analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
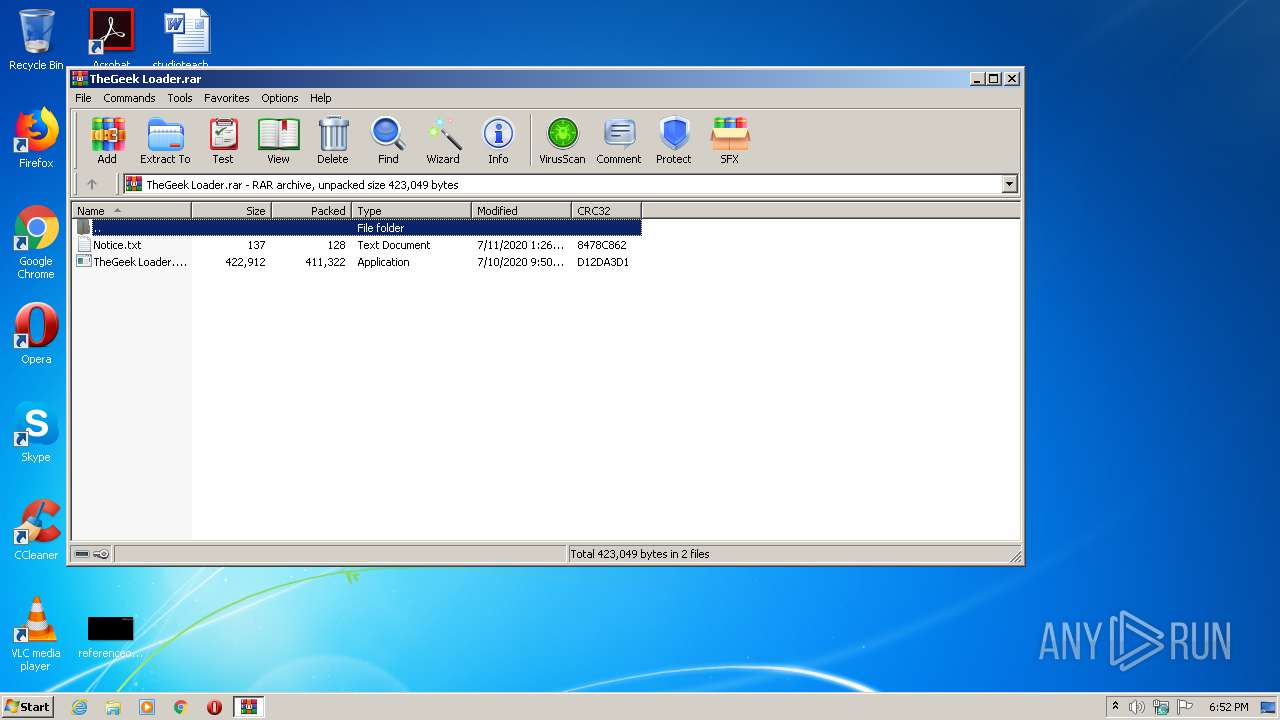
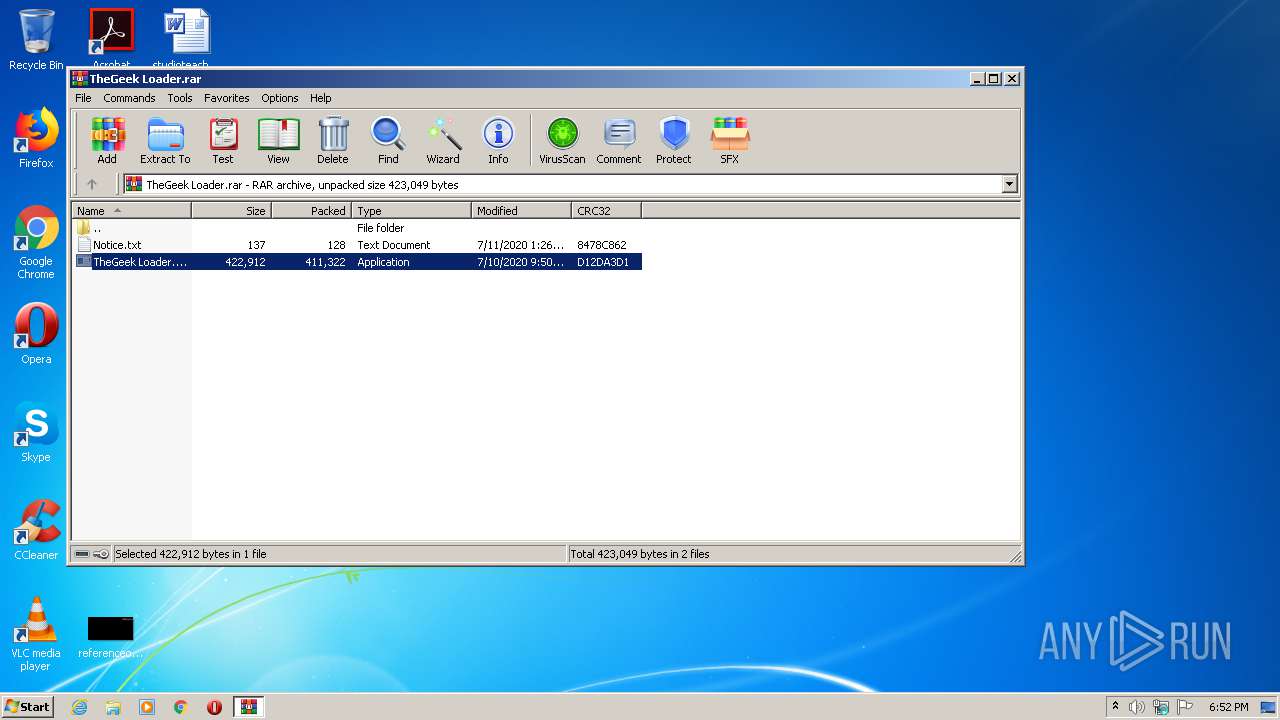
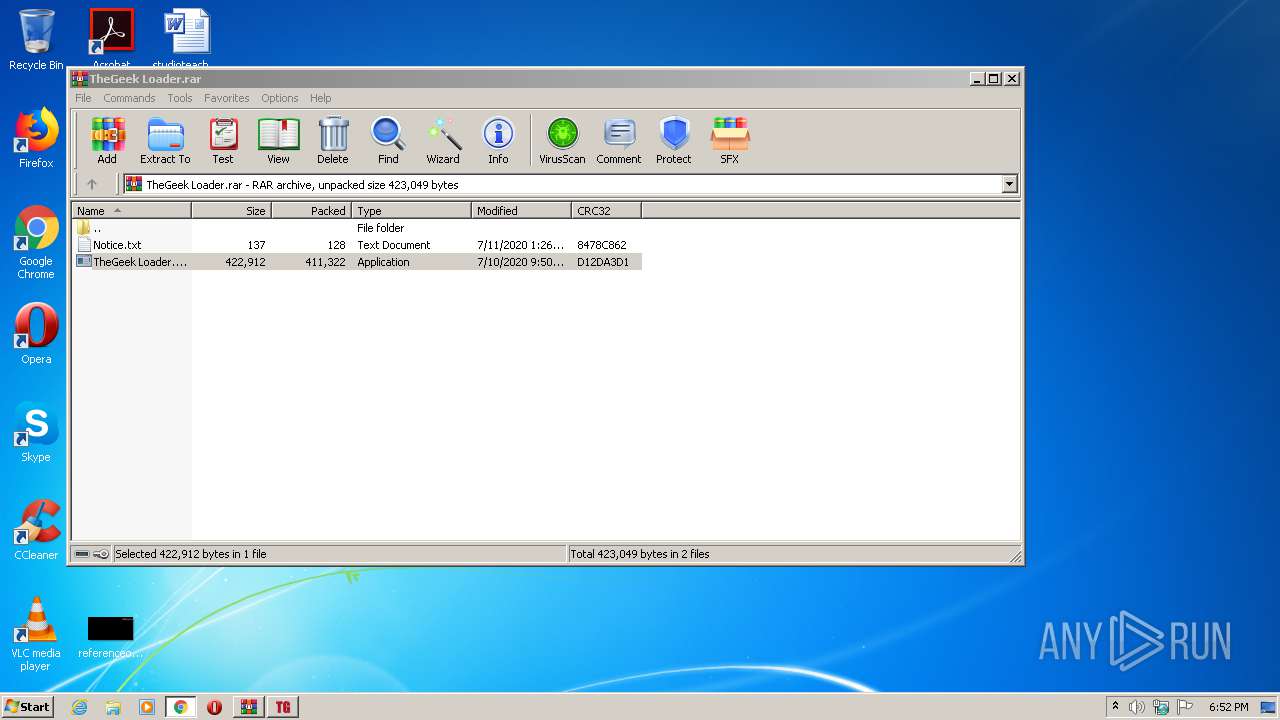
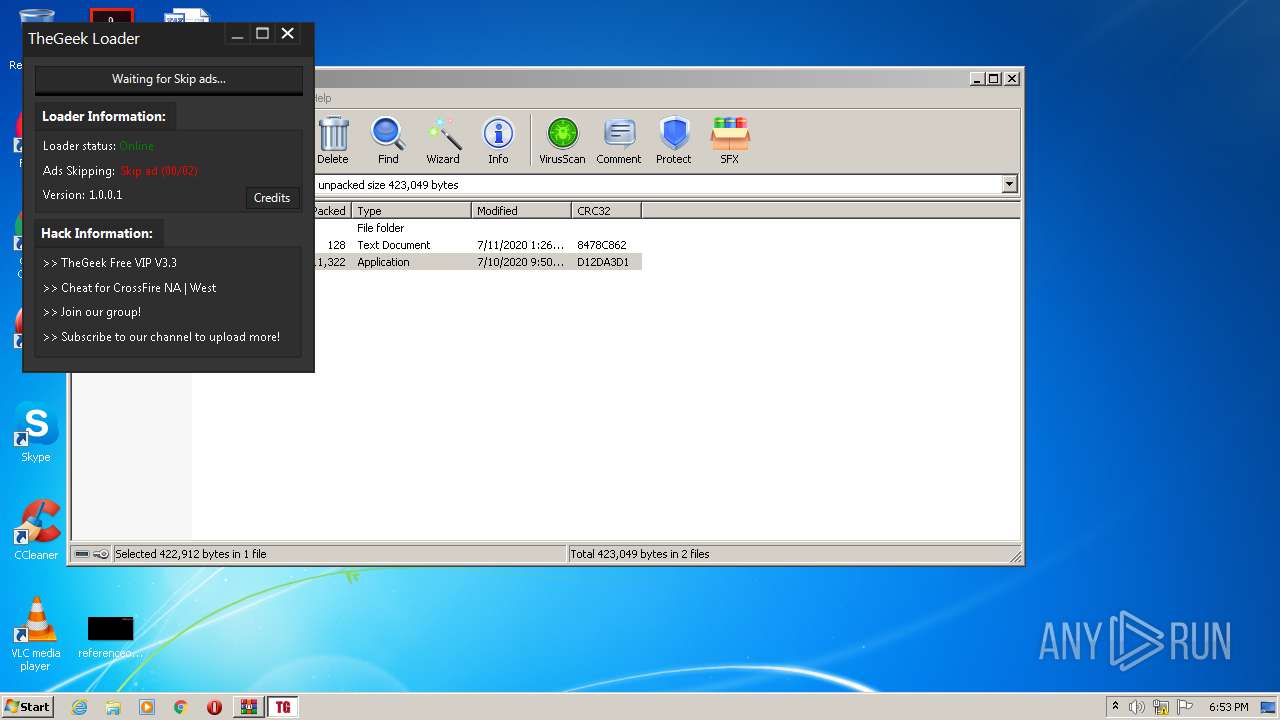
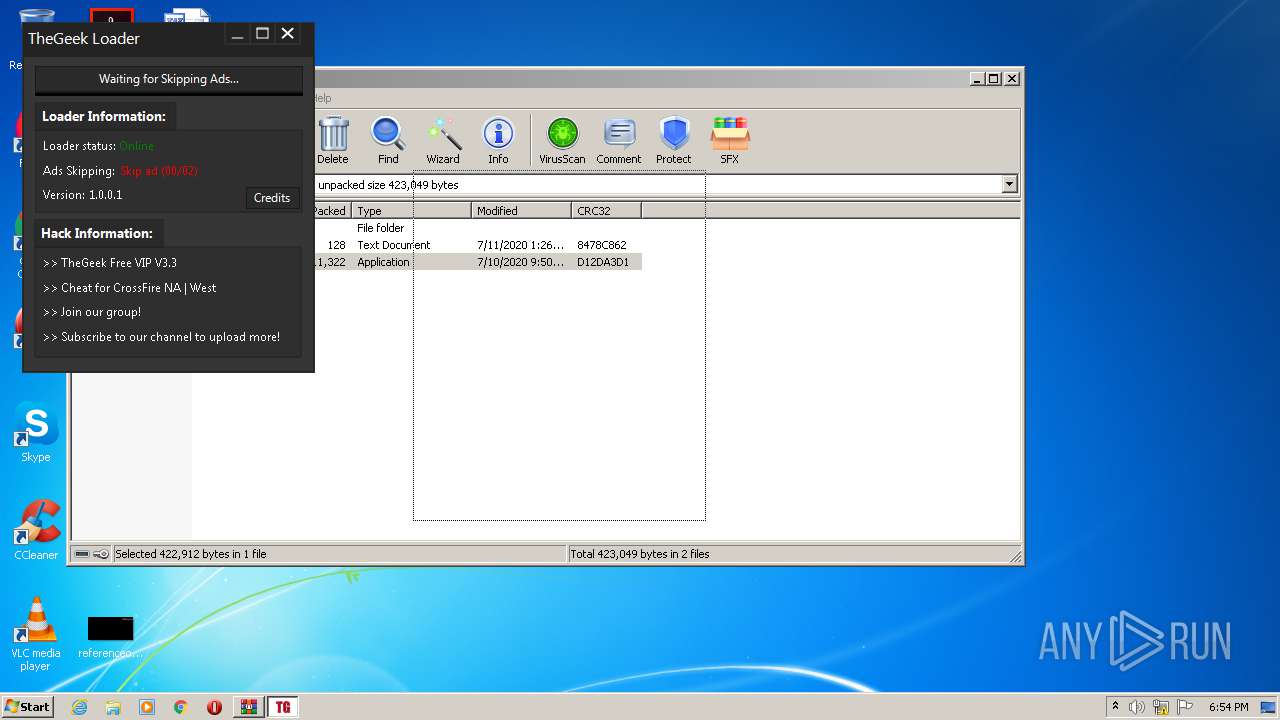
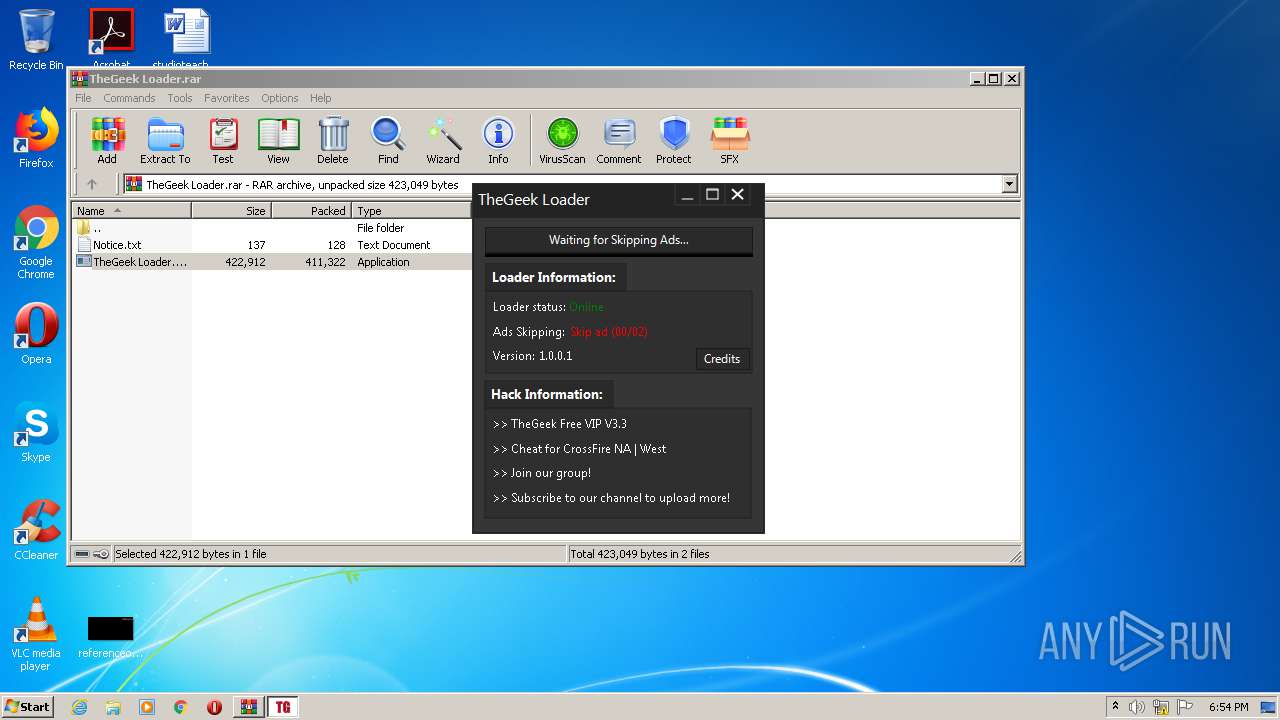
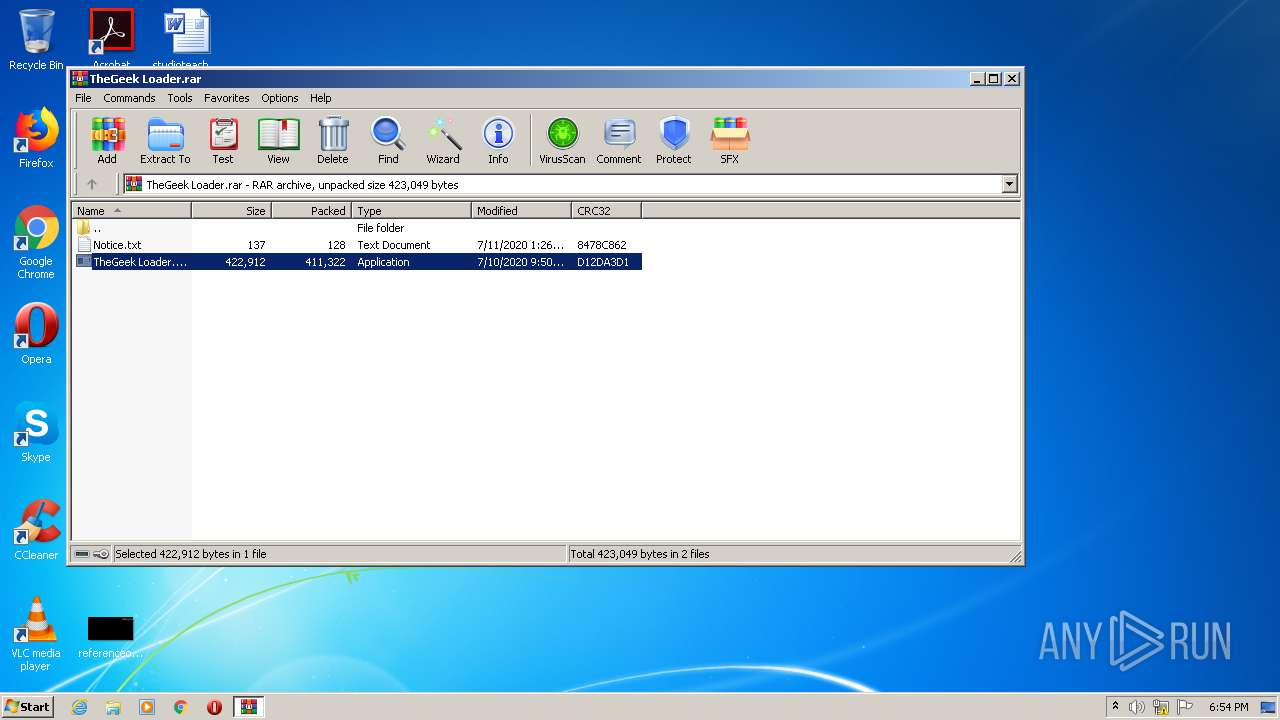
| File name: | TheGeek Loader.rar |
| Full analysis: | https://app.any.run/tasks/998d2207-b35d-48c8-8a5b-a6a576c29e88 |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2020, 17:51:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 8918A3B959CF08F7B363AF5AF3F8E962 |
| SHA1: | 4618336F448F76A4EFF07C4E12BCA3E23BE6342D |
| SHA256: | 2A72F187C79E411D730C2FEE513D2C1942E2E9A7A582164B3E8738D3F7481E15 |
| SSDEEP: | 12288:m5trCjAwpRr5S+BPQ5JRih02gIEn0v+8I6b/e:SrCdp7qr8uIgq/e |
MALICIOUS
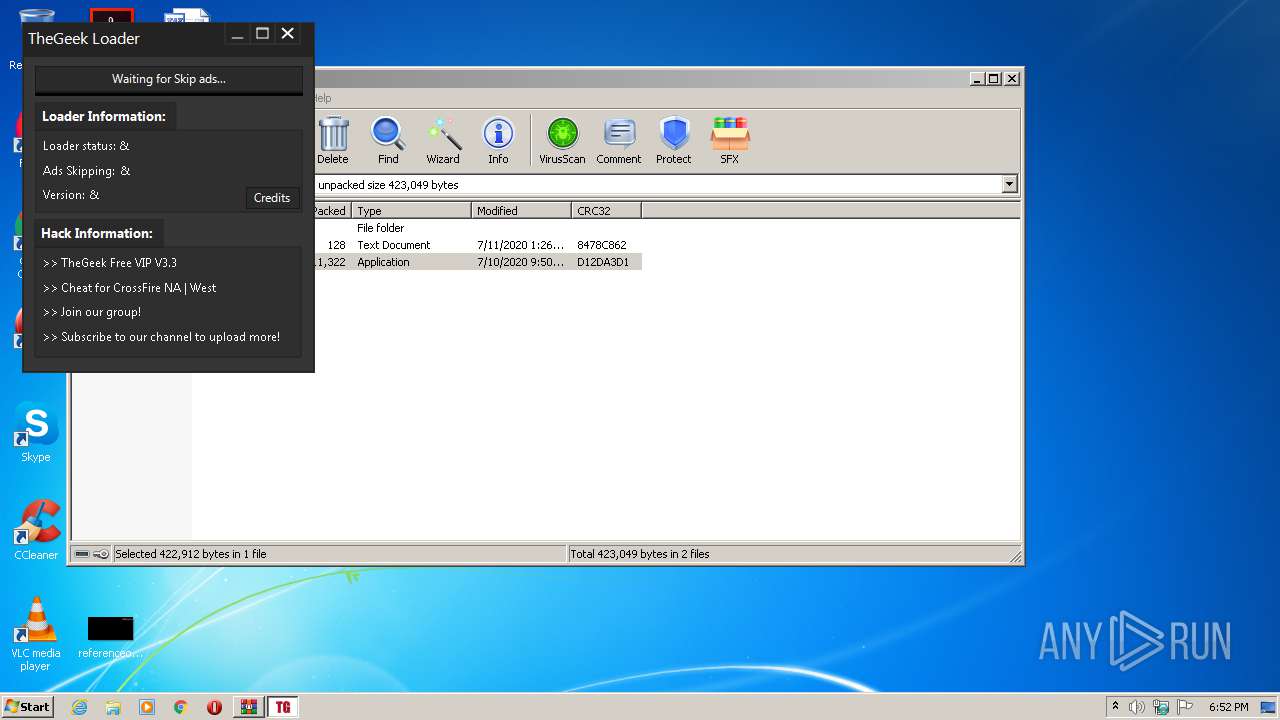
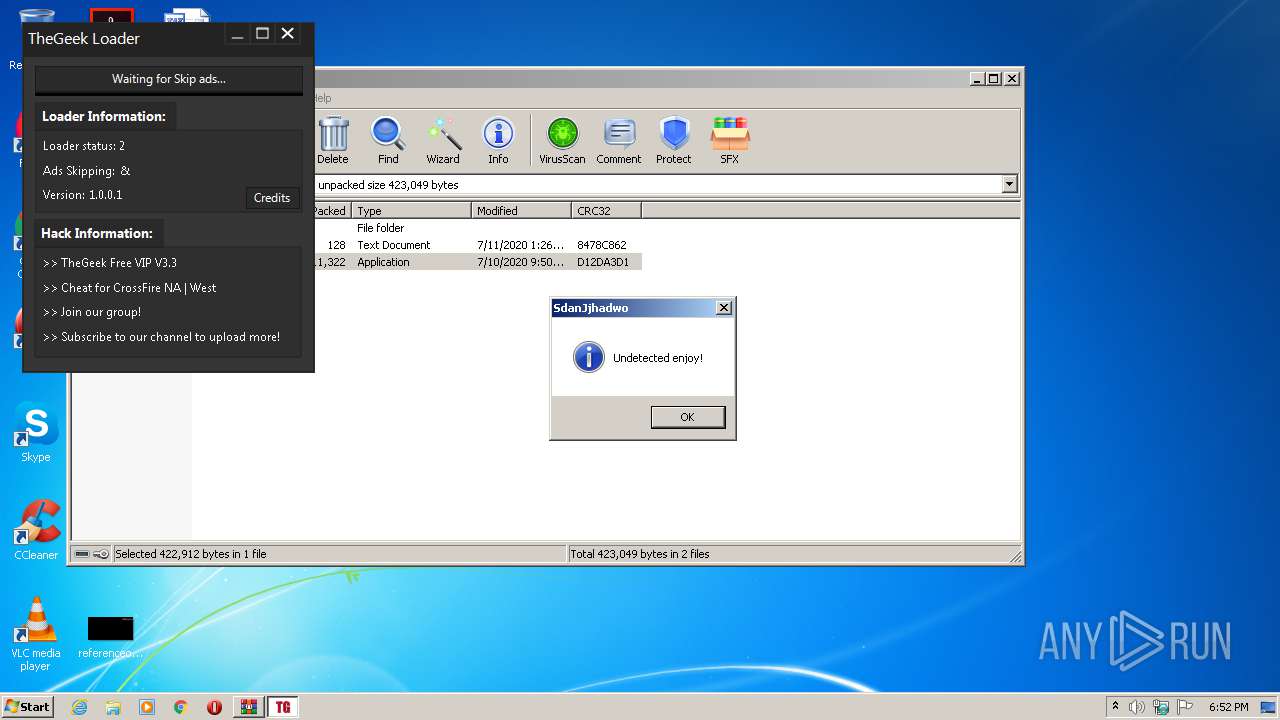
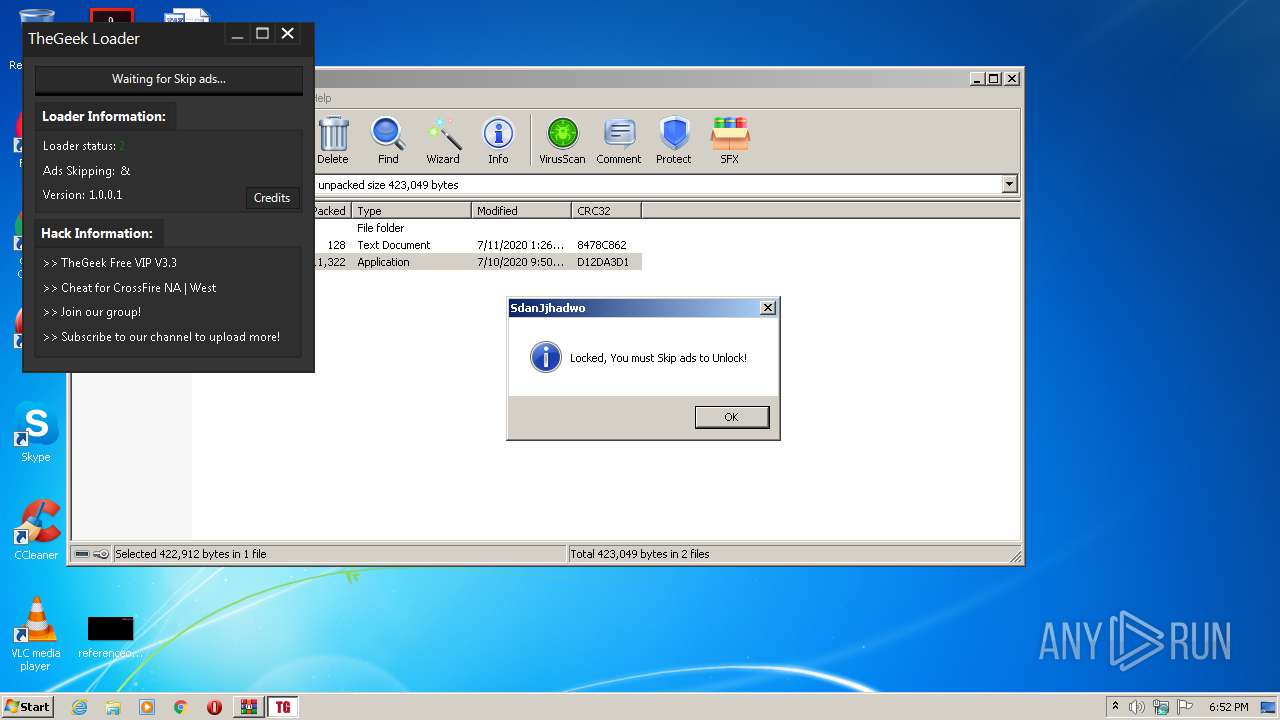
Application was dropped or rewritten from another process
- TheGeek Loader.exe (PID: 2528)
- TheGeek Loader.exe (PID: 4016)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1956)
INFO
Reads the hosts file
- chrome.exe (PID: 3060)
- chrome.exe (PID: 2096)
Application launched itself
- chrome.exe (PID: 3060)
Reads settings of System Certificates
- chrome.exe (PID: 2096)
Adds / modifies Windows certificates
- chrome.exe (PID: 2096)
Changes settings of System certificates
- chrome.exe (PID: 2096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
51
Monitored processes
13
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 1956 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\TheGeek Loader.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.60.0 | ||||
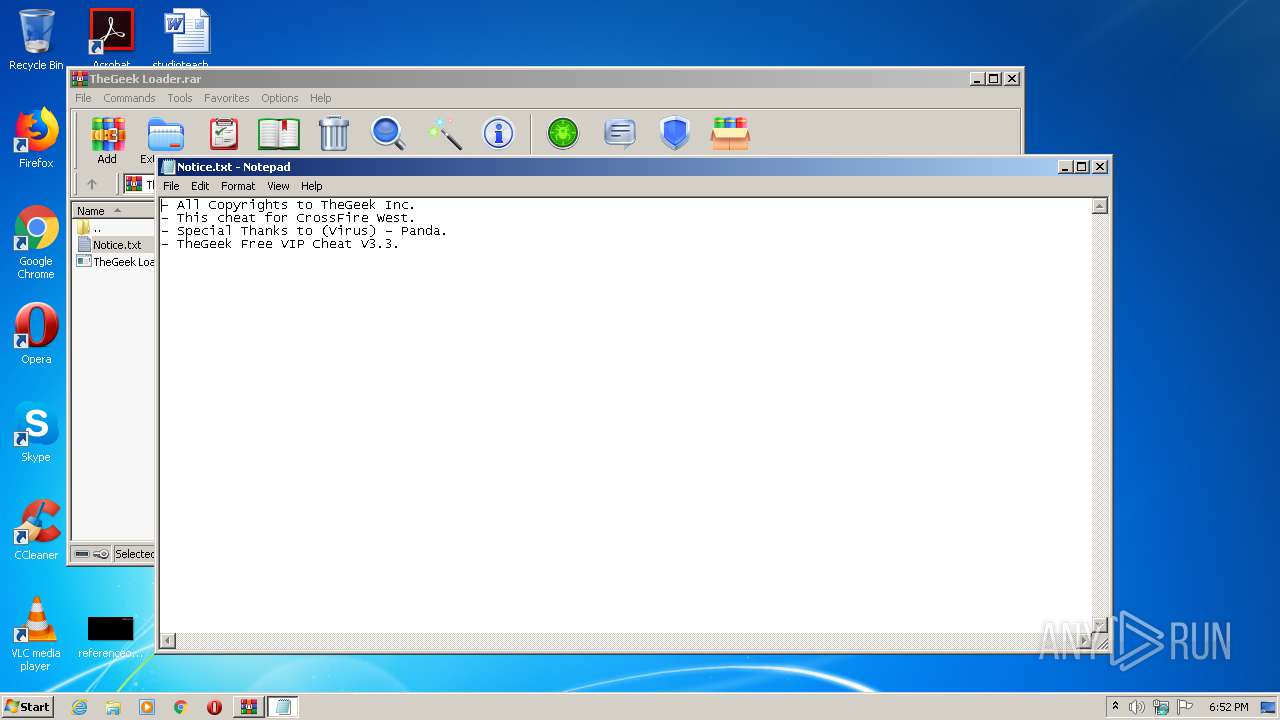
| 3876 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa1956.15671\Notice.txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
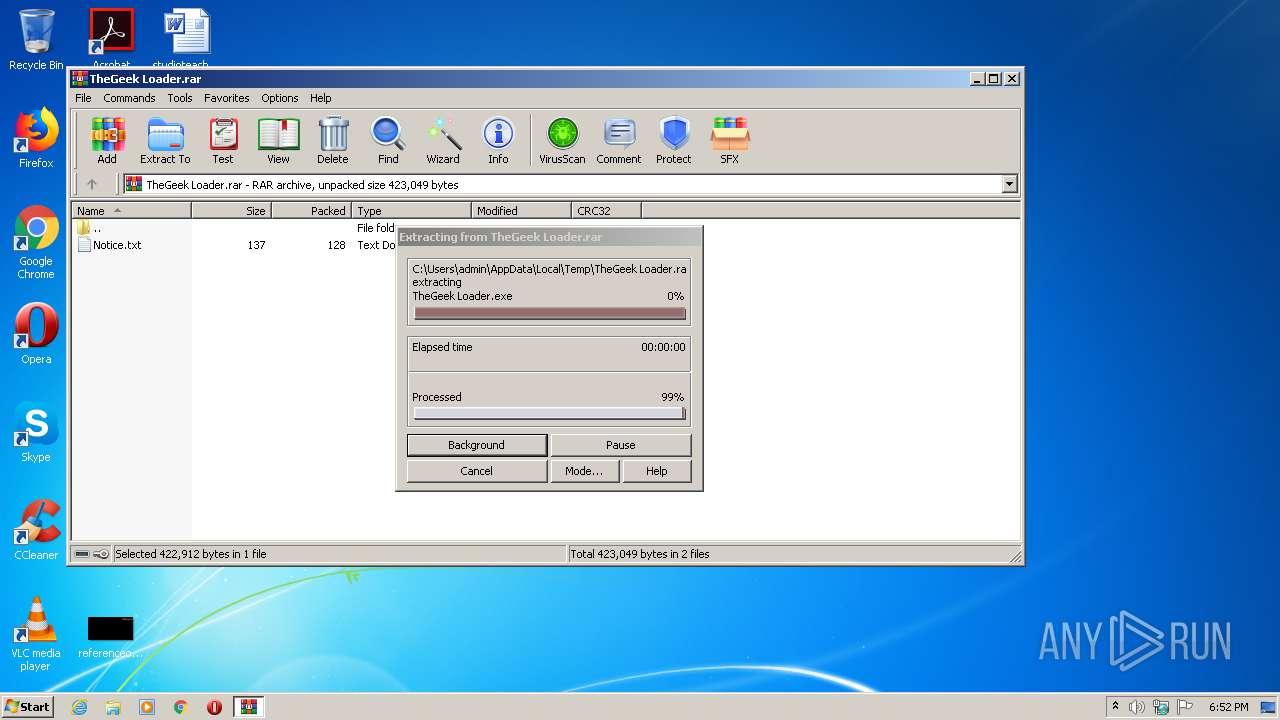
| 2528 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1956.16343\TheGeek Loader.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1956.16343\TheGeek Loader.exe | — | WinRAR.exe |
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 1.0.0.1 | ||||
| 4016 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1956.16343\TheGeek Loader.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1956.16343\TheGeek Loader.exe | WinRAR.exe | |
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 1.0.0.1 | ||||
| 3060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://cuts-url.com/0eftyE | C:\Program Files\Google\Chrome\Application\chrome.exe | TheGeek Loader.exe | |
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 3221225547 Version: 75.0.3770.100 | ||||
| 4088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6aa1a9d0,0x6aa1a9e0,0x6aa1a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 | ||||
| 2868 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3048 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 | ||||
| 2556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,483462412923465585,1306339465775045377,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=4667597633081330587 --mojo-platform-channel-handle=968 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 | ||||
| 2096 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,483462412923465585,1306339465775045377,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=5750617050218571837 --mojo-platform-channel-handle=1652 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | |
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 | ||||
| 2848 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,483462412923465585,1306339465775045377,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11187156911698432749 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2260 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 | ||||
Total events
2 773
Read events
1 017
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
14
Text files
85
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5F0B4DEB-BF4.pma | — | |
MD5:— | SHA256:— | |||
| 3060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\a0623dca-113c-452d-b2b8-8defcc488a27.tmp | — | |
MD5:— | SHA256:— | |||
| 1956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1956.15671\Notice.txt | text | |
MD5:55649E4EC1ED0F8F8C656B1441AA0CD9 | SHA256:F3940E58FA120BA5254844AC8B7C988237E48A236C72C5D2841017A7D256C9AD | |||
| 1956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1956.16343\Notice.txt | text | |
MD5:55649E4EC1ED0F8F8C656B1441AA0CD9 | SHA256:F3940E58FA120BA5254844AC8B7C988237E48A236C72C5D2841017A7D256C9AD | |||
| 1956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1956.16343\TheGeek Loader.exe | executable | |
MD5:658FF00AF1ECC605B087621ED4B2149A | SHA256:800BEDB2396FBF1AA9EBA9220C29466B2931FAE0187152B573E0C5CBB5F3A8D7 | |||
| 3060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:DA692BE42E4EF2668AE7499A7D5DA720 | SHA256:EB865CAF59002C092F5FDBE22D01935866BC1277108B29E897052CB2439630ED | |||
| 3060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1006c8.TMP | text | |
MD5:DA692BE42E4EF2668AE7499A7D5DA720 | SHA256:EB865CAF59002C092F5FDBE22D01935866BC1277108B29E897052CB2439630ED | |||
| 3060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF1006d8.TMP | text | |
MD5:F69C20D5B552B8D973FB1CBA5FDD7D87 | SHA256:48799968D50E2D74E625A0AB18E93C6792AF20010334C6BB4E935C8D26F7026A | |||
| 3060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:F69C20D5B552B8D973FB1CBA5FDD7D87 | SHA256:48799968D50E2D74E625A0AB18E93C6792AF20010334C6BB4E935C8D26F7026A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
11
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4016 | TheGeek Loader.exe | GET | 200 | 204.12.192.242:80 | http://tgramo.guncheats.com/version.txt | US | text | 7 b | suspicious |
4016 | TheGeek Loader.exe | GET | 200 | 204.12.192.242:80 | http://tgramo.guncheats.com/sandbox/status.txt | US | binary | 1 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2096 | chrome.exe | 35.208.223.29:443 | cuts-url.com | — | US | unknown |
4016 | TheGeek Loader.exe | 204.12.192.242:80 | tgramo.guncheats.com | WholeSale Internet, Inc. | US | suspicious |
2096 | chrome.exe | 216.58.207.36:443 | www.google.com | Google Inc. | US | whitelisted |
2096 | chrome.exe | 172.217.18.109:443 | accounts.google.com | Google Inc. | US | suspicious |
2096 | chrome.exe | 216.58.207.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2096 | chrome.exe | 216.58.207.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tgramo.guncheats.com |
| suspicious |
cuts-url.com |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
1 ETPRO signatures available at the full report