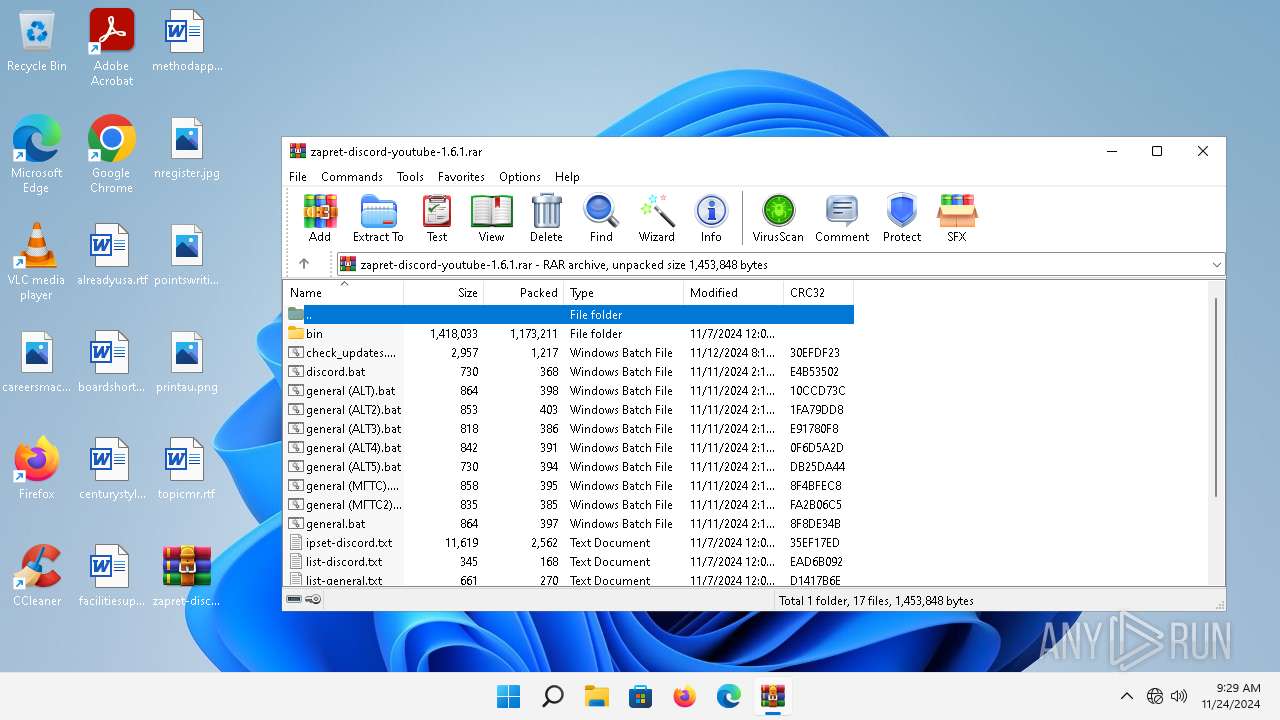
| File name: | zapret-discord-youtube-1.6.1.rar |
| Full analysis: | https://app.any.run/tasks/b9e184c1-47fd-4bf4-8e57-fbe7ae6a3fec |
| Verdict: | Malicious activity |
| Analysis date: | November 24, 2024, 09:29:04 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | DB6DDF779FEDE5B17A289880EB2CE217 |
| SHA1: | DF3ACA68FB4D28116FD17C286907DE4709E50F2A |
| SHA256: | 2AAC3961D99AB14BEE7BC9D4CC3ABDA083050BE23456BF15C4BAA2B580CF9B70 |
| SSDEEP: | 49152:nD2pC3Q/k0bvTtqsyTDWaxsJ/tfjnlcNw7hqnFTII6w8b+IWx8n/cYZrECWSBVcx:Dx3Q/k0dYT6axYhzIZnFkI6fHRcYZr/C |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3040)
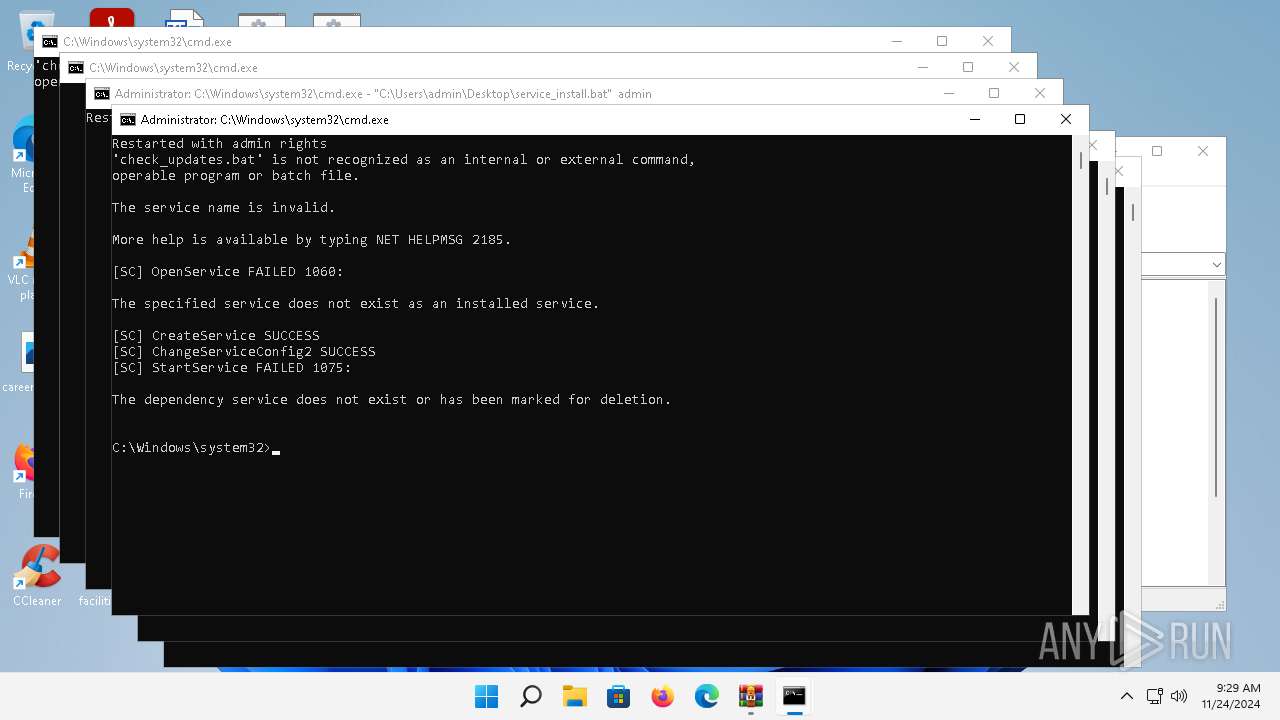
Starts NET.EXE for service management
- cmd.exe (PID: 1688)
- net.exe (PID: 1804)
- net.exe (PID: 1424)
- net.exe (PID: 32)
- cmd.exe (PID: 4604)
- net.exe (PID: 6064)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3040)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5524)
- cmd.exe (PID: 1408)
- cmd.exe (PID: 2196)
- cmd.exe (PID: 4080)
- cmd.exe (PID: 2780)
- cmd.exe (PID: 6904)
- cmd.exe (PID: 2824)
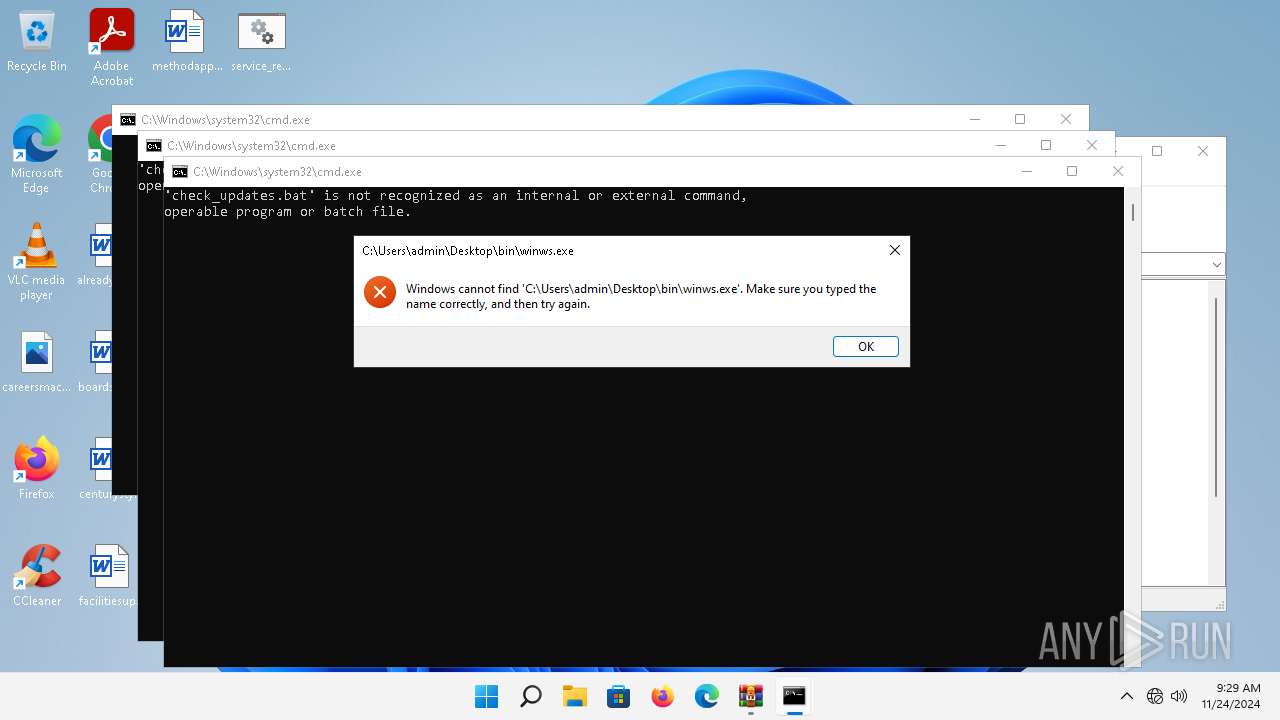
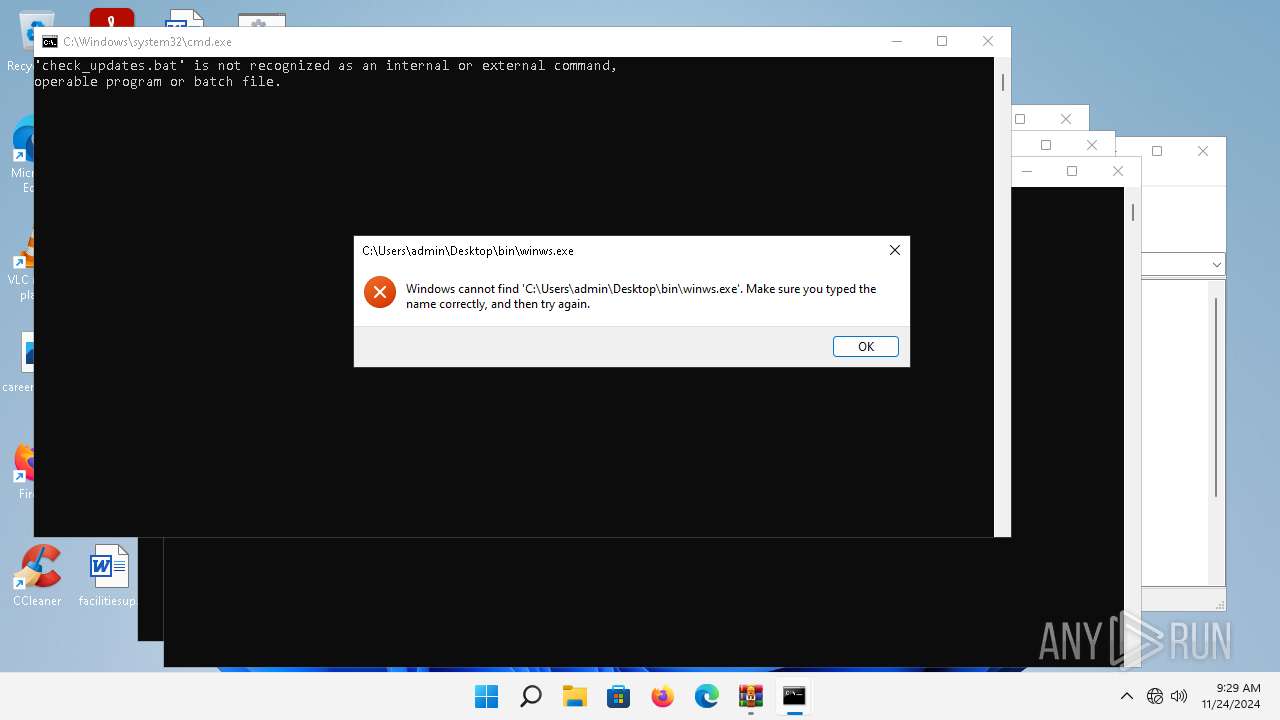
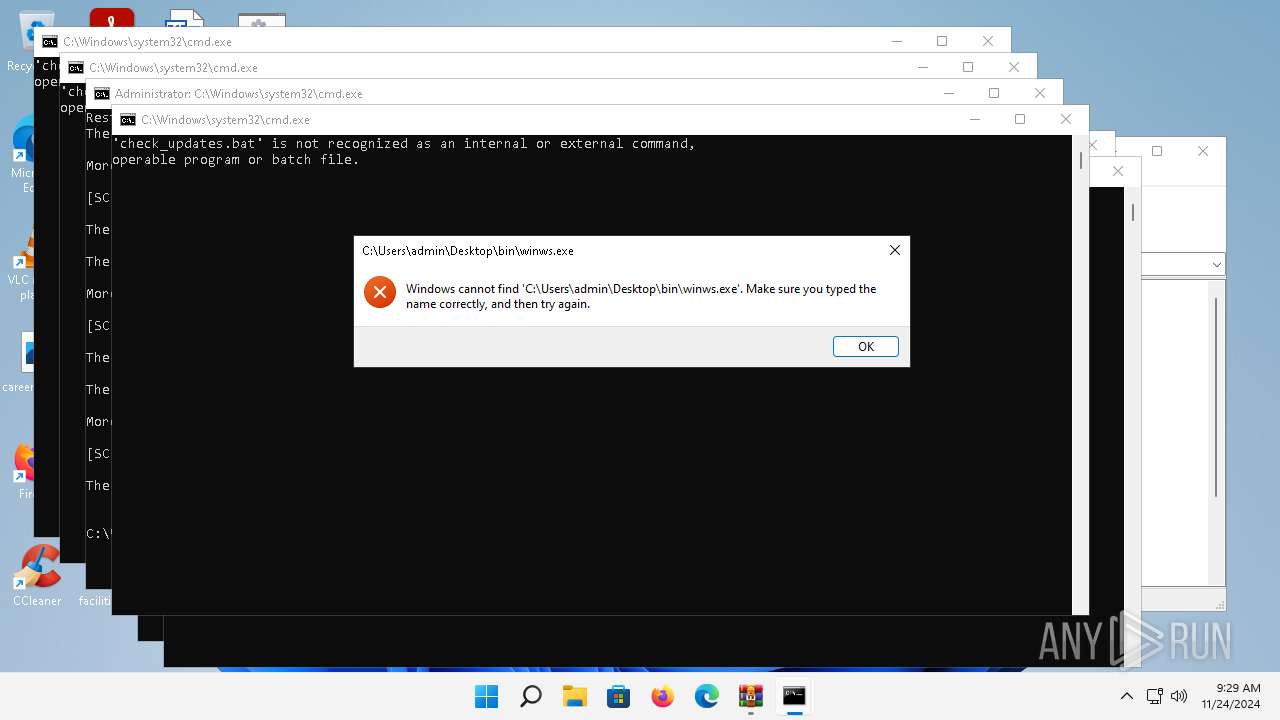
Starts application with an unusual extension
- cmd.exe (PID: 5524)
- cmd.exe (PID: 1512)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 1688)
- cmd.exe (PID: 1208)
- cmd.exe (PID: 5144)
- cmd.exe (PID: 2536)
- cmd.exe (PID: 1408)
- cmd.exe (PID: 7056)
- cmd.exe (PID: 2196)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 6500)
- cmd.exe (PID: 4604)
Reads the Internet Settings
- powershell.exe (PID: 6232)
- powershell.exe (PID: 1840)
- powershell.exe (PID: 4668)
- powershell.exe (PID: 5808)
- powershell.exe (PID: 440)
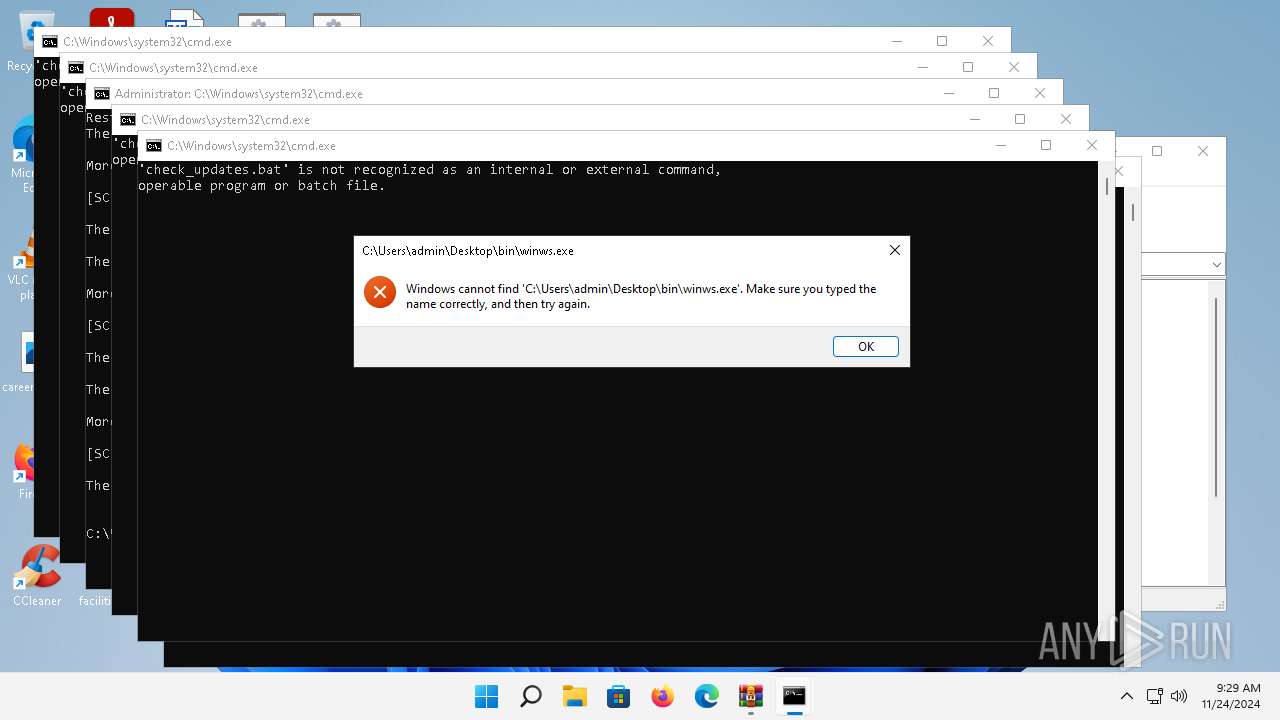
Executing commands from a ".bat" file
- powershell.exe (PID: 6232)
- powershell.exe (PID: 1840)
- powershell.exe (PID: 5808)
Starts process via Powershell
- powershell.exe (PID: 6232)
- powershell.exe (PID: 1840)
- powershell.exe (PID: 5808)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 6232)
- powershell.exe (PID: 1840)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 6500)
- powershell.exe (PID: 5808)
Starts SC.EXE for service management
- cmd.exe (PID: 1688)
- cmd.exe (PID: 4604)
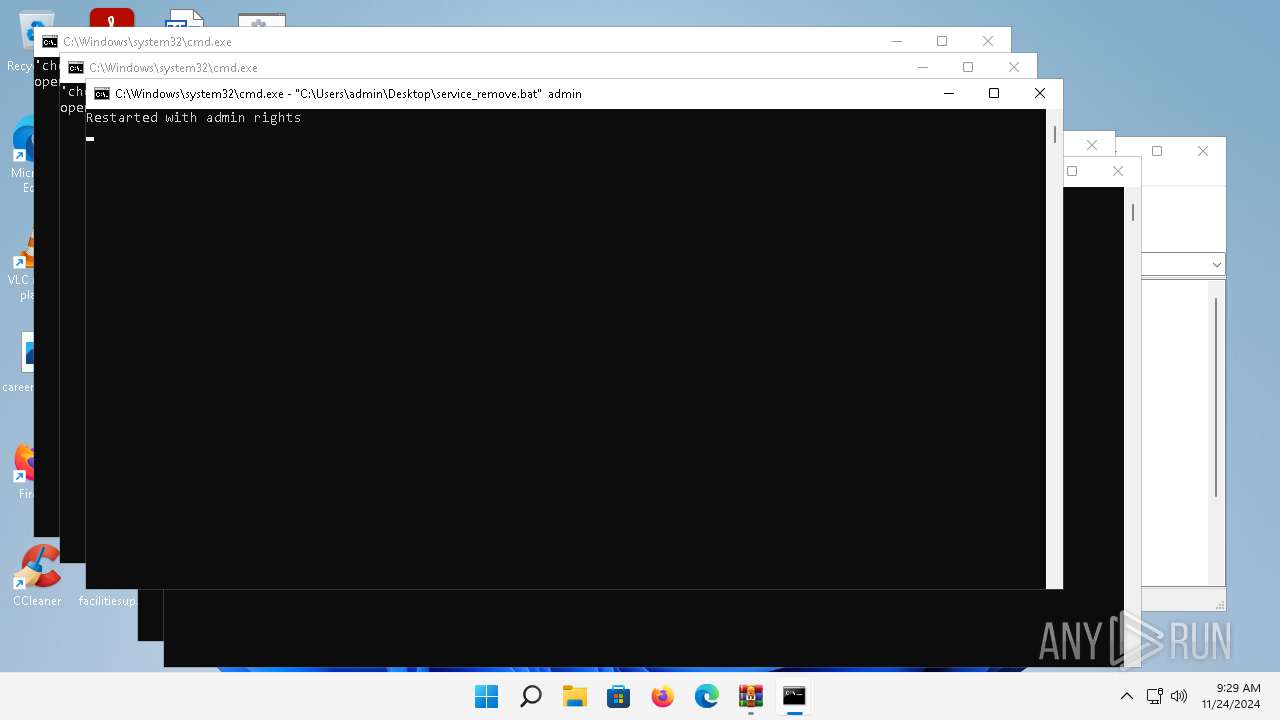
Application launched itself
- cmd.exe (PID: 6712)
- cmd.exe (PID: 6500)
Hides command output
- cmd.exe (PID: 6904)
- cmd.exe (PID: 2824)
INFO
Changes the display of characters in the console
- cmd.exe (PID: 5524)
- cmd.exe (PID: 1208)
- cmd.exe (PID: 1512)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 1688)
- cmd.exe (PID: 5144)
- cmd.exe (PID: 2536)
- cmd.exe (PID: 1408)
- cmd.exe (PID: 7056)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 6500)
- cmd.exe (PID: 2196)
- cmd.exe (PID: 4604)
Manual execution by a user
- cmd.exe (PID: 1208)
- cmd.exe (PID: 5524)
- cmd.exe (PID: 5144)
- cmd.exe (PID: 1512)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 2536)
- cmd.exe (PID: 1408)
- cmd.exe (PID: 7056)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 2196)
Checks supported languages
- chcp.com (PID: 6556)
- chcp.com (PID: 3424)
- chcp.com (PID: 2944)
- chcp.com (PID: 1316)
- chcp.com (PID: 7144)
- chcp.com (PID: 5768)
- chcp.com (PID: 2428)
- chcp.com (PID: 6776)
- chcp.com (PID: 1584)
- chcp.com (PID: 3828)
- chcp.com (PID: 4832)
- chcp.com (PID: 664)
- chcp.com (PID: 5804)
- chcp.com (PID: 1844)
The process uses the downloaded file
- powershell.exe (PID: 6232)
- powershell.exe (PID: 1840)
- powershell.exe (PID: 5808)
Disables trace logs
- powershell.exe (PID: 4668)
- powershell.exe (PID: 440)
Checks proxy server information
- powershell.exe (PID: 440)
- powershell.exe (PID: 4668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 2826 |
| UncompressedSize: | 7925 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | README.md |
Total processes
181
Monitored processes
67
Malicious processes
9
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | net stop zapret | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 32 | sc description zapret "zapret DPI bypass software" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | powershell -command "(Invoke-WebRequest -Uri https://raw.githubusercontent.com/Flowseal/zapret-discord-youtube/refs/heads/main/.service/version.txt -Headers @{\"Cache-Control\"=\"no-cache\"} -TimeoutSec 5).Content" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 764 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1016 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\general (ALT4).bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | powershell -command "[datetime]::Now.ToString('yyyy-MM-dd HH:mm:ss')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1148 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
32 583
Read events
32 532
Write events
51
Delete events
0
Modification events
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\zapret-discord-youtube-1.6.1.rar | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\4c\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
Executable files
0
Suspicious files
1
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1840 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_iq2zc4kl.4cf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1840 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dsgodsts.ry5.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2100 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_n52wx1ex.sek.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6232 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p4ogbxcj.wia.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6232 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_x5vbpshu.o1b.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 440 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cgyncsio.sjx.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 440 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fcnmyprh.vzx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6500 | cmd.exe | C:\Users\admin\Desktop\version.txt | text | |
MD5:ECC047A4C81F0A046BD148688F1588E7 | SHA256:955BB533250DE3BE2A3FF583E7E2D5E22F99A64B905304F156A274E95BE0D15C | |||
| 1116 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mgtffn2i.4ga.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5808 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zf50clnn.2ky.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
31
DNS requests
29
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1948 | rundll32.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?81c66ed9dca5d69f | unknown | — | — | whitelisted |
2524 | firefox.exe | POST | 200 | 95.101.74.224:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
2524 | firefox.exe | POST | 200 | 95.101.74.224:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
2524 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
2524 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
1296 | svchost.exe | GET | 200 | 95.101.74.215:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
6724 | MoUsoCoreWorker.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f0578ec7388e1ecb | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 69.192.160.109:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | unknown |
2524 | firefox.exe | POST | 200 | 95.101.74.224:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?bdb78aa50ddaee77 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5552 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4668 | OfficeC2RClient.exe | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
2524 | firefox.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
2524 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | whitelisted |
1948 | rundll32.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1296 | svchost.exe | 95.101.74.215:80 | r10.o.lencr.org | Akamai International B.V. | NL | whitelisted |
1948 | rundll32.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
4668 | OfficeC2RClient.exe | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
incoming.telemetry.mozilla.org |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
telemetry-incoming.r53-2.services.mozilla.com |
| whitelisted |
prod.remote-settings.prod.webservices.mozgcp.net |
| whitelisted |
google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ecs.office.com |
| whitelisted |
r10.o.lencr.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1296 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
1656 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |