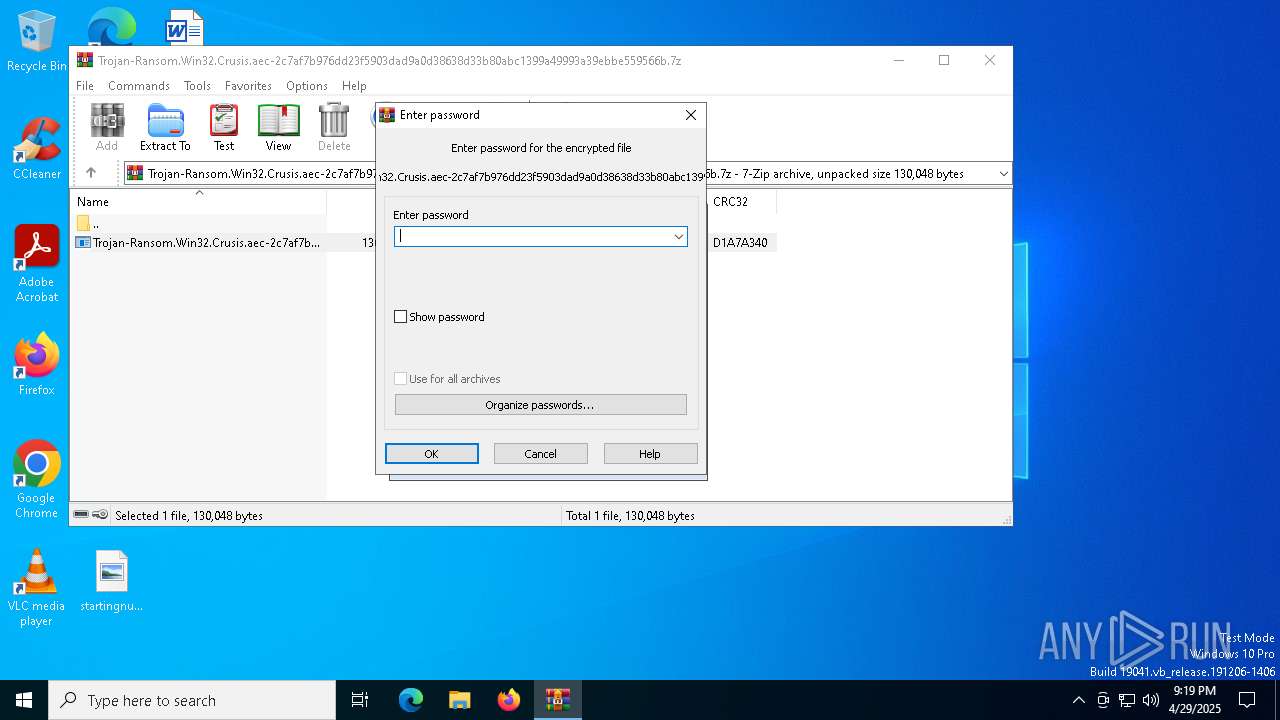
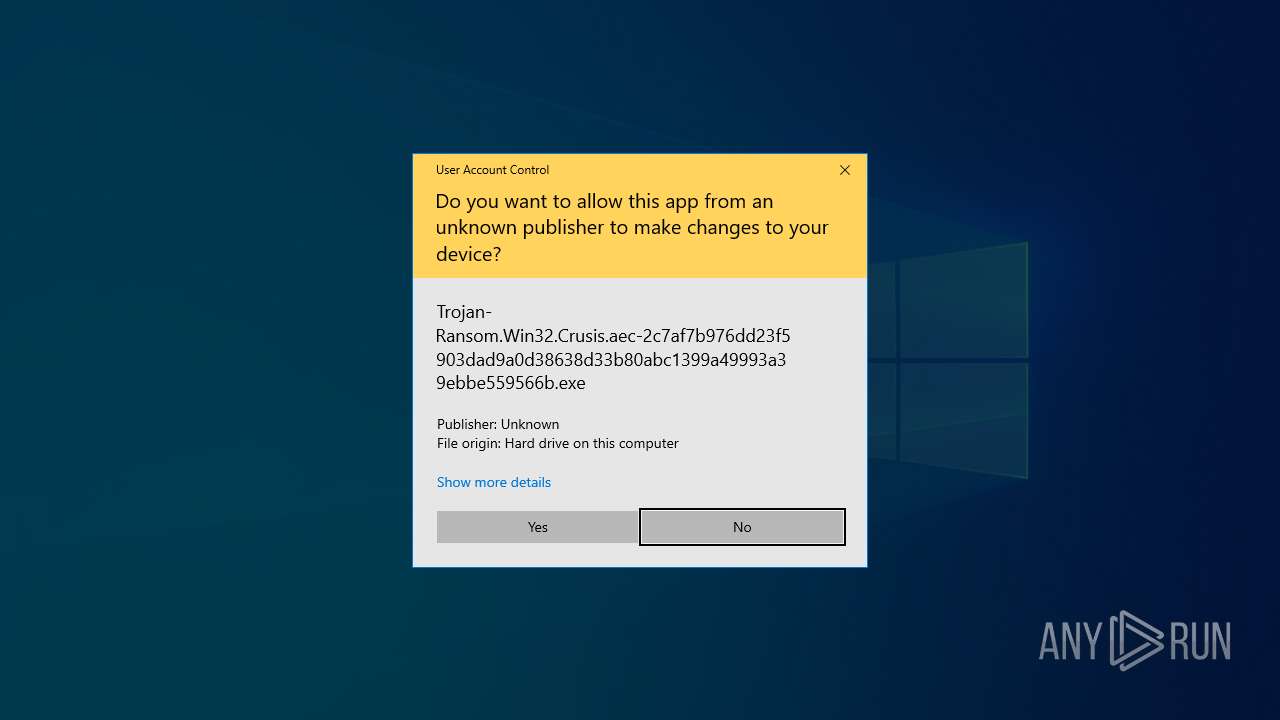
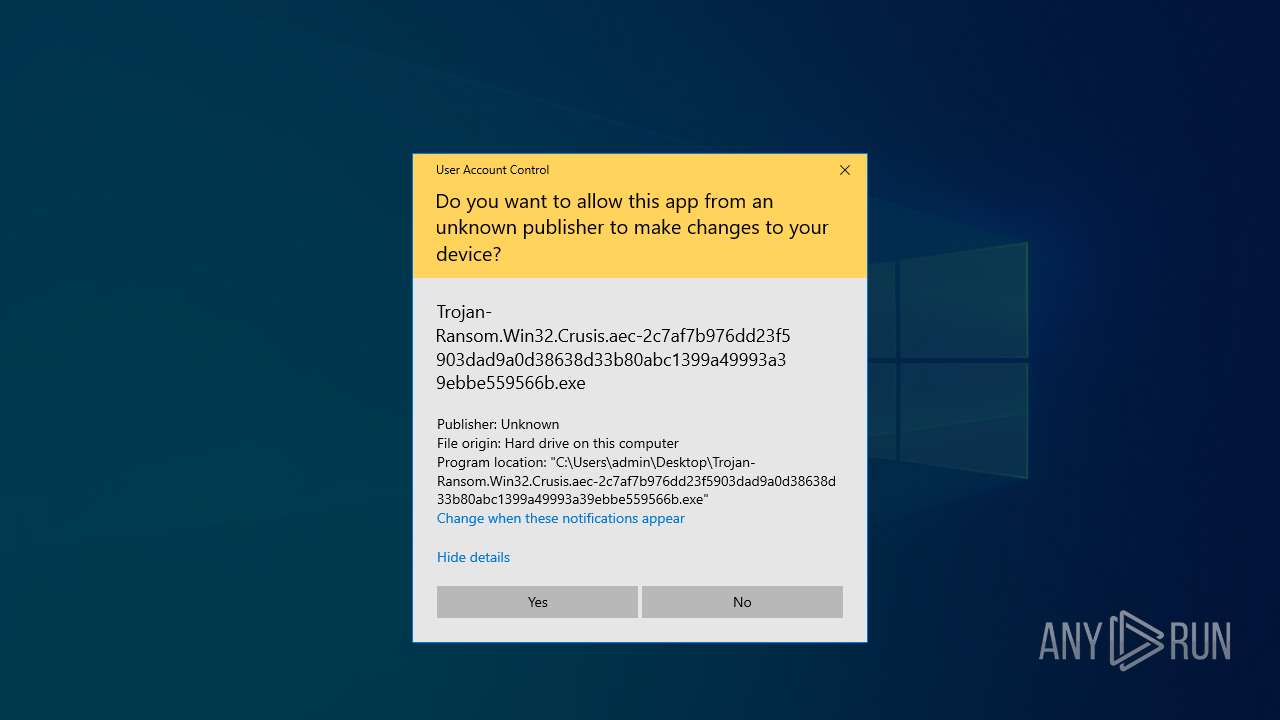
| File name: | Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.7z |
| Full analysis: | https://app.any.run/tasks/9e6b424e-ad62-4e6a-8e91-8392162ffba6 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | April 29, 2025, 21:19:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | CDE7FFCF1BE5A79733F563F67D7A16BB |
| SHA1: | F64132F21D20141F1AEBFA294927AB676214B2AA |
| SHA256: | 2A7CAEF92A584045801D706559D5CCB6A0873C02546D0C4BDD5AC9E382B69AA2 |
| SSDEEP: | 6144:UpasylGSat+JQhRtm0T+WpUskrRYN+c+M6pt:UphyYht++hDeWpUsKM6pt |
MALICIOUS
EMOTET has been detected (YARA)
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 7084)
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 1164)
EMOTET mutex has been found
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 1164)
SUSPICIOUS
Application launched itself
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 7084)
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 5988)
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 8084)
Executable content was dropped or overwritten
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 1164)
Executes as Windows Service
- systemhost.exe (PID: 4452)
Reads security settings of Internet Explorer
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 1164)
INFO
Checks supported languages
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 8084)
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 1164)
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 5988)
- systemhost.exe (PID: 4452)
UPX packer has been detected
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 5988)
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 7084)
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 8084)
- systemhost.exe (PID: 4452)
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 1164)
Reads the software policy settings
- slui.exe (PID: 7520)
- slui.exe (PID: 5404)
Reads the computer name
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 1164)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7348)
Manual execution by a user
- Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe (PID: 8084)
Checks proxy server information
- slui.exe (PID: 5404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2020:11:14 12:24:30+00:00 |
| ArchivedFileName: | Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe |
Total processes
139
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | "C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe" | C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe | Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4452 | C:\WINDOWS\SysWOW64\systemhost.exe | C:\Windows\SysWOW64\systemhost.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 5404 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5988 | "C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe" | C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe | — | Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7084 | "C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe" | C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe | Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7348 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7488 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7520 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8084 | "C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe" | C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
2 446
Read events
2 427
Write events
19
Delete events
0
Modification events
| (PID) Process: | (7348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.7z | |||
| (PID) Process: | (7348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7348.37343\Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe | executable | |
MD5:5B1CB300B43ECD08EBCC138912466038 | SHA256:2C7AF7B976DD23F5903DAD9A0D38638D33B80ABC1399A49993A39EBBE559566B | |||
| 1164 | Trojan-Ransom.Win32.Crusis.aec-2c7af7b976dd23f5903dad9a0d38638d33b80abc1399a49993a39ebbe559566b.exe | C:\Windows\SysWOW64\systemhost.exe | executable | |
MD5:5B1CB300B43ECD08EBCC138912466038 | SHA256:2C7AF7B976DD23F5903DAD9A0D38638D33B80ABC1399A49993A39EBBE559566B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.23:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7280 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7280 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.23:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |