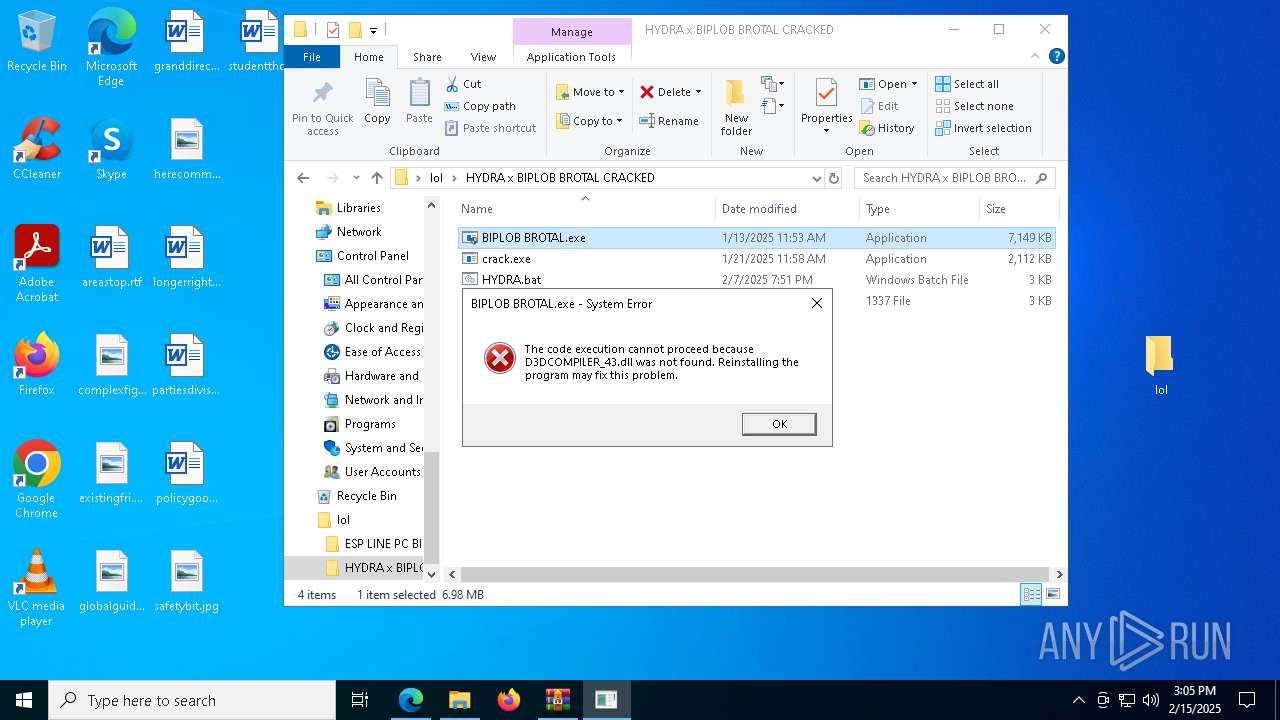
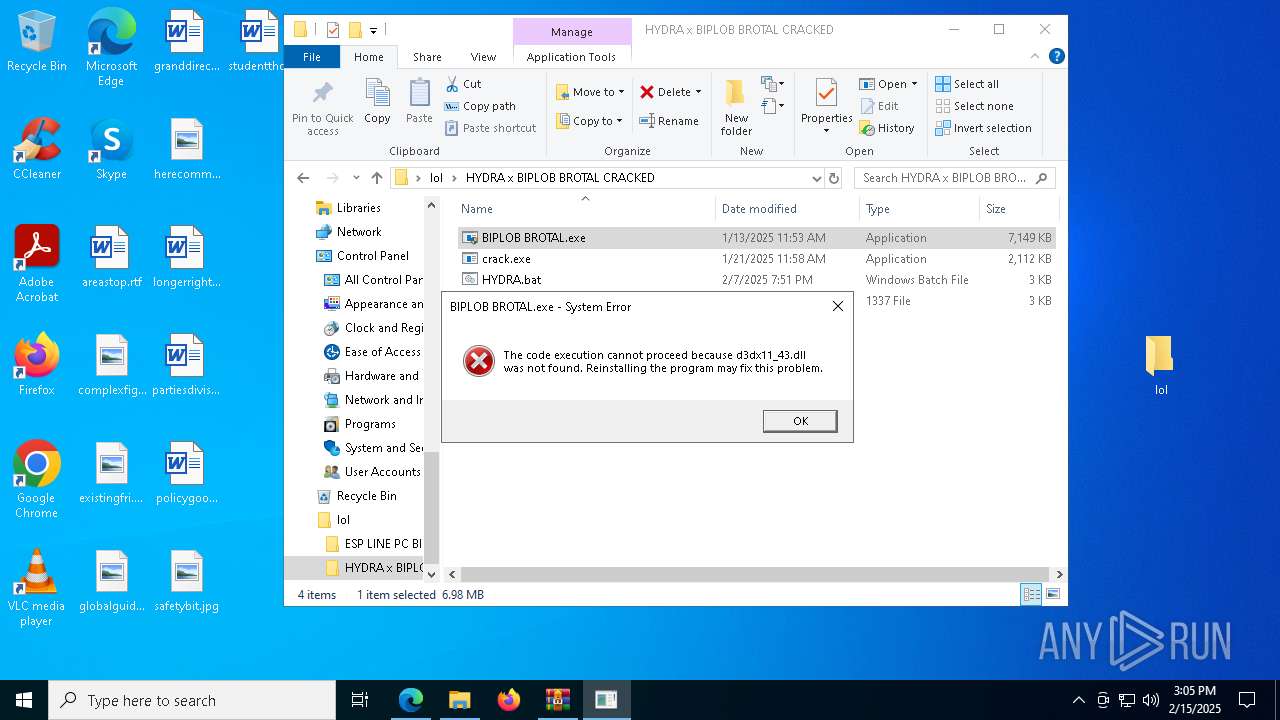
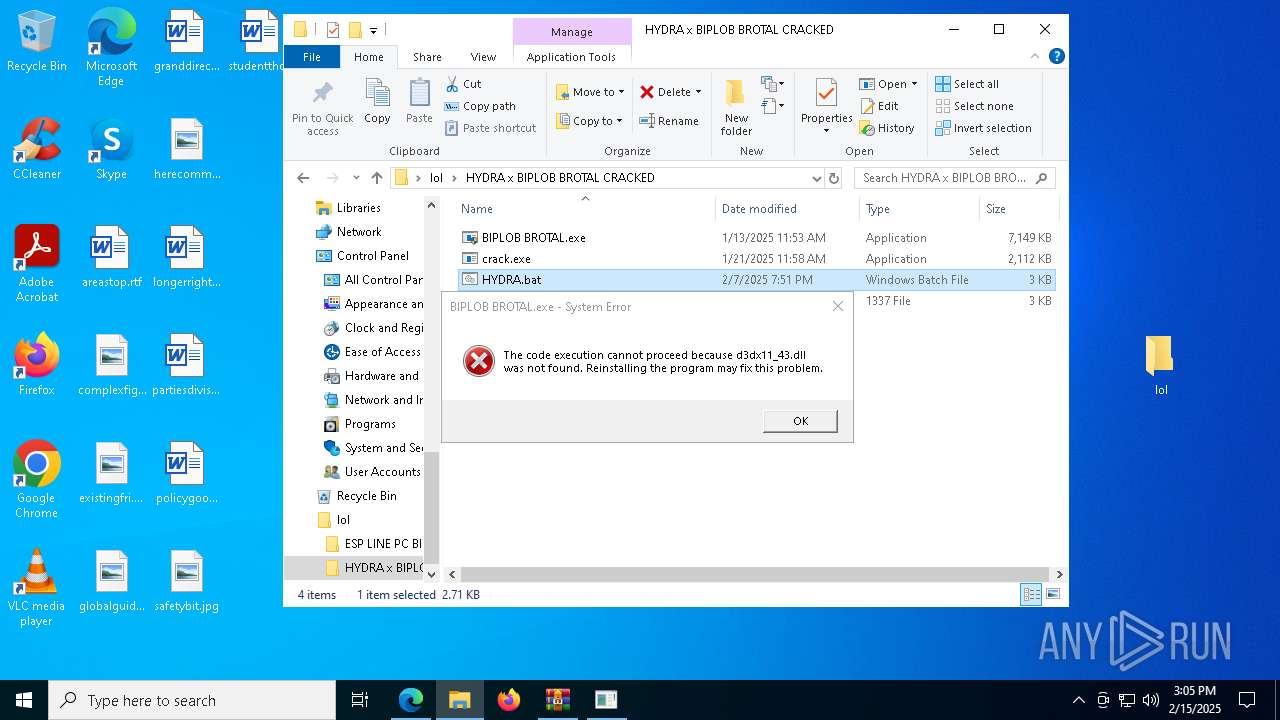
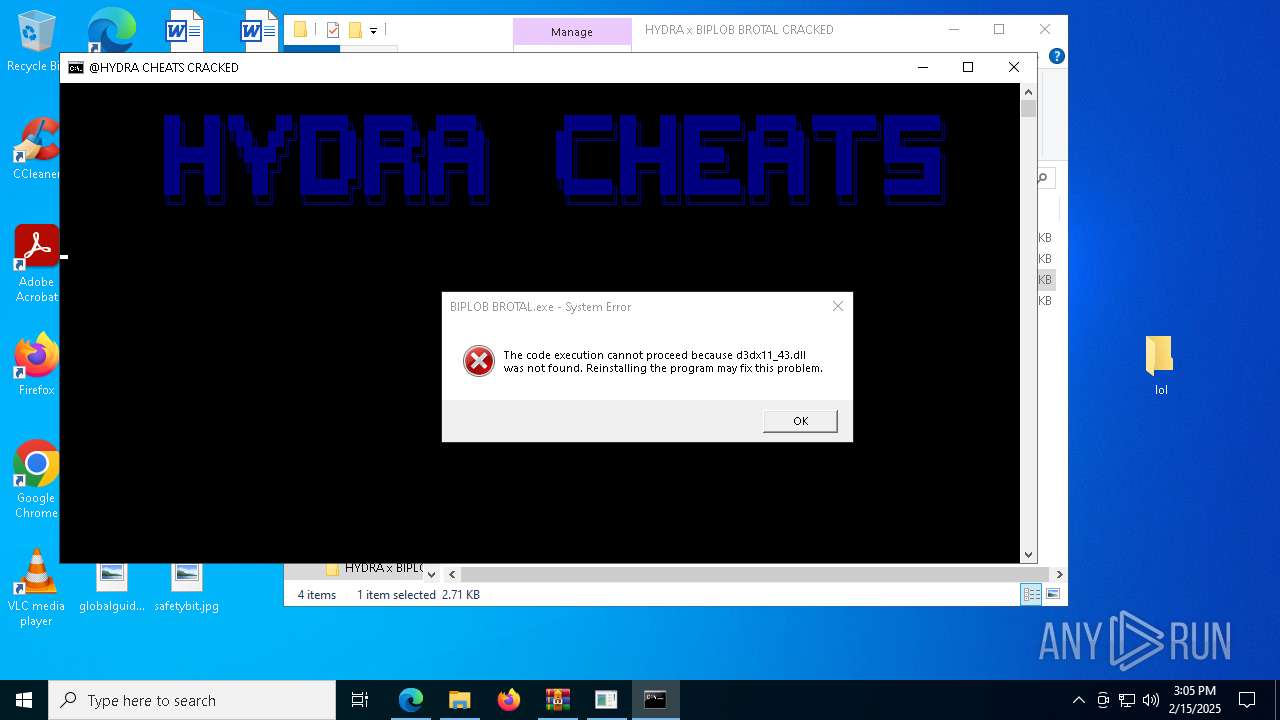
| URL: | https://limewire.com/d/5aa4eb6b-ccfa-4b6b-a3c5-9ef0233ee2b6#nnlRhiIc5rx1acvb83nOYMRv1L0sOVMLMRKUdzDRgUc |
| Full analysis: | https://app.any.run/tasks/bc4485b9-5654-43a5-8a22-197616299791 |
| Verdict: | Malicious activity |
| Analysis date: | February 15, 2025, 15:04:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8382D8F3279F147F5C101344C26CB091 |
| SHA1: | A18CE9B1845B30B36AD5111F9C844E89C70F471E |
| SHA256: | 2AAE5F1438241FDD098C7359CAD6CC77A05AB19E84C513E4D4004162ADD2EA89 |
| SSDEEP: | 3:N8MIA/enKQEVTH7BILcVzHTujTU6rwBcz:2MIA/eKRVTbBdTujTUS0w |
MALICIOUS
No malicious indicators.SUSPICIOUS
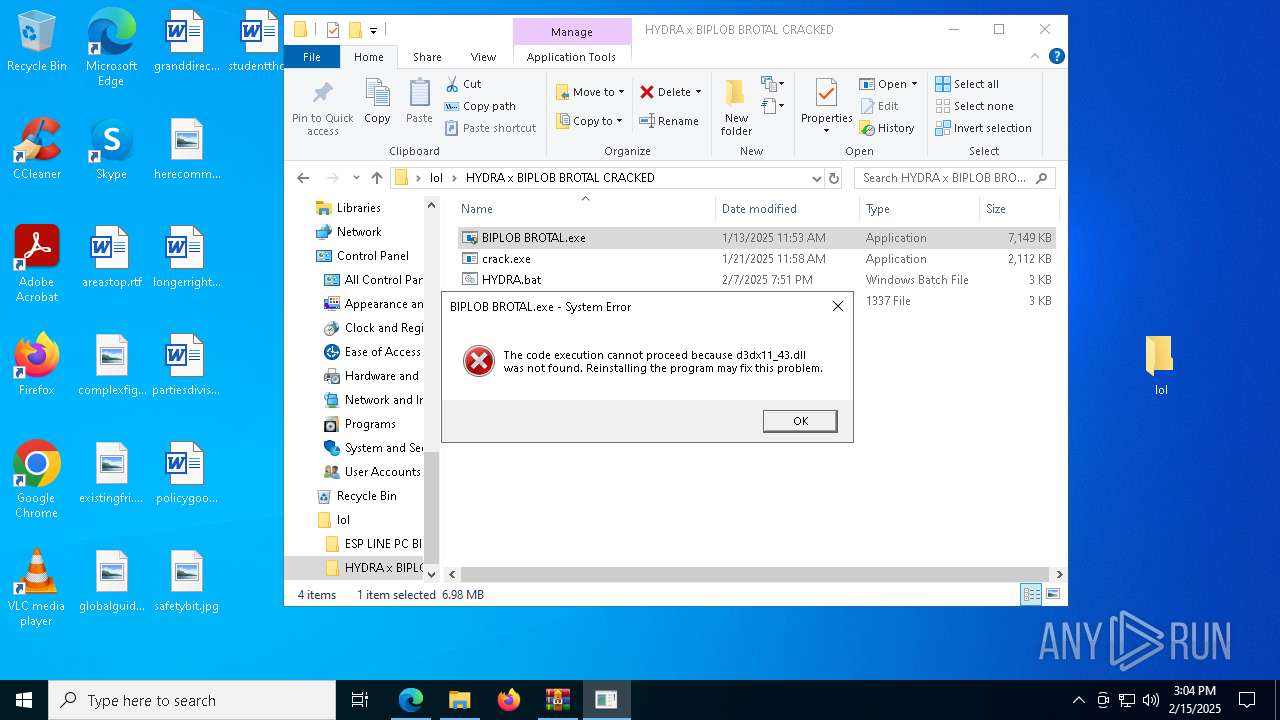
Starts application with an unusual extension
- cmd.exe (PID: 4740)
- cmd.exe (PID: 8040)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4740)
- cmd.exe (PID: 8040)
Starts NET.EXE to display or manage information about active sessions
- net.exe (PID: 7908)
- cmd.exe (PID: 4740)
- cmd.exe (PID: 8040)
- net.exe (PID: 7580)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4740)
- cmd.exe (PID: 8040)
Starts process via Powershell
- powershell.exe (PID: 8044)
- powershell.exe (PID: 7768)
Executing commands from a ".bat" file
- powershell.exe (PID: 8044)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 8044)
- cmd.exe (PID: 8040)
Application launched itself
- cmd.exe (PID: 8040)
Get information on the list of running processes
- cmd.exe (PID: 8040)
- cmd.exe (PID: 6176)
INFO
Reads Environment values
- identity_helper.exe (PID: 7824)
Application launched itself
- msedge.exe (PID: 6276)
Checks supported languages
- identity_helper.exe (PID: 7824)
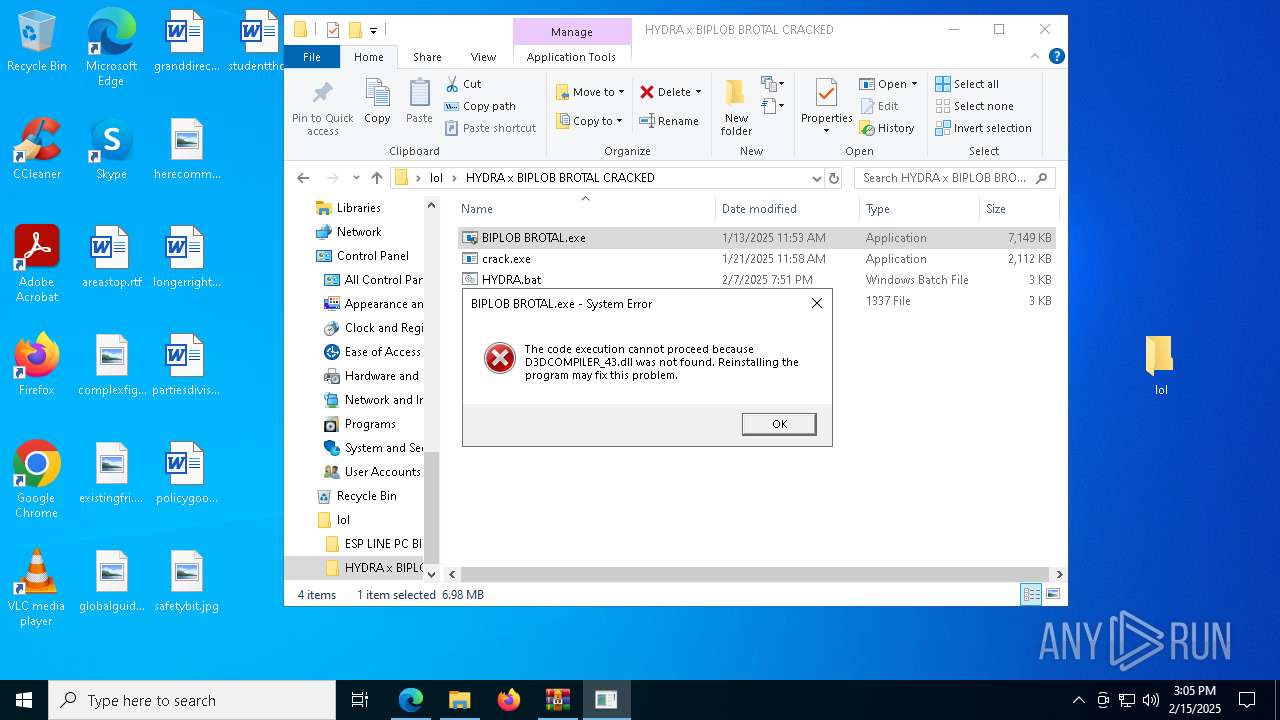
- crack.exe (PID: 5544)
- crack.exe (PID: 1572)
- crack.exe (PID: 8)
- crack.exe (PID: 8136)
- chcp.com (PID: 1512)
- chcp.com (PID: 4320)
- crack.exe (PID: 1572)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3808)
- msedge.exe (PID: 3792)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6276)
Reads the computer name
- identity_helper.exe (PID: 7824)
Manual execution by a user
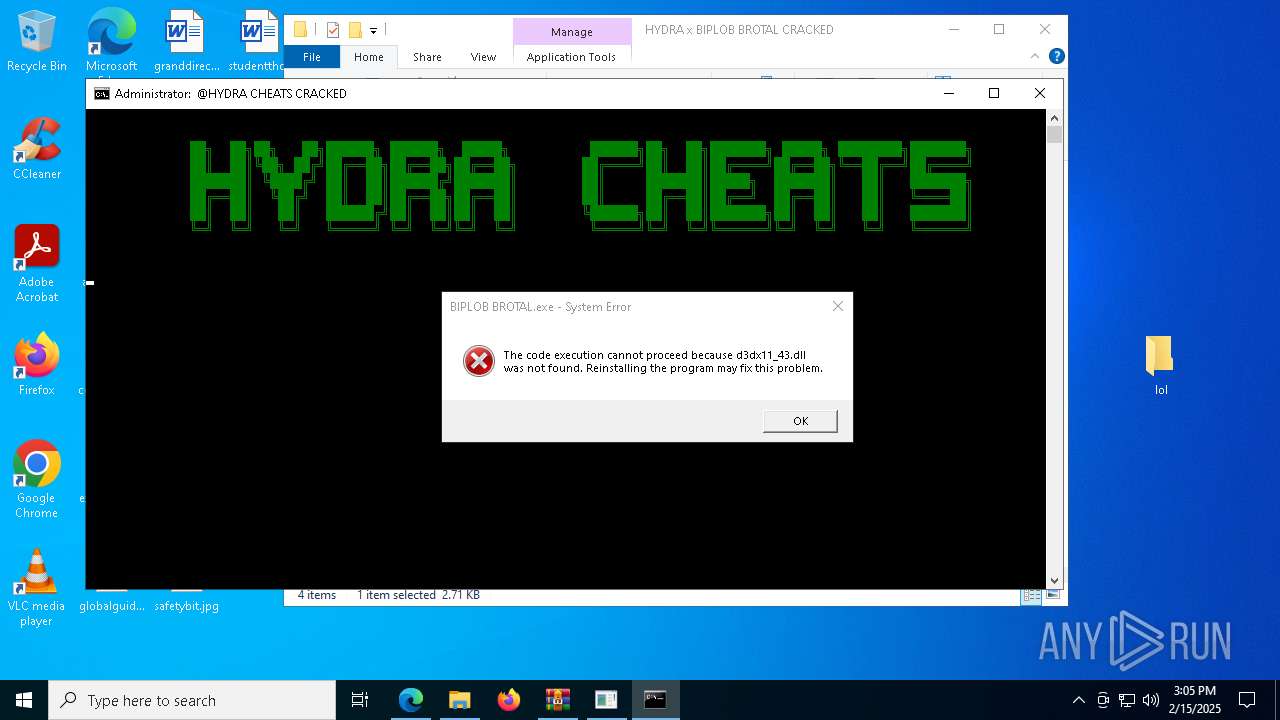
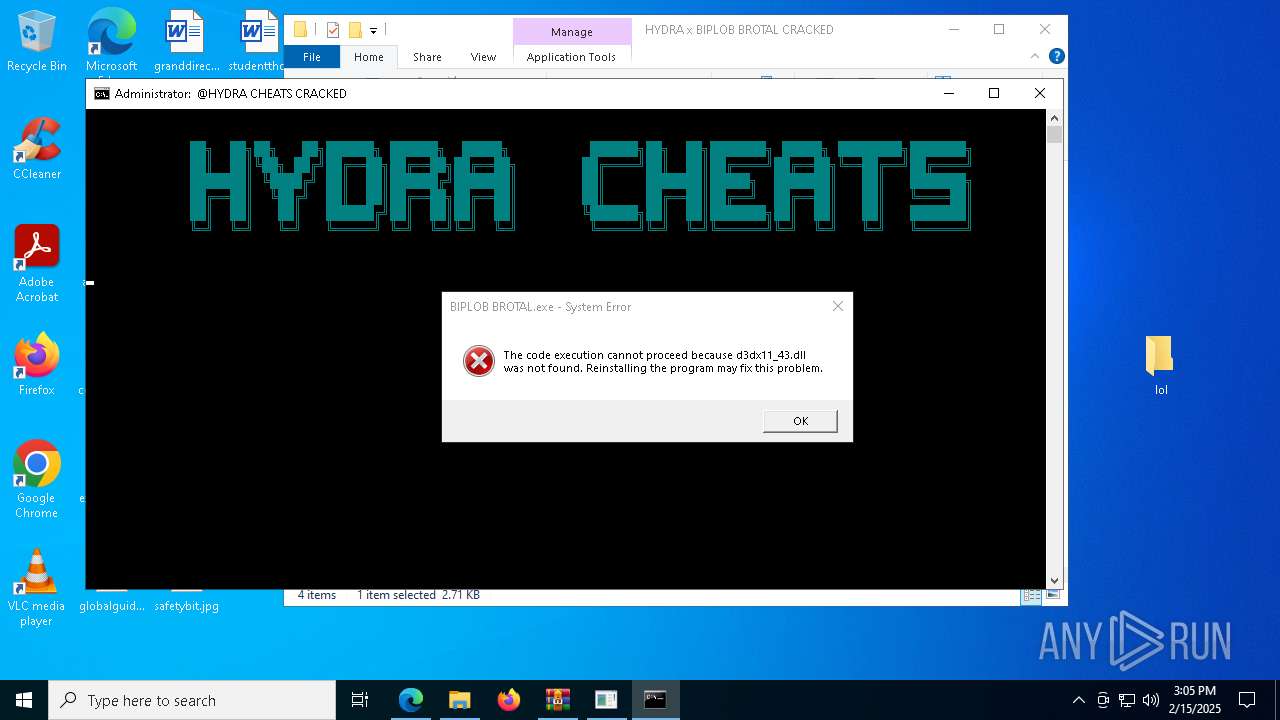
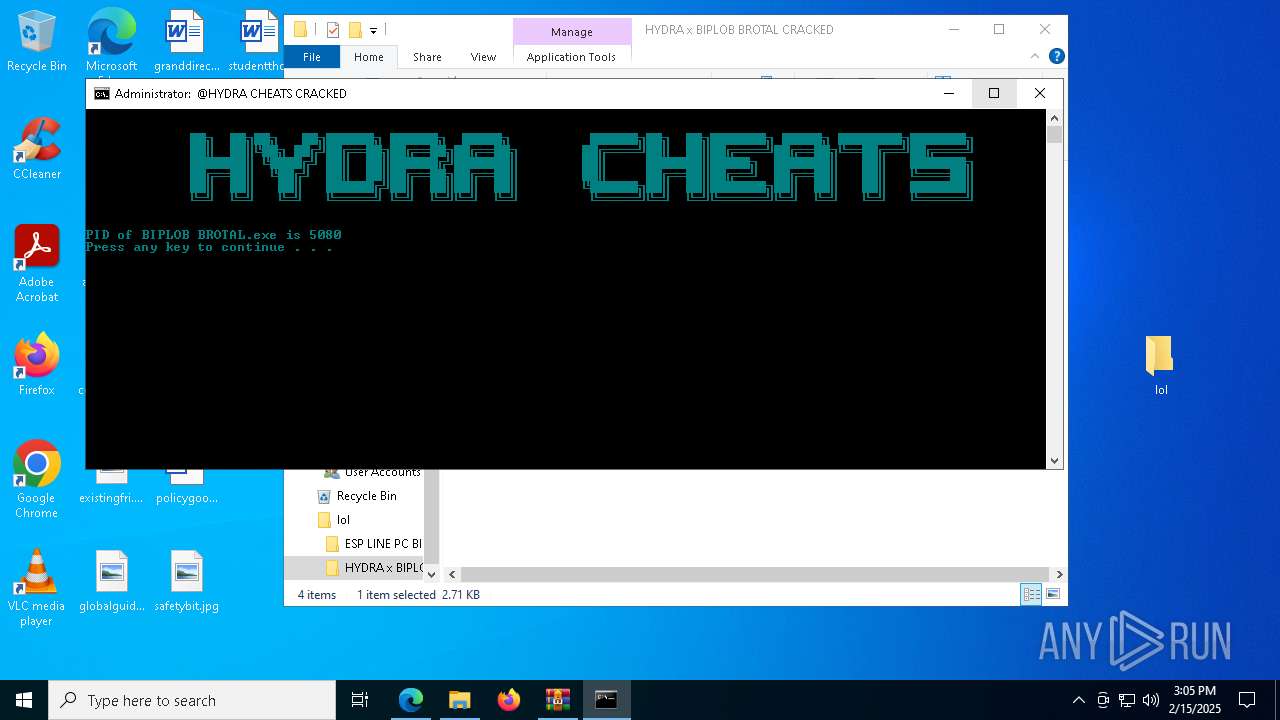
- BIPLOB BROTAL.exe (PID: 5392)
- crack.exe (PID: 1572)
- crack.exe (PID: 5544)
- crack.exe (PID: 8136)
- crack.exe (PID: 8)
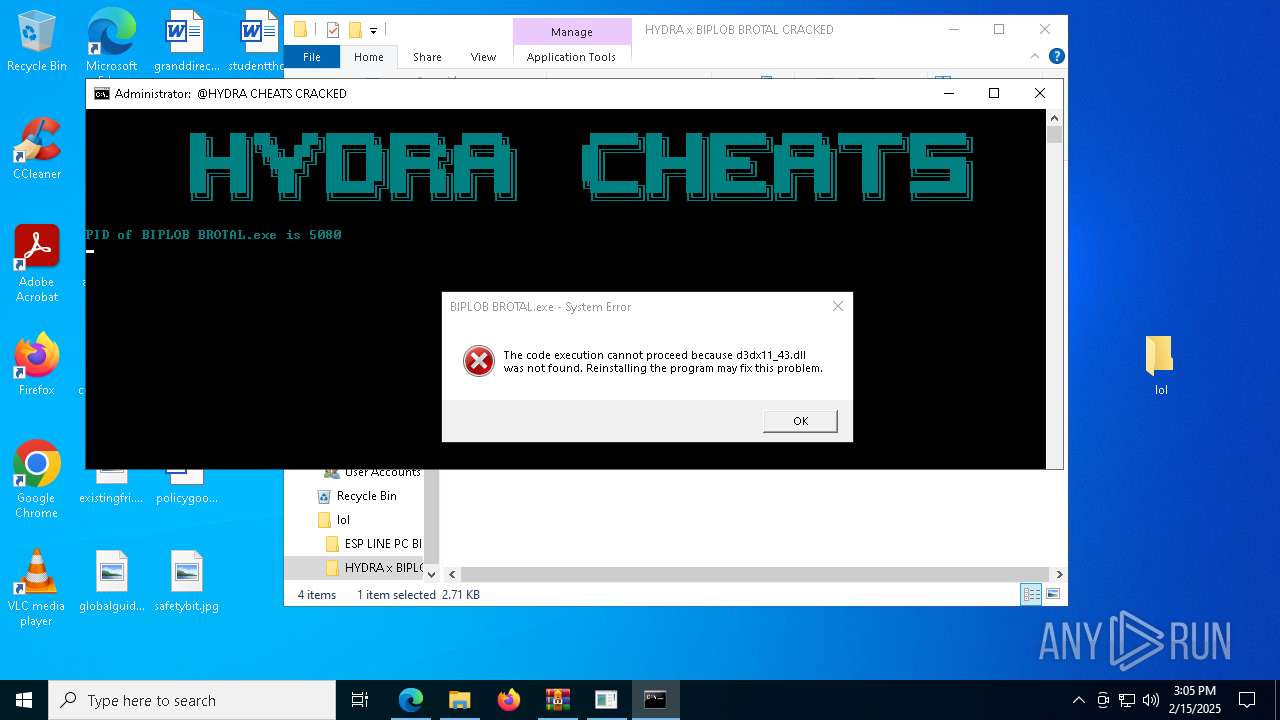
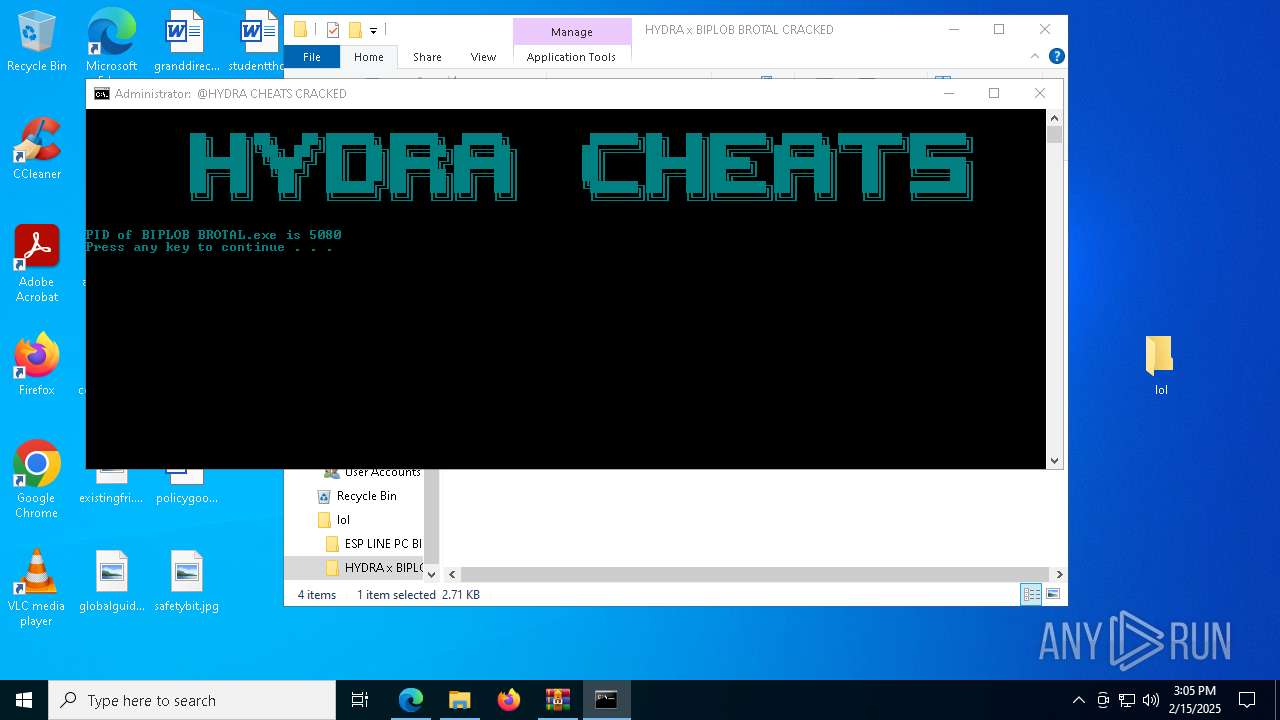
- BIPLOB BROTAL.exe (PID: 5080)
- cmd.exe (PID: 4740)
- BIPLOB BROTAL.exe (PID: 7512)
Changes the display of characters in the console
- cmd.exe (PID: 4740)
- cmd.exe (PID: 8040)
VMProtect protector has been detected
- BIPLOB BROTAL.exe (PID: 5080)
The sample compiled with english language support
- msedge.exe (PID: 3792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
230
Monitored processes
96
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
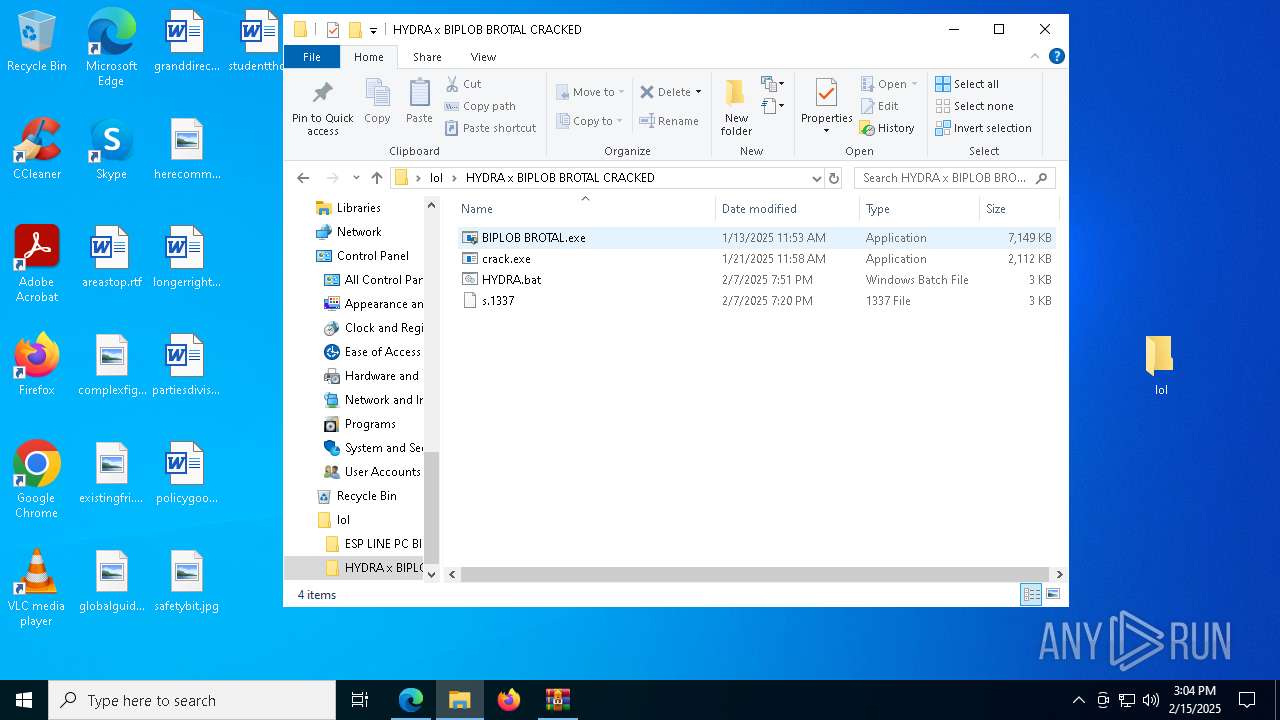
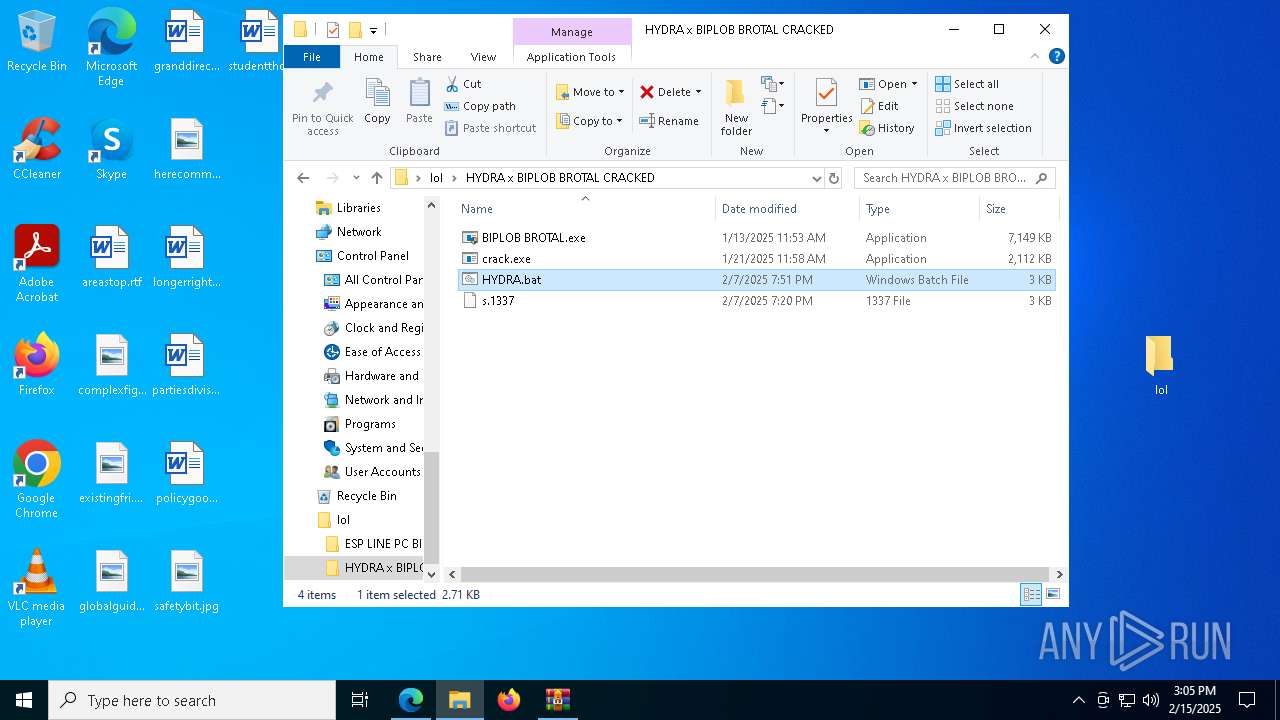
| 8 | "C:\Users\admin\Desktop\lol\HYDRA x BIPLOB BROTAL CRACKED\crack.exe" | C:\Users\admin\Desktop\lol\HYDRA x BIPLOB BROTAL CRACKED\crack.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1512 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1536 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5516 --field-trial-handle=2192,i,4089813030039356389,13885092378101397200,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1572 | "C:\Users\admin\Desktop\lol\HYDRA x BIPLOB BROTAL CRACKED\crack.exe" | C:\Users\admin\Desktop\lol\HYDRA x BIPLOB BROTAL CRACKED\crack.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1572 | "C:\Users\admin\Desktop\lol\HYDRA x BIPLOB BROTAL CRACKED\crack.exe" "C:\Users\admin\Desktop\lol\HYDRA x BIPLOB BROTAL CRACKED\s.1337" -pid 5080 -force | C:\Users\admin\Desktop\lol\HYDRA x BIPLOB BROTAL CRACKED\crack.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4 Modules
| |||||||||||||||
| 2076 | C:\WINDOWS\system32\net1 session | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5964 --field-trial-handle=2192,i,4089813030039356389,13885092378101397200,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2792 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2800 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --no-appcompat-clear --mojo-platform-channel-handle=5380 --field-trial-handle=2192,i,4089813030039356389,13885092378101397200,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2828 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3816 --field-trial-handle=2192,i,4089813030039356389,13885092378101397200,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
16 300
Read events
16 263
Write events
37
Delete events
0
Modification events
| (PID) Process: | (6276) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6276) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6276) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6276) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6276) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 6F599EE3C58C2F00 | |||
| (PID) Process: | (6276) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 9F8AA4E3C58C2F00 | |||
| (PID) Process: | (6276) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524798 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {7F3FE140-14F6-414F-864F-AEAC9383F16F} | |||
| (PID) Process: | (6276) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524798 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {079C2061-BA80-4CF1-B402-5E0EBBDAC89B} | |||
| (PID) Process: | (6276) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524798 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {B77DCEF0-01FF-4B58-8D53-4B435A664A72} | |||
| (PID) Process: | (6276) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524798 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {46DF23F5-9B45-48B2-880E-EA6012EC6631} | |||
Executable files
25
Suspicious files
701
Text files
102
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1349ed.TMP | — | |
MD5:— | SHA256:— | |||
| 6276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1349fd.TMP | — | |
MD5:— | SHA256:— | |||
| 6276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1349fd.TMP | — | |
MD5:— | SHA256:— | |||
| 6276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1349ed.TMP | — | |
MD5:— | SHA256:— | |||
| 6276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF134a3b.TMP | — | |
MD5:— | SHA256:— | |||
| 6276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
88
DNS requests
98
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
720 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7716 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1739801480&P2=404&P3=2&P4=DwMFx7LAeaVOzkKt3GBhhsJa1KinEzC%2bTEj0Sm1VHr6%2f%2bHkY9Lc%2bn6A5x9PEmU74xaeaaE6cWY0jHyg9mB8mzA%3d%3d | unknown | — | — | whitelisted |
6876 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6876 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7716 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1739801480&P2=404&P3=2&P4=DwMFx7LAeaVOzkKt3GBhhsJa1KinEzC%2bTEj0Sm1VHr6%2f%2bHkY9Lc%2bn6A5x9PEmU74xaeaaE6cWY0jHyg9mB8mzA%3d%3d | unknown | — | — | whitelisted |
7716 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1739801480&P2=404&P3=2&P4=DwMFx7LAeaVOzkKt3GBhhsJa1KinEzC%2bTEj0Sm1VHr6%2f%2bHkY9Lc%2bn6A5x9PEmU74xaeaaE6cWY0jHyg9mB8mzA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2324 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
716 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3976 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6276 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
limewire.com |
| unknown |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6652 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare R2 Storage (r2 .cloudflarestorage .com) |
6652 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare R2 Storage (r2 .cloudflarestorage .com) |
6652 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |
6652 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |