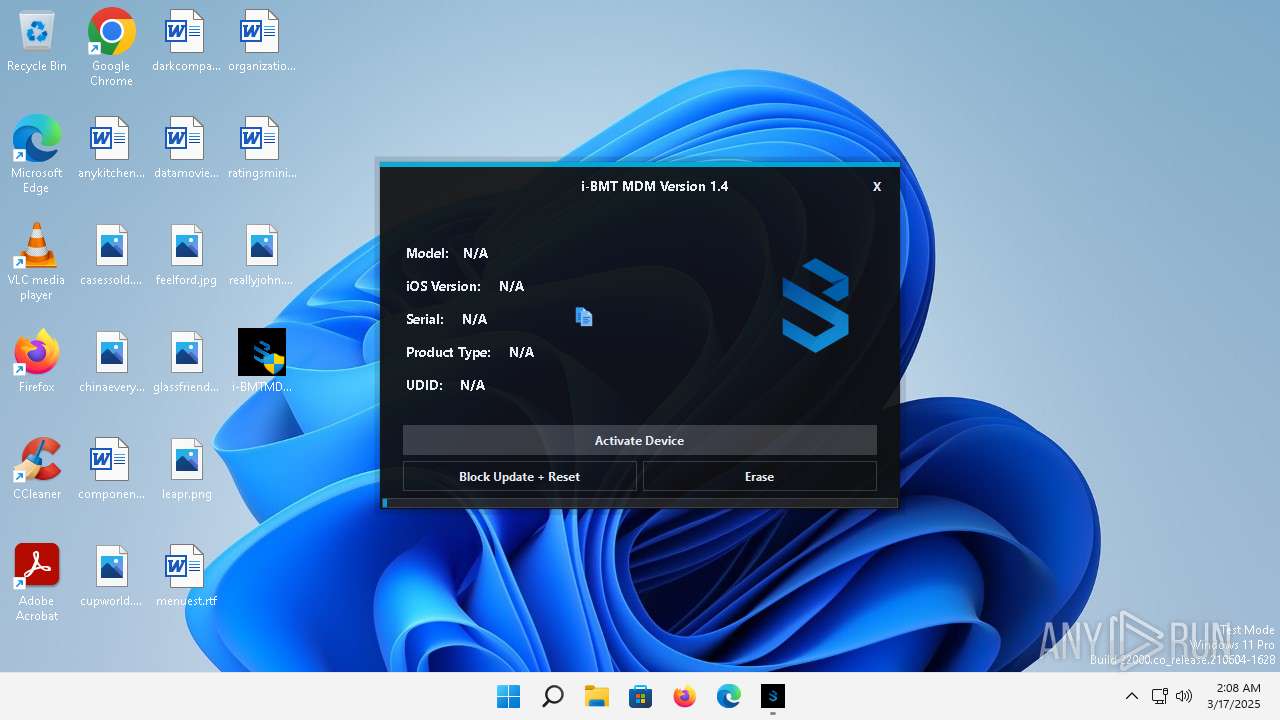
| File name: | i-BMTMDMv1.4.exe |
| Full analysis: | https://app.any.run/tasks/b67aee19-f62f-4000-a999-a581636b6c12 |
| Verdict: | Malicious activity |
| Analysis date: | March 17, 2025, 02:07:25 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 7203C703FF0E363665678A8B48CE6BC1 |
| SHA1: | BB7EDC979670C64531EF44CA68000763E2EFFB2E |
| SHA256: | 2A58FD33F333FD7E161D3B475032C19EA3BAA6D87F1B016869F8F91A6EF48A7A |
| SSDEEP: | 393216:gJmL4ZSW68mbpoHP9cZGmcvcm2uW+xhxb12TYEr7rv:om8ZBrDmcvJdjhxx2Nr7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- i-BMTMDMv1.4.exe (PID: 4480)
The process drops C-runtime libraries
- i-BMTMDMv1.4.exe (PID: 4480)
Process drops legitimate windows executable
- i-BMTMDMv1.4.exe (PID: 4480)
Reads security settings of Internet Explorer
- i-BMTMDMv1.4.exe (PID: 4480)
- i-BMT MDM.exe (PID: 5948)
Reads the Internet Settings
- i-BMTMDMv1.4.exe (PID: 4480)
- i-BMT MDM.exe (PID: 5948)
Reads settings of System Certificates
- i-BMT MDM.exe (PID: 5948)
There is functionality for taking screenshot (YARA)
- i-BMT MDM.exe (PID: 5948)
INFO
Creates files in the program directory
- i-BMTMDMv1.4.exe (PID: 4480)
The sample compiled with english language support
- i-BMTMDMv1.4.exe (PID: 4480)
Reads the computer name
- i-BMTMDMv1.4.exe (PID: 4480)
- i-BMT MDM.exe (PID: 5948)
Checks supported languages
- i-BMT MDM.exe (PID: 5948)
- i-BMTMDMv1.4.exe (PID: 4480)
- ideviceinfo.exe (PID: 5928)
Reads the machine GUID from the registry
- i-BMT MDM.exe (PID: 5948)
Disables trace logs
- i-BMT MDM.exe (PID: 5948)
Checks proxy server information
- i-BMT MDM.exe (PID: 5948)
Reads the software policy settings
- i-BMT MDM.exe (PID: 5948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (57.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (18.2) |
| .exe | | | Win16/32 Executable Delphi generic (8.3) |
| .exe | | | Generic Win/DOS Executable (8) |
| .exe | | | DOS Executable Generic (8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 107520 |
| InitializedDataSize: | 285184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1a238 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.0.0 |
| ProductVersionNumber: | 1.4.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | bmtmdm |
| FileVersion: | 1.4.0.0 |
| InternalName: | i-BMT MDM.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | - |
| OriginalFileName: | i-BMT MDM.exe |
| ProductName: | bmtmdm |
| ProductVersion: | 1.4.0.0 |
| AssemblyVersion: | 1.4.0.0 |
Total processes
104
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ideviceinfo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | "C:\Users\admin\Desktop\i-BMTMDMv1.4.exe" | C:\Users\admin\Desktop\i-BMTMDMv1.4.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: bmtmdm Exit code: 3221226540 Version: 1.4.0.0 Modules
| |||||||||||||||
| 4480 | "C:\Users\admin\Desktop\i-BMTMDMv1.4.exe" | C:\Users\admin\Desktop\i-BMTMDMv1.4.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: bmtmdm Version: 1.4.0.0 Modules
| |||||||||||||||
| 5928 | "C:\ProgramData\43f7cc1d/files/ideviceinfo.exe" | C:\ProgramData\43f7cc1d\files\ideviceinfo.exe | — | i-BMT MDM.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Modules
| |||||||||||||||
| 5948 | "C:\ProgramData\43f7cc1d\i-BMT MDM.exe" | C:\ProgramData\43f7cc1d\i-BMT MDM.exe | i-BMTMDMv1.4.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: bmtmdm Version: 1.4.0.0 Modules
| |||||||||||||||
Total events
4 104
Read events
4 074
Write events
30
Delete events
0
Modification events
| (PID) Process: | (4480) i-BMTMDMv1.4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4480) i-BMTMDMv1.4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4480) i-BMTMDMv1.4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4480) i-BMTMDMv1.4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5948) i-BMT MDM.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\i-BMT MDM_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5948) i-BMT MDM.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\i-BMT MDM_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5948) i-BMT MDM.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\i-BMT MDM_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5948) i-BMT MDM.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\i-BMT MDM_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5948) i-BMT MDM.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\i-BMT MDM_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5948) i-BMT MDM.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\i-BMT MDM_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
136
Suspicious files
11
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4480 | i-BMTMDMv1.4.exe | C:\ProgramData\43f7cc1d\files\bash.exe | executable | |
MD5:32275787C7C51D2310B8FE2FACF2A935 | SHA256:744343E01351BA92E365B7E24EEDD4ED18ED3EBE26E68C69D9B5E324FE64A1B5 | |||
| 4480 | i-BMTMDMv1.4.exe | C:\ProgramData\43f7cc1d\files\basenc.exe | executable | |
MD5:5D45A6C2FA8989CB2E974637EE0AF63D | SHA256:39A435A6A46A997417630BBC5374E89F3D34673EB10E65CEE6122A6BB547D47E | |||
| 4480 | i-BMTMDMv1.4.exe | C:\ProgramData\43f7cc1d\EasyHttp.dll | executable | |
MD5:B9565595F5CFA8252113045EE58C6C23 | SHA256:8B58D6316D584CAAC75A6E42D8FE10EDD487BE65660BE3EC5AD052AC466D0264 | |||
| 4480 | i-BMTMDMv1.4.exe | C:\ProgramData\43f7cc1d\files\bz2.dll | executable | |
MD5:4811FFA767191513A35B889E3B162241 | SHA256:65EA387636C06133B02E3F6B9C776FEB2DA851C89D6796CFA172C79BC43DF319 | |||
| 4480 | i-BMTMDMv1.4.exe | C:\ProgramData\43f7cc1d\files\awk.exe | executable | |
MD5:850A4DEE8799BC92FC454AA7EB75B926 | SHA256:6DAD72258006DC40A68C8C4B3841387198071CB833E843E01BCFA7FED72A0766 | |||
| 4480 | i-BMTMDMv1.4.exe | C:\ProgramData\43f7cc1d\files\cat.exe | executable | |
MD5:B3B5C6023C35EFBC288C13C125DD6ADA | SHA256:3BAE261D556F4B89C4883B07F9F9632A6495FBFDFFA507C1326007E77C20D9BB | |||
| 4480 | i-BMTMDMv1.4.exe | C:\ProgramData\43f7cc1d\files\BMT | binary | |
MD5:334A76C2015BDFD3952D68800C95C790 | SHA256:F0B9690E24FA67BBC3888EAA75E43E5EC30B540DAC30E986BC36F7CA0586D4BC | |||
| 4480 | i-BMTMDMv1.4.exe | C:\ProgramData\43f7cc1d\files\curl.exe | executable | |
MD5:0189C26A470BAE917C43E54206624CCE | SHA256:FB0F2B261DBA51EB888A1A6037E9502D2F21F1792FDC3B61EB85F6FDCE618926 | |||
| 4480 | i-BMTMDMv1.4.exe | C:\ProgramData\43f7cc1d\files\com.apple.purplebuddy.plist | binary | |
MD5:1EBD827269728E15CAEA34A2BCE762EA | SHA256:C43157470B15963125473A5F2A3F17972332320A7912EBF6C0664EB732E4B8AD | |||
| 4480 | i-BMTMDMv1.4.exe | C:\ProgramData\43f7cc1d\files\getopt.dll | executable | |
MD5:F37A855C8608F79C192A11FAC7BB1683 | SHA256:77191BF2E4640204FCC363896220B2EF81BFF27D15DDCCE39C54B65392382FCE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
18
DNS requests
13
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?95ffe5009287b7a1 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?2efe063e74f19306 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?15028c5fe99424fd | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?c3dcf37796d7e1e6 | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.110.147:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
2412 | MoUsoCoreWorker.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?09a568330712e269 | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.192.152.196:443 | https://www.apple.com/ | unknown | html | 186 Kb | whitelisted |
— | — | POST | 200 | 20.189.173.11:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.130:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.71:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
— | — | 88.221.110.147:80 | — | Akamai International B.V. | DE | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2412 | MoUsoCoreWorker.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
3640 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2864 | smartscreen.exe | 4.175.223.124:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1696 | svchost.exe | 23.60.203.209:443 | fs.microsoft.com | AKAMAI-AS | DE | whitelisted |
5948 | i-BMT MDM.exe | 88.223.84.190:443 | reseller.bmt-pro.com | UAB INIT | LT | unknown |
5948 | i-BMT MDM.exe | 184.31.84.172:443 | statici.icloud.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
login.live.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
reseller.bmt-pro.com |
| unknown |
statici.icloud.com |
| whitelisted |
www.apple.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |