| File name: | ZoomInfoContactContributor.exe |
| Full analysis: | https://app.any.run/tasks/923f86cf-7786-4706-bcfa-8cece7b73e5c |
| Verdict: | Malicious activity |
| Analysis date: | July 15, 2024, 04:58:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 0B5719E9FD40B85D4D95E475E9431CD0 |
| SHA1: | 132151D26E61D2FDA4E4B31EB376A41EA0D56E6D |
| SHA256: | 2AA9F15810E2C55DBC8522E386D76D1A8FB3A63A712B33E17BD2139A7B45C76B |
| SSDEEP: | 3072:mgXdZt9P6D3XJMzI7Op5KmEOm9Ek1ydrZeDAf1OnV8AHzsFypc95:me34qk7uUmq9EnvAH4F8u5 |
MALICIOUS
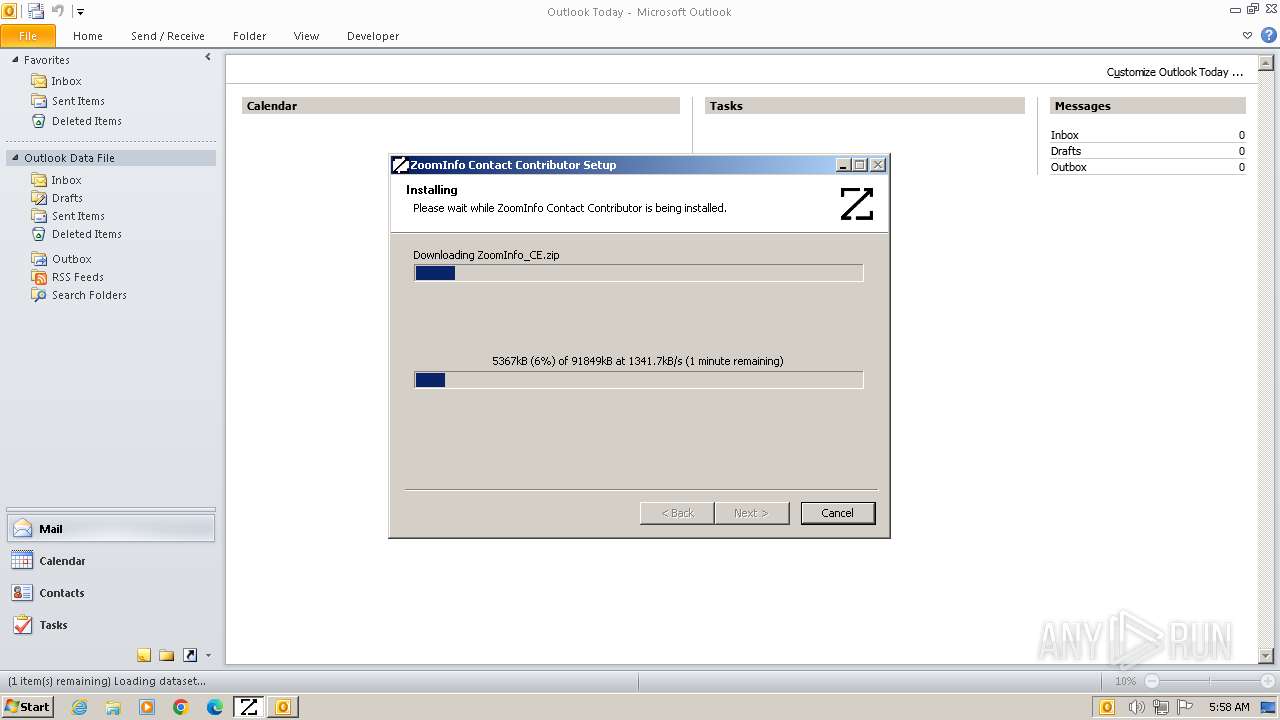
Drops the executable file immediately after the start
- ZoomInfoContactContributor.exe (PID: 3332)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- ZoomInfoContactContributor.exe (PID: 3332)
Reads the Internet Settings
- ZoomInfoContactContributor.exe (PID: 3332)
The process creates files with name similar to system file names
- ZoomInfoContactContributor.exe (PID: 3332)
Executable content was dropped or overwritten
- ZoomInfoContactContributor.exe (PID: 3332)
Contacting a server suspected of hosting an CnC
- ZoomInfoContactContributor.exe (PID: 3332)
Reads security settings of Internet Explorer
- ZoomInfoContactContributor.exe (PID: 3332)
Reads Microsoft Outlook installation path
- ZoomInfoContactContributor.exe (PID: 3332)
INFO
Reads the computer name
- ZoomInfoContactContributor.exe (PID: 3332)
Checks supported languages
- ZoomInfoContactContributor.exe (PID: 3332)
Create files in a temporary directory
- ZoomInfoContactContributor.exe (PID: 3332)
Checks proxy server information
- ZoomInfoContactContributor.exe (PID: 3332)
Reads Microsoft Office registry keys
- ZoomInfoContactContributor.exe (PID: 3332)
Creates files or folders in the user directory
- ZoomInfoContactContributor.exe (PID: 3332)
Reads Internet Explorer settings
- OUTLOOK.EXE (PID: 3272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 22:50:52+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30fa |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.62 |
| ProductVersionNumber: | 2.0.0.62 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | ASCII |
| FileDescription: | - |
| FileVersion: | 62 |
| LegalCopyright: | (c) Zoom Information, Inc. |
| ProductName: | ZoomInfo Contact Contributor |
| ProductVersion: | 62 |
Total processes
41
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3272 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | ZoomInfoContactContributor.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3332 | "C:\Users\admin\AppData\Local\Temp\ZoomInfoContactContributor.exe" | C:\Users\admin\AppData\Local\Temp\ZoomInfoContactContributor.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 62 Modules
| |||||||||||||||
Total events
10 771
Read events
10 610
Write events
121
Delete events
40
Modification events
| (PID) Process: | (3332) ZoomInfoContactContributor.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3332) ZoomInfoContactContributor.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3332) ZoomInfoContactContributor.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3332) ZoomInfoContactContributor.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3272) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3272) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3272) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3272) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3272) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3272) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
Executable files
5
