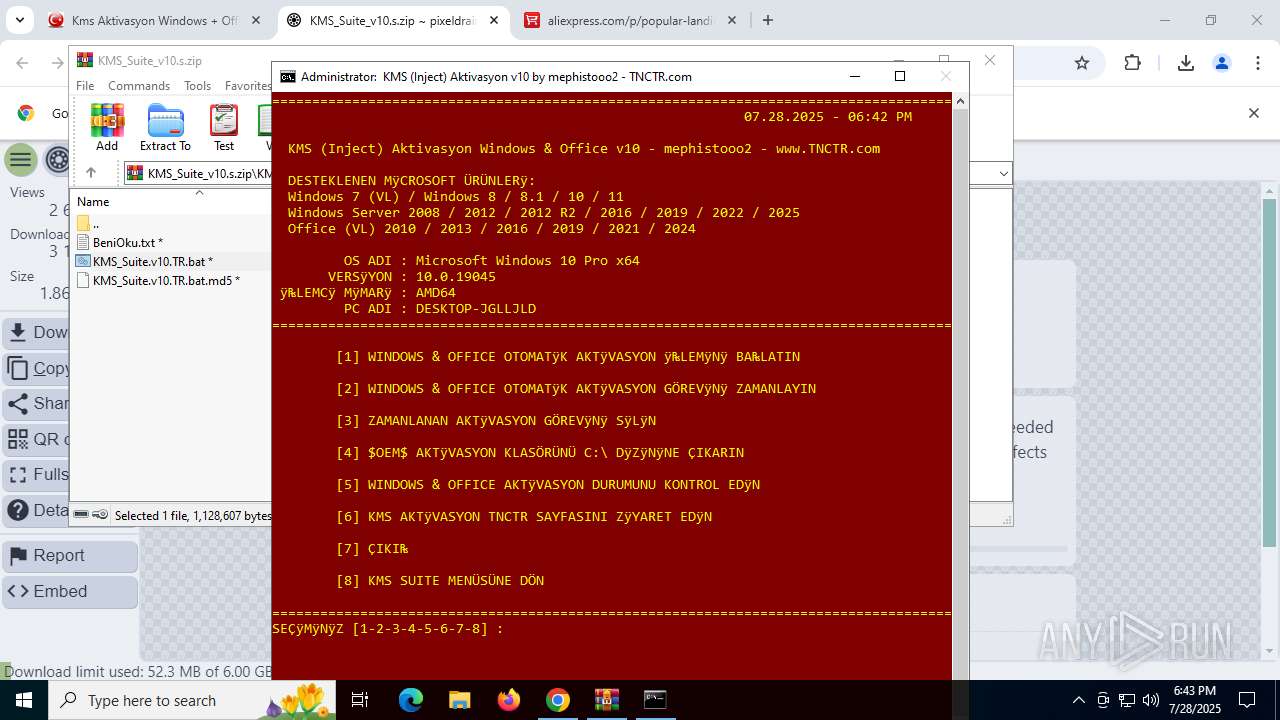
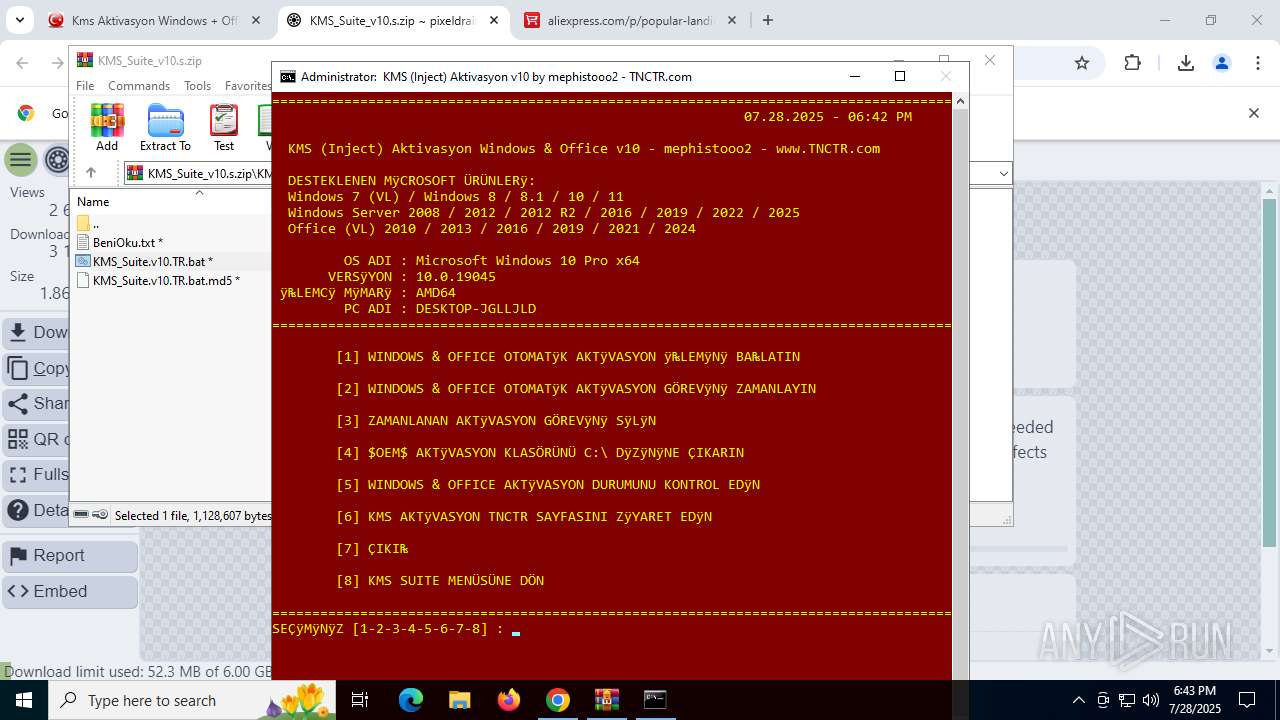
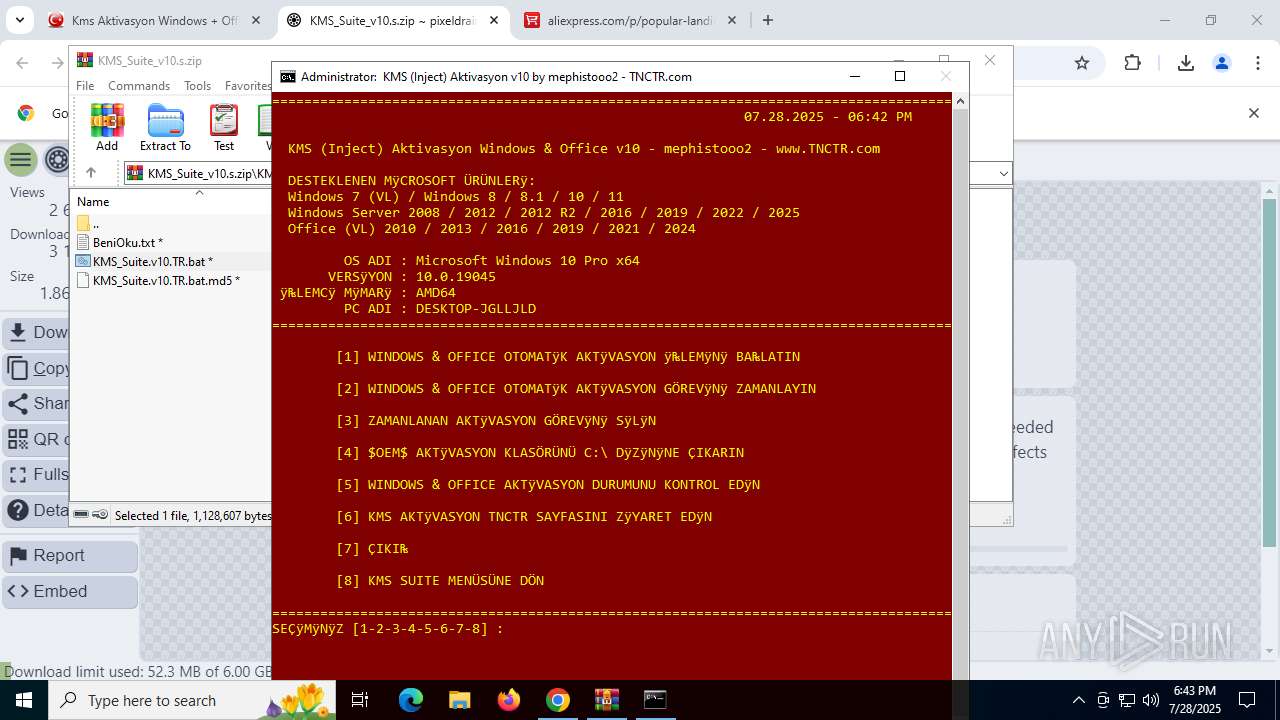
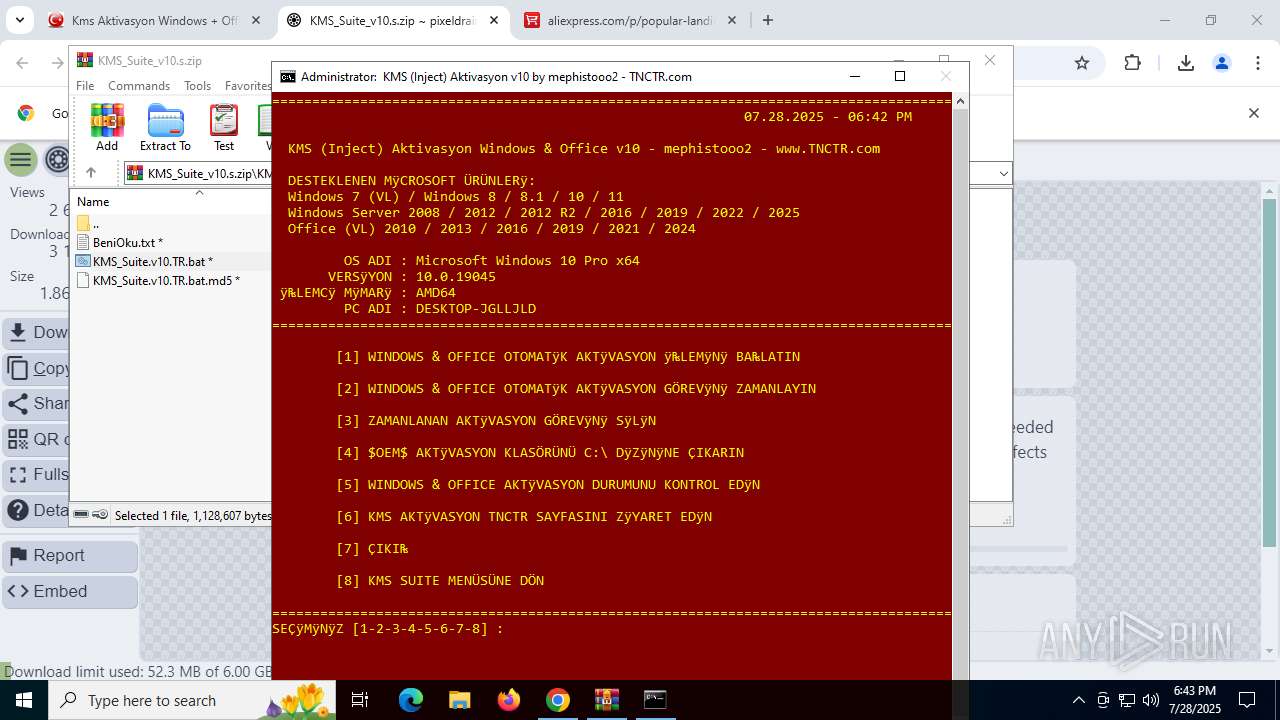
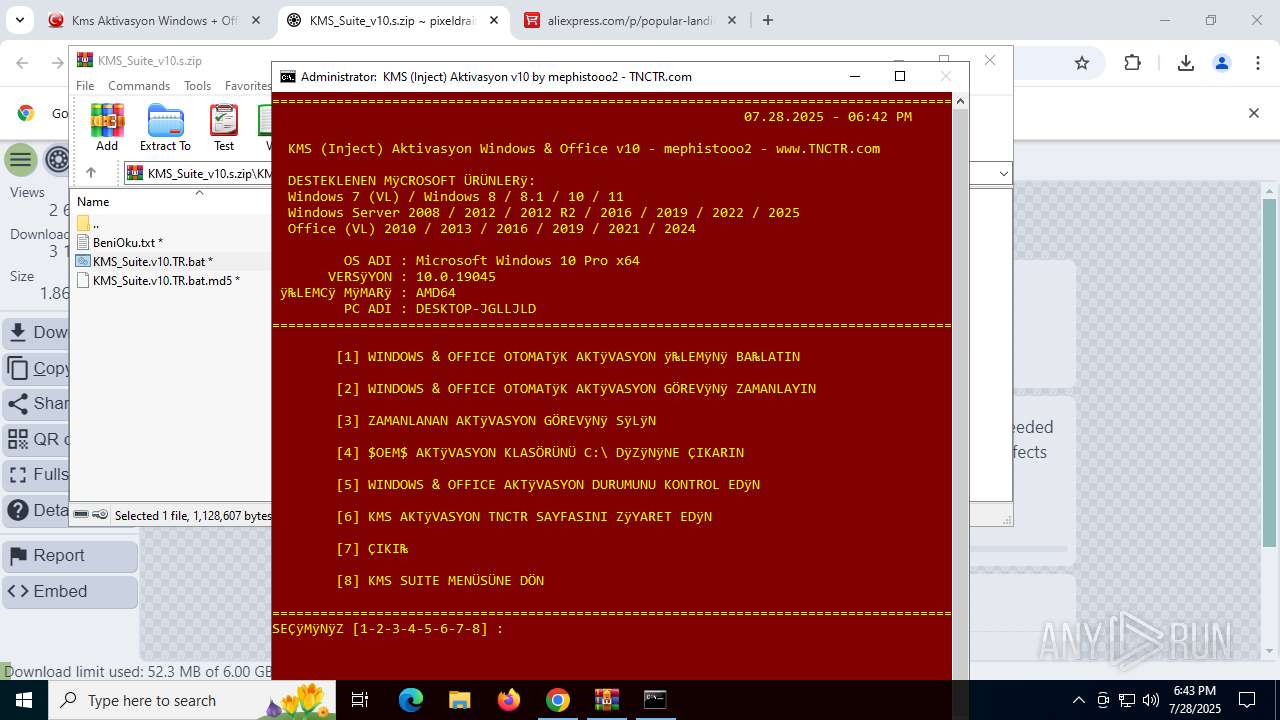
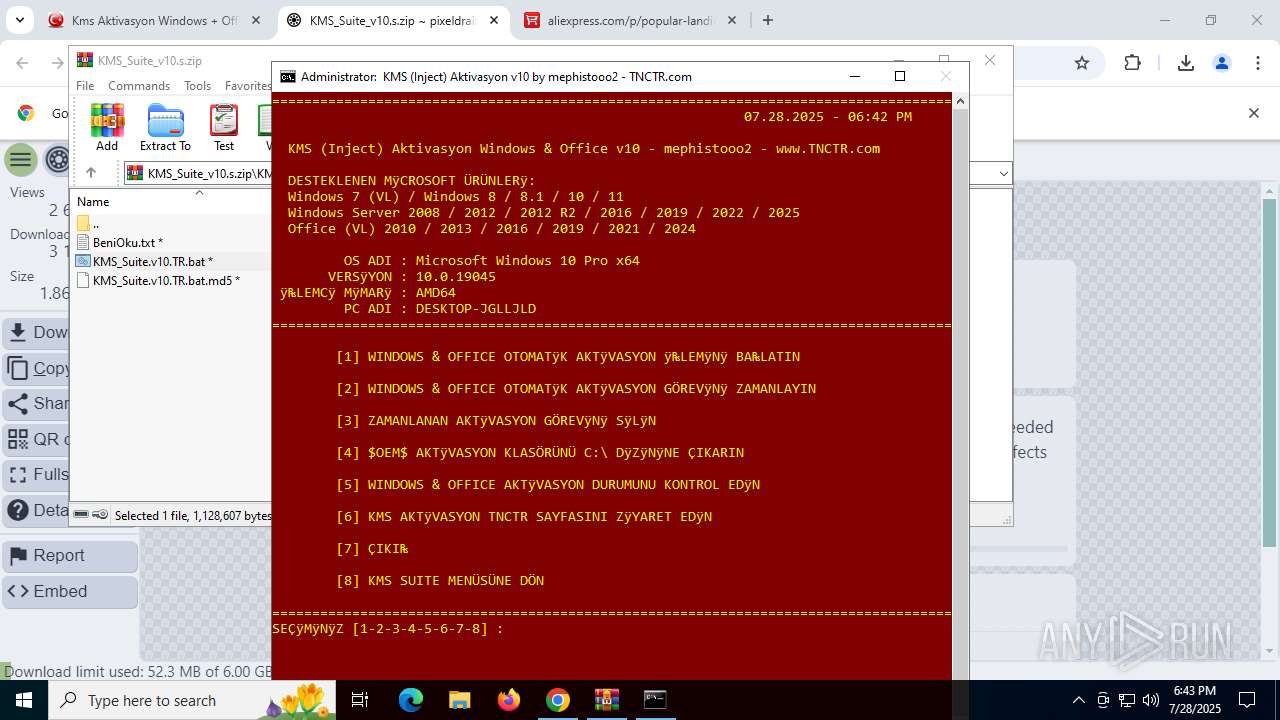
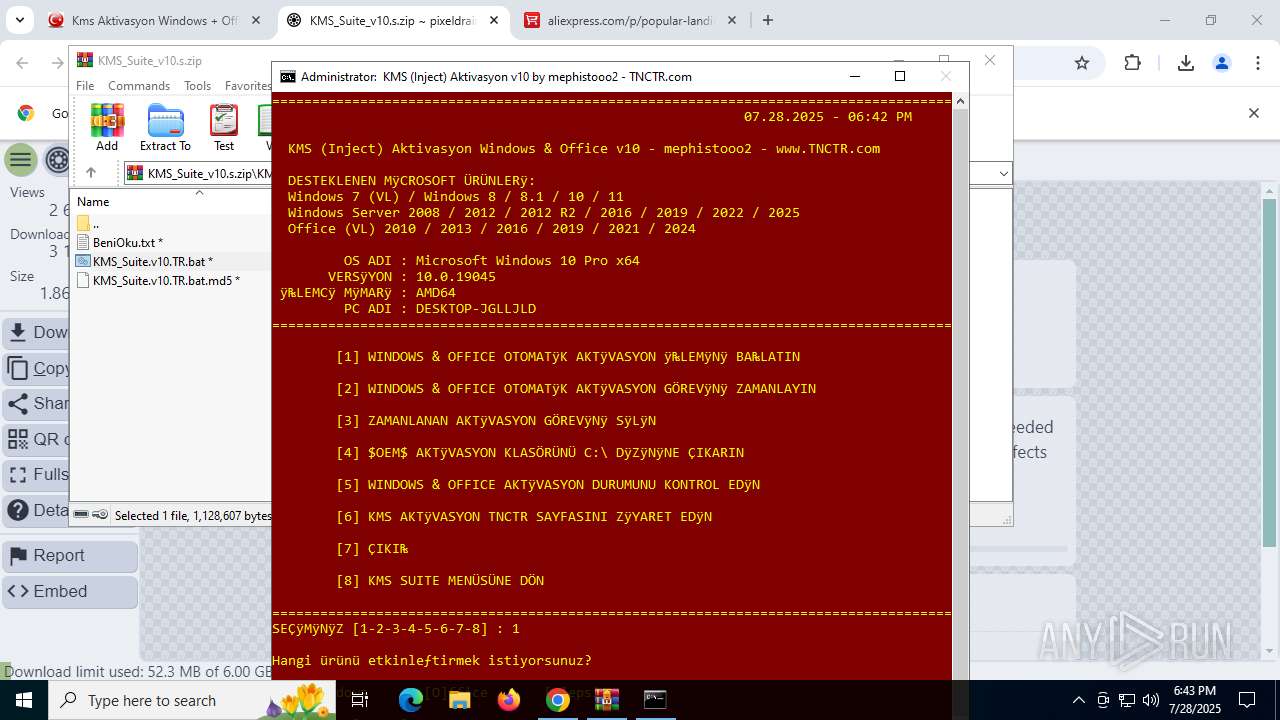
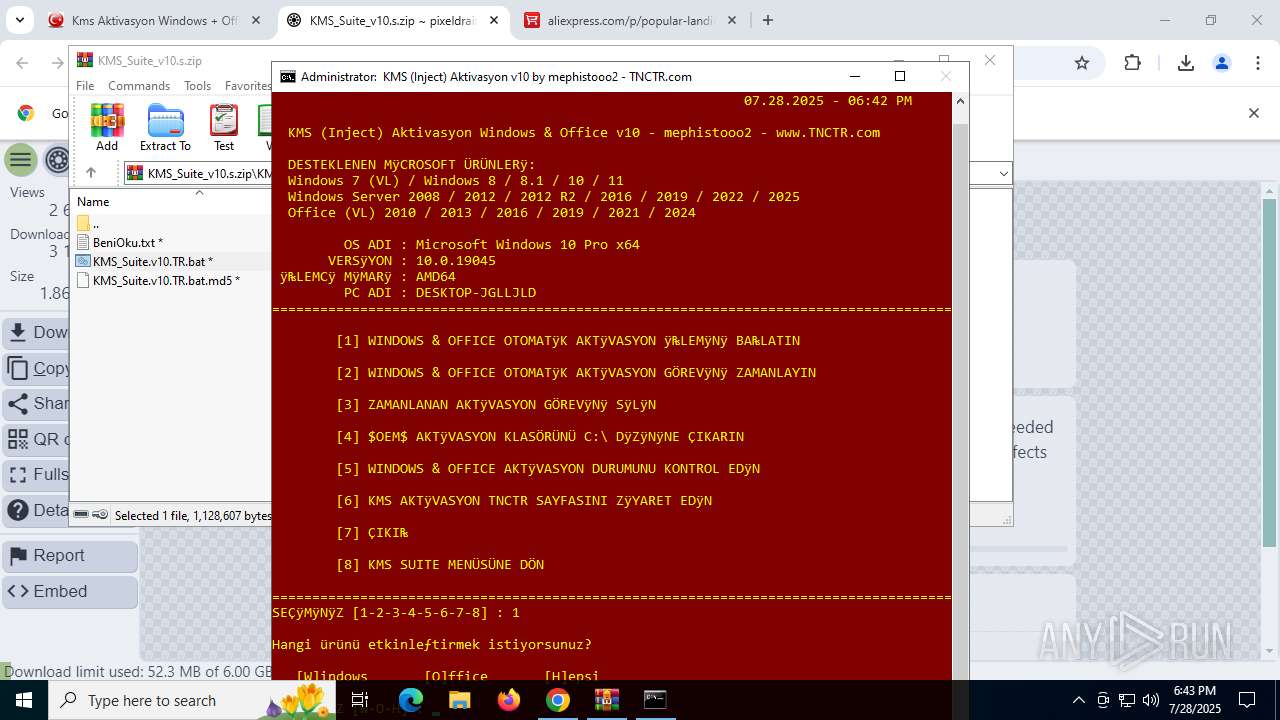
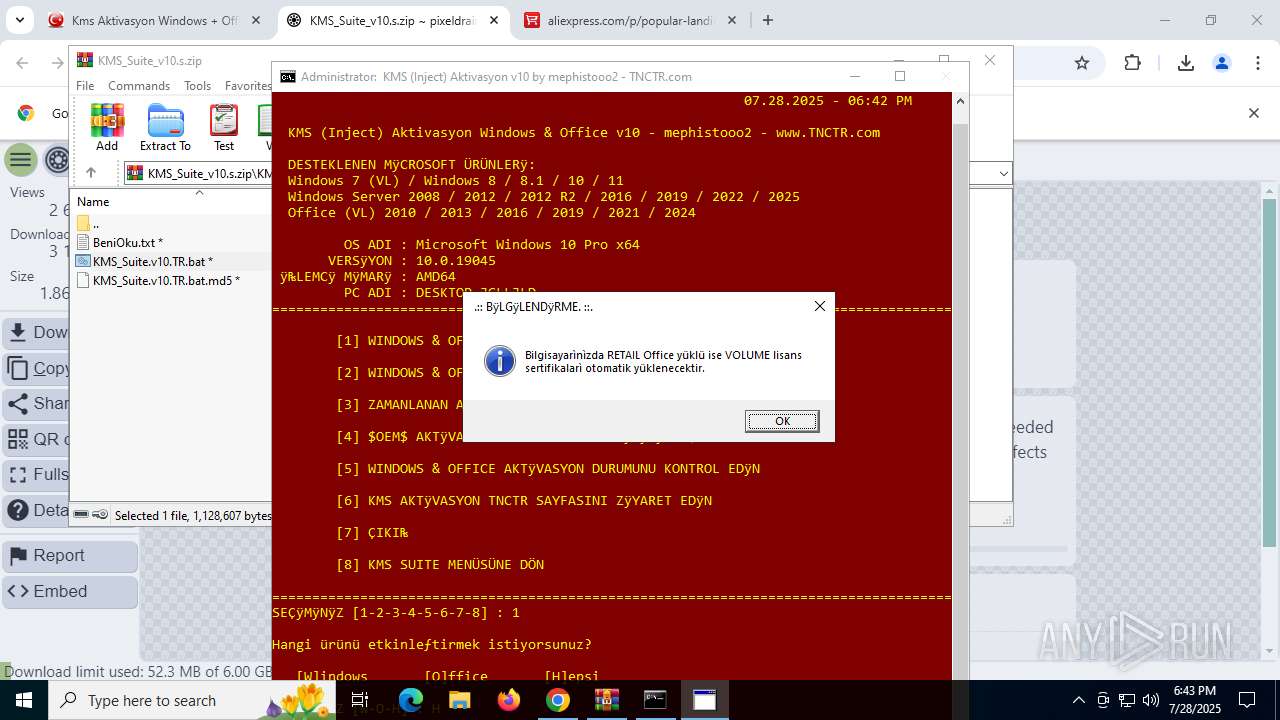
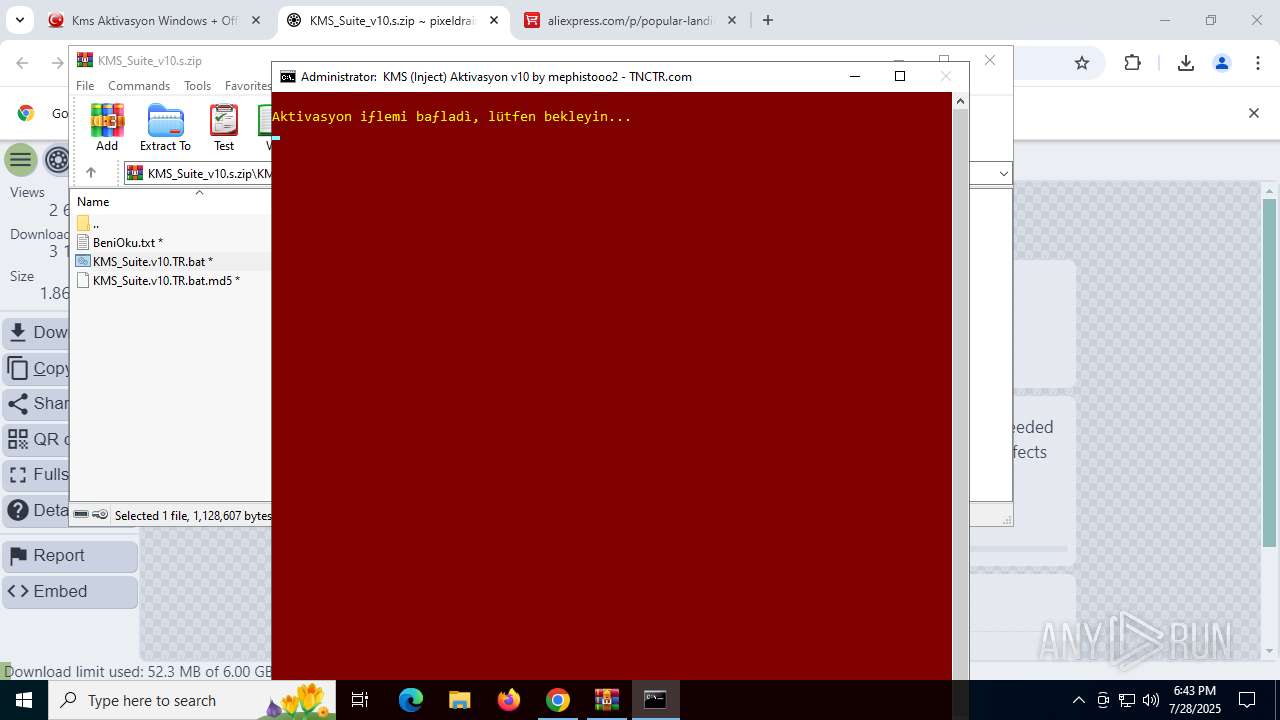
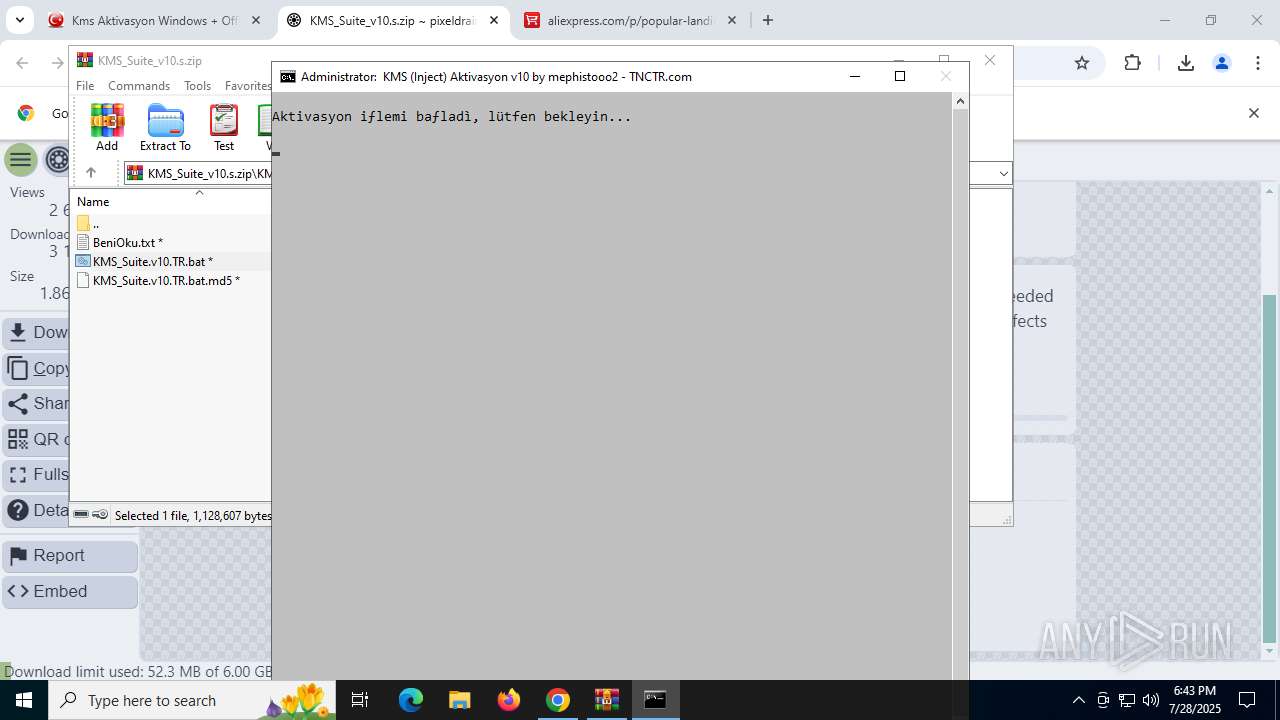
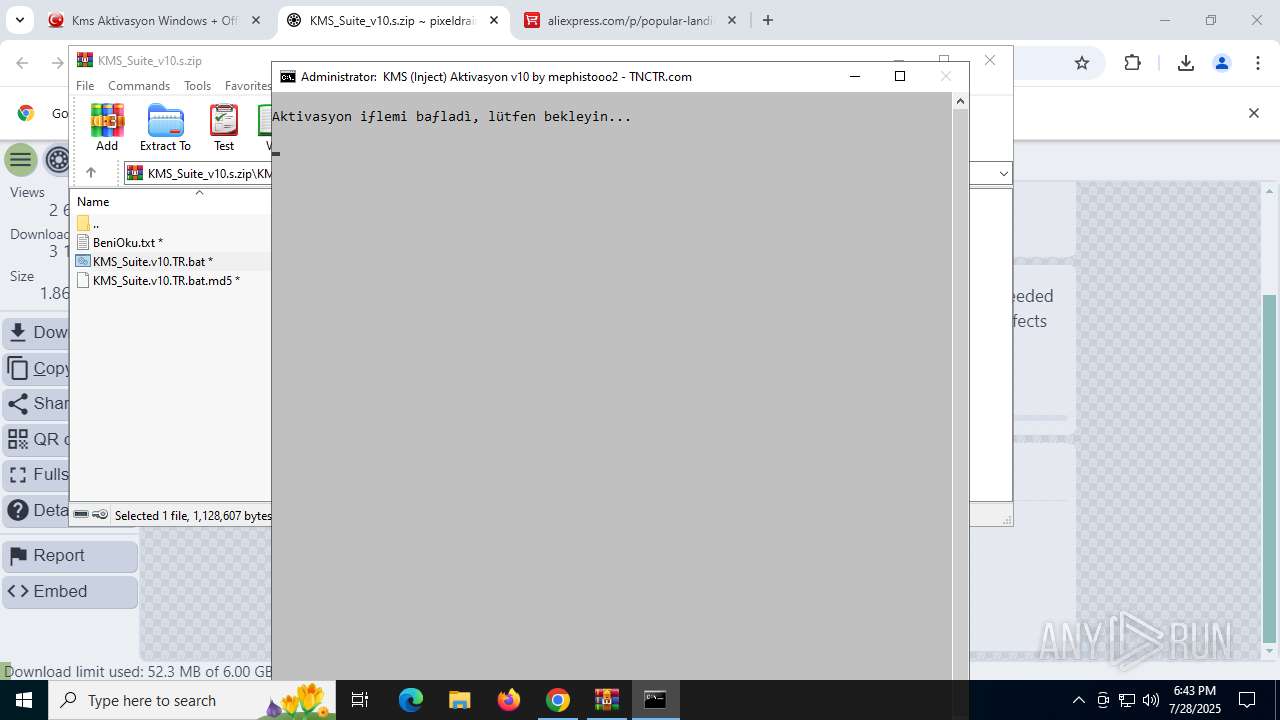
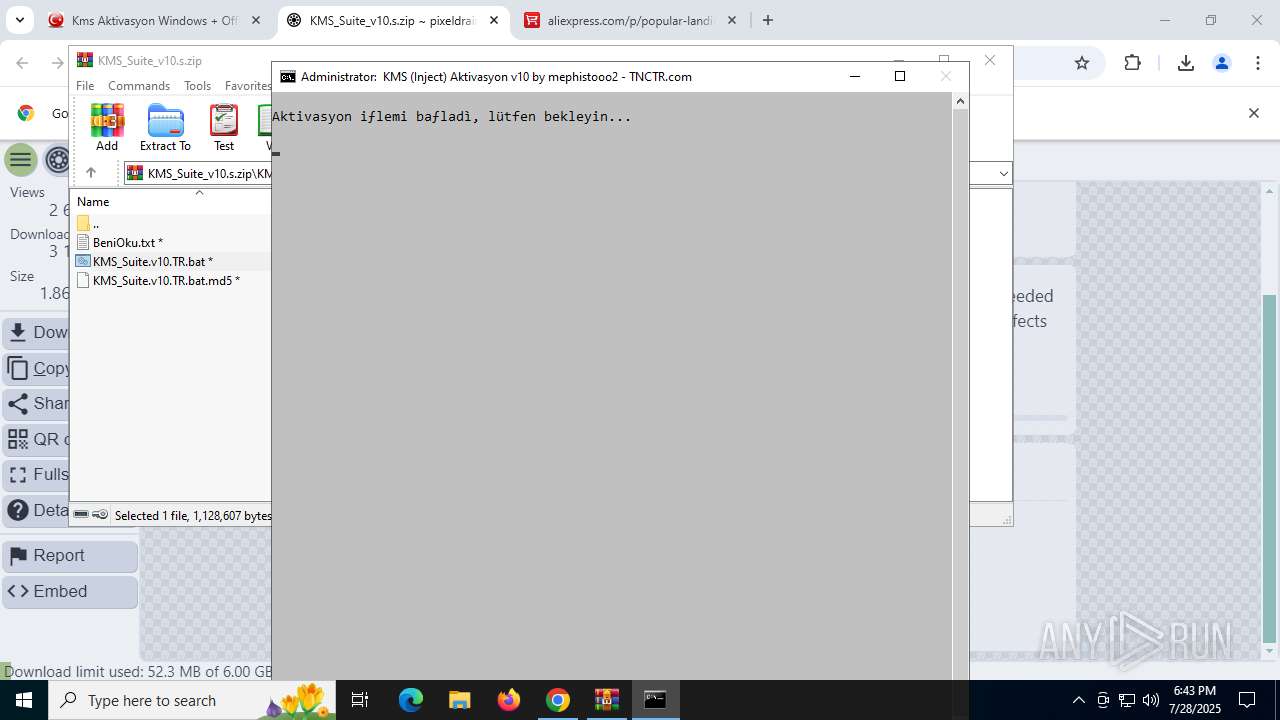
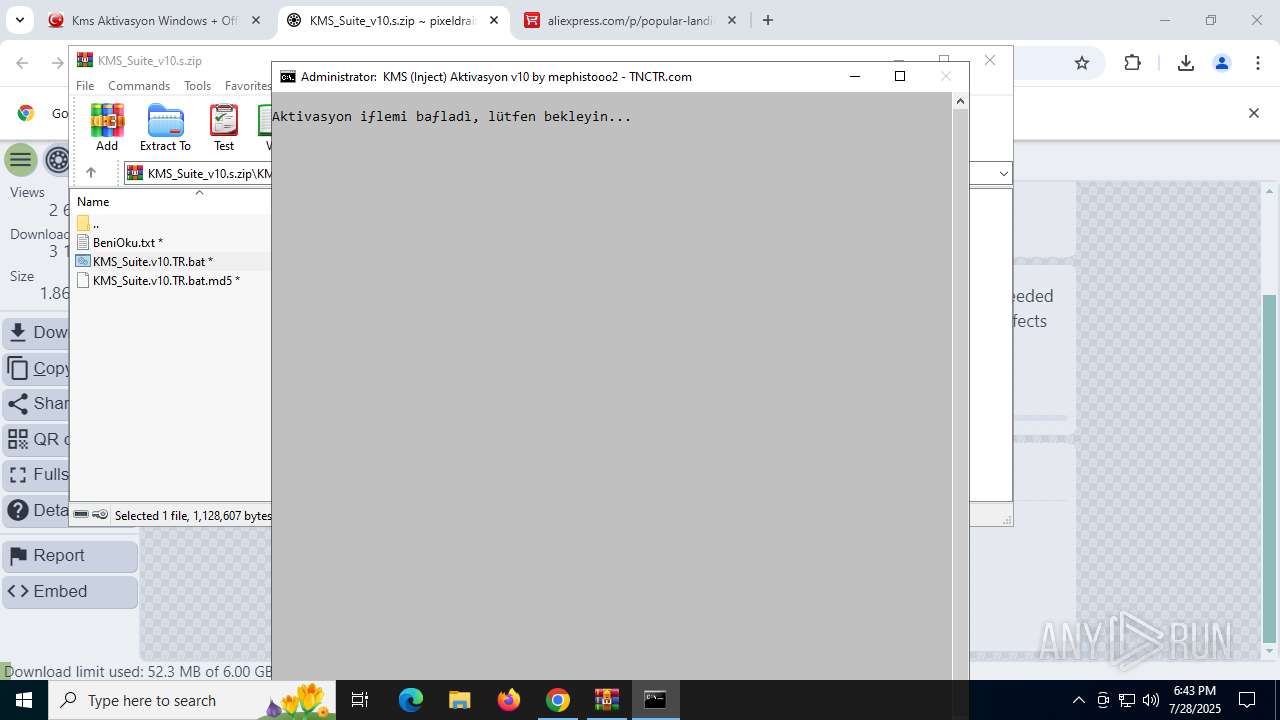
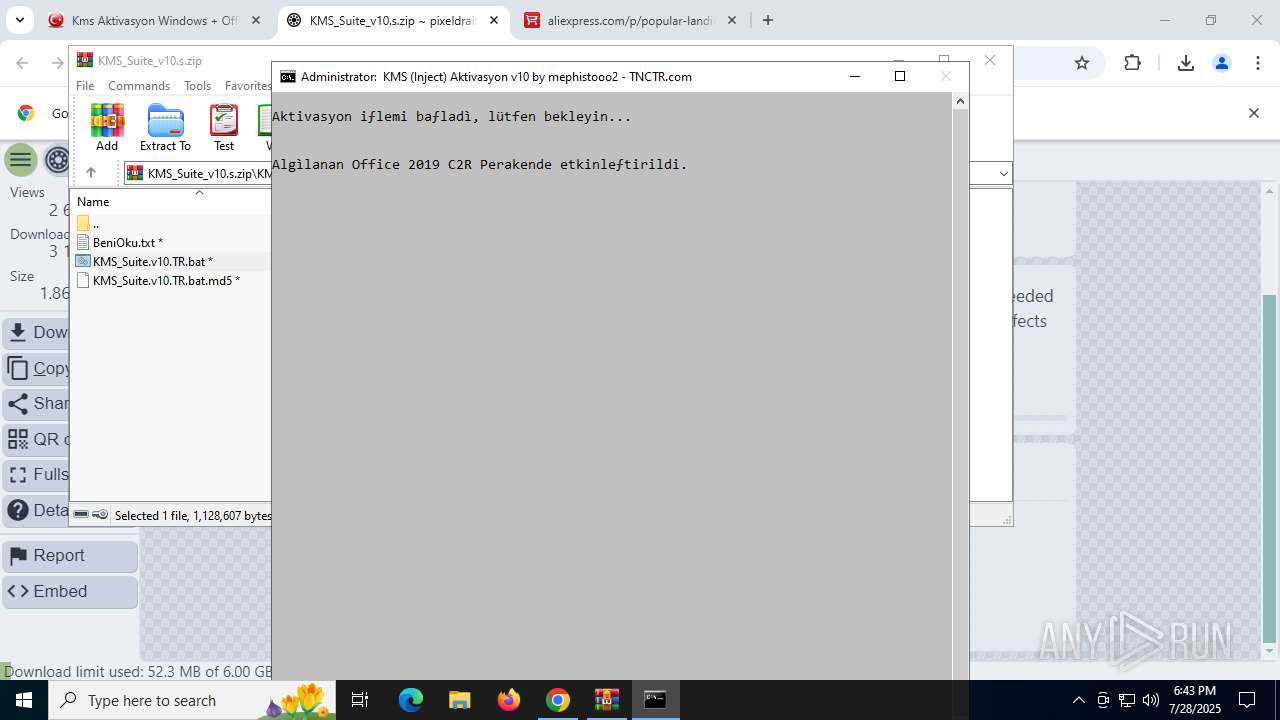
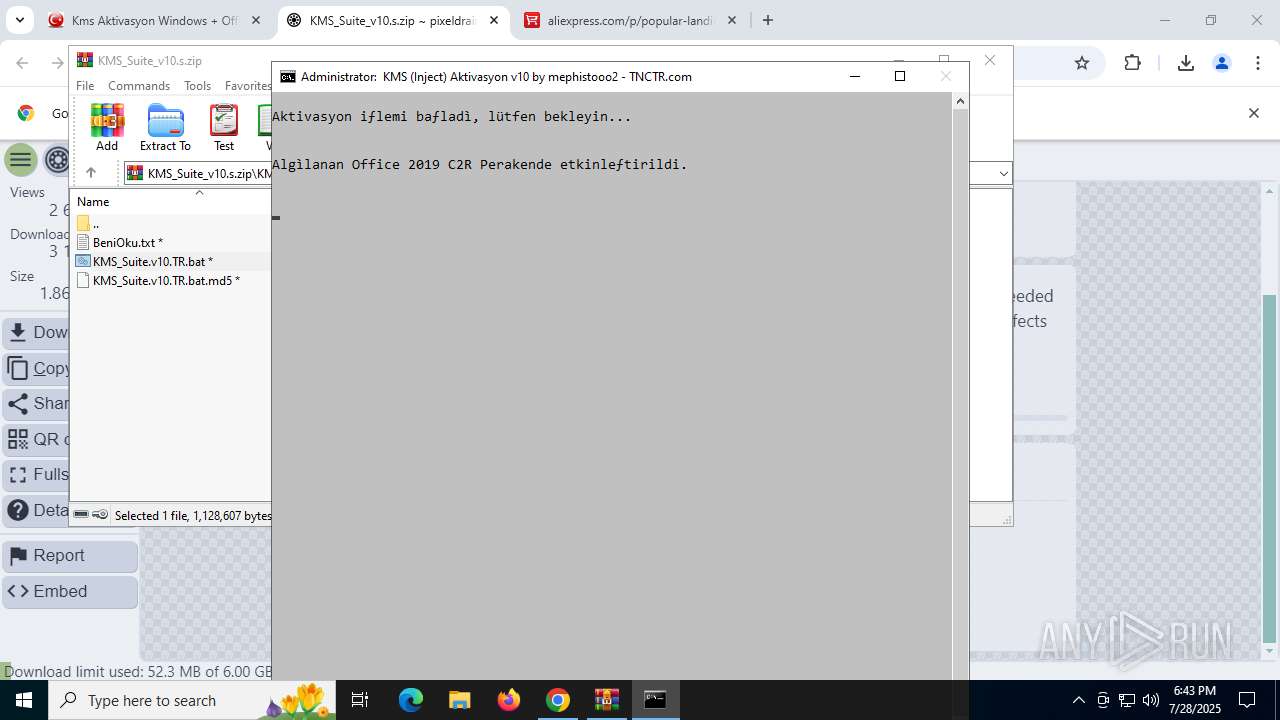
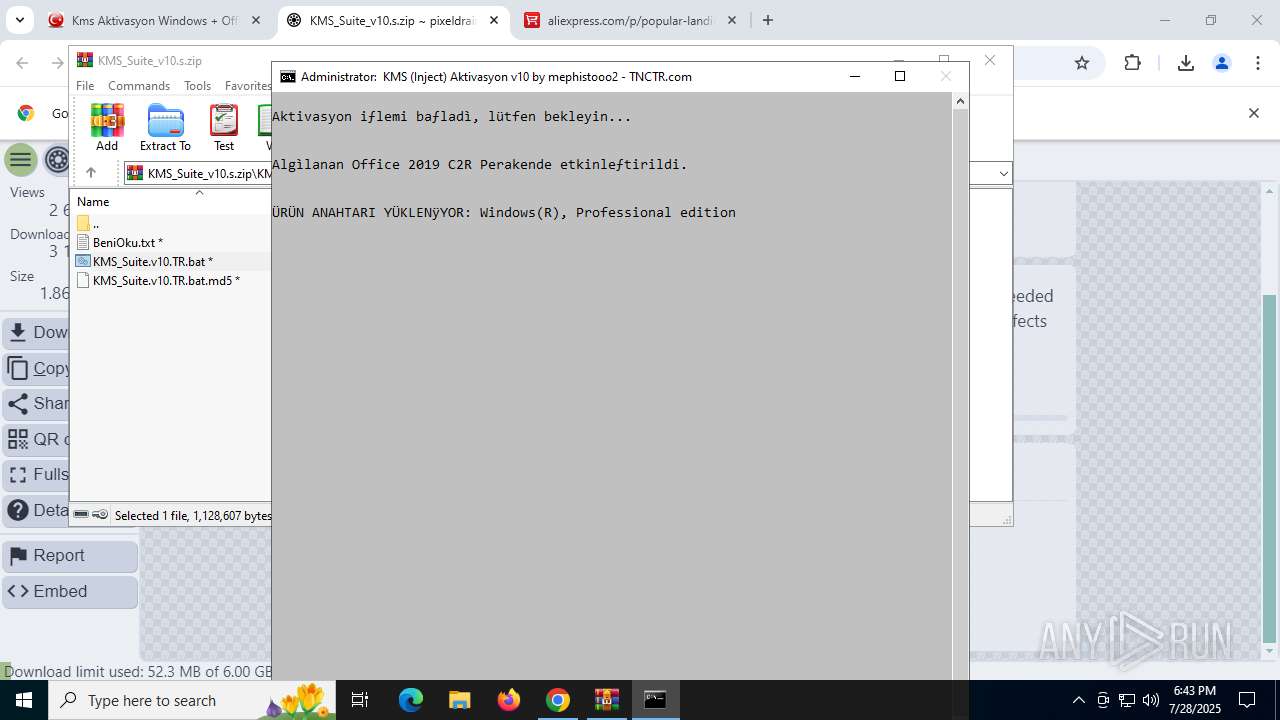
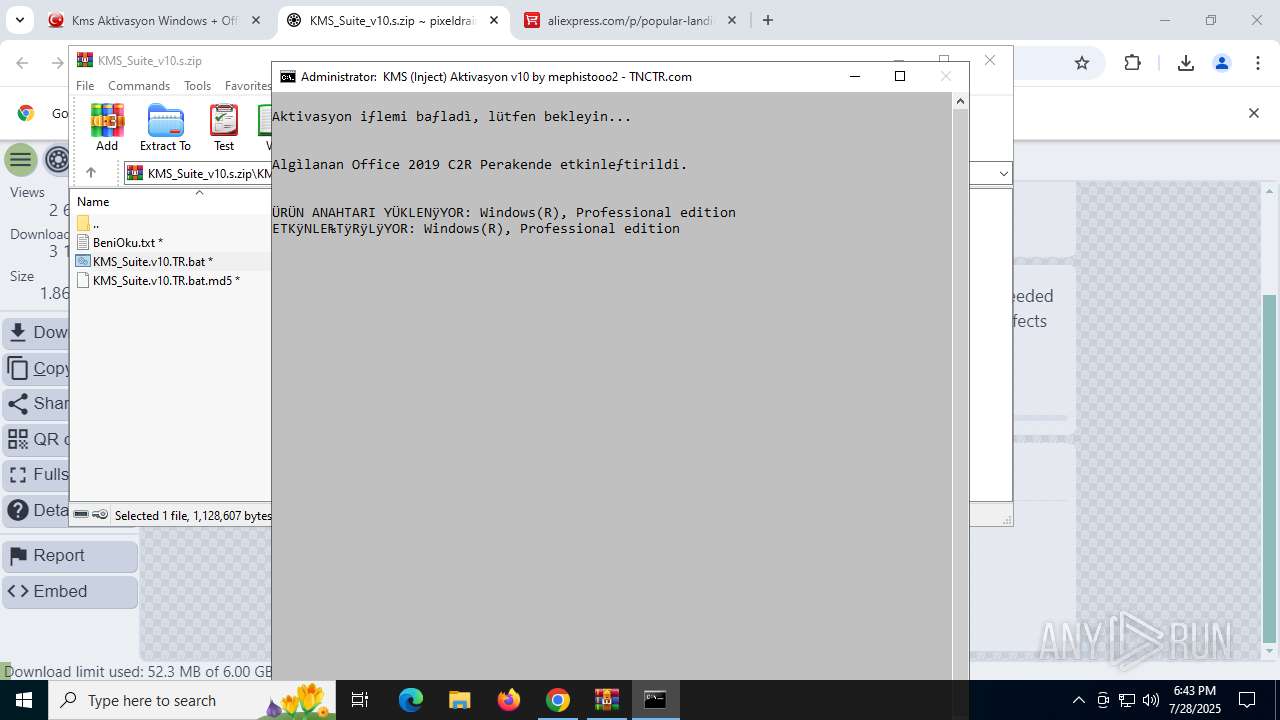
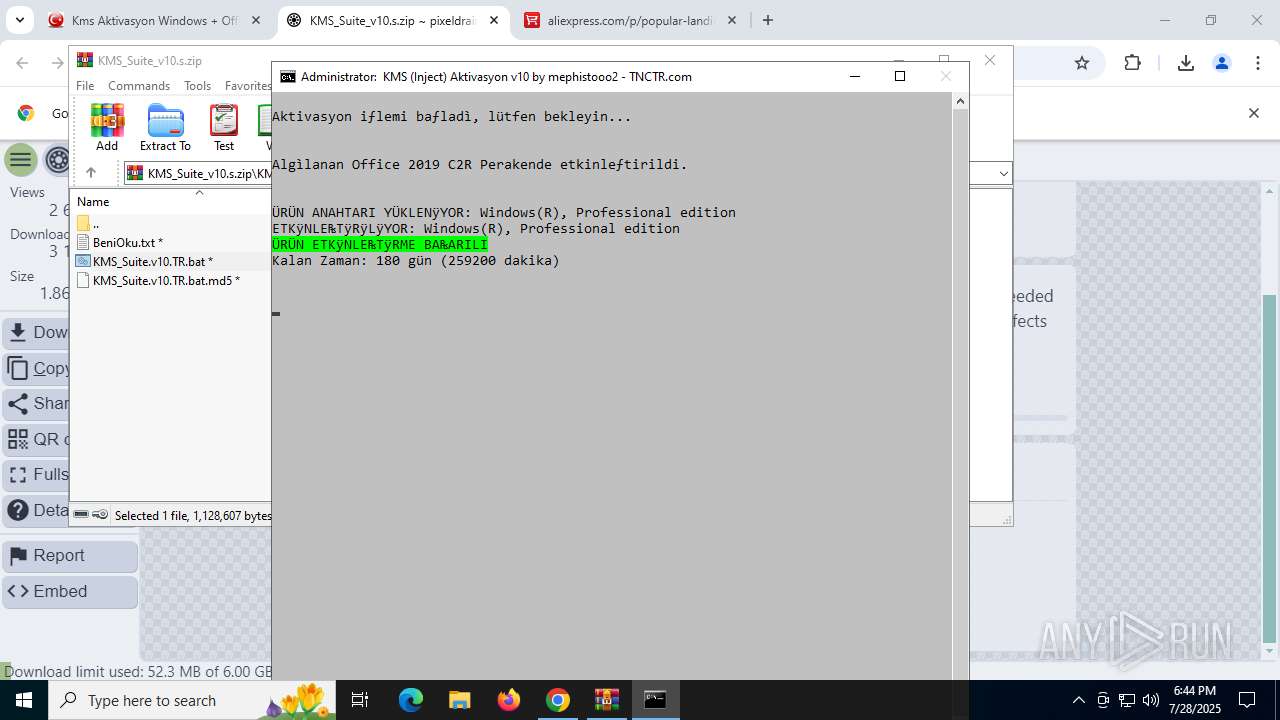
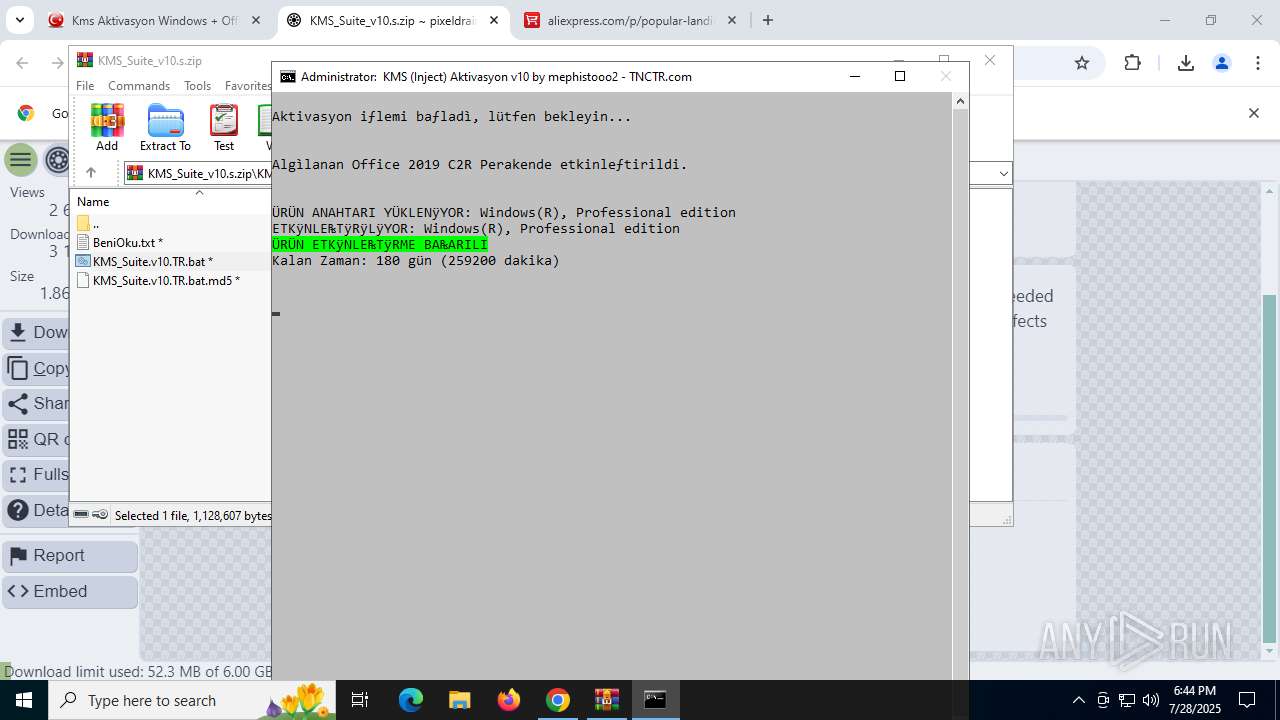
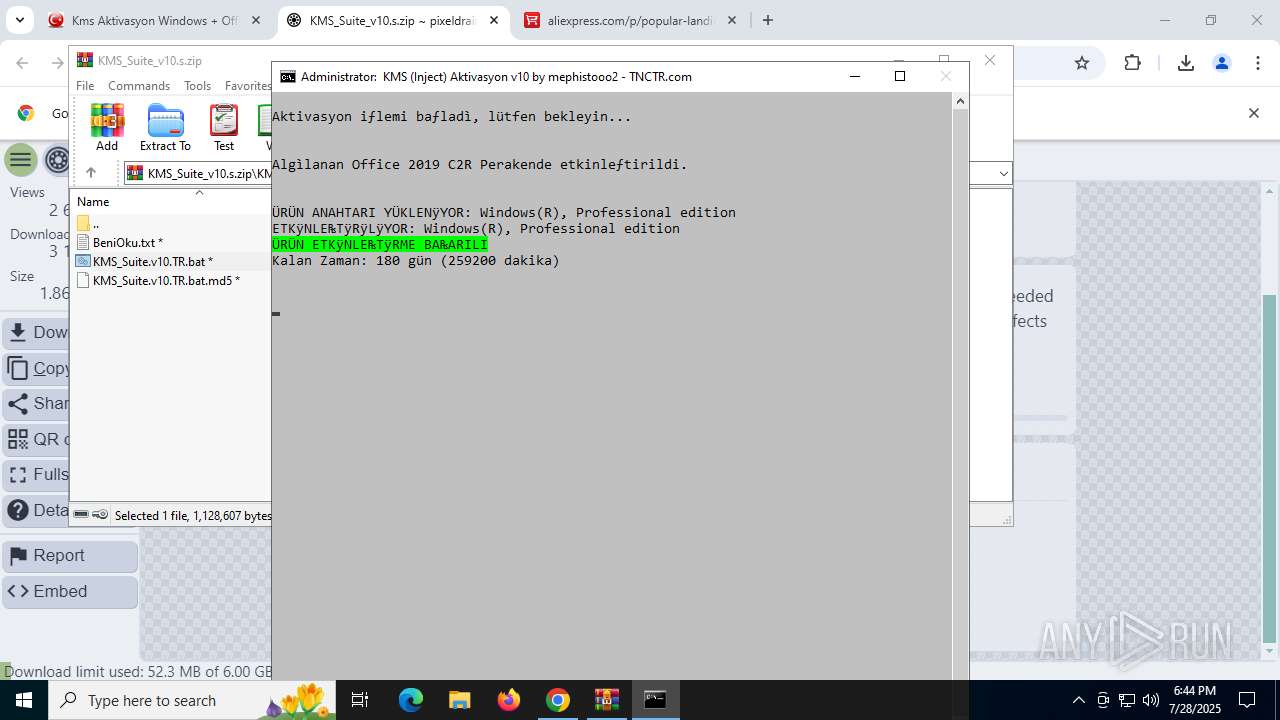
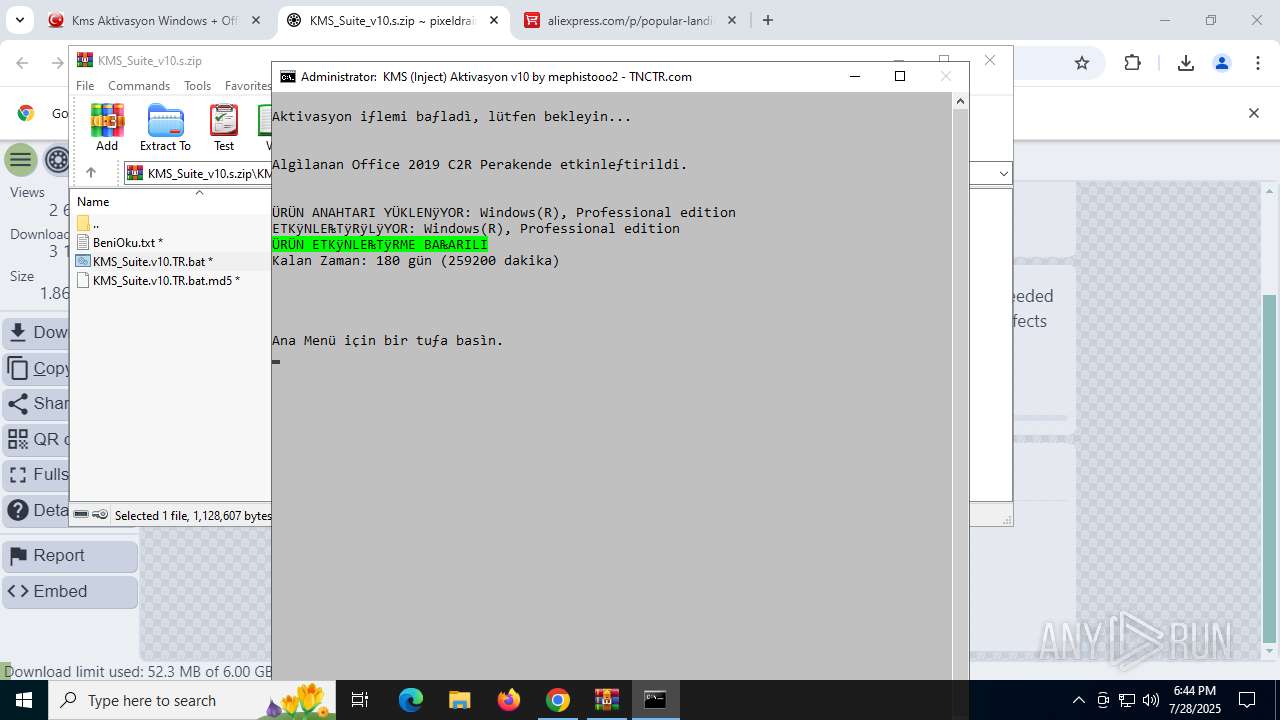
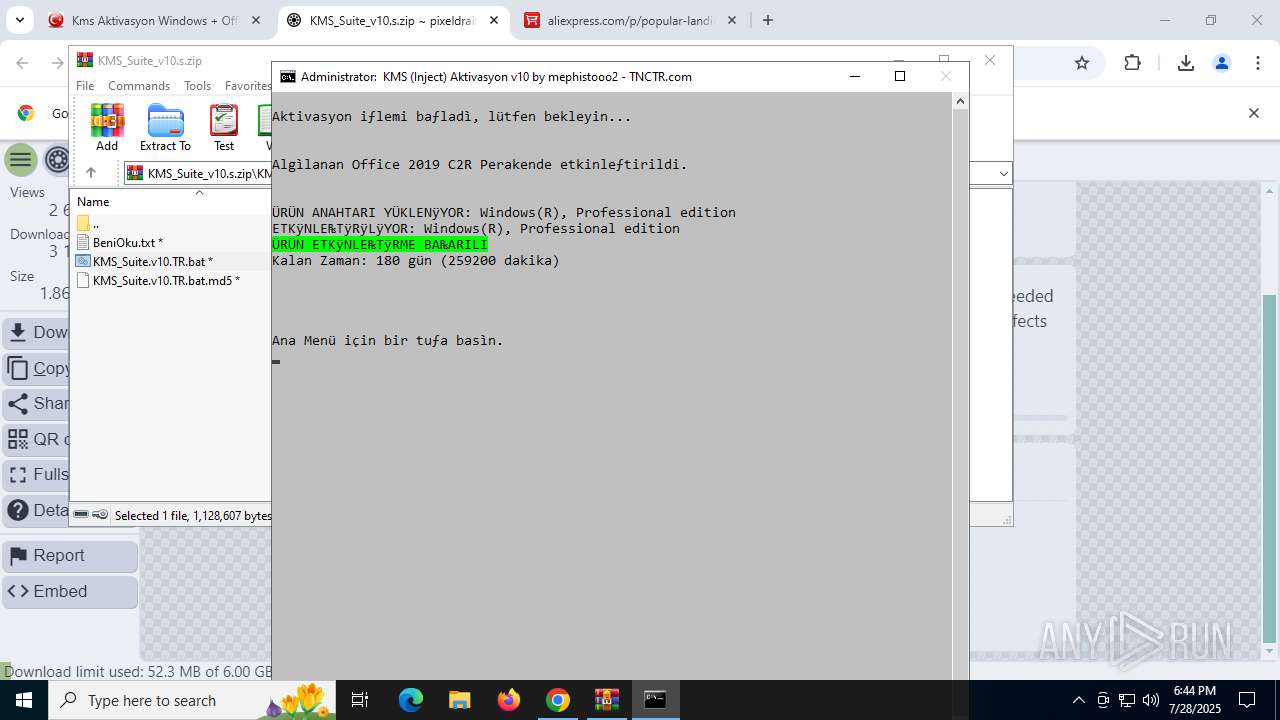
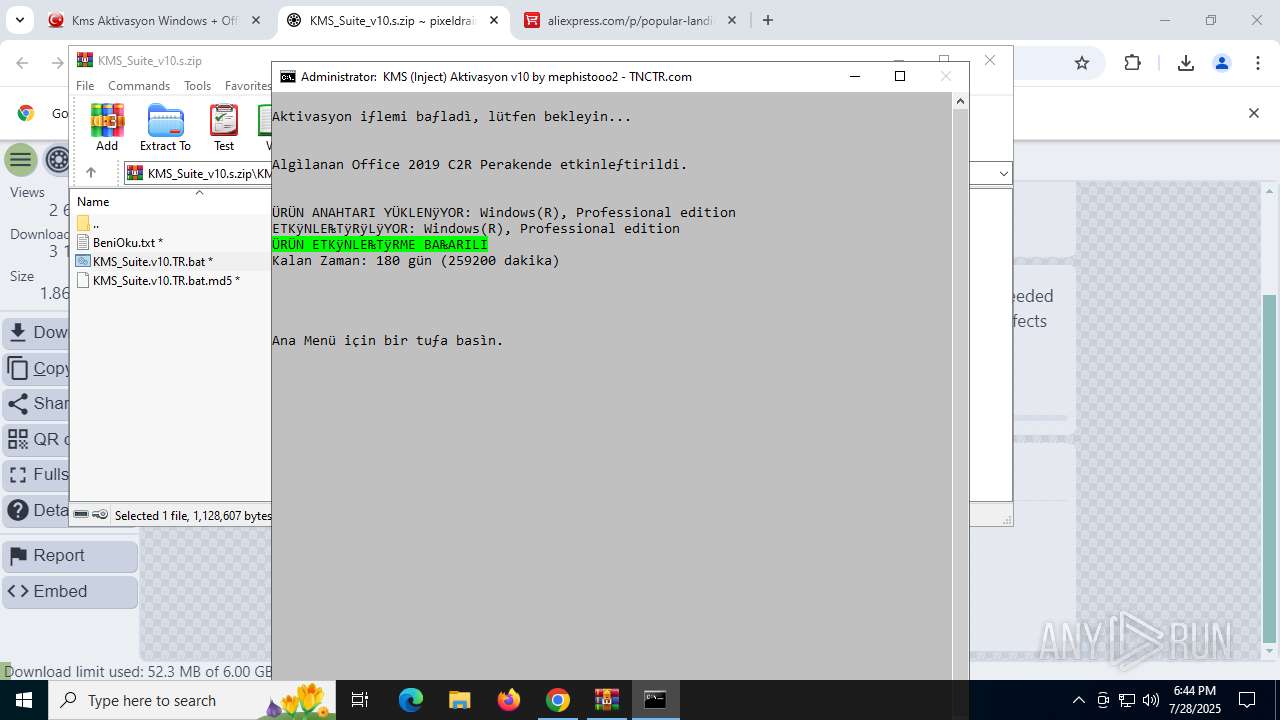
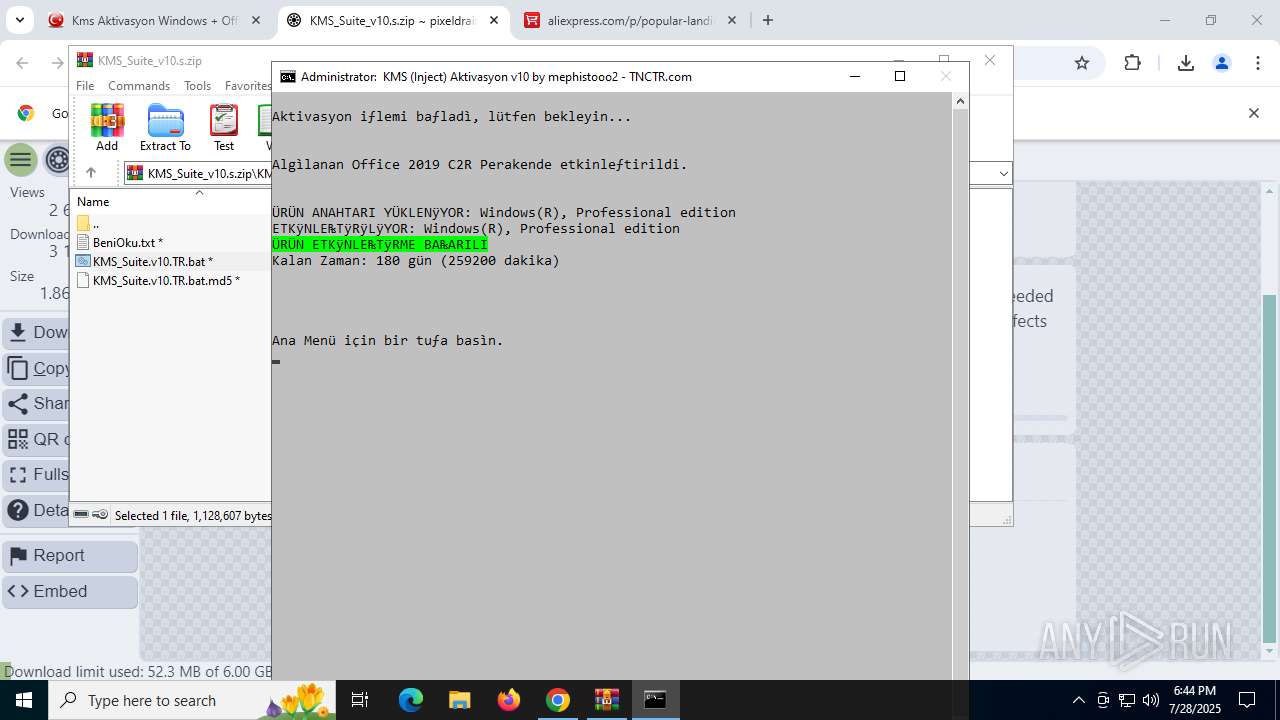
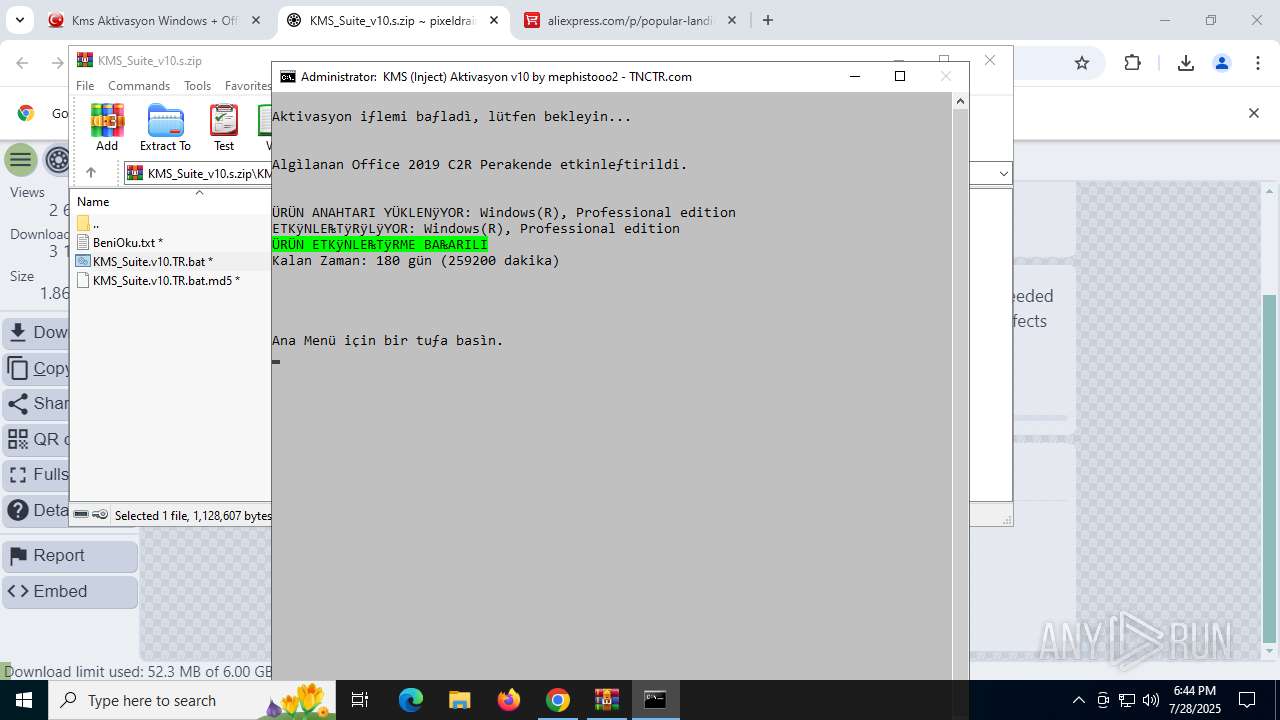
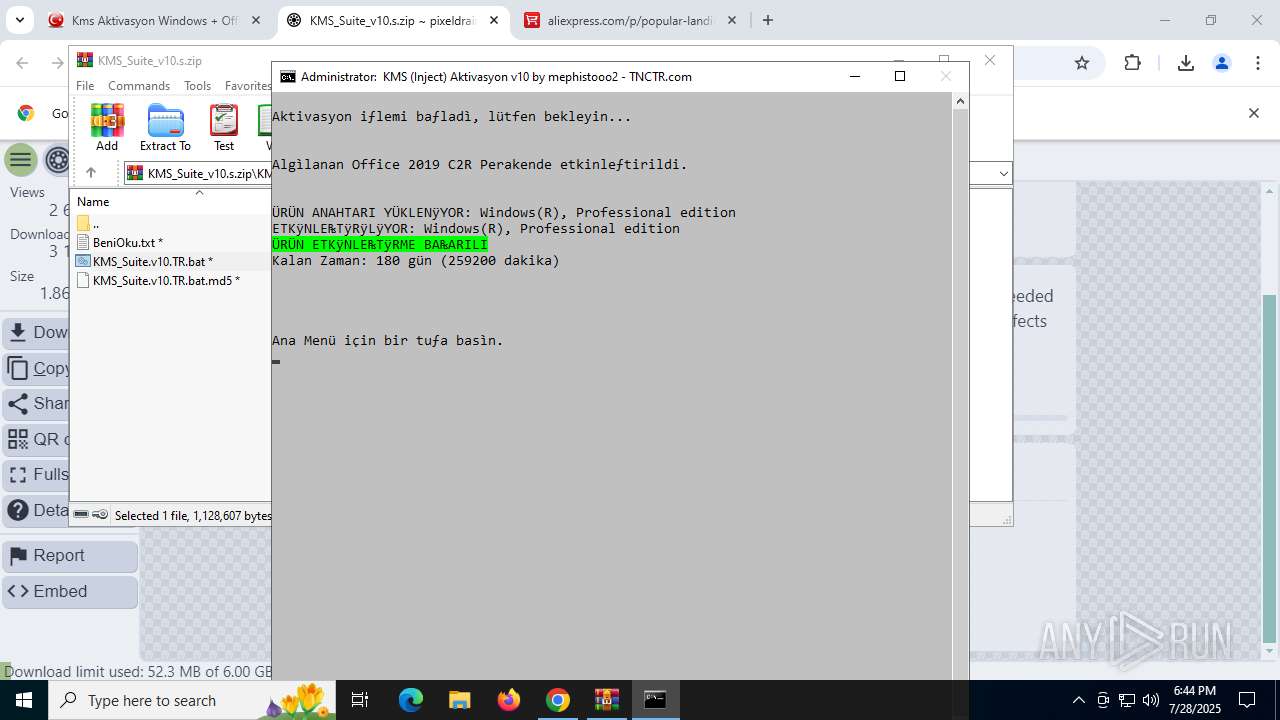
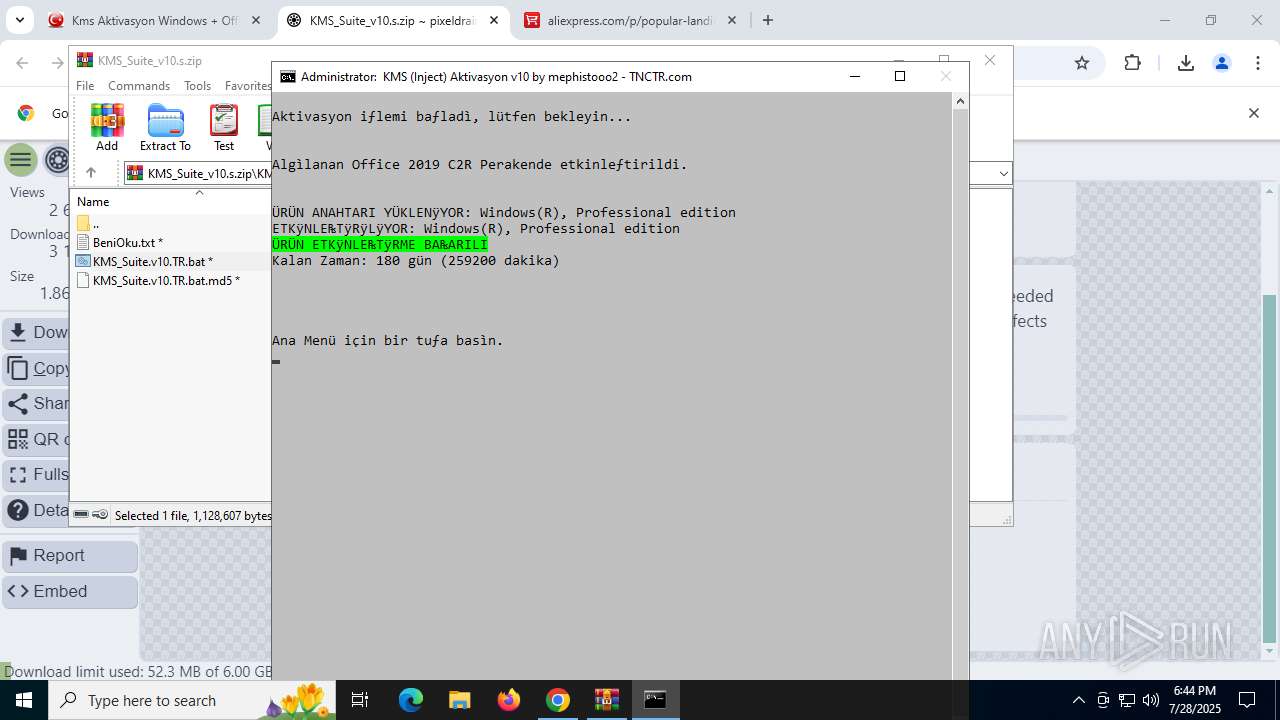
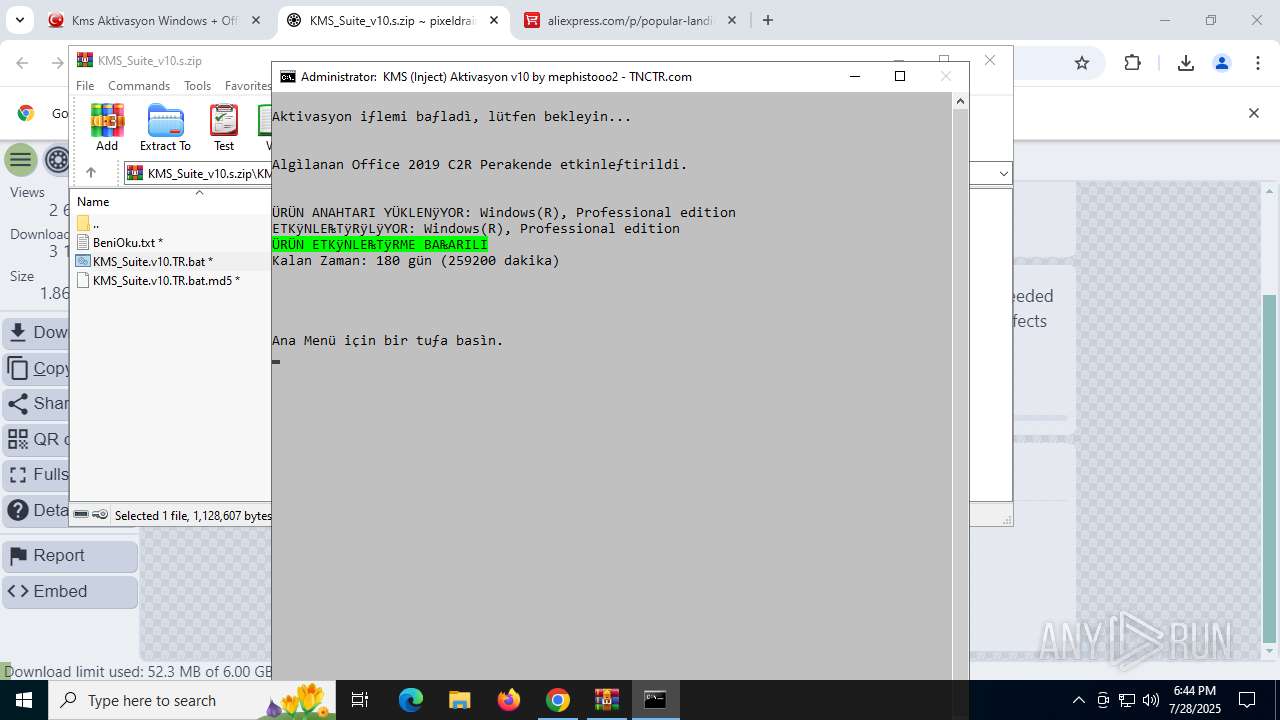
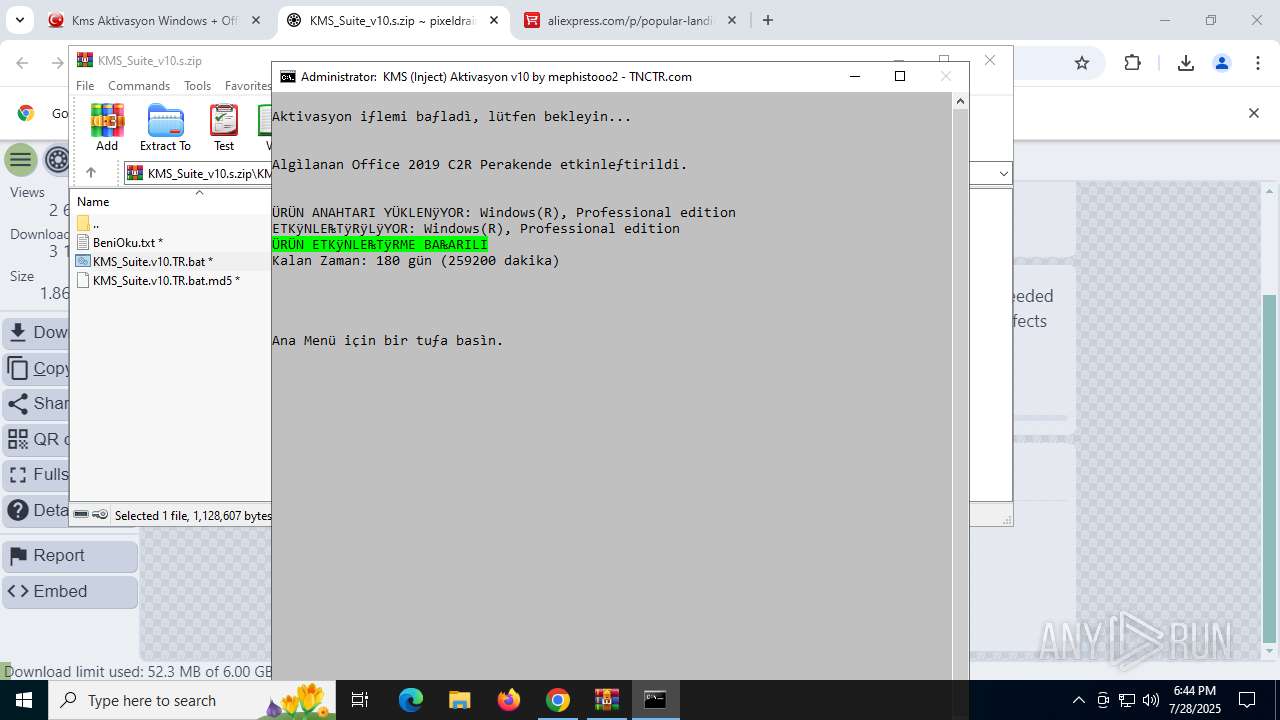
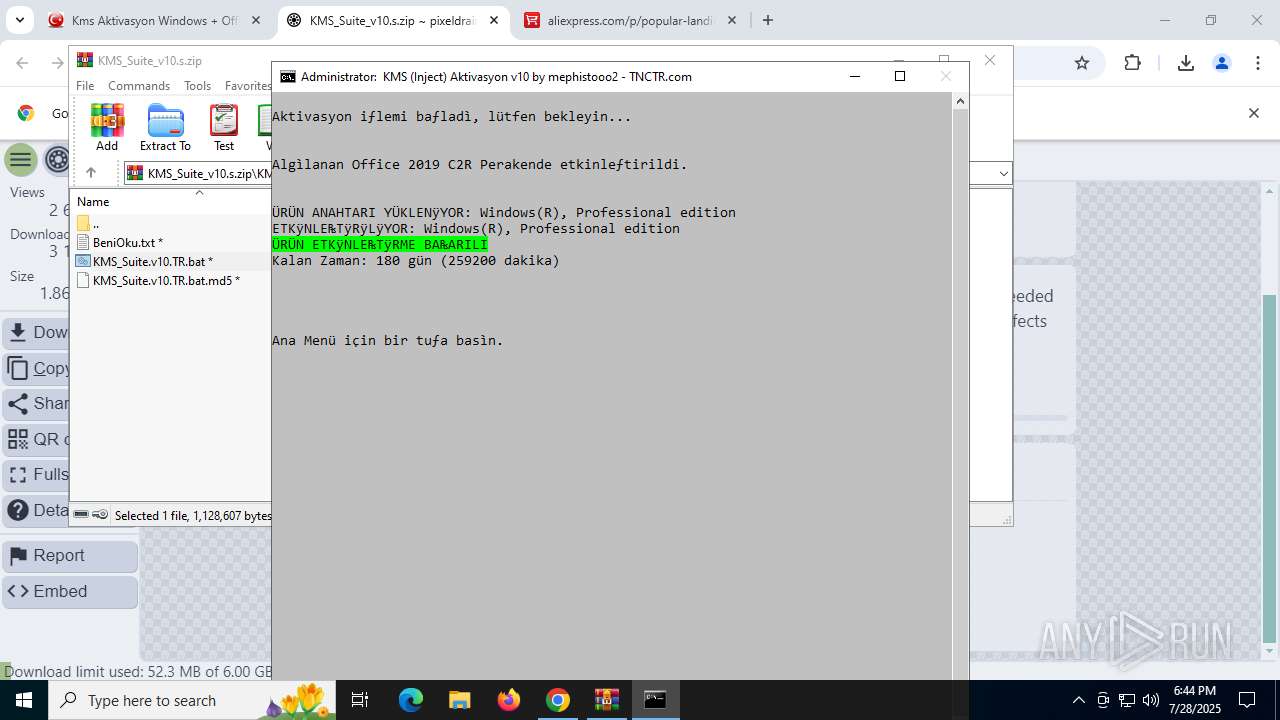
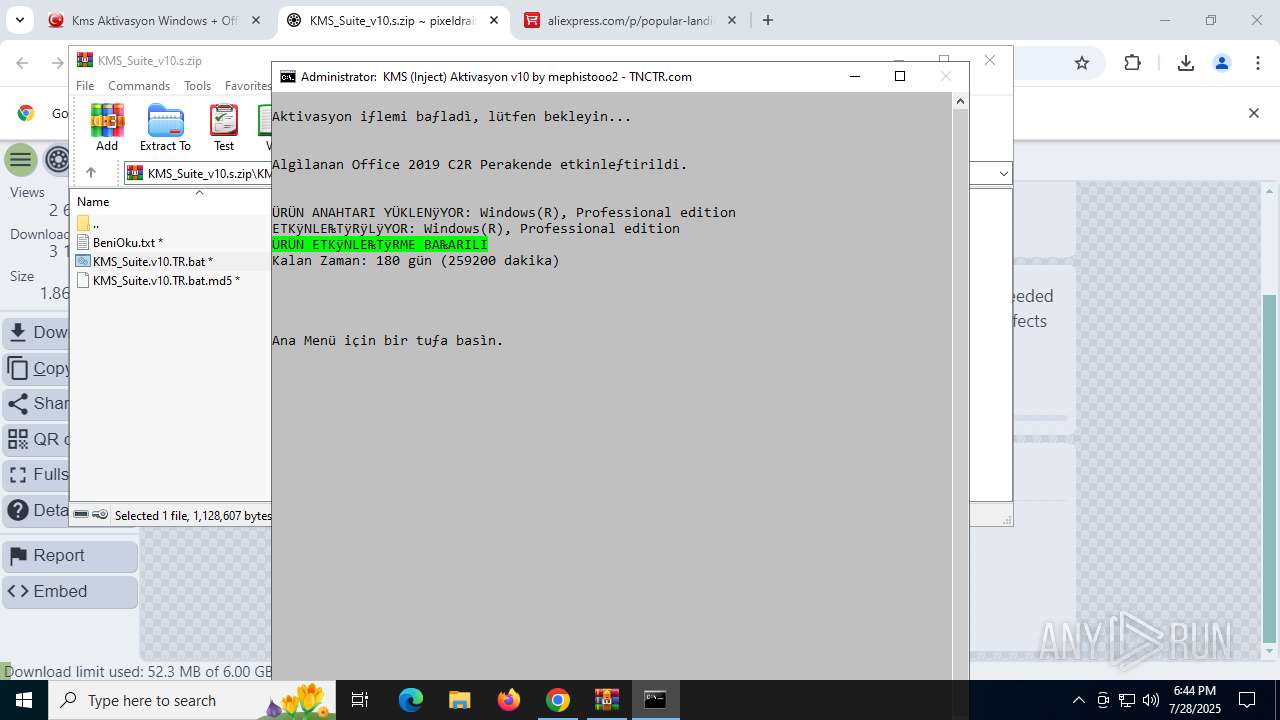
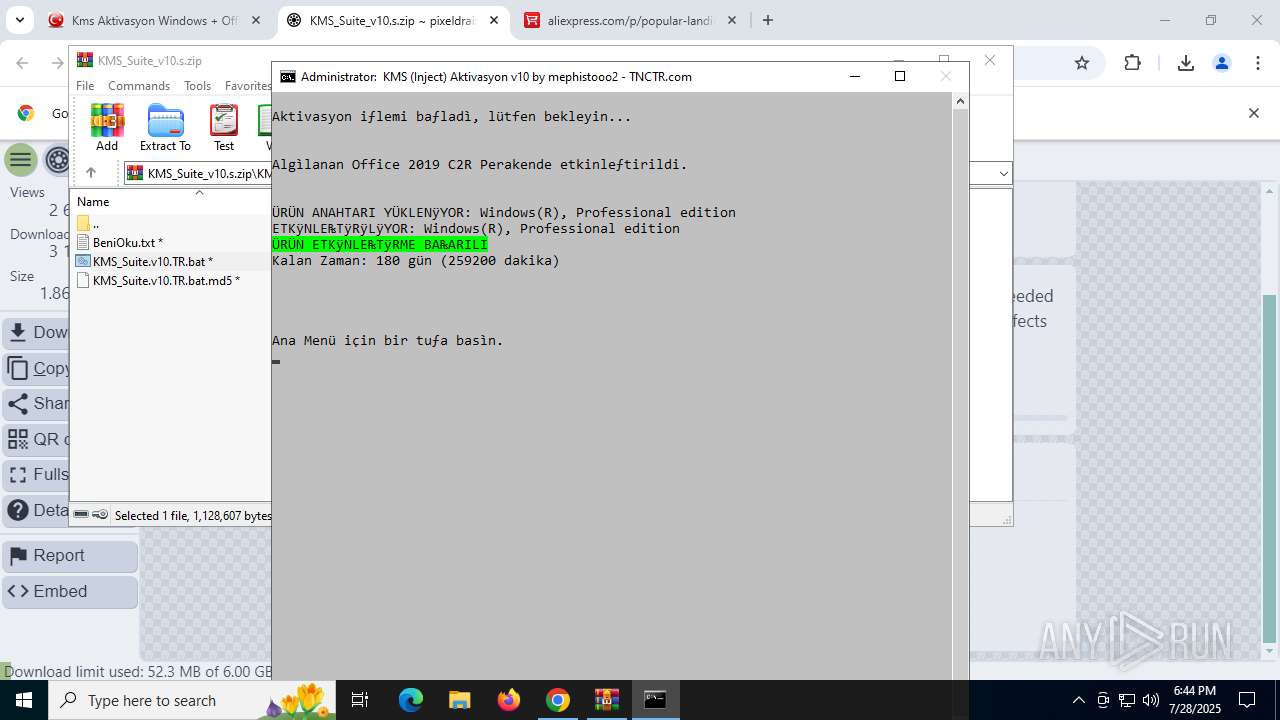
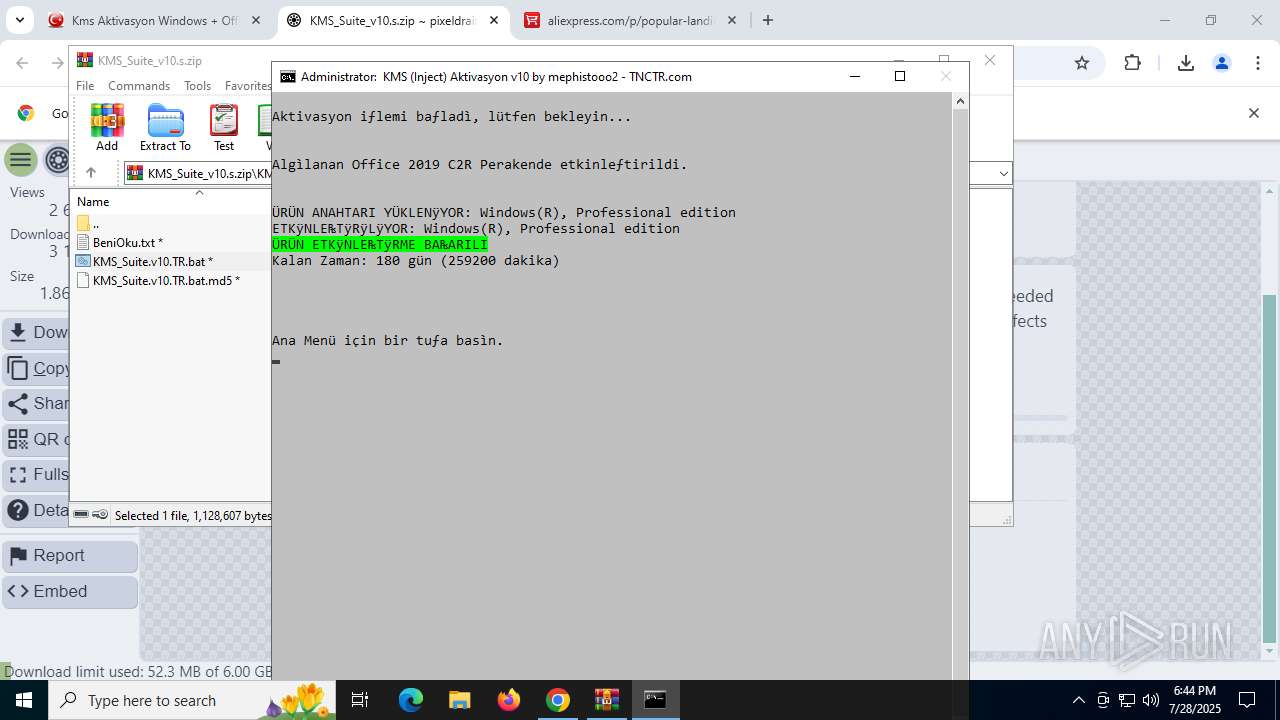
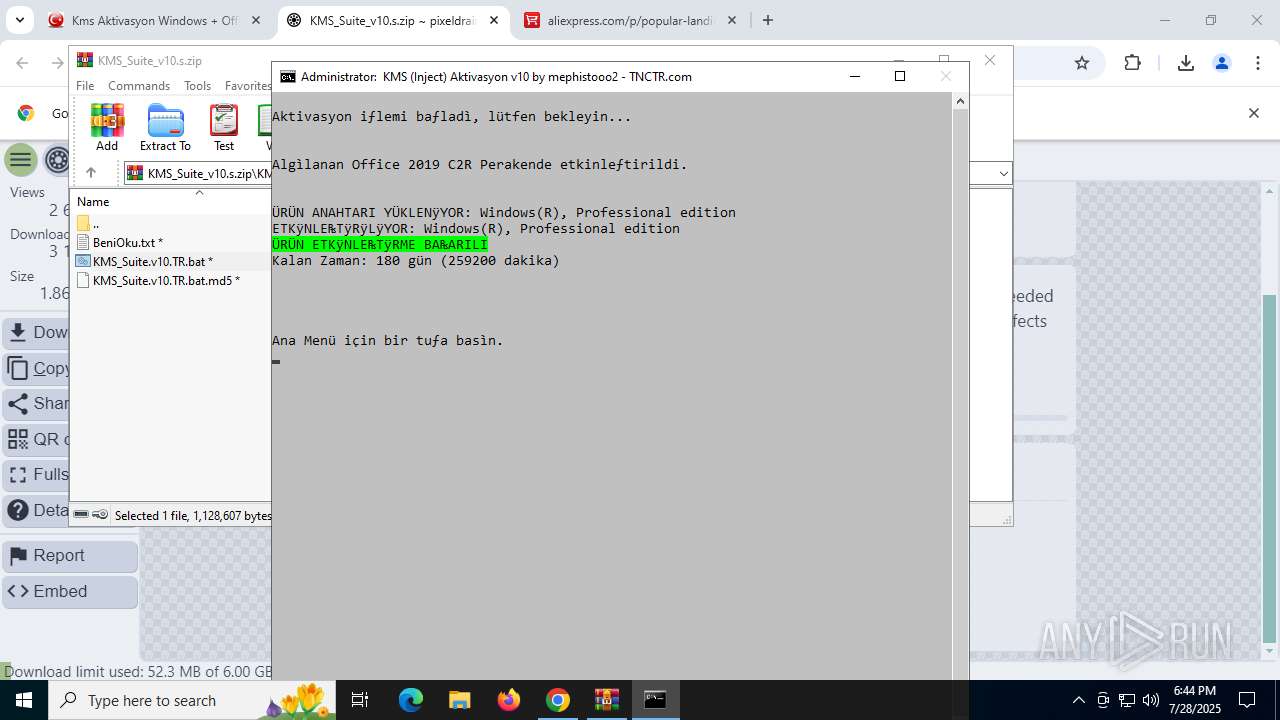
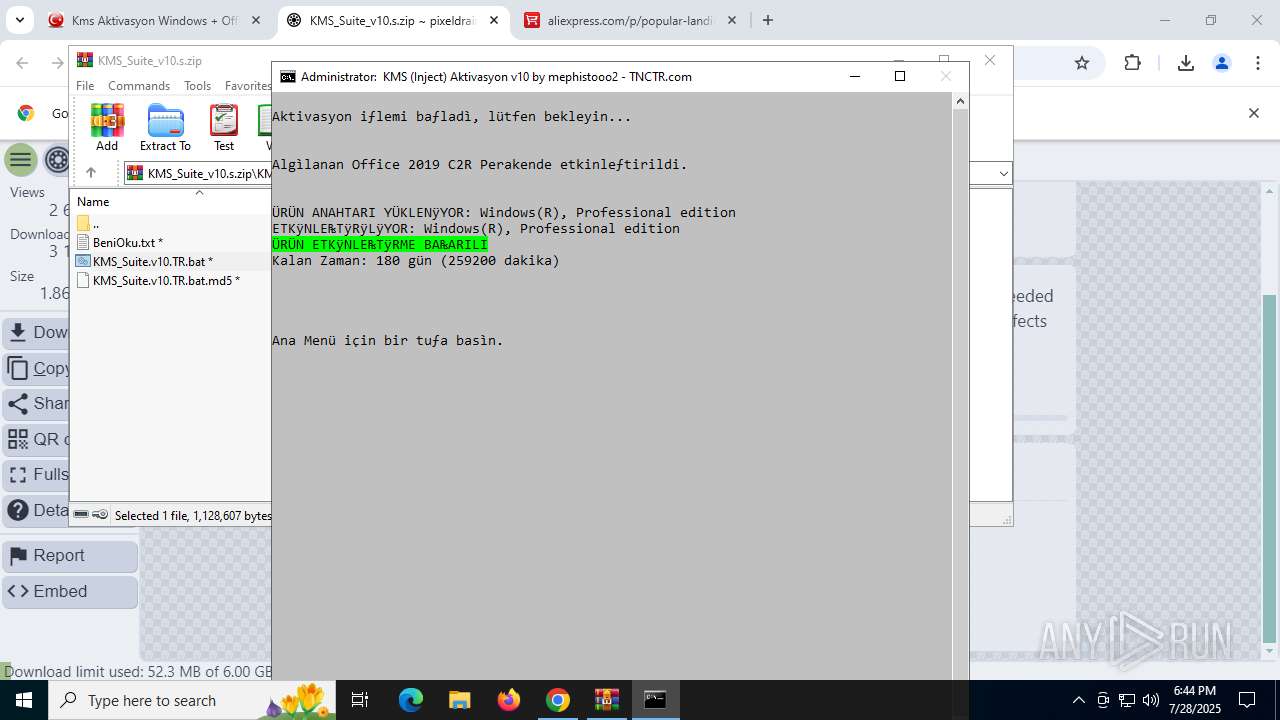
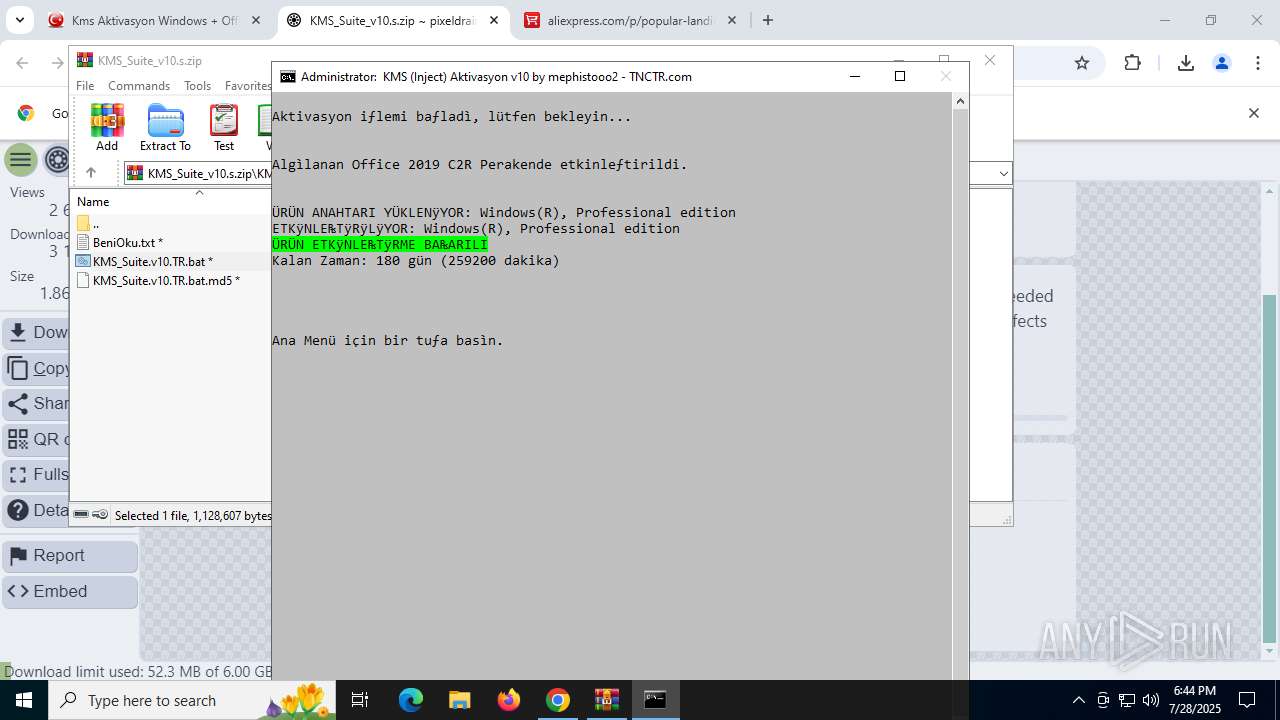
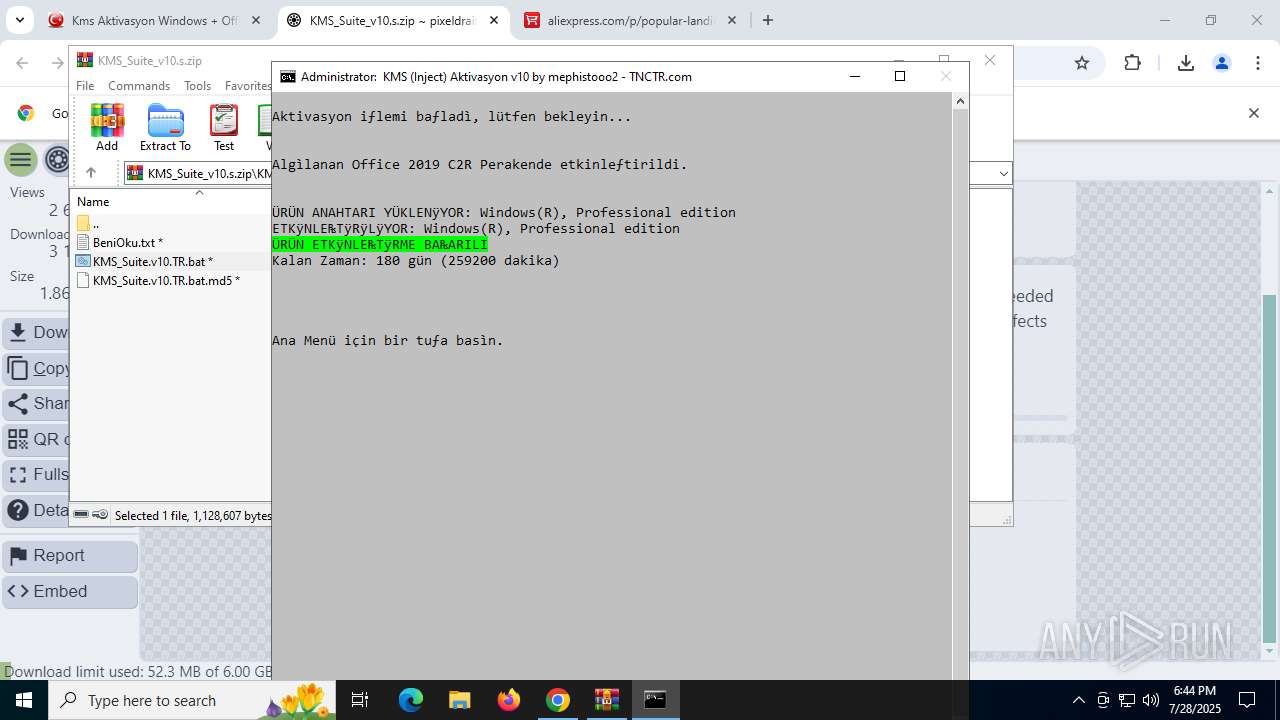
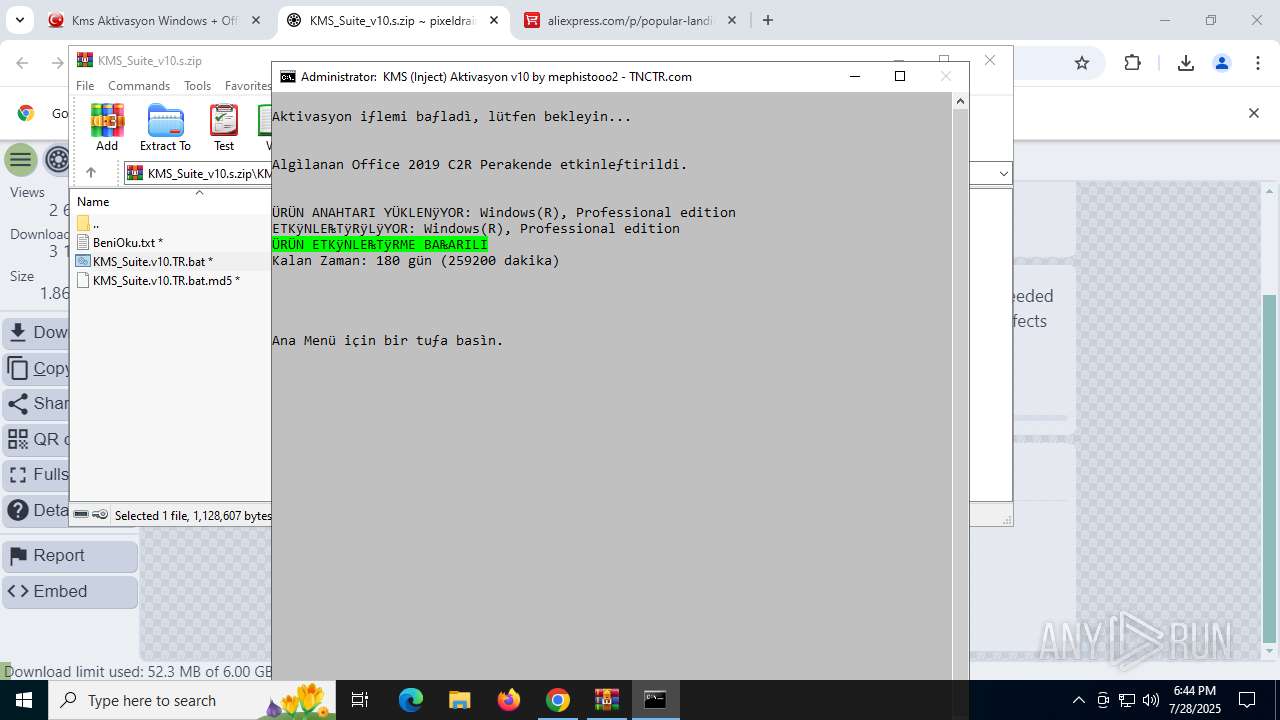
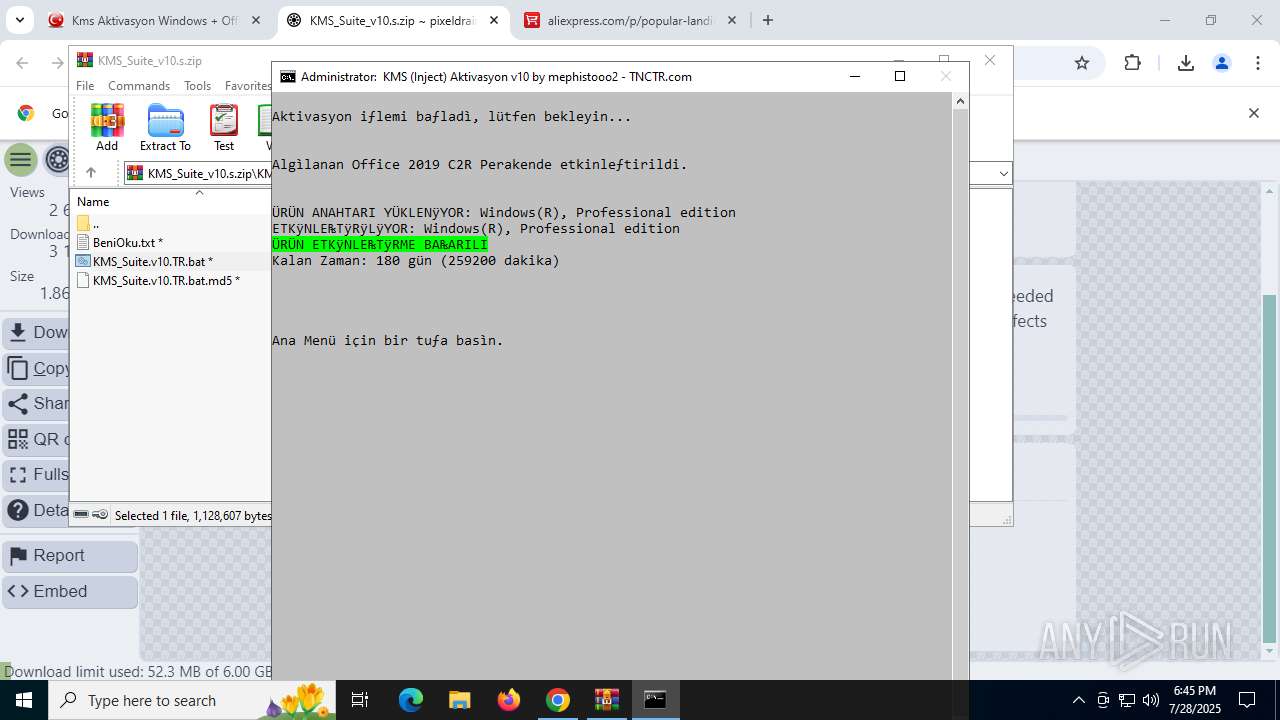
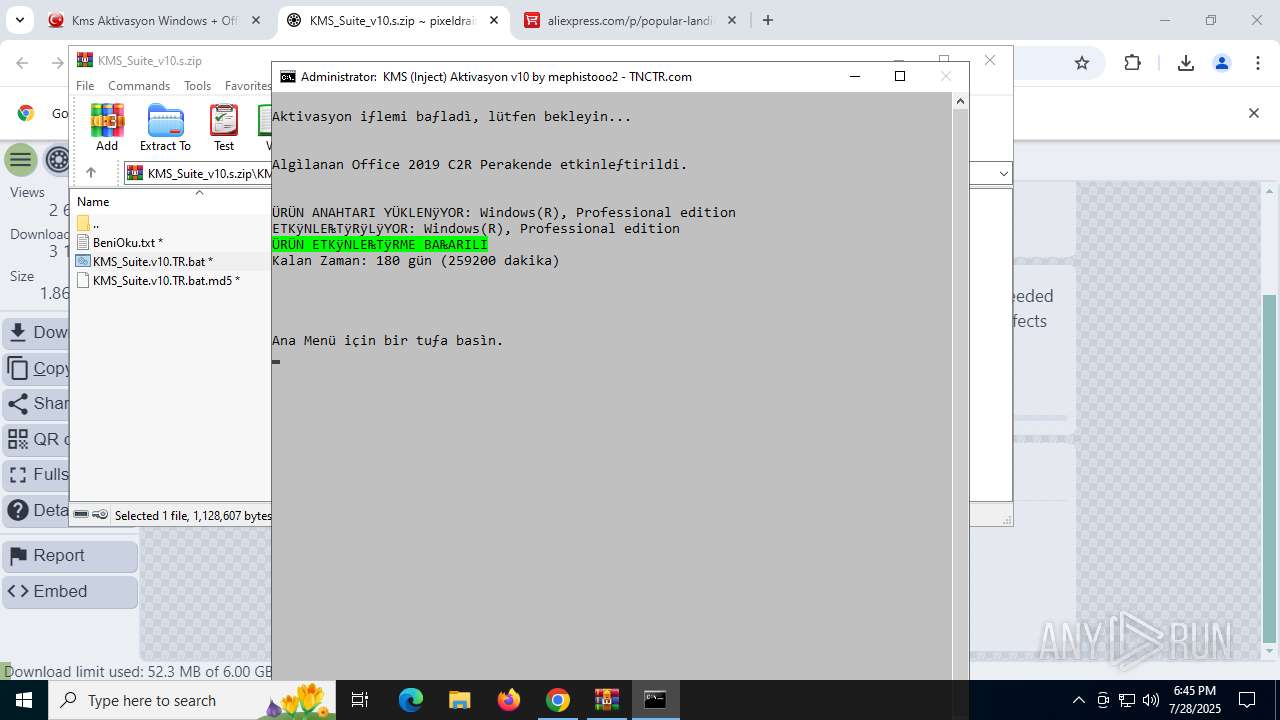
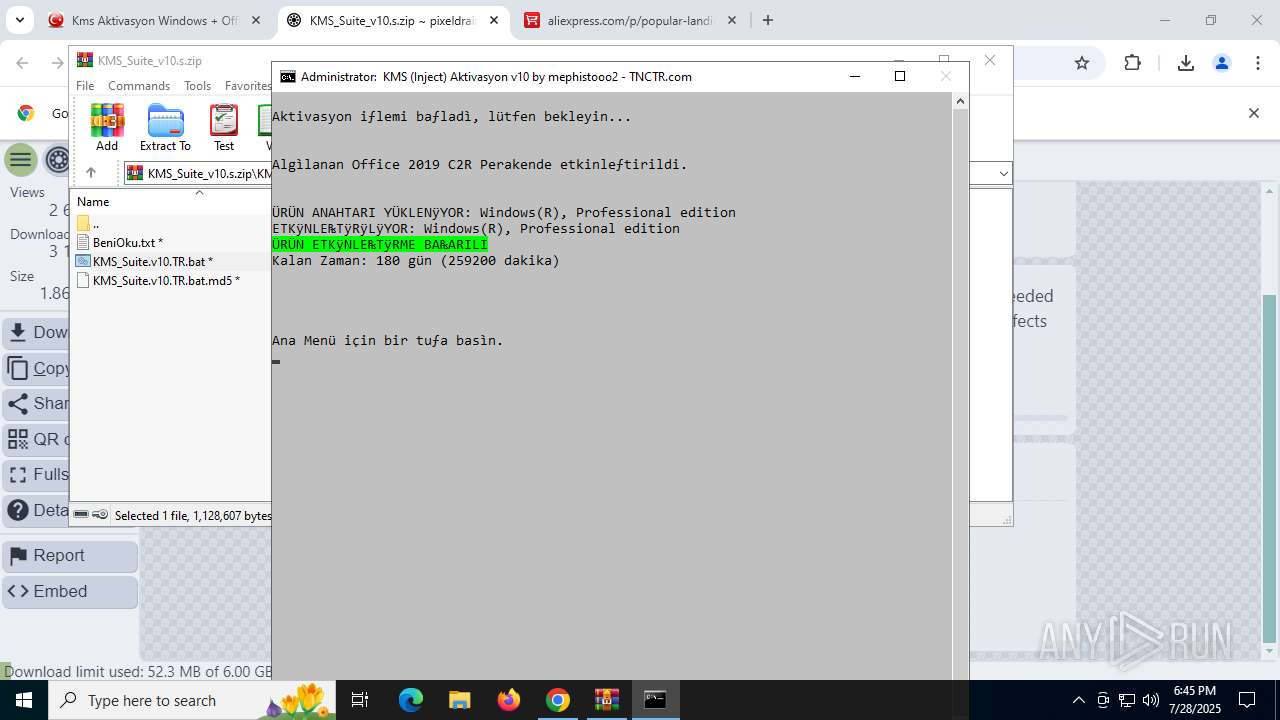
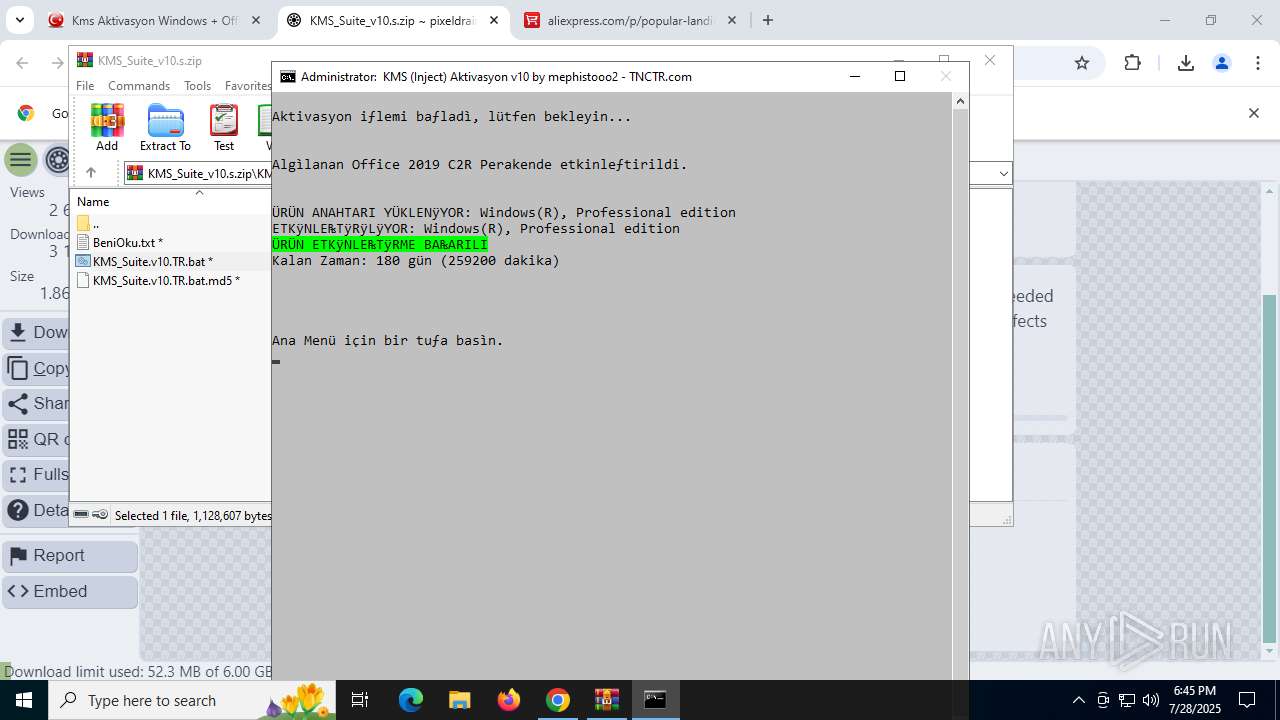
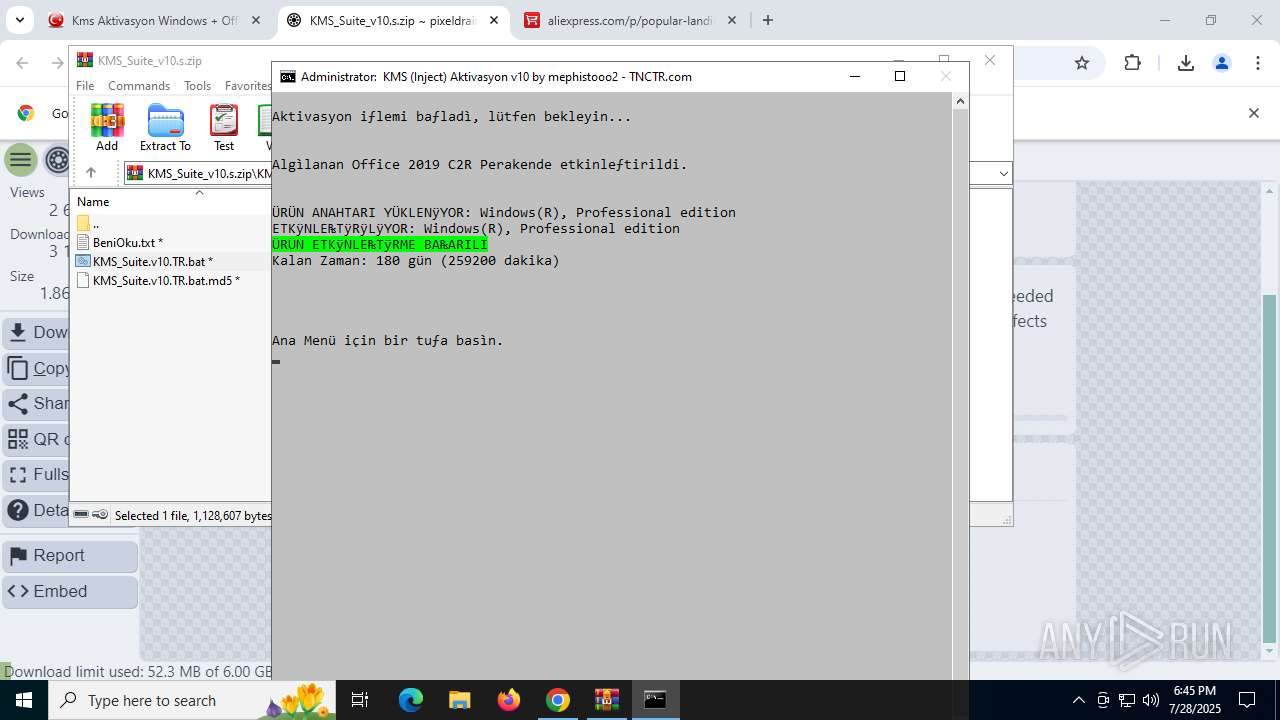
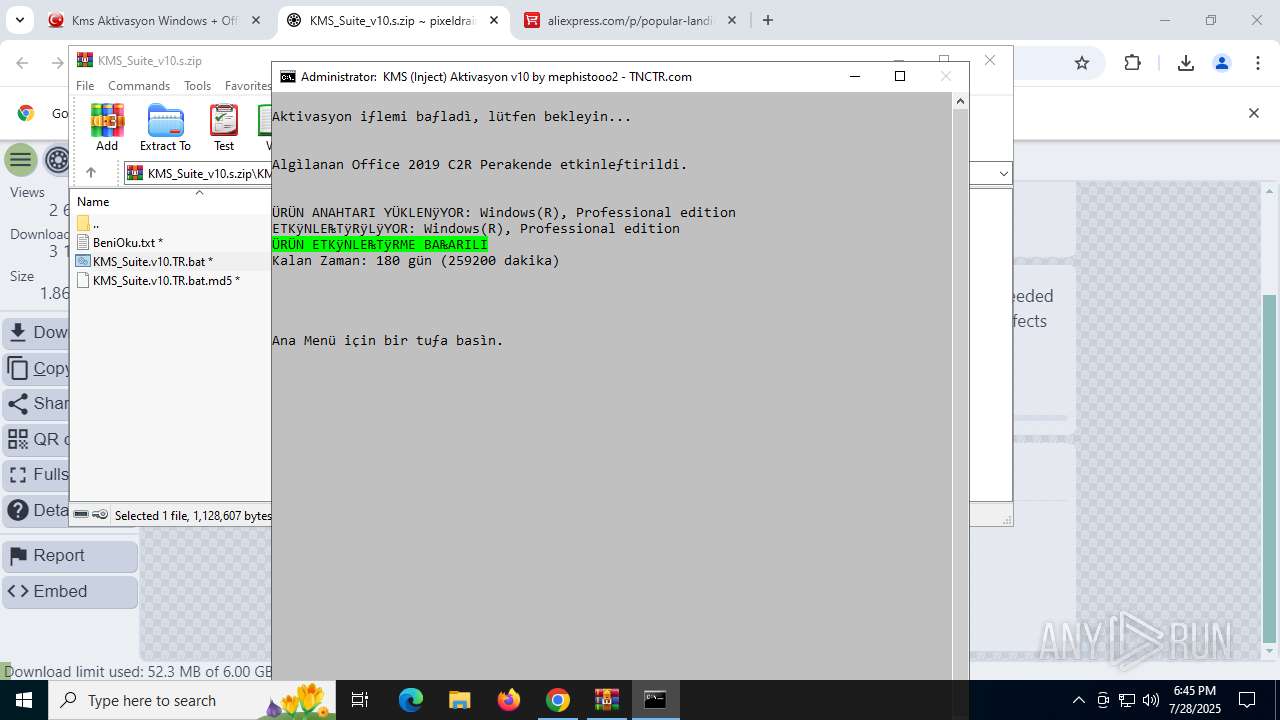
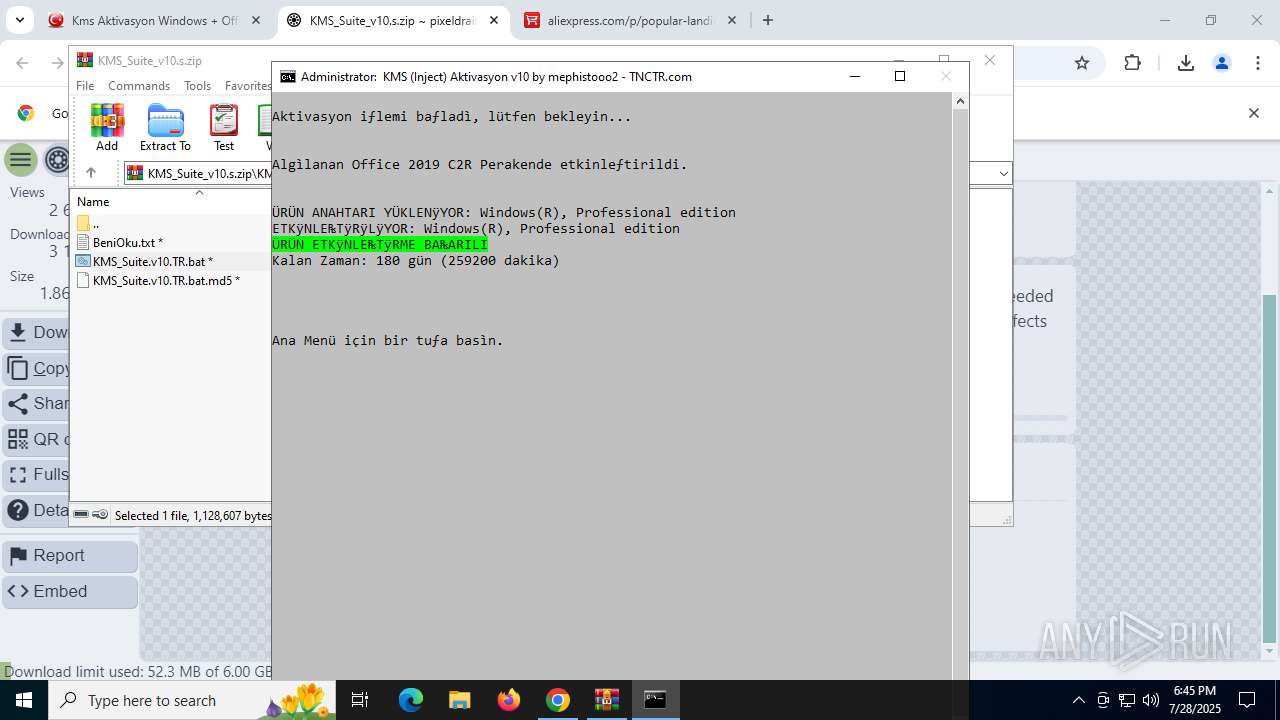
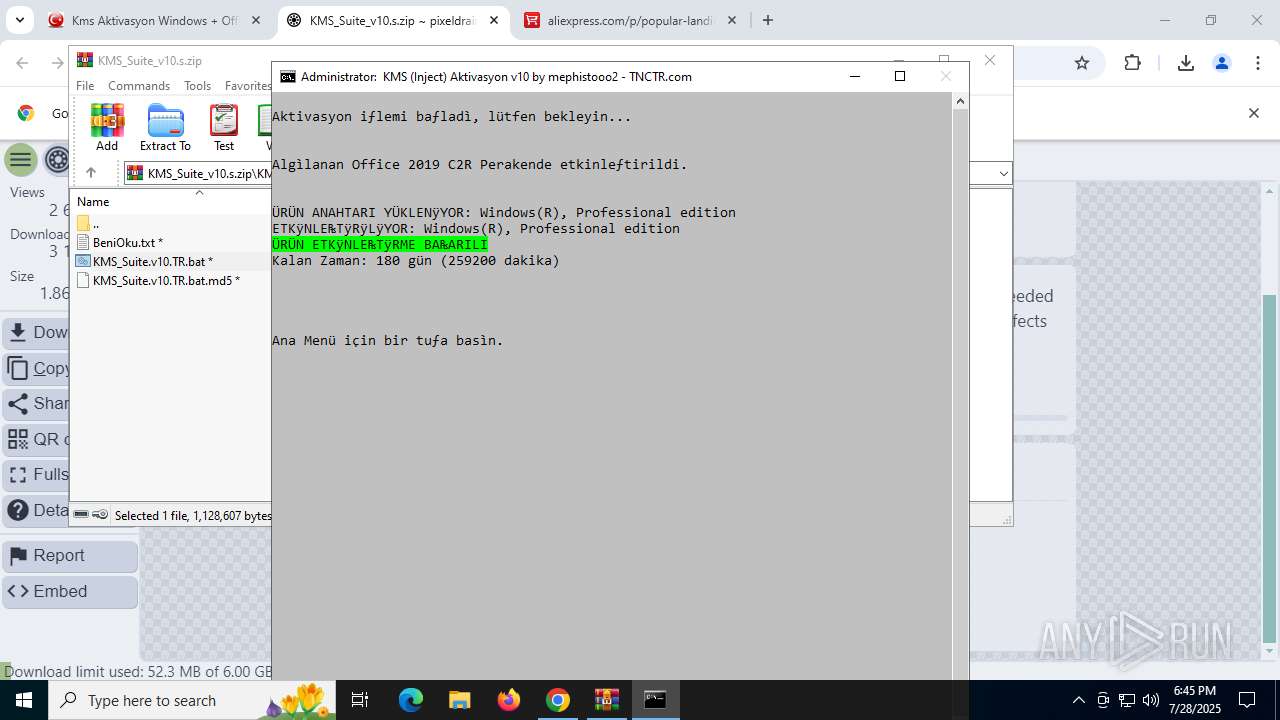
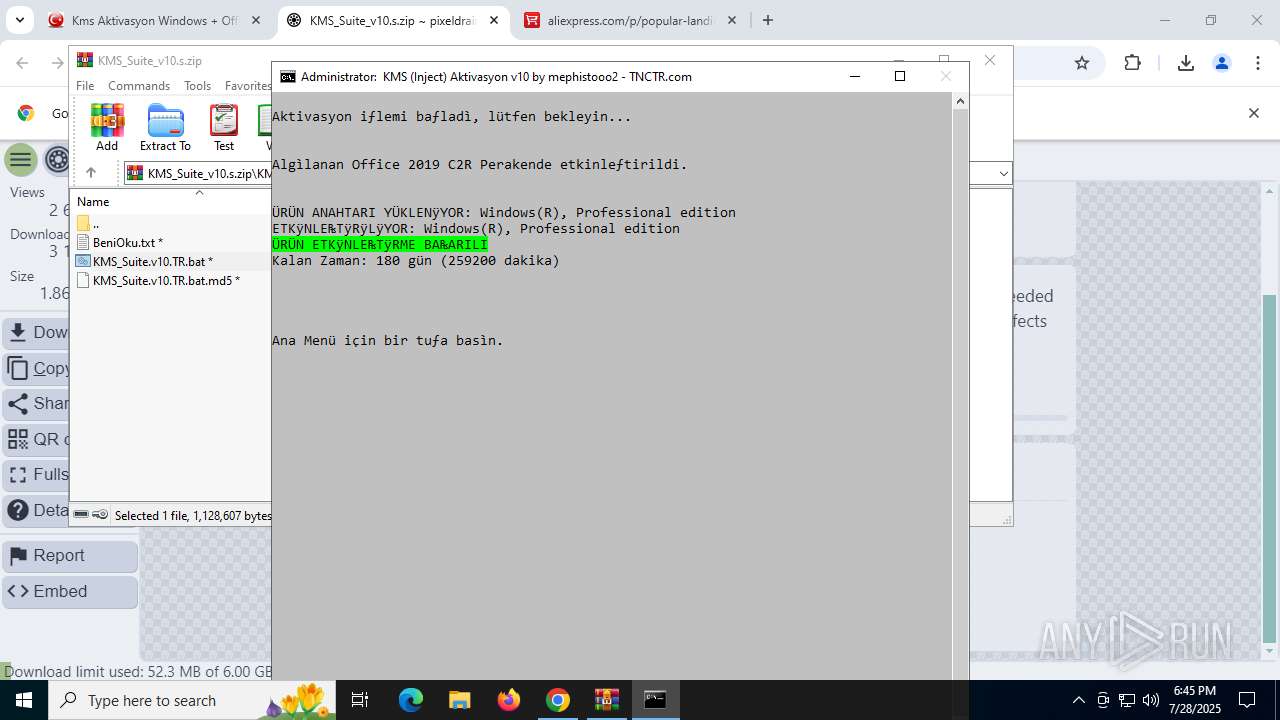
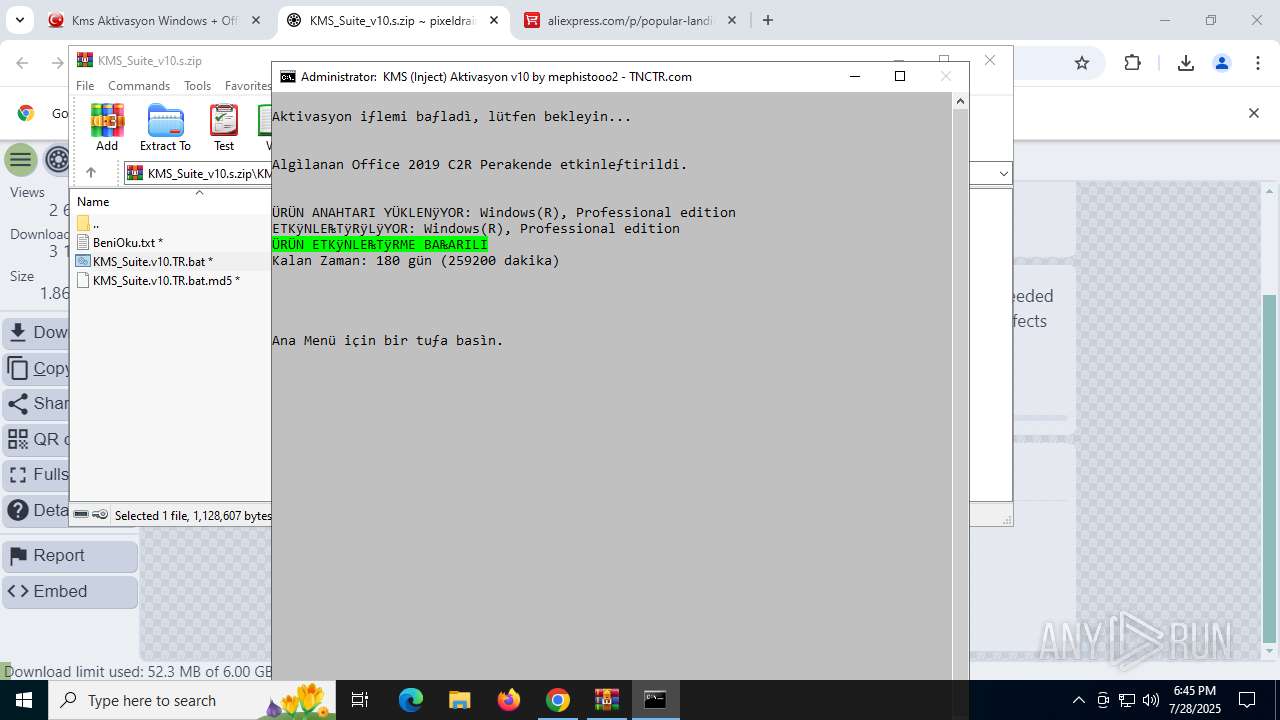
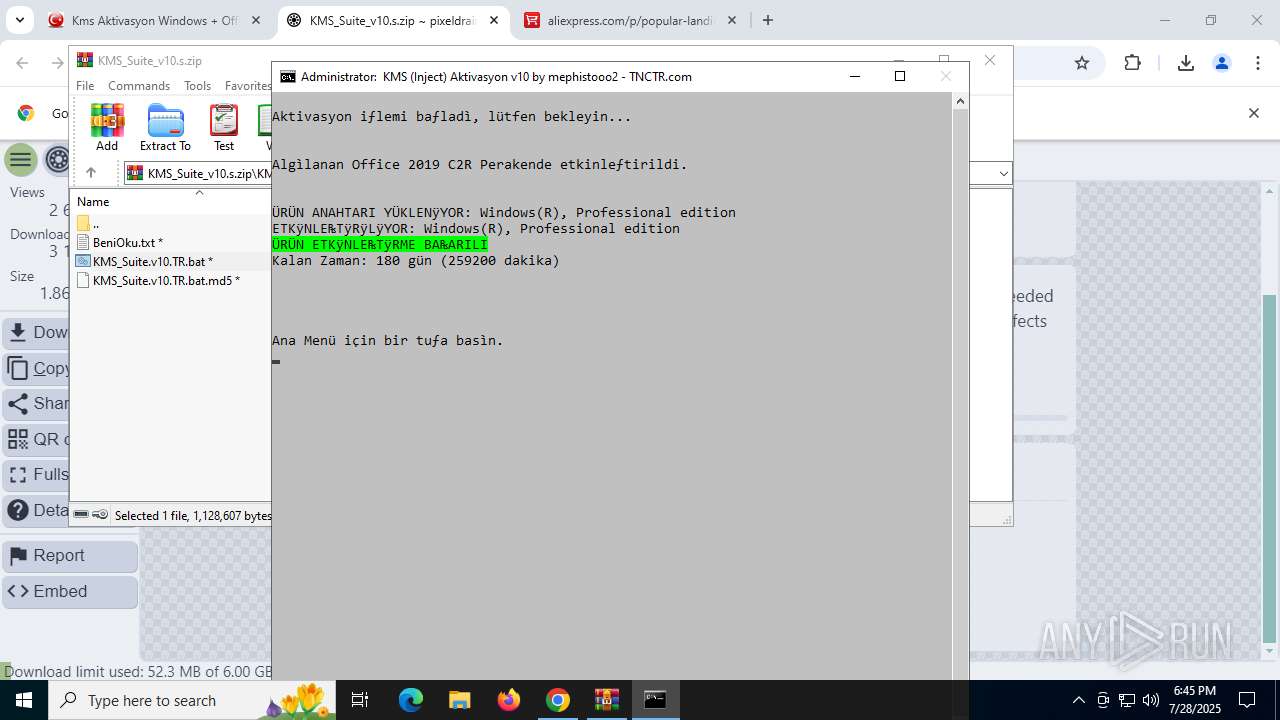
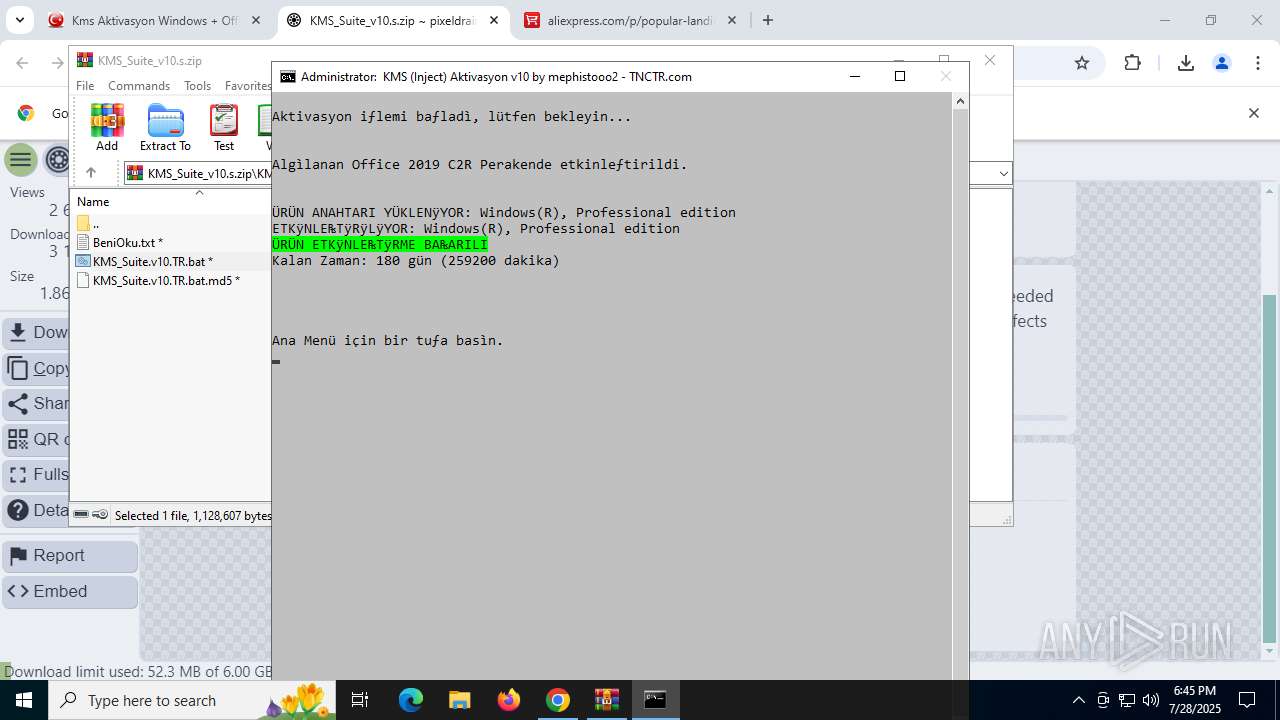
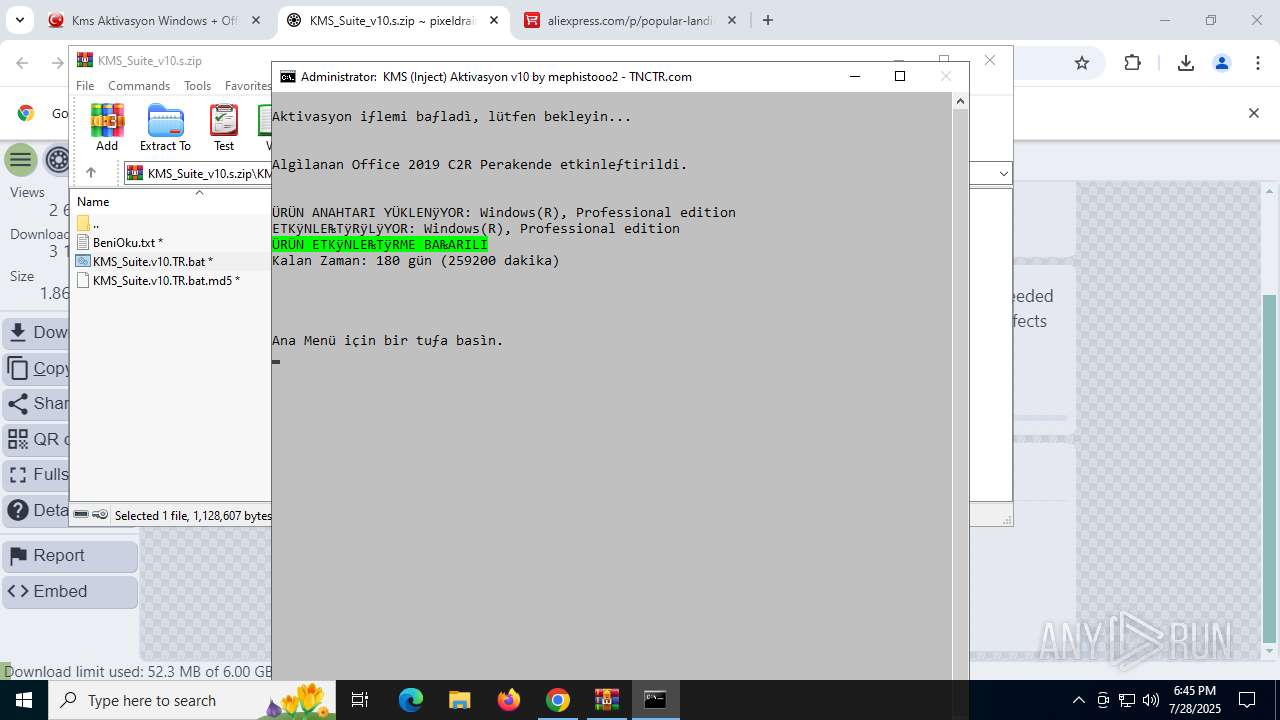
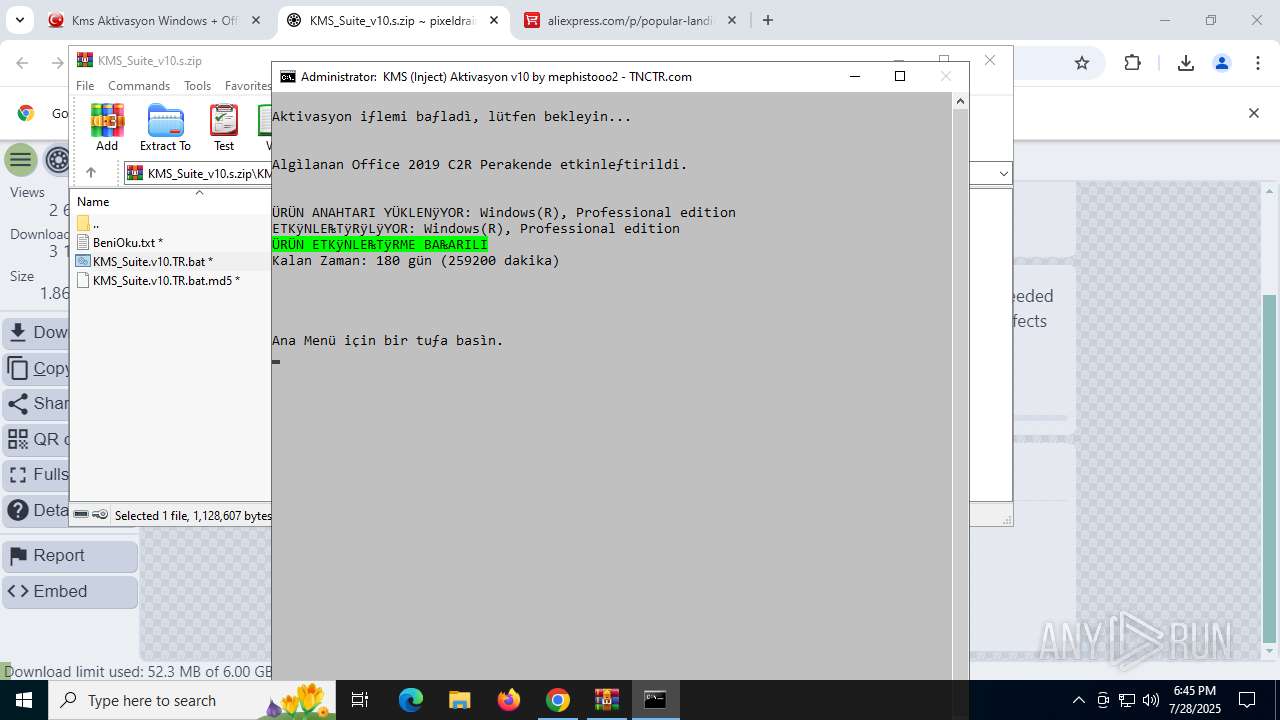
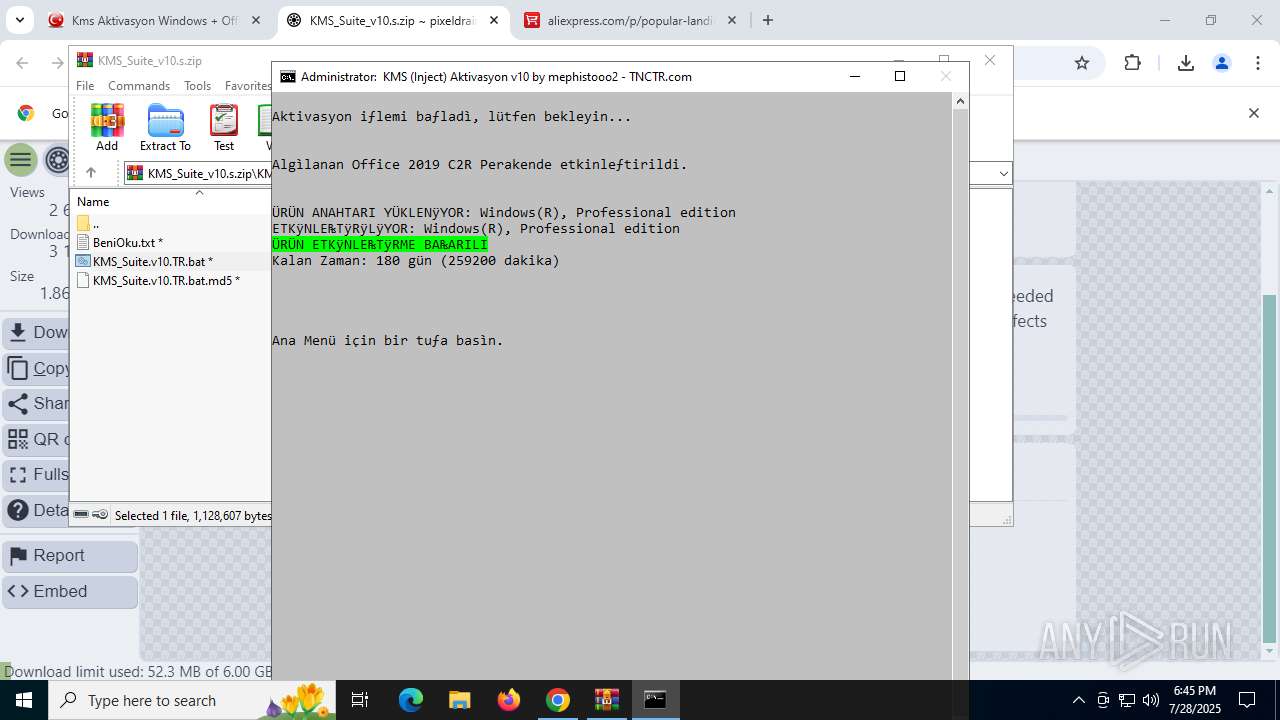
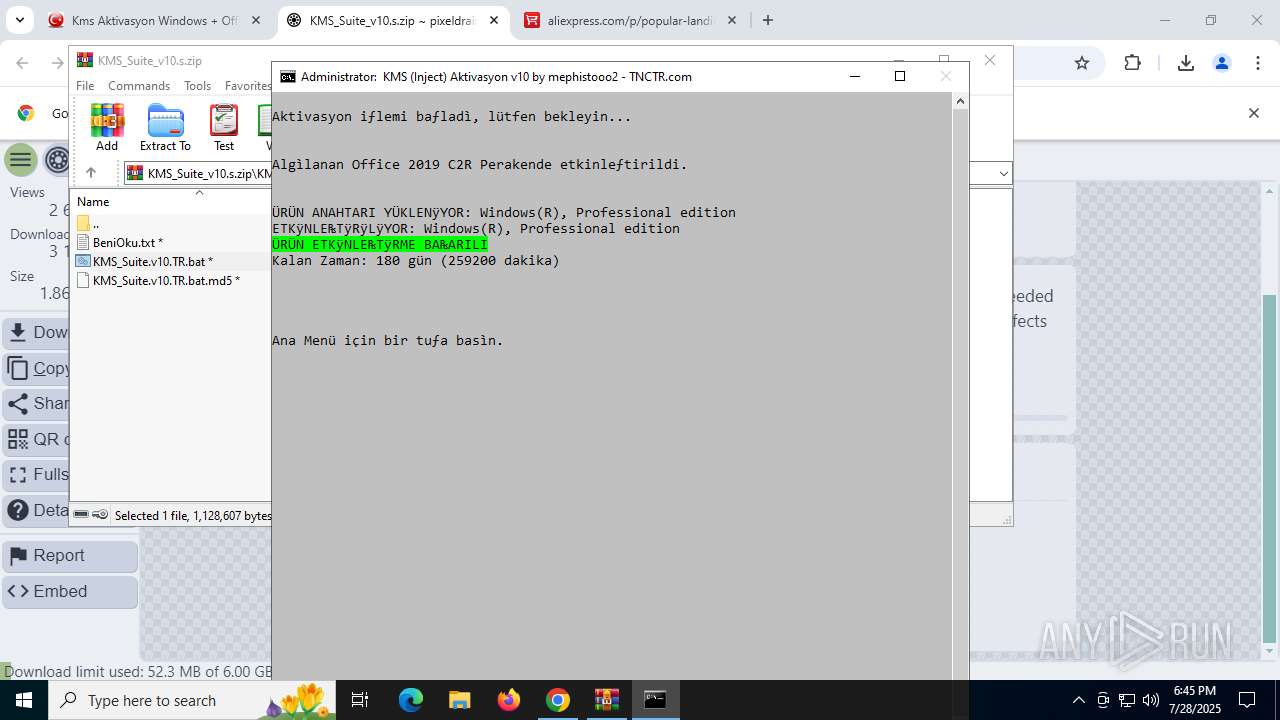
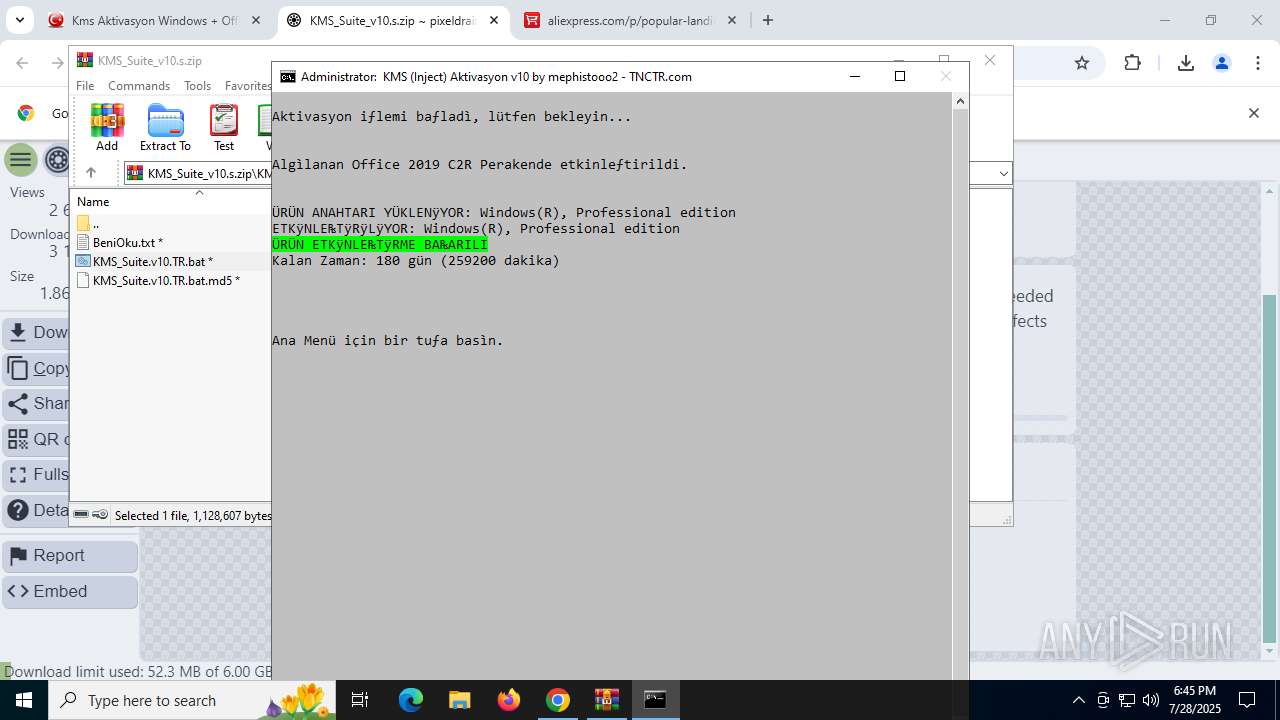
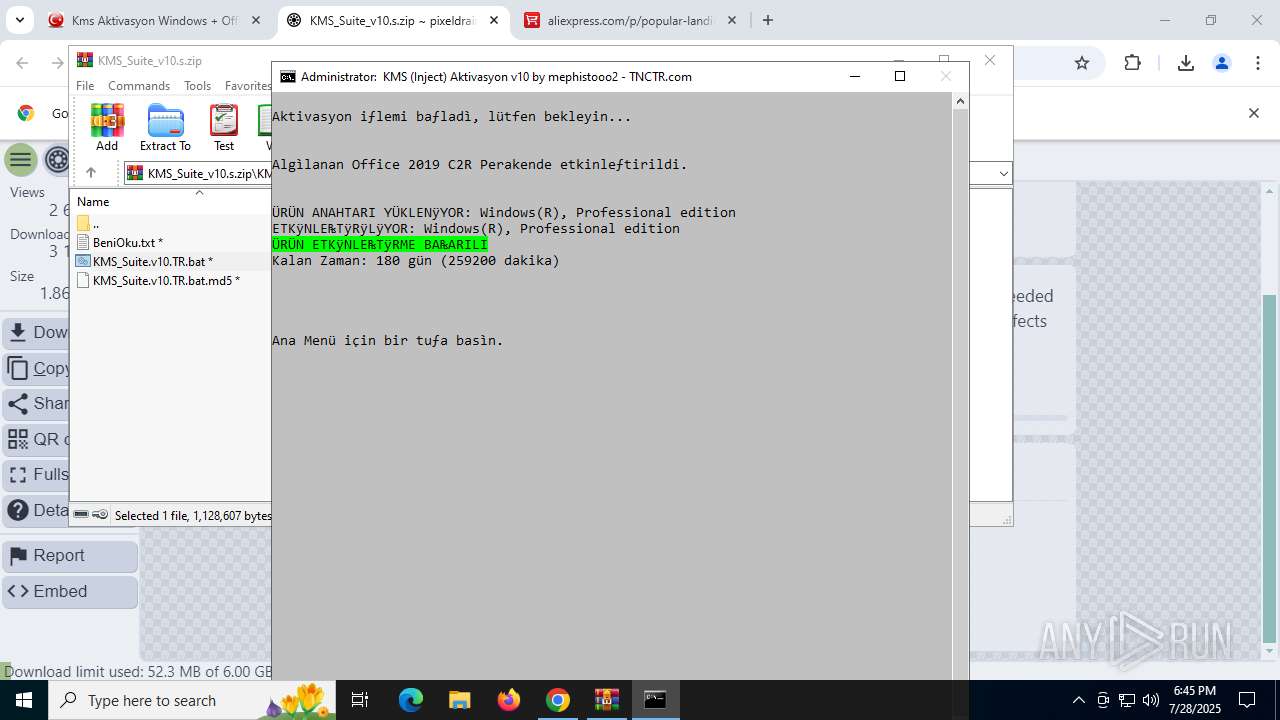
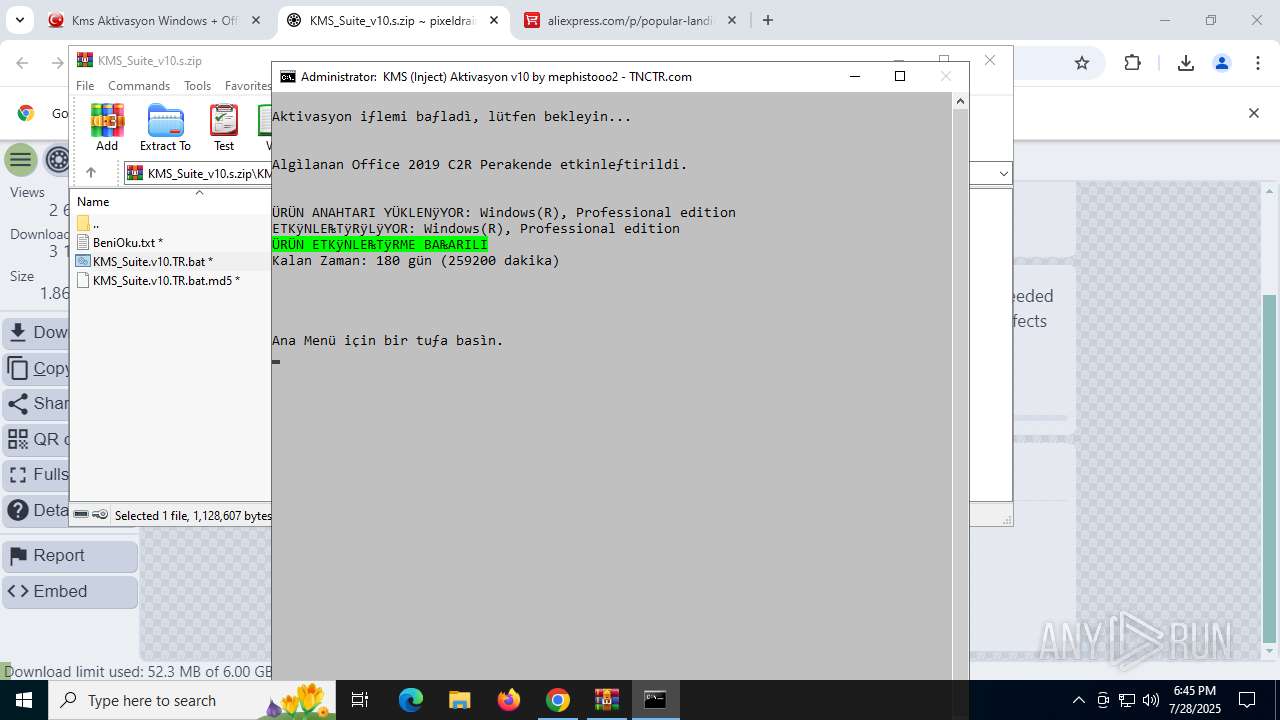
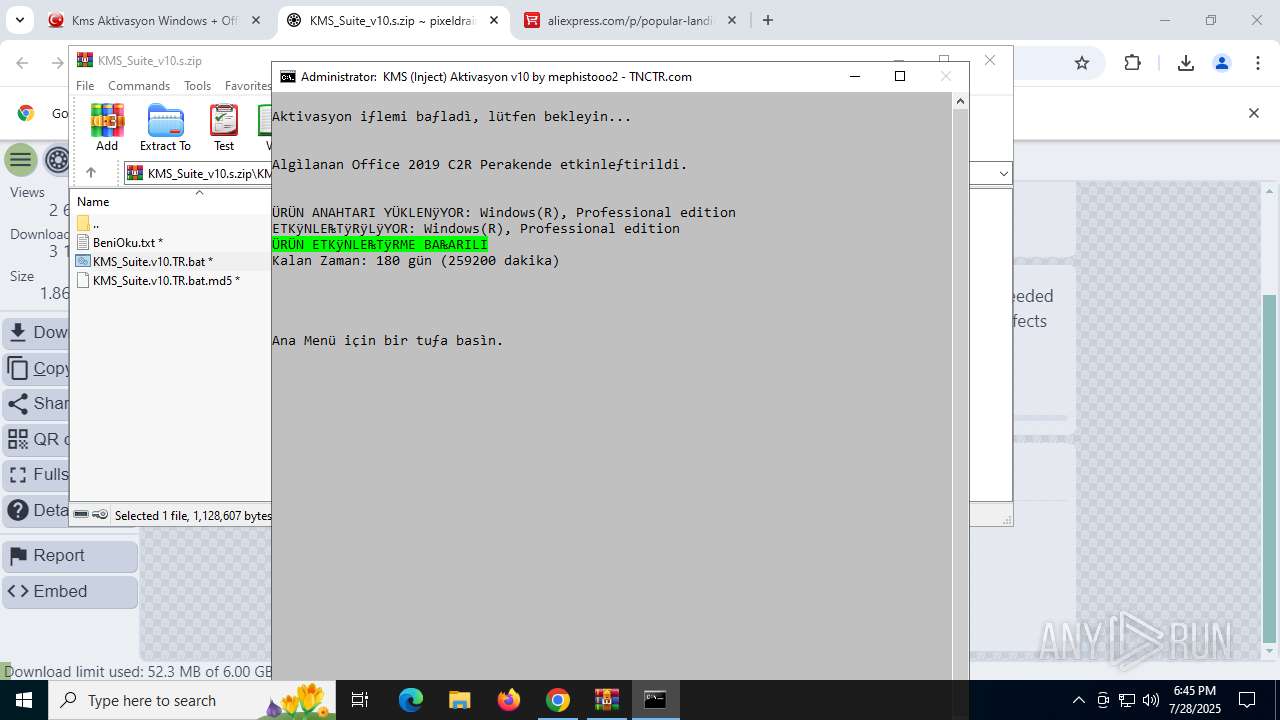
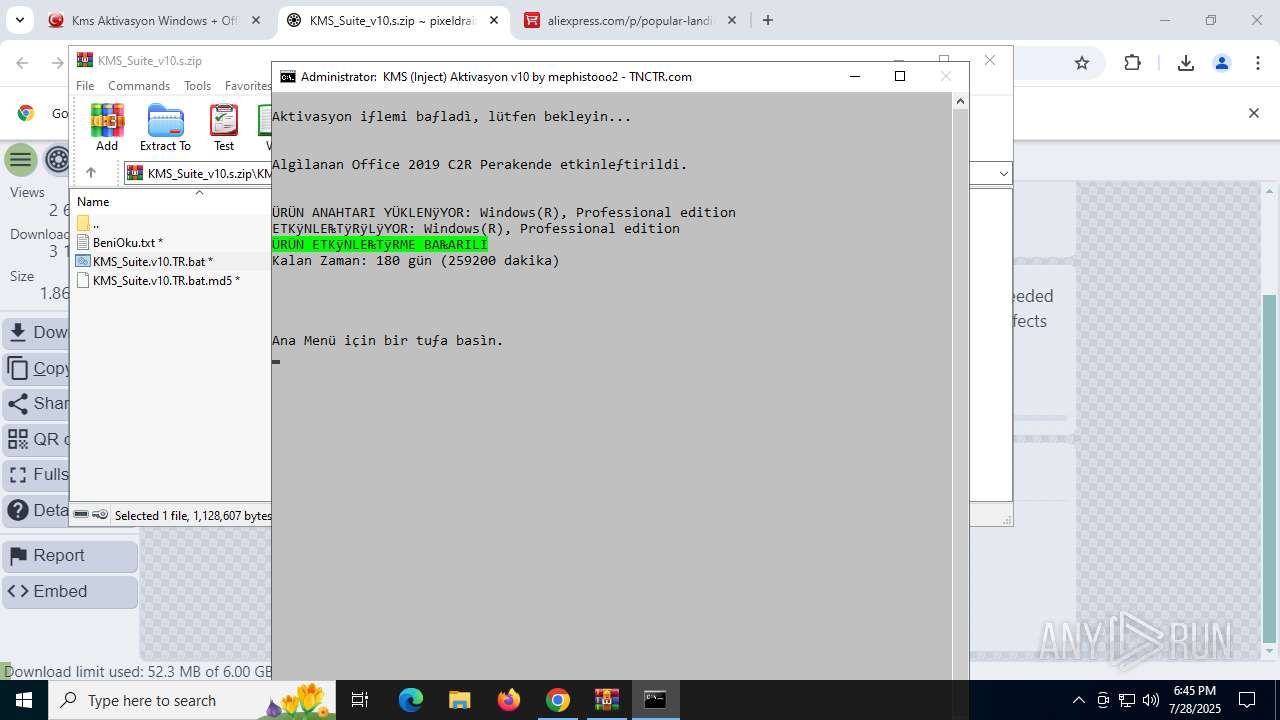
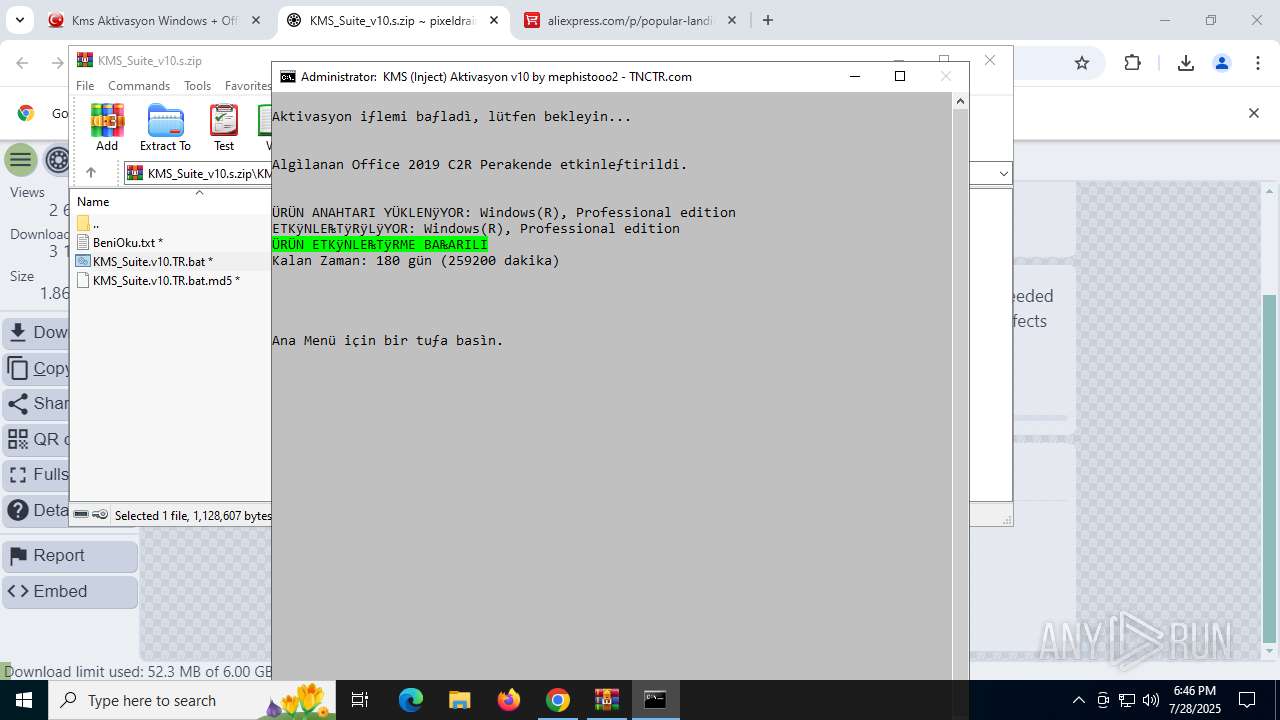
| URL: | https://www.fullprogramlarindir.net/kms-aktivasyon-windows-office-indir-tam-2469487.html |
| Full analysis: | https://app.any.run/tasks/a5fe91bb-bd0a-4ba3-b4e3-ad747b3dc17d |
| Verdict: | Malicious activity |
| Analysis date: | July 28, 2025, 18:41:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2AEC366F2B3DA09656CEDE9F20B2D3B5 |
| SHA1: | 14E9060A863F17B072D5771E8C105D541126B243 |
| SHA256: | 2AB0C0350700A15476934D77F962CB93D8FCE610DCCC58060A92CF7C76050960 |
| SSDEEP: | 3:N8DSLMdKCRJ+MueIPnqTEESDl1kLNR0:2OLMp0ecqTyDlwNR0 |
MALICIOUS
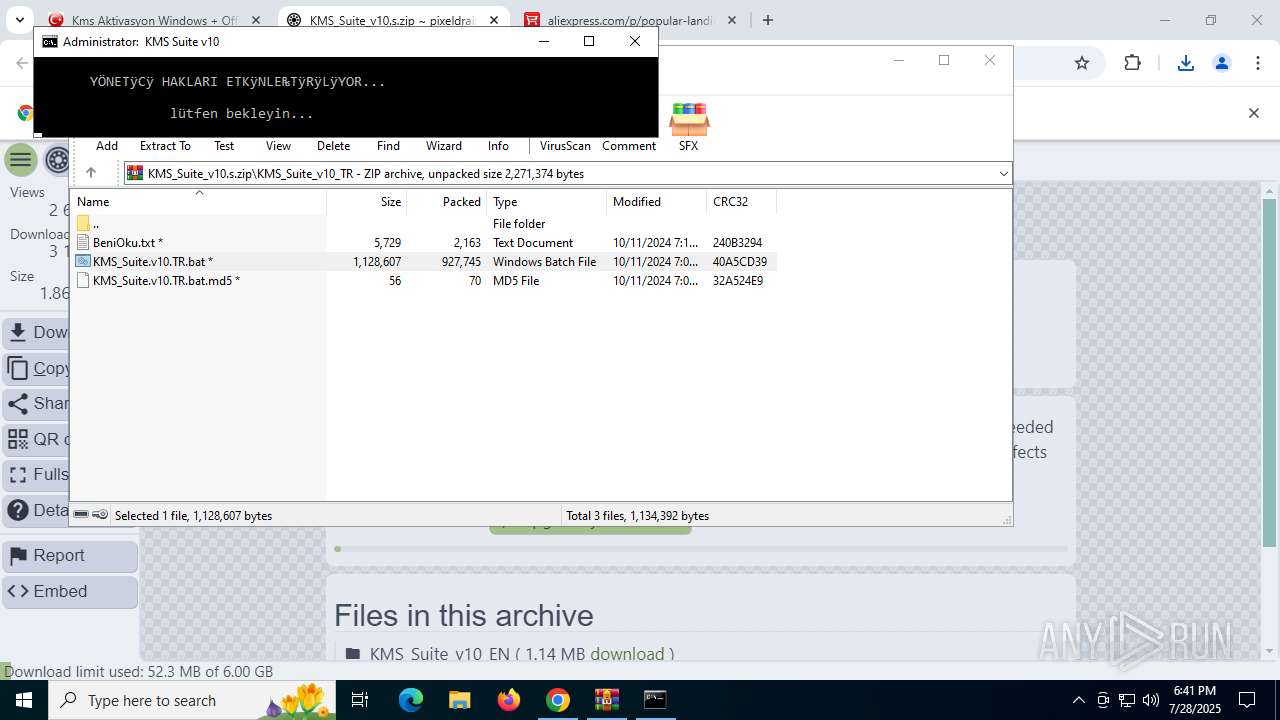
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 3620)
Changes Windows Defender settings
- cmd.exe (PID: 3620)
Changes powershell execution policy (RemoteSigned)
- cmd.exe (PID: 1728)
Starts NET.EXE for service management
- cmd.exe (PID: 1728)
- net.exe (PID: 7912)
- net.exe (PID: 4412)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7288)
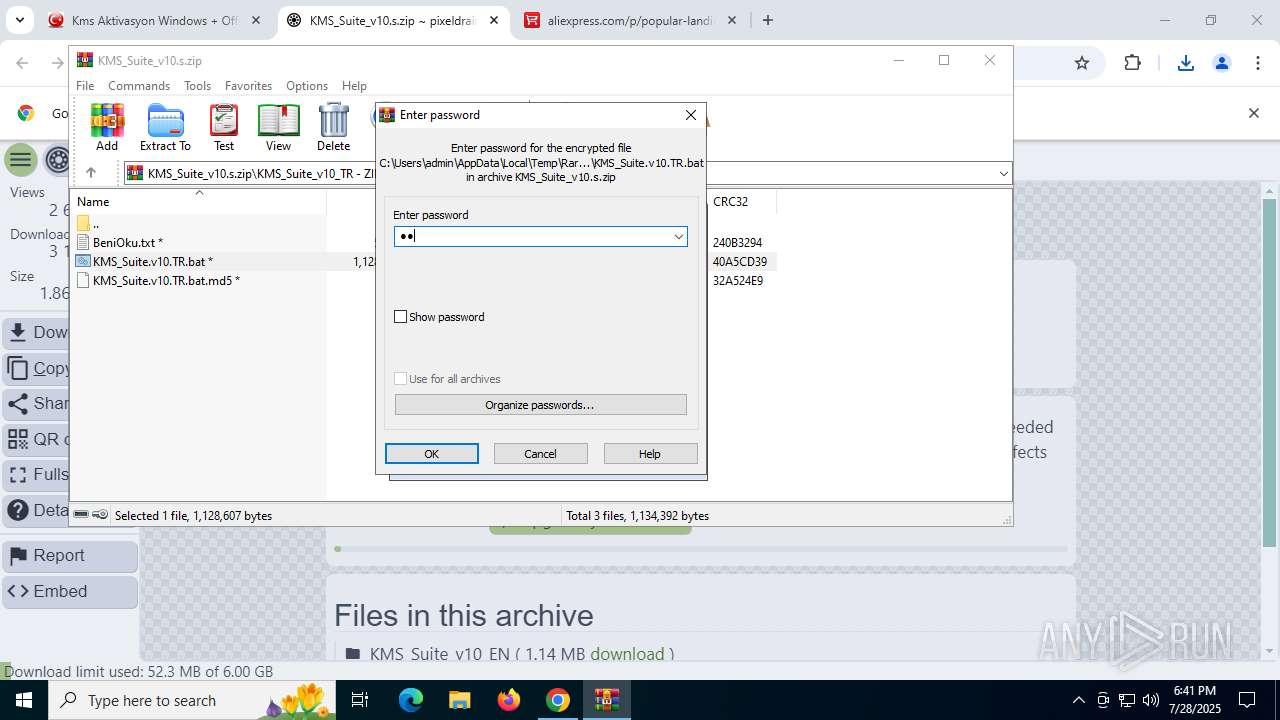
Executing commands from a ".bat" file
- WinRAR.exe (PID: 7288)
- mshta.exe (PID: 7356)
- cmd.exe (PID: 3620)
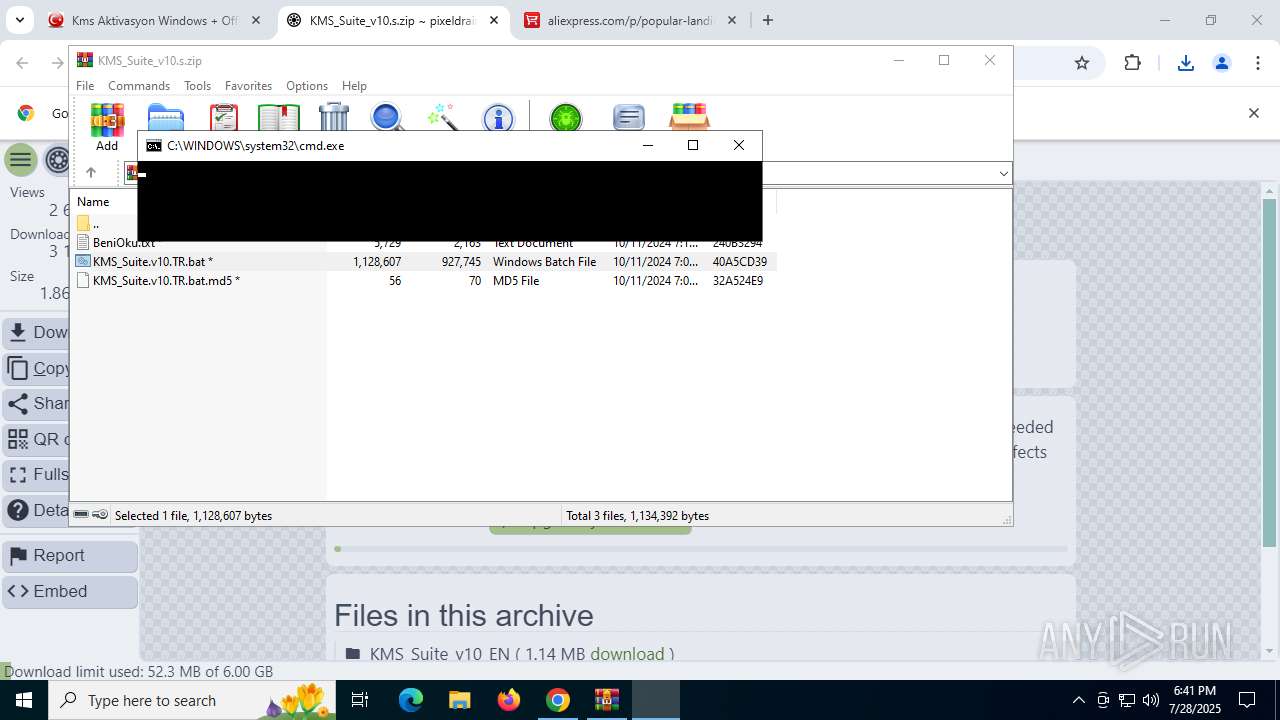
Starts CMD.EXE for commands execution
- mshta.exe (PID: 7356)
- WinRAR.exe (PID: 7288)
- cmd.exe (PID: 3620)
- cmd.exe (PID: 1728)
Executes script without checking the security policy
- powershell.exe (PID: 6360)
- powershell.exe (PID: 7444)
- powershell.exe (PID: 7768)
- powershell.exe (PID: 7360)
- powershell.exe (PID: 1300)
- powershell.exe (PID: 6508)
- powershell.exe (PID: 2536)
- powershell.exe (PID: 5284)
- powershell.exe (PID: 7884)
- powershell.exe (PID: 1704)
Runs shell command (SCRIPT)
- mshta.exe (PID: 7356)
Application launched itself
- cmd.exe (PID: 3620)
- cmd.exe (PID: 1728)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 3620)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3620)
- cmd.exe (PID: 1728)
- cmd.exe (PID: 7452)
- cmd.exe (PID: 7600)
- cmd.exe (PID: 952)
- cmd.exe (PID: 7408)
- cmd.exe (PID: 4572)
- cmd.exe (PID: 7364)
Unpacks CAB file
- expand.exe (PID: 8104)
- expand.exe (PID: 5960)
Executable content was dropped or overwritten
- csc.exe (PID: 5496)
- expand.exe (PID: 8104)
- csc.exe (PID: 8188)
- csc.exe (PID: 7044)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 3620)
- cmd.exe (PID: 1728)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 3620)
- cmd.exe (PID: 1728)
Manipulates environment variables
- powershell.exe (PID: 6360)
- powershell.exe (PID: 6508)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3620)
- cmd.exe (PID: 1728)
- cmd.exe (PID: 7452)
- cmd.exe (PID: 7600)
- cmd.exe (PID: 952)
- cmd.exe (PID: 7408)
- cmd.exe (PID: 4572)
- cmd.exe (PID: 7364)
CSC.EXE is used to compile C# code
- csc.exe (PID: 5496)
- csc.exe (PID: 8188)
- csc.exe (PID: 7044)
The process executes Powershell scripts
- cmd.exe (PID: 1728)
The executable file from the user directory is run by the CMD process
- center.exe (PID: 7400)
There is functionality for communication dyndns network (YARA)
- cmd.exe (PID: 1728)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1728)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 5504)
Starts NET.EXE to map network drives
- cmd.exe (PID: 1728)
Hides command output
- cmd.exe (PID: 7916)
- cmd.exe (PID: 6788)
- cmd.exe (PID: 6584)
- cmd.exe (PID: 5460)
- cmd.exe (PID: 5456)
- cmd.exe (PID: 2144)
- cmd.exe (PID: 4084)
- cmd.exe (PID: 1216)
- cmd.exe (PID: 6148)
- cmd.exe (PID: 7604)
- cmd.exe (PID: 1388)
- cmd.exe (PID: 8092)
- cmd.exe (PID: 6368)
- cmd.exe (PID: 4044)
- cmd.exe (PID: 4116)
- cmd.exe (PID: 6504)
- cmd.exe (PID: 6360)
- cmd.exe (PID: 7292)
- cmd.exe (PID: 7224)
- cmd.exe (PID: 8096)
- cmd.exe (PID: 1740)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 6428)
Windows service management via SC.EXE
- sc.exe (PID: 7496)
- sc.exe (PID: 8080)
- sc.exe (PID: 2212)
- sc.exe (PID: 8116)
- sc.exe (PID: 4528)
- sc.exe (PID: 1300)
- sc.exe (PID: 3972)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1728)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 1728)
Starts SC.EXE for service management
- cmd.exe (PID: 1728)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 1728)
- cmd.exe (PID: 1388)
- cmd.exe (PID: 432)
- cmd.exe (PID: 7500)
- cmd.exe (PID: 7936)
- cmd.exe (PID: 4576)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 1468)
- cmd.exe (PID: 4528)
- cmd.exe (PID: 1728)
The process executes VB scripts
- cmd.exe (PID: 1728)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 4544)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 4544)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 4544)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 4544)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 4544)
Lists all scheduled tasks
- schtasks.exe (PID: 7192)
INFO
Application launched itself
- chrome.exe (PID: 2880)
Reads Microsoft Office registry keys
- chrome.exe (PID: 2880)
- reg.exe (PID: 2120)
- reg.exe (PID: 3640)
- reg.exe (PID: 7664)
- reg.exe (PID: 3800)
- reg.exe (PID: 7816)
- reg.exe (PID: 7176)
- reg.exe (PID: 7844)
- reg.exe (PID: 6068)
- reg.exe (PID: 6680)
- reg.exe (PID: 3820)
- reg.exe (PID: 2400)
- reg.exe (PID: 420)
- reg.exe (PID: 3800)
- reg.exe (PID: 6320)
Reads Internet Explorer settings
- mshta.exe (PID: 7356)
- mshta.exe (PID: 6544)
Checks supported languages
- mode.com (PID: 6876)
- mode.com (PID: 2596)
- csc.exe (PID: 5496)
- cvtres.exe (PID: 6620)
- expand.exe (PID: 8104)
- csc.exe (PID: 8188)
- cvtres.exe (PID: 2096)
- mode.com (PID: 7044)
- mode.com (PID: 1300)
- center.exe (PID: 7400)
- mode.com (PID: 8080)
- mode.com (PID: 7948)
- mode.com (PID: 8068)
- csc.exe (PID: 7044)
- cvtres.exe (PID: 7116)
- mode.com (PID: 7380)
- expand.exe (PID: 5960)
Starts MODE.COM to configure console settings
- mode.com (PID: 6876)
- mode.com (PID: 2596)
- mode.com (PID: 8080)
- mode.com (PID: 7044)
- mode.com (PID: 1300)
- mode.com (PID: 7948)
- mode.com (PID: 8068)
- mode.com (PID: 7380)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5724)
- powershell.exe (PID: 7864)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7864)
- powershell.exe (PID: 5724)
Checks proxy server information
- mshta.exe (PID: 7356)
- slui.exe (PID: 2400)
Checks operating system version
- cmd.exe (PID: 3620)
- cmd.exe (PID: 1728)
Create files in a temporary directory
- csc.exe (PID: 5496)
- cvtres.exe (PID: 6620)
- expand.exe (PID: 8104)
- csc.exe (PID: 8188)
- cvtres.exe (PID: 2096)
- csc.exe (PID: 7044)
- cvtres.exe (PID: 7116)
- expand.exe (PID: 5960)
Reads the machine GUID from the registry
- expand.exe (PID: 8104)
- csc.exe (PID: 5496)
- csc.exe (PID: 8188)
- csc.exe (PID: 7044)
- expand.exe (PID: 5960)
The sample compiled with english language support
- expand.exe (PID: 8104)
- chrome.exe (PID: 7156)
Reads the software policy settings
- slui.exe (PID: 2400)
Executable content was dropped or overwritten
- chrome.exe (PID: 7156)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1156)
- WMIC.exe (PID: 7612)
- WMIC.exe (PID: 7468)
- WMIC.exe (PID: 4576)
- WMIC.exe (PID: 2508)
- WMIC.exe (PID: 5952)
- WMIC.exe (PID: 6840)
- WMIC.exe (PID: 2732)
- WMIC.exe (PID: 6452)
- WMIC.exe (PID: 5620)
- WMIC.exe (PID: 6900)
- WMIC.exe (PID: 7204)
- WMIC.exe (PID: 1068)
- WMIC.exe (PID: 7368)
- WMIC.exe (PID: 7488)
- WMIC.exe (PID: 4824)
- cscript.exe (PID: 4544)
- WMIC.exe (PID: 7404)
- WMIC.exe (PID: 6172)
- WMIC.exe (PID: 592)
- WMIC.exe (PID: 1864)
- WMIC.exe (PID: 7048)
- WMIC.exe (PID: 5284)
- WMIC.exe (PID: 7364)
- WMIC.exe (PID: 4052)
- WMIC.exe (PID: 3972)
- WMIC.exe (PID: 2836)
- WMIC.exe (PID: 6236)
- WMIC.exe (PID: 7944)
- WMIC.exe (PID: 2648)
- WMIC.exe (PID: 5456)
- WMIC.exe (PID: 3392)
- WMIC.exe (PID: 4540)
- WMIC.exe (PID: 6504)
- WMIC.exe (PID: 7800)
- WMIC.exe (PID: 7792)
- WMIC.exe (PID: 7224)
- WMIC.exe (PID: 5764)
- WMIC.exe (PID: 1872)
- WMIC.exe (PID: 8188)
- WMIC.exe (PID: 6172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
782
Monitored processes
633
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgABAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=1804,i,5570540336654165623,13323059347429360083,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=1980 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 420 | reg query HKLM\SOFTWARE\WOW6432Node\Microsoft\Office\16.0\Common\InstallRoot /v Path | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
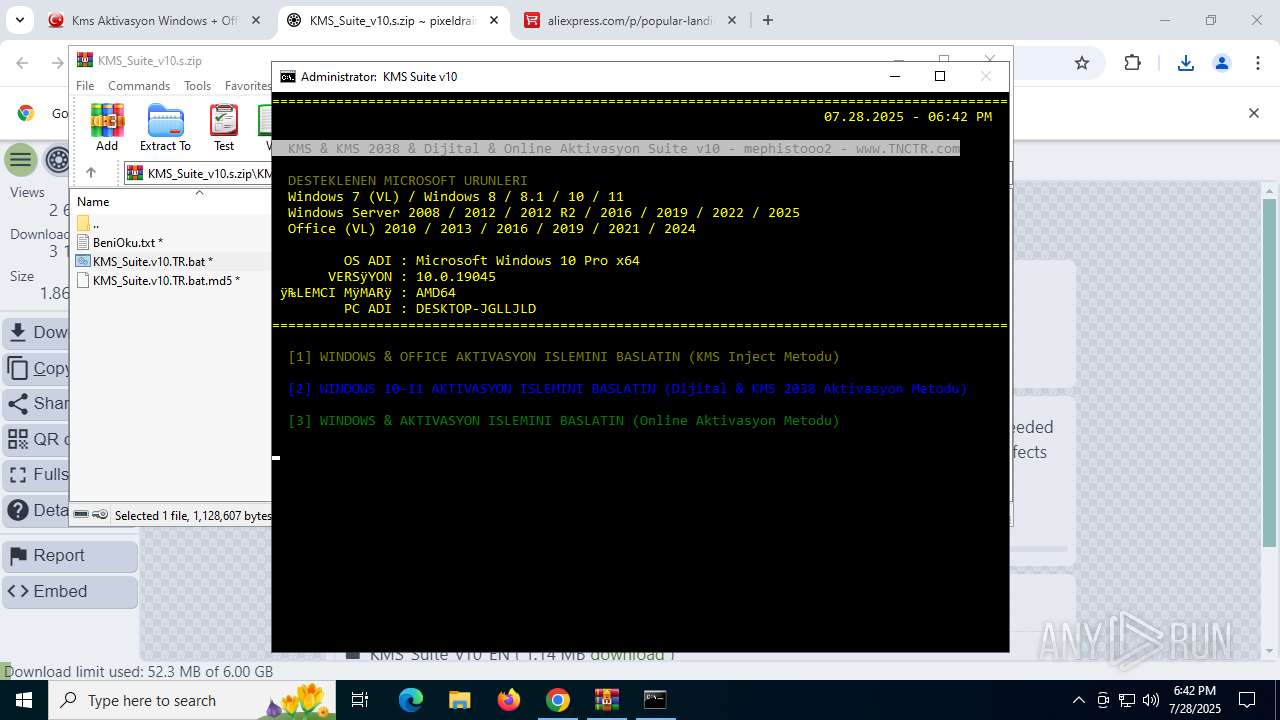
| 432 | C:\WINDOWS\system32\cmd.exe /c wmic path SoftwareLicensingProduct where "ApplicationID='55c92734-d682-4d71-983e-d6ec3f16059f' and Description like '%KMSCLIENT%' " get ID /value | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 476 | reg query HKLM\SOFTWARE\WOW6432Node\Microsoft\Office\15.0\ClickToRun /v InstallPath | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 476 | findstr /I /C:"Word2019Retail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 592 | wmic path SoftwareLicensingProduct where "LicenseStatus='1' and Description like '%KMSCLIENT%' " get Name /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | C:\WINDOWS\system32\cmd.exe /c ECHO Microsoft-Windows-ProfessionalEdition~31bf3856ad364e35~amd64~~10.0.19041.4046 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | findstr /I /C:"Word2021Volume" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | reg query "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\msoxmled.exe" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | find /i "STOPPED" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
89 256
Read events
89 180
Write events
63
Delete events
13
Modification events
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (7288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7288) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\KMS_Suite_v10.s.zip | |||
Executable files
12
Suspicious files
100
Text files
120
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF18e27b.TMP | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF18e27b.TMP | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF18e28b.TMP | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RF18e2aa.TMP | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SignalDB\LOG.old~RF18e2c9.TMP | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF18e2aa.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
145
DNS requests
161
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1632 | chrome.exe | GET | 200 | 142.250.184.238:80 | http://clients2.google.com/time/1/current?cup2key=8:YxTPV2aNuwj3J-i_vwWPldI8d-bISspqNidwKgpMZsc&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1632 | chrome.exe | GET | 301 | 172.67.164.228:80 | http://www.fullprogramlarindir.com/wp-content/uploads/2014/03/Download.png | unknown | — | — | whitelisted |
2980 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1632 | chrome.exe | GET | 301 | 172.67.164.228:80 | http://www.fullprogramlarindir.com/wp-content/uploads/2014/03/Download.png | unknown | — | — | whitelisted |
1632 | chrome.exe | GET | 301 | 172.67.164.228:80 | http://www.fullprogramlarindir.com/wp-content/uploads/2014/03/Download.png | unknown | — | — | whitelisted |
1632 | chrome.exe | GET | 301 | 172.67.164.228:80 | http://www.fullprogramlarindir.com/wp-content/uploads/2014/03/Download.png | unknown | — | — | whitelisted |
1632 | chrome.exe | GET | 301 | 172.67.164.228:80 | http://www.fullprogramlarindir.com/wp-content/uploads/2014/03/Download.png | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8040 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6356 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1632 | chrome.exe | 142.250.184.238:80 | clients2.google.com | GOOGLE | US | whitelisted |
1632 | chrome.exe | 172.217.16.202:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
1632 | chrome.exe | 104.26.5.158:443 | www.fullprogramlarindir.net | CLOUDFLARENET | US | unknown |
1632 | chrome.exe | 74.125.133.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
1632 | chrome.exe | 142.250.184.234:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
www.fullprogramlarindir.net |
| unknown |
accounts.google.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.fullprogramlarindir.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
cdn.fastcomments.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
1632 | chrome.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
1632 | chrome.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
1632 | chrome.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | Potential Corporate Privacy Violation | ET INFO External IP Lookup (ipify .org) |
1632 | chrome.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
1632 | chrome.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
1632 | chrome.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
1632 | chrome.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
1632 | chrome.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (pixeldrain .com) |