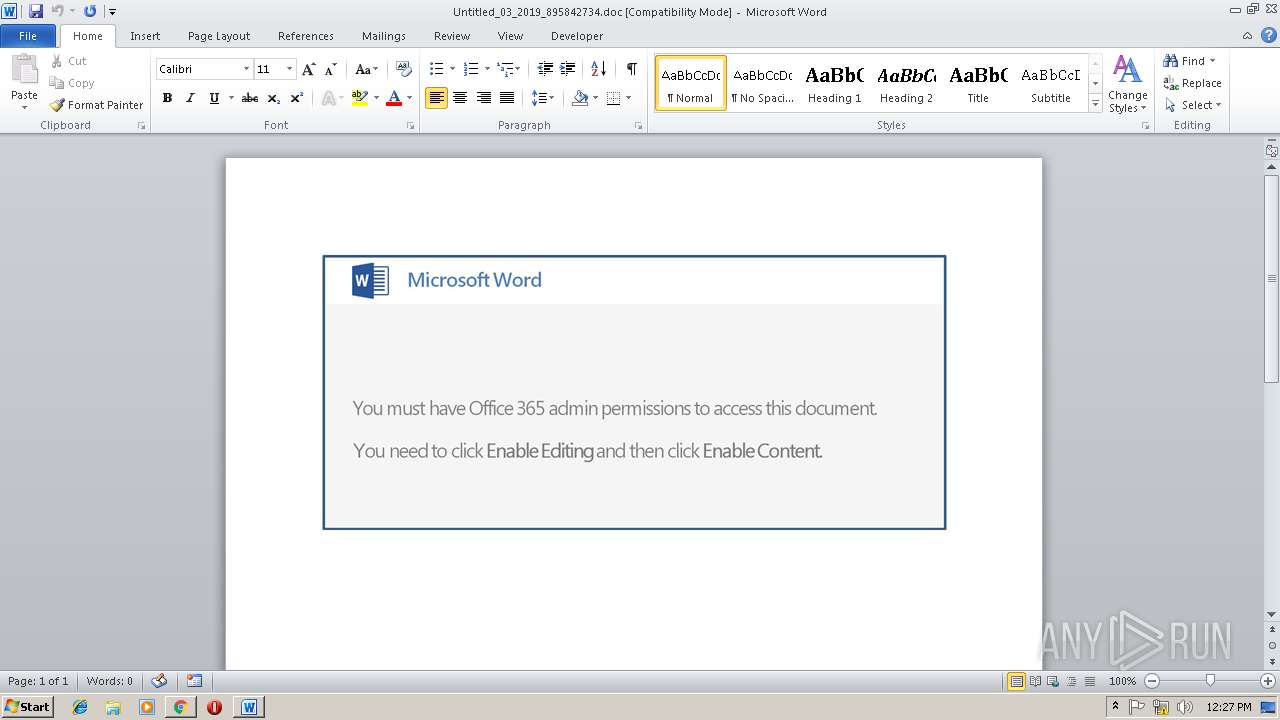
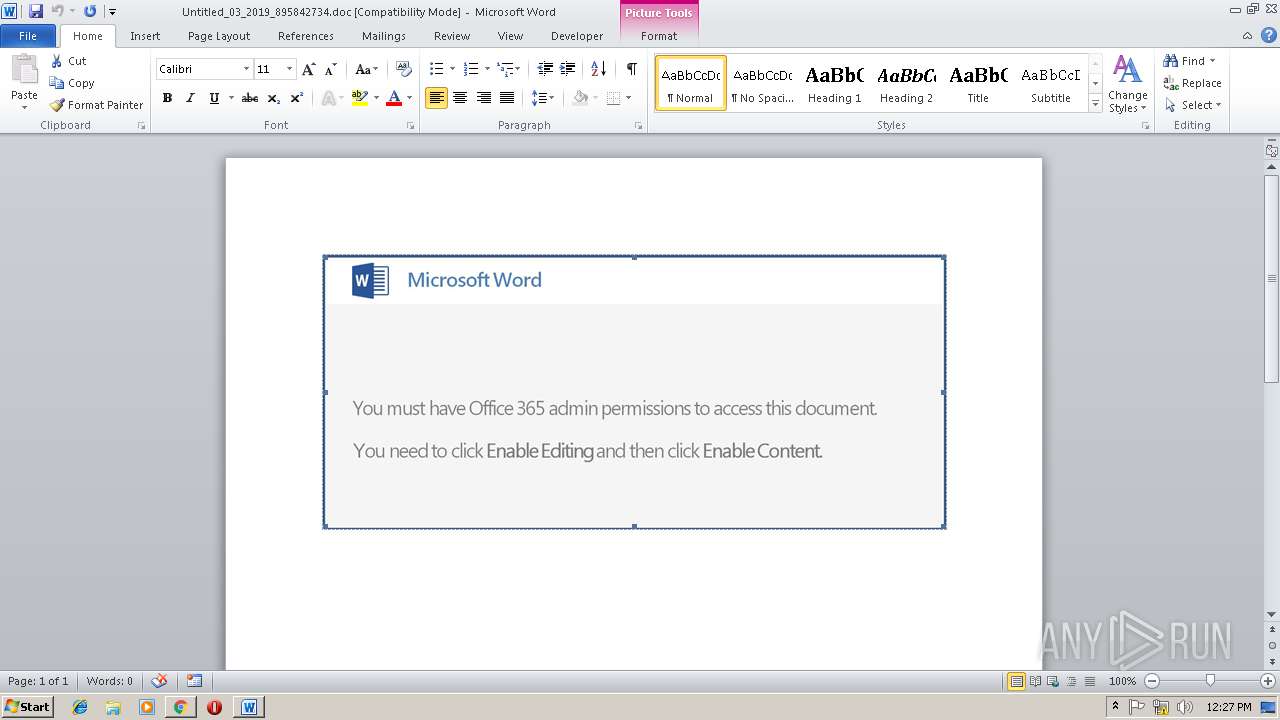
| URL: | http://13.127.80.82/ClvW8ZSqo0icX_OiB6Mv8/trust.myacc.send.com/ |
| Full analysis: | https://app.any.run/tasks/dd55d66c-e0ca-4874-9299-c66639e73bb1 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | March 14, 2019, 12:27:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8903E59F723E8901757945342E633BA4 |
| SHA1: | 7377DCFB800CED9818752BAC98873BD70E932D82 |
| SHA256: | 2A5A4C6445BA9E2E9732449A6D55CCFA5EDAD742D8EF83222C6D7535AFDAFFCC |
| SSDEEP: | 3:N1KuLVdami2UKVMGHkZRAWWGOLR:CuzaZmVkvQGkR |
MALICIOUS
Application was dropped or rewritten from another process
- 947.exe (PID: 3664)
- 947.exe (PID: 3316)
- wabmetagen.exe (PID: 3648)
- wabmetagen.exe (PID: 2852)
Downloads executable files from the Internet
- powershell.exe (PID: 3472)
Emotet process was detected
- wabmetagen.exe (PID: 3648)
Connects to CnC server
- wabmetagen.exe (PID: 2852)
EMOTET was detected
- wabmetagen.exe (PID: 2852)
Changes the autorun value in the registry
- wabmetagen.exe (PID: 2852)
SUSPICIOUS
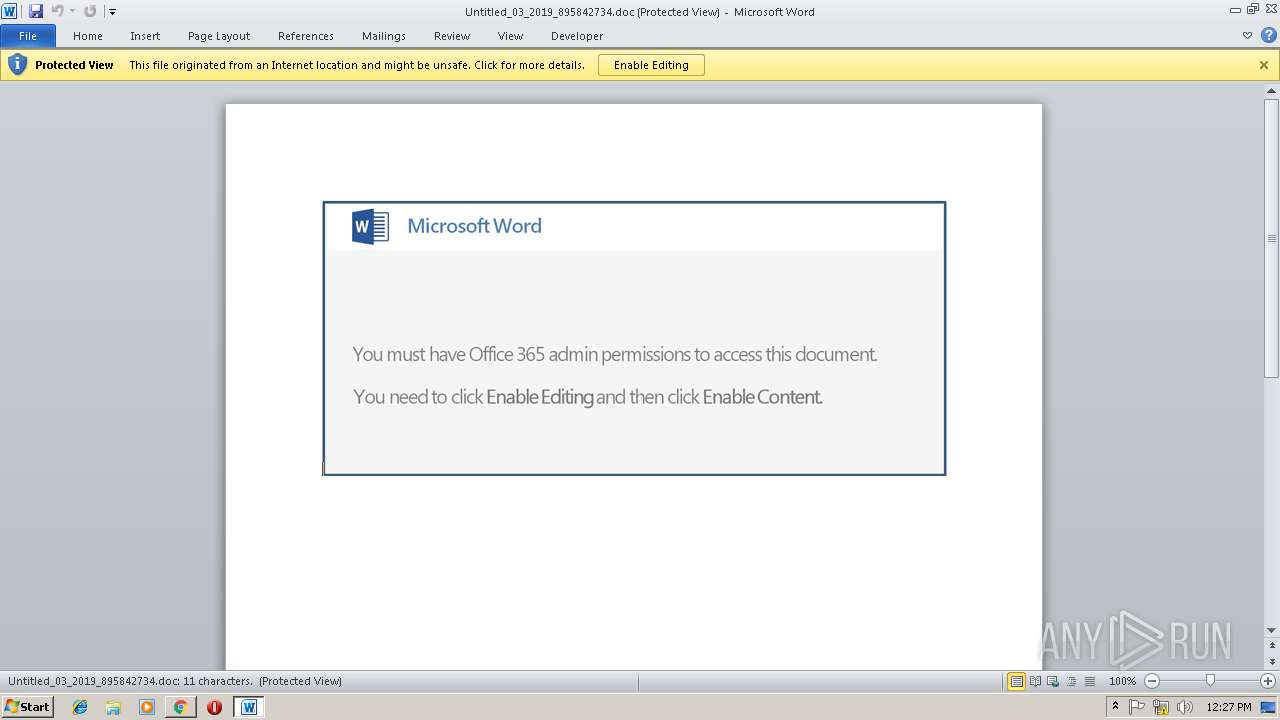
Starts Microsoft Office Application
- chrome.exe (PID: 3016)
- WINWORD.EXE (PID: 2672)
Application launched itself
- WINWORD.EXE (PID: 2672)
- 947.exe (PID: 3664)
- wabmetagen.exe (PID: 3648)
Creates files in the user directory
- powershell.exe (PID: 3472)
Executable content was dropped or overwritten
- powershell.exe (PID: 3472)
- 947.exe (PID: 3316)
Starts itself from another location
- 947.exe (PID: 3316)
INFO
Application launched itself
- chrome.exe (PID: 3016)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2672)
- WINWORD.EXE (PID: 2060)
Creates files in the user directory
- WINWORD.EXE (PID: 2672)
Reads Internet Cache Settings
- chrome.exe (PID: 3016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
15
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=896,6648249723427096982,15695952238347034389,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=AA494380577D90A2CDEFA9D0D1E41C19 --mojo-platform-channel-handle=992 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2588 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=896,6648249723427096982,15695952238347034389,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=58B0CE66A651CB62913C12F8F69BF9C0 --mojo-platform-channel-handle=3996 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2620 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=896,6648249723427096982,15695952238347034389,131072 --enable-features=PasswordImport --service-pipe-token=427DE808F1064E279CB6A5454577F939 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=427DE808F1064E279CB6A5454577F939 --renderer-client-id=4 --mojo-platform-channel-handle=1900 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2672 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Downloads\Untitled_03_2019_895842734.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | chrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3020 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" http://13.127.80.82/ClvW8ZSqo0icX_OiB6Mv8/trust.myacc.send.com/ | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3316 | "C:\Users\admin\947.exe" | C:\Users\admin\947.exe | 947.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3336 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=896,6648249723427096982,15695952238347034389,131072 --enable-features=PasswordImport --service-pipe-token=A476A9D1919CDB71C85A5C94B7F0B3CD --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=A476A9D1919CDB71C85A5C94B7F0B3CD --renderer-client-id=3 --mojo-platform-channel-handle=2120 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
3 233
Read events
2 756
Write events
463
Delete events
14
Modification events
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3016-13197040037605250 |
Value: 259 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
Executable files
2
Suspicious files
16
Text files
53
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\c6a484de-d67a-4c9d-b966-e6a0837a8f8f.tmp | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\bb7ec766-a2f6-4a0d-b5fb-31418e23255c.tmp | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\beb2c8e7-1877-4cba-a17f-1606f95062c8.tmp | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF20e802.TMP | text | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\Downloads\af77c0a6-931e-48e2-b0d0-20c56f0b50ad.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
9
DNS requests
5
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2852 | wabmetagen.exe | GET | 200 | 82.78.228.57:443 | http://82.78.228.57:443/ | RO | binary | 132 b | malicious |
3472 | powershell.exe | GET | 200 | 103.57.209.252:80 | http://ngkidshop.com/wp-content/Vtm8/ | VN | executable | 180 Kb | malicious |
3016 | chrome.exe | GET | 200 | 13.127.80.82:80 | http://13.127.80.82/ClvW8ZSqo0icX_OiB6Mv8/trust.myacc.send.com/ | IN | document | 245 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3016 | chrome.exe | 13.127.80.82:80 | — | Amazon.com, Inc. | IN | suspicious |
3016 | chrome.exe | 172.217.168.195:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3016 | chrome.exe | 216.58.208.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
3016 | chrome.exe | 216.58.210.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3016 | chrome.exe | 216.58.207.67:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3472 | powershell.exe | 103.57.209.252:80 | ngkidshop.com | — | VN | suspicious |
2852 | wabmetagen.exe | 82.78.228.57:443 | — | RCS & RDS | RO | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.gstatic.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
ngkidshop.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3016 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY Office Document Download Containing AutoOpen Macro |
3016 | chrome.exe | Misc activity | SUSPICIOUS [PTsecurity] Download DOC file with VBAScript |
3472 | powershell.exe | Misc Attack | ET COMPROMISED Known Compromised or Hostile Host Traffic group 1 |
3472 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3472 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3472 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2852 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1 ETPRO signatures available at the full report