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3272 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR193C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3272 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3332 | ZoomInfoContactContributor.exe | C:\Users\admin\AppData\Local\Temp\fccoordinator.tmp | text | |
MD5:08DD023B1EF1AA8F02F3D0B6CA8FBB38 | SHA256:07503BAFBC8BF1D21CF3DC09271780CF29110C02AC47A7B0C3BF3C8236887F7B | |||
| 3332 | ZoomInfoContactContributor.exe | C:\Users\admin\AppData\Local\Temp\nsaF6C1.tmp\FindProcDLL.dll | executable | |
MD5:83CD62EAB980E3D64C131799608C8371 | SHA256:A6122E80F1C51DC72770B4F56C7C482F7A9571143FBF83B19C4D141D0CB19294 | |||
| 3272 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{ADF15C6F-E8D4-4942-AD3B-D32DD02418E2}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 3332 | ZoomInfoContactContributor.exe | C:\Users\admin\AppData\Local\Temp\nsaF6C1.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 3332 | ZoomInfoContactContributor.exe | C:\Users\admin\AppData\Local\Temp\nsaF6C1.tmp\GetVersion.dll | executable | |
MD5:2E2412281A205ED8D53AAFB3EF770A2D | SHA256:DB09ADB6E17B6A0B31823802431FF5209018EE8C77A193AC8077E42E5F15FB00 | |||
| 3332 | ZoomInfoContactContributor.exe | C:\Users\admin\AppData\Local\Temp\nsaF6C1.tmp\nsDialogs.dll | executable | |
MD5:C10E04DD4AD4277D5ADC951BB331C777 | SHA256:E31AD6C6E82E603378CB6B80E67D0E0DCD9CF384E1199AC5A65CB4935680021A | |||
| 3332 | ZoomInfoContactContributor.exe | C:\Users\admin\AppData\Local\Temp\nsaF6C1.tmp\System.dll | executable | |
MD5:C17103AE9072A06DA581DEC998343FC1 | SHA256:DC58D8AD81CACB0C1ED72E33BFF8F23EA40B5252B5BB55D393A0903E6819AE2F | |||
| 3332 | ZoomInfoContactContributor.exe | C:\Users\admin\AppData\Local\Temp\nsaF6C1.tmp\NSISdl.dll | executable | |
MD5:A5F8399A743AB7F9C88C645C35B1EBB5 | SHA256:DACC88A12D3BA438FDAE3535DC7A5A1D389BCE13ADC993706424874A782E51C9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
14
DNS requests
9
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3332 | ZoomInfoContactContributor.exe | GET | 200 | 142.250.185.83:80 | http://cswapper.freshcontacts.com/client/installopen?client_id={1DEB2779-B34D-475C-A008-0FE6117DE266} | unknown | — | — | whitelisted |
3332 | ZoomInfoContactContributor.exe | GET | 302 | 142.250.185.83:80 | http://cswapper.freshcontacts.com/client/download2?client_version=62&client_id={1DEB2779-B34D-475C-A008-0FE6117DE266}&outlook_bitness=32&reachout=true&appid=3 | unknown | — | — | whitelisted |
— | — | GET | — | 216.58.212.187:80 | http://storage.googleapis.com/coordinator-packages-public/swapper-2258.zip | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 304 | 23.32.238.171:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?11acddbe1ebd82b3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3332 | ZoomInfoContactContributor.exe | 142.250.185.83:80 | cswapper.freshcontacts.com | GOOGLE | US | unknown |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3332 | ZoomInfoContactContributor.exe | 216.58.212.187:80 | storage.googleapis.com | GOOGLE | US | unknown |
3272 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 23.32.238.171:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
cswapper.freshcontacts.com |
| whitelisted |
storage.googleapis.com |
| whitelisted |
config.messenger.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3332 | ZoomInfoContactContributor.exe | Malware Command and Control Activity Detected | ET ADWARE_PUP ZoomInfo Contact Contributor Install |
6 ETPRO signatures available at the full report