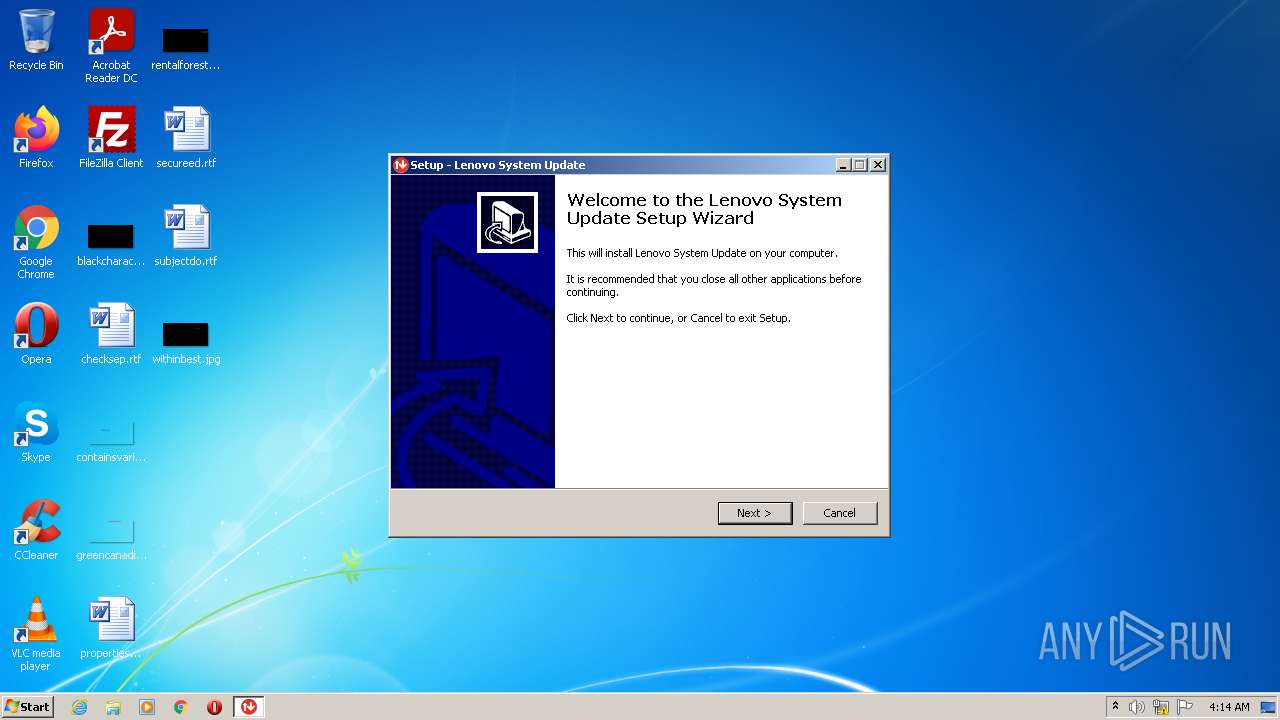
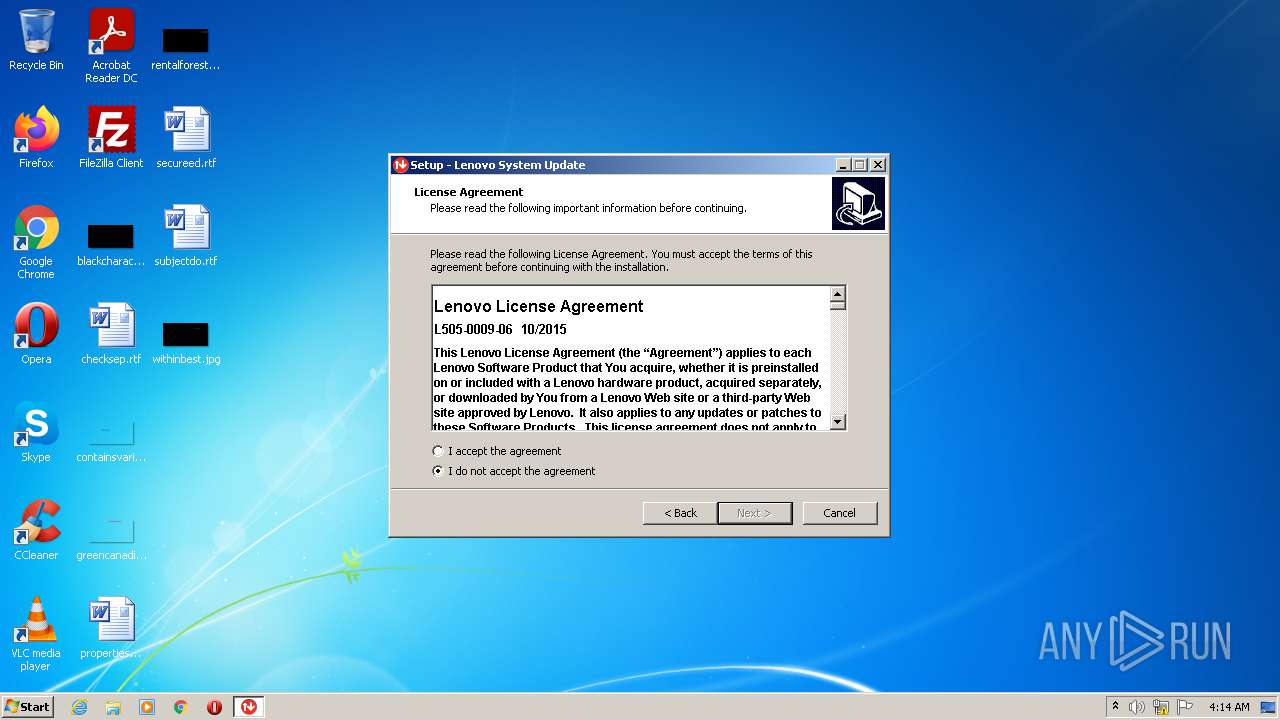
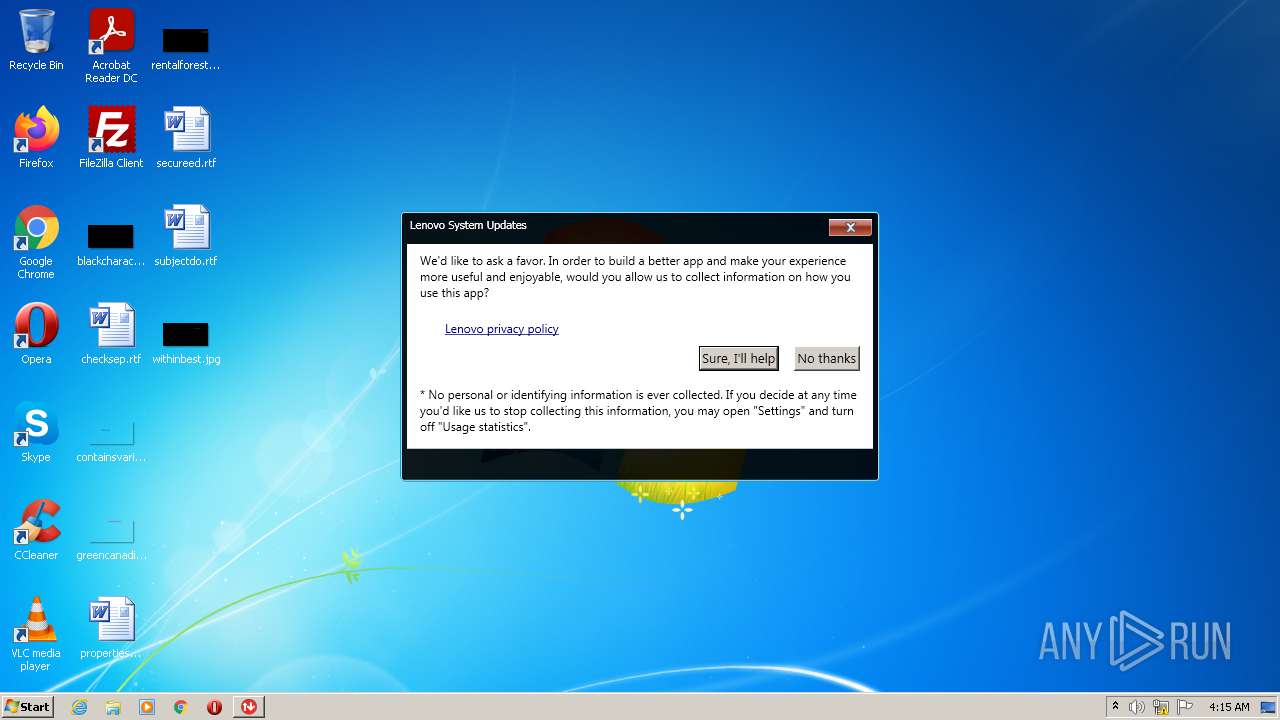
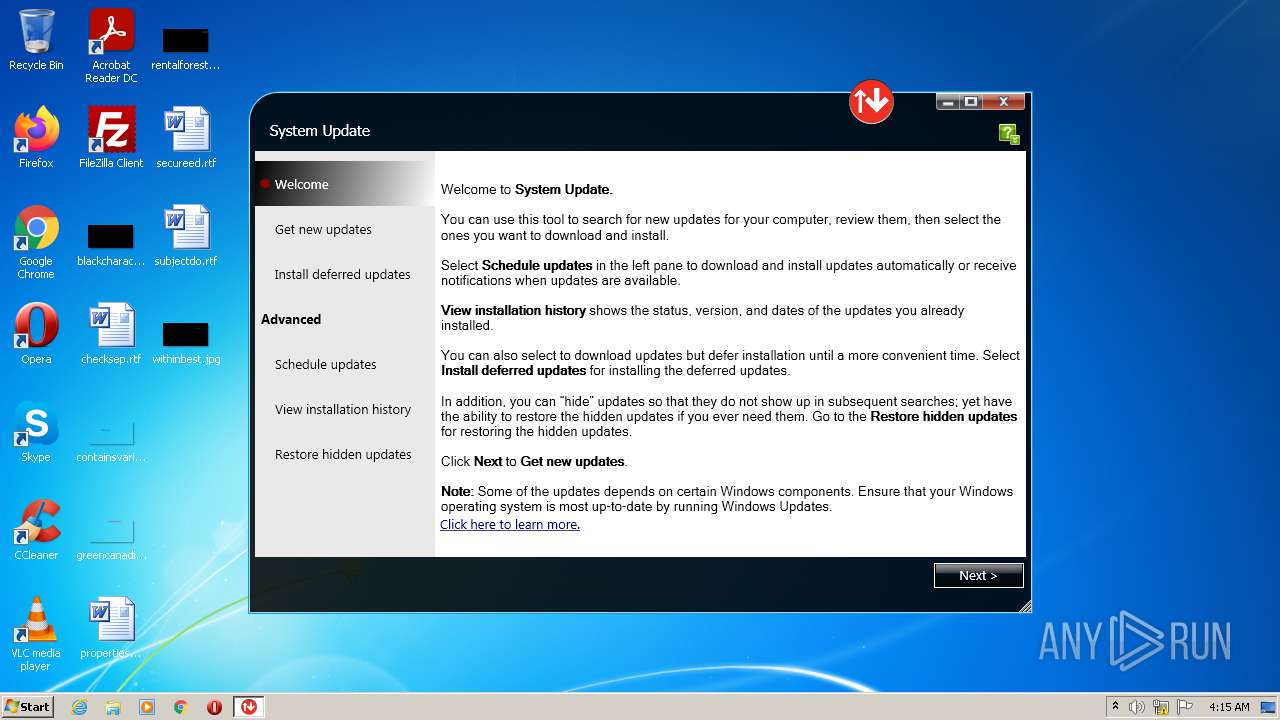
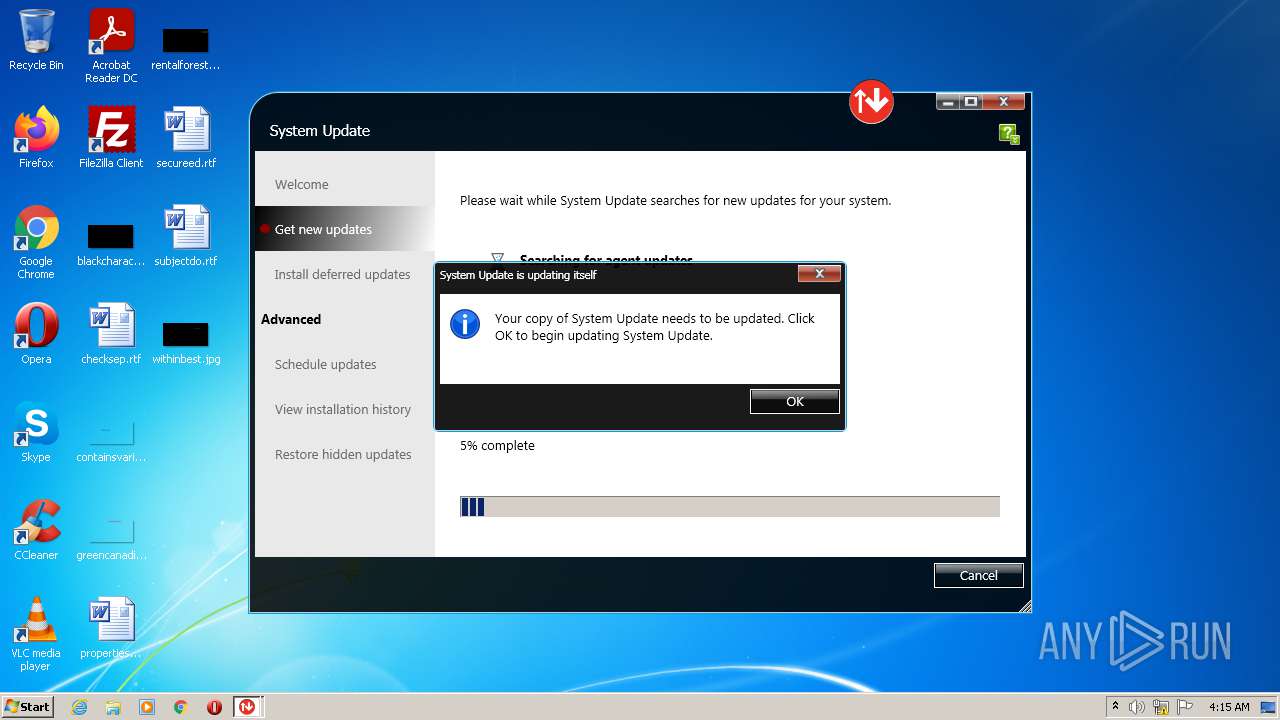
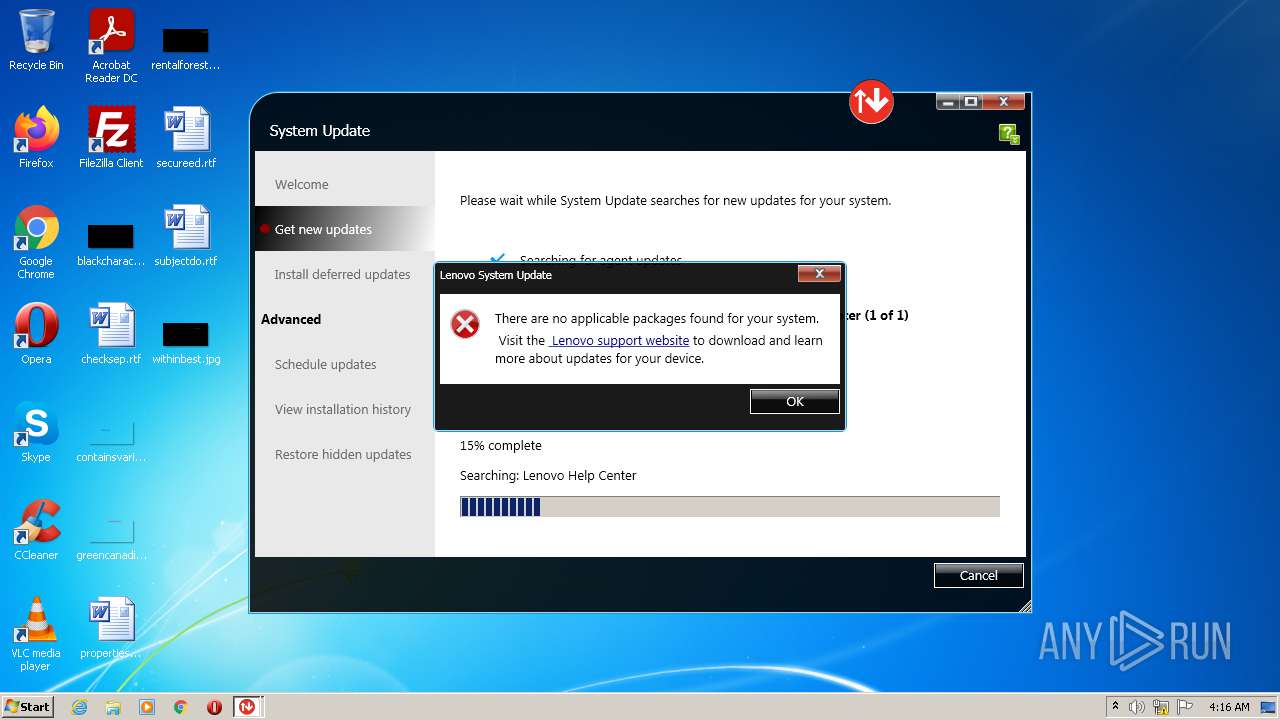
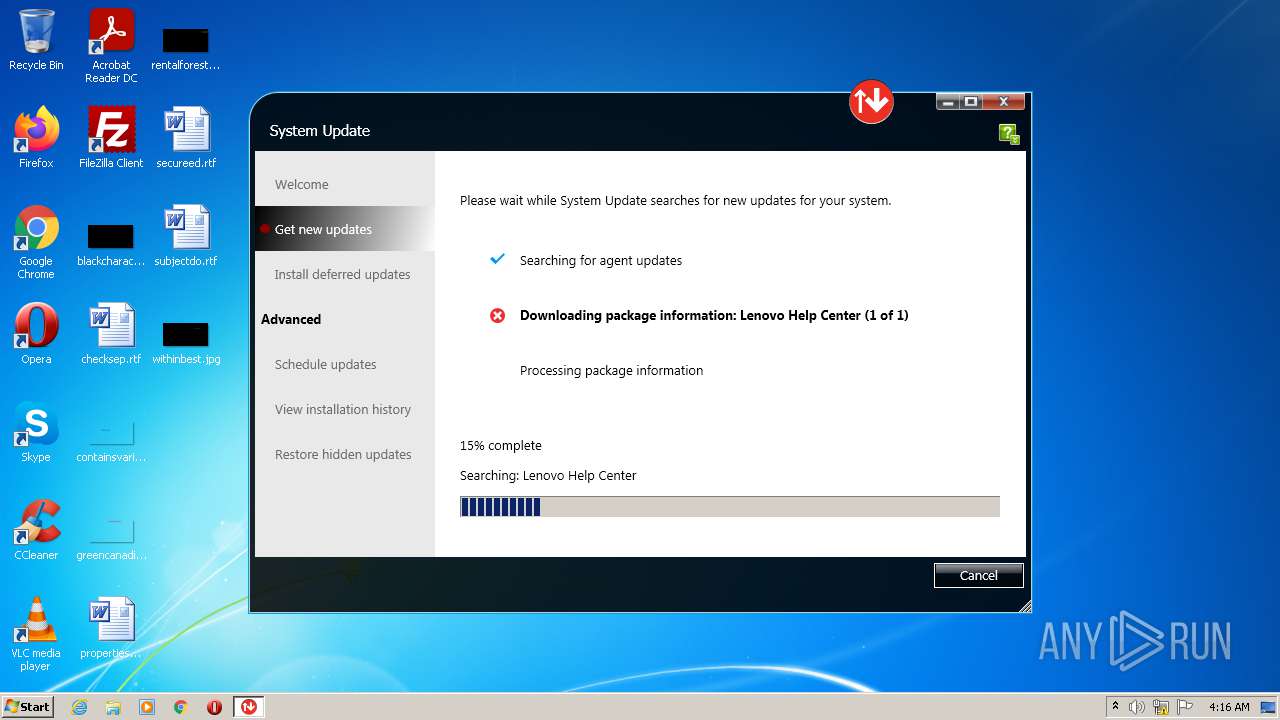
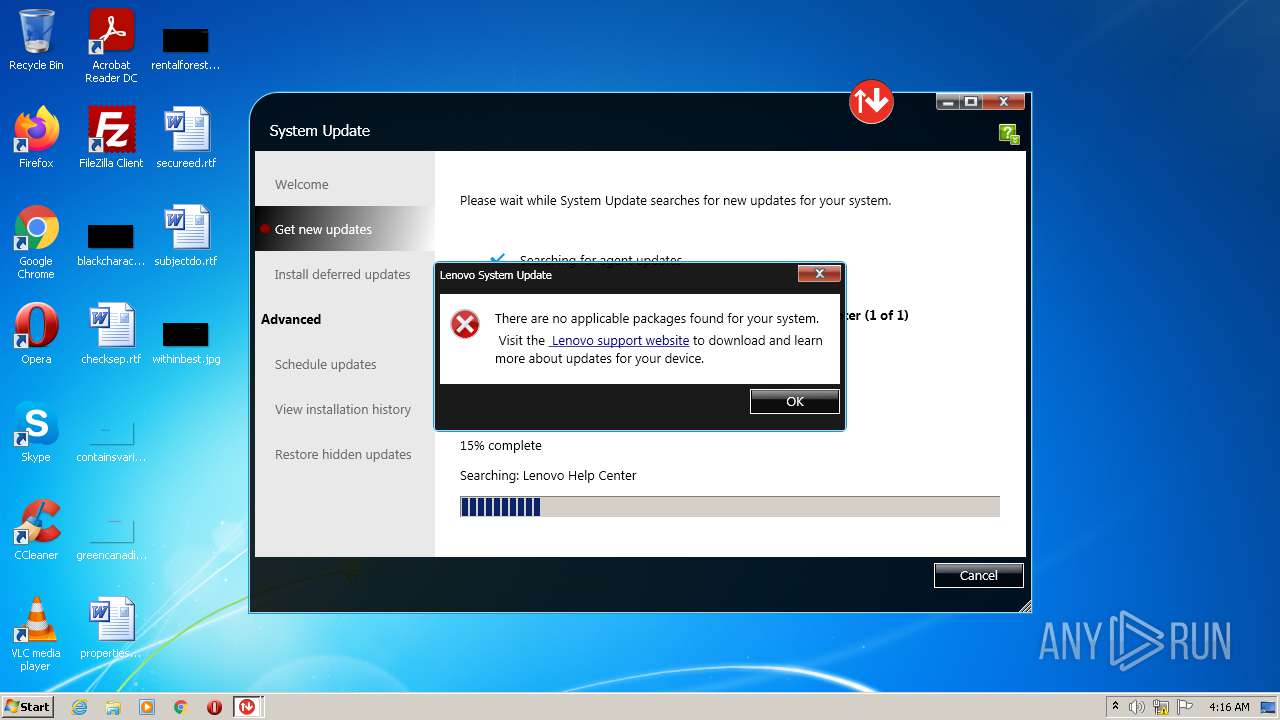
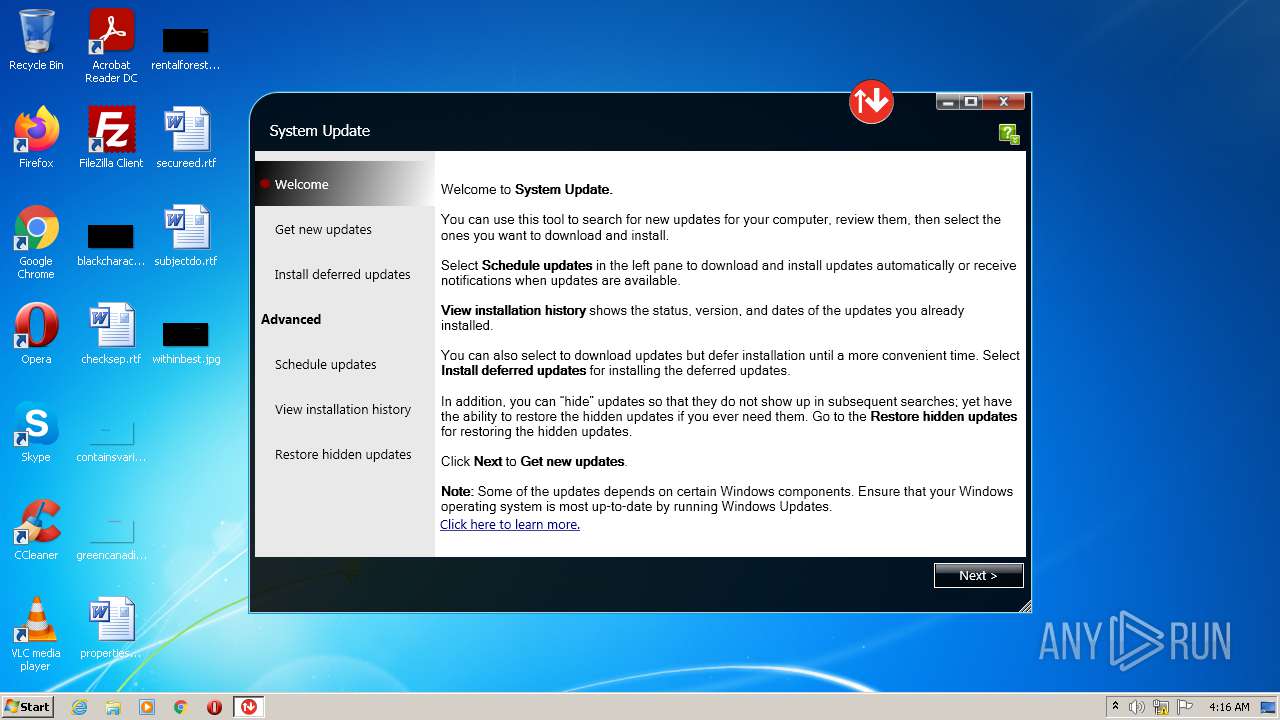
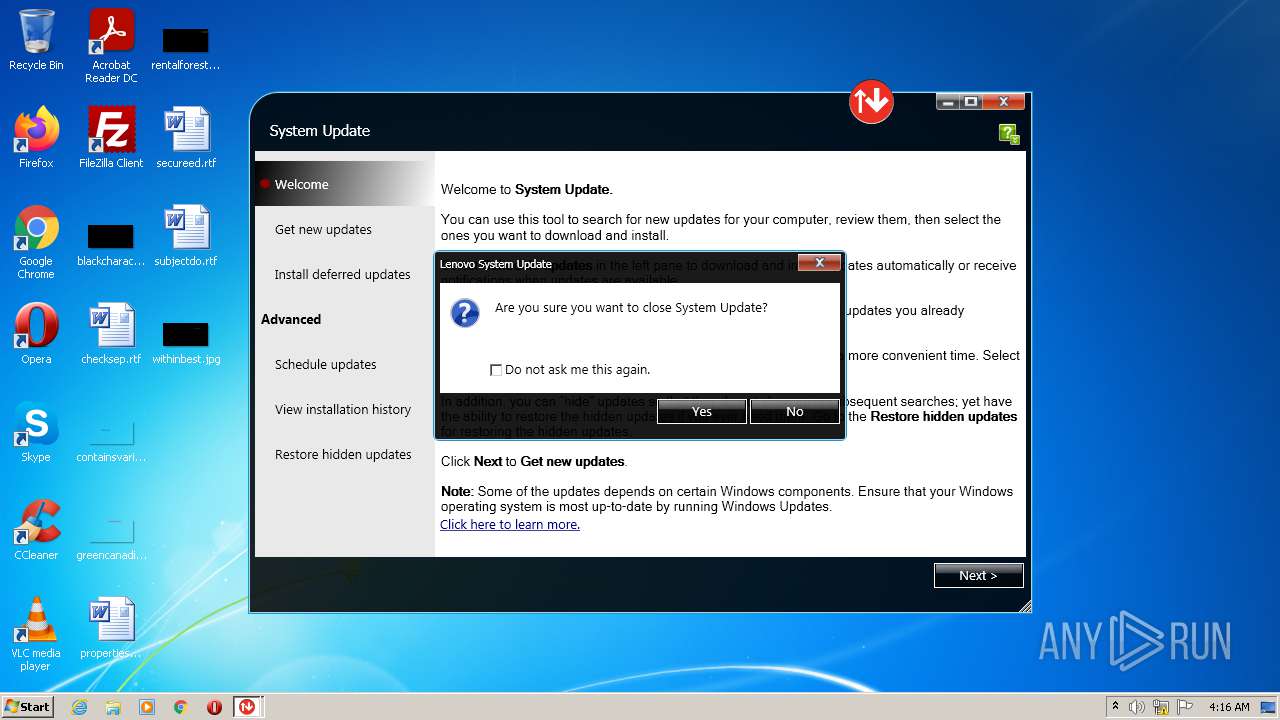
| File name: | system_update_5.07.0124.exe |
| Full analysis: | https://app.any.run/tasks/9caecb47-dbda-4be2-9d99-0cab6d0dcc07 |
| Verdict: | Malicious activity |
| Analysis date: | August 06, 2021, 03:13:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | DA7FCDF44593DA79BA8B238D386FD67F |
| SHA1: | 6379AAF83E5EC2C0D627247A14D6949BCBD25464 |
| SHA256: | 2A8B418FA1F00096CDF5D80AC66A22E8A29AE23C20CDD2D79C9A41B11B7EE533 |
| SSDEEP: | 196608:F0YT2Yi0Ev0C4lLR6pd5OO4rUYVuuByOFeyy:Flir0C4RRkdKrU0l8 |
MALICIOUS
Drops executable file immediately after starts
- system_update_5.07.0124.exe (PID: 3944)
- system_update_5.07.0124.exe (PID: 3300)
- Tvsukernel.exe (PID: 1156)
- systemupdate507-2021-07-13.exe (PID: 3052)
- unins000.exe (PID: 2292)
Application was dropped or rewritten from another process
- system_update_5.07.0124.tmp (PID: 3492)
- SUService.exe (PID: 4064)
- StartSuService.exe (PID: 3728)
- ConfigService.exe (PID: 3268)
- ConfigScheduledTask.exe (PID: 2940)
- susetsched.exe (PID: 3884)
- uncsetting.exe (PID: 2844)
- TVSU2DirAllowWriting.exe (PID: 1096)
- ConfigService.exe (PID: 4012)
- tvsu.exe (PID: 2620)
- TvsuCommandLauncher.exe (PID: 868)
- UACSdk.exe (PID: 2660)
- uncserver.exe (PID: 2892)
- TvsuCommandLauncher.exe (PID: 3540)
- uncsetting.exe (PID: 3128)
- ConfigService.exe (PID: 2284)
- ConfigService.exe (PID: 3280)
- Tvsukernel.exe (PID: 1076)
- susetsched.exe (PID: 3932)
- ConfigScheduledTask.exe (PID: 1268)
- uts.exe (PID: 3116)
- Tvsukernel.exe (PID: 1156)
- uts.exe (PID: 2112)
- systemupdate507-2021-07-13.exe (PID: 3052)
- unins000.exe (PID: 2292)
- _iu14D2N.tmp (PID: 1944)
- ConfigScheduledTask.exe (PID: 3452)
- susetsched.exe (PID: 3728)
- clearsuservice.exe (PID: 3240)
- systemupdate507-2021-07-13.tmp (PID: 2344)
- clearsuservice.exe (PID: 3240)
- uncsetting.exe (PID: 2540)
- StartSuService.exe (PID: 1396)
- SUService.exe (PID: 3680)
- susetsched.exe (PID: 1768)
- uncsetting.exe (PID: 3772)
- ConfigScheduledTask.exe (PID: 3856)
- TVSU2DirAllowWriting.exe (PID: 2688)
- ConfigService.exe (PID: 2652)
- TvsuCommandLauncher.exe (PID: 404)
- UACSdk.exe (PID: 3404)
- UNCServer.exe (PID: 2256)
- Tvsukernel.exe (PID: 2080)
- susetsched.exe (PID: 2296)
- ConfigScheduledTask.exe (PID: 1508)
- ia.exe (PID: 1588)
- ConfigService.exe (PID: 492)
- ConfigService.exe (PID: 2136)
- ia.exe (PID: 1212)
- ConfigService.exe (PID: 2028)
Loads dropped or rewritten executable
- SUService.exe (PID: 4064)
- InstallUtil.exe (PID: 3444)
- ConfigScheduledTask.exe (PID: 2940)
- TvsuCommandLauncher.exe (PID: 868)
- TvsuCommandLauncher.exe (PID: 3540)
- uncserver.exe (PID: 2892)
- Tvsukernel.exe (PID: 1076)
- ConfigScheduledTask.exe (PID: 1268)
- Tvsukernel.exe (PID: 1156)
- UACSdk.exe (PID: 2660)
- uts.exe (PID: 2112)
- ConfigScheduledTask.exe (PID: 3452)
- InstallUtil.exe (PID: 1116)
- InstallUtil.exe (PID: 3924)
- ConfigScheduledTask.exe (PID: 3856)
- SUService.exe (PID: 3680)
- TvsuCommandLauncher.exe (PID: 404)
- UNCServer.exe (PID: 2256)
- Tvsukernel.exe (PID: 2080)
- ConfigScheduledTask.exe (PID: 1508)
- ia.exe (PID: 1588)
- ia.exe (PID: 1212)
- UACSdk.exe (PID: 3404)
Loads the Task Scheduler COM API
- susetsched.exe (PID: 3884)
- schtasks.exe (PID: 3184)
- schtasks.exe (PID: 2864)
- schtasks.exe (PID: 2564)
- schtasks.exe (PID: 3844)
- schtasks.exe (PID: 3756)
- schtasks.exe (PID: 1524)
- schtasks.exe (PID: 3440)
- susetsched.exe (PID: 1768)
- schtasks.exe (PID: 3436)
- schtasks.exe (PID: 1580)
- schtasks.exe (PID: 2944)
Uses Task Scheduler to run other applications
- ConfigScheduledTask.exe (PID: 2940)
- ConfigScheduledTask.exe (PID: 1268)
- ConfigScheduledTask.exe (PID: 3452)
- ConfigScheduledTask.exe (PID: 3856)
- ConfigScheduledTask.exe (PID: 1508)
Changes settings of System certificates
- certutil.exe (PID: 3724)
- certutil.exe (PID: 1588)
- SUService.exe (PID: 4064)
Starts NET.EXE for service management
- cmd.exe (PID: 2872)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 1080)
SUSPICIOUS
Checks supported languages
- system_update_5.07.0124.tmp (PID: 2956)
- system_update_5.07.0124.exe (PID: 3944)
- system_update_5.07.0124.exe (PID: 3300)
- system_update_5.07.0124.tmp (PID: 3492)
- cmd.exe (PID: 2152)
- cmd.exe (PID: 3992)
- InstallUtil.exe (PID: 3444)
- StartSuService.exe (PID: 3728)
- SUService.exe (PID: 4064)
- ConfigScheduledTask.exe (PID: 2940)
- uncsetting.exe (PID: 2844)
- susetsched.exe (PID: 3884)
- ConfigService.exe (PID: 3268)
- TVSU2DirAllowWriting.exe (PID: 1096)
- ConfigService.exe (PID: 4012)
- cmd.exe (PID: 2564)
- tvsu.exe (PID: 2620)
- TvsuCommandLauncher.exe (PID: 868)
- uncserver.exe (PID: 2892)
- TvsuCommandLauncher.exe (PID: 3540)
- UACSdk.exe (PID: 2660)
- uncsetting.exe (PID: 3128)
- ConfigService.exe (PID: 2284)
- Tvsukernel.exe (PID: 1076)
- ConfigService.exe (PID: 3280)
- ConfigScheduledTask.exe (PID: 1268)
- susetsched.exe (PID: 3932)
- Tvsukernel.exe (PID: 1156)
- uts.exe (PID: 3116)
- uts.exe (PID: 2112)
- systemupdate507-2021-07-13.exe (PID: 3052)
- systemupdate507-2021-07-13.tmp (PID: 2344)
- cmd.exe (PID: 3996)
- unins000.exe (PID: 2292)
- _iu14D2N.tmp (PID: 1944)
- ConfigScheduledTask.exe (PID: 3452)
- susetsched.exe (PID: 3728)
- cmd.exe (PID: 2872)
- InstallUtil.exe (PID: 1116)
- clearsuservice.exe (PID: 3240)
- cmd.exe (PID: 1064)
- cmd.exe (PID: 3548)
- cmd.exe (PID: 3492)
- cmd.exe (PID: 1120)
- cmd.exe (PID: 2380)
- cmd.exe (PID: 2168)
- cmd.exe (PID: 3184)
- cmd.exe (PID: 3092)
- clearsuservice.exe (PID: 3240)
- cmd.exe (PID: 3128)
- uncsetting.exe (PID: 2540)
- cmd.exe (PID: 2072)
- cmd.exe (PID: 1080)
- cmd.exe (PID: 2168)
- cmd.exe (PID: 924)
- cmd.exe (PID: 1844)
- cmd.exe (PID: 976)
- InstallUtil.exe (PID: 3924)
- StartSuService.exe (PID: 1396)
- SUService.exe (PID: 3680)
- susetsched.exe (PID: 1768)
- uncsetting.exe (PID: 3772)
- ConfigScheduledTask.exe (PID: 3856)
- ConfigService.exe (PID: 2652)
- TVSU2DirAllowWriting.exe (PID: 2688)
- cmd.exe (PID: 3272)
- TvsuCommandLauncher.exe (PID: 404)
- UACSdk.exe (PID: 3404)
- Tvsukernel.exe (PID: 2080)
- UNCServer.exe (PID: 2256)
- ConfigService.exe (PID: 492)
- ConfigService.exe (PID: 2136)
- susetsched.exe (PID: 2296)
- ConfigScheduledTask.exe (PID: 1508)
- ia.exe (PID: 1588)
- ia.exe (PID: 1212)
- ConfigService.exe (PID: 2028)
Reads the computer name
- system_update_5.07.0124.tmp (PID: 2956)
- system_update_5.07.0124.tmp (PID: 3492)
- InstallUtil.exe (PID: 3444)
- StartSuService.exe (PID: 3728)
- SUService.exe (PID: 4064)
- uncsetting.exe (PID: 2844)
- ConfigScheduledTask.exe (PID: 2940)
- susetsched.exe (PID: 3884)
- ConfigService.exe (PID: 3268)
- TvsuCommandLauncher.exe (PID: 868)
- tvsu.exe (PID: 2620)
- uncsetting.exe (PID: 3128)
- TvsuCommandLauncher.exe (PID: 3540)
- uncserver.exe (PID: 2892)
- UACSdk.exe (PID: 2660)
- Tvsukernel.exe (PID: 1076)
- ConfigScheduledTask.exe (PID: 1268)
- ConfigService.exe (PID: 3280)
- Tvsukernel.exe (PID: 1156)
- uts.exe (PID: 3116)
- uts.exe (PID: 2112)
- systemupdate507-2021-07-13.tmp (PID: 2344)
- unins000.exe (PID: 2292)
- _iu14D2N.tmp (PID: 1944)
- ConfigScheduledTask.exe (PID: 3452)
- InstallUtil.exe (PID: 1116)
- uncsetting.exe (PID: 2540)
- StartSuService.exe (PID: 1396)
- SUService.exe (PID: 3680)
- InstallUtil.exe (PID: 3924)
- susetsched.exe (PID: 1768)
- uncsetting.exe (PID: 3772)
- ConfigScheduledTask.exe (PID: 3856)
- ConfigService.exe (PID: 2652)
- TvsuCommandLauncher.exe (PID: 404)
- UACSdk.exe (PID: 3404)
- Tvsukernel.exe (PID: 2080)
- UNCServer.exe (PID: 2256)
- ConfigService.exe (PID: 2136)
- ConfigScheduledTask.exe (PID: 1508)
- ia.exe (PID: 1212)
- ia.exe (PID: 1588)
Creates files in the Windows directory
- system_update_5.07.0124.exe (PID: 3300)
- system_update_5.07.0124.tmp (PID: 3492)
- InstallUtil.exe (PID: 3444)
- certutil.exe (PID: 3724)
- certutil.exe (PID: 1588)
- SUService.exe (PID: 4064)
- uts.exe (PID: 2112)
- systemupdate507-2021-07-13.tmp (PID: 2344)
- systemupdate507-2021-07-13.exe (PID: 3052)
- regedit.exe (PID: 2900)
- cmd.exe (PID: 3996)
- unins000.exe (PID: 2292)
- _iu14D2N.tmp (PID: 1944)
- InstallUtil.exe (PID: 1116)
- cmd.exe (PID: 3548)
- certutil.exe (PID: 4024)
- certutil.exe (PID: 3148)
- SUService.exe (PID: 3680)
Executable content was dropped or overwritten
- system_update_5.07.0124.exe (PID: 3944)
- system_update_5.07.0124.exe (PID: 3300)
- system_update_5.07.0124.tmp (PID: 3492)
- Tvsukernel.exe (PID: 1076)
- Tvsukernel.exe (PID: 1156)
- uts.exe (PID: 3116)
- uts.exe (PID: 2112)
- systemupdate507-2021-07-13.exe (PID: 3052)
- unins000.exe (PID: 2292)
- systemupdate507-2021-07-13.tmp (PID: 2344)
Starts application with an unusual extension
- system_update_5.07.0124.exe (PID: 3300)
- systemupdate507-2021-07-13.exe (PID: 3052)
- unins000.exe (PID: 2292)
Reads Windows owner or organization settings
- system_update_5.07.0124.tmp (PID: 3492)
- systemupdate507-2021-07-13.tmp (PID: 2344)
- _iu14D2N.tmp (PID: 1944)
Reads the Windows organization settings
- system_update_5.07.0124.tmp (PID: 3492)
- systemupdate507-2021-07-13.tmp (PID: 2344)
- _iu14D2N.tmp (PID: 1944)
Removes files from Windows directory
- system_update_5.07.0124.tmp (PID: 3492)
- certutil.exe (PID: 3724)
- certutil.exe (PID: 1588)
- system_update_5.07.0124.exe (PID: 3300)
- SUService.exe (PID: 4064)
- uts.exe (PID: 2112)
- systemupdate507-2021-07-13.exe (PID: 3052)
- systemupdate507-2021-07-13.tmp (PID: 2344)
- _iu14D2N.tmp (PID: 1944)
- cmd.exe (PID: 1080)
- cmd.exe (PID: 976)
- certutil.exe (PID: 3148)
- certutil.exe (PID: 4024)
- SUService.exe (PID: 3680)
Reads Environment values
- system_update_5.07.0124.tmp (PID: 3492)
- netsh.exe (PID: 3612)
- netsh.exe (PID: 2028)
- Tvsukernel.exe (PID: 1076)
- Tvsukernel.exe (PID: 1156)
- uts.exe (PID: 3116)
- uts.exe (PID: 2112)
- netsh.exe (PID: 3804)
- netsh.exe (PID: 2092)
- netsh.exe (PID: 3116)
- netsh.exe (PID: 1104)
- systemupdate507-2021-07-13.tmp (PID: 2344)
- netsh.exe (PID: 1764)
- netsh.exe (PID: 3580)
- netsh.exe (PID: 856)
- netsh.exe (PID: 3248)
- netsh.exe (PID: 3820)
- netsh.exe (PID: 3780)
- Tvsukernel.exe (PID: 2080)
- ia.exe (PID: 1212)
Starts CMD.EXE for commands execution
- system_update_5.07.0124.tmp (PID: 3492)
- cmd.exe (PID: 2152)
- systemupdate507-2021-07-13.tmp (PID: 2344)
- _iu14D2N.tmp (PID: 1944)
- cmd.exe (PID: 2168)
Application launched itself
- cmd.exe (PID: 2152)
- Tvsukernel.exe (PID: 1076)
- cmd.exe (PID: 2168)
Creates a directory in Program Files
- system_update_5.07.0124.tmp (PID: 3492)
- systemupdate507-2021-07-13.tmp (PID: 2344)
Drops a file with too old compile date
- system_update_5.07.0124.tmp (PID: 3492)
- Tvsukernel.exe (PID: 1076)
- uts.exe (PID: 3116)
- systemupdate507-2021-07-13.tmp (PID: 2344)
Changes default file association
- system_update_5.07.0124.tmp (PID: 3492)
- systemupdate507-2021-07-13.tmp (PID: 2344)
Creates a software uninstall entry
- system_update_5.07.0124.tmp (PID: 3492)
- systemupdate507-2021-07-13.tmp (PID: 2344)
Creates files in the program directory
- InstallUtil.exe (PID: 3444)
- StartSuService.exe (PID: 3728)
- system_update_5.07.0124.tmp (PID: 3492)
- ConfigScheduledTask.exe (PID: 2940)
- SUService.exe (PID: 4064)
- Tvsukernel.exe (PID: 1076)
- Tvsukernel.exe (PID: 1156)
- uts.exe (PID: 3116)
- uts.exe (PID: 2112)
- InstallUtil.exe (PID: 3924)
- StartSuService.exe (PID: 1396)
- ConfigScheduledTask.exe (PID: 3856)
- systemupdate507-2021-07-13.tmp (PID: 2344)
- TvsuCommandLauncher.exe (PID: 404)
- SUService.exe (PID: 3680)
- Tvsukernel.exe (PID: 2080)
- ia.exe (PID: 1212)
- ia.exe (PID: 1588)
Executed as Windows Service
- SUService.exe (PID: 4064)
- msiexec.exe (PID: 2544)
- SUService.exe (PID: 3680)
Uses ICACLS.EXE to modify access control list
- SUService.exe (PID: 4064)
- Tvsukernel.exe (PID: 1076)
- uts.exe (PID: 3116)
Creates or modifies windows services
- InstallUtil.exe (PID: 3444)
- InstallUtil.exe (PID: 3924)
Drops a file that was compiled in debug mode
- system_update_5.07.0124.tmp (PID: 3492)
- Tvsukernel.exe (PID: 1076)
- uts.exe (PID: 3116)
- systemupdate507-2021-07-13.tmp (PID: 2344)
Uses NETSH.EXE for network configuration
- uncsetting.exe (PID: 2844)
- uncsetting.exe (PID: 2540)
- uncsetting.exe (PID: 3772)
- uts.exe (PID: 2112)
Adds / modifies Windows certificates
- SUService.exe (PID: 4064)
Drops a file with a compile date too recent
- Tvsukernel.exe (PID: 1076)
- Tvsukernel.exe (PID: 1156)
- uts.exe (PID: 3116)
- systemupdate507-2021-07-13.tmp (PID: 2344)
Starts itself from another location
- uts.exe (PID: 3116)
- unins000.exe (PID: 2292)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1064)
Reads the date of Windows installation
- _iu14D2N.tmp (PID: 1944)
Searches for installed software
- ia.exe (PID: 1212)
INFO
Application was dropped or rewritten from another process
- system_update_5.07.0124.tmp (PID: 2956)
Checks supported languages
- findstr.exe (PID: 2040)
- icacls.exe (PID: 1820)
- schtasks.exe (PID: 3184)
- netsh.exe (PID: 3612)
- certutil.exe (PID: 3724)
- certutil.exe (PID: 1588)
- netsh.exe (PID: 2028)
- schtasks.exe (PID: 2864)
- icacls.exe (PID: 3116)
- icacls.exe (PID: 4004)
- icacls.exe (PID: 3696)
- icacls.exe (PID: 696)
- icacls.exe (PID: 3192)
- WISPTIS.EXE (PID: 1472)
- schtasks.exe (PID: 2564)
- icacls.exe (PID: 3528)
- regedit.exe (PID: 2900)
- regedit.exe (PID: 3432)
- msiexec.exe (PID: 3248)
- msiexec.exe (PID: 2544)
- net.exe (PID: 348)
- schtasks.exe (PID: 3844)
- net1.exe (PID: 3136)
- schtasks.exe (PID: 3756)
- schtasks.exe (PID: 3440)
- schtasks.exe (PID: 1524)
- taskkill.exe (PID: 2552)
- netsh.exe (PID: 2092)
- netsh.exe (PID: 3116)
- PING.EXE (PID: 2108)
- netsh.exe (PID: 3804)
- netsh.exe (PID: 1104)
- findstr.exe (PID: 3276)
- regedit.exe (PID: 3868)
- regedit.exe (PID: 3252)
- netsh.exe (PID: 856)
- schtasks.exe (PID: 3436)
- schtasks.exe (PID: 1580)
- netsh.exe (PID: 1764)
- certutil.exe (PID: 4024)
- certutil.exe (PID: 3148)
- netsh.exe (PID: 3580)
- netsh.exe (PID: 3820)
- netsh.exe (PID: 3780)
- netsh.exe (PID: 3248)
- schtasks.exe (PID: 2944)
- WISPTIS.EXE (PID: 2324)
Dropped object may contain Bitcoin addresses
- system_update_5.07.0124.tmp (PID: 3492)
- ia.exe (PID: 1212)
- systemupdate507-2021-07-13.tmp (PID: 2344)
Reads the computer name
- icacls.exe (PID: 1820)
- schtasks.exe (PID: 3184)
- certutil.exe (PID: 3724)
- netsh.exe (PID: 3612)
- schtasks.exe (PID: 2864)
- netsh.exe (PID: 2028)
- certutil.exe (PID: 1588)
- icacls.exe (PID: 3116)
- icacls.exe (PID: 4004)
- icacls.exe (PID: 3696)
- icacls.exe (PID: 3192)
- schtasks.exe (PID: 2564)
- WISPTIS.EXE (PID: 1472)
- icacls.exe (PID: 3528)
- msiexec.exe (PID: 3248)
- msiexec.exe (PID: 2544)
- schtasks.exe (PID: 3844)
- net1.exe (PID: 3136)
- schtasks.exe (PID: 3440)
- schtasks.exe (PID: 1524)
- schtasks.exe (PID: 3756)
- taskkill.exe (PID: 2552)
- netsh.exe (PID: 1104)
- netsh.exe (PID: 2092)
- netsh.exe (PID: 3116)
- netsh.exe (PID: 3804)
- PING.EXE (PID: 2108)
- schtasks.exe (PID: 1580)
- netsh.exe (PID: 1764)
- schtasks.exe (PID: 3436)
- certutil.exe (PID: 4024)
- certutil.exe (PID: 3148)
- netsh.exe (PID: 856)
- netsh.exe (PID: 3248)
- netsh.exe (PID: 3780)
- netsh.exe (PID: 3580)
- netsh.exe (PID: 3820)
- schtasks.exe (PID: 2944)
- WISPTIS.EXE (PID: 2324)
Reads settings of System Certificates
- certutil.exe (PID: 3724)
- certutil.exe (PID: 1588)
- SUService.exe (PID: 4064)
- Tvsukernel.exe (PID: 1076)
- Tvsukernel.exe (PID: 1156)
- uts.exe (PID: 2112)
- certutil.exe (PID: 4024)
- certutil.exe (PID: 3148)
- SUService.exe (PID: 3680)
- Tvsukernel.exe (PID: 2080)
- ia.exe (PID: 1212)
Manual execution by user
- tvsu.exe (PID: 2620)
Checks Windows Trust Settings
- SUService.exe (PID: 4064)
- Tvsukernel.exe (PID: 1076)
- Tvsukernel.exe (PID: 1156)
- uts.exe (PID: 2112)
- SUService.exe (PID: 3680)
- Tvsukernel.exe (PID: 2080)
- ia.exe (PID: 1212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (79.7) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (8.6) |
| .exe | | | Win16/32 Executable Delphi generic (3.9) |
| .exe | | | Generic Win/DOS Executable (3.8) |
| .exe | | | DOS Executable Generic (3.8) |
EXIF
EXE
| ProductVersion: | 5.07.0124 |
|---|---|
| ProductName: | Lenovo System Update |
| LegalCopyright: | |
| FileVersion: | 5.07.0124 |
| FileDescription: | Lenovo System Update Setup |
| CompanyName: | Lenovo |
| Comments: | This installation was built with Inno Setup. |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 5.7.124.0 |
| FileVersionNumber: | 5.7.124.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5 |
| ImageVersion: | 6 |
| OSVersion: | 5 |
| EntryPoint: | 0x25be0 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 257536 |
| CodeSize: | 151552 |
| LinkerVersion: | 2.25 |
| PEType: | PE32 |
| TimeStamp: | 2020:01:06 07:31:46+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 06-Jan-2020 06:31:46 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Lenovo |
| FileDescription: | Lenovo System Update Setup |
| FileVersion: | 5.07.0124 |
| LegalCopyright: | - |
| ProductName: | Lenovo System Update |
| ProductVersion: | 5.07.0124 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 10 |
| Time date stamp: | 06-Jan-2020 06:31:46 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00023AA0 | 0x00023C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.32291 |
.itext | 0x00025000 | 0x00001368 | 0x00001400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.91348 |
.data | 0x00027000 | 0x00001628 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.32921 |
.bss | 0x00029000 | 0x00006158 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00030000 | 0x00000648 | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.08948 |
.didata | 0x00031000 | 0x00000E3E | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.2563 |
.edata | 0x00032000 | 0x00000071 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.3265 |
.tls | 0x00033000 | 0x00000014 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x00034000 | 0x0000005D | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.37999 |
.rsrc | 0x00035000 | 0x0003B9EC | 0x0003BA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.02781 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.18481 | 2676 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 3.30618 | 304 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 2.47581 | 176 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 7.73695 | 4201 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 2.79096 | 1640 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 3.20638 | 744 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 3.31916 | 488 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 3.25564 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 7.93819 | 11287 | Latin 1 / Western European | English - United States | RT_ICON |
10 | 4.47867 | 3752 | Latin 1 / Western European | English - United States | RT_ICON |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
kernel32.dll (delay-loaded) |
oleaut32.dll |
user32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 0x0002C58C |
__dbk_fcall_wrapper | 2 | 0x0000B294 |
Total processes
228
Monitored processes
126
Malicious processes
33
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 348 | net.exe stop SUService" | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 404 | "C:\Program Files\Lenovo\System Update\TvsuCommandLauncher.exe" 9 | C:\Program Files\Lenovo\System Update\TvsuCommandLauncher.exe | — | uts.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Lenovo System Update TvsuCommandLauncher Exit code: 2147483648 Version: 5.7.0.127 Modules
| |||||||||||||||
| 492 | "C:\Program Files\Lenovo\System Update\ConfigService.exe" stop | C:\Program Files\Lenovo\System Update\ConfigService.exe | — | Tvsukernel.exe | |||||||||||
User: admin Integrity Level: HIGH Description: ConfigService Application Exit code: 0 Version: 5, 7, 0, 127 Modules
| |||||||||||||||
| 696 | "C:\Windows\system32\icacls.exe" "c:\windows\TempInst" /reset /T /C /L /Q | C:\Windows\system32\icacls.exe | — | Tvsukernel.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 856 | "C:\Windows\system32\netsh.exe" advfirewall firewall add rule name="TvsuUNCServer" dir=out action=allow program="C:\Program Files\Lenovo\System Update\uncserver.exe" enable=yes profile=any protocol=UDP | C:\Windows\system32\netsh.exe | — | uncsetting.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 868 | "C:\Program Files\Lenovo\System Update\TvsuCommandLauncher.exe" 6 | C:\Program Files\Lenovo\System Update\TvsuCommandLauncher.exe | — | tvsu.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Lenovo System Update TvsuCommandLauncher Exit code: 2147483648 Version: 5.7.0.124 Modules
| |||||||||||||||
| 924 | "C:\Windows\system32\cmd.exe" /C ""C:\Windows\delsu.cmd"" | C:\Windows\system32\cmd.exe | — | _iu14D2N.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 976 | "C:\Windows\system32\cmd.exe" /c del /q "%windir%\upgradesu.tag" | C:\Windows\system32\cmd.exe | — | systemupdate507-2021-07-13.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1064 | "C:\Windows\system32\cmd.exe" /c taskkill /f /im "UNCServer.exe" | C:\Windows\system32\cmd.exe | — | _iu14D2N.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1076 | "C:\Program Files\Lenovo\System Update\\Tvsukernel.exe" | C:\Program Files\Lenovo\System Update\Tvsukernel.exe | UACSdk.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Lenovo System Update Exit code: 0 Version: 5.7.0.124 Modules
| |||||||||||||||
Total events
73 522
Read events
72 029
Write events
1 427
Delete events
66
Modification events
| (PID) Process: | (3492) system_update_5.07.0124.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: A40D0000A6A13E1D718AD701 | |||
| (PID) Process: | (3492) system_update_5.07.0124.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 65B0C6B31DB8183CBF237D6CE5E1859C40BB0016F594097DF68932852C1E5A0C | |||
| (PID) Process: | (3492) system_update_5.07.0124.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3492) system_update_5.07.0124.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: A55D91E8BD30370543F65C8210DA5D7F1D363737F12CC5597B111CDA4B2C2ECF | |||
| (PID) Process: | (3492) system_update_5.07.0124.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\tvsu.exe |
| Operation: | write | Name: | (default) |
Value: C:\Program Files\Lenovo\System Update\tvsu.exe | |||
| (PID) Process: | (3492) system_update_5.07.0124.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\tvsu.exe |
| Operation: | write | Name: | Path |
Value: C:\Program Files\Lenovo\System Update\ | |||
| (PID) Process: | (3492) system_update_5.07.0124.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\tvsu_install.exe |
| Operation: | write | Name: | (default) |
Value: C:\swtools\readyapps\appinstall.exe -tvsu | |||
| (PID) Process: | (3492) system_update_5.07.0124.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\tvsu_install.exe |
| Operation: | write | Name: | Path |
Value: C:\swtools\readyapps\tvsu | |||
| (PID) Process: | (3492) system_update_5.07.0124.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\tvsu_install.exe |
| Operation: | write | Name: | Version |
Value: 5.07 | |||
| (PID) Process: | (3492) system_update_5.07.0124.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\tvsu_install.exe |
| Operation: | write | Name: | W7_CmdInst |
Value: setuptvsu.exe | |||
Executable files
481
Suspicious files
2
Text files
837
Unknown types
76
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3944 | system_update_5.07.0124.exe | C:\Users\admin\AppData\Local\Temp\is-PHBP3.tmp\system_update_5.07.0124.tmp | executable | |
MD5:— | SHA256:— | |||
| 3300 | system_update_5.07.0124.exe | C:\Windows\TempInst\is-FTGH6.tmp\system_update_5.07.0124.tmp | executable | |
MD5:— | SHA256:— | |||
| 3492 | system_update_5.07.0124.tmp | C:\Program Files\Lenovo\System Update\is-86GAQ.tmp | xml | |
MD5:— | SHA256:— | |||
| 3492 | system_update_5.07.0124.tmp | C:\Program Files\Lenovo\System Update\is-5CHSE.tmp | executable | |
MD5:— | SHA256:— | |||
| 3492 | system_update_5.07.0124.tmp | C:\Program Files\Lenovo\System Update\is-S488L.tmp | executable | |
MD5:— | SHA256:— | |||
| 3492 | system_update_5.07.0124.tmp | C:\Program Files\Lenovo\System Update\unins000.exe | executable | |
MD5:— | SHA256:— | |||
| 3492 | system_update_5.07.0124.tmp | C:\Program Files\Lenovo\System Update\ApsChk64.exe | executable | |
MD5:— | SHA256:— | |||
| 3492 | system_update_5.07.0124.tmp | C:\Program Files\Lenovo\System Update\ApsChk86.exe | executable | |
MD5:— | SHA256:— | |||
| 3492 | system_update_5.07.0124.tmp | C:\Program Files\Lenovo\System Update\is-CMQSE.tmp | executable | |
MD5:— | SHA256:— | |||
| 3492 | system_update_5.07.0124.tmp | C:\Program Files\Lenovo\System Update\clearsuservice.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
6
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | Tvsukernel.exe | 23.45.104.218:443 | download.lenovo.com | Akamai International B.V. | NL | unknown |
1076 | Tvsukernel.exe | 23.210.252.87:443 | filedownload.lenovo.com | Akamai International B.V. | NL | unknown |
2112 | uts.exe | 23.45.104.218:443 | download.lenovo.com | Akamai International B.V. | NL | unknown |
1076 | Tvsukernel.exe | 38.106.231.204:443 | chifsr.lenovomm.com | Cogent Communications | US | unknown |
2080 | Tvsukernel.exe | 104.84.245.210:443 | download.lenovo.com | Time Warner Cable Internet LLC | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.lenovo.com |
| suspicious |
filedownload.lenovo.com |
| suspicious |
chifsr.lenovomm.com |
| whitelisted |