analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
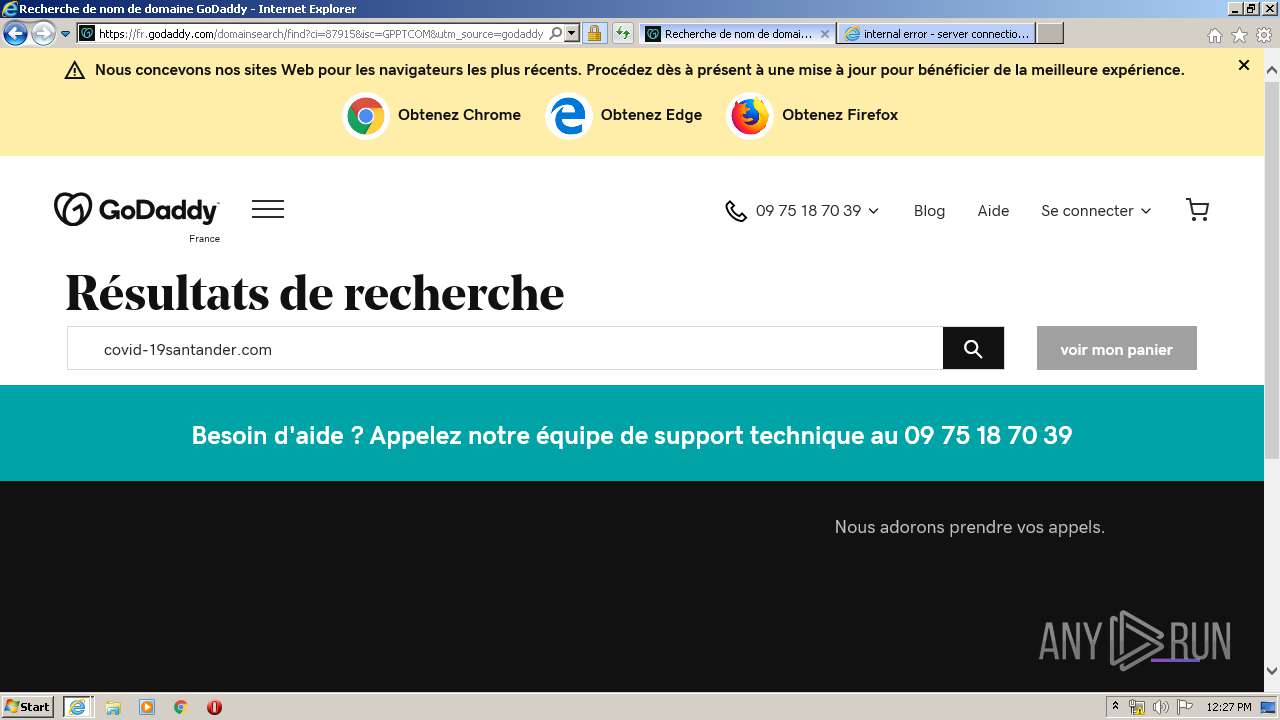
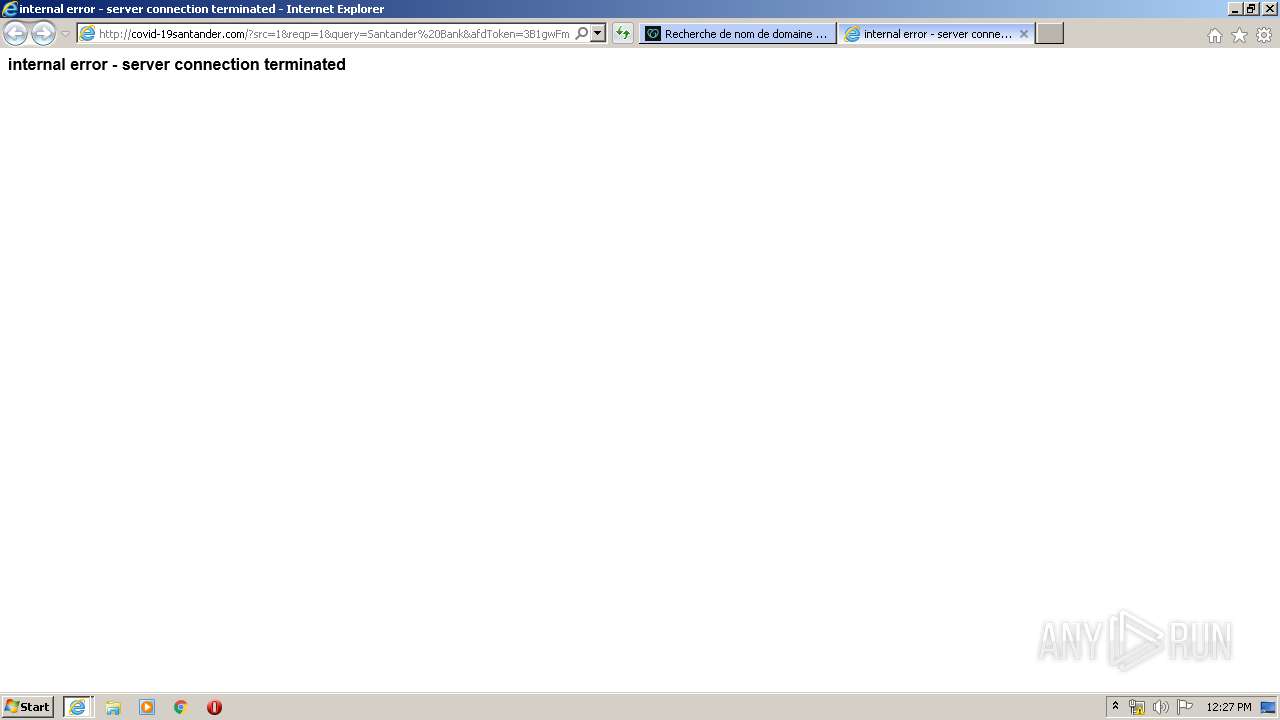
| URL: | http://covid-19santander.com/ |
| Full analysis: | https://app.any.run/tasks/e6d05e07-c9d9-4218-9ccf-5f3a4d8440b8 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 11:25:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C4D2B51DB7BE0DCCCE708DC561783D1A |
| SHA1: | FE87BDA25DC4A939FD3032CE281D307B09DC7785 |
| SHA256: | 2A457288A2E04679E83053546E40F11CAA82DA405EC2111D2FCCD2534E73BAD1 |
| SSDEEP: | 3:N1KdKTAyBiBA9:CIkLa |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Drops Coronavirus (possible) decoy
- iexplore.exe (PID: 3896)
- iexplore.exe (PID: 3028)
- iexplore.exe (PID: 1500)
Reads internet explorer settings
- iexplore.exe (PID: 3896)
- iexplore.exe (PID: 1500)
Reads Internet Cache Settings
- iexplore.exe (PID: 3028)
- iexplore.exe (PID: 3896)
- iexplore.exe (PID: 1500)
Changes internet zones settings
- iexplore.exe (PID: 3028)
Reads settings of System Certificates
- iexplore.exe (PID: 3896)
- iexplore.exe (PID: 3028)
Creates files in the user directory
- iexplore.exe (PID: 3896)
- iexplore.exe (PID: 3028)
Application launched itself
- iexplore.exe (PID: 3028)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3028)
Changes settings of System certificates
- iexplore.exe (PID: 3028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 3028 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://covid-19santander.com/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 3896 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3028 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 1500 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3028 CREDAT:595218 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
Total events
8 097
Read events
569
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
107
Text files
152
Unknown types
51
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3896 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabE5B5.tmp | — | |
MD5:— | SHA256:— | |||
| 3896 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarE5B6.tmp | — | |
MD5:— | SHA256:— | |||
| 3896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\pTWcqaRgZGyzozSaozSkpzHhpTW6[1].htm | html | |
MD5:58E8D4B037A0777C748FF1F9BB2BCDD8 | SHA256:56F3372F81D2A9BF6BE86405E3CB683006A9ADA30CDE484DFC409E0799A46B81 | |||
| 3896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\feature-illu-dot-com-domain[1].png | image | |
MD5:DB3AA7AA093885431A1E1A3702178386 | SHA256:121D7775C24FCFCE6AF1A5E5B1506F3F81F930C1B47089B9C9CC4572BC9E2F5A | |||
| 3896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\jquery-1.3.1.min[1].js | text | |
MD5:5B5A4B70ADC295F9FB97D698C3CB054F | SHA256:8629280C64020E8B35C76F71BF51D449BCE65EC56FBE467799A1BB98A0C68EC4 | |||
| 3896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\1UAOJV3W.htm | html | |
MD5:AE931C177EF0F614BA9F9E60D2B46321 | SHA256:E8D53108CDCD4CA7485B22FB7285F18712027A2B1E4742BC983A932324FB8516 | |||
| 3896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\8QU1CQCK.htm | html | |
MD5:B883C5853B2354F6173602C57A3BB4B5 | SHA256:0DAAF8AE77F8AAF25C9C67A6386C83AB19EA80883A151F804F5D54E46A8AA7AD | |||
| 3896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | binary | |
MD5:B15739CA0BF6984976BB73BEE951204D | SHA256:BECF7EDED8CDA10AF7A7D58FD806DA7B5CCE605616D93D9D22B7263C2DEBBB90 | |||
| 3896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\uxcore2.min[1].css | text | |
MD5:91CF7B6379623513814916F4C4B3D10B | SHA256:BBC268F3EAA9F03A68A43EDEEAF7E8C2C610FD1887151BCD6700366056AD4C84 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
86
TCP/UDP connections
166
DNS requests
54
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3896 | iexplore.exe | GET | — | 192.124.249.23:80 | http://ocsp.starfieldtech.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQUwPiEZQ6%2FsVZNPaFToNfxx8ZwqAQUfAwyH6fZMH%2FEfWijYqihzqsHWycCAQc%3D | US | — | — | whitelisted |
3896 | iexplore.exe | GET | 200 | 50.63.202.58:80 | http://covid-19santander.com/ | US | html | 465 b | malicious |
3896 | iexplore.exe | GET | 200 | 23.55.110.190:80 | http://ak2.imgaft.com/images/feature-illu-dot-com-domain.png | US | image | 1.42 Kb | shared |
3896 | iexplore.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
3896 | iexplore.exe | GET | — | 192.124.249.23:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | — | — | whitelisted |
3896 | iexplore.exe | GET | 200 | 104.109.73.120:80 | http://parked-content.godaddy.com/images/99C_code.png | NL | image | 7.42 Kb | whitelisted |
3896 | iexplore.exe | GET | 200 | 23.55.110.190:80 | http://ak2.imgaft.com/images/new_logo_GDTrans.png | US | image | 3.78 Kb | shared |
3896 | iexplore.exe | GET | 200 | 216.58.210.4:80 | http://www.google.com/adsense/domains/caf.js | US | text | 56.0 Kb | whitelisted |
3896 | iexplore.exe | GET | 200 | 23.55.110.190:80 | http://ak2.imgaft.com/script/jquery-1.3.1.min.js | US | text | 23.7 Kb | shared |
3896 | iexplore.exe | GET | 200 | 104.109.73.120:80 | http://parked-content.godaddy.com/park/pTWcqaRgZGyzozSaozSkpzHhpTW6 | NL | html | 263 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3896 | iexplore.exe | 216.58.210.4:80 | www.google.com | Google Inc. | US | whitelisted |
3896 | iexplore.exe | 23.8.15.19:443 | www.godaddy.com | Akamai International B.V. | NL | suspicious |
3896 | iexplore.exe | 192.124.249.22:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
3896 | iexplore.exe | 50.63.202.58:80 | — | GoDaddy.com, LLC | US | malicious |
3028 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3896 | iexplore.exe | 192.124.249.23:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
3896 | iexplore.exe | 104.109.73.120:80 | parked-content.godaddy.com | Akamai International B.V. | NL | whitelisted |
3896 | iexplore.exe | 23.55.110.190:80 | ak2.imgaft.com | NTT America, Inc. | US | unknown |
3896 | iexplore.exe | 192.124.249.31:80 | crl.godaddy.com | Sucuri | US | unknown |
3028 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
covid-19santander.com |
| malicious |
parked-content.godaddy.com |
| whitelisted |
www.google.com |
| whitelisted |
www.godaddy.com |
| whitelisted |
ak2.imgaft.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
crl.godaddy.com |
| whitelisted |
img1.wsimg.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Suspicious Domain Request for Possible COVID-19 Domain M1 |
3896 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious GET Request with Possible COVID-19 Domain M1 |
3896 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious GET Request with Possible COVID-19 Domain M1 |
3896 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious GET Request with Possible COVID-19 Domain M1 |
3896 | iexplore.exe | Potentially Bad Traffic | ET HUNTING Suspicious GET Request with Possible COVID-19 URI M1 |
3028 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious GET Request with Possible COVID-19 Domain M1 |
1500 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious GET Request with Possible COVID-19 Domain M1 |
3896 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious GET Request with Possible COVID-19 Domain M1 |
3896 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious GET Request with Possible COVID-19 Domain M1 |
3896 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious GET Request with Possible COVID-19 Domain M1 |